4.9 KiB
PsExec/Winexec/ScExec
HackTricks in 🐦 Twitter 🐦 - 🎙️ Twitch Wed - 18.30(UTC) 🎙️ - 🎥 Youtube 🎥
-
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
-
Discover The PEASS Family, our collection of exclusive NFTs
-
Get the official PEASS & HackTricks swag
-
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
-
Share your hacking tricks by submitting PRs to the hacktricks repo and hacktricks-cloud repo.
How do they work
- Copy a service binary to the ADMIN$ share over SMB
- Create a service on the remote machine pointing to the binary
- Remotely start the service
- When exited, stop the service and delete the binary
Manually PsExec'ing
First let's assume we have a payload executable we generated with msfvenom and obfuscated with Veil (so AV doesn't flag it). In this case, I created a meterpreter reverse_http payload and called it 'met8888.exe'
Copy the binary. From our "jarrieta" command prompt, simply copy the binary to the ADMIN$. Really though, it could be copied and hidden anywhere on the filesystem.
Create a service. The Windows sc command is used to query, create, delete, etc Windows services and can be used remotely. Read more about it here. From our command prompt, we'll remotely create a service called "meterpreter" that points to our uploaded binary:
Start the service. The last step is to start the service and execute the binary. Note: when the service starts it will "time-out" and generate an error. That's because our meterpreter binary isn't an actual service binary and won't return the expected response code. That's fine because we just need it to execute once to fire:
If we look at our Metasploit listener, we'll see the session has been opened.
Clean the service.
Extracted from here: https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-2-psexec-and-services/
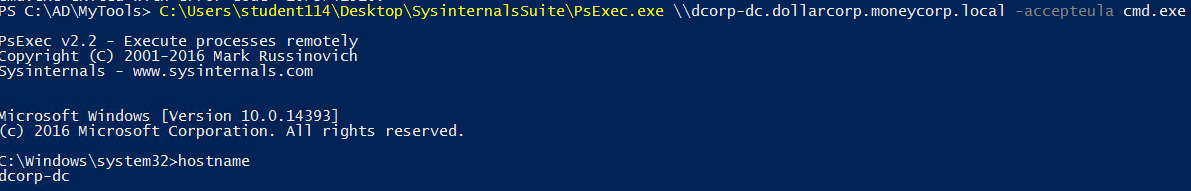
You could also use the Windows Sysinternals binary PsExec.exe:
HackTricks in 🐦 Twitter 🐦 - 🎙️ Twitch Wed - 18.30(UTC) 🎙️ - 🎥 Youtube 🎥
-
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
-
Discover The PEASS Family, our collection of exclusive NFTs
-
Get the official PEASS & HackTricks swag
-
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
-
Share your hacking tricks by submitting PRs to the hacktricks repo and hacktricks-cloud repo.