4.7 KiB
SMTP Smuggling
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
Basic Information
This type of vulnerability was originally discovered in this post were it's explained that It's possible to exploit discrepancies in how the SMTP protocol is interpreted when finalising an email, allowing an attacker to smuggle more emails in the body of the legit one, allowing to impersonate other users of the affected domain (such as admin@outlook.com) bypassing defenses such as SPF.
Why
This is because in the SMTP protocol, the data of the message to be sent in the email is controlled by a user (attacker) which could send specially crafted data abusing differences in parsers that will smuggle extra emails in the receptor. Take a look to this illustrated example from the original post:
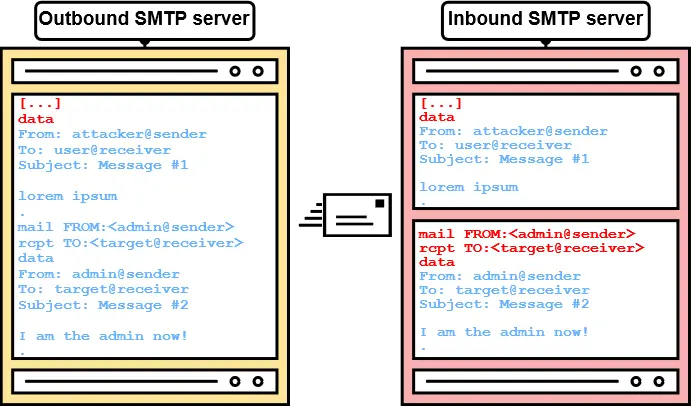
How
In order to exploit this vulnerability an attacker needs to send some data that the Outbound SMPT server thinks that it's just 1 email but the Inbound SMTP server thinks that there are several emails.
The researchers discovered that different Inboud servers considers different characters as the end of the data of the email message that Outbound servers doesn't.
For example, a regular end of the data is \r\n.\r. But if the Inbound SMTP server also supports \n., an attacker could just add that data in his email and start indicating the SMTP commands of a new new ones to smuggle it just like in the previous image.
Ofc, this could only work if the Outbound SMTP server doesn't also treat this data as the end of the message data, because in that case it will see 2 emails instead of just 1, so at the end this is the desynchronization that is being abused in this vulnerability.
Potential desynchronization data:
\n.\n.\r
Also note that the SPF is bypassed because if you smuggle an email from admin@outlook.com from an email from user@outlook.com, the sender is still outlook.com.
References
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.