6.4 KiB
113 - Pentesting Ident
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.

Use Trickest to easily build and automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=113-pentesting-ident" %}
Basic Information
Protokali ya Ident inatumika juu ya Intaneti kuhusisha muunganisho wa TCP na mtumiaji maalum. Ilipangwa awali kusaidia katika usimamizi wa mtandao na usalama, inafanya kazi kwa kuruhusu seva kuuliza mteja kwenye bandari 113 ili kutafuta taarifa kuhusu mtumiaji wa muunganisho maalum wa TCP.
Hata hivyo, kutokana na wasiwasi wa kisasa kuhusu faragha na uwezekano wa matumizi mabaya, matumizi yake yamepungua kwani yanaweza bila kukusudia kufichua taarifa za mtumiaji kwa wahusika wasioidhinishwa. Hatua za usalama zilizoboreshwa, kama vile muunganisho wa siri na udhibiti mkali wa ufikiaji, zinapendekezwa ili kupunguza hatari hizi.
Bandari ya kawaida: 113
PORT STATE SERVICE
113/tcp open ident
Enumeration
Manual - Get user/Identify the service
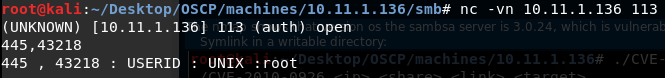
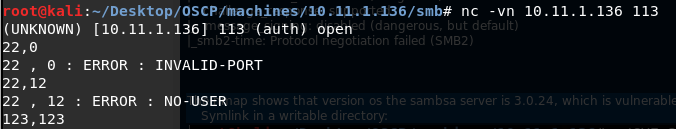
Ikiwa mashine inafanya kazi na huduma ya ident na samba (445) na umeunganishwa na samba ukitumia bandari 43218. Unaweza kupata ni mtumiaji gani anayeendesha huduma ya samba kwa kufanya:
Ikiwa unabonyeza tu enter unapounganisha na huduma:
Makosa mengine:
Nmap
Kwa kawaida (`-sC``) nmap itatambua kila mtumiaji wa kila bandari inayofanya kazi:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3p2 Debian 9 (protocol 2.0)
|_auth-owners: root
| ssh-hostkey:
| 1024 88:23:98:0d:9d:8a:20:59:35:b8:14:12:14:d5:d0:44 (DSA)
|_ 2048 6b:5d:04:71:76:78:56:96:56:92:a8:02:30:73:ee:fa (RSA)
113/tcp open ident
|_auth-owners: identd
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: LOCAL)
|_auth-owners: root
445/tcp open netbios-ssn Samba smbd 3.0.24 (workgroup: LOCAL)
|_auth-owners: root
Ident-user-enum
Ident-user-enum ni script rahisi ya PERL ya kuuliza huduma ya ident (113/TCP) ili kubaini mmiliki wa mchakato unaosikiliza kwenye kila bandari ya TCP ya mfumo wa lengo. Orodha ya majina ya watumiaji iliyokusanywa inaweza kutumika kwa mashambulizi ya kukisia nywila kwenye huduma nyingine za mtandao. Inaweza kusakinishwa kwa apt install ident-user-enum.
root@kali:/opt/local/recon/192.168.1.100# ident-user-enum 192.168.1.100 22 113 139 445
ident-user-enum v1.0 ( http://pentestmonkey.net/tools/ident-user-enum )
192.168.1.100:22 root
192.168.1.100:113 identd
192.168.1.100:139 root
192.168.1.100:445 root
Shodan
oident
Files
identd.conf

Tumia Trickest kujenga na kujiendesha kwa urahisi kazi zinazotumiwa na zana za jamii za kisasa zaidi duniani.
Pata Ufikiaji Leo:
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=113-pentesting-ident" %}
HackTricks Automatic Commands
Protocol_Name: Ident #Protocol Abbreviation if there is one.
Port_Number: 113 #Comma separated if there is more than one.
Protocol_Description: Identification Protocol #Protocol Abbreviation Spelled out
Entry_1:
Name: Notes
Description: Notes for Ident
Note: |
The Ident Protocol is used over the Internet to associate a TCP connection with a specific user. Originally designed to aid in network management and security, it operates by allowing a server to query a client on port 113 to request information about the user of a particular TCP connection.
https://book.hacktricks.xyz/pentesting/113-pentesting-ident
Entry_2:
Name: Enum Users
Description: Enumerate Users
Note: apt install ident-user-enum ident-user-enum {IP} 22 23 139 445 (try all open ports)
{% hint style="success" %}
Jifunze na fanya mazoezi ya AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au tufuatilie kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.