1.5 KiB
Memory dump analysis
Start searching for malware inside the pcap. Use the tools mentioned in Malware Analysis.
Volatility
The premiere open-source framework for memory dump analysis is Volatility. Volatility is a Python script for parsing memory dumps that were gathered with an external tool or a VMware memory image gathered by pausing the VM. So, given the memory dump file and the relevant "profile" the OS from which the dump was gathered, Volatility can start identifying the structures in the data: running processes, passwords, etc. It is also extensible using plugins for extracting various types of artifact.
From: https://trailofbits.github.io/ctf/forensics/
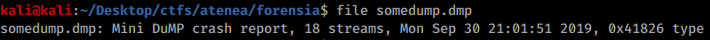
Mini dump crash report
When the dump is small just some KB, maybe a few MB the it's probably a mini dump crash report and not a memory dump.
If you hat Visual Studio installed, you can open this file and bind some basic information like process name, architecture, exception info and modules being executed:
You can also load the exception and see the decompiled instructions
Anyway Visual Studio isn't the best tool to perform a analysis in depth of the dump.
You should open it using IDA or Radare to inspection it in depth.