| .. | ||
| README.md | ||
| volatility-cheatsheet.md | ||
Memory dump analysis
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
- Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
- Discover The PEASS Family, our collection of exclusive NFTs
- Get the official PEASS & HackTricks swag
- Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
- Share your hacking tricks by submitting PRs to the hacktricks repo and hacktricks-cloud repo.

RootedCON is the most relevant cybersecurity event in Spain and one of the most important in Europe. With the mission of promoting technical knowledge, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
{% embed url="https://www.rootedcon.com/" %}
Start
Start searching for malware inside the pcap. Use the tools mentioned in Malware Analysis.
Volatility
Volatility is the main open-source framework for memory dump analysis. This Python tool analyzes dumps from external sources or VMware VMs, identifying data like processes and passwords based on the dump's OS profile. It's extensible with plugins, making it highly versatile for forensic investigations.
Mini dump crash report
When the dump is small (just some KB, maybe a few MB) then it's probably a mini dump crash report and not a memory dump.
If you have Visual Studio installed, you can open this file and bind some basic information like process name, architecture, exception info and modules being executed:
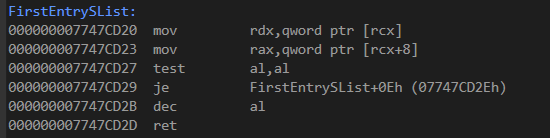
You can also load the exception and see the decompiled instructions
Anyway, Visual Studio isn't the best tool to perform an analysis of the depth of the dump.
You should open it using IDA or Radare to inspection it in depth.

RootedCON is the most relevant cybersecurity event in Spain and one of the most important in Europe. With the mission of promoting technical knowledge, this congress is a boiling meeting point for technology and cybersecurity professionals in every discipline.
{% embed url="https://www.rootedcon.com/" %}
Learn AWS hacking from zero to hero with htARTE (HackTricks AWS Red Team Expert)!
- Do you work in a cybersecurity company? Do you want to see your company advertised in HackTricks? or do you want to have access to the latest version of the PEASS or download HackTricks in PDF? Check the SUBSCRIPTION PLANS!
- Discover The PEASS Family, our collection of exclusive NFTs
- Get the official PEASS & HackTricks swag
- Join the 💬 Discord group or the telegram group or follow me on Twitter 🐦@carlospolopm.
- Share your hacking tricks by submitting PRs to the hacktricks repo and hacktricks-cloud repo.