7.2 KiB
27017,27018 - Pentesting MongoDB
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.

Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
Engage with content that delves into the thrill and challenges of hacking
Real-Time Hack News
Keep up-to-date with fast-paced hacking world through real-time news and insights
Latest Announcements
Stay informed with the newest bug bounties launching and crucial platform updates
Join us on Discord and start collaborating with top hackers today!
Basic Information
MongoDB ni mfumo wa usimamizi wa data wa chanzo wazi unaotumia mfano wa hifadhidata ya hati kushughulikia aina mbalimbali za data. Inatoa kubadilika na upanuzi kwa usimamizi wa data zisizo na muundo au zenye muundo wa nusu katika programu kama vile uchanganuzi wa data kubwa na usimamizi wa maudhui. Port ya kawaida: 27017, 27018
PORT STATE SERVICE VERSION
27017/tcp open mongodb MongoDB 2.6.9 2.6.9
Enumeration
Manual
from pymongo import MongoClient
client = MongoClient(host, port, username=username, password=password)
client.server_info() #Basic info
#If you have admin access you can obtain more info
admin = client.admin
admin_info = admin.command("serverStatus")
cursor = client.list_databases()
for db in cursor:
print(db)
print(client[db["name"]].list_collection_names())
#If admin access, you could dump the database also
Baadhi ya amri za MongoDB:
show dbs
use <db>
show collections
db.<collection>.find() #Dump the collection
db.<collection>.count() #Number of records of the collection
db.current.find({"username":"admin"}) #Find in current db the username admin
Kiotomatiki
nmap -sV --script "mongo* and default" -p 27017 <IP> #By default all the nmap mongo enumerate scripts are used
Shodan
- Mongodb yote:
"mongodb server information" - Tafuta seva za mongodb zilizo wazi kabisa:
"mongodb server information" -"partially enabled" - Tu sehemu ya kuanzisha uthibitisho:
"mongodb server information" "partially enabled"
Login
Kwa default mongo haitaji nenosiri.
Admin ni hifadhidata ya kawaida ya mongo.
mongo <HOST>
mongo <HOST>:<PORT>
mongo <HOST>:<PORT>/<DB>
mongo <database> -u <username> -p '<password>'
The nmap script: mongodb-brute itakagua kama creds zinahitajika.
nmap -n -sV --script mongodb-brute -p 27017 <ip>
Brute force
Angalia ndani ya /opt/bitnami/mongodb/mongodb.conf kujua kama nywila zinahitajika:
grep "noauth.*true" /opt/bitnami/mongodb/mongodb.conf | grep -v "^#" #Not needed
grep "auth.*true" /opt/bitnami/mongodb/mongodb.conf | grep -v "^#\|noauth" #Not needed
Mongo Objectid Predict
Mfano kutoka hapa.
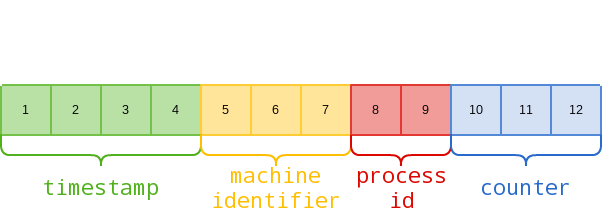
Mongo Object IDs ni nyuzi 12 za hexadecimal:
Kwa mfano, hapa kuna jinsi tunavyoweza kuchambua ID halisi ya Object iliyorejeshwa na programu: 5f2459ac9fa6dc2500314019
- 5f2459ac: 1596217772 katika desimali = Ijumaa, 31 Julai 2020 17:49:32
- 9fa6dc: Kitambulisho cha Mashine
- 2500: Kitambulisho cha Mchakato
- 314019: Kihesabu kinachoongezeka
Kati ya vipengele vilivyotajwa, kitambulisho cha mashine kitabaki kuwa sawa kwa muda wote ambapo hifadhidata inatumia mashine halisi/virtual ile ile. Kitambulisho cha mchakato kitabadilika tu ikiwa mchakato wa MongoDB utaanzishwa upya. Wakati wa kutokea utaongezwa kila sekunde. Changamoto pekee katika kukisia Object IDs kwa kuongezea tu thamani za kihesabu na wakati, ni ukweli kwamba Mongo DB inazalisha Object IDs na inatoa Object IDs kwa kiwango cha mfumo.
Zana https://github.com/andresriancho/mongo-objectid-predict, ikitolewa ID ya kuanzia ya Object (unaweza kuunda akaunti na kupata ID ya kuanzia), inarudisha karibu Object IDs 1000 zinazoweza kuwa zimetolewa kwa vitu vya baadaye, hivyo unahitaji tu kuzitafutia nguvu.
Post
Ikiwa wewe ni root unaweza kubadilisha faili ya mongodb.conf ili usihitaji akidi (noauth = true) na kuingia bila akidi.

Jiunge na HackenProof Discord server ili kuwasiliana na hackers wenye uzoefu na wawindaji wa makosa!
Hacking Insights
Shiriki na maudhui yanayochunguza msisimko na changamoto za hacking
Real-Time Hack News
Endelea kuwa na habari za hivi punde katika ulimwengu wa hacking kupitia habari na maarifa ya wakati halisi
Latest Announcements
Baki na habari kuhusu makosa mapya yanayoanzishwa na masasisho muhimu ya jukwaa
Jiunge nasi kwenye Discord na uanze kushirikiana na hackers bora leo!
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.