6.5 KiB
macOS Installers Abuse
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
- Discover The PEASS Family, our collection of exclusive NFTs
- Get the official PEASS & HackTricks swag
- Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
- Share your hacking tricks by submitting PRs to the hacktricks repo and hacktricks-cloud repo.
Basic Information
A macOS installer package (also known as a .pkg file) is a file format used by macOS to distribute software. These files are like a box that contains everything a piece of software needs to install and run correctly.
The package file itself is an archive that holds a hierarchy of files and directories that will be installed on the target computer. It can also include scripts to perform tasks before and after the installation, like setting up configuration files or cleaning up old versions of the software.
Hierarchy
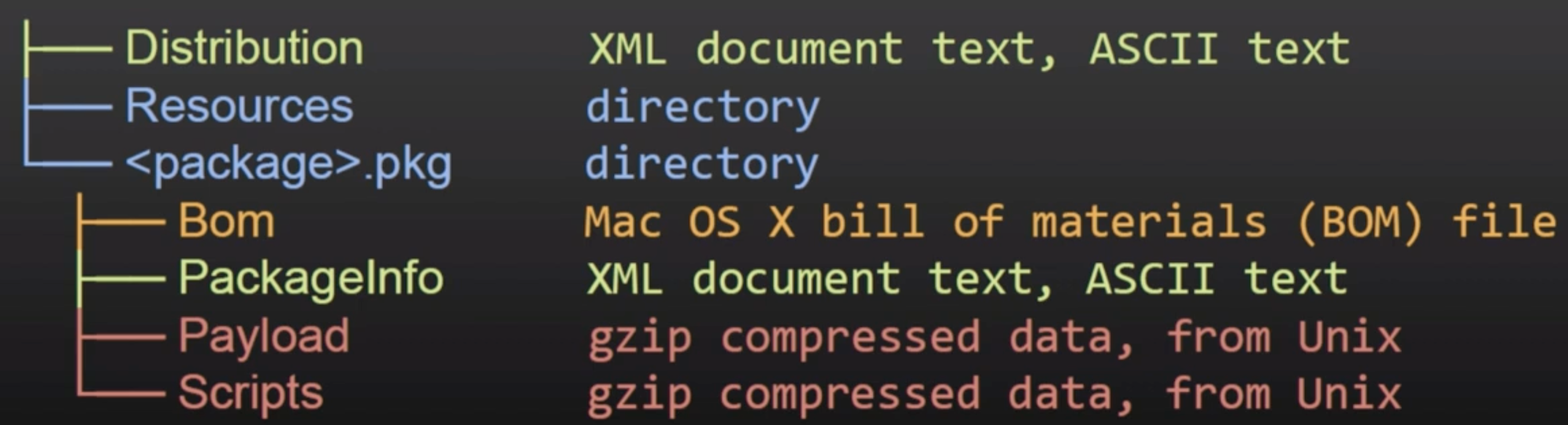
- Distribution (xml): Customizations (title, welcome text…) and script/installation checks
- PackageInfo (xml): Info, install requirements, install location, paths to scripts to run
- Bill of materials (bom): List of files to install, update or remove with file permissions
- Payload (CPIO archive gzip compresses): Files to install in the
install-locationfrom PackageInfo - Scripts (CPIO archive gzip compressed): Pre and post install scripts and more resources extracted to a temp directory for execution.
Decompress
# Tool to directly get the files inside a package
pkgutil —expand "/path/to/package.pkg" "/path/to/out/dir"
# Get the files ina. more manual way
mkdir -p "/path/to/out/dir"
cd "/path/to/out/dir"
xar -xf "/path/to/package.pkg"
# Decompress also the CPIO gzip compressed ones
cat Scripts | gzip -dc | cpio -i
cpio -i < Scripts
Privesc via pkg abuse
Execution from public directories
If a pre or post installation script is for example executing from /var/tmp/Installerutil, and attacker could control that script so he escalate privileges whenever it's executed. Or another similar example:

AuthorizationExecuteWithPrivileges
This is a public function that several installers and updaters will call to execute something as root. This function accepts the path of the file to execute as parameter, however, if an attacker could modify this file, he will be able to abuse its execution with root to escalate privileges.
# Breakpoint in the function to check wich file is loaded
(lldb) b AuthorizationExecuteWithPrivileges
# You could also check FS events to find this missconfig
For more info check this talk: https://www.youtube.com/watch?v=lTOItyjTTkw
Execution by mounting
If an installer writes to /tmp/fixedname/bla/bla, it's possible to create a mount over /tmp/fixedname with noowners so you could modify any file during the installation to abuse the installation process.
An example of this is CVE-2021-26089 which managed to overwrite a periodic script to get execution as root. For more information take a look to the talk: OBTS v4.0: "Mount(ain) of Bugs" - Csaba Fitzl
References
☁️ HackTricks Cloud ☁️ -🐦 Twitter 🐦 - 🎙️ Twitch 🎙️ - 🎥 Youtube 🎥
- Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
- Discover The PEASS Family, our collection of exclusive NFTs
- Get the official PEASS & HackTricks swag
- Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
- Share your hacking tricks by submitting PRs to the hacktricks repo and hacktricks-cloud repo.