3.9 KiB
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.
Pickle Rick
This machine was categorised as easy and it was pretty easy.
Enumeration
I started enumerating the machine using my tool Legion:
In as you can see 2 ports are open: 80 (HTTP) and 22 (SSH)
So, I launched legion to enumerate the HTTP service:
Note that in the image you can see that robots.txt contains the string Wubbalubbadubdub
After some seconds I reviewed what disearch has already discovered :
And as you may see in the last image a login page was discovered.
Checking the source code of the root page, a username is discovered: R1ckRul3s
Therefore, you can login on the login page using the credentials R1ckRul3s:Wubbalubbadubdub
User
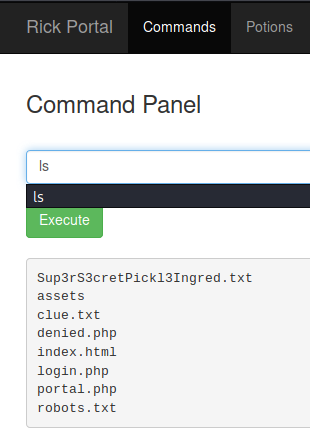
Using those credentials you will access a portal where you can execute commands:
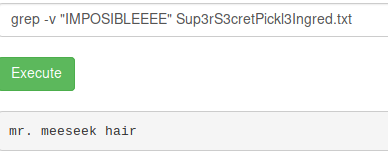
Some commands like cat aren't allowed but you can read the first ingredient (flag) using for example grep:
Then I used:
To obtain a reverse shell:
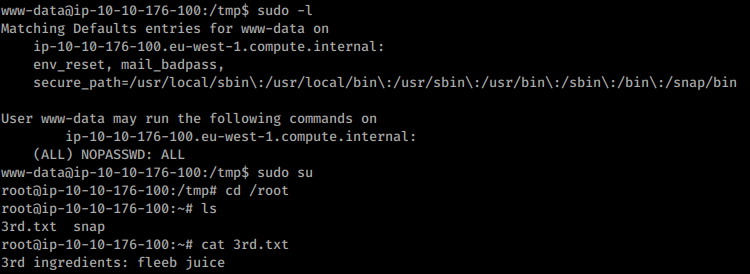
The second ingredient can be found in /home/rick
Root
The user www-data can execute anything as sudo:
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.