8.4 KiB
macOS 유용한 명령어
htARTE (HackTricks AWS Red Team Expert)를 통해 AWS 해킹을 처음부터 전문가까지 배워보세요!
HackTricks를 지원하는 다른 방법:
- 회사를 HackTricks에서 광고하거나 HackTricks를 PDF로 다운로드하려면 SUBSCRIPTION PLANS를 확인하세요!
- 공식 PEASS & HackTricks 스웨그를 얻으세요.
- The PEASS Family를 발견하세요. 독점적인 NFTs 컬렉션입니다.
- 💬 Discord 그룹 또는 텔레그램 그룹에 참여하거나 Twitter 🐦 @carlospolopm를 팔로우하세요.
- Hacking 트릭을 공유하려면 HackTricks 및 HackTricks Cloud github 저장소에 PR을 제출하세요.
MacOS 자동 열거 도구
- MacPEAS: https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS
- Metasploit: https://github.com/rapid7/metasploit-framework/blob/master/modules/post/osx/gather/enum_osx.rb
- SwiftBelt: https://github.com/cedowens/SwiftBelt
특정 MacOS 명령어
#System info
date
cal
uptime #show time from starting
w #list users
whoami #this user
finger username #info about user
uname -a #sysinfo
cat /proc/cpuinfo #processor
cat /proc/meminfo #memory
free #check memory
df #check disk
launchctl list #List services
atq #List "at" tasks for the user
sysctl -a #List kernel configuration
diskutil list #List connected hard drives
nettop #Monitor network usage of processes in top style
system_profiler SPSoftwareDataType #System info
system_profiler SPPrintersDataType #Printer
system_profiler SPApplicationsDataType #Installed Apps
system_profiler SPFrameworksDataType #Instaled framework
system_profiler SPDeveloperToolsDataType #Developer tools info
system_profiler SPStartupItemDataType #Startup Items
system_profiler SPNetworkDataType #Network Capabilities
system_profiler SPFirewallDataType #Firewall Status
system_profiler SPNetworkLocationDataType #Known Network
system_profiler SPBluetoothDataType #Bluetooth Info
system_profiler SPEthernetDataType #Ethernet Info
system_profiler SPUSBDataType #USB info
system_profiler SPAirPortDataType #Airport Info
#Searches
mdfind password #Show all the files that contains the word password
mfind -name password #List all the files containing the word password in the name
#Open any app
open -a <Application Name> --hide #Open app hidden
open some.doc -a TextEdit #Open a file in one application
#Computer doesn't go to sleep
caffeinate &
#Screenshot
# This will ask for permission to the user
screencapture -x /tmp/ss.jpg #Save screenshot in that file
#Get clipboard info
pbpaste
#system_profiler
system_profiler --help #This command without arguments take lot of memory and time.
system_profiler -listDataTypes
system_profiler SPSoftwareDataType SPNetworkDataType
#Network
arp -i en0 -l -a #Print the macOS device's ARP table
lsof -i -P -n | grep LISTEN
smbutil statshares -a #View smb shares mounted to the hard drive
#networksetup - set or view network options: Proxies, FW options and more
networksetup -listallnetworkservices #List network services
networksetup -listallhardwareports #Hardware ports
networksetup -getinfo Wi-Fi #Wi-Fi info
networksetup -getautoproxyurl Wi-Fi #Get proxy URL for Wifi
networksetup -getwebproxy Wi-Fi #Wifi Web proxy
networksetup -getftpproxy Wi-Fi #Wifi ftp proxy
#Brew
brew list #List installed
brew search <text> #Search package
brew info <formula>
brew install <formula>
brew uninstall <formula>
brew cleanup #Remove older versions of installed formulae.
brew cleanup <formula> #Remove older versions of specified formula.
#Make the machine talk
say hello -v diego
#spanish: diego, Jorge, Monica
#mexican: Juan, Paulina
#french: Thomas, Amelie
########### High privileges actions
sudo purge #purge RAM
#Sharing preferences
sudo launchctl load -w /System/Library/LaunchDaemons/ssh.plist (enable ssh)
sudo launchctl unload /System/Library/LaunchDaemons/ssh.plist (disable ssh)
#Start apache
sudo apachectl (start|status|restart|stop)
##Web folder: /Library/WebServer/Documents/
#Remove DNS cache
dscacheutil -flushcache
sudo killall -HUP mDNSResponder
설치된 소프트웨어 및 서비스
설치된 응용 프로그램과 설치된 리소스에 대한 권한을 확인하여 의심스러운 애플리케이션을 찾습니다:
system_profiler SPApplicationsDataType #Installed Apps
system_profiler SPFrameworksDataType #Instaled framework
lsappinfo list #Installed Apps
launchtl list #Services
사용자 프로세스
User processes refer to the programs or applications that are executed by individual users on a macOS system. These processes run in the user's context and are associated with their user account. Understanding user processes is essential for managing and securing a macOS system.
List User Processes
To list all user processes running on a macOS system, you can use the following command:
ps -U <username>
Replace <username> with the actual username of the user whose processes you want to list.
Kill User Process
To terminate a specific user process, you can use the kill command followed by the process ID (PID) of the process. The PID can be obtained from the process list.
kill <PID>
Replace <PID> with the actual process ID of the process you want to terminate.
Monitor User Processes
To monitor the activity of user processes in real-time, you can use the top command. This command displays a dynamic view of the processes running on the system, including their resource usage and other relevant information.
top -U <username>
Replace <username> with the actual username of the user whose processes you want to monitor.
Check Process Ownership
To check the ownership of a specific process, you can use the ps command followed by the process ID (PID) of the process.
ps -p <PID> -o user
Replace <PID> with the actual process ID of the process you want to check.
Conclusion
Understanding user processes and how to manage them is crucial for maintaining the security and stability of a macOS system. By being able to list, terminate, and monitor user processes, you can effectively manage the activities of individual users on the system.
# will print all the running services under that particular user domain.
launchctl print gui/<users UID>
# will print all the running services under root
launchctl print system
# will print detailed information about the specific launch agent. And if it’s not running or you’ve mistyped, you will get some output with a non-zero exit code: Could not find service “com.company.launchagent.label” in domain for login
launchctl print gui/<user's UID>/com.company.launchagent.label
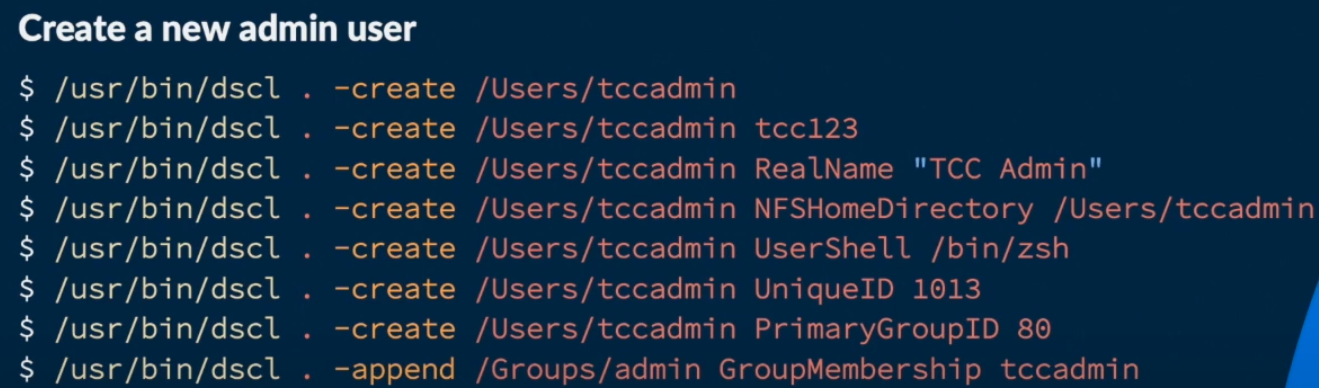
사용자 생성
프롬프트 없이
htARTE (HackTricks AWS Red Team Expert)를 통해 AWS 해킹을 처음부터 전문가까지 배워보세요!
HackTricks를 지원하는 다른 방법:
- 회사를 HackTricks에서 광고하거나 HackTricks를 PDF로 다운로드하려면 SUBSCRIPTION PLANS를 확인하세요!
- 공식 PEASS & HackTricks 상품을 구매하세요.
- The PEASS Family를 발견하세요. 독점적인 NFT 컬렉션입니다.
- 💬 Discord 그룹 또는 텔레그램 그룹에 참여하거나 Twitter 🐦 @carlospolopm을 팔로우하세요.
- HackTricks와 HackTricks Cloud github 저장소에 PR을 제출하여 여러분의 해킹 기법을 공유하세요.