4.5 KiB
43 - Pentesting WHOIS
Jifunze AWS hacking kutoka sifuri hadi shujaa na htARTE (Mtaalam wa Timu Nyekundu ya AWS ya HackTricks)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona kampuni yako ikitangazwa kwenye HackTricks au kupakua HackTricks kwa PDF Angalia MIPANGO YA USAJILI!
- Pata bidhaa rasmi za PEASS & HackTricks
- Gundua Familia ya PEASS, mkusanyiko wetu wa NFTs ya kipekee
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @carlospolopm.
- Shiriki mbinu zako za udukuzi kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
Kikundi cha Usalama cha Try Hard

{% embed url="https://discord.gg/tryhardsecurity" %}
Taarifa Msingi
Itifaki ya WHOIS hutumika kama njia ya kawaida ya kuuliza kuhusu wamiliki au wamiliki wa rasilimali mbalimbali za mtandao kupitia ma
PORT STATE SERVICE
43/tcp open whois?
Kuchunguza
Pata habari zote ambazo huduma ya whois ina kuhusu kikoa:
whois -h <HOST> -p <PORT> "domain.tld"
echo "domain.ltd" | nc -vn <HOST> <PORT>
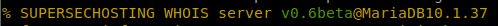
Kumbuka kwamba mara nyingine unapouliza habari fulani kwa huduma ya WHOIS, database inayotumiwa inaonekana kwenye jibu:
Pia, huduma ya WHOIS daima inahitaji kutumia database kuhifadhi na kutoa habari. Kwa hivyo, SQLInjection inaweza kuwepo wakati wa kuuliza database kutoka kwa habari iliyotolewa na mtumiaji. Kwa mfano kufanya: whois -h 10.10.10.155 -p 43 "a') or 1=1#" unaweza kuweza kutoa habari yote iliyohifadhiwa kwenye database.
Shodan
port:43 whois
Kikundi cha Usalama cha Try Hard

{% embed url="https://discord.gg/tryhardsecurity" %}
Amri za Kiotomatiki za HackTricks
Protocol_Name: WHOIS #Protocol Abbreviation if there is one.
Port_Number: 43 #Comma separated if there is more than one.
Protocol_Description: WHOIS #Protocol Abbreviation Spelled out
Entry_1:
Name: Notes
Description: Notes for WHOIS
Note: |
The WHOIS protocol serves as a standard method for inquiring about the registrants or holders of various Internet resources through specific databases. These resources encompass domain names, blocks of IP addresses, and autonomous systems, among others. Beyond these, the protocol finds application in accessing a broader spectrum of information.
https://book.hacktricks.xyz/pentesting/pentesting-smtp
Entry_2:
Name: Banner Grab
Description: Grab WHOIS Banner
Command: whois -h {IP} -p 43 {Domain_Name} && echo {Domain_Name} | nc -vn {IP} 43
Jifunze AWS hacking kutoka sifuri hadi shujaa na htARTE (Mtaalam wa Timu Nyekundu ya AWS ya HackTricks)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona kampuni yako ikitangazwa kwenye HackTricks au kupakua HackTricks kwa PDF Angalia MIPANGO YA KUJIUNGA!
- Pata bidhaa rasmi za PEASS & HackTricks
- Gundua Familia ya PEASS, mkusanyiko wetu wa NFTs ya kipekee
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @carlospolopm.
- Shiriki mbinu zako za kuhack kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.