7.4 KiB
27017,27018 - Pentesting MongoDB
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.

Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
Engage with content that delves into the thrill and challenges of hacking
Real-Time Hack News
Keep up-to-date with fast-paced hacking world through real-time news and insights
Latest Announcements
Stay informed with the newest bug bounties launching and crucial platform updates
Join us on Discord and start collaborating with top hackers today!
基本情報
MongoDBは、さまざまな形式のデータを処理するためにドキュメント指向データベースモデルを使用するオープンソースのデータベース管理システムです。ビッグデータ分析やコンテンツ管理などのアプリケーションで、非構造化または半構造化データを管理するための柔軟性とスケーラビリティを提供します。デフォルトポート: 27017, 27018
PORT STATE SERVICE VERSION
27017/tcp open mongodb MongoDB 2.6.9 2.6.9
列挙
手動
from pymongo import MongoClient
client = MongoClient(host, port, username=username, password=password)
client.server_info() #Basic info
#If you have admin access you can obtain more info
admin = client.admin
admin_info = admin.command("serverStatus")
cursor = client.list_databases()
for db in cursor:
print(db)
print(client[db["name"]].list_collection_names())
#If admin access, you could dump the database also
いくつかのMongoDBコマンド:
show dbs
use <db>
show collections
db.<collection>.find() #Dump the collection
db.<collection>.count() #Number of records of the collection
db.current.find({"username":"admin"}) #Find in current db the username admin
自動的
nmap -sV --script "mongo* and default" -p 27017 <IP> #By default all the nmap mongo enumerate scripts are used
Shodan
- すべてのmongodb:
"mongodb server information" - 完全にオープンなmongodbサーバーを検索:
"mongodb server information" -"partially enabled" - 認証が部分的に有効なもののみ:
"mongodb server information" "partially enabled"
Login
デフォルトではmongoはパスワードを必要としません。
Adminは一般的なmongoデータベースです。
mongo <HOST>
mongo <HOST>:<PORT>
mongo <HOST>:<PORT>/<DB>
mongo <database> -u <username> -p '<password>'
nmapスクリプト: mongodb-brute は、認証情報が必要かどうかを確認します。
nmap -n -sV --script mongodb-brute -p 27017 <ip>
ブルートフォース
/opt/bitnami/mongodb/mongodb.conf を見て、認証情報が必要かどうかを確認します:
grep "noauth.*true" /opt/bitnami/mongodb/mongodb.conf | grep -v "^#" #Not needed
grep "auth.*true" /opt/bitnami/mongodb/mongodb.conf | grep -v "^#\|noauth" #Not needed
Mongo Objectid Predict
Example from here.
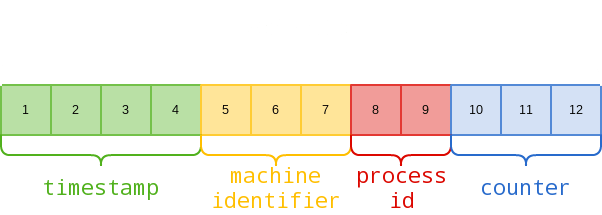
Mongo Object IDs are 12-byte hexadecimal strings:
For example, here’s how we can dissect an actual Object ID returned by an application: 5f2459ac9fa6dc2500314019
- 5f2459ac: 1596217772 in decimal = 2020年7月31日金曜日 17:49:32
- 9fa6dc: マシン識別子
- 2500: プロセスID
- 314019: インクリメンタルカウンター
Of the above elements, machine identifier will remain the same for as long as the database is running the same physical/virtual machine. Process ID will only change if the MongoDB process is restarted. Timestamp will be updated every second. The only challenge in guessing Object IDs by simply incrementing the counter and timestamp values, is the fact that Mongo DB generates Object IDs and assigns Object IDs at a system level.
The tool https://github.com/andresriancho/mongo-objectid-predict, given a starting Object ID (you can create an account and get a starting ID), it sends back about 1000 probable Object IDs that could have possibly been assigned to the next objects, so you just need to bruteforce them.
Post
If you are root you can modify the mongodb.conf file so no credentials are needed (noauth = true) and login without credentials.

Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
Engage with content that delves into the thrill and challenges of hacking
Real-Time Hack News
Keep up-to-date with fast-paced hacking world through real-time news and insights
Latest Announcements
Stay informed with the newest bug bounties launching and crucial platform updates
Join us on Discord and start collaborating with top hackers today!
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.