6.7 KiB
Google CTF 2018 - 我们来玩个游戏吧?
☁️ HackTricks 云 ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- 你在一家网络安全公司工作吗?想要在 HackTricks 中宣传你的公司吗?或者你想要获取最新版本的 PEASS 或下载 HackTricks 的 PDF吗?请查看订阅计划!
- 发现我们的独家NFTs收藏品——The PEASS Family
- 获取官方 PEASS & HackTricks 商品
- 加入💬 Discord 群组 或 Telegram 群组,或者关注我在Twitter上的🐦@carlospolopm。
- 通过向hacktricks 仓库 和hacktricks-cloud 仓库 提交 PR 来分享你的黑客技巧。
在这里下载 APK:
我将上传 APK 到 https://appetize.io/(免费账户)来查看 APK 的行为:
看起来你需要赢得 1000000 次才能获得 flag。
按照 pentesting Android 的步骤,你可以反编译应用程序以获取 smali 代码,并使用 jadx 读取 Java 代码。
阅读 Java 代码:
看起来打印 flag 的函数是 m()。
Smali 更改
第一次调用 m()
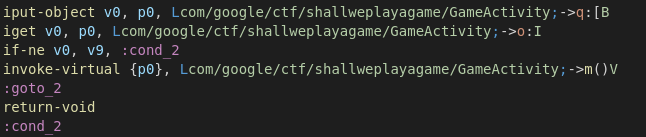
让应用程序在变量 this.o != 1000000 时调用 m(),只需更改条件:
if-ne v0, v9, :cond_2
/hive/hacktricks/mobile-pentesting/android-app-pentesting/google-ctf-2018-shall-we-play-a-game.md
Google CTF 2018 - Shall we play a game?
Challenge Description
This challenge is an Android application that simulates a game. The goal is to find a vulnerability in the app and exploit it to gain access to the flag.
Initial Analysis
To start the analysis, we can decompile the APK file using tools like JADX or apktool. Once decompiled, we can analyze the source code to identify any potential vulnerabilities.
Reverse Engineering
Upon analyzing the source code, we find that the app uses a custom encryption algorithm to encrypt the flag. The algorithm takes the flag as input and performs a series of mathematical operations to encrypt it. To reverse engineer the algorithm, we can analyze the code and understand the mathematical operations being performed.
Vulnerability Identification
After reverse engineering the encryption algorithm, we identify a vulnerability in the way the encryption key is generated. The key is derived from a hardcoded string, which makes it predictable and easy to guess. This vulnerability allows an attacker to easily decrypt the flag without knowing the encryption algorithm.
Exploitation
To exploit the vulnerability, we can write a script that generates the encryption key based on the hardcoded string. Once we have the key, we can decrypt the flag and obtain the secret information.
Conclusion
This challenge demonstrates the importance of secure encryption algorithms and key generation. Hardcoding encryption keys can lead to vulnerabilities that can be easily exploited by attackers. It is crucial to use strong and unpredictable keys to ensure the security of sensitive information.
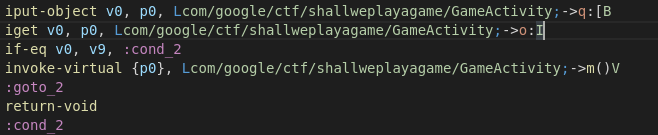
if-eq v0, v9, :cond_2
按照pentest Android的步骤重新编译和签名APK。然后,将其上传到https://appetize.io/,看看会发生什么:
看起来,旗帜在没有完全解密的情况下被写入。可能应该调用m()函数1000000次。
另一种方法是不改变指令,而是改变比较的指令:
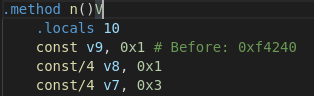
另一种方法是将比较值设置为1,这样this.o将与1进行比较:
第四种方法是添加一条指令,将v9(1000000)的值移动到v0(this.o):
解决方案
当你第一次赢得比赛时,让应用程序运行循环100000次。为此,您只需要创建**:goto_6循环,并使应用程序在_this.o**不等于100000时跳转到那里:
您需要在物理设备上执行此操作,因为(我不知道为什么)在模拟设备上无法正常工作。
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- 您在网络安全公司工作吗?您想在HackTricks中看到您的公司广告吗?或者您想获得最新版本的PEASS或下载PDF格式的HackTricks吗?请查看SUBSCRIPTION PLANS!
- 发现我们的独家NFTs收藏品The PEASS Family
- 获取官方PEASS和HackTricks衣物
- 加入💬 Discord群组或电报群组,或在Twitter上关注我🐦@carlospolopm。
- 通过向hacktricks repo 和hacktricks-cloud repo 提交PR来分享您的黑客技巧。