5 KiB
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.
Tutorial copied from https://infosecwriteups.com/genymotion-xposed-inspeckage-89f0c8decba7
Install Xposed Framework
- Download Xposed Installer APK from here
- Download Xposed Framework zip from here
- Download Inspeckage v2.4 APK from the github repo here
Start the Virtual Device from the menu
Make sure the device is online for adb
Drag and drop the Xposed framework zip file (xposed-vXX-sdkXX-x86.zip) to your virtual device display to flash the device.
Drag and drop Xposed Installer APK (XposedInstaller_*.apk). This should install and launch Xposed Installer application. At this stage, it will display that the Xposed framework is installed but disabled:
Reboot the device with adb reboot command. Do not reboot from Xposed Installer as this will freeze the device.
Launch Xposed installer. It should display “Xposed Framework version XX is active”
Drag and drop the Inspeackage APK (app-release.apk) to your virtual device display to install the app.
After installing, Go to Xposed Installer → Modules→ Activate the Module → reboot via adb
Dynamic Analysis with Inspeckage
After, Successful installing of Inspeckage and Xposed Installer. Now we can hook any application with Inspeackage. To do this follow the below steps
- Launch the Inspeckage Application from the application drawer
- Click on the “Choose target” text and select the target application
3. Then forward VD local-host port to main machine using adb
adb forward tcp:8008 tcp:8008
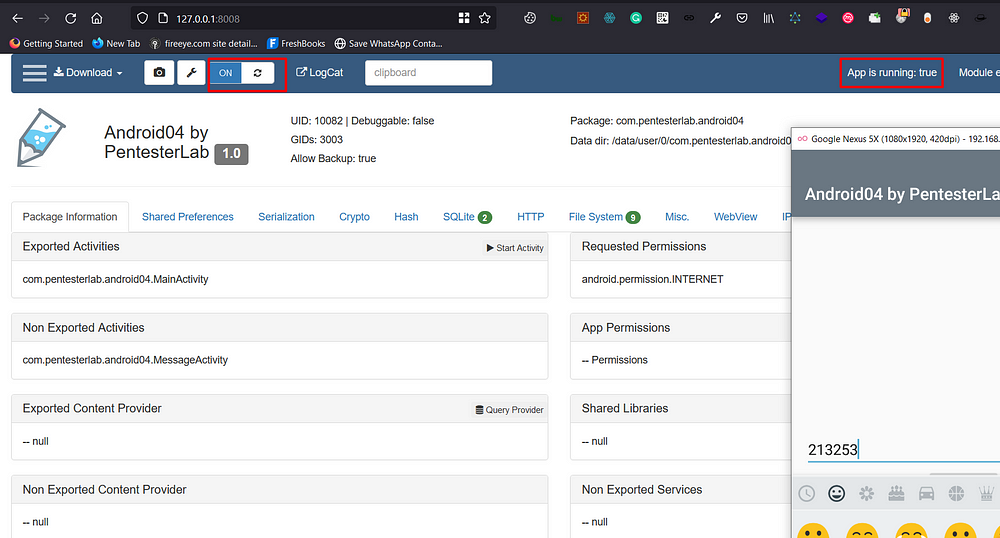
4. Now click on the “LAUNCH APP” Button and then visit http://127.0.0.1:8008
5. Now click Turn On the button to Inspect the app. (make sure App is running: status should be True before you “Turn On”
Support HackTricks and get benefits!
Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
Discover The PEASS Family, our collection of exclusive NFTs
Get the official PEASS & HackTricks swag
Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
Share your hacking tricks submitting PRs to the hacktricks github repo.