5.8 KiB
Google CTF 2018 - Je Tuonane Kucheza Mchezo?
Jifunze kuhusu kudukua AWS kutoka sifuri hadi shujaa na htARTE (Mtaalam wa Timu Nyekundu ya AWS ya HackTricks)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona kampuni yako ikionekana katika HackTricks au kupakua HackTricks kwa PDF Angalia MPANGO WA KUJIUNGA!
- Pata swag rasmi ya PEASS & HackTricks
- Gundua Familia ya PEASS, mkusanyiko wetu wa NFTs ya kipekee
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @carlospolopm.
- Shiriki mbinu zako za kudukua kwa kuwasilisha PR kwa HackTricks na HackTricks Cloud repos za github.
Pakua APK hapa:
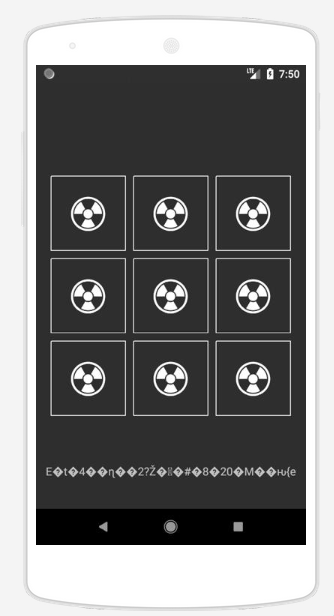
Nitaipakia APK kwenye https://appetize.io/ (akaunti ya bure) kuona jinsi apk inavyofanya kazi:
Inaonekana unahitaji kushinda mara 1000000 ili kupata bendera.
Kwa kufuata hatua kutoka kudukua Android unaweza kudecompile programu ili kupata msimbo wa smali na kusoma msimbo wa Java kwa kutumia jadx.
Kusoma msimbo wa java:
Inaonekana kama kazi ambayo itachapisha bendera ni m().
Mabadiliko ya Smali
Piga m() mara ya kwanza
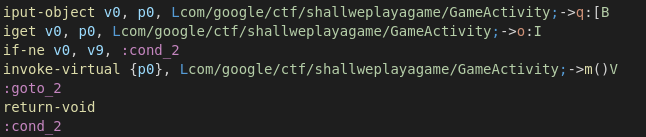
Tufanye programu ipige m() ikiwa kipengele this.o != 1000000, kwa kufanya hivyo, tuibadilishe hali:
if-ne v0, v9, :cond_2
/hive/hacktricks/mobile-pentesting/android-app-pentesting/google-ctf-2018-shall-we-play-a-game.md
Shall we play a game?
Challenge Description
This challenge is about an Android application that simulates a game. The goal is to find a vulnerability in the app and exploit it to gain access to the flag.
Initial Analysis
To start, we need to decompile the APK file using a tool like JADX or apktool. Once decompiled, we can analyze the source code to identify any potential vulnerabilities.
Reverse Engineering
Upon analyzing the source code, we find that the app uses a WebView to load a URL. This is a common vulnerability as it can allow an attacker to execute arbitrary JavaScript code.
Exploiting the Vulnerability
To exploit this vulnerability, we can intercept the network traffic using a tool like Burp Suite. By modifying the response from the server, we can inject our own JavaScript code to execute on the WebView.
Finding the Flag
Once we have control over the WebView, we can use JavaScript to manipulate the app and find the flag. In this case, we can search for the flag by inspecting the DOM elements or by using JavaScript functions to interact with the app's logic.
Conclusion
By identifying and exploiting vulnerabilities in Android applications, we can gain unauthorized access and find sensitive information like flags. It is important for developers to secure their apps and for security professionals to perform thorough penetration testing to identify and fix any vulnerabilities.
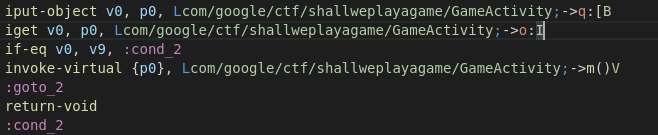
if-eq v0, v9, :cond_2
Fuata hatua za pentest Android ili kurekebisha na kusaini APK. Kisha, pakia kwenye https://appetize.io/ na tuone kinachotokea:
Inaonekana bendera imeandikwa bila kufunguliwa kabisa. Labda kazi ya m() inapaswa kuitwa mara 1000000.
Njia nyingine ya kufanya hii ni kubadilisha maagizo yanayolinganishwa:
Njia nyingine ni badala ya kulinganisha na 1000000, weka thamani kuwa 1 ili this.o ilinganishwe na 1:
Njia ya nne ni kuongeza maagizo ya kuhamisha thamani ya v9(1000000) kwenda v0 (this.o):
Suluhisho
Fanya programu ifanye mzunguko mara 100000 unaposhinda mara ya kwanza. Kufanya hivyo, unahitaji tu kuunda mzunguko wa :goto_6 na kufanya programu iruke hapo ikiwa this.o haifai 100000:
Unahitaji kufanya hivi ndani ya kifaa halisi kwa sababu (sijui kwa nini) hii haifanyi kazi kwenye kifaa cha kusimulizi.
Jifunze kuhusu kudukua AWS kutoka mwanzo hadi mtaalamu na htARTE (HackTricks AWS Red Team Expert)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona kampuni yako inatangazwa kwenye HackTricks au kupakua HackTricks kwa muundo wa PDF Angalia MPANGO WA KUJIUNGA!
- Pata swag rasmi wa PEASS & HackTricks
- Gundua The PEASS Family, mkusanyiko wetu wa NFTs ya kipekee
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @carlospolopm.
- Shiriki mbinu zako za kudukua kwa kuwasilisha PR kwa HackTricks na HackTricks Cloud github repos.