| .. | ||
| drozer-tutorial | ||
| frida-tutorial | ||
| adb-commands.md | ||
| android-applications-basics.md | ||
| android-task-hijacking.md | ||
| apk-decompilers.md | ||
| avd-android-virtual-device.md | ||
| bypass-biometric-authentication-android.md | ||
| content-protocol.md | ||
| exploiting-a-debuggeable-applciation.md | ||
| google-ctf-2018-shall-we-play-a-game.md | ||
| install-burp-certificate.md | ||
| intent-injection.md | ||
| make-apk-accept-ca-certificate.md | ||
| manual-deobfuscation.md | ||
| react-native-application.md | ||
| README.md | ||
| reversing-native-libraries.md | ||
| smali-changes.md | ||
| spoofing-your-location-in-play-store.md | ||
| tapjacking.md | ||
| webview-attacks.md | ||
Android Applications Pentesting
{% hint style="success" %}
Jifunze na fanya mazoezi ya AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Jifunze na fanya mazoezi ya GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Angalia mpango wa usajili!
- Jiunge na 💬 kikundi cha Discord au kikundi cha telegram au fuata sisi kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu za hacking kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud github repos.

Jiunge na HackenProof Discord server kuwasiliana na hackers wenye uzoefu na wawindaji wa bug bounty!
Hacking Insights
Shiriki na maudhui yanayoangazia msisimko na changamoto za hacking
Real-Time Hack News
Baki na habari za hivi punde katika ulimwengu wa hacking kupitia habari na maarifa ya wakati halisi
Latest Announcements
Baki na taarifa kuhusu bug bounties mpya zinazozinduliwa na masasisho muhimu ya jukwaa
Jiunge nasi kwenye Discord na uanze kushirikiana na hackers bora leo!
Misingi ya Programu za Android
Inapendekezwa sana kuanza kusoma ukurasa huu ili kujua kuhusu sehemu muhimu zaidi zinazohusiana na usalama wa Android na vipengele hatari zaidi katika programu ya Android:
{% content-ref url="android-applications-basics.md" %} android-applications-basics.md {% endcontent-ref %}
ADB (Android Debug Bridge)
Hii ni chombo kikuu unachohitaji kuungana na kifaa cha android (kilichotengenezwa au halisi).
ADB inaruhusu kudhibiti vifaa ama kupitia USB au Network kutoka kwa kompyuta. Hii inaruhusu kuhamasisha faili katika mwelekeo wote, ufungaji na kuondoa programu, kutekeleza amri za shell, kuhifadhi data, kusoma kumbukumbu, kati ya kazi nyingine.
Angalia orodha ifuatayo ya ADB Commands kujifunza jinsi ya kutumia adb.
Smali
Wakati mwingine ni muhimu kubadilisha msimbo wa programu ili kufikia habari zilizofichwa (labda nywila au bendera zilizofichwa vizuri). Hivyo, inaweza kuwa ya kuvutia kufungua apk, kubadilisha msimbo na kuirejesha.
Katika mafunzo haya unaweza kujifunza jinsi ya kufungua APK, kubadilisha msimbo wa Smali na kuirejesha APK na kazi mpya. Hii inaweza kuwa ya manufaa kama mbadala wa majaribio kadhaa wakati wa uchambuzi wa dynamic ambao utawasilishwa. Hivyo, weka daima katika akili uwezekano huu.
Mbinu nyingine za kuvutia
- Kudanganya eneo lako katika Play Store
- Pakua APKs: https://apps.evozi.com/apk-downloader/, https://apkpure.com/es/, https://www.apkmirror.com/, https://apkcombo.com/es-es/apk-downloader/, https://github.com/kiber-io/apkd
- Toa APK kutoka kifaa:
adb shell pm list packages
com.android.insecurebankv2
adb shell pm path com.android.insecurebankv2
package:/data/app/com.android.insecurebankv2-Jnf8pNgwy3QA_U5f-n_4jQ==/base.apk
adb pull /data/app/com.android.insecurebankv2-Jnf8pNgwy3QA_U5f-n_4jQ==/base.apk
- Unganisha vipasuo vyote na apks za msingi kwa kutumia APKEditor:
mkdir splits
adb shell pm path com.android.insecurebankv2 | cut -d ':' -f 1 | xargs -n1 -i adb pull {} splits
java -jar ../APKEditor.jar m -i splits/ -o merged.apk
# after merging, you will need to align and sign the apk, personally, I like to use the uberapksigner
java -jar uber-apk-signer.jar -a merged.apk --allowResign -o merged_signed
Static Analysis
Kwanza kabisa, kwa kuchambua APK unapaswa kuangalia msimbo wa Java kwa kutumia decompiler.
Tafadhali, soma hapa kupata taarifa kuhusu decompilers mbalimbali zinazopatikana.
Looking for interesting Info
Kwa kuangalia tu nyuzi za APK unaweza kutafuta nywila, URLs (https://github.com/ndelphit/apkurlgrep), api funguo, sifuri, bluetooth uuids, tokens na chochote kinachovutia... angalia hata kwa utekelezaji wa msimbo backdoors au backdoors za uthibitishaji (akili za admin zilizowekwa ndani ya programu).
Firebase
Lipa kipaumbele maalum kwa firebase URLs na angalia kama imewekwa vibaya. Taarifa zaidi kuhusu nini FIrebase na jinsi ya kuitumia hapa.
Basic understanding of the application - Manifest.xml, strings.xml
uchambuzi wa faili za _Manifest.xml** na **strings.xml_** unaweza kufichua udhaifu wa usalama**. Faili hizi zinaweza kufikiwa kwa kutumia decompilers au kwa kubadilisha kiendelezi cha faili la APK kuwa .zip na kisha kuzipa.
Udhaifu ulioainishwa kutoka kwa Manifest.xml ni pamoja na:
- Programu zinazoweza kudhibitiwa: Programu zilizowekwa kama zinazoweza kudhibitiwa (
debuggable="true") katika faili la Manifest.xml zina hatari kwani zinaruhusu muunganisho ambao unaweza kusababisha matumizi mabaya. Kwa ufahamu zaidi kuhusu jinsi ya kutumia programu zinazoweza kudhibitiwa, rejelea mafunzo juu ya kutafuta na kutumia programu zinazoweza kudhibitiwa kwenye kifaa. - Mipangilio ya Nakala: Sifa ya
android:allowBackup="false"inapaswa kuwekwa wazi kwa programu zinazoshughulika na taarifa nyeti ili kuzuia nakala zisizoidhinishwa za data kupitia adb, hasa wakati ufuatiliaji wa usb umewezeshwa. - Usalama wa Mtandao: Mipangilio ya usalama wa mtandao ya kawaida (
android:networkSecurityConfig="@xml/network_security_config") katika res/xml/ inaweza kubainisha maelezo ya usalama kama vile pini za cheti na mipangilio ya trafiki ya HTTP. Mfano ni kuruhusu trafiki ya HTTP kwa maeneo maalum. - Shughuli na Huduma Zilizotolewa: Kutambua shughuli na huduma zilizotolewa katika manifest kunaweza kuonyesha vipengele ambavyo vinaweza kutumika vibaya. Uchambuzi zaidi wakati wa upimaji wa nguvu unaweza kufichua jinsi ya kutumia vipengele hivi.
- Watoa Maudhui na Watoa Faili: Watoa maudhui walio wazi wanaweza kuruhusu ufikiaji usioidhinishwa au mabadiliko ya data. Mipangilio ya Watoa Faili inapaswa pia kuchunguzwa kwa makini.
- Vipokezi vya Matangazo na Mipango ya URL: Vipengele hivi vinaweza kutumika kwa matumizi mabaya, huku kukiwa na umakini maalum juu ya jinsi mipango ya URL inavyoshughulikiwa kwa udhaifu wa ingizo.
- Toleo la SDK: Sifa za
minSdkVersion,targetSDKVersion, namaxSdkVersionzinaonyesha toleo la Android linaloungwa mkono, zikisisitiza umuhimu wa kutosaidia toleo la zamani la Android lenye udhaifu kwa sababu za usalama.
Kutoka kwa faili ya strings.xml, taarifa nyeti kama funguo za API, mipango ya kawaida, na maelezo mengine ya waendelezaji yanaweza kugundulika, yakisisitiza hitaji la ukaguzi wa makini wa rasilimali hizi.
Tapjacking
Tapjacking ni shambulio ambapo programu mbaya inazinduliwa na kujiweka juu ya programu ya mwathirika. Mara inapoificha wazi programu ya mwathirika, kiolesura chake cha mtumiaji kimeundwa kwa njia ya kudanganya mtumiaji kuingiliana nayo, wakati inapitisha mwingiliano huo kwa programu ya mwathirika.
Kwa hivyo, inafanya mtumiaji kuwa kipofu kwa kujua kwamba kwa kweli wanatekeleza vitendo kwenye programu ya mwathirika.
Pata taarifa zaidi katika:
{% content-ref url="tapjacking.md" %} tapjacking.md {% endcontent-ref %}
Task Hijacking
shughuli yenye launchMode iliyowekwa kuwa singleTask bila taskAffinity iliyofafanuliwa ina udhaifu wa hijacking ya kazi. Hii inamaanisha kwamba programu inaweza kusakinishwa na ikiwa itazinduliwa kabla ya programu halisi inaweza kuchukua kazi ya programu halisi (hivyo mtumiaji atakuwa akifanya kazi na programu mbaya akidhani anatumia halisi).
Taarifa zaidi katika:
{% content-ref url="android-task-hijacking.md" %} android-task-hijacking.md {% endcontent-ref %}
Insecure data storage
Hifadhi ya Ndani
Katika Android, faili zilizohifadhiwa katika hifadhi ya ndani zime kusudiwa kuwa zinapatikana pekee na programu iliyozitengeneza. Kipimo hiki cha usalama kina imarishwa na mfumo wa uendeshaji wa Android na kwa ujumla kinatosha kwa mahitaji ya usalama ya programu nyingi. Hata hivyo, waendelezaji wakati mwingine hutumia njia kama MODE_WORLD_READABLE na MODE_WORLD_WRITABLE ili kuruhusu faili kushirikiwa kati ya programu tofauti. Hata hivyo, njia hizi hazizuii ufikiaji wa faili hizi na programu nyingine, ikiwa ni pamoja na zile zenye nia mbaya.
- Uchambuzi wa Kimuundo:
- Hakikisha kwamba matumizi ya
MODE_WORLD_READABLEnaMODE_WORLD_WRITABLEyana chunguzwa kwa makini. Njia hizi zinaweza kufichua faili kwa ufikiaji usioidhinishwa au usio kusudiwa.
- Uchambuzi wa Dini:
- Thibitisha idhini zilizowekwa kwenye faili zilizoundwa na programu. Kwa haswa, angalia kama faili yoyote ime wekwa kuwa inasomeka au kuandikwa duniani kote. Hii inaweza kuwa hatari kubwa ya usalama, kwani itaruhusu programu yoyote iliyosakinishwa kwenye kifaa, bila kujali asili yake au nia, kusoma au kubadilisha faili hizi.
Hifadhi ya Nje
Wakati wa kushughulikia faili kwenye hifadhi ya nje, kama vile Kadi za SD, tahadhari fulani zinapaswa kuchukuliwa:
- Ufikivu:
- Faili kwenye hifadhi ya nje ni zinazosomeka na kuandikwa duniani kote. Hii inamaanisha programu au mtumiaji yeyote anaweza kufikia faili hizi.
- Masuala ya Usalama:
- Kwa kuzingatia urahisi wa ufikiaji, inashauriwa kutohifadhi taarifa nyeti kwenye hifadhi ya nje.
- Hifadhi ya nje inaweza kuondolewa au kufikiwa na programu yoyote, na kuifanya kuwa na usalama mdogo.
- Kushughulikia Data kutoka Hifadhi ya Nje:
- Daima fanya uthibitisho wa ingizo kwenye data iliyopatikana kutoka hifadhi ya nje. Hii ni muhimu kwa sababu data hiyo inatoka kwenye chanzo kisichoaminika.
- Kuhifadhi executable au faili za darasa kwenye hifadhi ya nje kwa ajili ya upakiaji wa nguvu kunashauriwa kutozwa.
- Ikiwa programu yako inapaswa kupata faili za executable kutoka hifadhi ya nje, hakikisha faili hizi zime sainiwa na kuthibitishwa kwa njia ya kisasa kabla ya kupakiwa kwa nguvu. Hatua hii ni muhimu kwa kudumisha uaminifu wa usalama wa programu yako.
Hifadhi ya nje inaweza kupatikana katika /storage/emulated/0, /sdcard, /mnt/sdcard
{% hint style="info" %} Kuanza na Android 4.4 (API 17), kadi ya SD ina muundo wa saraka ambao unapunguza ufikiaji kutoka kwa programu hadi saraka ambayo ni maalum kwa programu hiyo. Hii inazuia programu mbaya kupata ufikiaji wa kusoma au kuandika kwenye faili za programu nyingine. {% endhint %}
Taarifa nyeti zilizohifadhiwa kwa maandiko wazi
- Mipangilio ya pamoja: Android inaruhusu kila programu kuhifadhi kwa urahisi faili za xml katika njia
/data/data/<packagename>/shared_prefs/na wakati mwingine inawezekana kupata taarifa nyeti kwa maandiko wazi katika folda hiyo. - Maktaba: Android inaruhusu kila programu kuhifadhi kwa urahisi maktaba za sqlite katika njia
/data/data/<packagename>/databases/na wakati mwingine inawezekana kupata taarifa nyeti kwa maandiko wazi katika folda hiyo.
Broken TLS
Kubaliana na Vyeti Vyote
Kwa sababu fulani wakati mwingine waendelezaji wanakubali vyeti vyote hata kama kwa mfano jina la mwenyeji halifanani na mistari ya msimbo kama ifuatavyo:
SSLSocketFactory sf = new cc(trustStore);
sf.setHostnameVerifier(SSLSocketFactory.ALLOW_ALL_HOSTNAME_VERIFIER);
A good way to test this is to try to capture the traffic using some proxy like Burp without authorising Burp CA inside the device. Also, you can generate with Burp a certificate for a different hostname and use it.
Broken Cryptography
Poor Key Management Processes
Wakandarasi wengine huhifadhi data nyeti katika hifadhi ya ndani na kuificha kwa kutumia funguo zilizowekwa kwa ngumu/zinazoweza kutabiriwa katika msimbo. Hii haipaswi kufanywa kwani baadhi ya kurudi nyuma kunaweza kuruhusu washambuliaji kutoa taarifa za siri.
Use of Insecure and/or Deprecated Algorithms
Wakandarasi hawapaswi kutumia algorithms zilizopitwa na wakati kufanya muhimu, hifadhi au tuma data. Baadhi ya hizi ni: RC4, MD4, MD5, SHA1... Ikiwa hashes zinatumika kuhifadhi nywila kwa mfano, hashes zinazopinga brute-force zinapaswa kutumika na chumvi.
Other checks
- Inapendekezwa kuficha APK ili kufanya kazi ya mhandisi wa kurudi kuwa ngumu kwa washambuliaji.
- Ikiwa programu ni nyeti (kama programu za benki), inapaswa kufanya muhimu yake mwenyewe kuona kama simu imejikita na kuchukua hatua.
- Ikiwa programu ni nyeti (kama programu za benki), inapaswa kuangalia kama emulator inatumika.
- Ikiwa programu ni nyeti (kama programu za benki), inapaswa kuangalia uadilifu wake kabla ya kutekeleza ili kuangalia kama imebadilishwa.
- Tumia APKiD kuangalia ni compiler/packer/obfuscator gani ilitumika kujenga APK
React Native Application
Read the following page to learn how to easily access javascript code of React applications:
{% content-ref url="react-native-application.md" %} react-native-application.md {% endcontent-ref %}
Xamarin Applications
Read the following page to learn how to easily access C# code of a xamarin applications:
{% content-ref url="../xamarin-apps.md" %} xamarin-apps.md {% endcontent-ref %}
Superpacked Applications
According to this blog post superpacked is a Meta algorithm that compress the content of an application into a single file. The blog talks about the possibility of creating an app that decompress these kind of apps... and a faster way which involves to execute the application and gather the decompressed files from the filesystem.
Automated Static Code Analysis
The tool mariana-trench is capable of finding vulnerabilities by scanning the code of the application. This tool contains a series of known sources (that indicates to the tool the places where the input is controlled by the user), sinks (which indicates to the tool dangerous places where malicious user input could cause damages) and rules. These rules indicates the combination of sources-sinks that indicates a vulnerability.
With this knowledge, mariana-trench will review the code and find possible vulnerabilities on it.
Secrets leaked
An application may contain secrets (API keys, passwords, hidden urls, subdomains...) inside of it that you might be able to discover. You could us a tool such as https://github.com/dwisiswant0/apkleaks
Bypass Biometric Authentication
{% content-ref url="bypass-biometric-authentication-android.md" %} bypass-biometric-authentication-android.md {% endcontent-ref %}
Other interesting functions
- Code execution:
Runtime.exec(), ProcessBuilder(), native code:system() - Send SMSs:
sendTextMessage, sendMultipartTestMessage - Native functions declared as
native:public native, System.loadLibrary, System.load - Read this to learn how to reverse native functions
Other tricks
{% content-ref url="content-protocol.md" %} content-protocol.md {% endcontent-ref %}

Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
Engage with content that delves into the thrill and challenges of hacking
Real-Time Hack News
Keep up-to-date with fast-paced hacking world through real-time news and insights
Latest Announcements
Stay informed with the newest bug bounties launching and crucial platform updates
Join us on Discord and start collaborating with top hackers today!
Dynamic Analysis
First of all, you need an environment where you can install the application and all the environment (Burp CA cert, Drozer and Frida mainly). Therefore, a rooted device (emulated or not) is extremely recommended.
Online Dynamic analysis
You can create a free account in: https://appetize.io/. This platform allows you to upload and execute APKs, so it is useful to see how an apk is behaving.
You can even see the logs of your application in the web and connect through adb.
Thanks to the ADB connection you can use Drozer and Frida inside the emulators.
Local Dynamic Analysis
Using an emulator
- Android Studio (You can create x86 and arm devices, and according to this latest x86 versions support ARM libraries without needing an slow arm emulator).
- Learn to set it up in this page:
{% content-ref url="avd-android-virtual-device.md" %} avd-android-virtual-device.md {% endcontent-ref %}
- Genymotion (Free version: Personal Edition, you need to create an account. It's recommend to download the version WITH VirtualBox to avoid potential errors.)
- Nox (Free, but it doesn't support Frida or Drozer).
{% hint style="info" %} When creating a new emulator on any platform remember that the bigger the screen is, the slower the emulator will run. So select small screens if possible. {% endhint %}
To install google services (like AppStore) in Genymotion you need to click on the red marked button of the following image:
Also, notice that in the configuration of the Android VM in Genymotion you can select Bridge Network mode (this will be useful if you will be connecting to the Android VM from a different VM with the tools).
Use a physical device
You need to activate the debugging options and it will be cool if you can root it:
- Settings.
- (FromAndroid 8.0) Select System.
- Select About phone.
- Press Build number 7 times.
- Go back and you will find the Developer options.
Once you have installed the application, the first thing you should do is to try it and investigate what does it do, how does it work and get comfortable with it.
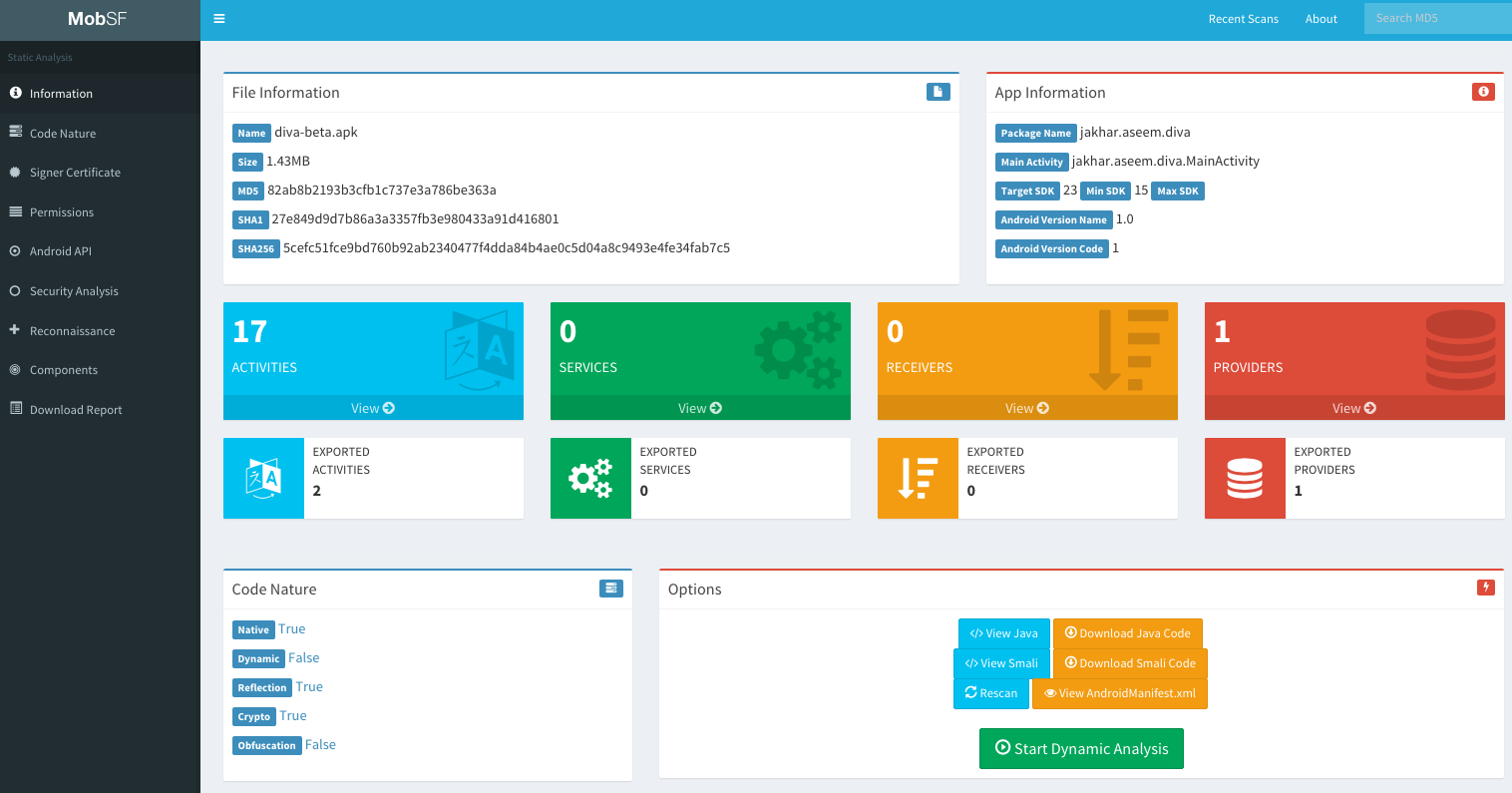
I will suggest to perform this initial dynamic analysis using MobSF dynamic analysis + pidcat, so we will be able to learn how the application works while MobSF captures a lot of interesting data you can review later on.
Unintended Data Leakage
Logging
Wakandarasi wanapaswa kuwa makini kuhusu kufichua taarifa za ufuatiliaji hadharani, kwani inaweza kusababisha uvujaji wa data nyeti. Zana pidcat na adb logcat zinapendekezwa kwa ajili ya kufuatilia kumbukumbu za programu ili kubaini na kulinda taarifa nyeti. Pidcat inapendwa kwa urahisi wa matumizi na usomaji.
{% hint style="warning" %}
Note that from later newer than Android 4.0, applications are only able to access their own logs. So applications cannot access other apps logs.
Anyway, it's still recommended to not log sensitive information.
{% endhint %}
Copy/Paste Buffer Caching
Mfumo wa clipboard-based wa Android unaruhusu kazi ya kunakili-na-kut粘 katika programu, lakini unatoa hatari kwani programu nyingine zinaweza kupata clipboard, na hivyo kuweza kufichua data nyeti. Ni muhimu kuondoa kazi za kunakili/kut粘 kwa sehemu nyeti za programu, kama vile maelezo ya kadi ya mkopo, ili kuzuia uvujaji wa data.
Crash Logs
Ikiwa programu inasambaratika na kuhifadhi kumbukumbu, kumbukumbu hizi zinaweza kusaidia washambuliaji, hasa wakati programu haiwezi kurudi nyuma. Ili kupunguza hatari hii, epuka kuandika kumbukumbu wakati wa ajali, na ikiwa kumbukumbu lazima zitumwe kupitia mtandao, hakikisha zinatumwa kupitia njia ya SSL kwa usalama.
Kama pentester, jaribu kuangalia kumbukumbu hizi.
Analytics Data Sent To 3rd Parties
Programu mara nyingi hujumuisha huduma kama Google Adsense, ambazo zinaweza bila kukusudia kuvuja data nyeti kutokana na utekelezaji usiofaa na wakandarasi. Ili kubaini uvujaji wa data, inashauriwa kukamata trafiki ya programu na kuangalia kama kuna taarifa nyeti zinazotumwa kwa huduma za upande wa tatu.
SQLite DBs
Mara nyingi programu zitatumia maktaba za ndani za SQLite kuhifadhi taarifa. Wakati wa pentest angalia maktaba zilizoundwa, majina ya meza na safu na data yote iliyohifadhiwa kwa sababu unaweza kupata taarifa nyeti (ambayo itakuwa udhaifu).
Maktaba zinapaswa kuwa katika /data/data/the.package.name/databases kama /data/data/com.mwr.example.sieve/databases
Ikiwa maktaba inahifadhi taarifa za siri na ime fichwa lakini unaweza kupata nywila ndani ya programu bado ni udhaifu.
Taja meza kwa kutumia .tables na taja safu za meza kwa kufanya .schema <table_name>
Drozer (Exploit Activities, Content Providers and Services)
From Drozer Docs: Drozer allows you to assume the role of an Android app and interact with other apps. It can do anything that an installed application can do, such as make use of Android’s Inter-Process Communication (IPC) mechanism and interact with the underlying operating system. .
Drozer is s useful tool to exploit exported activities, exported services and Content Providers as you will learn in the following sections.
Exploiting exported Activities
Read this if you want to refresh what is an Android Activity.
Also remember that the code of an activity starts in the onCreate method.
Authorisation bypass
When an Activity is exported you can invoke its screen from an external app. Therefore, if an activity with sensitive information is exported you could bypass the authentication mechanisms to access it.
Learn how to exploit exported activities with Drozer.
You can also start an exported activity from adb:
- PackageName is com.example.demo
- Exported ActivityName is com.example.test.MainActivity
adb shell am start -n com.example.demo/com.example.test.MainActivity
NOTE: MobSF itagundua kama hatari matumizi ya singleTask/singleInstance kama android:launchMode katika shughuli, lakini kutokana na hii, inaonekana hii ni hatari tu kwenye toleo za zamani (API versions < 21).
{% hint style="info" %} Kumbuka kwamba kupita kwa idhini si kila wakati ni udhaifu, itategemea jinsi kupita kunavyofanya kazi na ni taarifa gani zinazoonyeshwa. {% endhint %}
Kuvuja kwa taarifa nyeti
Shughuli zinaweza pia kurudisha matokeo. Ikiwa utaweza kupata shughuli iliyosafirishwa na isiyo na ulinzi inayoita setResult na kurudisha taarifa nyeti, kuna uvujaji wa taarifa nyeti.
Tapjacking
Ikiwa tapjacking haizuiwi, unaweza kutumia shughuli iliyosafirishwa kufanya mtumiaji afanye vitendo visivyotarajiwa. Kwa maelezo zaidi kuhusu nini Tapjacking fuata kiungo.
Kutumia Watoa Maudhui - Kufikia na kubadilisha taarifa nyeti
Soma hii ikiwa unataka kukumbusha nini ni Mtoa Maudhui.
Watoa maudhui kimsingi hutumiwa kushiriki data. Ikiwa programu ina watoa maudhui wanaopatikana unaweza kuwa na uwezo wa kuchota taarifa nyeti kutoka kwao. Pia ni ya kuvutia kujaribu SQL injections na Path Traversals kwani zinaweza kuwa na udhaifu.
Jifunze jinsi ya kutumia Watoa Maudhui na Drozer.
Kutumia Huduma
Soma hii ikiwa unataka kukumbusha nini ni Huduma.
Kumbuka kwamba vitendo vya Huduma huanza katika njia onStartCommand.
Huduma kimsingi ni kitu ambacho kinaweza kupokea data, kuchakata na kurudisha (au la) jibu. Hivyo, ikiwa programu inasafirisha baadhi ya huduma unapaswa kuangalia msimbo ili kuelewa inafanya nini na kujaribu kwa dynamically ili kuchota taarifa za siri, kupita hatua za uthibitishaji...
Jifunze jinsi ya kutumia Huduma na Drozer.
Kutumia Vastika za Matangazo
Soma hii ikiwa unataka kukumbusha nini ni Vastika za Matangazo.
Kumbuka kwamba vitendo vya Vastika za Matangazo huanza katika njia onReceive.
Vastika ya matangazo itakuwa ikisubiri aina fulani ya ujumbe. Kulingana na jinsi vastika inavyoshughulikia ujumbe inaweza kuwa na udhaifu.
Jifunze jinsi ya kutumia Vastika za Matangazo na Drozer.
Kutumia Mipango / Viungo vya Kina
Unaweza kutafuta viungo vya kina kwa mikono, ukitumia zana kama MobSF au scripts kama hii.
Unaweza kufungua mpango ulioelezwa kwa kutumia adb au brower:
{% code overflow="wrap" %}
adb shell am start -a android.intent.action.VIEW -d "scheme://hostname/path?param=value" [your.package.name]
{% endcode %}
Kumbuka kwamba unaweza kuacha jina la kifurushi na simu itaita kiotomatiki programu ambayo inapaswa kufungua kiungo hicho.
{% code overflow="wrap" %}
<!-- Browser regular link -->
<a href="scheme://hostname/path?param=value">Click me</a>
<!-- fallback in your url you could try the intent url -->
<a href="intent://hostname#Intent;scheme=scheme;package=your.package.name;S.browser_fallback_url=http%3A%2F%2Fwww.example.com;end">with alternative</a>
{% endcode %}
Msimbo uliofanywa
Ili kupata msimbo utakaotekelezwa katika App, nenda kwenye shughuli inayoitwa na deeplink na tafuta kazi onNewIntent.
Taarifa nyeti
Kila wakati unapata deeplink hakikisha kuwa haipati data nyeti (kama nywila) kupitia vigezo vya URL, kwa sababu programu nyingine yoyote inaweza kujifanya kuwa deeplink na kuiba data hiyo!
Vigezo katika njia
Unapaswa kuangalia pia kama deeplink yoyote inatumia parameter ndani ya njia ya URL kama: https://api.example.com/v1/users/{username}, katika kesi hiyo unaweza kulazimisha usafiri wa njia ukifika kitu kama: example://app/users?username=../../unwanted-endpoint%3fparam=value.
Kumbuka kwamba ikiwa utapata mwisho sahihi ndani ya programu unaweza kuwa na uwezo wa kusababisha Open Redirect (ikiwa sehemu ya njia inatumika kama jina la kikoa), kuchukua akaunti (ikiwa unaweza kubadilisha maelezo ya watumiaji bila CSRF token na mwisho ulio na vuln ulitumia njia sahihi) na vuln nyingine yoyote. Maelezo zaidi hapa.
Mifano zaidi
Ripoti ya bug bounty ya kuvutia kuhusu viungo (/.well-known/assetlinks.json).
Ukaguzi wa Tabaka la Usafirishaji na Kushindwa kwa Uthibitishaji
- Vyeti havikaguliwi kila wakati ipasavyo na programu za Android. Ni kawaida kwa programu hizi kupuuza onyo na kukubali vyeti vilivyojitegemea au, katika baadhi ya matukio, kurudi kutumia muunganisho wa HTTP.
- Majadiliano wakati wa mkono wa SSL/TLS wakati mwingine ni dhaifu, yakitumia cipher suites zisizo salama. Uthibitisho huu unafanya muunganisho uwe hatarini kwa mashambulizi ya mtu katikati (MITM), kuruhusu washambuliaji kufungua data.
- Kuvuja kwa taarifa binafsi ni hatari wakati programu zinathibitisha kwa kutumia njia salama lakini kisha kuwasiliana kupitia njia zisizo salama kwa shughuli nyingine. Njia hii inashindwa kulinda data nyeti, kama vile vidakuzi vya kikao au maelezo ya mtumiaji, kutokana na kukamatwa na wahalifu.
Uthibitishaji wa Cheti
Tutazingatia uthibitishaji wa cheti. Uadilifu wa cheti cha seva lazima uthibitishwe ili kuimarisha usalama. Hii ni muhimu kwa sababu usanidi usio salama wa TLS na uhamasishaji wa data nyeti kupitia njia zisizo na usalama unaweza kuleta hatari kubwa. Kwa hatua za kina za kuthibitisha vyeti vya seva na kushughulikia udhaifu, rasilimali hii inatoa mwongozo wa kina.
SSL Pinning
SSL Pinning ni hatua ya usalama ambapo programu inathibitisha cheti cha seva dhidi ya nakala inayojulikana iliyohifadhiwa ndani ya programu yenyewe. Njia hii ni muhimu kwa kuzuia mashambulizi ya MITM. Kutekeleza SSL Pinning kunapendekezwa kwa nguvu kwa programu zinazoshughulikia taarifa nyeti.
Ukaguzi wa Trafiki
Ili kukagua trafiki ya HTTP, ni muhimu kusanidi cheti cha zana ya proxy (mfano, Burp). Bila kusanidi cheti hiki, trafiki iliyosimbwa inaweza isionekane kupitia proxy. Kwa mwongozo wa kusanidi cheti cha CA cha kawaida, bonyeza hapa.
Programu zinazolenga API Level 24 na zaidi zinahitaji marekebisho kwenye Usanidi wa Usalama wa Mtandao ili kukubali cheti cha CA cha proxy. Hatua hii ni muhimu kwa kukagua trafiki iliyosimbwa. Kwa maelekezo ya kubadilisha Usanidi wa Usalama wa Mtandao, rejelea mafunzo haya.
Kupita SSL Pinning
Wakati SSL Pinning inatekelezwa, kupita inakuwa muhimu ili kukagua trafiki ya HTTPS. Njia mbalimbali zinapatikana kwa kusudi hili:
- Kiotomatiki badilisha apk ili kupita SSLPinning na apk-mitm. Faida bora ya chaguo hili ni kwamba hutahitaji root ili kupita SSL Pinning, lakini utahitaji kufuta programu na kuisakinisha upya, na hii haitafanya kazi kila wakati.
- Unaweza kutumia Frida (iliyajadiliwa hapa chini) ili kupita ulinzi huu. Hapa kuna mwongozo wa kutumia Burp+Frida+Genymotion: https://spenkk.github.io/bugbounty/Configuring-Frida-with-Burp-and-GenyMotion-to-bypass-SSL-Pinning/
- Unaweza pia kujaribu kupita kiotomatiki SSL Pinning kwa kutumia objection:
objection --gadget com.package.app explore --startup-command "android sslpinning disable" - Unaweza pia kujaribu kupita kiotomatiki SSL Pinning kwa kutumia uchambuzi wa dynamic wa MobSF (ilivyoelezwa hapa chini)
- Ikiwa bado unafikiri kuna trafiki ambayo hujapata unaweza kujaribu kupeleka trafiki kwa burp kwa kutumia iptables. Soma blog hii: https://infosecwriteups.com/bypass-ssl-pinning-with-ip-forwarding-iptables-568171b52b62
Kutafuta Udhaifu wa Kawaida wa Mtandao
Ni muhimu pia kutafuta udhaifu wa kawaida wa mtandao ndani ya programu. Taarifa za kina kuhusu kutambua na kupunguza udhaifu hizi ziko nje ya upeo wa muhtasari huu lakini zimefunikwa kwa kina mahali pengine.
Frida
Frida ni zana ya uhandisi wa dynamic kwa ajili ya waendelezaji, wahandisi wa kurudi nyuma, na watafiti wa usalama.
Unaweza kufikia programu inayofanya kazi na kuunganisha mbinu wakati wa wakati wa kukimbia kubadilisha tabia, kubadilisha thamani, kutoa thamani, kukimbia msimbo tofauti...
Ikiwa unataka kufanya pentest kwenye programu za Android unahitaji kujua jinsi ya kutumia Frida.
- Jifunze jinsi ya kutumia Frida: Mafunzo ya Frida
- Baadhi ya "GUI" kwa vitendo na Frida: https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security
- Ojection ni nzuri kwa kuharakisha matumizi ya Frida: https://github.com/sensepost/objection , https://github.com/dpnishant/appmon
- Unaweza kupata baadhi ya scripts za Frida za kushangaza hapa: https://codeshare.frida.re/
- Jaribu kupita mitambo ya kupinga-debugging / kupinga-frida kwa kupakia Frida kama ilivyoonyeshwa katika https://erfur.github.io/blog/dev/code-injection-without-ptrace (chombo linjector)
Dump Memory - Fridump
Angalia ikiwa programu inahifadhi taarifa nyeti ndani ya kumbukumbu ambayo haipaswi kuhifadhi kama nywila au maneno ya kukumbuka.
Kwa kutumia Fridump3 unaweza dump kumbukumbu ya programu na:
# With PID
python3 fridump3.py -u <PID>
# With name
frida-ps -Uai
python3 fridump3.py -u "<Name>"
Hii itatoa kumbukumbu katika folda ya ./dump, na humo unaweza kutumia grep na kitu kama:
{% code overflow="wrap" %}
strings * | grep -E "^[a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+ [a-z]+$"
{% endcode %}
Data nyeti katika Keystore
Katika Android, Keystore ni mahali bora pa kuhifadhi data nyeti, hata hivyo, kwa ruhusa ya kutosha bado inawezekana kuipata. Kadri programu zinavyotenda kuhifadhi hapa data nyeti katika maandiko wazi, pentests zinapaswa kuangalia kwa mtumiaji wa root au mtu mwenye ufikiaji wa kimwili kwenye kifaa anaweza kuwa na uwezo wa kuiba data hii.
Hata kama programu imehifadhi data katika keystore, data inapaswa kuwa imefungwa.
Ili kufikia data ndani ya keystore unaweza kutumia script hii ya Frida: https://github.com/WithSecureLabs/android-keystore-audit/blob/master/frida-scripts/tracer-cipher.js
frida -U -f com.example.app -l frida-scripts/tracer-cipher.js
Fingerprint/Biometrics Bypass
Kwa kutumia skripti ya Frida ifuatayo inaweza kuwa inawezekana kuzidi uthibitisho wa alama za vidole ambayo programu za Android zinaweza kuwa zinafanya ili kulinda maeneo fulani nyeti:
{% code overflow="wrap" %}
frida --codeshare krapgras/android-biometric-bypass-update-android-11 -U -f <app.package>
{% endcode %}
Picha za Muktadha
Unapoweka programu katika muktadha, Android huhifadhi picha ya programu ili wakati inaporejeshwa kwenye mbele inaanza kupakia picha kabla ya programu ili ionekane kama programu ilipakiwa haraka.
Hata hivyo, ikiwa picha hii ina habari nyeti, mtu mwenye ufikiaji wa picha hiyo anaweza kuchukua habari hiyo (kumbuka kuwa unahitaji root ili kuweza kuifikia).
Picha hizo kwa kawaida huhifadhiwa katika: /data/system_ce/0/snapshots
Android inatoa njia ya kuzuia upigaji picha wa skrini kwa kuweka kipimo cha FLAG_SECURE. Kwa kutumia bendera hii, maudhui ya dirisha yanachukuliwa kama salama, kuzuia kuonekana katika picha za skrini au kutazamwa kwenye onyesho lisilo salama.
getWindow().setFlags(LayoutParams.FLAG_SECURE, LayoutParams.FLAG_SECURE);
Android Application Analyzer
Chombo hiki kinaweza kukusaidia kusimamia zana tofauti wakati wa uchambuzi wa dynamic: https://github.com/NotSoSecure/android_application_analyzer
Intent Injection
Wak developers mara nyingi huunda vipengele vya proxy kama shughuli, huduma, na wapokeaji wa matangazo ambao hushughulikia hizi Intents na kuzipitisha kwa mbinu kama startActivity(...) au sendBroadcast(...), ambayo inaweza kuwa hatari.
Hatari iko katika kuruhusu washambuliaji kuanzisha vipengele vya programu visivyoweza kusambazwa au kufikia watoa maudhui nyeti kwa kuhamasisha hizi Intents. Mfano maarufu ni kipengele cha WebView kinachobadilisha URLs kuwa vitu vya Intent kupitia Intent.parseUri(...) na kisha kuyatekeleza, ambayo yanaweza kusababisha uhamasishaji mbaya wa Intent.
Essential Takeaways
- Intent Injection ni sawa na tatizo la Open Redirect la wavuti.
- Uhalifu unahusisha kupitisha vitu vya
Intentkama ziada, ambavyo vinaweza kuhamasishwa kutekeleza operesheni zisizo salama. - Inaweza kufichua vipengele visivyoweza kusambazwa na watoa maudhui kwa washambuliaji.
- Ubadilishaji wa URL wa
WebViewkuwaIntentunaweza kuwezesha vitendo visivyokusudiwa.
Android Client Side Injections and others
Labda unajua kuhusu aina hii ya udhaifu kutoka kwa Wavuti. Lazima uwe makini sana na udhaifu huu katika programu ya Android:
- SQL Injection: Unaposhughulikia maswali ya dynamic au Watoa-Maudhui hakikisha unatumia maswali yaliyopangwa.
- JavaScript Injection (XSS): Hakikisha kuwa msaada wa JavaScript na Plugin umezimwa kwa WebViews yoyote (umezimwa kwa default). Maelezo zaidi hapa.
- Local File Inclusion: WebViews zinapaswa kuwa na ufikiaji wa mfumo wa faili umezimwa (umewezeshwa kwa default) -
(webview.getSettings().setAllowFileAccess(false);). Maelezo zaidi hapa. - Eternal cookies: Katika kesi kadhaa wakati programu ya android inamaliza kikao, cookie haifutwi au inaweza hata kuhifadhiwa kwenye diski.
- Secure Flag katika cookies

Jiunge na HackenProof Discord server ili kuwasiliana na hackers wenye uzoefu na wawindaji wa bug bounty!
Hacking Insights
Shiriki na maudhui yanayochunguza msisimko na changamoto za hacking
Real-Time Hack News
Endelea kuwa na habari za hivi punde katika ulimwengu wa hacking kupitia habari na maarifa ya wakati halisi
Latest Announcements
Baki na habari kuhusu bug bounties mpya zinazozinduliwa na masasisho muhimu ya jukwaa
Jiunge nasi kwenye Discord na uanze kushirikiana na hackers bora leo!
Automatic Analysis
MobSF
Static analysis
Tathmini ya udhaifu wa programu kwa kutumia frontend nzuri ya wavuti. Unaweza pia kufanya uchambuzi wa dynamic (lakini unahitaji kuandaa mazingira).
docker pull opensecurity/mobile-security-framework-mobsf
docker run -it -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
Notice that MobSF can analyse Android(apk), IOS(ipa) and Windows(apx) applications (Windows applications must be analyzed from a MobSF installed in a Windows host).
Pia, ikiwa unaunda ZIP faili na msimbo wa chanzo wa programu ya Android au IOS (nenda kwenye folda ya mzizi ya programu, chagua kila kitu na uunde faili la ZIP), itakuwa na uwezo wa kuichambua pia.
MobSF also allows you to diff/Compare analysis and to integrate VirusTotal (you will need to set your API key in MobSF/settings.py and enable it: VT_ENABLED = TRUE VT_API_KEY = <Your API key> VT_UPLOAD = TRUE). You can also set VT_UPLOAD to False, then the hash will be upload instead of the file.
Assisted Dynamic analysis with MobSF
MobSF can also be very helpful for dynamic analysis in Android, but in that case you will need to install MobSF and genymotion in your host (a VM or Docker won't work). Note: You need to start first a VM in genymotion and then MobSF.
Mchambuzi wa MobSF dynamic anaweza:
- Dump application data (URLs, logs, clipboard, screenshots made by you, screenshots made by "Exported Activity Tester", emails, SQLite databases, XML files, and other created files). All of this is done automatically except for the screenshots, you need to press when you want a screenshot or you need to press "Exported Activity Tester" to obtain screenshots of all the exported activities.
- Capture HTTPS traffic
- Use Frida to obtain runtime information
From android versions > 5, it will automatically start Frida and will set global proxy settings to capture traffic. It will only capture traffic from the tested application.
Frida
By default, it will also use some Frida Scripts to bypass SSL pinning, root detection and debugger detection and to monitor interesting APIs.
MobSF can also invoke exported activities, grab screenshots of them and save them for the report.
To start the dynamic testing press the green bottom: "Start Instrumentation". Press the "Frida Live Logs" to see the logs generated by the Frida scripts and "Live API Monitor" to see all the invocation to hooked methods, arguments passed and returned values (this will appear after pressing "Start Instrumentation").
MobSF also allows you to load your own Frida scripts (to send the results of your Friday scripts to MobSF use the function send()). It also has several pre-written scripts you can load (you can add more in MobSF/DynamicAnalyzer/tools/frida_scripts/others/), just select them, press "Load" and press "Start Instrumentation" (you will be able to see the logs of that scripts inside "Frida Live Logs").
Moreover, you have some Auxiliary Frida functionalities:
- Enumerate Loaded Classes: It will print all the loaded classes
- Capture Strings: It will print all the capture strings while using the application (super noisy)
- Capture String Comparisons: Could be very useful. It will show the 2 strings being compared and if the result was True or False.
- Enumerate Class Methods: Put the class name (like "java.io.File") and it will print all the methods of the class.
- Search Class Pattern: Search classes by pattern
- Trace Class Methods: Trace a whole class (see inputs and outputs of all methods of th class). Remember that by default MobSF traces several interesting Android Api methods.
Once you have selected the auxiliary module you want to use you need to press "Start Intrumentation" and you will see all the outputs in "Frida Live Logs".
Shell
Mobsf pia inakuletea shell yenye baadhi ya adb commands, MobSF commands, na amri za kawaida za shell chini ya ukurasa wa uchambuzi wa dynamic. Baadhi ya amri za kuvutia:
help
shell ls
activities
exported_activities
services
receivers
HTTP tools
Wakati trafiki ya http inakamatwa unaweza kuona mtazamo mbaya wa trafiki iliyokamatwa kwenye "HTTP(S) Traffic" chini au mtazamo mzuri kwenye "Start HTTPTools" kitufe kibichi. Kutoka kwenye chaguo la pili, unaweza kutuma maombi yaliyokamatwa kwa proxies kama Burp au Owasp ZAP.
Ili kufanya hivyo, washa Burp --> zimisha Intercept --> katika MobSB HTTPTools chagua ombi --> bonyeza "Send to Fuzzer" --> chagua anwani ya proxy (http://127.0.0.1:8080\).
Mara tu unapo maliza uchambuzi wa dynamic na MobSF unaweza kubonyeza "Start Web API Fuzzer" ili fuzz maombi ya http na kutafuta udhaifu.
{% hint style="info" %} Baada ya kufanya uchambuzi wa dynamic na MobSF mipangilio ya proxy inaweza kuwa haijapangwa vizuri na huwezi kuziweka sawa kutoka kwenye GUI. Unaweza kurekebisha mipangilio ya proxy kwa kufanya:
adb shell settings put global http_proxy :0
{% endhint %}
Msaada wa Uchambuzi wa Kijamii na Inspeckage
Unaweza kupata chombo kutoka Inspeckage.
Chombo hiki kitatumia Hooks kukujulisha kila kinachotokea katika programu wakati unafanya uchambuzi wa kijamii.
Yaazhini
Hii ni chombo bora kufanya uchambuzi wa statiki na GUI
Qark
Chombo hiki kimeundwa kutafuta udhaifu wa usalama wa programu za Android kadhaa, iwe katika kanuni ya chanzo au APKs zilizofungashwa. Chombo hiki pia ni capable of creating a "Proof-of-Concept" deployable APK na ADB commands, ili kutumia baadhi ya udhaifu uliofindika (Shughuli zilizo wazi, nia, tapjacking...). Kama ilivyo kwa Drozer, hakuna haja ya ku-root kifaa cha mtihani.
pip3 install --user qark # --user is only needed if not using a virtualenv
qark --apk path/to/my.apk
qark --java path/to/parent/java/folder
qark --java path/to/specific/java/file.java
ReverseAPK
- Inaonyesha faili zote zilizotolewa kwa ajili ya rejeleo rahisi
- Inachambua faili za APK moja kwa moja hadi katika muundo wa Java na Smali
- Changanua AndroidManifest.xml kwa ajili ya udhaifu na tabia za kawaida
- Uchambuzi wa msimbo wa chanzo wa statiki kwa ajili ya udhaifu na tabia za kawaida
- Taarifa za kifaa
- na zaidi
reverse-apk relative/path/to/APP.apk
SUPER Android Analyzer
SUPER ni programu ya amri ambayo inaweza kutumika katika Windows, MacOS X na Linux, inayochambua faili za .apk kutafuta udhaifu. Inafanya hivyo kwa kubonyeza APKs na kutumia mfululizo wa sheria kugundua udhaifu hao.
Sheria zote zinazingatia faili ya rules.json, na kila kampuni au mtathmini anaweza kuunda sheria zake mwenyewe kuchambua kile wanachohitaji.
Pakua binaries za hivi karibuni kutoka kwenye ukurasa wa upakuaji
super-analyzer {apk_file}
StaCoAn
StaCoAn ni chombo crossplatform ambacho kinawasaidia waendelezaji, wawindaji wa bugbounty na hackers wa kimaadili wanaofanya static code analysis kwenye programu za simu.
Wazo ni kwamba unavuta na kuacha faili yako ya programu ya simu (faili .apk au .ipa) kwenye programu ya StaCoAn na itaunda ripoti ya kuona na kubebeka kwako. Unaweza kubadilisha mipangilio na orodha za maneno ili kupata uzoefu wa kibinafsi.
Pakua toleo la hivi karibuni:
./stacoan
AndroBugs
AndroBugs Framework ni mfumo wa uchambuzi wa udhaifu wa Android ambao unawasaidia waendelezaji au hackers kutafuta udhaifu wa usalama unaoweza kutokea katika programu za Android.
Windows releases
python androbugs.py -f [APK file]
androbugs.exe -f [APK file]
Androwarn
Androwarn ni chombo ambacho lengo lake kuu ni kugundua na kumwonya mtumiaji kuhusu tabia mbaya zinazoweza kutokea zinazotengenezwa na programu ya Android.
Ugunduzi unafanywa kwa uchambuzi wa statiki wa bytecode ya Dalvik ya programu, inayowakilishwa kama Smali, kwa kutumia maktaba ya androguard.
Chombo hiki kinatafuta tabia za kawaida za programu "mbaya" kama: Uhamasishaji wa vitambulisho vya Simu, Ukatishaji wa mtiririko wa sauti/video, Marekebisho ya data za PIM, Utekelezaji wa msimbo wa kiholela...
python androwarn.py -i my_application_to_be_analyzed.apk -r html -v 3
MARA Framework
MARA ni Mobile Application Reverse engineering na Analysis Framework. Ni chombo ambacho kinaweka pamoja zana zinazotumika mara kwa mara za uhandisi wa nyuma na uchambuzi wa programu za simu, kusaidia katika kupima programu za simu dhidi ya vitisho vya usalama wa simu vya OWASP. Lengo lake ni kufanya kazi hii iwe rahisi na rafiki kwa watengenezaji wa programu za simu na wataalamu wa usalama.
Inaweza:
- Kutolewa Java na Smali code kwa kutumia zana tofauti
- Kuchambua APKs kwa kutumia: smalisca, ClassyShark, androbugs, androwarn, APKiD
- Kutolewa taarifa za kibinafsi kutoka kwa APK kwa kutumia regexps.
- Kuchambua Manifest.
- Kuchambua maeneo yaliyopatikana kwa kutumia: pyssltest, testssl na whatweb
- Kuondoa obfuscation ya APK kupitia apk-deguard.com
Koodous
Inatumika kugundua malware: https://koodous.com/
Obfuscating/Deobfuscating code
Kumbuka kwamba kulingana na huduma na usanidi unayotumia kuondoa obfuscation ya msimbo. Siri zinaweza kuwa zimeondolewa obfuscated au la.
ProGuard
Kutoka Wikipedia: ProGuard ni chombo cha amri cha wazi ambacho kinapunguza, kinaboresha na kinaondoa obfuscation ya Java code. Inaweza kuboresha bytecode pamoja na kugundua na kuondoa maagizo yasiyotumika. ProGuard ni programu ya bure na inasambazwa chini ya GNU General Public License, toleo la 2.
ProGuard inasambazwa kama sehemu ya Android SDK na inafanya kazi wakati wa kujenga programu katika hali ya kutolewa.
DexGuard
Pata mwongozo wa hatua kwa hatua wa kuondoa obfuscation ya apk katika https://blog.lexfo.fr/dexguard.html
(Kutoka kwa mwongozo huo) Mara ya mwisho tulipoangalia, hali ya uendeshaji ya Dexguard ilikuwa:
- kupakia rasilimali kama InputStream;
- kutoa matokeo kwa darasa linalorithishwa kutoka FilterInputStream ili kuyafungua;
- kufanya obfuscation isiyo na maana ili kupoteza dakika chache za muda kutoka kwa mhandisi wa nyuma;
- kutoa matokeo yaliyofunguliwa kwa ZipInputStream ili kupata faili ya DEX;
- hatimaye kupakia DEX inayotokana kama Rasilimali kwa kutumia njia ya
loadDex.
DeGuard
DeGuard inarudisha mchakato wa obfuscation uliofanywa na zana za obfuscation za Android. Hii inaruhusu uchambuzi mwingi wa usalama, ikiwa ni pamoja na ukaguzi wa msimbo na kutabiri maktaba.
Unaweza kupakia APK iliyokuwa obfuscated kwenye jukwaa lao.
Simplify
Ni deobfuscator ya android ya jumla. Simplify inatekeleza programu kwa karibu ili kuelewa tabia yake na kisha jaribu kuboresha msimbo ili iwe na tabia sawa lakini iwe rahisi kwa binadamu kuelewa. Kila aina ya kuboresha ni rahisi na ya jumla, hivyo haijalishi ni aina gani maalum ya obfuscation inayotumika.
APKiD
APKiD inakupa taarifa kuhusu jinsi APK ilivyotengenezwa. Inatambua waandishi wengi, packers, obfuscators, na vitu vingine vya ajabu. Ni PEiD kwa Android.
Manual
Somai hii tutorial ili kujifunza mbinu za jinsi ya kurudi nyuma obfuscation ya kawaida
Labs
Androl4b
AndroL4b ni mashine ya virtual ya usalama wa Android inayotegemea ubuntu-mate inajumuisha mkusanyiko wa mfumo wa hivi karibuni, mafunzo na maabara kutoka kwa wahandisi wa usalama na watafiti mbalimbali kwa ajili ya uhandisi wa nyuma na uchambuzi wa malware.
References
- https://owasp.org/www-project-mobile-app-security/
- https://appsecwiki.com/#/ Ni orodha nzuri ya rasilimali
- https://maddiestone.github.io/AndroidAppRE/ Kozi ya haraka ya Android
- https://manifestsecurity.com/android-application-security/
- https://github.com/Ralireza/Android-Security-Teryaagh
- https://www.youtube.com/watch?v=PMKnPaGWxtg&feature=youtu.be&ab_channel=B3nacSec
Yet to try

Join HackenProof Discord server to communicate with experienced hackers and bug bounty hunters!
Hacking Insights
Engage with content that delves into the thrill and challenges of hacking
Real-Time Hack News
Keep up-to-date with fast-paced hacking world through real-time news and insights
Latest Announcements
Stay informed with the newest bug bounties launching and crucial platform updates
Join us on Discord and start collaborating with top hackers today!
{% hint style="success" %}
Learn & practice AWS Hacking: HackTricks Training AWS Red Team Expert (ARTE)
HackTricks Training AWS Red Team Expert (ARTE)
Learn & practice GCP Hacking:  HackTricks Training GCP Red Team Expert (GRTE)
HackTricks Training GCP Red Team Expert (GRTE)
Support HackTricks
- Check the subscription plans!
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @hacktricks_live.
- Share hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.