mirror of
https://github.com/carlospolop/hacktricks
synced 2024-12-23 19:43:31 +00:00
5.7 KiB
5.7 KiB
macOS Kernel Extensions
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
- Discover The PEASS Family, our collection of exclusive NFTs
- Get the official PEASS & HackTricks swag
- Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
- Share your hacking tricks by submitting PRs to the hacktricks repo and hacktricks-cloud repo.
Basic Information
Kernel extensions (Kexts) are bundles using .kext extension that are loaded directly into the kernel space of macOS, providing additional functionality to the core operating system.
Requirements
Obviously, this is so powerful, it's complicated to load a kernel extension. These are the requirements of a kernel extension to be loaded:
- Going into recovery mode Kexts need to be allowed to be loaded:
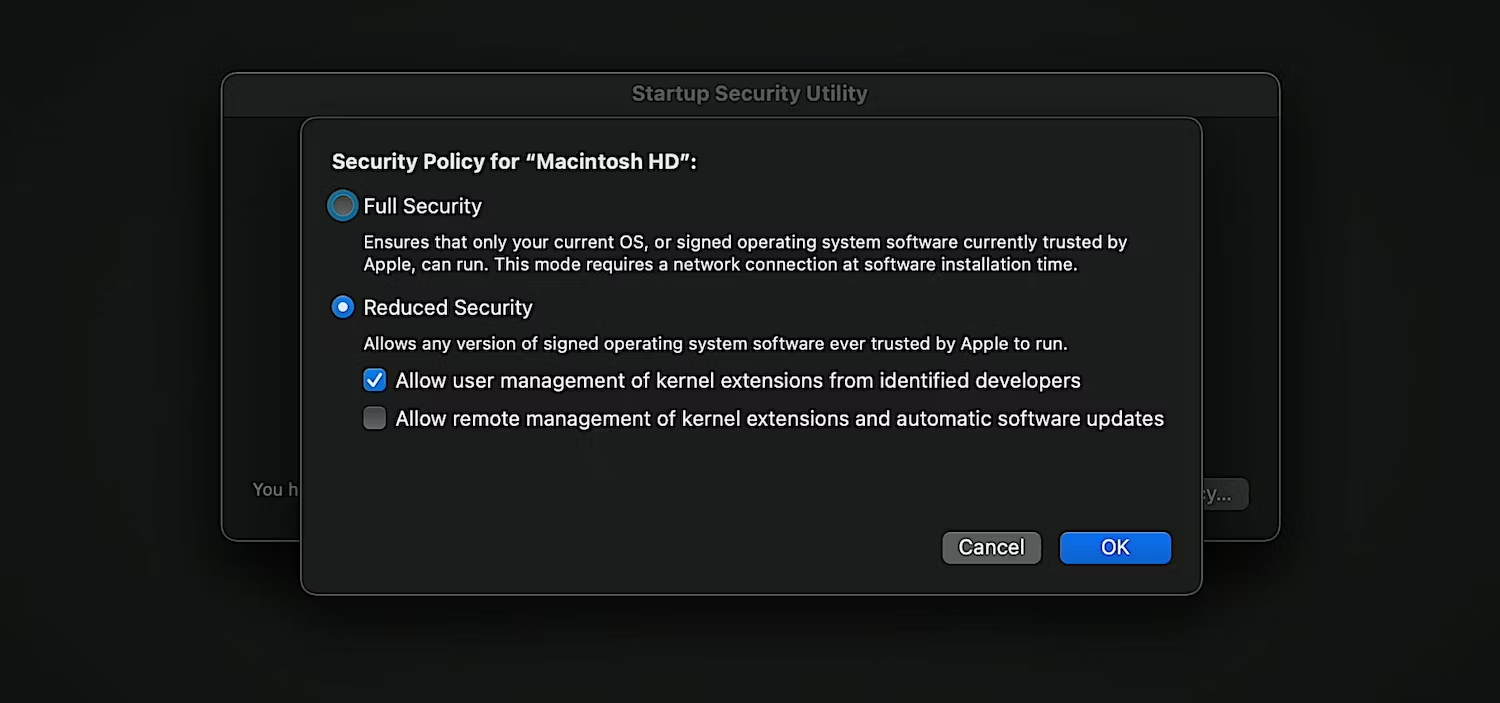
- The Kext must be signed with a kernel code signing certificate, which can only be granted by Apple. Who will be reviewing in detail the company and the reasons why this is needed.
- The Kext also needs to be notarized, Apple will be able to check it for malware.
- Then, the root user is the one that can load the Kext and the files inside the bundle must belong to root.
- During the loading process the bundle must be staged to a rootless protected location: /
Library/StagedExtensions(requires entitlementcom.apple.rootless.storage.KernelExtensionManagement) - Finally, once trying to load it, the user will be prompted for confirmation and if accepted, the computer must reboot to load it.
Loading Process
Back in Catalina it was like this: It's interesting to note that the verification process occurs on userland. However, only applications with the entitlement com.apple.private.security.kext-management can ask the kernel to load an extension: kextcache, kextload, kextutil, kextd, syspolicyd
kextutilcli starts the verification process to load an extension- It'll talk to
kextdsending using a Mach service
- It'll talk to
kextdwill check several things, such as the signature- It'll talk to
syspolicydto check if the extension can be loaded
- It'll talk to
syspolicydasks the user if the extension hasn't be loaded previouslysyspolicydwill indicate the result tokextd
kextdwill finally be able to indicate the kernel to load the extension
If kextd is not available, kextutil can perform the same checks.
References
- https://www.makeuseof.com/how-to-enable-third-party-kernel-extensions-apple-silicon-mac/
- https://www.youtube.com/watch?v=hGKOskSiaQo
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
- Discover The PEASS Family, our collection of exclusive NFTs
- Get the official PEASS & HackTricks swag
- Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
- Share your hacking tricks by submitting PRs to the hacktricks repo and hacktricks-cloud repo.