8 KiB
1883 - Pentesting MQTT (Mosquitto)
htARTE (HackTricks AWS Red Team Expert) !HackTricks AWS Red Team Expert!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
Basic Information
MQ Telemetry Transport (MQTT) is known as a publish/subscribe messaging protocol that stands out for its extreme simplicity and lightness. This protocol is specifically tailored for environments where devices have limited capabilities and operate over networks that are characterized by low bandwidth, high latency, or unreliable connections. The core objectives of MQTT include minimizing the usage of network bandwidth and reducing the demand on device resources. Additionally, it aims to maintain reliable communication and provide a certain level of delivery assurance. These goals make MQTT exceptionally suitable for the burgeoning field of machine-to-machine (M2M) communication and the Internet of Things (IoT), where it's essential to connect a myriad of devices efficiently. Moreover, MQTT is highly beneficial for mobile applications, where conserving bandwidth and battery life is crucial.
Default port: 1883
PORT STATE SERVICE REASON
1883/tcp open mosquitto version 1.4.8 syn-ack
Inspecting the traffic
CONNECT packet jImej MQTT brokers Daq ghaH CONNACK packet yIlo'. vaj packet Hoch 'ej vItlhutlh return code, 'oH crucial connection status jatlh. return code 0x00 jImej credentials qabHa'lu'chugh, connection successful signifying. vaj, return code 0x05 jImej credentials invalid, connection preventing signal.
vaj, broker credentials invalid vaj connection reject, scenario vItlhutlh:
{
"returnCode": "0x05",
"description": "Connection Refused, not authorized"
}
Brute-Force MQTT
Pentesting MQTT
Authentication is totally optional and even if authentication is being performed, encryption is not used by default (credentials are sent in clear text). MITM attacks can still be executed to steal passwords.
To connect to a MQTT service you can use: https://github.com/bapowell/python-mqtt-client-shell and subscribe yourself to all the topics doing:
Brute-Force MQTT
Pentesting MQTT
Authentication is totally optional and even if authentication is being performed, encryption is not used by default (credentials are sent in clear text). MITM attacks can still be executed to steal passwords.
To connect to a MQTT service you can use: https://github.com/bapowell/python-mqtt-client-shell and subscribe yourself to all the topics doing:
> connect (NOTICE that you need to indicate before this the params of the connection, by default 127.0.0.1:1883)
> subscribe "#" 1
> subscribe "$SYS/#"
https://github.com/akamai-threat-research/mqtt-pwn is a useful resource for MQTT pentesting.
apt-get install mosquitto mosquitto-clients
mosquitto_sub -t 'test/topic' -v #Subscriribe to 'test/topic'
jImej run vItlhutlh code vaj connect MQTT service authentication, subscribe topic vaj ngIm.
#This is a modified version of https://github.com/Warflop/IOT-MQTT-Exploit/blob/master/mqtt.py
import paho.mqtt.client as mqtt
import time
import os
HOST = "127.0.0.1"
PORT = 1883
def on_connect(client, userdata, flags, rc):
client.subscribe('#', qos=1)
client.subscribe('$SYS/#')
def on_message(client, userdata, message):
print('Topic: %s | QOS: %s | Message: %s' % (message.topic, message.qos, message.payload))
def main():
client = mqtt.Client()
client.on_connect = on_connect
client.on_message = on_message
client.connect(HOST, PORT)
client.loop_start()
#time.sleep(10)
#client.loop_stop()
if __name__ == "__main__":
main()
More information
from here: https://morphuslabs.com/hacking-the-iot-with-mqtt-8edaf0d07b9b
The Publish/Subscribe Pattern
The publish/subscribe model is composed of:
- Publisher: publishes a message to one (or many) topic(s) in the broker.
- Subscriber: subscribes to one (or many) topic(s) in the broker and receives all the messages sent from the publisher.
- Broker: routes all the messages from the publishers to the subscribers.
- Topic: consists of one or more levels that are separated by a a forward slash (e.g., /smartshouse/livingroom/temperature).
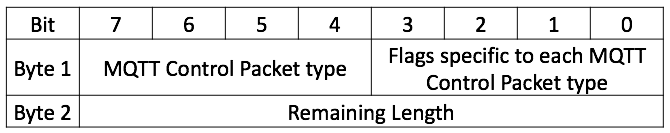
Packet Format
Every MQTT packet contains a fixed header (Figure 02).Figure 02: Fixed Header
Packet Types
- CONNECT (1): Initiated by the client to request a connection to the server.
- CONNACK (2): The server's acknowledgment of a successful connection.
- PUBLISH (3): Used to send a message from the client to the server or vice versa.
- PUBACK (4): Acknowledgment of a PUBLISH packet.
- PUBREC (5): Part of a message delivery protocol ensuring the message is received.
- PUBREL (6): Further assurance in message delivery, indicating a message release.
- PUBCOMP (7): Final part of the message delivery protocol, indicating completion.
- SUBSCRIBE (8): A client's request to listen for messages from a topic.
- SUBACK (9): The server's acknowledgment of a SUBSCRIBE request.
- UNSUBSCRIBE (10): A client's request to stop receiving messages from a topic.
- UNSUBACK (11): The server's response to an UNSUBSCRIBE request.
- PINGREQ (12): A heartbeat message sent by the client.
- PINGRESP (13): Server's response to the heartbeat message.
- DISCONNECT (14): Initiated by the client to terminate the connection.
- Two values, 0 and 15, are marked as reserved and their use is forbidden.
Shodan
port:1883 MQTT
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.