13 KiB
9200 - Pentesting Elasticsearch
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
Basic information
Elasticsearch ni distributed, open source injini ya kutafuta na kuchambua aina zote za data. Inajulikana kwa speed, scalability, na simple REST APIs. Imejengwa juu ya Apache Lucene, ilitolewa kwa mara ya kwanza mwaka 2010 na Elasticsearch N.V. (sasa inajulikana kama Elastic). Elasticsearch ni sehemu kuu ya Elastic Stack, mkusanyiko wa zana za open source za kuingiza data, kuongeza thamani, kuhifadhi, kuchambua, na kuonyesha. Stack hii, inayojulikana kama ELK Stack, pia inajumuisha Logstash na Kibana, na sasa ina wakala wa usafirishaji wa data wa mwanga unaoitwa Beats.
What is an Elasticsearch index?
Index ya Elasticsearch ni mkusanyiko wa nyaraka zinazohusiana zilizohifadhiwa kama JSON. Kila hati ina funguo na thamani zao zinazolingana (nyuzi, nambari, booleans, tarehe, orodha, maeneo ya kijiografia, nk.).
Elasticsearch inatumia muundo wa data wenye ufanisi unaoitwa inverted index ili kuwezesha utafutaji wa haraka wa maandiko yote. Index hii inataja kila neno la kipekee katika nyaraka na kutambua nyaraka ambazo kila neno linaonekana.
Wakati wa mchakato wa kuunda index, Elasticsearch inahifadhi nyaraka na kujenga index iliyo kinyume, ikiruhusu utafutaji wa karibu wakati halisi. Index API inatumika kuongeza au kuboresha nyaraka za JSON ndani ya index maalum.
Default port: 9200/tcp
Manual Enumeration
Banner
Protokali inayotumika kufikia Elasticsearch ni HTTP. Unapofikia kupitia HTTP utaona taarifa za kuvutia: http://10.10.10.115:9200/
Ikiwa huoni jibu hilo unapofikia / angalia sehemu ifuatayo.
Authentication
Kwa default Elasticsearch haina uthibitisho ulioanzishwa, hivyo kwa default unaweza kufikia kila kitu ndani ya hifadhidata bila kutumia akidi yoyote.
Unaweza kuthibitisha kuwa uthibitisho umezimwa kwa ombi la:
curl -X GET "ELASTICSEARCH-SERVER:9200/_xpack/security/user"
{"error":{"root_cause":[{"type":"exception","reason":"Security must be explicitly enabled when using a [basic] license. Enable security by setting [xpack.security.enabled] to [true] in the elasticsearch.yml file and restart the node."}],"type":"exception","reason":"Security must be explicitly enabled when using a [basic] license. Enable security by setting [xpack.security.enabled] to [true] in the elasticsearch.yml file and restart the node."},"status":500}
Hata hivyo, ikiwa utatuma ombi kwa / na kupokea jibu kama hili:
{"error":{"root_cause":[{"type":"security_exception","reason":"missing authentication credentials for REST request [/]","header":{"WWW-Authenticate":"Basic realm=\"security\" charset=\"UTF-8\""}}],"type":"security_exception","reason":"missing authentication credentials for REST request [/]","header":{"WWW-Authenticate":"Basic realm=\"security\" charset=\"UTF-8\""}},"status":401}
Hii itamaanisha kwamba uthibitishaji umewekwa na unahitaji akidi halali kupata taarifa yoyote kutoka elasticserach. Kisha, unaweza kujaribu kuibua nguvu (inatumia HTTP basic auth, hivyo chochote kinachoweza BF HTTP basic auth kinaweza kutumika).
Hapa una orodha ya majina ya watumiaji ya kawaida: elastic (superuser), remote_monitoring_user, beats_system, logstash_system, kibana, kibana_system, apm_system, _anonymous_._ Matoleo ya zamani ya Elasticsearch yana nenosiri la kawaida changeme kwa ajili ya mtumiaji huyu.
curl -X GET http://user:password@IP:9200/
Msingi wa Uainishaji wa Watumiaji
#List all roles on the system:
curl -X GET "ELASTICSEARCH-SERVER:9200/_security/role"
#List all users on the system:
curl -X GET "ELASTICSEARCH-SERVER:9200/_security/user"
#Get more information about the rights of an user:
curl -X GET "ELASTICSEARCH-SERVER:9200/_security/user/<USERNAME>"
Elastic Info
Hapa kuna baadhi ya endpoints ambazo unaweza kupata kupitia GET ili kupata baadhi ya habari kuhusu elasticsearch:
| _cat | /_cluster | /_security |
|---|---|---|
| /_cat/segments | /_cluster/allocation/explain | /_security/user |
| /_cat/shards | /_cluster/settings | /_security/privilege |
| /_cat/repositories | /_cluster/health | /_security/role_mapping |
| /_cat/recovery | /_cluster/state | /_security/role |
| /_cat/plugins | /_cluster/stats | /_security/api_key |
| /_cat/pending_tasks | /_cluster/pending_tasks | |
| /_cat/nodes | /_nodes | |
| /_cat/tasks | /_nodes/usage | |
| /_cat/templates | /_nodes/hot_threads | |
| /_cat/thread_pool | /_nodes/stats | |
| /_cat/ml/trained_models | /_tasks | |
| /_cat/transforms/_all | /_remote/info | |
| /_cat/aliases | ||
| /_cat/allocation | ||
| /_cat/ml/anomaly_detectors | ||
| /_cat/count | ||
| /_cat/ml/data_frame/analytics | ||
| /_cat/ml/datafeeds | ||
| /_cat/fielddata | ||
| /_cat/health | ||
| /_cat/indices | ||
| /_cat/master | ||
| /_cat/nodeattrs | ||
| /_cat/nodes |
Hizi endpoints zilichukuliwa kutoka kwenye nyaraka ambapo unaweza kupata zaidi.
Pia, ukipata /_cat jibu litakuwa na /_cat/* endpoints zinazoungwa mkono na mfano.
Katika /_security/user (ikiwa uthibitishaji umewezeshwa) unaweza kuona ni nani mtumiaji mwenye jukumu superuser.
Indices
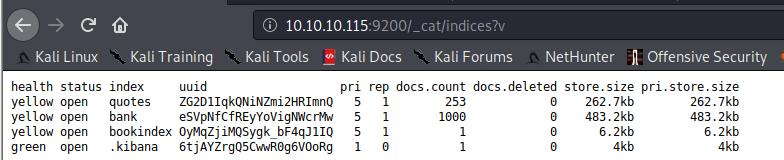
Unaweza kusanya indices zote kwa kufikia http://10.10.10.115:9200/_cat/indices?v
health status index uuid pri rep docs.count docs.deleted store.size pri.store.size
green open .kibana 6tjAYZrgQ5CwwR0g6VOoRg 1 0 1 0 4kb 4kb
yellow open quotes ZG2D1IqkQNiNZmi2HRImnQ 5 1 253 0 262.7kb 262.7kb
yellow open bank eSVpNfCfREyYoVigNWcrMw 5 1 1000 0 483.2kb 483.2kb
To obtain information about which kind of data is saved inside an index you can access: http://host:9200/<index> from example in this case http://10.10.10.115:9200/bank
Dump index
If you want to dump all the contents of an index you can access: http://host:9200/<index>/_search?pretty=true like http://10.10.10.115:9200/bank/_search?pretty=true
Take a moment to compare the contents of the each document (entry) inside the bank index and the fields of this index that we saw in the previous section.
So, at this point you may notice that there is a field called "total" inside "hits" that indicates that 1000 documents were found inside this index but only 10 were retried. This is because by default there is a limit of 10 documents.
But, now that you know that this index contains 1000 documents, you can dump all of them indicating the number of entries you want to dump in the size parameter: http://10.10.10.115:9200/quotes/_search?pretty=true&size=1000asd
Note: If you indicate bigger number all the entries will be dumped anyway, for example you could indicate size=9999 and it will be weird if there were more entries (but you should check).
Dump all
In order to dump all you can just go to the same path as before but without indicating any indexhttp://host:9200/_search?pretty=true like http://10.10.10.115:9200/_search?pretty=true
Remember that in this case the default limit of 10 results will be applied. You can use the size parameter to dump a bigger amount of results. Read the previous section for more information.
Search
If you are looking for some information you can do a raw search on all the indices going to http://host:9200/_search?pretty=true&q=<search_term> like in http://10.10.10.115:9200/_search?pretty=true&q=Rockwell
If you want just to search on an index you can just specify it on the path: http://host:9200/<index>/_search?pretty=true&q=<search_term>
Note that the q parameter used to search content supports regular expressions
You can also use something like https://github.com/misalabs/horuz to fuzz an elasticsearch service.
Write permissions
You can check your write permissions trying to create a new document inside a new index running something like the following:
curl -X POST '10.10.10.115:9200/bookindex/books' -H 'Content-Type: application/json' -d'
{
"bookId" : "A00-3",
"author" : "Sankaran",
"publisher" : "Mcgrahill",
"name" : "how to get a job"
}'
Hiyo cmd itaunda index mpya inayoitwa bookindex yenye hati ya aina books ambayo ina sifa "bookId", "author", "publisher" na "name"
Tazama jinsi index mpya inavyoonekana sasa kwenye orodha:
Na kumbuka sifa zilizoundwa kiotomatiki:
Automatic Enumeration
Zana zingine zitapata baadhi ya data zilizowasilishwa hapo awali:
msf > use auxiliary/scanner/elasticsearch/indices_enum
{% embed url="https://github.com/theMiddleBlue/nmap-elasticsearch-nse" %}
Shodan
port:9200 elasticsearch
{% hint style="success" %}
Jifunze na fanya mazoezi ya AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au fuata sisi kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.