3.7 KiB
3702/UDP - Pentesting WS-Discovery
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
Basic Information
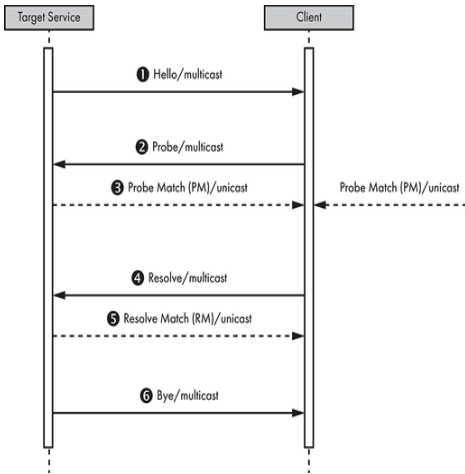
The Web Services Dynamic Discovery Protocol (WS-Discovery) is identified as a protocol designed for the discovery of services within a local network through multicast. It facilitates the interaction between Target Services and Clients. Target Services are endpoints available for discovery, while Clients are the ones actively searching for these services. Communication is established using SOAP queries over UDP, directed to the multicast address 239.255.255.250 and UDP port 3702.
Upon joining a network, a Target Service announces its presence by broadcasting a multicast Hello. It remains open to receiving multicast Probes from Clients that are on the lookout for services by Type, an identifier unique to the endpoint (e.g., NetworkVideoTransmitter for an IP camera). In response to a matching Probe, a Target Service may send a unicast Probe Match. Similarly, a Target Service could receive a multicast Resolve aimed at identifying a service by name, to which it may reply with a unicast Resolve Match if it is the intended target. In the event of leaving the network, a Target Service attempts to broadcast a multicast Bye, signaling its departure.
Default port: 3702
PORT STATE SERVICE
3702/udp open|filtered unknown
| wsdd-discover:
| Devices
| Message id: 39a2b7f2-fdbd-690c-c7c9-deadbeefceb3
| Address: http://10.0.200.116:50000
|_ Type: Device wprt:PrintDeviceType
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.