mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-26 22:52:06 +00:00
4.3 KiB
4.3 KiB
Google CTF 2018 - 我们来玩个游戏吧?
从零开始学习AWS黑客技术,成为专家 htARTE(HackTricks AWS红队专家)!
支持HackTricks的其他方式:
- 如果您想在HackTricks中看到您的公司广告或下载PDF格式的HackTricks,请查看订阅计划!
- 获取官方PEASS & HackTricks周边产品
- 探索PEASS家族,我们的独家NFTs收藏品
- 加入 💬 Discord群组 或 电报群组 或 关注我的 Twitter 🐦 @carlospolopm。
- 通过向 HackTricks 和 HackTricks Cloud github仓库提交PR来分享您的黑客技巧。
在此下载APK:
我将上传APK到https://appetize.io/(免费账户)以查看APK的行为:
看起来您需要赢得1000000次才能获得flag。
按照Android渗透测试中的步骤,您可以反编译应用程序以获取smali代码,并使用jadx读取Java代码。
阅读Java代码:
看起来打印flag的函数是 m().
Smali更改
第一次调用m()
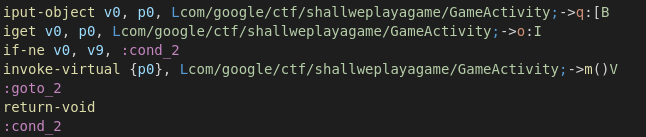
让应用程序在变量 this.o != 1000000 时调用m(),只需更改条件:
if-ne v0, v9, :cond_2
Google CTF 2018: Shall we play a game?
Task 1: Install the APK
- Download the APK from the challenge page.
- Install the APK on your Android device.
Task 2: Explore the app
- Open the app and explore its functionalities.
- Use tools like APKTool, JADX, and JEB to analyze the APK.
- Look for interesting strings, APIs, and endpoints.
Task 3: Analyze the network traffic
- Use tools like Burp Suite or Wireshark to intercept and analyze the app's network traffic.
- Look for any sensitive information being transmitted.
- Identify any potential security vulnerabilities in the network communication.
Task 4: Reverse engineering
- Use tools like JADX, Ghidra, or IDA Pro to reverse engineer the APK.
- Analyze the app's code and look for vulnerabilities or backdoors.
- Try to understand the app's logic and how it handles user input.
Task 5: Exploit the app
- Exploit any vulnerabilities found during the analysis.
- Try to bypass any security mechanisms implemented in the app.
- Gain unauthorized access or control over the app.
Task 6: Get the flag
- Find and extract the flag from the app.
- Submit the flag to complete the challenge.
By completing these tasks, you will gain a better understanding of Android app pentesting and hone your skills as a mobile security professional. Good luck!
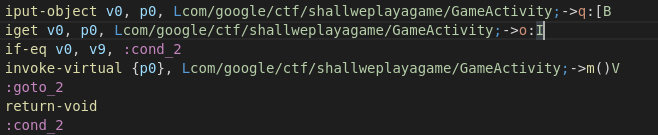
if-eq v0, v9, :cond_2
按照Android渗透测试的步骤重新编译并签署APK。然后,将其上传到https://appetize.io/,看看会发生什么:
看起来旗标是未完全解密就被写入的。可能应该调用m()函数1000000次。
另一种方法是不更改指令,而是更改比较指令:
另一种方法是将值与1000000进行比较,将值设置为1,以便将this.o与1进行比较:
第四种方法是添加一条指令将v9(1000000)的值移动到v0 (this.o):
解决方案
当您第一次获胜时,使应用程序运行循环100000次。为此,您只需要创建**:goto_6循环,并使应用程序跳转到那里,如果this.o**的值不是100000\:
您需要在物理设备内执行此操作,因为(我不知道为什么)在模拟设备中无法正常工作。