| .. | ||
| drozer-tutorial | ||
| frida-tutorial | ||
| adb-commands.md | ||
| android-applications-basics.md | ||
| android-burp-suite-settings.md | ||
| android-task-hijacking.md | ||
| apk-decompilers.md | ||
| avd-android-virtual-device.md | ||
| bypass-biometric-authentication-android.md | ||
| content-protocol.md | ||
| exploiting-a-debuggeable-applciation.md | ||
| google-ctf-2018-shall-we-play-a-game.md | ||
| inspeckage-tutorial.md | ||
| install-burp-certificate.md | ||
| intent-injection.md | ||
| make-apk-accept-ca-certificate.md | ||
| manual-deobfuscation.md | ||
| react-native-application.md | ||
| README.md | ||
| reversing-native-libraries.md | ||
| smali-changes.md | ||
| spoofing-your-location-in-play-store.md | ||
| tapjacking.md | ||
| webview-attacks.md | ||
Android Applications Pentesting
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.

Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
ハッキングのスリルと課題に深く掘り下げたコンテンツに参加してください
Real-Time Hack News
リアルタイムのニュースと洞察を通じて、急速に変化するハッキングの世界に遅れずについていきましょう
Latest Announcements
新しいバグバウンティの開始や重要なプラットフォームの更新について最新情報を入手してください
Join us on Discord and start collaborating with top hackers today!
Android Applications Basics
このページを読むことを強くお勧めします。Androidセキュリティに関連する最も重要な部分とAndroidアプリケーションの最も危険なコンポーネントについて知るためです:
{% content-ref url="android-applications-basics.md" %} android-applications-basics.md {% endcontent-ref %}
ADB (Android Debug Bridge)
これは、Androidデバイス(エミュレートまたは物理)に接続するために必要な主なツールです。
ADBは、コンピュータからUSBまたはネットワーク経由でデバイスを制御することを可能にします。このユーティリティは、ファイルのコピー、アプリのインストールとアンインストール、シェルコマンドの実行、データのバックアップ、ログの読み取りなどの機能を提供します。
以下のADB Commandsのリストを確認して、adbの使い方を学んでください。
Smali
時には、アプリケーションコードを修正して隠された情報(おそらくよく難読化されたパスワードやフラグ)にアクセスすることが興味深い場合があります。そのため、apkを逆コンパイルし、コードを修正して再コンパイルすることが興味深いかもしれません。
このチュートリアルでは、APKを逆コンパイルし、Smaliコードを修正して、新しい機能を持つAPKを再コンパイルする方法を学ぶことができます。これは、動的分析中のいくつかのテストの代替手段として非常に役立つ可能性があります。したがって、この可能性を常に念頭に置いておいてください。
Other interesting tricks
- Play Storeでの位置情報の偽装
- APKのダウンロード: https://apps.evozi.com/apk-downloader/, https://apkpure.com/es/, https://www.apkmirror.com/, https://apkcombo.com/es-es/apk-downloader/, https://github.com/kiber-io/apkd
- デバイスからAPKを抽出:
adb shell pm list packages
com.android.insecurebankv2
adb shell pm path com.android.insecurebankv2
package:/data/app/com.android.insecurebankv2-Jnf8pNgwy3QA_U5f-n_4jQ==/base.apk
adb pull /data/app/com.android.insecurebankv2-Jnf8pNgwy3QA_U5f-n_4jQ==/base.apk
- APKEditorを使用して、すべてのスプリットとベースAPKをマージします:
mkdir splits
adb shell pm path com.android.insecurebankv2 | cut -d ':' -f 2 | xargs -n1 -i adb pull {} splits
java -jar ../APKEditor.jar m -i splits/ -o merged.apk
# after merging, you will need to align and sign the apk, personally, I like to use the uberapksigner
java -jar uber-apk-signer.jar -a merged.apk --allowResign -o merged_signed
静的分析
まず、APKを分析するためには、Javaコードを確認するためにデコンパイラを使用する必要があります。
こちらを読んで、利用可能なデコンパイラに関する情報を見つけてください。
興味深い情報を探す
APKの文字列を確認するだけで、パスワード、URL(https://github.com/ndelphit/apkurlgrep)、APIキー、暗号化、Bluetooth UUID、トークン、および興味深いものを検索できます... コード実行のバックドアや認証バックドア(アプリへのハードコーディングされた管理者資格情報)も探してください。
Firebase
FirebaseのURLに特に注意を払い、設定が不適切でないか確認してください。Firebaseとは何か、どのように悪用するかについての詳細情報はこちら。
アプリケーションの基本理解 - Manifest.xml, strings.xml
アプリケーションの**_Manifest.xml****および**strings.xml_**ファイルの検査は、潜在的なセキュリティ脆弱性を明らかにすることができます。これらのファイルはデコンパイラを使用するか、APKファイルの拡張子を.zipに変更してから解凍することでアクセスできます。
Manifest.xmlから特定された脆弱性には以下が含まれます:
- デバッグ可能なアプリケーション:_Manifest.xml_ファイルでデバッグ可能として設定されたアプリケーション(
debuggable="true")は、接続を許可するため、悪用のリスクがあります。デバッグ可能なアプリケーションを見つけて悪用する方法については、デバイス上でのチュートリアルを参照してください。 - バックアップ設定:機密情報を扱うアプリケーションには、
android:allowBackup="false"属性を明示的に設定して、特にUSBデバッグが有効な場合にadbを介した不正なデータバックアップを防ぐ必要があります。 - ネットワークセキュリティ:_res/xml/_内のカスタムネットワークセキュリティ構成(
android:networkSecurityConfig="@xml/network_security_config")は、証明書ピンやHTTPトラフィック設定などのセキュリティ詳細を指定できます。特定のドメインに対してHTTPトラフィックを許可する例があります。 - エクスポートされたアクティビティとサービス:マニフェスト内のエクスポートされたアクティビティとサービスを特定することで、悪用される可能性のあるコンポーネントを明らかにできます。動的テスト中のさらなる分析により、これらのコンポーネントを悪用する方法が明らかになります。
- コンテンツプロバイダーとファイルプロバイダー:公開されたコンテンツプロバイダーは、不正なアクセスやデータの変更を許可する可能性があります。ファイルプロバイダーの構成も注意深く確認する必要があります。
- ブロードキャストレシーバーとURLスキーム:これらのコンポーネントは悪用される可能性があり、特に入力脆弱性に対するURLスキームの管理方法に注意を払う必要があります。
- SDKバージョン:
minSdkVersion、targetSDKVersion、およびmaxSdkVersion属性は、サポートされているAndroidバージョンを示し、セキュリティ上の理由から古い脆弱なAndroidバージョンをサポートしないことの重要性を強調します。
strings.xmlファイルからは、APIキー、カスタムスキーマ、およびその他の開発者ノートなどの機密情報が発見される可能性があり、これらのリソースの注意深いレビューの必要性を強調しています。
タップジャッキング
タップジャッキングは、悪意のある アプリケーションが起動され、被害者アプリケーションの上に位置する攻撃です。被害者アプリを視覚的に隠すと、そのユーザーインターフェースはユーザーを騙してそれと対話させるように設計されており、実際には被害者アプリに対するインタラクションを渡しています。
実際には、ユーザーが被害者アプリで実際にアクションを実行していることを知らないようにしています。
詳細情報は以下で確認できます:
{% content-ref url="tapjacking.md" %} tapjacking.md {% endcontent-ref %}
タスクハイジャック
launchModeがsingleTaskに設定され、taskAffinityが定義されていないアクティビティは、タスクハイジャックに対して脆弱です。これは、アプリケーションがインストールされ、実際のアプリケーションの前に起動されると、実際のアプリケーションのタスクをハイジャックする可能性があることを意味します(つまり、ユーザーは悪意のあるアプリケーションと対話していると思っている)。
詳細情報は以下で確認できます:
{% content-ref url="android-task-hijacking.md" %} android-task-hijacking.md {% endcontent-ref %}
不安定なデータストレージ
内部ストレージ
Androidでは、内部ストレージに保存されたファイルは、作成したアプリのみがアクセスできるように設計されています。このセキュリティ対策はAndroidオペレーティングシステムによって強制され、ほとんどのアプリケーションのセキュリティニーズには一般的に十分です。しかし、開発者は時折、MODE_WORLD_READABLEやMODE_WORLD_WRITABLEのようなモードを利用して、ファイルを異なるアプリケーション間で共有できるようにします。しかし、これらのモードは、潜在的に悪意のある他のアプリケーションによるこれらのファイルへのアクセスを制限しません。
- 静的分析:
MODE_WORLD_READABLEおよびMODE_WORLD_WRITABLEの使用が注意深く精査されることを確認してください。これらのモードは、意図しないまたは不正なアクセスにファイルをさらす可能性があります。
- 動的分析:
- アプリによって作成されたファイルに設定された権限を確認してください。特に、ファイルが全世界に対して読み取りまたは書き込み可能に設定されているかどうかを確認してください。これは重大なセキュリティリスクを引き起こす可能性があり、デバイスにインストールされた任意のアプリケーションが、出所や意図に関係なく、これらのファイルを読み取ったり変更したりできるようになります。
外部ストレージ
外部ストレージ上のファイルを扱う際には、いくつかの注意が必要です:
- アクセス可能性:
- 外部ストレージ上のファイルは全世界に対して読み取りおよび書き込み可能です。つまり、任意のアプリケーションやユーザーがこれらのファイルにアクセスできます。
- セキュリティの懸念:
- アクセスの容易さを考慮して、機密情報を外部ストレージに保存しないことをお勧めします。
- 外部ストレージは取り外し可能であり、任意のアプリケーションによってアクセスされる可能性があるため、セキュリティが低下します。
- 外部ストレージからのデータ処理:
- 外部ストレージから取得したデータに対しては常に入力検証を行ってください。これは、データが信頼できないソースからのものであるため、重要です。
- 動的読み込みのために外部ストレージに実行可能ファイルやクラスファイルを保存することは強く推奨されません。
- アプリケーションが外部ストレージから実行可能ファイルを取得する必要がある場合、これらのファイルが署名され、暗号的に検証されていることを確認してください。このステップは、アプリケーションのセキュリティの整合性を維持するために重要です。
外部ストレージは/storage/emulated/0、/sdcard、/mnt/sdcardでアクセス可能です。
{% hint style="info" %} Android 4.4(API 17)以降、SDカードには、アプリが特定のアプリ用のディレクトリにのみアクセスできるように制限するディレクトリ構造があります。これにより、悪意のあるアプリケーションが他のアプリのファイルに対して読み取りまたは書き込みアクセスを得ることが防止されます。 {% endhint %}
平文で保存された機密データ
- 共有設定:Androidは各アプリケーションが
/data/data/<packagename>/shared_prefs/パスにXMLファイルを簡単に保存できるようにしており、時にはそのフォルダ内に平文で機密情報が見つかることがあります。 - データベース:Androidは各アプリケーションが
/data/data/<packagename>/databases/パスにSQLiteデータベースを簡単に保存できるようにしており、時にはそのフォルダ内に平文で機密情報が見つかることがあります。
壊れたTLS
すべての証明書を受け入れる
何らかの理由で、開発者は時々、ホスト名が以下のようなコード行と一致しない場合でも、すべての証明書を受け入れます:
SSLSocketFactory sf = new cc(trustStore);
sf.setHostnameVerifier(SSLSocketFactory.ALLOW_ALL_HOSTNAME_VERIFIER);
A good way to test this is to try to capture the traffic using some proxy like Burp without authorising Burp CA inside the device. Also, you can generate with Burp a certificate for a different hostname and use it.
Broken Cryptography
Poor Key Management Processes
一部の開発者は、機密データをローカルストレージに保存し、コード内にハードコーディングされた/予測可能なキーで暗号化します。これは行うべきではなく、リバースエンジニアリングにより攻撃者が機密情報を抽出できる可能性があります。
Use of Insecure and/or Deprecated Algorithms
開発者は、認証チェック、データの保存または送信を行うために非推奨のアルゴリズムを使用すべきではありません。これらのアルゴリズムには、RC4、MD4、MD5、SHA1などがあります。例えば、パスワードを保存するためにハッシュが使用される場合、ソルトを使用したハッシュのブルートフォース耐性が必要です。
Other checks
- APKを難読化することを推奨します。これにより、攻撃者のリバースエンジニアリング作業が困難になります。
- アプリが機密性が高い場合(銀行アプリなど)、モバイルがルート化されているかどうかを確認する独自のチェックを実行し、適切に対処する必要があります。
- アプリが機密性が高い場合(銀行アプリなど)、エミュレーターが使用されているかどうかを確認する必要があります。
- アプリが機密性が高い場合(銀行アプリなど)、実行前に自身の整合性を確認し、変更されていないかを確認する必要があります。
- APKiDを使用して、APKをビルドするために使用されたコンパイラ/パッカー/難読化ツールを確認します。
React Native Application
Read the following page to learn how to easily access javascript code of React applications:
{% content-ref url="react-native-application.md" %} react-native-application.md {% endcontent-ref %}
Xamarin Applications
Read the following page to learn how to easily access C# code of a xamarin applications:
{% content-ref url="../xamarin-apps.md" %} xamarin-apps.md {% endcontent-ref %}
Superpacked Applications
According to this blog post superpacked is a Meta algorithm that compress the content of an application into a single file. The blog talks about the possibility of creating an app that decompress these kind of apps... and a faster way which involves to execute the application and gather the decompressed files from the filesystem.
Automated Static Code Analysis
The tool mariana-trench is capable of finding vulnerabilities by scanning the code of the application. This tool contains a series of known sources (that indicates to the tool the places where the input is controlled by the user), sinks (which indicates to the tool dangerous places where malicious user input could cause damages) and rules. These rules indicates the combination of sources-sinks that indicates a vulnerability.
With this knowledge, mariana-trench will review the code and find possible vulnerabilities on it.
Secrets leaked
An application may contain secrets (API keys, passwords, hidden urls, subdomains...) inside of it that you might be able to discover. You could us a tool such as https://github.com/dwisiswant0/apkleaks
Bypass Biometric Authentication
{% content-ref url="bypass-biometric-authentication-android.md" %} bypass-biometric-authentication-android.md {% endcontent-ref %}
Other interesting functions
- Code execution:
Runtime.exec(), ProcessBuilder(), native code:system() - Send SMSs:
sendTextMessage, sendMultipartTestMessage - Native functions declared as
native:public native, System.loadLibrary, System.load - Read this to learn how to reverse native functions
Other tricks
{% content-ref url="content-protocol.md" %} content-protocol.md {% endcontent-ref %}

Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
Engage with content that delves into the thrill and challenges of hacking
Real-Time Hack News
Keep up-to-date with fast-paced hacking world through real-time news and insights
Latest Announcements
Stay informed with the newest bug bounties launching and crucial platform updates
Join us on Discord and start collaborating with top hackers today!
Dynamic Analysis
First of all, you need an environment where you can install the application and all the environment (Burp CA cert, Drozer and Frida mainly). Therefore, a rooted device (emulated or not) is extremely recommended.
Online Dynamic analysis
You can create a free account in: https://appetize.io/. This platform allows you to upload and execute APKs, so it is useful to see how an apk is behaving.
You can even see the logs of your application in the web and connect through adb.
Thanks to the ADB connection you can use Drozer and Frida inside the emulators.
Local Dynamic Analysis
Using an emulator
- Android Studio (You can create x86 and arm devices, and according to this latest x86 versions support ARM libraries without needing an slow arm emulator).
- Learn to set it up in this page:
{% content-ref url="avd-android-virtual-device.md" %} avd-android-virtual-device.md {% endcontent-ref %}
- Genymotion (Free version: Personal Edition, you need to create an account. It's recommend to download the version WITH VirtualBox to avoid potential errors.)
- Nox (Free, but it doesn't support Frida or Drozer).
{% hint style="info" %} When creating a new emulator on any platform remember that the bigger the screen is, the slower the emulator will run. So select small screens if possible. {% endhint %}
To install google services (like AppStore) in Genymotion you need to click on the red marked button of the following image:
Also, notice that in the configuration of the Android VM in Genymotion you can select Bridge Network mode (this will be useful if you will be connecting to the Android VM from a different VM with the tools).
Use a physical device
You need to activate the debugging options and it will be cool if you can root it:
- Settings.
- (FromAndroid 8.0) Select System.
- Select About phone.
- Press Build number 7 times.
- Go back and you will find the Developer options.
Once you have installed the application, the first thing you should do is to try it and investigate what does it do, how does it work and get comfortable with it.
I will suggest to perform this initial dynamic analysis using MobSF dynamic analysis + pidcat, so we will be able to learn how the application works while MobSF captures a lot of interesting data you can review later on.
Unintended Data Leakage
Logging
開発者は、デバッグ情報を公開することに注意すべきです。これは機密データの漏洩につながる可能性があります。アプリケーションログを監視して機密情報を特定し保護するために、pidcatとadb logcatを推奨します。Pidcatは使いやすさと可読性のために好まれます。
{% hint style="warning" %}
Android 4.0以降、アプリケーションは自分自身のログにのみアクセスできることに注意してください。したがって、アプリケーションは他のアプリのログにアクセスできません。
それでも、機密情報をログに記録しないことを推奨します。
{% endhint %}
Copy/Paste Buffer Caching
Androidのクリップボードベースのフレームワークは、アプリ内でのコピー&ペースト機能を可能にしますが、他のアプリケーションがクリップボードにアクセスできるため、機密データが漏洩するリスクがあります。クレジットカードの詳細など、アプリケーションの機密セクションではコピー/ペースト機能を無効にすることが重要です。
Crash Logs
アプリケーションがクラッシュし、ログを保存する場合、これらのログは攻撃者に役立つ可能性があります。特にアプリケーションがリバースエンジニアリングできない場合はそうです。このリスクを軽減するために、クラッシュ時にログを記録しないようにし、ログをネットワーク経由で送信する必要がある場合は、SSLチャネルを介して送信されることを確認してください。
ペンテスターとして、これらのログを確認することをお勧めします。
Analytics Data Sent To 3rd Parties
アプリケーションは、Google Adsenseなどのサービスを統合することが多く、開発者による不適切な実装により機密データが漏洩する可能性があります。潜在的なデータ漏洩を特定するために、アプリケーションのトラフィックを傍受し、第三者サービスに送信される機密情報がないかを確認することをお勧めします。
SQLite DBs
ほとんどのアプリケーションは、情報を保存するために内部SQLiteデータベースを使用します。ペンテスト中に作成されたデータベース、テーブルとカラムの名前、保存されたすべてのデータを確認してください。機密情報を見つけることができるかもしれません(これは脆弱性となります)。
データベースは/data/data/the.package.name/databasesに配置されるべきです。例えば/data/data/com.mwr.example.sieve/databases
データベースが機密情報を保存しており、暗号化されているが、アプリケーション内にパスワードが見つかる場合、それでも脆弱性です。
.tablesを使用してテーブルを列挙し、.schema <table_name>を使用してテーブルのカラムを列挙します。
Drozer (Exploit Activities, Content Providers and Services)
From Drozer Docs: Drozer allows you to assume the role of an Android app and interact with other apps. It can do anything that an installed application can do, such as make use of Android’s Inter-Process Communication (IPC) mechanism and interact with the underlying operating system. .
Drozer is s useful tool to exploit exported activities, exported services and Content Providers as you will learn in the following sections.
Exploiting exported Activities
Read this if you want to refresh what is an Android Activity.
Also remember that the code of an activity starts in the onCreate method.
Authorisation bypass
Activityがエクスポートされると、外部アプリからその画面を呼び出すことができます。したがって、機密情報を含むActivityがエクスポートされている場合、認証メカニズムをバイパスしてアクセスできる可能性があります。
Learn how to exploit exported activities with Drozer.
You can also start an exported activity from adb:
- PackageName is com.example.demo
- Exported ActivityName is com.example.test.MainActivity
adb shell am start -n com.example.demo/com.example.test.MainActivity
注意: MobSFは、アクティビティのandroid:launchModeにおける_singleTask/singleInstance_の使用を悪意のあるものとして検出しますが、これによると、これは古いバージョン(APIバージョン< 21)でのみ危険なようです。
{% hint style="info" %} 認可バイパスは常に脆弱性ではないことに注意してください。バイパスの動作とどの情報が公開されているかによります。 {% endhint %}
機密情報の漏洩
アクティビティは結果を返すこともできます。もし、**setResult**メソッドを呼び出し、機密情報を返すエクスポートされた保護されていないアクティビティを見つけることができれば、機密情報の漏洩があります。
タップジャッキング
タップジャッキングが防止されていない場合、エクスポートされたアクティビティを悪用してユーザーに予期しないアクションを実行させることができます。タップジャッキングについての詳細は、こちらのリンクを参照してください。
コンテンツプロバイダーの悪用 - 機密情報へのアクセスと操作
コンテンツプロバイダーとは何かを再確認したい場合は、こちらをお読みください。
コンテンツプロバイダーは基本的にデータを共有するために使用されます。アプリに利用可能なコンテンツプロバイダーがある場合、そこから機密データを抽出できるかもしれません。また、SQLインジェクションやパストラバーサルの可能性をテストすることも興味深いです。これらは脆弱である可能性があります。
Drozerを使用してコンテンツプロバイダーを悪用する方法を学びましょう。
サービスの悪用
サービスとは何かを再確認したい場合は、こちらをお読みください。
サービスのアクションはonStartCommandメソッドで始まることを覚えておいてください。
サービスは基本的にデータを受信し、処理し、応答(またはしない)を返すことができるものです。したがって、アプリケーションがいくつかのサービスをエクスポートしている場合は、コードを確認して何をしているのかを理解し、機密情報を抽出するために動的にテストする必要があります。認証手段をバイパスすることも...
Drozerを使用してサービスを悪用する方法を学びましょう。
ブロードキャストレシーバーの悪用
ブロードキャストレシーバーとは何かを再確認したい場合は、こちらをお読みください。
ブロードキャストレシーバーのアクションはonReceiveメソッドで始まることを覚えておいてください。
ブロードキャストレシーバーは、特定のメッセージを待機しています。レシーバーがメッセージをどのように処理するかによって、脆弱である可能性があります。
Drozerを使用してブロードキャストレシーバーを悪用する方法を学びましょう。
スキーム/ディープリンクの悪用
手動でディープリンクを探すことができ、MobSFのようなツールやこのスクリプトを使用できます。
adbやブラウザを使用して宣言されたスキームを開くことができます:
{% code overflow="wrap" %}
adb shell am start -a android.intent.action.VIEW -d "scheme://hostname/path?param=value" [your.package.name]
{% endcode %}
パッケージ名を省略することができ、モバイルは自動的にそのリンクを開くべきアプリを呼び出します。
{% code overflow="wrap" %}
<!-- Browser regular link -->
<a href="scheme://hostname/path?param=value">Click me</a>
<!-- fallback in your url you could try the intent url -->
<a href="intent://hostname#Intent;scheme=scheme;package=your.package.name;S.browser_fallback_url=http%3A%2F%2Fwww.example.com;end">with alternative</a>
{% endcode %}
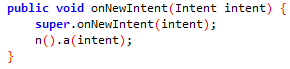
実行されるコード
アプリで実行されるコードを見つけるために、ディープリンクによって呼び出されるアクティビティに移動し、関数**onNewIntent**を検索します。
機密情報
ディープリンクを見つけるたびに、URLパラメータを介して機密データ(パスワードなど)を受信していないか確認してください。他のアプリケーションがディープリンクを偽装してそのデータを盗む可能性があります!
パス内のパラメータ
URLのパス内にパラメータを使用しているディープリンクがあるかどうかも確認する必要があります。例えば: https://api.example.com/v1/users/{username} の場合、パストラバーサルを強制して、example://app/users?username=../../unwanted-endpoint%3fparam=valueのようなものにアクセスできます。
アプリケーション内で正しいエンドポイントを見つけた場合、オープンリダイレクト(パスの一部がドメイン名として使用される場合)、アカウント乗っ取り(CSRFトークンなしでユーザーの詳細を変更でき、脆弱なエンドポイントが正しいメソッドを使用している場合)、およびその他の脆弱性を引き起こす可能性があります。詳細はこちらを参照してください。
さらなる例
リンクに関する興味深いバグバウンティレポート(/.well-known/assetlinks.json)。
トランスポート層の検査と検証の失敗
- 証明書はAndroidアプリケーションによって常に適切に検査されるわけではありません。これらのアプリケーションは警告を見落とし、自己署名証明書を受け入れたり、場合によってはHTTP接続に戻ったりすることが一般的です。
- SSL/TLSハンドシェイク中の交渉は時々弱く、安全でない暗号スイートを使用しています。この脆弱性により、接続が中間者攻撃(MITM)に対して脆弱になり、攻撃者がデータを復号化できるようになります。
- 機密情報の漏洩は、アプリケーションが安全なチャネルを使用して認証するが、他のトランザクションのために非安全なチャネルで通信する場合にリスクがあります。このアプローチは、セッションクッキーやユーザーの詳細などの機密データを悪意のあるエンティティによる傍受から保護できません。
証明書の検証
証明書の検証に焦点を当てます。サーバーの証明書の整合性を確認することは、セキュリティを強化するために重要です。これは、安全でないTLS構成や暗号化されていないチャネルを介して機密データを送信することが重大なリスクをもたらすため、重要です。サーバー証明書の検証と脆弱性への対処に関する詳細な手順は、このリソースで包括的に説明されています。
SSLピンニング
SSLピンニングは、アプリケーションがサーバーの証明書をアプリケーション内に保存された既知のコピーと照合するセキュリティ対策です。この方法は、MITM攻撃を防ぐために不可欠です。機密情報を扱うアプリケーションには、SSLピンニングの実装が強く推奨されます。
トラフィックの検査
HTTPトラフィックを検査するには、プロキシツールの証明書をインストールする必要があります(例:Burp)。この証明書をインストールしないと、暗号化されたトラフィックはプロキシを通じて表示されない可能性があります。カスタムCA証明書のインストールに関するガイドは、こちらをクリックしてください。
APIレベル24以上をターゲットとするアプリケーションは、プロキシのCA証明書を受け入れるためにネットワークセキュリティ構成を変更する必要があります。このステップは、暗号化されたトラフィックを検査するために重要です。ネットワークセキュリティ構成の変更に関する指示は、このチュートリアルを参照してください。
SSLピンニングのバイパス
SSLピンニングが実装されている場合、HTTPSトラフィックを検査するためにそれをバイパスする必要があります。この目的のためにさまざまな方法があります:
- 自動的にapkを修正してSSLピンニングをバイパスするには、apk-mitmを使用します。このオプションの最大の利点は、SSLピンニングをバイパスするためにrootが必要ないことですが、アプリケーションを削除して新しいものを再インストールする必要があり、これが常に機能するわけではありません。
- Frida(下記で説明)を使用してこの保護をバイパスすることもできます。Burp+Frida+Genymotionを使用するためのガイドはこちらです:https://spenkk.github.io/bugbounty/Configuring-Frida-with-Burp-and-GenyMotion-to-bypass-SSL-Pinning/
- objectionを使用してSSLピンニングを自動的にバイパスすることもできます:
objection --gadget com.package.app explore --startup-command "android sslpinning disable" - MobSF動的分析を使用してSSLピンニングを自動的にバイパスすることも試みることができます(下記で説明)。
- まだキャプチャしていないトラフィックがあると思われる場合は、iptablesを使用してトラフィックをburpに転送することを試みることができます。このブログを読んでください:https://infosecwriteups.com/bypass-ssl-pinning-with-ip-forwarding-iptables-568171b52b62
一般的なWeb脆弱性の検索
アプリケーション内で一般的なWeb脆弱性を検索することも重要です。これらの脆弱性を特定し、軽減するための詳細な情報はこの要約の範囲を超えていますが、他の場所で広範にカバーされています。
Frida
Fridaは、開発者、リバースエンジニア、セキュリティ研究者のための動的インスツルメンテーションツールキットです。
実行中のアプリケーションにアクセスし、実行時にメソッドをフックして動作を変更したり、値を変更したり、値を抽出したり、異なるコードを実行したりできます...
Androidアプリケーションをペンテストする場合は、Fridaの使い方を知っておく必要があります。
- Fridaの使い方を学ぶ:Fridaチュートリアル
- Fridaでのアクション用の「GUI」:https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security
- OjectionはFridaの使用を自動化するのに最適です:https://github.com/sensepost/objection , https://github.com/dpnishant/appmon
- ここで素晴らしいFridaスクリプトを見つけることができます:https://codeshare.frida.re/
- https://erfur.github.io/blog/dev/code-injection-without-ptraceに示されているようにFridaを読み込んで、アンチデバッグ/アンチFridaメカニズムをバイパスしてみてください(ツールlinjector)。
メモリダンプ - Fridump
アプリケーションがパスワードやニーモニックのような機密情報を保存していないか確認してください。
Fridump3を使用して、アプリのメモリをダンプできます:
# With PID
python3 fridump3.py -u <PID>
# With name
frida-ps -Uai
python3 fridump3.py -u "<Name>"
これは./dumpフォルダーにメモリをダンプします。そこで、次のようにgrepできます:
{% code overflow="wrap" %}
strings * | grep -E "^[a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+$"
{% endcode %}
キーストア内の機密データ
Androidでは、キーストアは機密データを保存するのに最適な場所ですが、十分な権限があればアクセスすることが可能です。アプリケーションはここに平文で機密データを保存する傾向があるため、ペンテストはそれを確認する必要があります。ルートユーザーやデバイスに物理的にアクセスできる誰かがこのデータを盗むことができるかもしれません。
アプリがキーストアにデータを保存していても、そのデータは暗号化されているべきです。
キーストア内のデータにアクセスするには、次のFridaスクリプトを使用できます: https://github.com/WithSecureLabs/android-keystore-audit/blob/master/frida-scripts/tracer-cipher.js
frida -U -f com.example.app -l frida-scripts/tracer-cipher.js
指紋/生体認証バイパス
次のFridaスクリプトを使用することで、Androidアプリケーションが特定の機密領域を保護するために実行している指紋認証をバイパスすることが可能です:
{% code overflow="wrap" %}
frida --codeshare krapgras/android-biometric-bypass-update-android-11 -U -f <app.package>
{% endcode %}
バックグラウンド画像
アプリケーションをバックグラウンドに置くと、Androidはアプリケーションのスナップショットを保存します。これにより、フォアグラウンドに復帰したときに、アプリがより早く読み込まれているように見えます。
しかし、このスナップショットに機密情報が含まれている場合、スナップショットにアクセスできる人はその情報を盗む可能性があります(アクセスするにはrootが必要です)。
スナップショットは通常、**/data/system_ce/0/snapshots**の周辺に保存されます。
Androidは、FLAG_SECUREレイアウトパラメータを設定することでスクリーンショットのキャプチャを防ぐ方法を提供します。このフラグを使用すると、ウィンドウの内容は安全と見なされ、スクリーンショットに表示されたり、非安全なディスプレイで表示されたりすることを防ぎます。
getWindow().setFlags(LayoutParams.FLAG_SECURE, LayoutParams.FLAG_SECURE);
Android Application Analyzer
このツールは、動的分析中に異なるツールを管理するのに役立ちます: https://github.com/NotSoSecure/android_application_analyzer
Intent Injection
開発者は、これらのインテントを処理し、startActivity(...)やsendBroadcast(...)などのメソッドに渡すプロキシコンポーネント(アクティビティ、サービス、ブロードキャストレシーバーなど)を作成することがよくありますが、これはリスクを伴います。
危険は、攻撃者がこれらのインテントを誤って誘導することによって、非エクスポートアプリコンポーネントをトリガーしたり、機密コンテンツプロバイダーにアクセスしたりできることにあります。注目すべき例は、WebViewコンポーネントがURLをIntentオブジェクトに変換し、Intent.parseUri(...)を介して実行することで、悪意のあるインテント注入を引き起こす可能性があることです。
Essential Takeaways
- Intent Injectionは、ウェブのオープンリダイレクト問題に似ています。
- 脆弱性は、
Intentオブジェクトをエクストラとして渡すことに関与し、これが不安全な操作を実行するためにリダイレクトされる可能性があります。 - 攻撃者に非エクスポートコンポーネントやコンテンツプロバイダーを露出させる可能性があります。
WebViewのURLからIntentへの変換は、意図しないアクションを促進する可能性があります。
Android Client Side Injections and others
おそらく、あなたはウェブからこの種の脆弱性について知っているでしょう。Androidアプリケーションにおいては、これらの脆弱性に特に注意する必要があります:
- SQL Injection: 動的クエリやコンテンツプロバイダーを扱う際は、パラメータ化されたクエリを使用していることを確認してください。
- JavaScript Injection (XSS): すべてのWebViewに対してJavaScriptとプラグインのサポートが無効になっていることを確認してください(デフォルトで無効)。 More info here.
- Local File Inclusion: WebViewはファイルシステムへのアクセスを無効にする必要があります(デフォルトで有効) -
(webview.getSettings().setAllowFileAccess(false);)。 More info here. - Eternal cookies: Androidアプリケーションがセッションを終了するとき、クッキーが取り消されない場合や、ディスクに保存されることがあります。
- Secure Flag in cookies

経験豊富なハッカーやバグバウンティハンターとコミュニケーションを取るために、HackenProof Discordサーバーに参加してください!
Hacking Insights
ハッキングのスリルと課題に深く掘り下げたコンテンツに参加してください。
Real-Time Hack News
リアルタイムのニュースと洞察を通じて、急速に変化するハッキングの世界に遅れずについていきましょう。
Latest Announcements
新しいバグバウンティの開始や重要なプラットフォームの更新について最新情報を入手してください。
Join us on Discord and start collaborating with top hackers today!
Automatic Analysis
MobSF
Static analysis
アプリケーションの脆弱性評価を行うための素晴らしいウェブベースのフロントエンドを使用します。動的分析も実行できますが、環境を準備する必要があります。
docker pull opensecurity/mobile-security-framework-mobsf
docker run -it -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
注意してください、MobSFはAndroid(apk)、IOS(ipa)、およびWindows(apx)アプリケーションを分析できます(WindowsアプリケーションはWindowsホストにインストールされたMobSFから分析する必要があります)。
また、AndroidまたはIOSアプリのソースコードでZIPファイルを作成すると(アプリケーションのルートフォルダーに移動し、すべてを選択してZIPファイルを作成)、それも分析できます。
MobSFはまた、diff/Compare分析を行い、VirusTotalを統合することも可能です(_MobSF/settings.py_でAPIキーを設定し、有効にする必要があります:VT_ENABLED = TRUE VT_API_KEY = <Your API key> VT_UPLOAD = TRUE)。VT_UPLOADをFalseに設定すると、ハッシュがアップロードされ、ファイルではなくなります。
MobSFによる支援された動的分析
MobSFはAndroidにおける動的分析にも非常に役立ちますが、その場合はホストにMobSFとgenymotionをインストールする必要があります(VMやDockerでは動作しません)。注:最初にgenymotionでVMを起動し、**その後MobSFを起動する必要があります。
MobSF動的アナライザーは以下を行うことができます:
- アプリケーションデータをダンプ(URL、ログ、クリップボード、あなたが作成したスクリーンショット、"Exported Activity Tester"によって作成されたスクリーンショット、メール、SQLiteデータベース、XMLファイル、その他の作成されたファイル)。これらはすべて自動的に行われますが、スクリーンショットは、スクリーンショットを取得したいときに押す必要があります。または、すべてのエクスポートされたアクティビティのスクリーンショットを取得するには"Exported Activity Tester"を押す必要があります。
- HTTPSトラフィックをキャプチャ
- Fridaを使用してランタイムの情報を取得
Androidのバージョン > 5では、Fridaを自動的に起動し、トラフィックをキャプチャするためにグローバルプロキシ設定を行います。テストされたアプリケーションからのトラフィックのみをキャプチャします。
Frida
デフォルトでは、SSLピンニング、ルート検出、およびデバッガ検出をバイパスし、興味深いAPIを監視するためにいくつかのFridaスクリプトを使用します。
MobSFはまた、エクスポートされたアクティビティを呼び出し、それらのスクリーンショットを取得し、レポート用に保存することもできます。
動的テストを開始するには、緑のボタン"Start Instrumentation"を押します。"Frida Live Logs"を押すと、Fridaスクリプトによって生成されたログを見ることができ、"Live API Monitor"を押すと、フックされたメソッドへのすべての呼び出し、渡された引数、および返された値を見ることができます(これは"Start Instrumentation"を押した後に表示されます)。
MobSFはまた、独自のFridaスクリプトを読み込むこともできます(Fridaスクリプトの結果をMobSFに送信するには、send()関数を使用します)。また、読み込むことができるいくつかの事前に書かれたスクリプトもあります(MobSF/DynamicAnalyzer/tools/frida_scripts/others/に追加できます)、ただ選択し、"Load"を押し、"Start Instrumentation"を押します(そのスクリプトのログは"Frida Live Logs"内で見ることができます)。
さらに、いくつかの補助的なFrida機能があります:
- 読み込まれたクラスを列挙:すべての読み込まれたクラスを印刷します
- 文字列をキャプチャ:アプリケーションを使用中にキャプチャされたすべての文字列を印刷します(非常に騒がしい)
- 文字列比較をキャプチャ:非常に役立つ可能性があります。比較されている2つの文字列と結果がTrueかFalseかを表示します。
- クラスメソッドを列挙:クラス名(例:"java.io.File")を入力すると、そのクラスのすべてのメソッドを印刷します。
- クラスパターンを検索:パターンでクラスを検索
- クラスメソッドをトレース:クラス全体をトレース(そのクラスのすべてのメソッドの入力と出力を確認)。デフォルトでは、MobSFは興味深いAndroid APIメソッドをいくつかトレースします。
使用したい補助モジュールを選択したら、"Start Intrumentation"を押す必要があり、すべての出力は"Frida Live Logs"に表示されます。
シェル
Mobsfはまた、動的分析ページの下部にいくつかのadbコマンド、MobSFコマンド、および一般的なシェルコマンドを持つシェルを提供します。いくつかの興味深いコマンド:
help
shell ls
activities
exported_activities
services
receivers
HTTPツール
httpトラフィックがキャプチャされると、"HTTP(S) Traffic"の下にキャプチャされたトラフィックの醜いビューが表示されるか、"Start HTTPTools"の緑のボタンでより良いビューが表示されます。2番目のオプションから、captured requestsをBurpやOwasp ZAPのようなproxiesにsendできます。
そのためには、Burpを起動 --> Interceptをオフにする --> MobSB HTTPToolsでリクエストを選択 --> "Send to Fuzzer"を押す --> プロキシアドレスを選択 (http://127.0.0.1:8080\)。
MobSFで動的分析が完了したら、"Start Web API Fuzzer"を押してfuzz http requestsを行い、脆弱性を探します。
{% hint style="info" %} MobSFで動的分析を実行した後、プロキシ設定が誤って構成される可能性があり、GUIから修正できなくなることがあります。プロキシ設定を修正するには、次の手順を実行します:
adb shell settings put global http_proxy :0
{% endhint %}
Assisted Dynamic Analysis with Inspeckage
ツールはInspeckageから入手できます。
このツールは、動的分析を実行している間にアプリケーションで何が起こっているかを知るためにいくつかのHooksを使用します。
Yaazhini
これはGUIを使用した静的分析を実行するための優れたツールです。
Qark
このツールは、ソースコードまたはパッケージ化されたAPKのいずれかで、いくつかのセキュリティ関連のAndroidアプリケーションの脆弱性を探すように設計されています。このツールは、見つかった脆弱性のいくつかを悪用するための**「Proof-of-Concept」デプロイ可能APKとADBコマンドを作成することも可能です**(公開されたアクティビティ、インテント、タップジャッキング...)。Drozerと同様に、テストデバイスをルート化する必要はありません。
pip3 install --user qark # --user is only needed if not using a virtualenv
qark --apk path/to/my.apk
qark --java path/to/parent/java/folder
qark --java path/to/specific/java/file.java
ReverseAPK
- 参照のためにすべての抽出ファイルを表示
- APKファイルを自動的にJavaおよびSmali形式にデコンパイル
- 一般的な脆弱性と動作のためにAndroidManifest.xmlを分析
- 一般的な脆弱性と動作のための静的ソースコード分析
- デバイス情報
- その他多数
reverse-apk relative/path/to/APP.apk
SUPER Android Analyzer
SUPERは、Windows、MacOS X、Linuxで使用できるコマンドラインアプリケーションで、脆弱性を探すために_.apk_ファイルを分析します。これは、APKを解凍し、一連のルールを適用して脆弱性を検出することによって行われます。
すべてのルールはrules.jsonファイルに集中しており、各企業やテスターは自分たちの必要に応じて分析するための独自のルールを作成できます。
最新のバイナリはダウンロードページからダウンロードしてください。
super-analyzer {apk_file}
StaCoAn
StaCoAnは、開発者、バグバウンティハンター、倫理的ハッカーがモバイルアプリケーションに対して静的コード分析を行うのを支援するクロスプラットフォームツールです。
コンセプトは、モバイルアプリケーションファイル(.apkまたは.ipaファイル)をStaCoAnアプリケーションにドラッグアンドドロップすると、視覚的でポータブルなレポートが生成されるというものです。設定やワードリストを調整して、カスタマイズされた体験を得ることができます。
最新リリースをダウンロード:
./stacoan
AndroBugs
AndroBugs Frameworkは、開発者やハッカーがAndroidアプリケーションの潜在的なセキュリティ脆弱性を見つけるのを助けるAndroid脆弱性分析システムです。
Windowsリリース
python androbugs.py -f [APK file]
androbugs.exe -f [APK file]
Androwarn
Androwarnは、Androidアプリケーションによって開発された潜在的な悪意のある動作を検出し、ユーザーに警告することを主な目的としたツールです。
検出は、アプリケーションのDalvikバイトコードの静的解析を使用して行われ、Smaliとして表現されます。androguardライブラリを使用しています。
このツールは、次のような**「悪い」アプリケーションの一般的な動作**を探します:テレフォニー識別子の流出、音声/ビデオフローの傍受、PIMデータの変更、任意のコード実行...
python androwarn.py -i my_application_to_be_analyzed.apk -r html -v 3
MARA Framework
MARAはモバイルアプリケーションの逆アセンブルと分析フレームワークです。これは、OWASPモバイルセキュリティ脅威に対してモバイルアプリケーションをテストするために、一般的に使用されるモバイルアプリケーションの逆アセンブルおよび分析ツールをまとめたツールです。その目的は、この作業をモバイルアプリケーションの開発者やセキュリティ専門家にとってより簡単で親しみやすくすることです。
以下のことが可能です:
- 異なるツールを使用してJavaおよびSmaliコードを抽出する
- smalisca、ClassyShark、androbugs、androwarn、APKiDを使用してAPKを分析する
- regexpsを使用してAPKからプライベート情報を抽出する
- マニフェストを分析する
- pyssltest、testssl、およびwhatwebを使用して見つかったドメインを分析する
- apk-deguard.comを介してAPKをデオブフスケートする
Koodous
マルウェアを検出するのに役立ちます: https://koodous.com/
コードの難読化/デオブフスケート
使用するサービスと構成によって、コードを難読化する際に秘密が難読化される場合とされない場合があります。
ProGuard
Wikipediaから: ProGuardは、Javaコードを縮小、最適化、難読化するオープンソースのコマンドラインツールです。バイトコードを最適化し、未使用の命令を検出して削除することができます。ProGuardはフリーソフトウェアで、GNU一般公衆ライセンス第2版の下で配布されています。
ProGuardはAndroid SDKの一部として配布され、アプリケーションをリリースモードでビルドする際に実行されます。
DexGuard
APKをデオブフスケートするためのステップバイステップガイドはhttps://blog.lexfo.fr/dexguard.htmlにあります。
(そのガイドから)最後に確認したとき、Dexguardの動作モードは次のとおりでした:
- リソースをInputStreamとして読み込む;
- 結果をFilterInputStreamから継承したクラスに渡して復号化する;
- リバースエンジニアに数分の時間を無駄にさせるために無駄な難読化を行う;
- 復号化された結果をZipInputStreamに渡してDEXファイルを取得する;
- 最後に、
loadDexメソッドを使用して結果のDEXをリソースとして読み込む。
DeGuard
DeGuardは、Androidの難読化ツールによって行われた難読化プロセスを逆転させます。これにより、コード検査やライブラリの予測など、数多くのセキュリティ分析が可能になります。
難読化されたAPKを彼らのプラットフォームにアップロードできます。
Simplify
これは汎用のAndroidデオブフスケーターです。Simplifyはアプリを仮想的に実行してその動作を理解し、その後コードを最適化しようとします。各最適化タイプはシンプルで汎用的であるため、使用される特定の難読化の種類は関係ありません。
APKiD
APKiDはAPKがどのように作成されたかに関する情報を提供します。多くのコンパイラ、パッカー、難読化ツール、およびその他の奇妙なものを特定します。これはAndroid用のPEiDです。
マニュアル
カスタム難読化を逆転させる方法に関するいくつかのトリックを学ぶためにこのチュートリアルを読んでください
ラボ
Androl4b
AndroL4bは、ubuntu-mateに基づいたAndroidセキュリティ仮想マシンで、リバースエンジニアリングとマルウェア分析のための最新のフレームワーク、チュートリアル、ラボのコレクションを含んでいます。
参考文献
- https://owasp.org/www-project-mobile-app-security/
- https://appsecwiki.com/#/ これは素晴らしいリソースのリストです
- https://maddiestone.github.io/AndroidAppRE/ Androidのクイックコース
- https://manifestsecurity.com/android-application-security/
- https://github.com/Ralireza/Android-Security-Teryaagh
- https://www.youtube.com/watch?v=PMKnPaGWxtg&feature=youtu.be&ab_channel=B3nacSec
まだ試していない

HackenProof Discordサーバーに参加して、経験豊富なハッカーやバグバウンティハンターとコミュニケーションを取りましょう!
ハッキングの洞察
ハッキングのスリルと課題に関するコンテンツに参加する
リアルタイムハックニュース
リアルタイムのニュースと洞察を通じて、急速に進化するハッキングの世界を把握する
最新の発表
新しいバグバウンティの開始や重要なプラットフォームの更新について情報を得る
Discordに参加して、今日からトップハッカーとコラボレーションを始めましょう!
{% hint style="success" %}
AWSハッキングを学び、実践する: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
GCPハッキングを学び、実践する:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
HackTricksをサポートする
- サブスクリプションプランを確認してください!
- **💬 Discordグループまたはテレグラムグループに参加するか、Twitter 🐦 @hacktricks_liveをフォローしてください。
- ハッキングのトリックを共有するために、HackTricksおよびHackTricks CloudのGitHubリポジトリにPRを提出してください。